Architectural Styles Software Architecture Lecture 4 Copyright Richard








- Slides: 63

Architectural Styles Software Architecture Lecture 4 Copyright © Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy. All rights reserved.

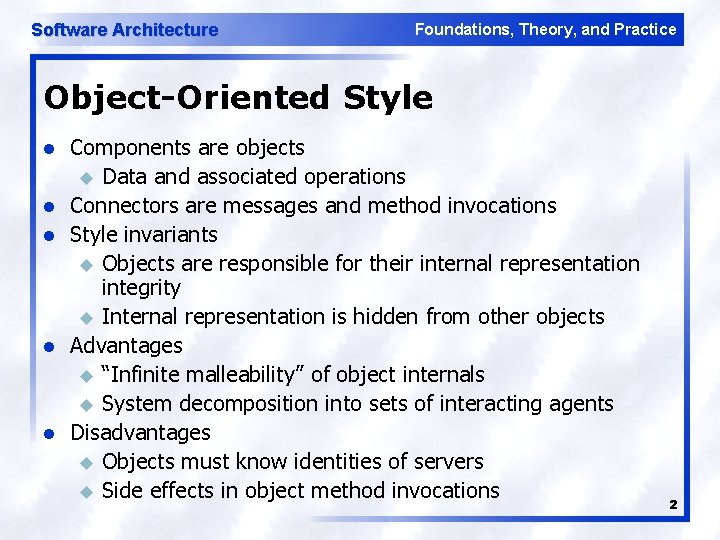
Software Architecture Foundations, Theory, and Practice Object-Oriented Style l l l Components are objects u Data and associated operations Connectors are messages and method invocations Style invariants u Objects are responsible for their internal representation integrity u Internal representation is hidden from other objects Advantages u “Infinite malleability” of object internals u System decomposition into sets of interacting agents Disadvantages u Objects must know identities of servers u Side effects in object method invocations 2

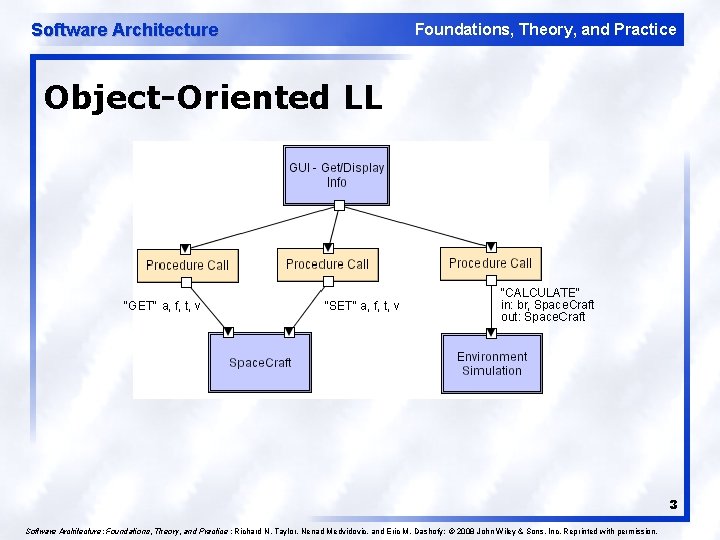
Software Architecture Foundations, Theory, and Practice Object-Oriented LL 3 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

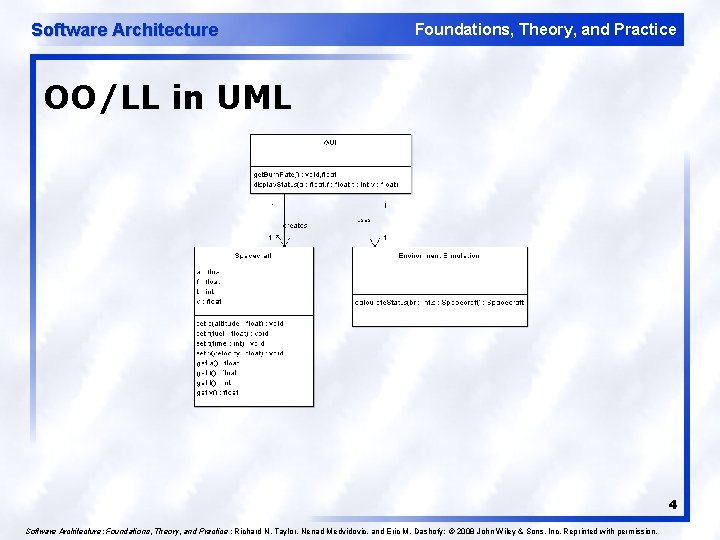
Software Architecture Foundations, Theory, and Practice OO/LL in UML 4 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

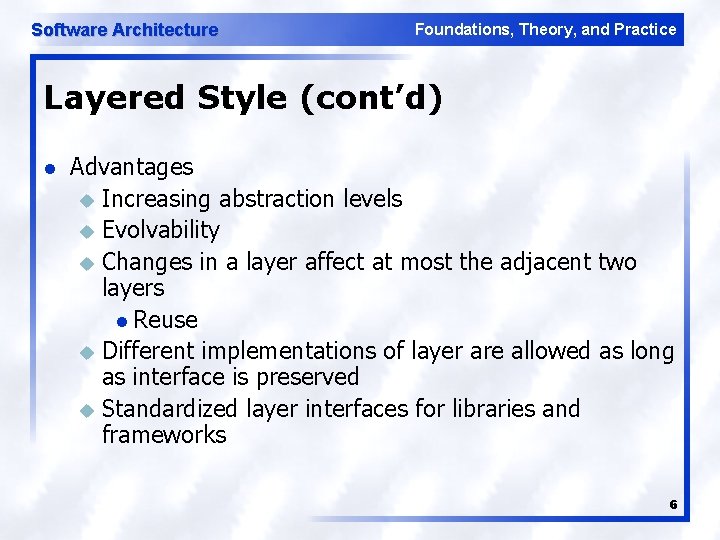
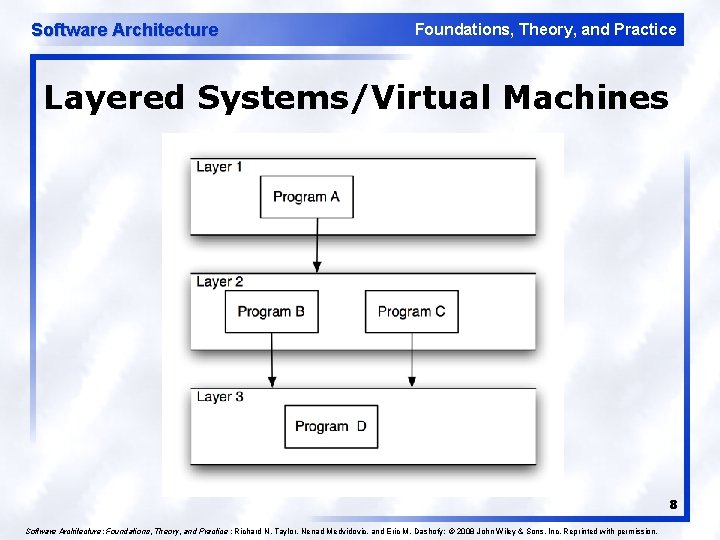
Software Architecture Foundations, Theory, and Practice Layered Style l l l Hierarchical system organization u “Multi-level client-server” u Each layer exposes an interface (API) to be used by above layers Each layer acts as a u Server: service provider to layers “above” u Client: service consumer of layer(s) “below” Connectors are protocols of layer interaction Example: operating systems Virtual machine style results from fully opaque layers 5

Software Architecture Foundations, Theory, and Practice Layered Style (cont’d) l Advantages u Increasing abstraction levels u Evolvability u Changes in a layer affect at most the adjacent two layers l Reuse u Different implementations of layer are allowed as long as interface is preserved u Standardized layer interfaces for libraries and frameworks 6

Software Architecture Foundations, Theory, and Practice Layered Style (cont’d) l l Disadvantages u Not universally applicable u Performance Layers may have to be skipped u Determining the correct abstraction level 7

Software Architecture Foundations, Theory, and Practice Layered Systems/Virtual Machines 8 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture Foundations, Theory, and Practice Layered LL 9 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

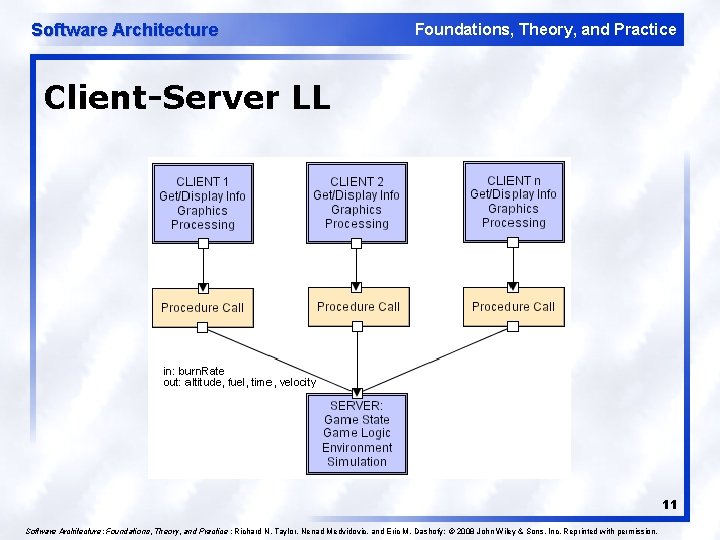
Software Architecture Foundations, Theory, and Practice Client-Server Style l l Components are clients and servers Servers do not know number or identities of clients Clients know server’s identity Connectors are RPC-based network interaction protocols 10

Software Architecture Foundations, Theory, and Practice Client-Server LL 11 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

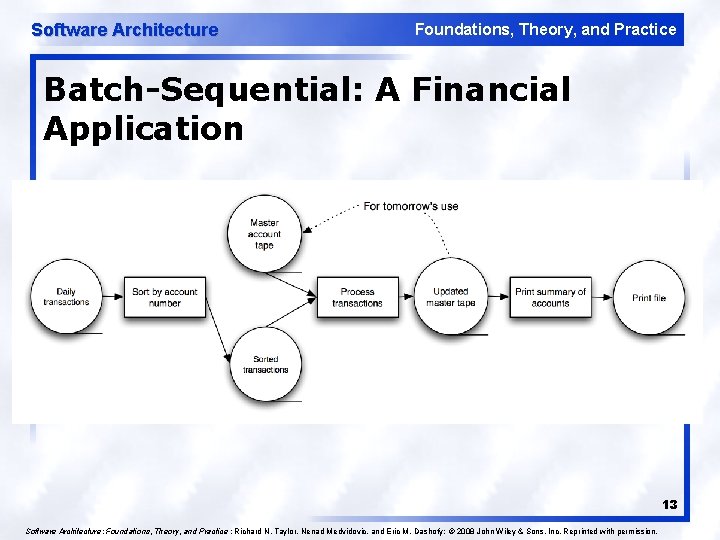
Software Architecture Foundations, Theory, and Practice Data-Flow Styles Batch Sequential u Separate programs are executed in order; data is passed as an aggregate from one program to the next. u Connectors: “The human hand” carrying tapes between the programs, a. k. a. “sneaker-net ” u Data Elements: Explicit, aggregate elements passed from one component to the next upon completion of the producing program’s execution. l Typical uses: Transaction processing in financial systems. “The Granddaddy of Styles” 12

Software Architecture Foundations, Theory, and Practice Batch-Sequential: A Financial Application 13 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

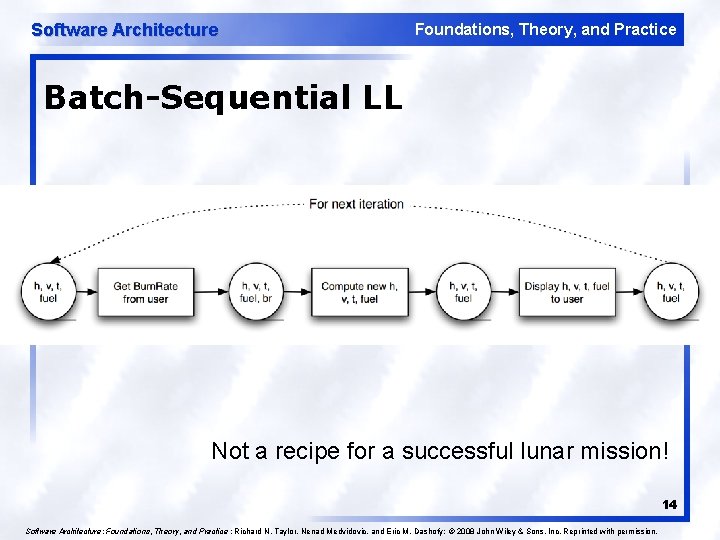
Software Architecture Foundations, Theory, and Practice Batch-Sequential LL Not a recipe for a successful lunar mission! 14 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

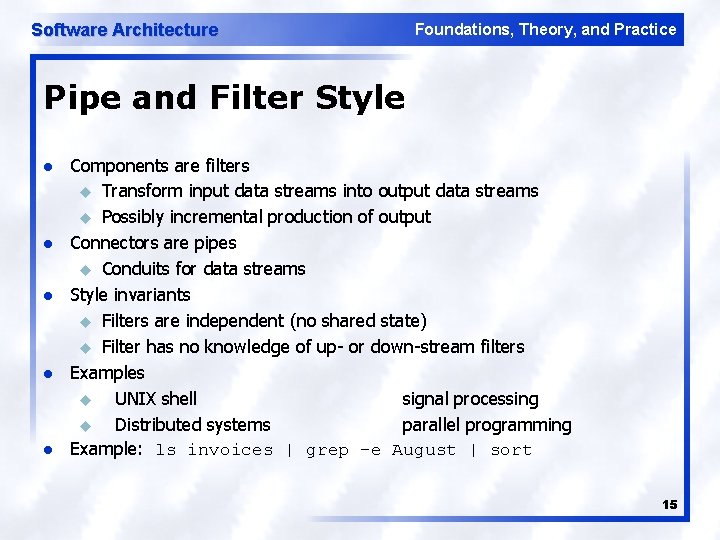
Software Architecture Foundations, Theory, and Practice Pipe and Filter Style l l l Components are filters u Transform input data streams into output data streams u Possibly incremental production of output Connectors are pipes u Conduits for data streams Style invariants u Filters are independent (no shared state) u Filter has no knowledge of up- or down-stream filters Examples u UNIX shell signal processing u Distributed systems parallel programming Example: ls invoices | grep -e August | sort 15

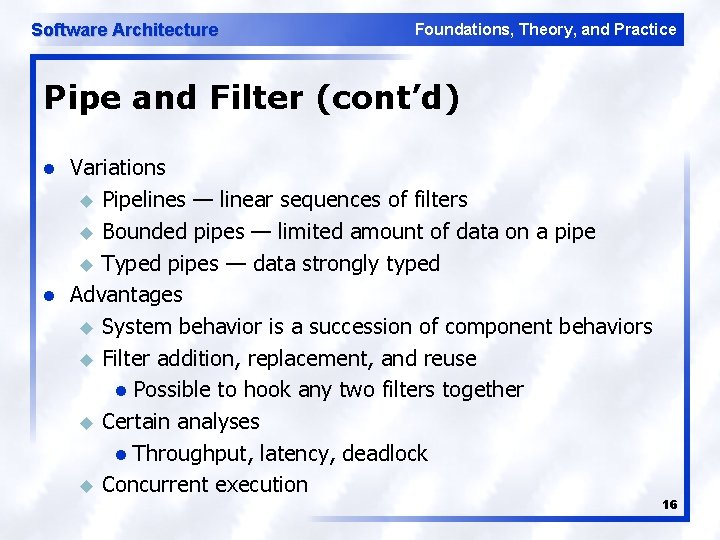
Software Architecture Foundations, Theory, and Practice Pipe and Filter (cont’d) l l Variations u Pipelines — linear sequences of filters u Bounded pipes — limited amount of data on a pipe u Typed pipes — data strongly typed Advantages u System behavior is a succession of component behaviors u Filter addition, replacement, and reuse l Possible to hook any two filters together u Certain analyses l Throughput, latency, deadlock u Concurrent execution 16

Software Architecture Foundations, Theory, and Practice Pipe and Filter (cont’d) l Disadvantages u Batch organization of processing u Interactive applications u Lowest common denominator on data transmission 17

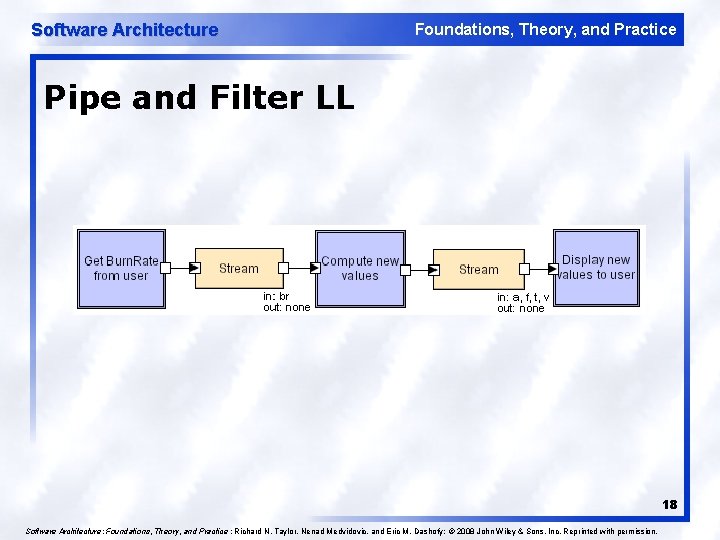
Software Architecture Foundations, Theory, and Practice Pipe and Filter LL 18 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

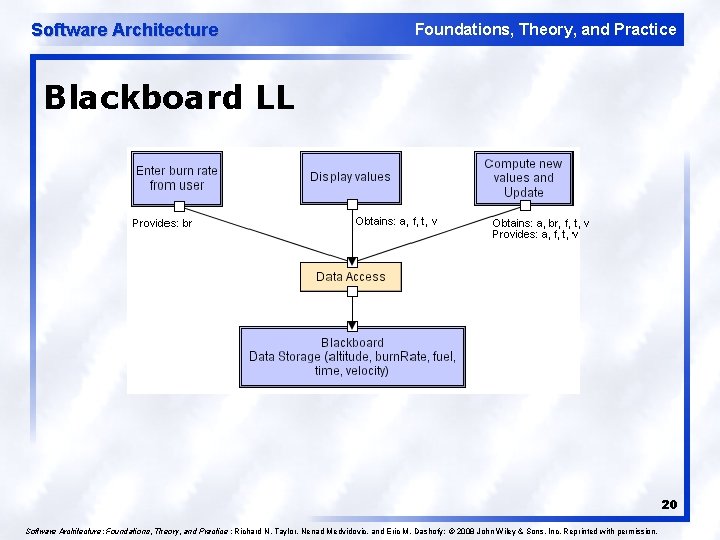
Software Architecture Foundations, Theory, and Practice Blackboard Style l l l Two kinds of components u Central data structure — blackboard u Components operating on the blackboard System control is entirely driven by the blackboard state Examples u Typically used for AI systems u Integrated software environments (e. g. , Interlisp) u Compiler architecture 19

Software Architecture Foundations, Theory, and Practice Blackboard LL 20 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture Foundations, Theory, and Practice Implicit Invocation Style l l Event announcement instead of method invocation u “Listeners” register interest in and associate methods with events u System invokes all registered methods implicitly Component interfaces are methods and events Two types of connectors u Invocation is either explicit or implicit in response to events Style invariants u “Announcers” are unaware of their events’ effects u No assumption about processing in response to events 21

Software Architecture Foundations, Theory, and Practice Implicit Invocation (cont’d) l l Advantages u Component reuse u System evolution l Both at system construction-time & run-time Disadvantages u Counter-intuitive system structure u Components relinquish computation control to the system u No knowledge of what components will respond to event u No knowledge of order of responses 22

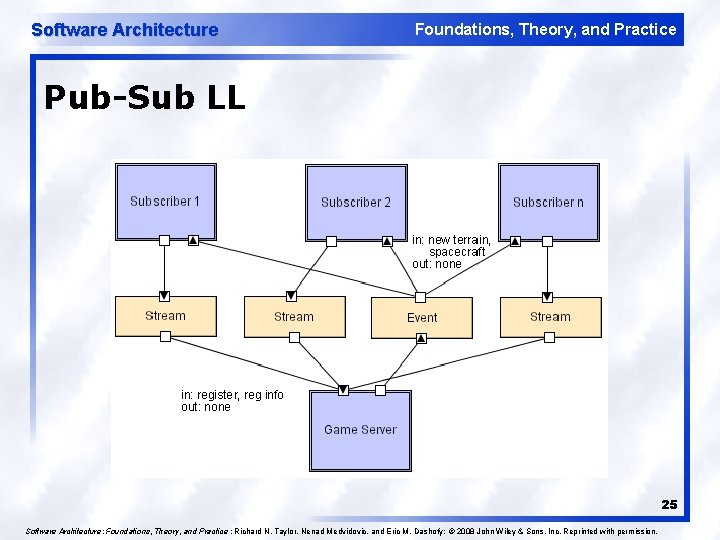
Software Architecture Foundations, Theory, and Practice Publish-Subscribers register/deregister to receive specific messages or specific content. Publishers broadcast messages to subscribers either synchronously or asynchronously. 23

Software Architecture Foundations, Theory, and Practice Publish-Subscribe (cont’d) l l l Components: Publishers, subscribers, proxies for managing distribution Connectors: Typically a network protocol is required. Content -based subscription requires sophisticated connectors. Data Elements: Subscriptions, notifications, published information Topology: Subscribers connect to publishers either directly or may receive notifications via a network protocol from intermediaries Qualities yielded: Highly efficient one-way dissemination of information with very low-coupling of components 24

Software Architecture Foundations, Theory, and Practice Pub-Sub LL 25 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

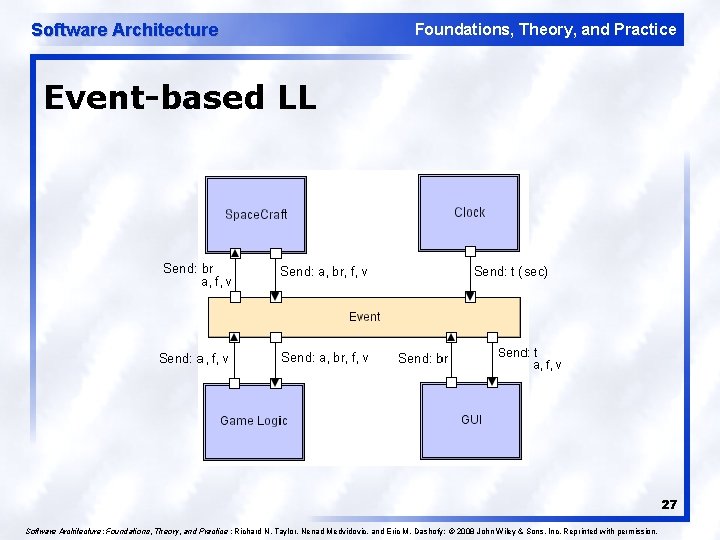
Software Architecture Foundations, Theory, and Practice Event-Based Style l l l l Independent components asynchronously emit and receive events communicated over event buses Components: Independent, concurrent event generators and/or consumers Connectors: Event buses (at least one) Data Elements: Events – data sent as a first-class entity over the event bus Topology: Components communicate with the event buses, not directly to each other. Variants: Component communication with the event bus may either be push or pull based. Highly scalable, easy to evolve, effective for highly distributed applications. 26

Software Architecture Foundations, Theory, and Practice Event-based LL 27 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

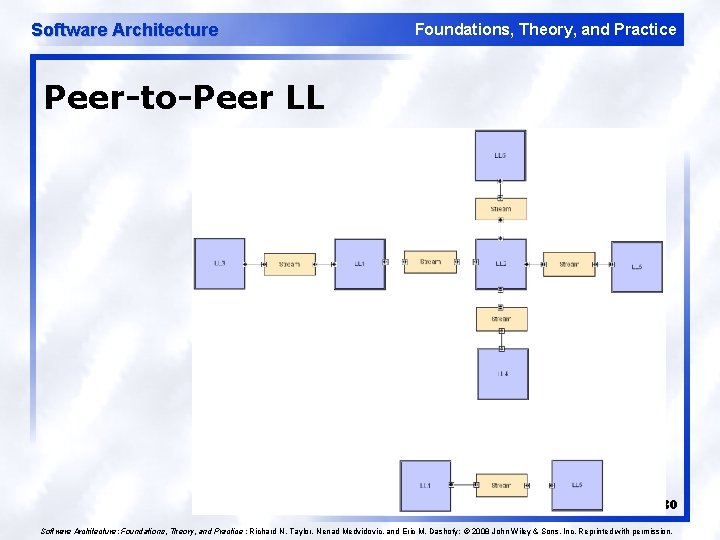
Software Architecture Foundations, Theory, and Practice Peer-to-Peer Style l l State and behavior are distributed among peers which can act as either clients or servers. Peers: independent components, having their own state and control thread. Connectors: Network protocols, often custom. Data Elements: Network messages 28

Software Architecture Foundations, Theory, and Practice Peer-to-Peer Style (cont’d) l l Topology: Network (may have redundant connections between peers); can vary arbitrarily and dynamically Supports decentralized computing with flow of control and resources distributed among peers. Highly robust in the face of failure of any given node. Scalable in terms of access to resources and computing power. u But caution on the protocol! 29

Software Architecture Foundations, Theory, and Practice Peer-to-Peer LL 30 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture Foundations, Theory, and Practice Heterogeneous Styles l l More complex styles created through composition of simpler styles REST (from the first lecture) u Complex history presented later in course C 2 u Implicit invocation + Layering + other constraints Distributed objects u OO + client-server network style u CORBA 31

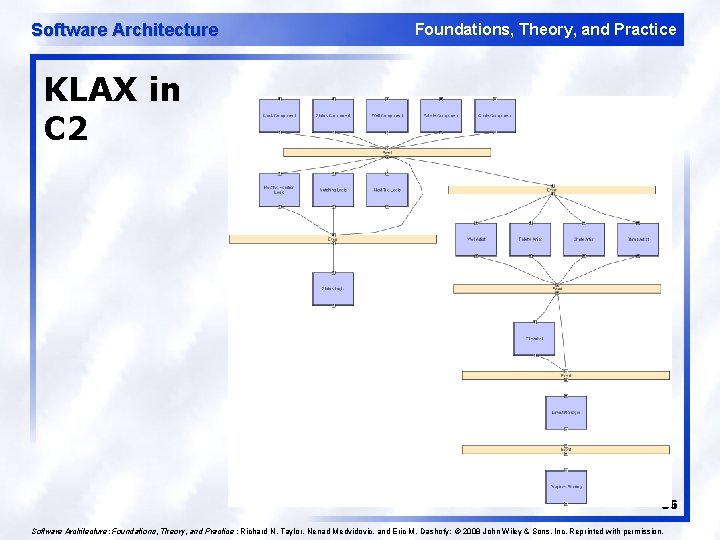
Software Architecture Foundations, Theory, and Practice C 2 Style An indirect invocation style in which independent components communicate exclusively through message routing connectors. Strict rules on connections between components and connectors induce layering. 32

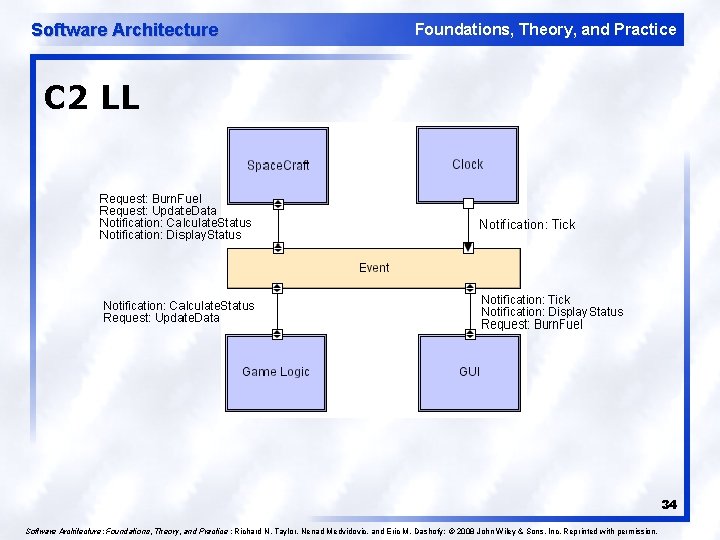
Software Architecture Foundations, Theory, and Practice C 2 Style (cont’d) l l Components: Independent, potentially concurrent message generators and/or consumers Connectors: Message routers that may filter, translate, and broadcast messages of two kinds: notifications and requests. Data Elements: Messages – data sent as first-class entities over the connectors. Notification messages announce changes of state. Request messages request performance of an action. Topology: Layers of components and connectors, with a defined “top” and “bottom”, wherein notifications flow downwards and requests upwards. 33

Software Architecture Foundations, Theory, and Practice C 2 LL 34 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

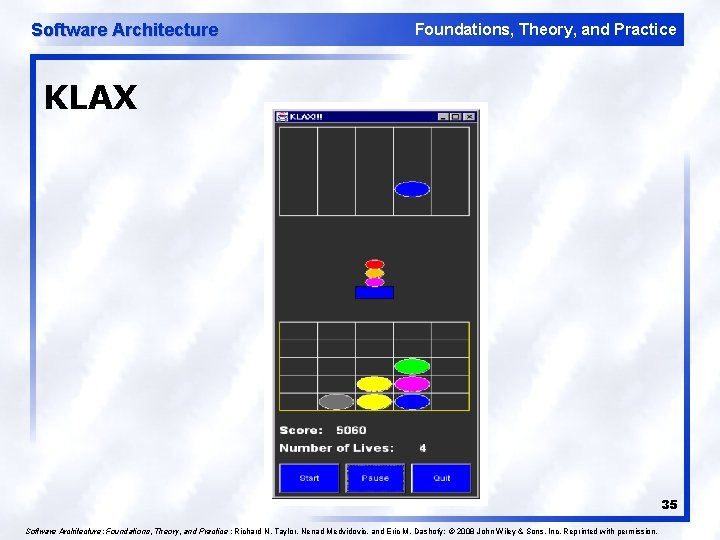
Software Architecture Foundations, Theory, and Practice KLAX 35 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture Foundations, Theory, and Practice KLAX in C 2 36 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture Foundations, Theory, and Practice Distributed Objects: CORBA l l l l “Objects” (coarse- or fine-grained) run on heterogeneous hosts, written in heterogeneous languages. Objects provide services through well-defined interfaces. Objects invoke methods across host, process, and language boundaries via remote procedure calls (RPCs). Components: Objects (software components exposing services through well-defined provided interfaces) Connector: (Remote) Method invocation Data Elements: Arguments to methods, return values, and exceptions Topology: General graph of objects from callers to callees. Additional constraints imposed: Data passed in remote procedure calls must be serializable. Callers must deal with exceptions that can arise due to network or process faults. Location, platform, and language “transparency”. CAUTION 37

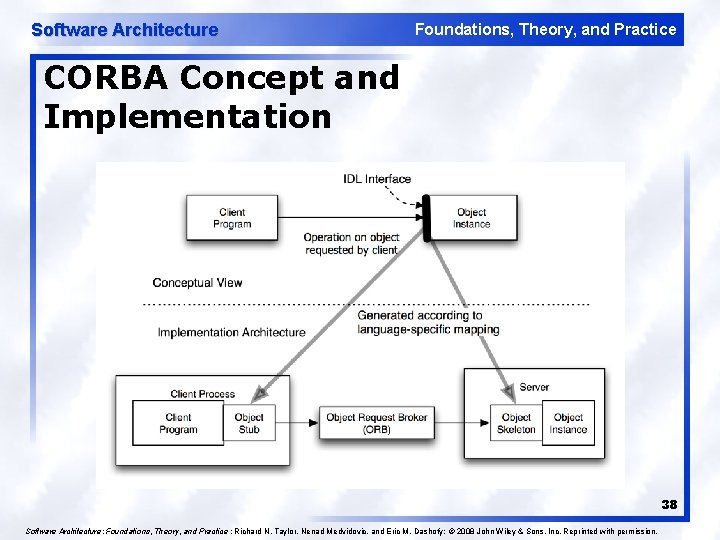
Software Architecture Foundations, Theory, and Practice CORBA Concept and Implementation 38 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

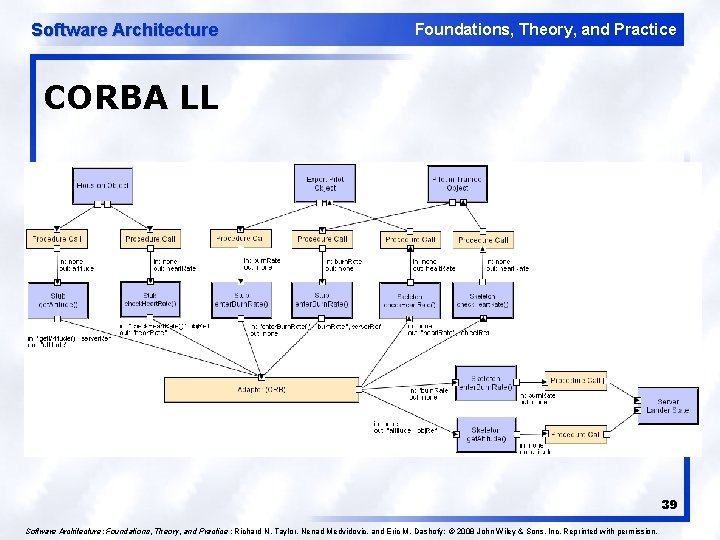
Software Architecture Foundations, Theory, and Practice CORBA LL 39 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture Foundations, Theory, and Practice Styles in Practice l l l Case study – the grid A distributed systems technology that enables sharing of resources across organizations scalably, efficiently, reliably, and securely Analogous to electric grid

Software Architecture Foundations, Theory, and Practice Why Study the Grid? l l l A highly successful technology Deficiencies in the existing guidance for building grids Grids are not easy to build u l Their architecture was published very early u l l E. g. , CERN’s Large Hadron Collider anatomy and physiology Most grid projects were open-source “What is (not) a grid? ” a subject of debate

Software Architecture Foundations, Theory, and Practice The Architectural Perspective l l l Grids are large, complex systems u Thousands of nodes or more u Span many agency boundaries Qualities of Service (Qo. S) are critical u Scalability u Security u Performance u Reliability. . . Architecture is an appropriate abstraction

Software Architecture Foundations, Theory, and Practice Case Study Goals l l Study grid’s reference requirements and architecture Study the architectures of existing grid technologies Compare the two Ø Knowing there will likely be few straightforward answers Suggest how to fix any discrepancies Ø Knowing there will likely be few straightforward answers

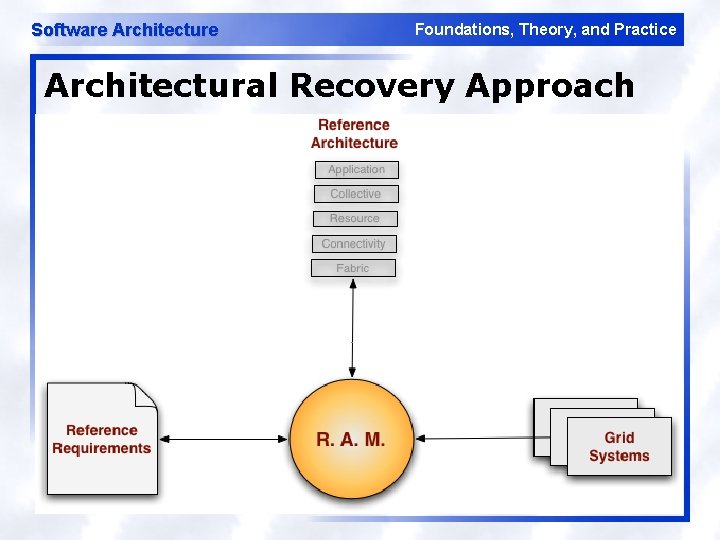
Software Architecture Foundations, Theory, and Practice Architectural Recovery Approach

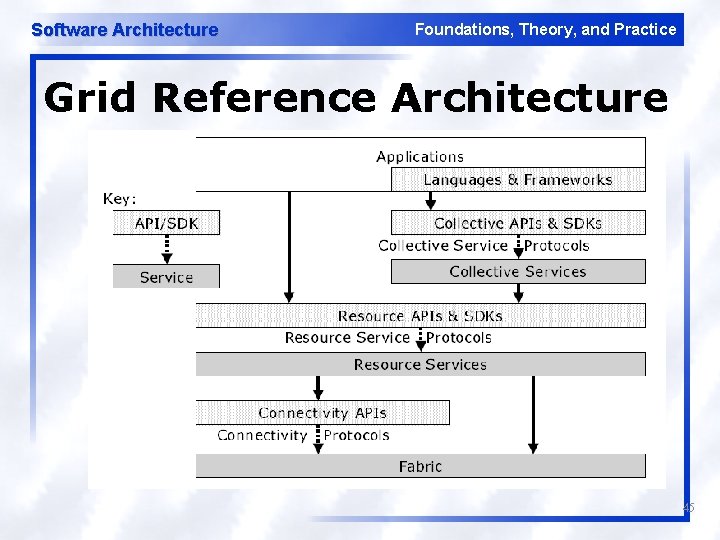
Software Architecture Foundations, Theory, and Practice Grid Reference Architecture 45

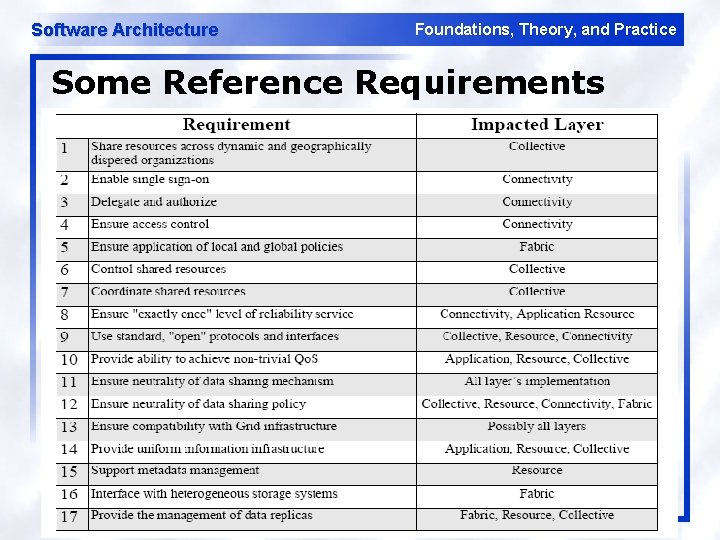
Software Architecture Foundations, Theory, and Practice Some Reference Requirements

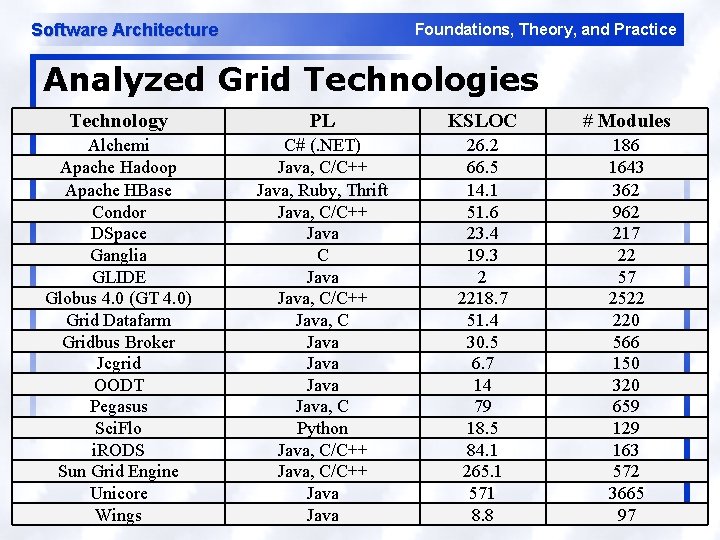
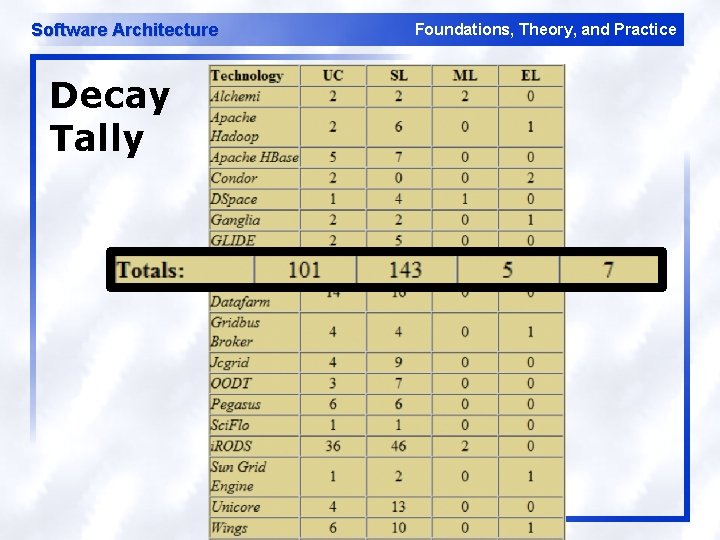
Software Architecture Foundations, Theory, and Practice Analyzed Grid Technologies Technology PL KSLOC # Modules Alchemi Apache Hadoop Apache HBase Condor DSpace Ganglia GLIDE Globus 4. 0 (GT 4. 0) Grid Datafarm Gridbus Broker Jcgrid OODT Pegasus Sci. Flo i. RODS Sun Grid Engine Unicore Wings C# (. NET) Java, C/C++ Java, Ruby, Thrift Java, C/C++ Java C Java, C/C++ Java, C Java, C Python Java, C/C++ Java 26. 2 66. 5 14. 1 51. 6 23. 4 19. 3 2 2218. 7 51. 4 30. 5 6. 7 14 79 18. 5 84. 1 265. 1 571 8. 8 186 1643 362 962 217 22 57 2522 220 566 150 320 659 129 163 572 3665 97

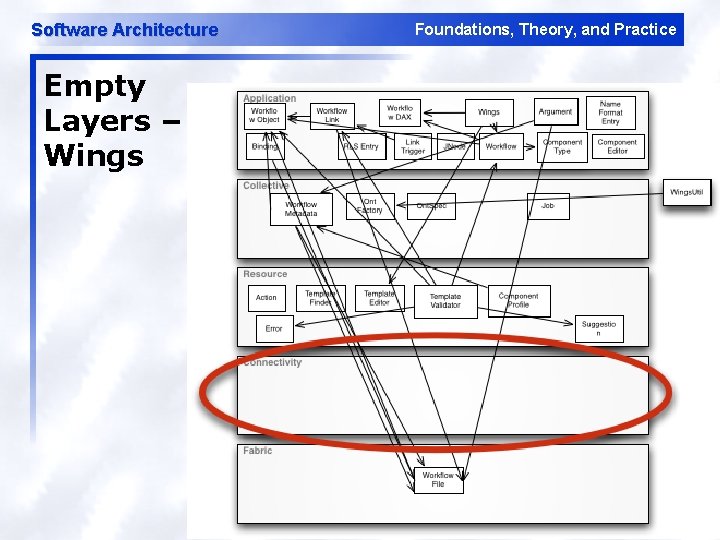
Software Architecture Empty Layers – Wings Foundations, Theory, and Practice

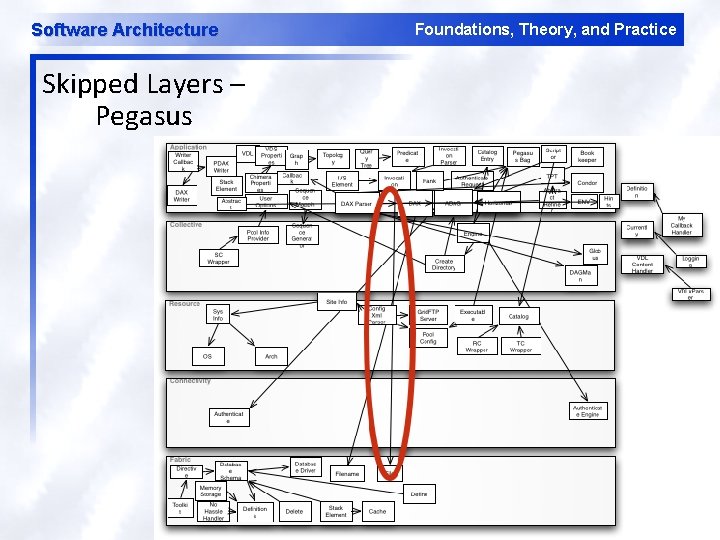
Software Architecture Skipped Layers – Pegasus Foundations, Theory, and Practice

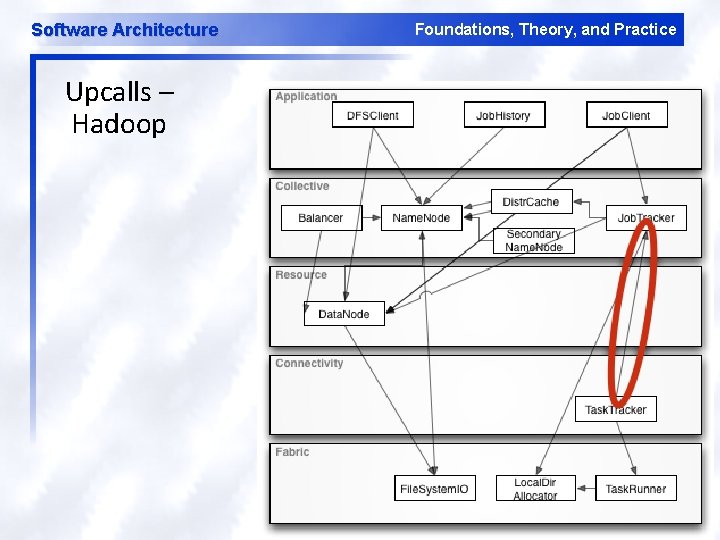
Software Architecture Upcalls – Hadoop Foundations, Theory, and Practice

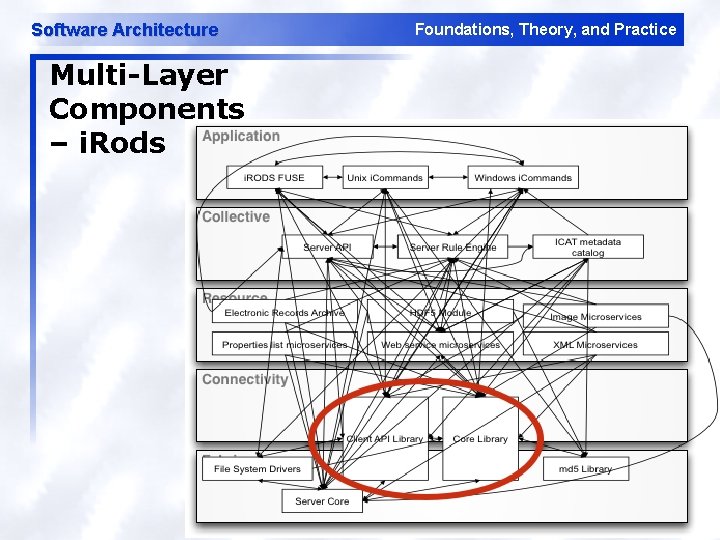
Software Architecture Multi-Layer Components – i. Rods Foundations, Theory, and Practice

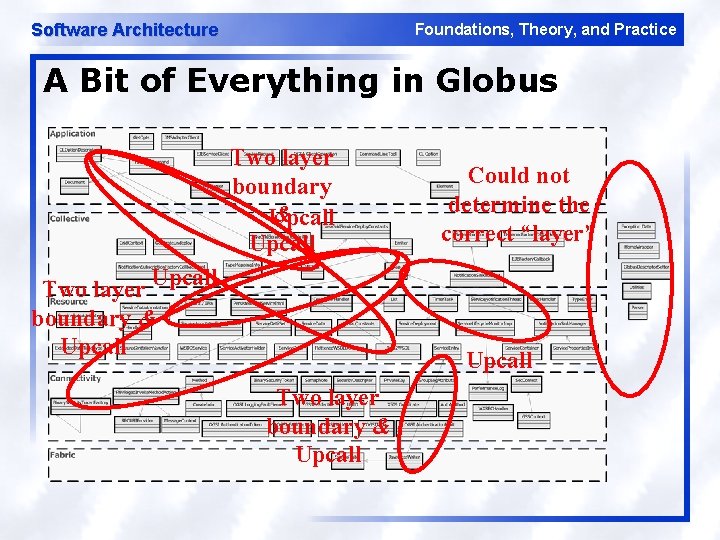
Software Architecture Foundations, Theory, and Practice A Bit of Everything in Globus Two layer boundary & Upcall Two layer Upcall boundary & Upcall Could not determine the correct “layer” Upcall Two layer boundary & Upcall

Software Architecture Decay Tally Foundations, Theory, and Practice

Software Architecture Foundations, Theory, and Practice Revised Grid Architecture l l l The connectivity layer is eliminated Explicitly addressing deployment view Subsystem types rather than layer-oriented Four architectural styles comprise the grid u Client/server u Peer-to-peer u Layered u Event-based An improved classification of grid technologies

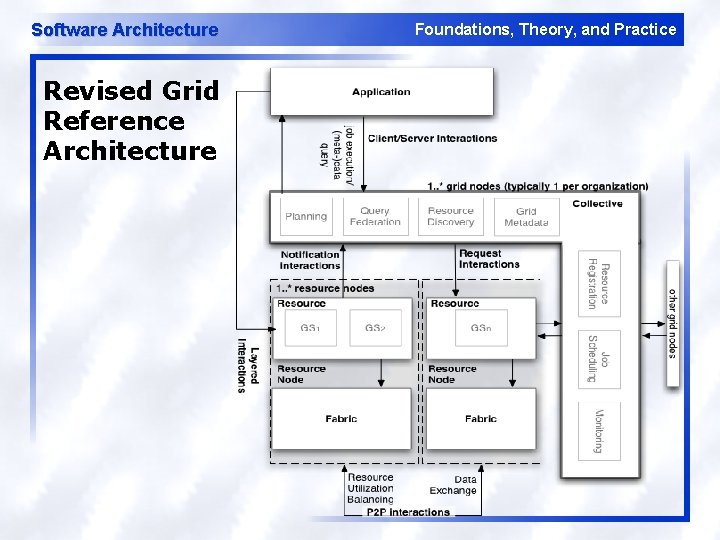
Software Architecture Revised Grid Reference Architecture Foundations, Theory, and Practice

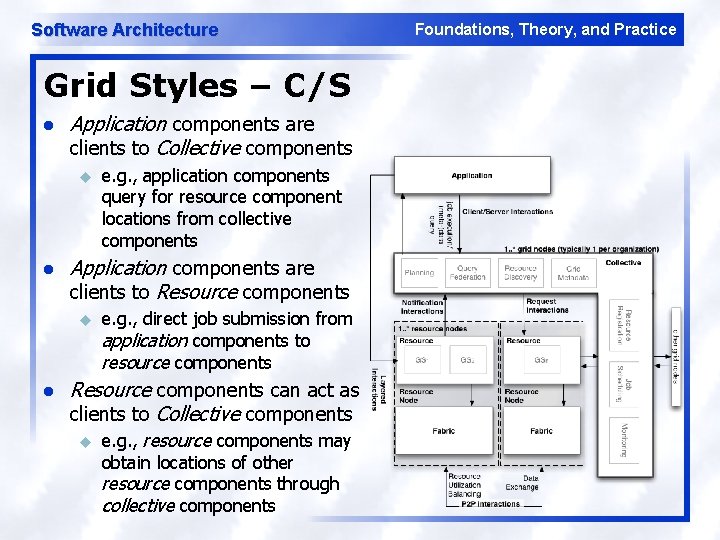
Software Architecture Grid Styles – C/S l Application components are clients to Collective components u l Application components are clients to Resource components u l e. g. , application components query for resource component locations from collective components e. g. , direct job submission from application components to resource components Resource components can act as clients to Collective components u e. g. , resource components may obtain locations of other resource components through collective components Foundations, Theory, and Practice

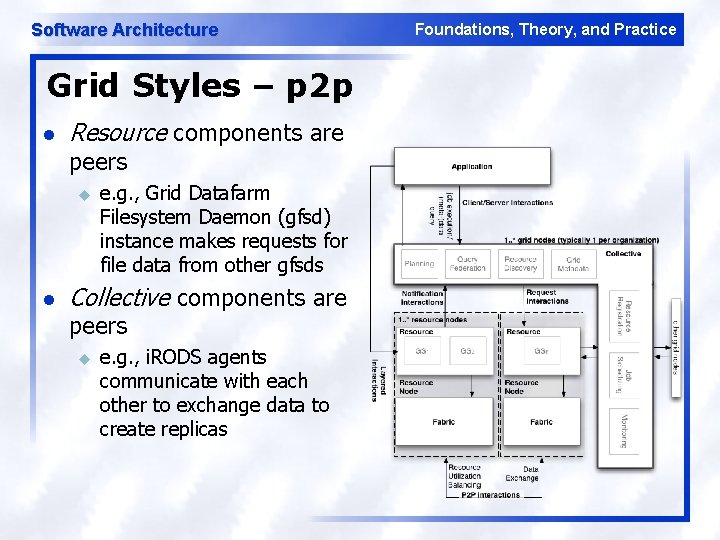
Software Architecture Grid Styles – p 2 p l Resource components are peers u l e. g. , Grid Datafarm Filesystem Daemon (gfsd) instance makes requests for file data from other gfsds Collective components are peers u e. g. , i. RODS agents communicate with each other to exchange data to create replicas Foundations, Theory, and Practice

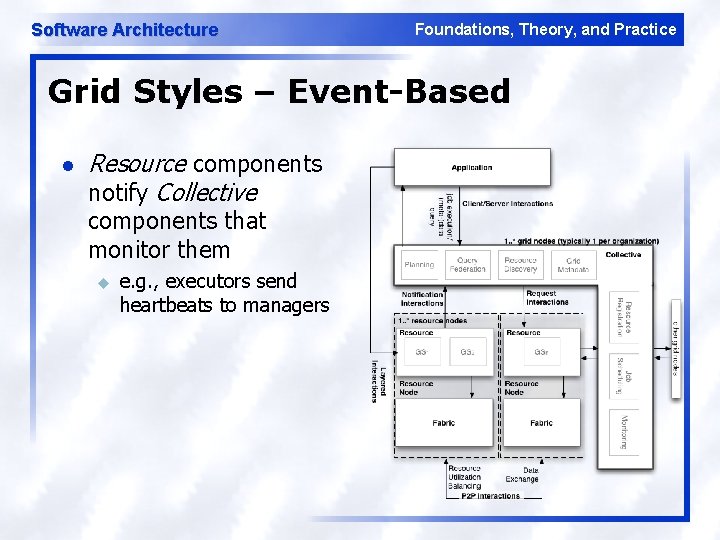
Software Architecture Foundations, Theory, and Practice Grid Styles – Event-Based l Resource components notify Collective components that monitor them u e. g. , executors send heartbeats to managers

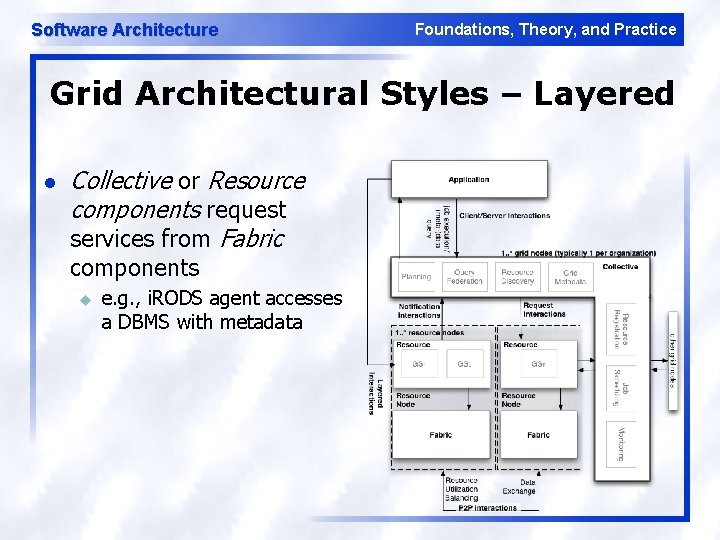
Software Architecture Foundations, Theory, and Practice Grid Architectural Styles – Layered l Collective or Resource components request services from Fabric components u e. g. , i. RODS agent accesses a DBMS with metadata

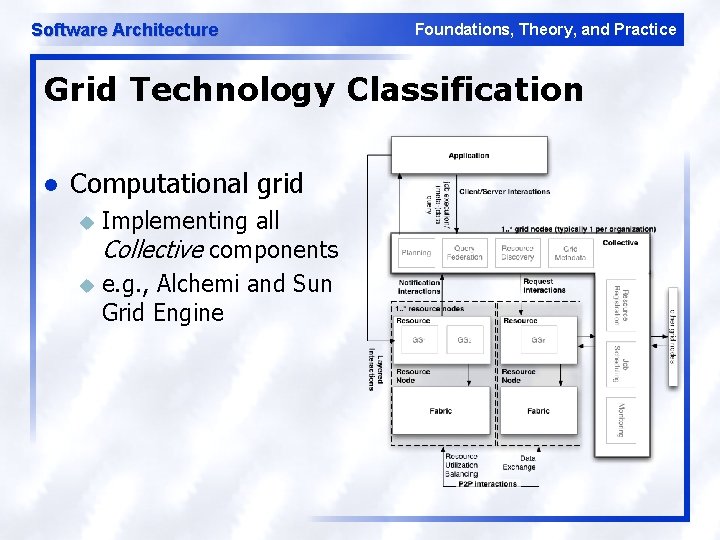
Software Architecture Foundations, Theory, and Practice Grid Technology Classification l Computational grid Implementing all Collective components u e. g. , Alchemi and Sun Grid Engine u

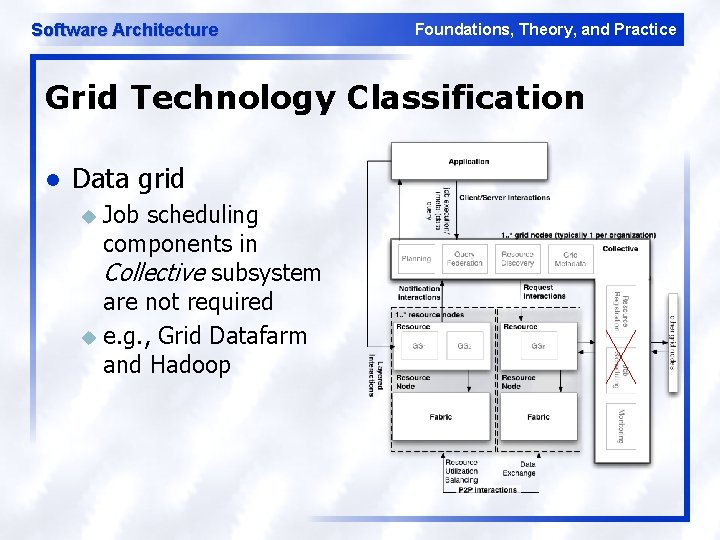
Software Architecture Foundations, Theory, and Practice Grid Technology Classification l Data grid Job scheduling components in Collective subsystem are not required u e. g. , Grid Datafarm and Hadoop u

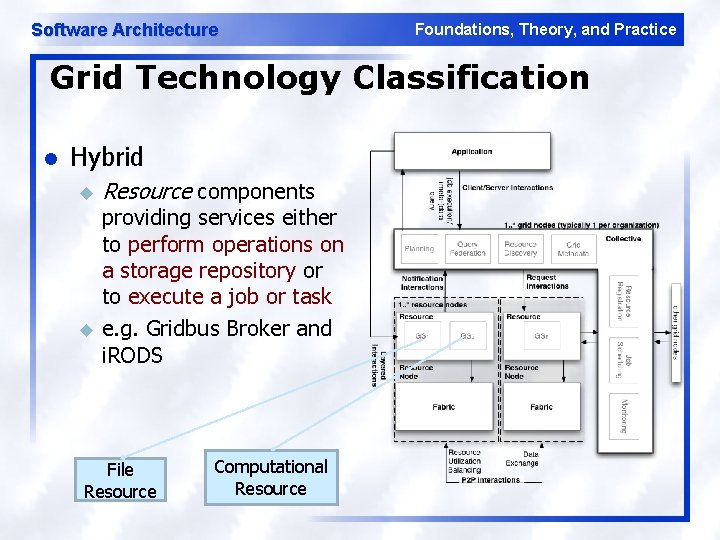
Software Architecture Foundations, Theory, and Practice Grid Technology Classification l Hybrid u u Resource components providing services either to perform operations on a storage repository or to execute a job or task e. g. Gridbus Broker and i. RODS File Resource Computational Resource

Software Architecture Foundations, Theory, and Practice How Styles Helped to Correct Reference Architecture Violations l Why were there originally so many upcalls? u l Why so many skipped layer calls? u u l The Fabric layer was at the wrong level of abstraction Mostly utility classes that should be abstracted away Why so many multi-layer components? u u u l Legitimate client-server and event-based communication Connectivity layer was at the wrong level of abstraction Not a layer, but utility libraries to enable connector functionality Also accounts for skipped layer calls Benefit of the deployment view u u Essential for distributed systems Helped identify that the Fabric layer was not abstracted properly