ASN 1 Cryptographic files Zdenk ha ASN 1










- Slides: 39

ASN. 1: Cryptographic files Zdeněk Říha

ASN. 1 Grammar l To understand the structure (what is the meaning of particular fields) we need ASN. 1 grammar

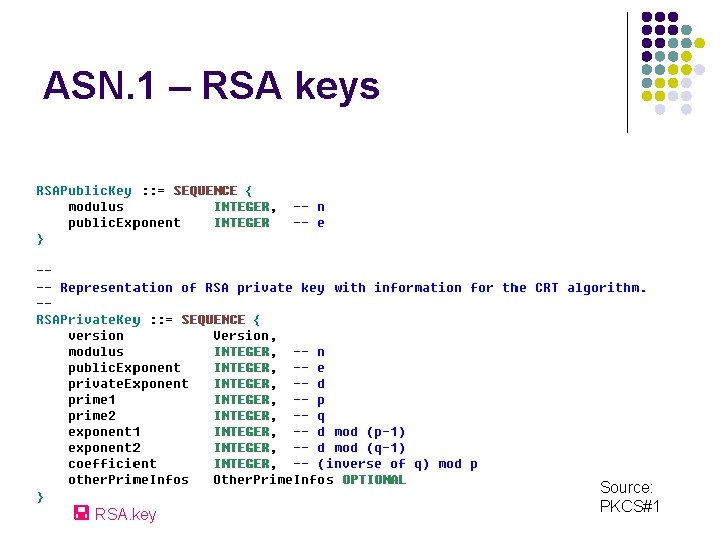
ASN. 1 – RSA keys RSA. key Source: PKCS#1

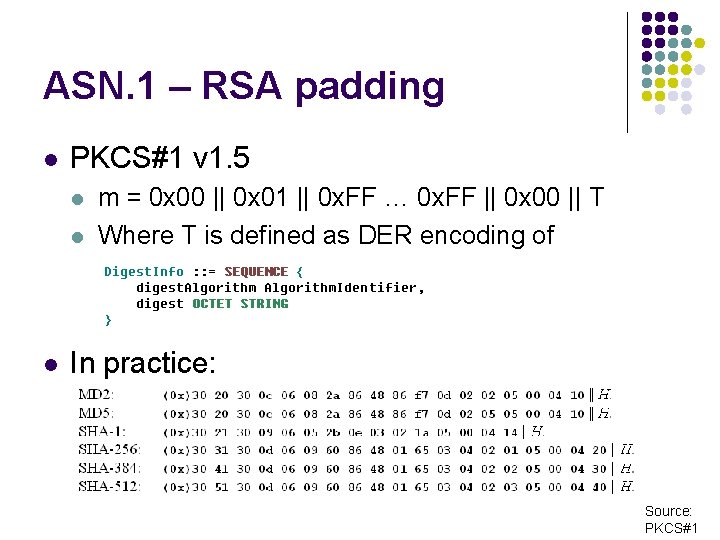
ASN. 1 – RSA padding l PKCS#1 v 1. 5 l l l m = 0 x 00 || 0 x 01 || 0 x. FF … 0 x. FF || 0 x 00 || T Where T is defined as DER encoding of In practice: Source: PKCS#1

ASN. 1 – RSA signature l RSA signature is the number s = md mod n TSA. crt

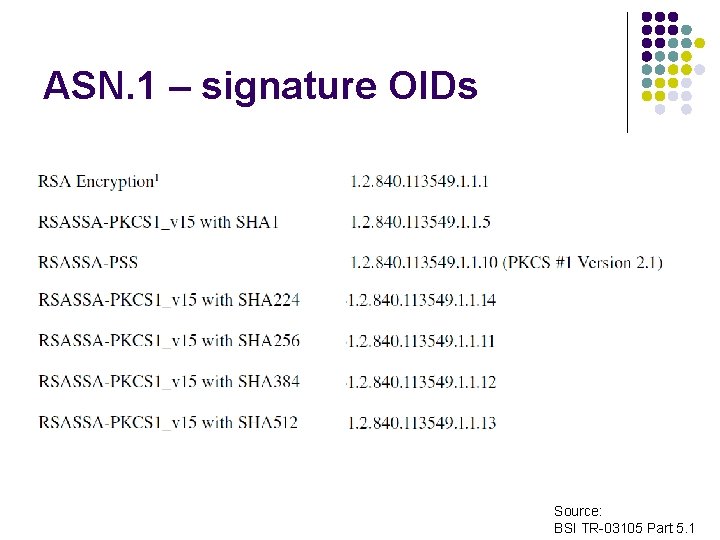
ASN. 1 – signature OIDs Source: BSI TR-03105 Part 5. 1

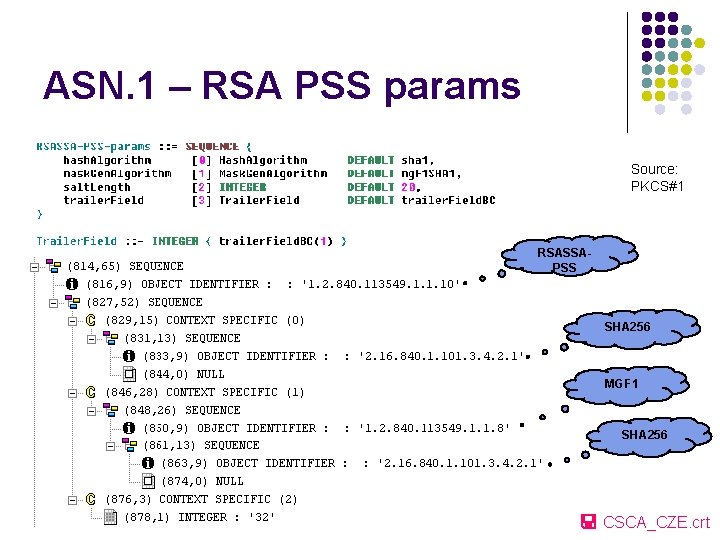
ASN. 1 – RSA PSS params Source: PKCS#1 RSASSAPSS SHA 256 MGF 1 SHA 256 CSCA_CZE. crt

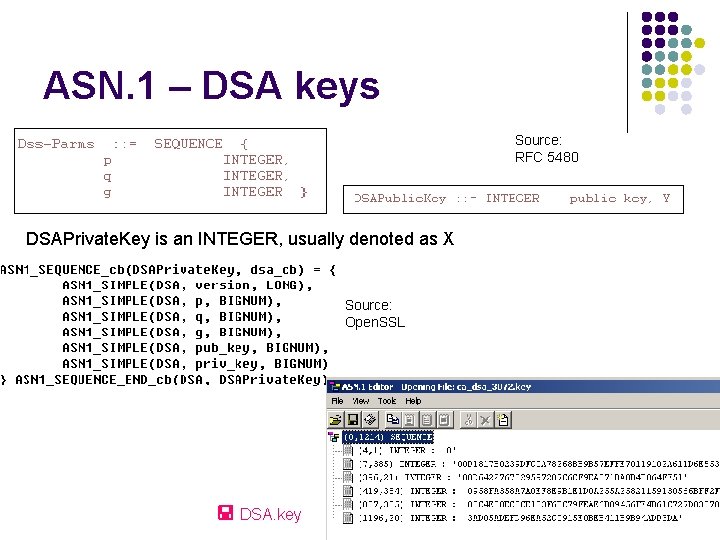
ASN. 1 – DSA keys Source: RFC 5480 DSAPrivate. Key is an INTEGER, usually denoted as X Source: Open. SSL DSA. key

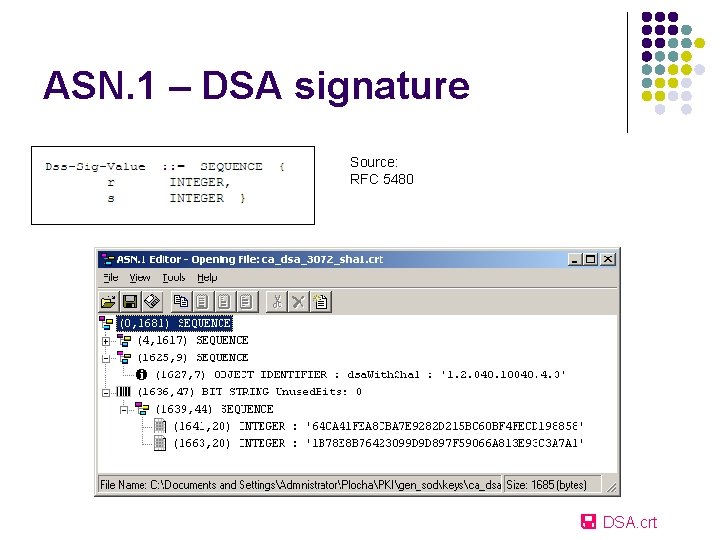
ASN. 1 – DSA signature Source: RFC 5480 DSA. crt

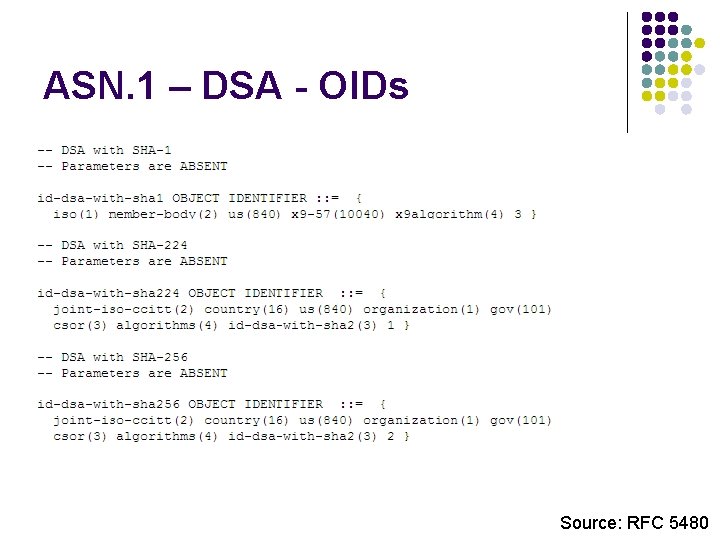
ASN. 1 – DSA - OIDs Source: RFC 5480

ASN. 1 – ECDSA keys INTEGER ECPoint Source: RFC 5915

ASN. 1 - ECDSA public key CSCA_Switzerland. crt

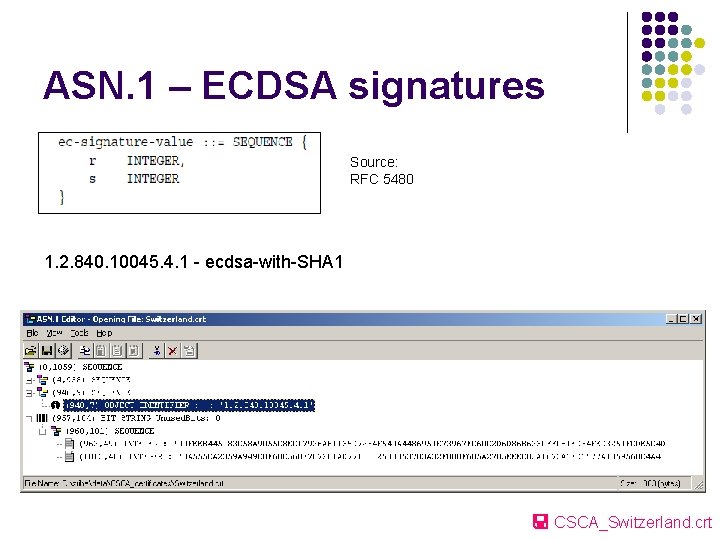
ASN. 1 – ECDSA signatures Source: RFC 5480 1. 2. 840. 10045. 4. 1 - ecdsa-with-SHA 1 CSCA_Switzerland. crt

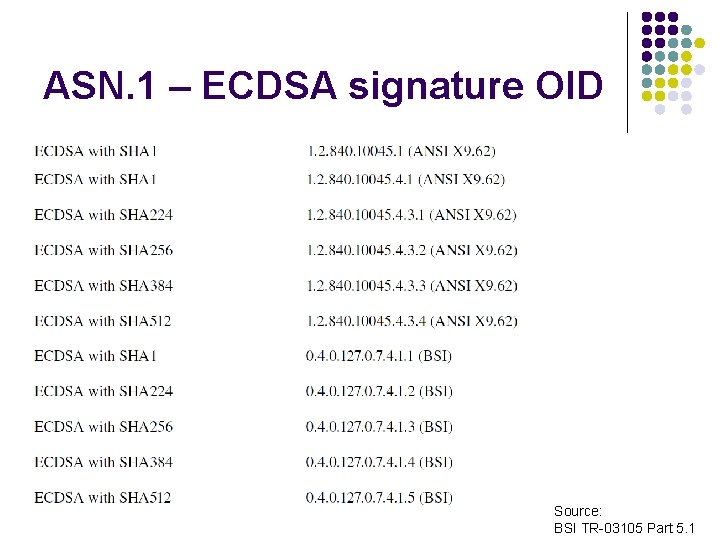
ASN. 1 – ECDSA signature OID Source: BSI TR-03105 Part 5. 1

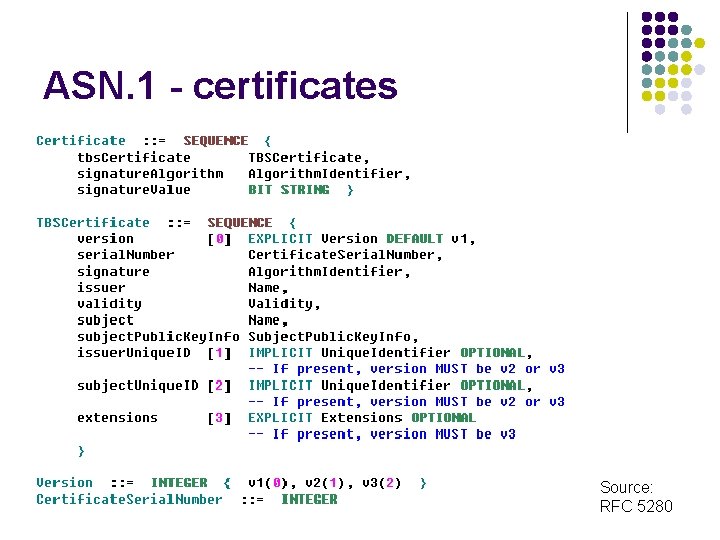
ASN. 1 - certificates Source: RFC 5280

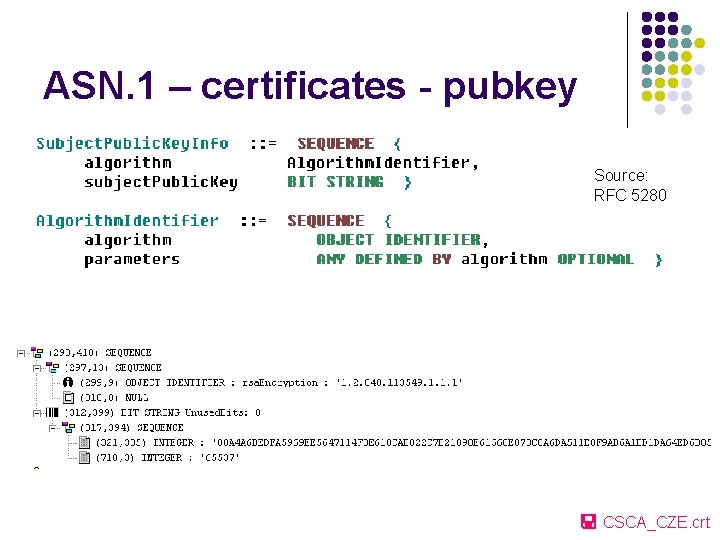
ASN. 1 – certificates - pubkey Source: RFC 5280 CSCA_CZE. crt

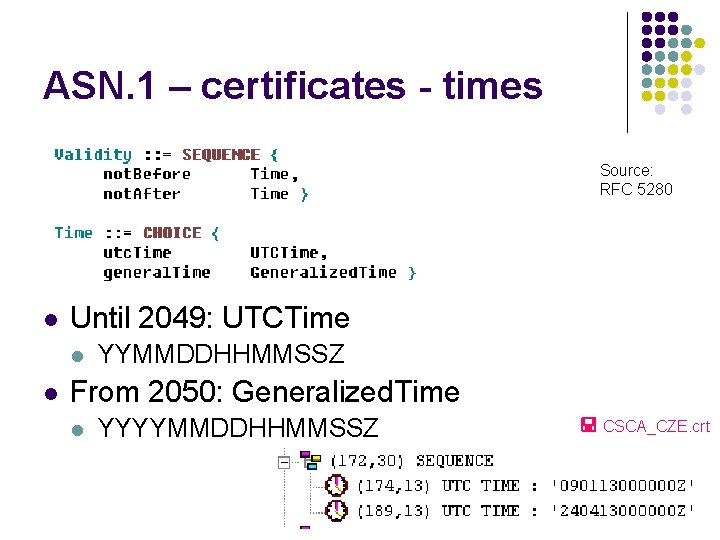
ASN. 1 – certificates - times Source: RFC 5280 l Until 2049: UTCTime l l YYMMDDHHMMSSZ From 2050: Generalized. Time l YYYYMMDDHHMMSSZ CSCA_CZE. crt

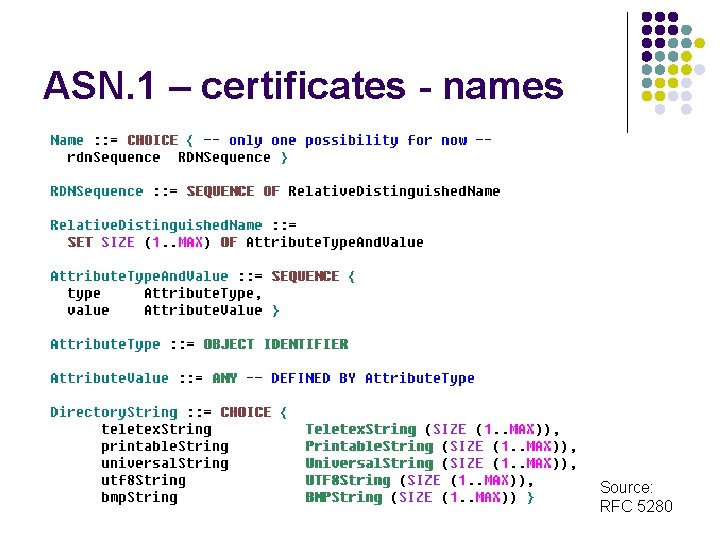
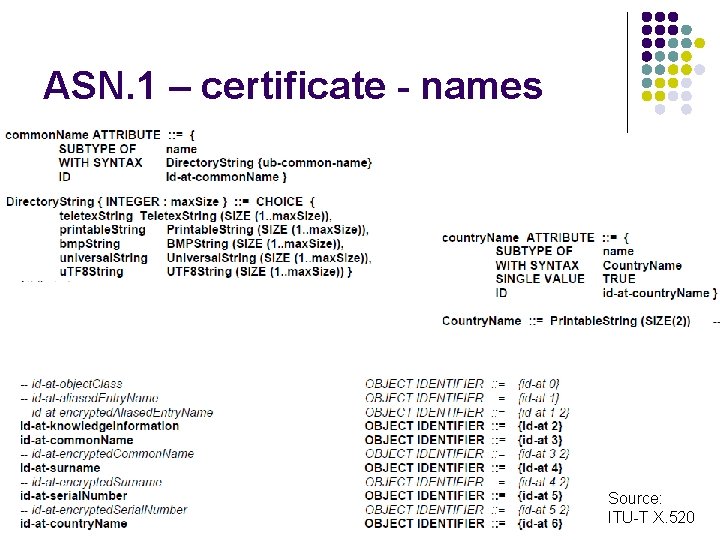
ASN. 1 – certificates - names Source: RFC 5280

ASN. 1 – certificate - names CSCA_CZE. crt

ASN. 1 – certificate - names Source: ITU-T X. 520

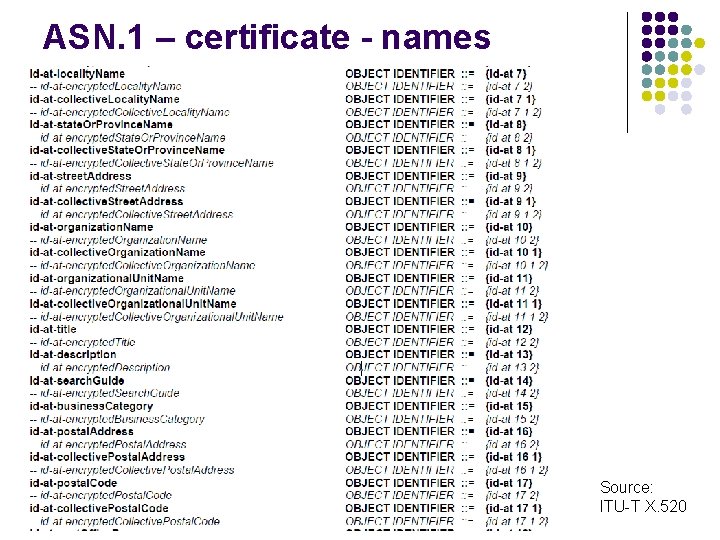
ASN. 1 – certificate - names Source: ITU-T X. 520

Certificate profiles l l For particular areas/purposes there exist certificate profiles which prescribe what kind of attributes will be used in Names E. g. for electronic passports ICAO Doc. 9303 states: Source: ICAO Doc. 9303

ASN. 1 – certificates – v 3 Source: RFC 5280 l Critical x non-critical extensions

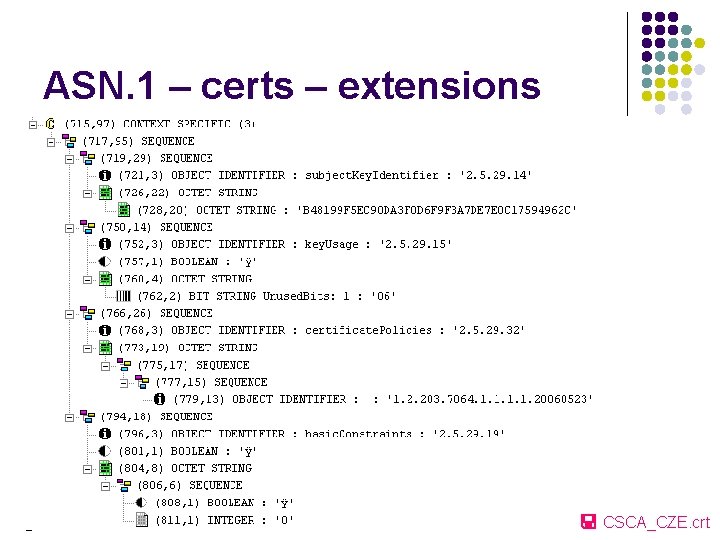
ASN. 1 – certs – extensions CSCA_CZE. crt

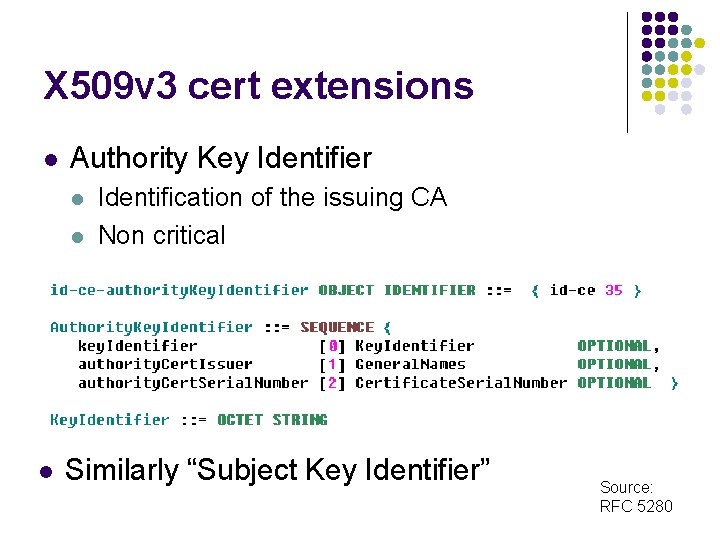
X 509 v 3 cert extensions l Authority Key Identifier l l l Identification of the issuing CA Non critical Similarly “Subject Key Identifier” Source: RFC 5280

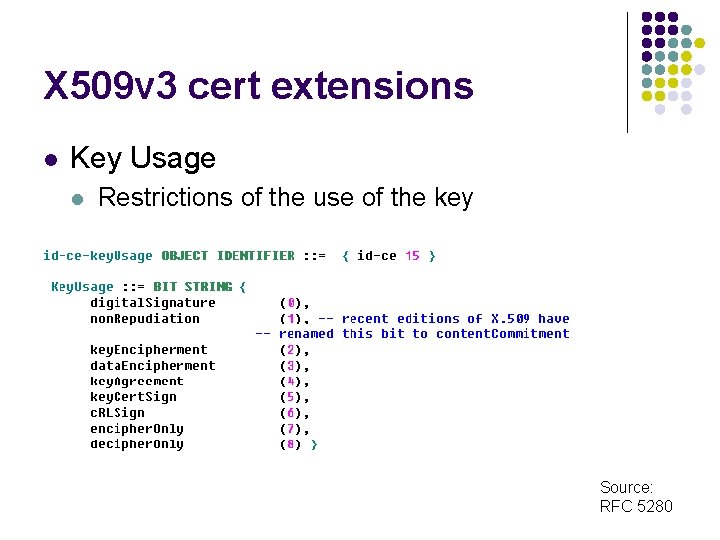
X 509 v 3 cert extensions l Key Usage l Restrictions of the use of the key Source: RFC 5280

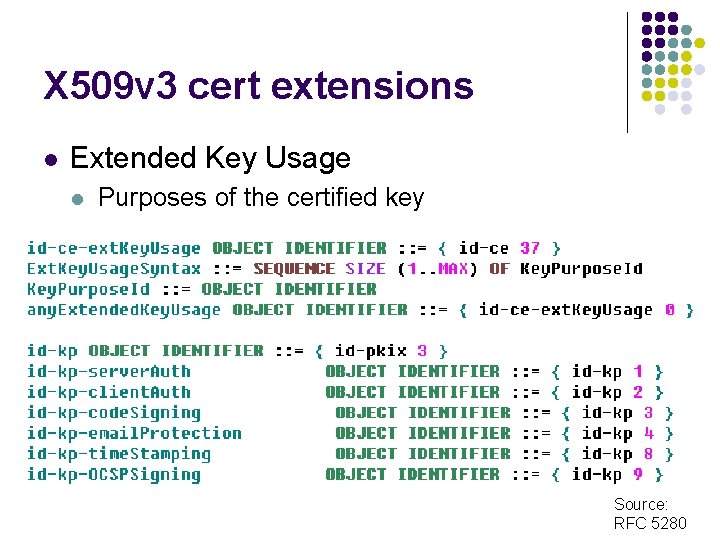
X 509 v 3 cert extensions l Extended Key Usage l Purposes of the certified key Source: RFC 5280

X 509 v 3 cert extensions l Certificate Policies l l Policy relevant for the issue and use of the certificate Preferably only an OID Source: RFC 5280

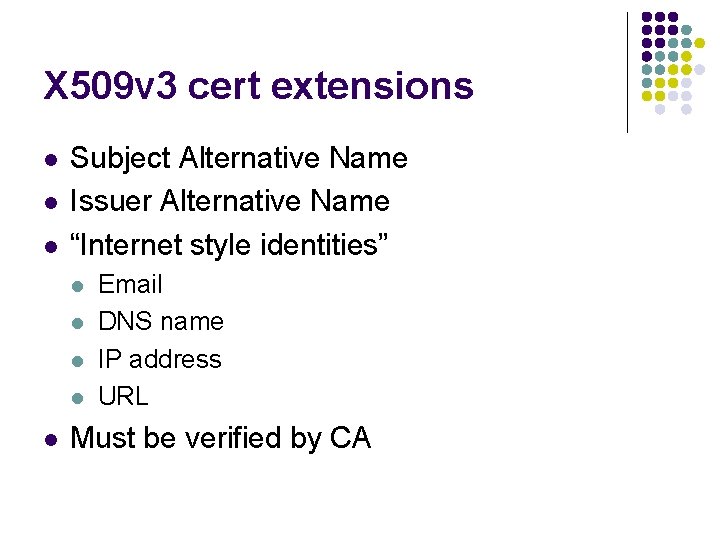
X 509 v 3 cert extensions l l l Subject Alternative Name Issuer Alternative Name “Internet style identities” l l l Email DNS name IP address URL Must be verified by CA

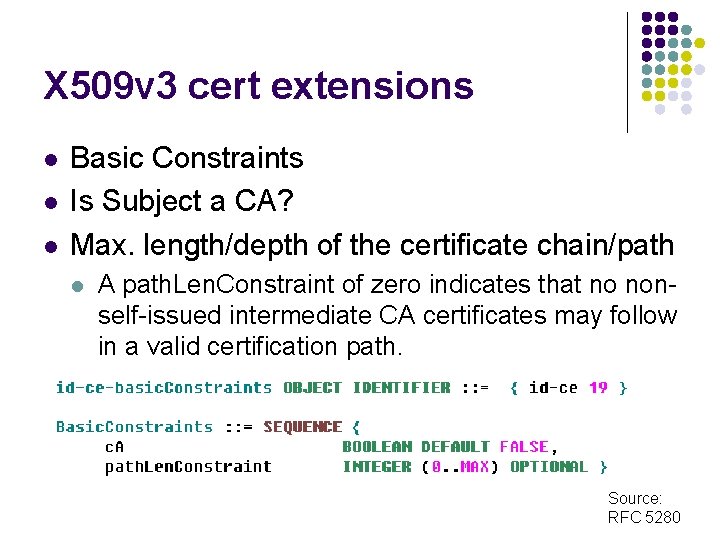
X 509 v 3 cert extensions l l l Basic Constraints Is Subject a CA? Max. length/depth of the certificate chain/path l A path. Len. Constraint of zero indicates that no nonself-issued intermediate CA certificates may follow in a valid certification path. Source: RFC 5280

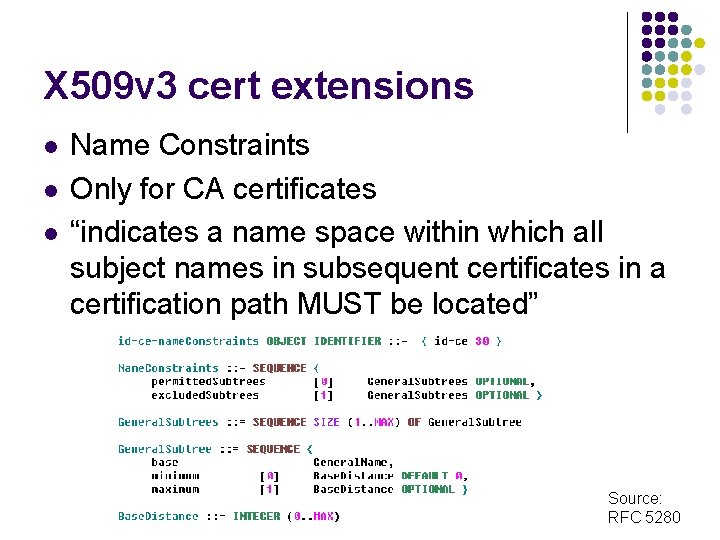
X 509 v 3 cert extensions l l l Name Constraints Only for CA certificates “indicates a name space within which all subject names in subsequent certificates in a certification path MUST be located” Source: RFC 5280

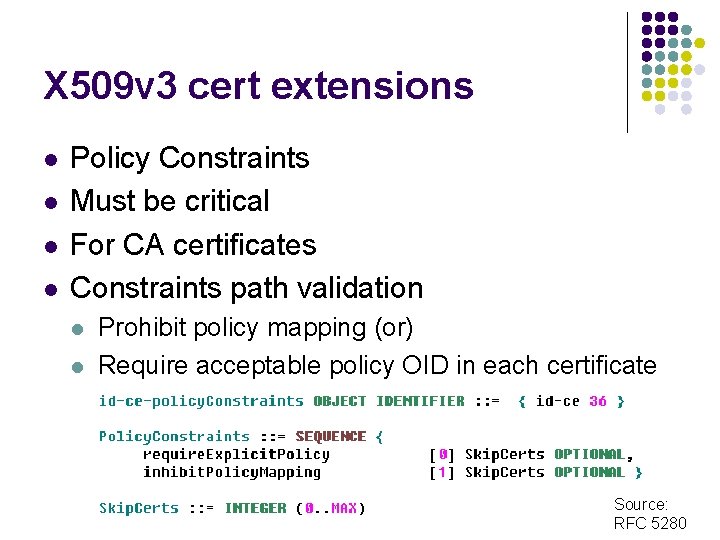
X 509 v 3 cert extensions l l Policy Constraints Must be critical For CA certificates Constraints path validation l l Prohibit policy mapping (or) Require acceptable policy OID in each certificate Source: RFC 5280

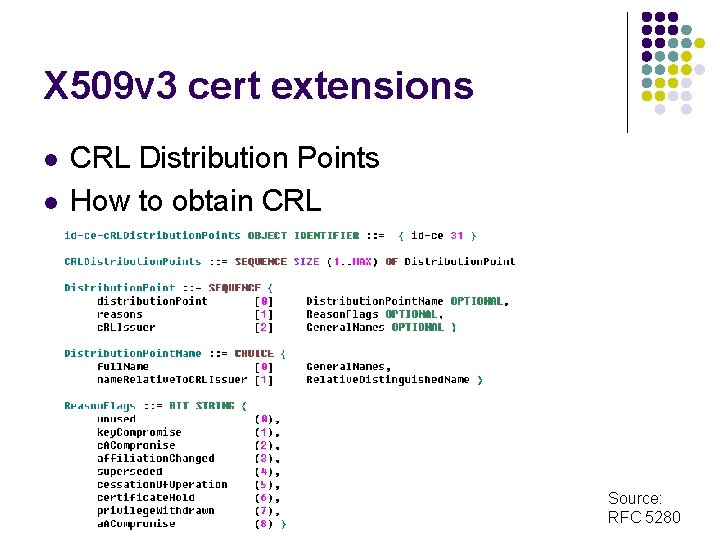
X 509 v 3 cert extensions l l CRL Distribution Points How to obtain CRL Source: RFC 5280

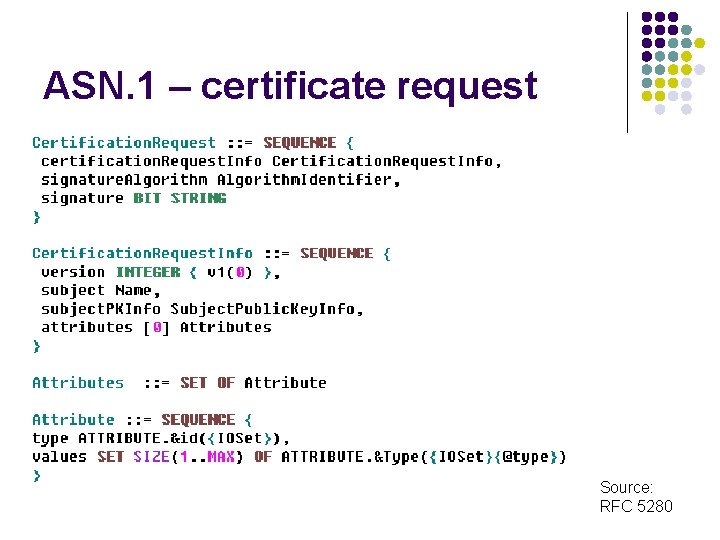
ASN. 1 – certificate request Source: RFC 5280

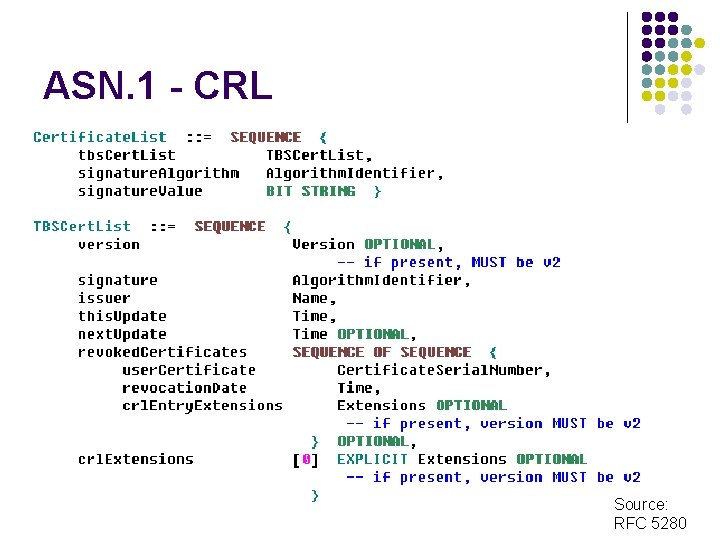
ASN. 1 - CRL Source: RFC 5280

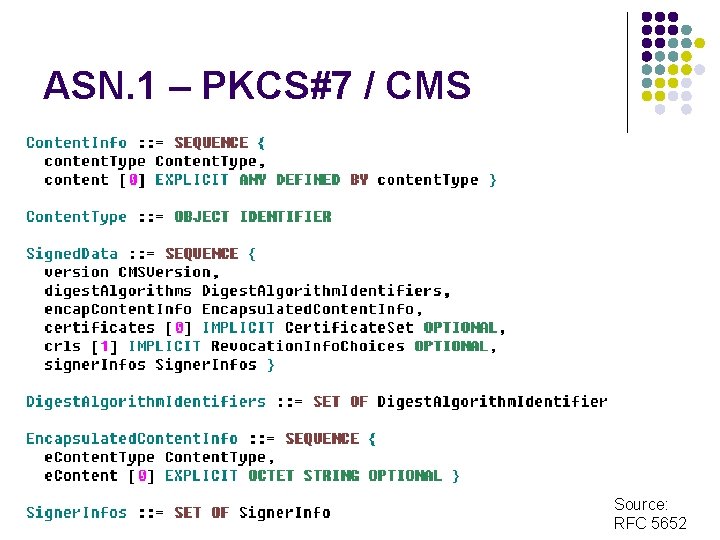
ASN. 1 – PKCS#7 / CMS Source: RFC 5652

ASN. 1 - PKCS#7 / CMS Source: RFC 5652

PKCS#7 Sample France. p 7 s

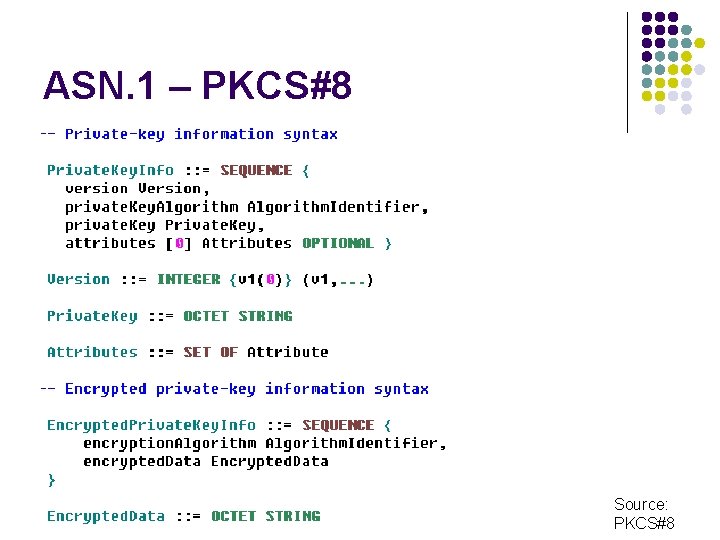
ASN. 1 – PKCS#8 Source: PKCS#8
 Zdenk
Zdenk Dot powai files are binary files
Dot powai files are binary files Cjis security training
Cjis security training Cjis meaning
Cjis meaning Cryptographic tools
Cryptographic tools Kgx-93
Kgx-93 Insecure cryptographic storage challenge 3
Insecure cryptographic storage challenge 3 Insecure cryptographic storage challenge 2
Insecure cryptographic storage challenge 2 Cryptographic attacks
Cryptographic attacks Collision resistant hash function
Collision resistant hash function Mit time lock puzzle
Mit time lock puzzle Cryptographic concepts
Cryptographic concepts Owasp definition
Owasp definition Cryptographic
Cryptographic The strength of any cryptographic system rests with the
The strength of any cryptographic system rests with the Pin punctures steganography
Pin punctures steganography Cryptographic systems are generically classified by
Cryptographic systems are generically classified by Koi 18
Koi 18 Two simple hash functions
Two simple hash functions Indexed sequential file
Indexed sequential file Ged m files
Ged m files Transfer bif files
Transfer bif files Omfi media files
Omfi media files Tsd export files
Tsd export files 320 fahrenheit to celsius
320 fahrenheit to celsius Management files for
Management files for Chapter 17 darwins theory of evolution
Chapter 17 darwins theory of evolution Visual basic and database files
Visual basic and database files Bob files
Bob files What is dqf dot
What is dqf dot Arterial spurts blood spatter
Arterial spurts blood spatter Makefile multiple source files
Makefile multiple source files Face recognition
Face recognition File management in c
File management in c Eznec antenna models
Eznec antenna models Uvm zoo files
Uvm zoo files Data files in c
Data files in c Dynamics 365 multiple files storage
Dynamics 365 multiple files storage Sca tools list
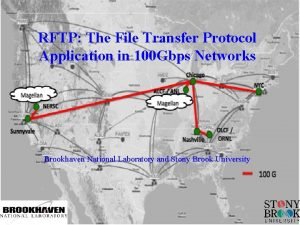
Sca tools list Rftp
Rftp