Architecting Cloud Solutions OCI Fundamentals Andrea Marchesini Oracle


























- Slides: 109

Architecting Cloud Solutions OCI Fundamentals Andrea Marchesini Oracle Cloud Infrastructure Product Manager December, 2019 © 2019 Oracle

Safe harbor statement The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, timing, and pricing of any features or functionality described for Oracle’s products may change and remains at the sole discretion of Oracle Corporation. 2 Copyright © 2019, Oracle and/or its affiliates. All rights reserved.

Oracle Cloud Infrastructure (OCI) is Oracle’s Cloud Platform on which Iaa. S, Paa. S and Saa. S services are built. .

Oracle Cloud Infrastructure Global Footprint October 2019: 16 Regions, 20 Live Planned LONDON NEWPORT, WALES AMSTERDAM FRANKFURT MONTREAL TORONTO EUROPE CHICAGO BAY AREA PHOENIX US GOV ZURICH ASHBURN CHUNCHEON SEOUL ISRAEL TOKYO ASIA JEDDAH SAUDI 2 Commercial Planned DUBAI UAE 2 OSAKA MUMBAI HYDERABAD SINGAPORE Government Planned Microsoft Azure Interconnect BELO HORIZONTE CHILE Microsoft Azure Interconnect Planned Copyright © 2019 Oracle and/or its affiliates. SAO PAULO SOUTH AFRICA SYDNEY MELBOURNE

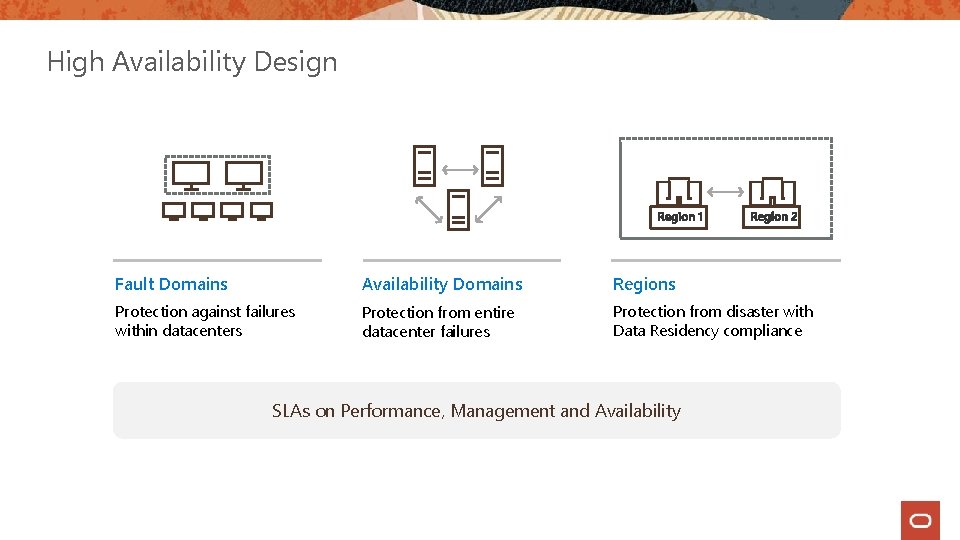
High Availability Design Fault Domains Availability Domains Regions Protection against failures within datacenters Protection from entire datacenter failures Protection from disaster with Data Residency compliance SLAs on Performance, Management and Availability

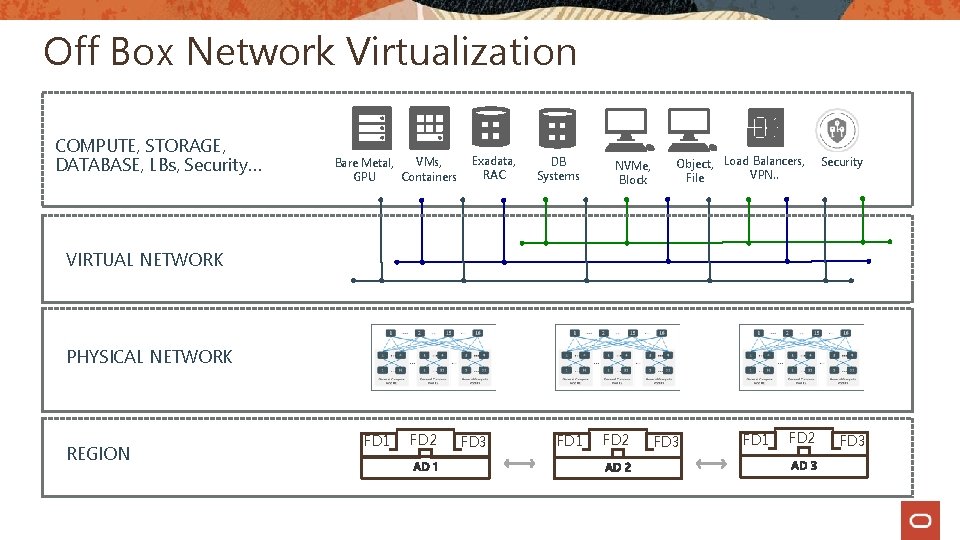
Off Box Network Virtualization COMPUTE, STORAGE, DATABASE, LBs, Security… VMs, Bare Metal, Containers GPU Exadata, RAC DB Systems NVMe, Block Object, Load Balancers, VPN. . File Security VIRTUAL NETWORK PHYSICAL NETWORK REGION FD 1 FD 2 FD 3

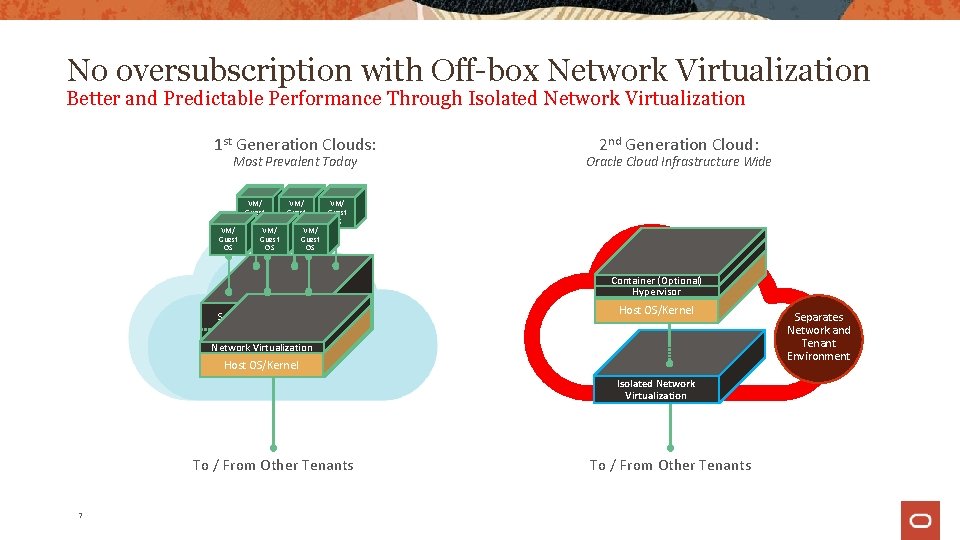
No oversubscription with Off-box Network Virtualization Better and Predictable Performance Through Isolated Network Virtualization 1 st Generation Clouds: Most Prevalent Today 2 nd Generation Cloud: Oracle Cloud Infrastructure Wide VM/ VM/ VM/ Guest Guest OS OS OS Container (Optional) Hypervisor Server Virtualization Hypervisor Network Virtualization Host OS/Kernel Isolated Network Virtualization To / From Other Tenants 7 To / From Other Tenants Separates Network and Tenant Environment

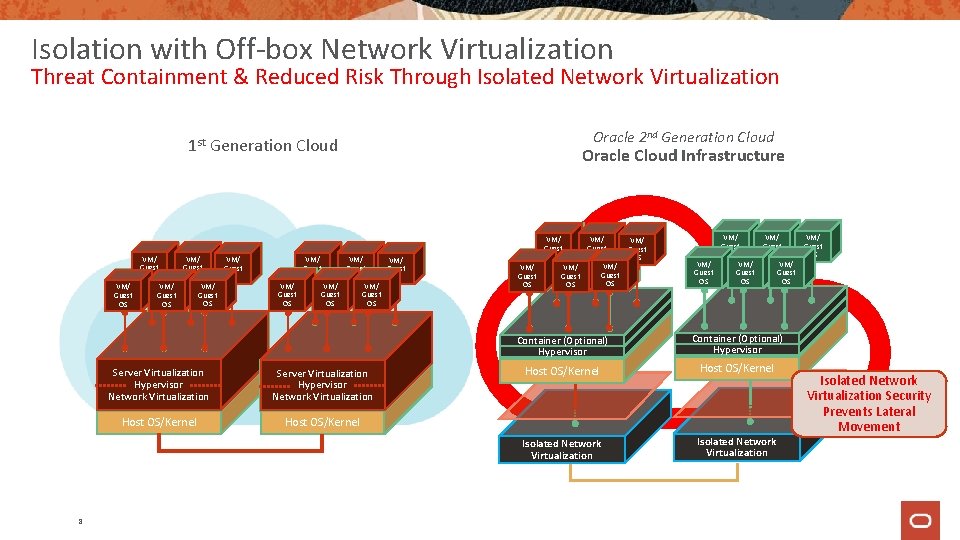
Isolation with Off-box Network Virtualization Threat Containment & Reduced Risk Through Isolated Network Virtualization 1 st Generation Cloud VM/ VM/ Guest OS OS VM/ VM/ VM/ Guest Guest OS OS OS 8 VM/ VM/ Guest OS OS VM/ VM/ VM/ Guest Guest OS OS OS Server Virtualization Hypervisor Network Virtualization Host OS/Kernel Oracle 2 nd Generation Cloud Oracle Cloud Infrastructure VM/ VM/ VM/ Guest Guest Guest OS OS OS VM/ VM/ VM/ Guest Guest OS OS OS Container (Optional) Hypervisor Host OS/Kernel Isolated Network Virtualization Security Prevents Lateral Movement

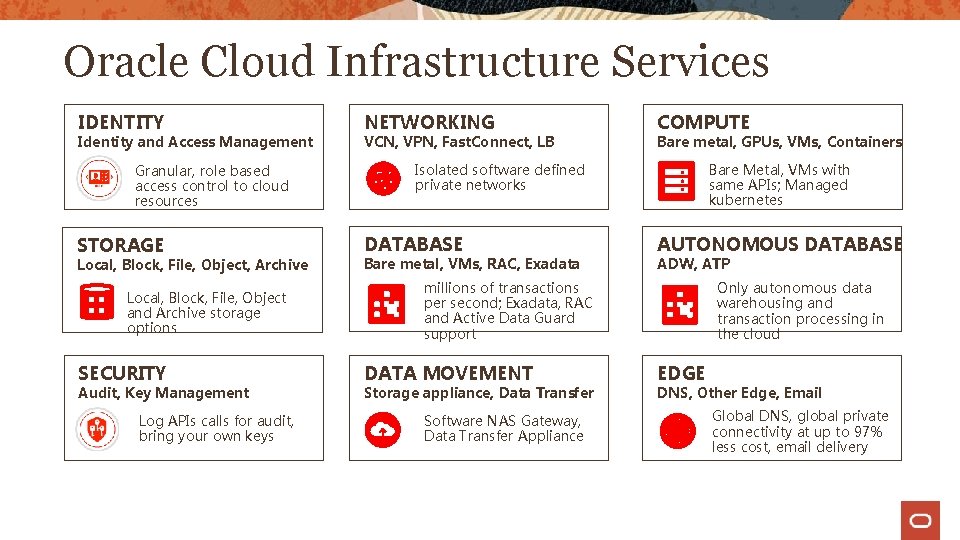
Oracle Cloud Infrastructure Services IDENTITY Identity and Access Management Granular, role based access control to cloud resources STORAGE Local, Block, File, Object, Archive Local, Block, File, Object and Archive storage options SECURITY Audit, Key Management Log APIs calls for audit, bring your own keys NETWORKING VCN, VPN, Fast. Connect, LB COMPUTE Bare metal, GPUs, VMs, Containers Isolated software defined private networks DATABASE Bare metal, VMs, RAC, Exadata Bare Metal, VMs with same APIs; Managed kubernetes AUTONOMOUS DATABASE ADW, ATP millions of transactions per second; Exadata, RAC and Active Data Guard support DATA MOVEMENT Storage appliance, Data Transfer Software NAS Gateway, Data Transfer Appliance Only autonomous data warehousing and transaction processing in the cloud EDGE DNS, Other Edge, Email Global DNS, global private connectivity at up to 97% less cost, email delivery

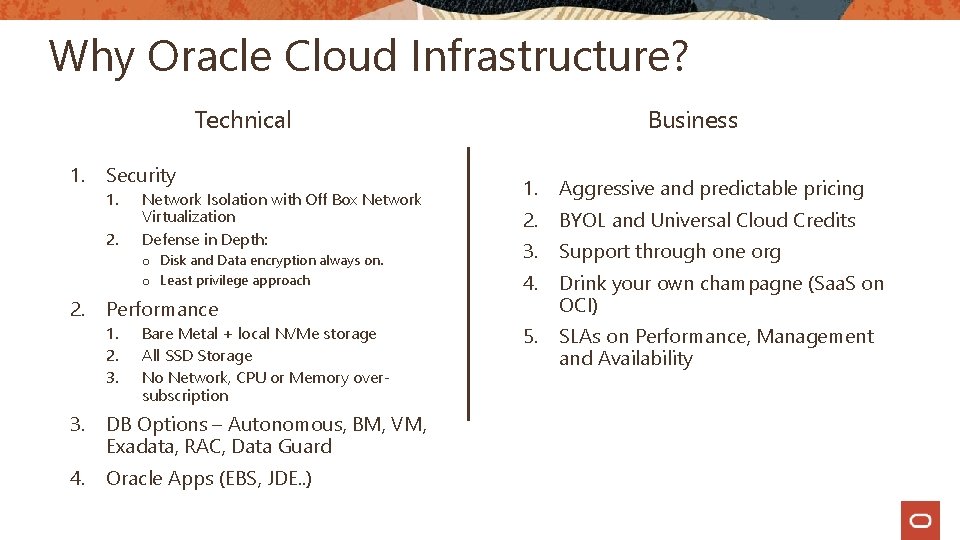
Why Oracle Cloud Infrastructure? Technical 1. Security 1. 2. Network Isolation with Off Box Network Virtualization Defense in Depth: o Disk and Data encryption always on. o Least privilege approach 2. Performance 1. 2. 3. Bare Metal + local NVMe storage All SSD Storage No Network, CPU or Memory oversubscription 3. DB Options – Autonomous, BM, VM, Exadata, RAC, Data Guard 4. Oracle Apps (EBS, JDE. . ) Business 1. Aggressive and predictable pricing 2. BYOL and Universal Cloud Credits 3. Support through one org 4. Drink your own champagne (Saa. S on OCI) 5. SLAs on Performance, Management and Availability

Identity and Access Management 11 Copyright © 2019, Oracle and/or its affiliates. All rights reserved.

Principals • A principal is an IAM entity that is allowed to interact with OCI resources • Principals – IAM users and Instance Principals • IAM Users and Groups • Users are persistent identities setup through IAM service to represent individual people or applications • When customers sign-up for an OCI account, the first IAM user is the default administrator • Default administrator sets up other IAM users and groups • Users enforce security principle of least privilege 1. User has no permissions until placed in one (or more) groups and 2. Group having at least one policy with permission to tenancy or a compartment • • A Group is a collection of users who all need the same type of access to a particular set of resources Same user can be member of multiple groups • Instance Principals lets instances (and applications) to make API calls against other OCI services removing the need to configure user credentials or a configuration file

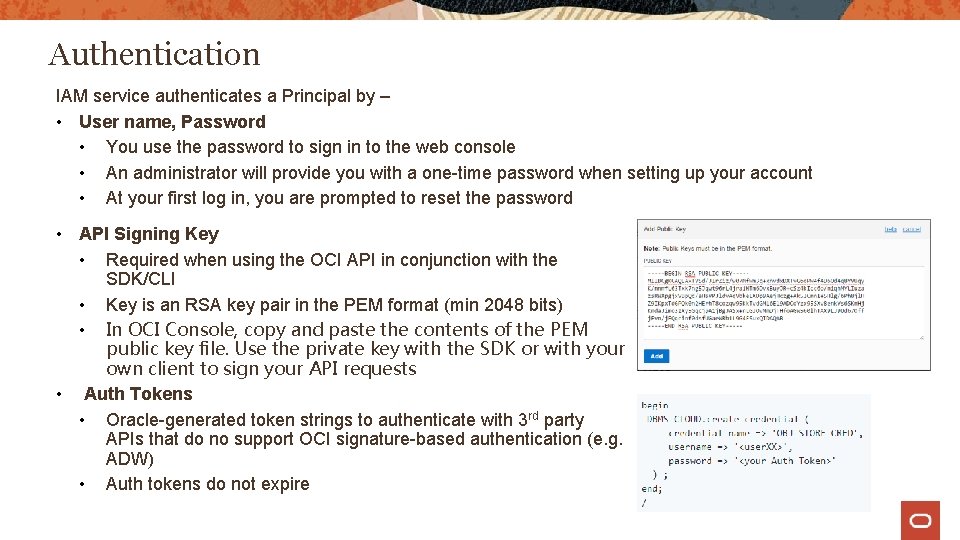
Authentication IAM service authenticates a Principal by – • User name, Password • You use the password to sign in to the web console • An administrator will provide you with a one-time password when setting up your account • At your first log in, you are prompted to reset the password • API Signing Key • Required when using the OCI API in conjunction with the SDK/CLI • Key is an RSA key pair in the PEM format (min 2048 bits) • In OCI Console, copy and paste the contents of the PEM public key file. Use the private key with the SDK or with your own client to sign your API requests • Auth Tokens • Oracle-generated token strings to authenticate with 3 rd party APIs that do no support OCI signature-based authentication (e. g. ADW) • Auth tokens do not expire

Authorization • Authorization specifies various actions an authenticated Principal can perform • OCI Authorization - define specific privileges in policies and associating them with principals • Supports security principle of least privilege; by default, users are not allowed to perform any actions (policies cannot be attached to users, but only groups) • Policies are comprised of one or more statements which specify what groups can access what resources and at what level of access • Policies are written in human-readable format: • Allow group <group_name> to <verb> <resource-type> in tenancy • Allow group <group_name> to <verb> <resource-type> in compartment <compartment_name> [where <conditions>] • Policy Attachment: Policies can be attached to a compartment or the tenancy. Where you attach it controls who can then modify it or delete it

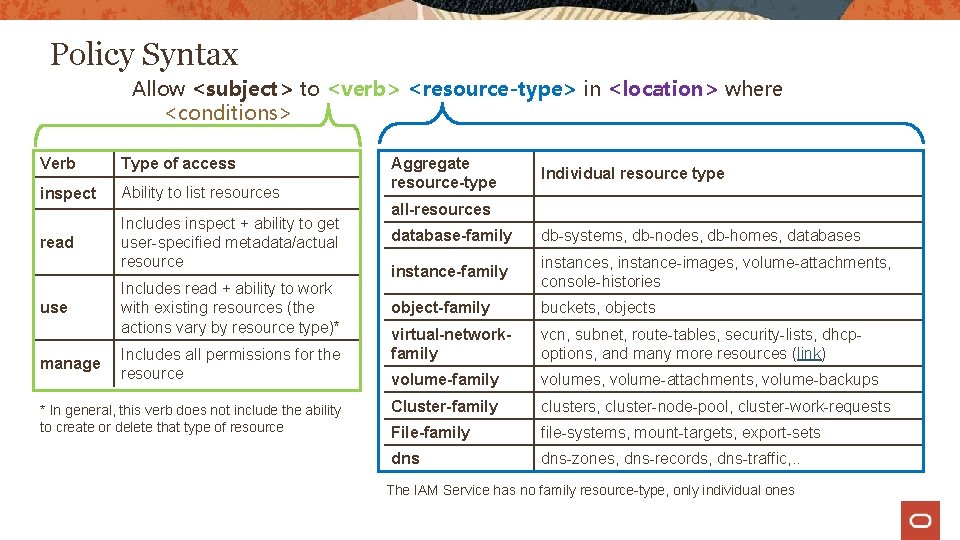
Policy Syntax Allow <subject> to <verb> <resource-type> in <location> where <conditions> Verb Type of access inspect Ability to list resources read Includes inspect + ability to get user-specified metadata/actual resource use manage Includes read + ability to work with existing resources (the actions vary by resource type)* Includes all permissions for the resource * In general, this verb does not include the ability to create or delete that type of resource Aggregate resource-type Individual resource type all-resources database-family db-systems, db-nodes, db-homes, databases instance-family instances, instance-images, volume-attachments, console-histories object-family buckets, objects virtual-networkfamily vcn, subnet, route-tables, security-lists, dhcpoptions, and many more resources (link) volume-family volumes, volume-attachments, volume-backups Cluster-family clusters, cluster-node-pool, cluster-work-requests File-family file-systems, mount-targets, export-sets dns-zones, dns-records, dns-traffic, . . The IAM Service has no family resource-type, only individual ones

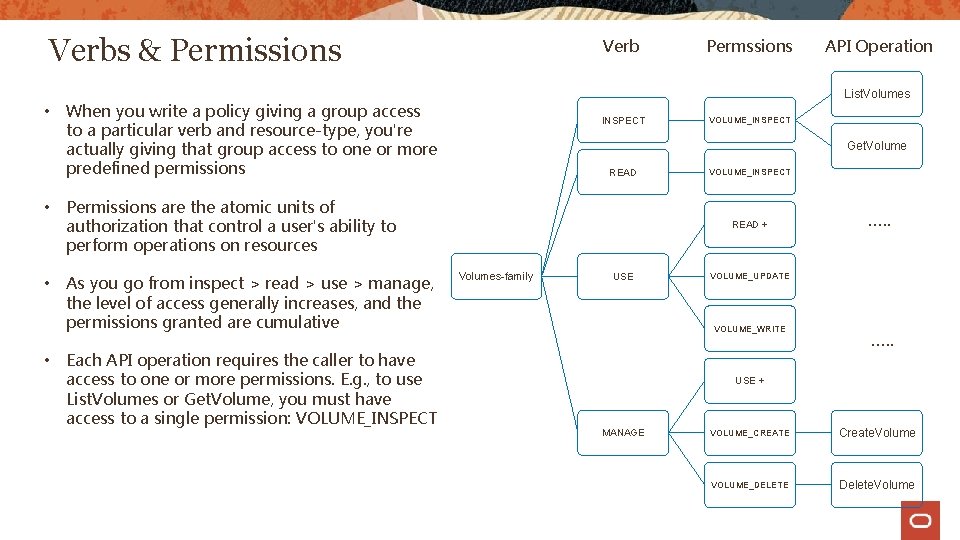
Verbs & Permissions • • Verb INSPECT VOLUME_INSPECT Get. Volume READ Permissions are the atomic units of authorization that control a user's ability to perform operations on resources Each API operation requires the caller to have access to one or more permissions. E. g. , to use List. Volumes or Get. Volume, you must have access to a single permission: VOLUME_INSPECT API Operation List. Volumes When you write a policy giving a group access to a particular verb and resource-type, you're actually giving that group access to one or more predefined permissions As you go from inspect > read > use > manage, the level of access generally increases, and the permissions granted are cumulative Permssions VOLUME_INSPECT READ + Volumes-family USE …. . VOLUME_UPDATE VOLUME_WRITE …. . USE + MANAGE VOLUME_CREATE Create. Volume VOLUME_DELETE Delete. Volume

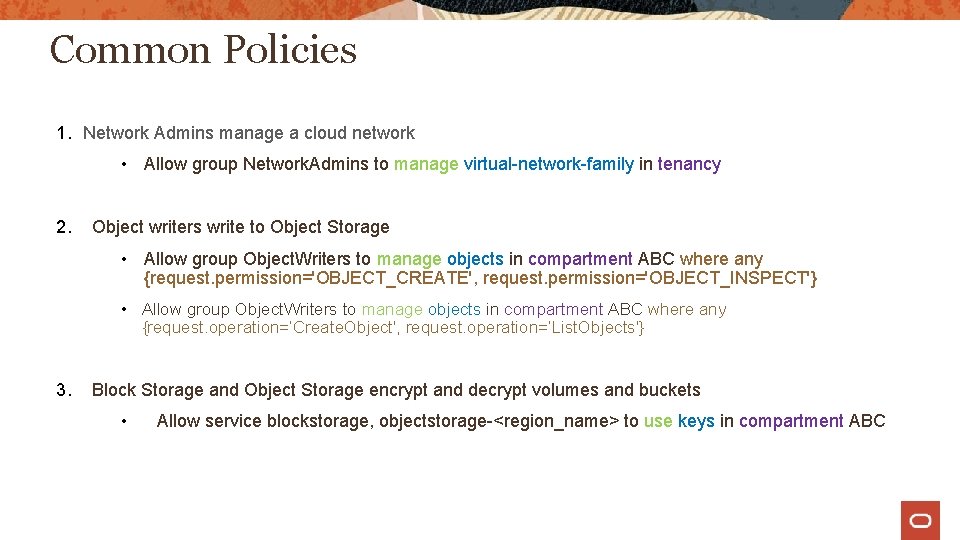
Common Policies 1. Network Admins manage a cloud network • Allow group Network. Admins to manage virtual-network-family in tenancy 2. Object writers write to Object Storage • Allow group Object. Writers to manage objects in compartment ABC where any {request. permission='OBJECT_CREATE', request. permission='OBJECT_INSPECT'} • Allow group Object. Writers to manage objects in compartment ABC where any {request. operation=‘Create. Object', request. operation=‘List. Objects'} 3. Block Storage and Object Storage encrypt and decrypt volumes and buckets • Allow service blockstorage, objectstorage-<region_name> to use keys in compartment ABC

Compartment • A compartment is a collection of related resources (VCN, instances, . . ) that can be accessed only by groups that have been given permission (by an administrator in your organization) • Compartments help you organize and control access to your resources • Design considerations: • Each resource belongs to a single compartment but resources can be connected/shared across compartments (VCN and its subnets can live in different compartments) • A compartment can be deleted after creation or renamed • A compartment can have sub compartments that can be up to six levels deep • Most resources can be moved to a different compartment after they are created (some restrictions apply) • After creating a compartment, you need to write at least one policy for it, otherwise it cannot be accessed (except by administrators or users who have permission to the tenancy) • Sub compartment inherits access permissions from compartments higher up its hierarchy • When you create a policy, you need to specify which compartment to attach it to

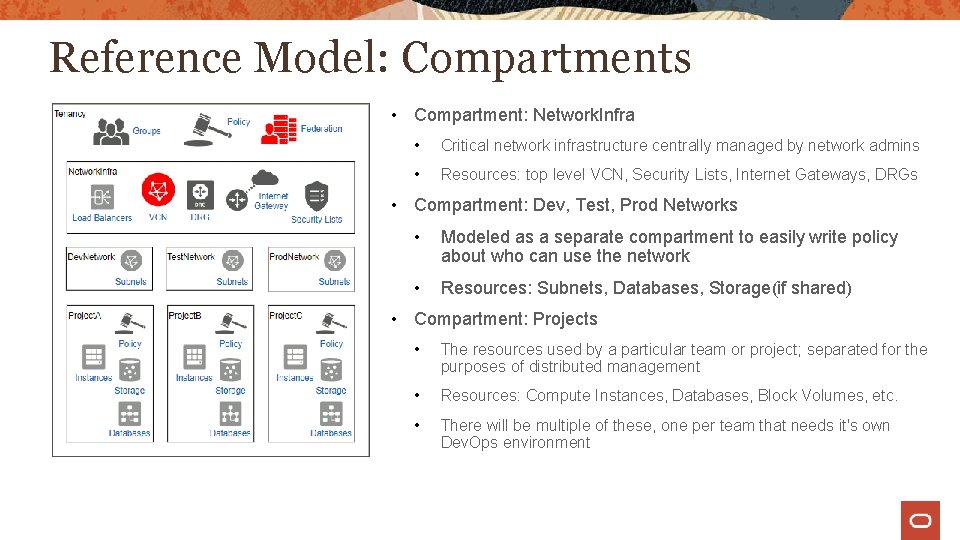
Reference Model: Compartments • Compartment: Network. Infra • Critical network infrastructure centrally managed by network admins • Resources: top level VCN, Security Lists, Internet Gateways, DRGs • Compartment: Dev, Test, Prod Networks • Modeled as a separate compartment to easily write policy about who can use the network • Resources: Subnets, Databases, Storage(if shared) • Compartment: Projects • The resources used by a particular team or project; separated for the purposes of distributed management • Resources: Compute Instances, Databases, Block Volumes, etc. • There will be multiple of these, one per team that needs it's own Dev. Ops environment

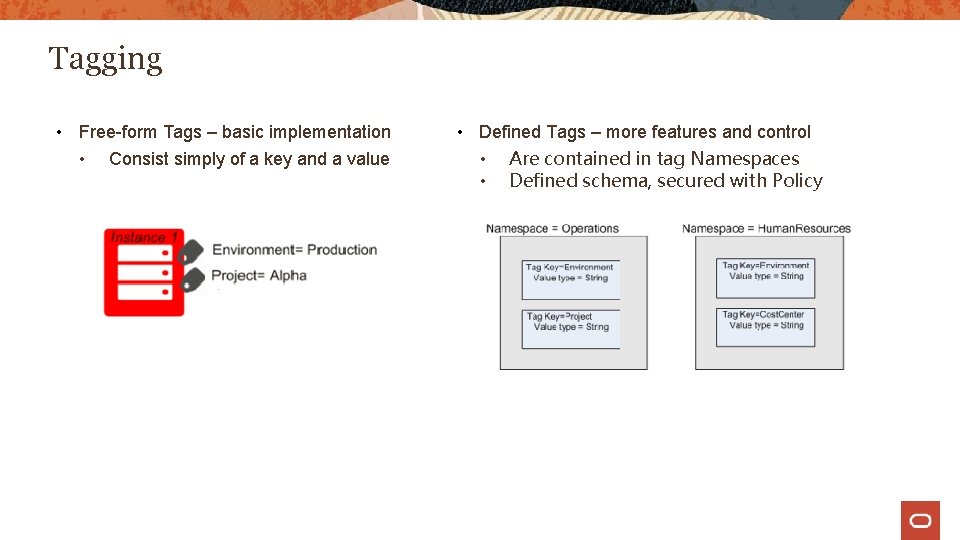
Tagging • Free-form Tags – basic implementation • Consist simply of a key and a value • Defined Tags – more features and control • Are contained in tag Namespaces • Defined schema, secured with Policy

Working with defined tags • Consist of a tag namespace, a key, and a value • Tag namespace and tag key definition must be set up in your tenancy before users can apply them • A tag key can have either a tag value type of string or a list of values (from which the user must choose) • You can use a variable to set the value of a tag. When you add the tag to a resource, the variable resolves to the data it represent. E. g. • Operations. Cost. Center = ${iam. principal. name} at ${oci. datetime} • Operations is the namespace, Cost. Center is the tag key, and the tag value contains two tag variables ${iam. principal. name} and ${oci. datetime} • When you add this tag to a resource, the variable resolves to your user name (the name of the principal that applied the tag) and a time date stamp for when you added the tag

Virtual Cloud Network 22 Copyright © 2019, Oracle and/or its affiliates. All rights reserved.

Virtual Cloud Network (VCN) • A private network that you set up in the Oracle data centers, with firewall rules and specific types of communication gateways that you can choose to use • A VCN covers a single, contiguous IPv 4 CIDR block of your choice • A VCN resides within a single region

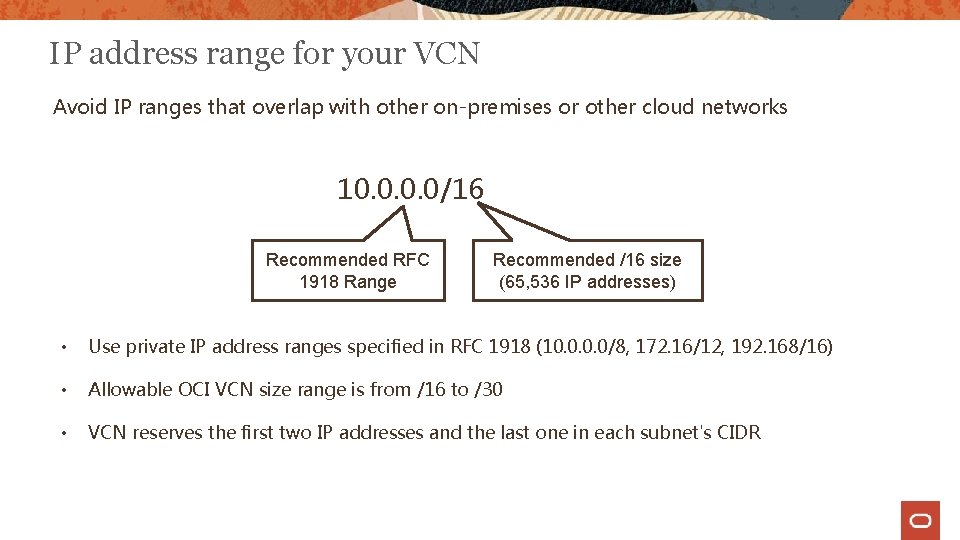
IP address range for your VCN Avoid IP ranges that overlap with other on-premises or other cloud networks 10. 0/16 Recommended RFC 1918 Range Recommended /16 size (65, 536 IP addresses) • Use private IP address ranges specified in RFC 1918 (10. 0/8, 172. 16/12, 192. 168/16) • Allowable OCI VCN size range is from /16 to /30 • VCN reserves the first two IP addresses and the last one in each subnet's CIDR

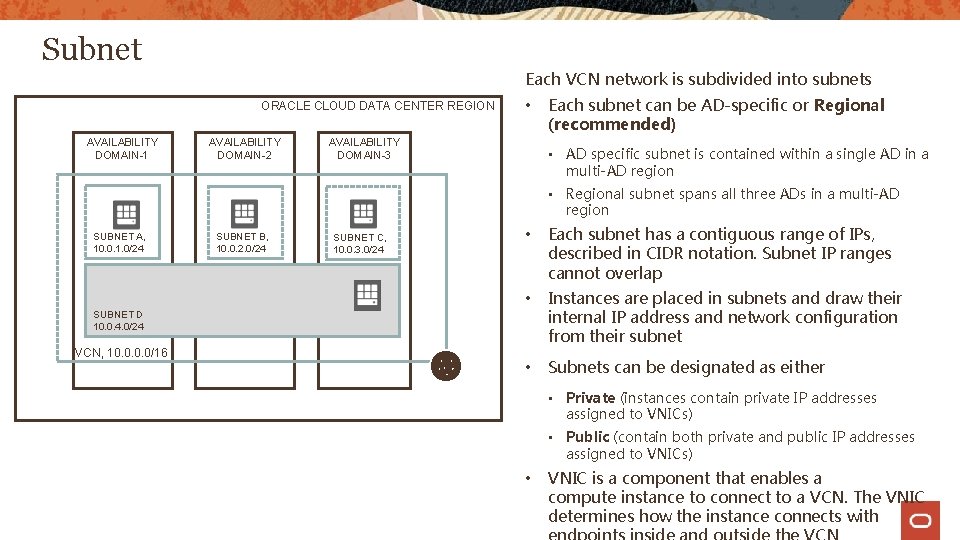
Subnet Each VCN network is subdivided into subnets ORACLE CLOUD DATA CENTER REGION AVAILABILITY DOMAIN-1 AVAILABILITY DOMAIN-2 • AVAILABILITY DOMAIN-3 Each subnet can be AD-specific or Regional (recommended) • AD specific subnet is contained within a single AD in a multi-AD region • Regional subnet spans all three ADs in a multi-AD region SUBNET A, 10. 0. 1. 0/24 SUBNET B, 10. 0. 2. 0/24 SUBNET C, 10. 0. 3. 0/24 • Each subnet has a contiguous range of IPs, described in CIDR notation. Subnet IP ranges cannot overlap • Instances are placed in subnets and draw their internal IP address and network configuration from their subnet • Subnets can be designated as either SUBNET D 10. 0. 4. 0/24 VCN, 10. 0/16 • Private (instances contain private IP addresses assigned to VNICs) • Public (contain both private and public IP addresses assigned to VNICs) • VNIC is a component that enables a compute instance to connect to a VCN. The VNIC determines how the instance connects with

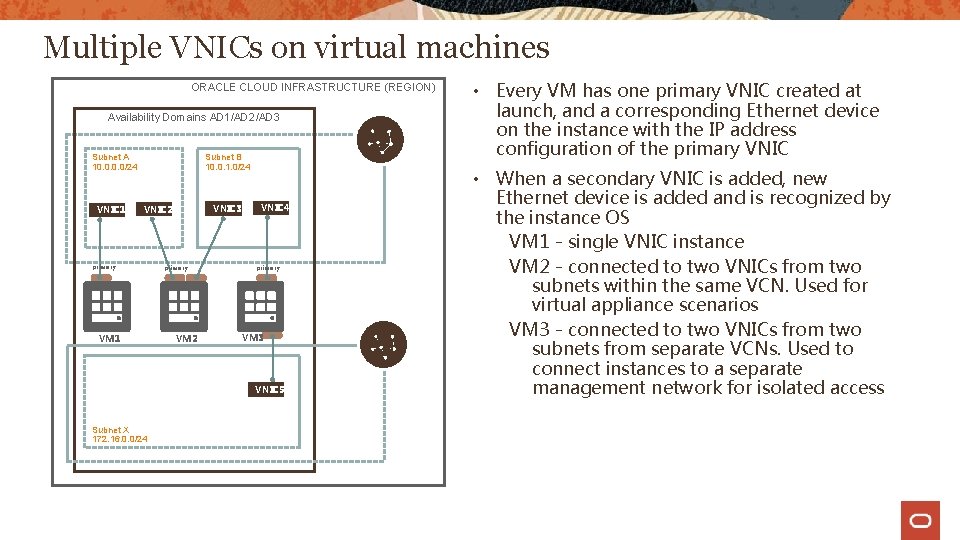
Multiple VNICs on virtual machines ORACLE CLOUD INFRASTRUCTURE (REGION) Availability Domains AD 1/AD 2/AD 3 Subnet A 10. 0/24 VNIC 1 Subnet B 10. 0. 1. 0/24 primary VM 1 VNIC 4 VNIC 3 VNIC 2 primary VM 2 VM 3 VCN Subnet X 172. 16. 0. 0/24 VNIC 5 • Every VM has one primary VNIC created at launch, and a corresponding Ethernet device on the instance with the IP address configuration of the primary VNIC • When a secondary VNIC is added, new Ethernet device is added and is recognized by the instance OS VM 1 - single VNIC instance VM 2 - connected to two VNICs from two subnets within the same VCN. Used for virtual appliance scenarios VM 3 - connected to two VNICs from two subnets from separate VCNs. Used to connect instances to a separate management network for isolated access

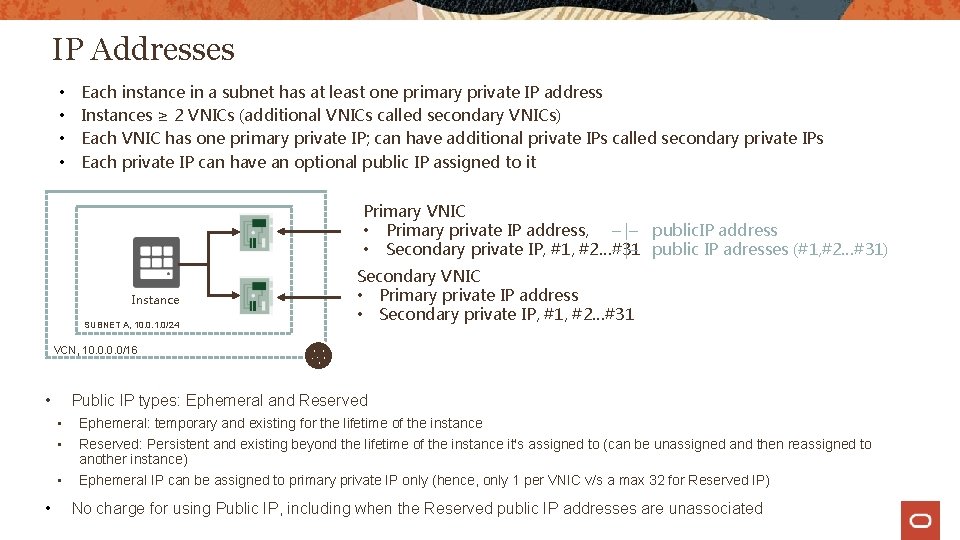
IP Addresses • • Each instance in a subnet has at least one primary private IP address Instances ≥ 2 VNICs (additional VNICs called secondary VNICs) Each VNIC has one primary private IP; can have additional private IPs called secondary private IPs Each private IP can have an optional public IP assigned to it Primary VNIC • Primary private IP address, – |– public. IP address • Secondary private IP, #1, #2…#31 – |– public IP adresses (#1, #2…#31) Instance SUBNET A, 10. 0. 1. 0/24 Secondary VNIC • Primary private IP address • Secondary private IP, #1, #2…#31 VCN, 10. 0/16 • • Public IP types: Ephemeral and Reserved • • Ephemeral: temporary and existing for the lifetime of the instance • Ephemeral IP can be assigned to primary private IP only (hence, only 1 per VNIC v/s a max 32 for Reserved IP) Reserved: Persistent and existing beyond the lifetime of the instance it's assigned to (can be unassigned and then reassigned to another instance) No charge for using Public IP, including when the Reserved public IP addresses are unassociated

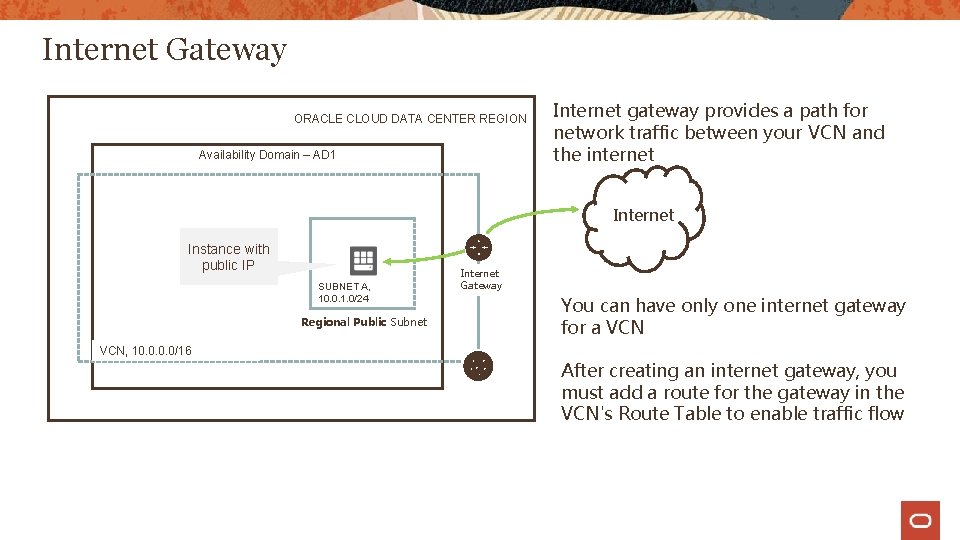
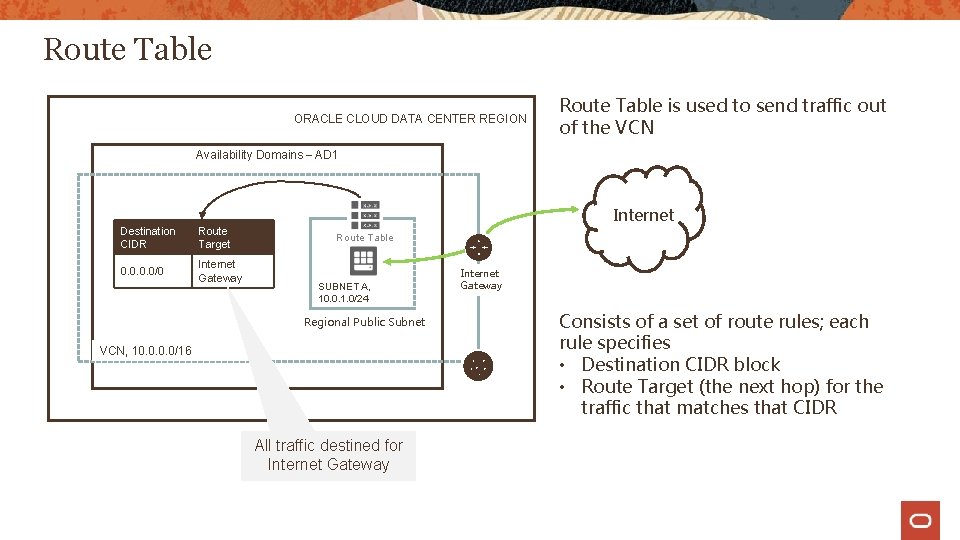
Internet Gateway ORACLE CLOUD DATA CENTER REGION Availability Domain – AD 1 Internet gateway provides a path for network traffic between your VCN and the internet Instance with public IP SUBNET A, 10. 0. 1. 0/24 Regional Public Subnet Internet Gateway You can have only one internet gateway for a VCN, 10. 0/16 After creating an internet gateway, you must add a route for the gateway in the VCN's Route Table to enable traffic flow

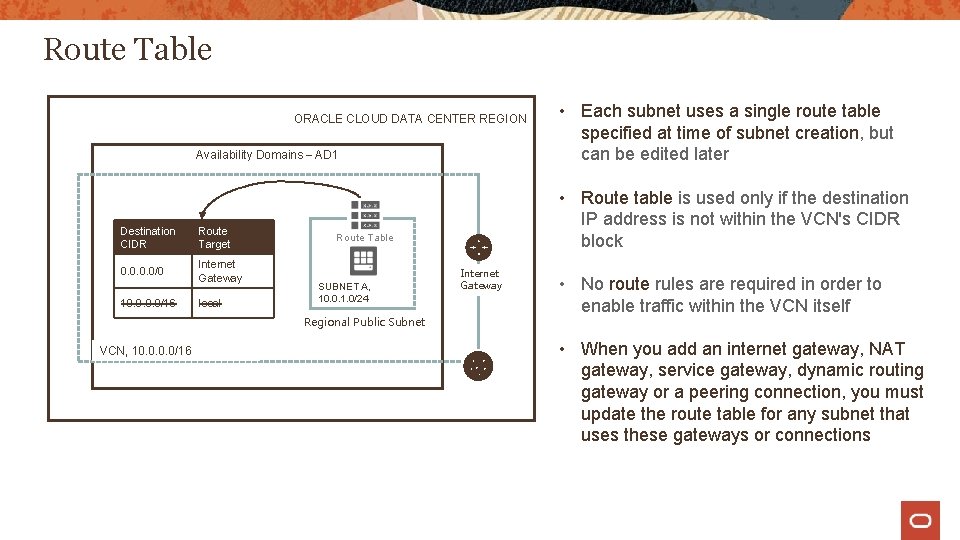
Route Table ORACLE CLOUD DATA CENTER REGION Route Table is used to send traffic out of the VCN Availability Domains – AD 1 Destination CIDR Route Target 0. 0/0 Internet Gateway Internet Route Table SUBNET A, 10. 0. 1. 0/24 Regional Public Subnet VCN, 10. 0/16 All traffic destined for Internet Gateway Consists of a set of route rules; each rule specifies • Destination CIDR block • Route Target (the next hop) for the traffic that matches that CIDR

Route Table ORACLE CLOUD DATA CENTER REGION Availability Domains – AD 1 Destination CIDR Route Target 0. 0/0 Internet Gateway 10. 0/16 local Regional Public Subnet VCN, 10. 0/16 • Route table is used only if the destination IP address is not within the VCN's CIDR block Route Table SUBNET A, 10. 0. 1. 0/24 • Each subnet uses a single route table specified at time of subnet creation, but can be edited later Internet Gateway • No route rules are required in order to enable traffic within the VCN itself • When you add an internet gateway, NAT gateway, service gateway, dynamic routing gateway or a peering connection, you must update the route table for any subnet that uses these gateways or connections

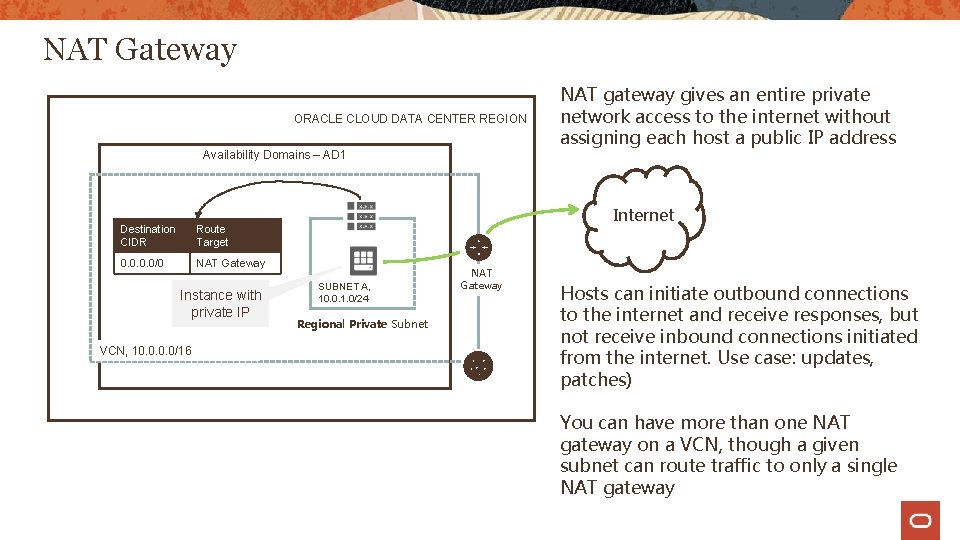
NAT Gateway ORACLE CLOUD DATA CENTER REGION Availability Domains – AD 1 Destination CIDR Route Target 0. 0/0 NAT Gateway Instance with private IP VCN, 10. 0/16 NAT gateway gives an entire private network access to the internet without assigning each host a public IP address Internet SUBNET A, 10. 0. 1. 0/24 Regional Private Subnet NAT Gateway Hosts can initiate outbound connections to the internet and receive responses, but not receive inbound connections initiated from the internet. Use case: updates, patches) You can have more than one NAT gateway on a VCN, though a given subnet can route traffic to only a single NAT gateway

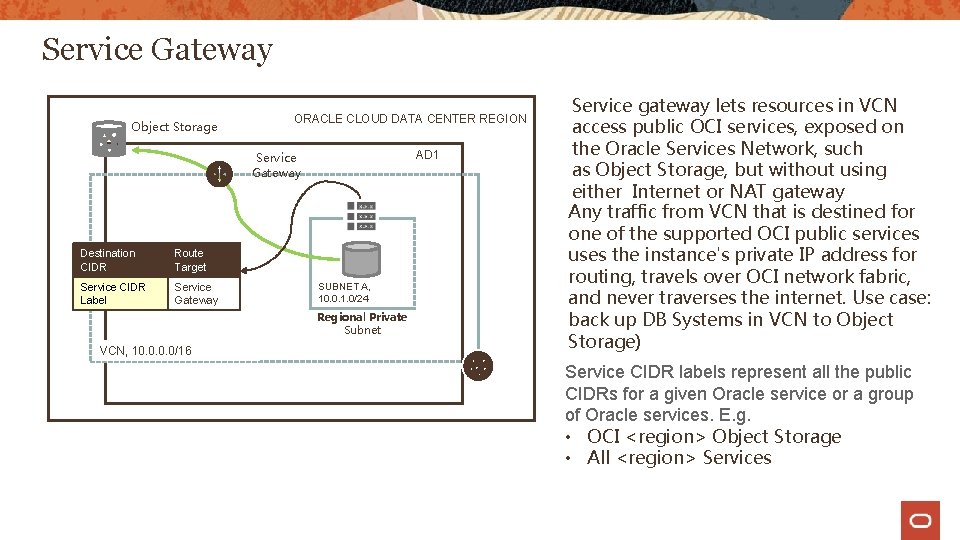
Service Gateway Object Storage ORACLE CLOUD DATA CENTER REGION AD 1 Service Gateway Destination CIDR Route Target Service CIDR Label Service Gateway SUBNET A, 10. 0. 1. 0/24 Regional Private Subnet VCN, 10. 0/16 Service gateway lets resources in VCN access public OCI services, exposed on the Oracle Services Network, such as Object Storage, but without using either Internet or NAT gateway Any traffic from VCN that is destined for one of the supported OCI public services uses the instance's private IP address for routing, travels over OCI network fabric, and never traverses the internet. Use case: back up DB Systems in VCN to Object Storage) Service CIDR labels represent all the public CIDRs for a given Oracle service or a group of Oracle services. E. g. • OCI <region> Object Storage • All <region> Services

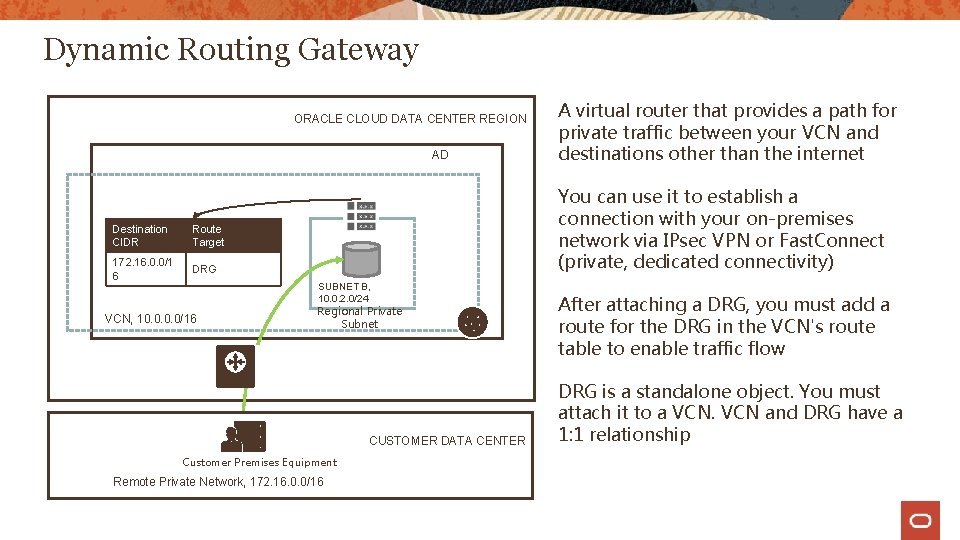
Dynamic Routing Gateway ORACLE CLOUD DATA CENTER REGION AD Destination CIDR Route Target 172. 16. 0. 0/1 6 DRG You can use it to establish a connection with your on-premises network via IPsec VPN or Fast. Connect (private, dedicated connectivity) SUBNET B, 10. 0. 2. 0/24 VCN, 10. 0/16 A virtual router that provides a path for private traffic between your VCN and destinations other than the internet Regional Private Subnet CUSTOMER DATA CENTER Customer Premises Equipment (CPE) Remote Private Network, 172. 16. 0. 0/16 After attaching a DRG, you must add a route for the DRG in the VCN's route table to enable traffic flow DRG is a standalone object. You must attach it to a VCN and DRG have a 1: 1 relationship

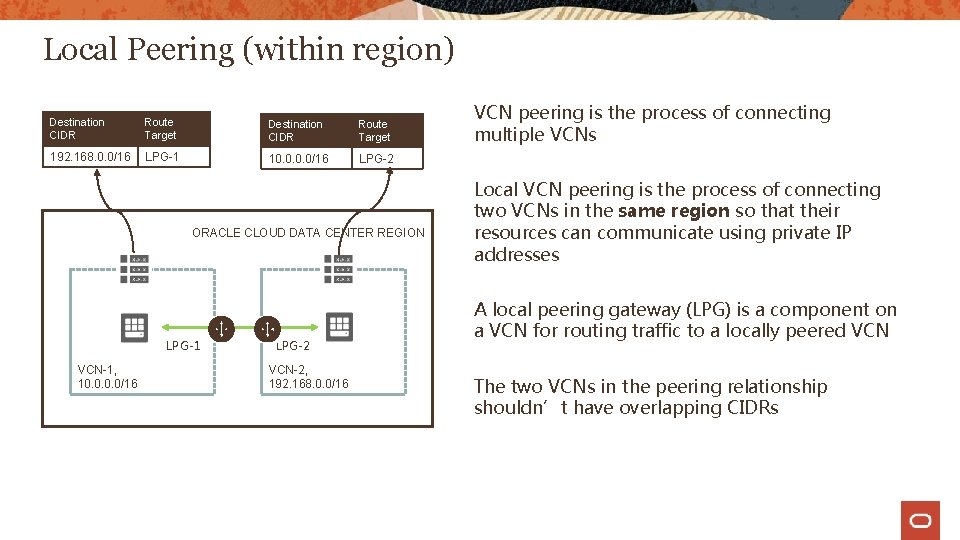
Local Peering (within region) Destination CIDR Route Target 192. 168. 0. 0/16 LPG-1 10. 0/16 LPG-2 ORACLE CLOUD DATA CENTER REGION LPG-1 VCN-1, 10. 0/16 LPG-2 VCN-2, 192. 168. 0. 0/16 VCN peering is the process of connecting multiple VCNs Local VCN peering is the process of connecting two VCNs in the same region so that their resources can communicate using private IP addresses A local peering gateway (LPG) is a component on a VCN for routing traffic to a locally peered VCN The two VCNs in the peering relationship shouldn’t have overlapping CIDRs

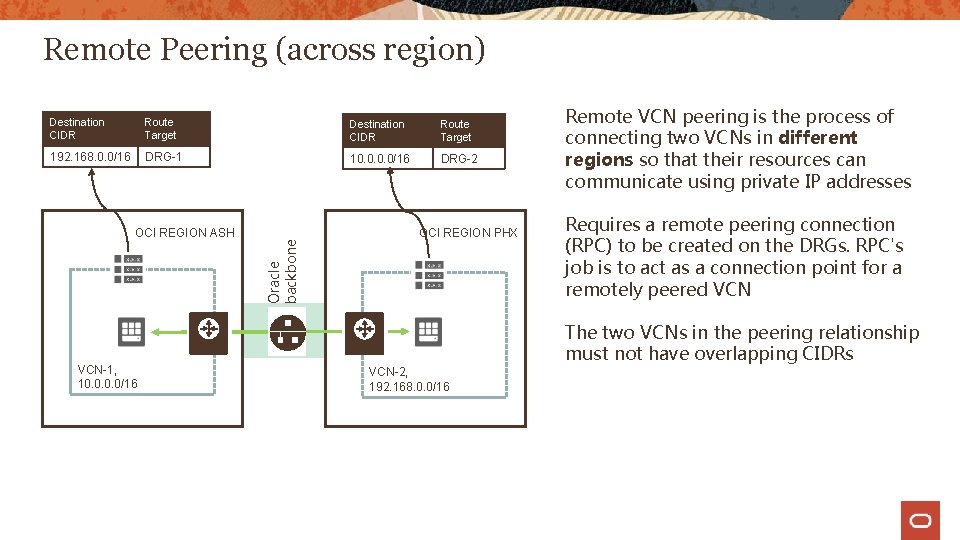
Remote Peering (across region) Route Target Destination CIDR Route Target 192. 168. 0. 0/16 DRG-1 10. 0/16 DRG-2 OCI REGION ASH VCN-1, 10. 0/16 Oracle backbone Destination CIDR OCI REGION PHX Remote VCN peering is the process of connecting two VCNs in different regions so that their resources can communicate using private IP addresses Requires a remote peering connection (RPC) to be created on the DRGs. RPC's job is to act as a connection point for a remotely peered VCN The two VCNs in the peering relationship must not have overlapping CIDRs VCN-2, 192. 168. 0. 0/16

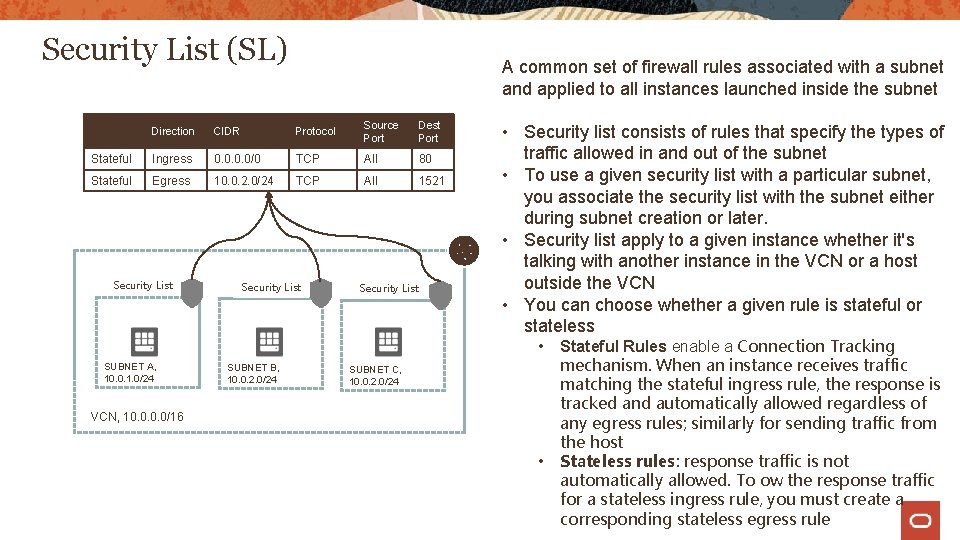
Security List (SL) A common set of firewall rules associated with a subnet and applied to all instances launched inside the subnet Direction CIDR Protocol Source Port Dest Port Stateful Ingress 0. 0/0 TCP All 80 Stateful Egress 10. 0. 2. 0/24 TCP All 1521 Security List • Security list consists of rules that specify the types of traffic allowed in and out of the subnet • To use a given security list with a particular subnet, you associate the security list with the subnet either during subnet creation or later. • Security list apply to a given instance whether it's talking with another instance in the VCN or a host outside the VCN • You can choose whether a given rule is stateful or stateless • SUBNET A, 10. 0. 1. 0/24 SUBNET B, 10. 0. 2. 0/24 SUBNET C, 10. 0. 2. 0/24 VCN, 10. 0/16 • Stateful Rules enable a Connection Tracking mechanism. When an instance receives traffic matching the stateful ingress rule, the response is tracked and automatically allowed regardless of any egress rules; similarly for sending traffic from the host Stateless rules: response traffic is not automatically allowed. To ow the response traffic for a stateless ingress rule, you must create a corresponding stateless egress rule

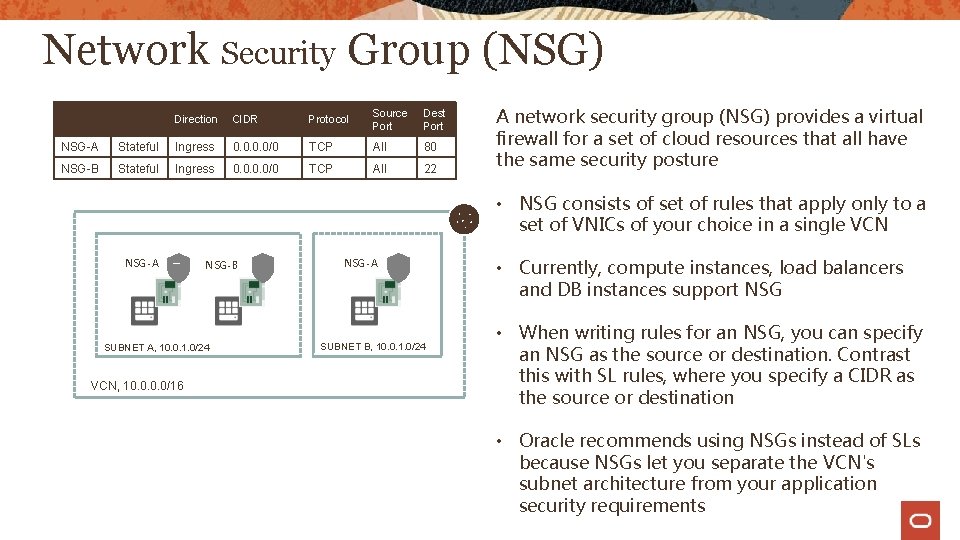
Network Security Group (NSG) Direction CIDR Protocol Source Port Dest Port NSG-A Stateful Ingress 0. 0/0 TCP All 80 NSG-B Stateful Ingress 0. 0/0 TCP All 22 A network security group (NSG) provides a virtual firewall for a set of cloud resources that all have the same security posture • NSG consists of set of rules that apply only to a set of VNICs of your choice in a single VCN NSG-A NSG-B SUBNET A, 10. 0. 1. 0/24 VCN, 10. 0/16 NSG-A SUBNET B, 10. 0. 1. 0/24 • Currently, compute instances, load balancers and DB instances support NSG • When writing rules for an NSG, you can specify an NSG as the source or destination. Contrast this with SL rules, where you specify a CIDR as the source or destination • Oracle recommends using NSGs instead of SLs because NSGs let you separate the VCN's subnet architecture from your application security requirements

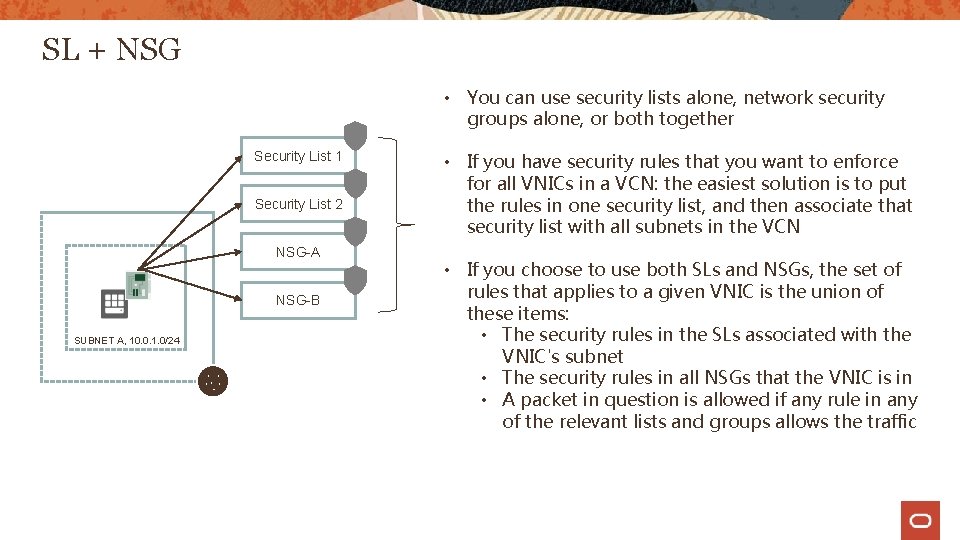
SL + NSG • You can use security lists alone, network security groups alone, or both together Security List 1 Security List 2 NSG-A NSG-B SUBNET A, 10. 0. 1. 0/24 • If you have security rules that you want to enforce for all VNICs in a VCN: the easiest solution is to put the rules in one security list, and then associate that security list with all subnets in the VCN • If you choose to use both SLs and NSGs, the set of rules that applies to a given VNIC is the union of these items: • The security rules in the SLs associated with the VNIC's subnet • The security rules in all NSGs that the VNIC is in • A packet in question is allowed if any rule in any of the relevant lists and groups allows the traffic

Compute 39 Copyright © 2019, Oracle and/or its affiliates. All rights reserved.

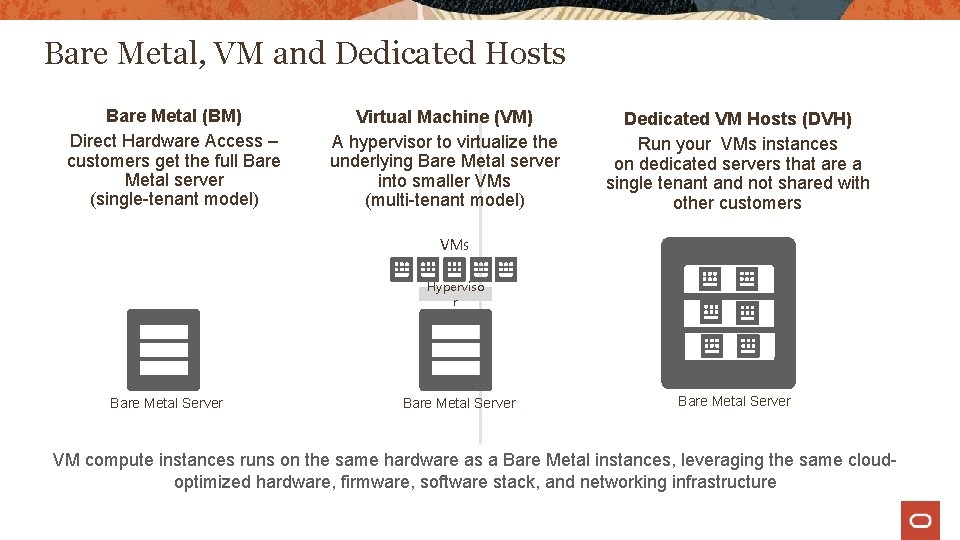
Bare Metal, VM and Dedicated Hosts Bare Metal (BM) Direct Hardware Access – customers get the full Bare Metal server (single-tenant model) Virtual Machine (VM) A hypervisor to virtualize the underlying Bare Metal server into smaller VMs (multi-tenant model) Dedicated VM Hosts (DVH) Run your VMs instances on dedicated servers that are a single tenant and not shared with other customers VMs Hyperviso r Bare Metal Server VM compute instances runs on the same hardware as a Bare Metal instances, leveraging the same cloudoptimized hardware, firmware, software stack, and networking infrastructure

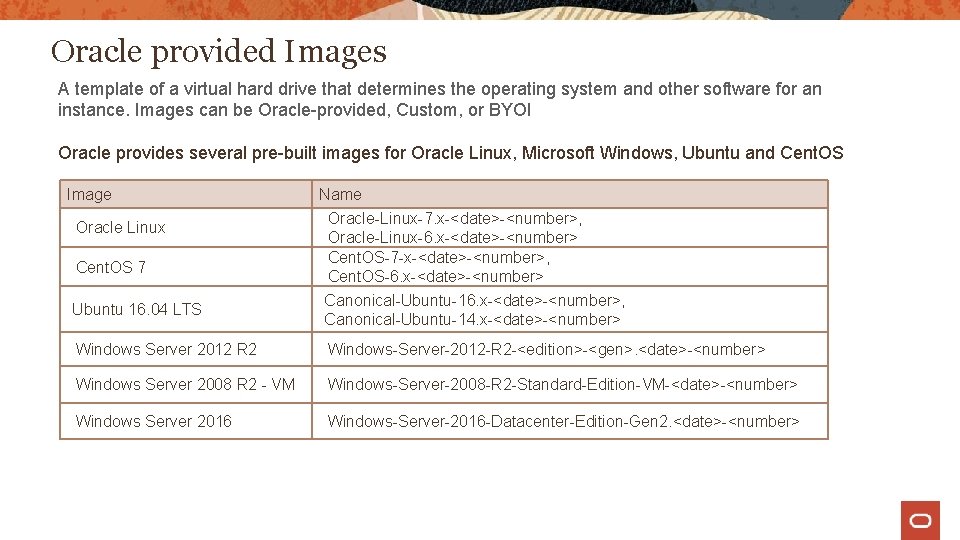
Oracle provided Images A template of a virtual hard drive that determines the operating system and other software for an instance. Images can be Oracle-provided, Custom, or BYOI Oracle provides several pre-built images for Oracle Linux, Microsoft Windows, Ubuntu and Cent. OS Image Oracle Linux Cent. OS 7 Ubuntu 16. 04 LTS Name Oracle-Linux-7. x-<date>-<number>, Oracle-Linux-6. x-<date>-<number> Cent. OS-7 -x-<date>-<number>, Cent. OS-6. x-<date>-<number> Canonical-Ubuntu-16. x-<date>-<number>, Canonical-Ubuntu-14. x-<date>-<number> Windows Server 2012 R 2 Windows-Server-2012 -R 2 -<edition>-<gen>. <date>-<number> Windows Server 2008 R 2 - VM Windows-Server-2008 -R 2 -Standard-Edition-VM-<date>-<number> Windows Server 2016 Windows-Server-2016 -Datacenter-Edition-Gen 2. <date>-<number>

Custom Images • • • Create a custom image of an instance’s boot disk and use it to launch other instances Instances you launch from your custom image include customizations, configuration, and software installed when you created the image During the process, instance shuts down and remains unavailable for several minutes. The instance restarts when the process completes Custom images do not include the data from any attached block volumes A custom image cannot exceed 300 GB Windows custom images cannot be exported or downloaded out of the tenancy Image Import/Export • • Compute service enables you to share custom images across tenancies and regions using image import/export Image import/export uses OCI Object Storage service You can import Linux and Windows Operating System Supports: • Emulation Mode: Fully emulated NIC, block boot, legacy BIOS. • Native Mode: Offer maximum performance with modern OS’s https: //cloud. oracle. com/iaas/whitepapers/deploying_custom_os_images. pdf

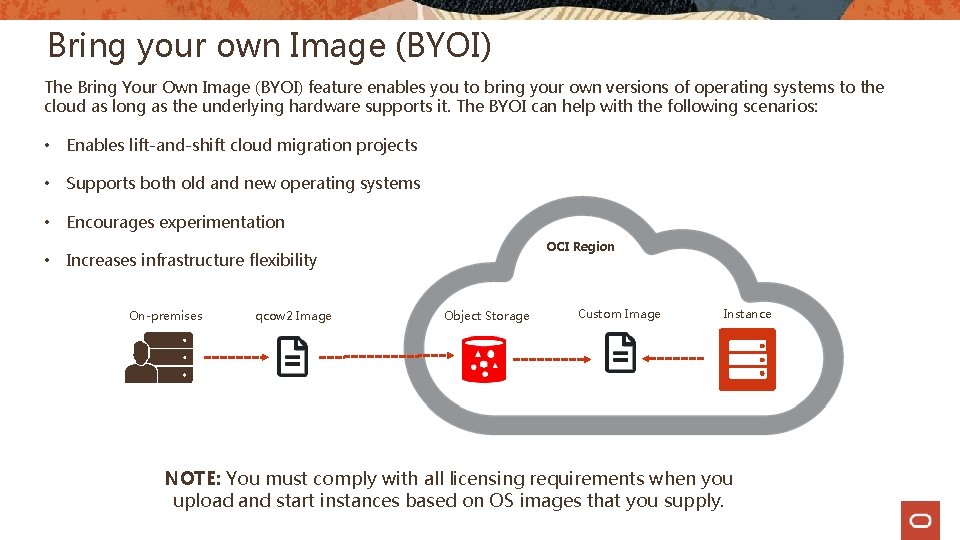
Bring your own Image (BYOI) The Bring Your Own Image (BYOI) feature enables you to bring your own versions of operating systems to the cloud as long as the underlying hardware supports it. The BYOI can help with the following scenarios: • Enables lift-and-shift cloud migration projects • Supports both old and new operating systems • Encourages experimentation • OCI Region Increases infrastructure flexibility On-premises qcow 2 Image Object Storage Custom Image Instance NOTE: You must comply with all licensing requirements when you upload and start instances based on OS images that you supply.

Boot Volumes • A compute instance is launched using OS image stored on a remote boot volume • Boot volume is created automated and associated with an instance until you terminate the instance • Boot volumes are encrypted, have faster performance, lower launch times, and higher durability for BM and VM instances • Compute instance can be scaled to a larger shape by using boot volumes • You can preserve the boot volume when you terminate a compute instance • Boot volumes are only terminated when you manually delete them • Boot volumes cannot be detached from a running instance • Possible to take a manual backup, assign backup policy or create clone of boot volumes

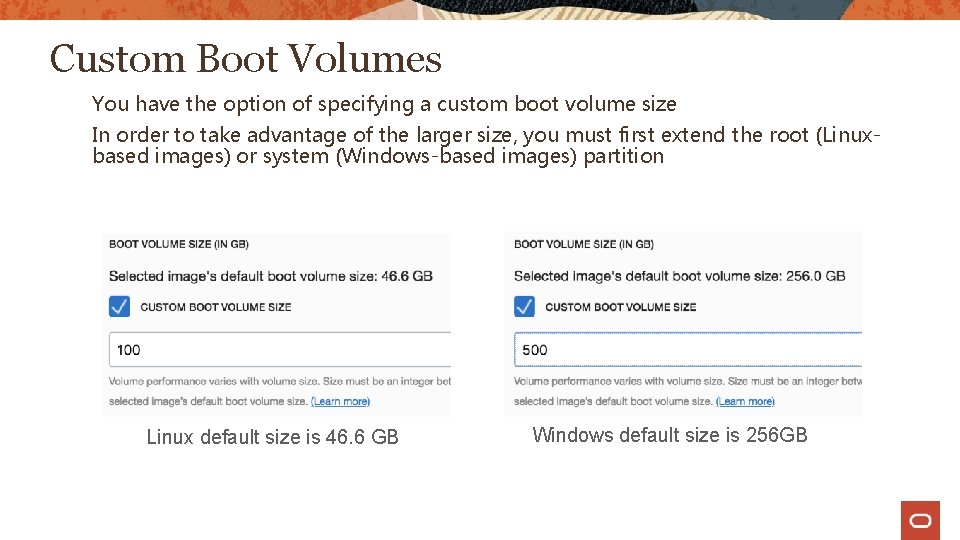
Custom Boot Volumes You have the option of specifying a custom boot volume size In order to take advantage of the larger size, you must first extend the root (Linuxbased images) or system (Windows-based images) partition Linux default size is 46. 6 GB Windows default size is 256 GB

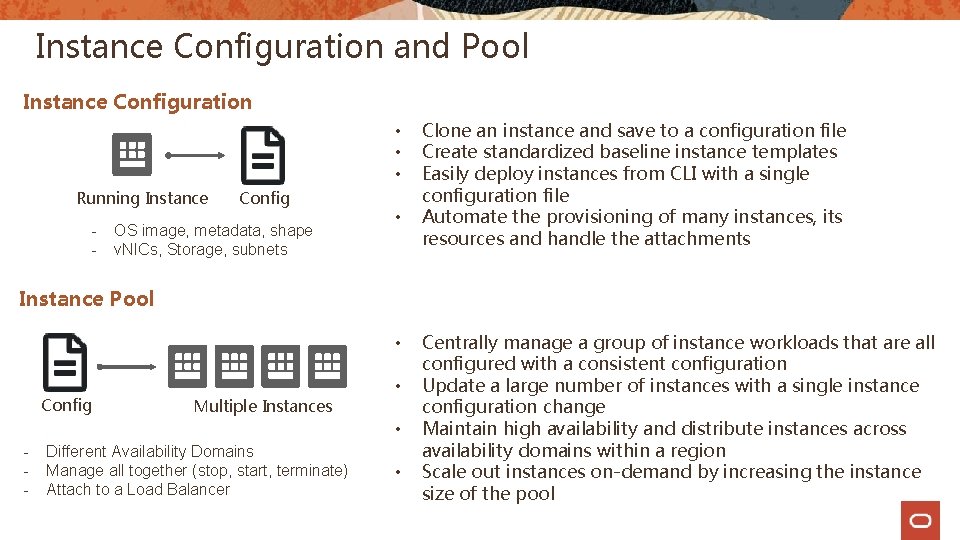
Instance Configuration and Pool Instance Configuration • • • Running Instance - Config OS image, metadata, shape v. NICs, Storage, subnets • Clone an instance and save to a configuration file Create standardized baseline instance templates Easily deploy instances from CLI with a single configuration file Automate the provisioning of many instances, its resources and handle the attachments Instance Pool • Config Multiple Instances • • - Different Availability Domains Manage all together (stop, start, terminate) Attach to a Load Balancer • Centrally manage a group of instance workloads that are all configured with a consistent configuration Update a large number of instances with a single instance configuration change Maintain high availability and distribute instances across availability domains within a region Scale out instances on-demand by increasing the instance size of the pool

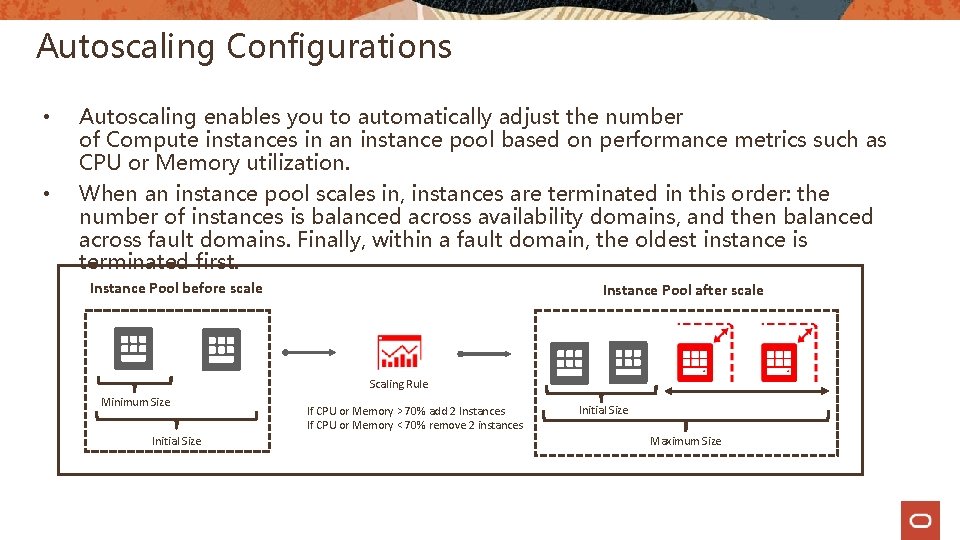
Autoscaling Configurations • Autoscaling enables you to automatically adjust the number of Compute instances in an instance pool based on performance metrics such as CPU or Memory utilization. • When an instance pool scales in, instances are terminated in this order: the number of instances is balanced across availability domains, and then balanced across fault domains. Finally, within a fault domain, the oldest instance is terminated first. Instance Pool before scale Instance Pool after scale Scaling Rule Minimum Size Initial Size If CPU or Memory > 70% add 2 Instances If CPU or Memory < 70% remove 2 instances Initial Size Maximum Size

Storage Services 48 Copyright © 2019, Oracle and/or its affiliates. All rights reserved.

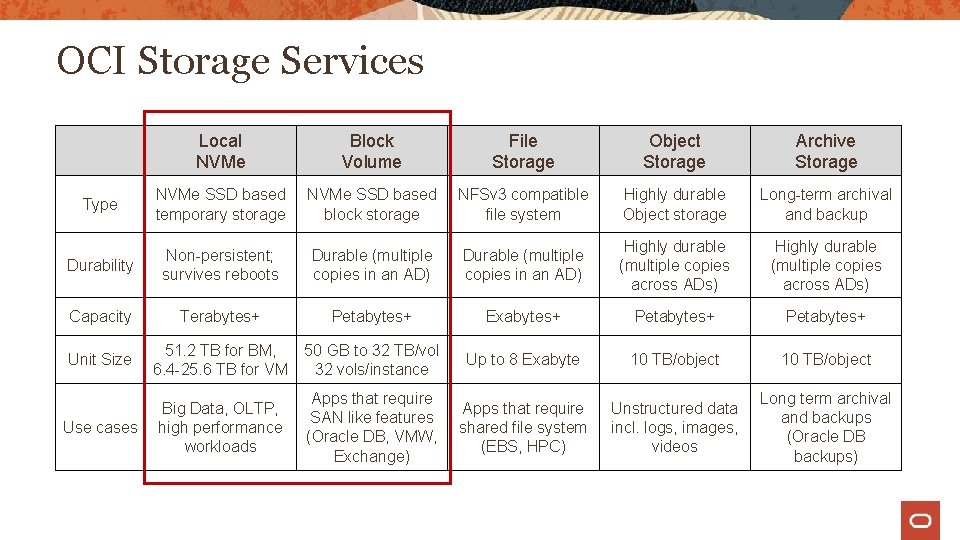
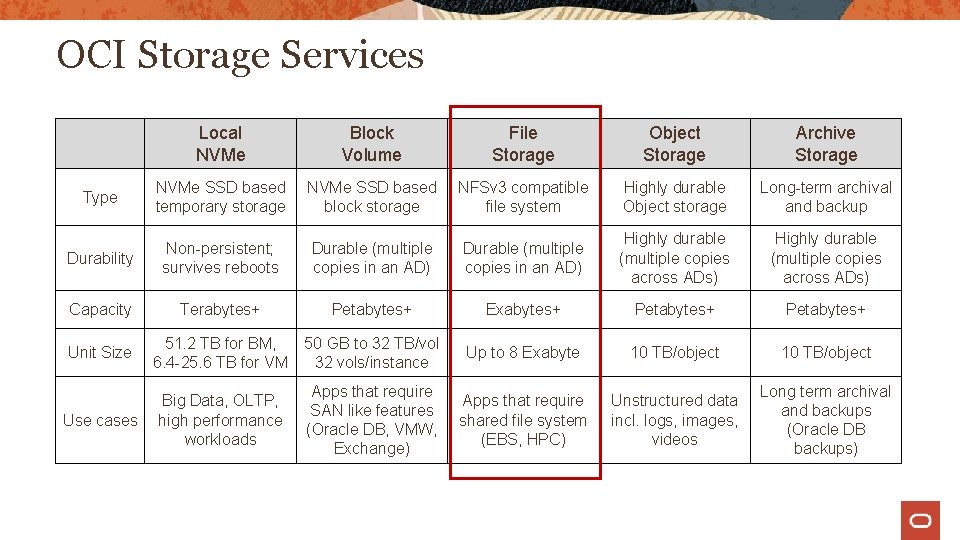
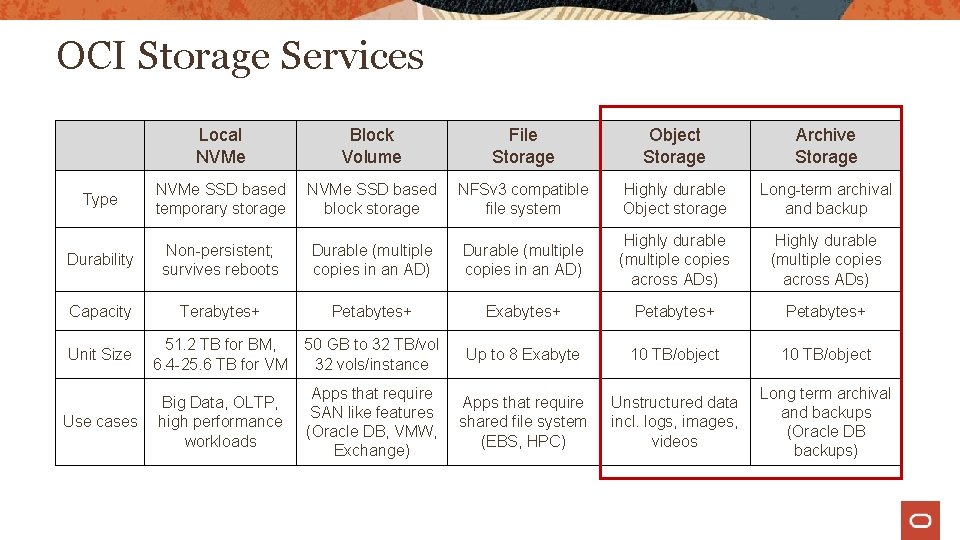
OCI Storage Services Local NVMe Block Volume File Storage Object Storage Archive Storage Type NVMe SSD based temporary storage NVMe SSD based block storage NFSv 3 compatible file system Highly durable Object storage Long-term archival and backup Durability Non-persistent; survives reboots Durable (multiple copies in an AD) Highly durable (multiple copies across ADs) Capacity Terabytes+ Petabytes+ Exabytes+ Petabytes+ Unit Size 51. 2 TB for BM, 6. 4 -25. 6 TB for VM 50 GB to 32 TB/vol 32 vols/instance Up to 8 Exabyte 10 TB/object Use cases Big Data, OLTP, high performance workloads Apps that require SAN like features (Oracle DB, VMW, Exchange) Apps that require shared file system (EBS, HPC) Unstructured data incl. logs, images, videos Long term archival and backups (Oracle DB backups)

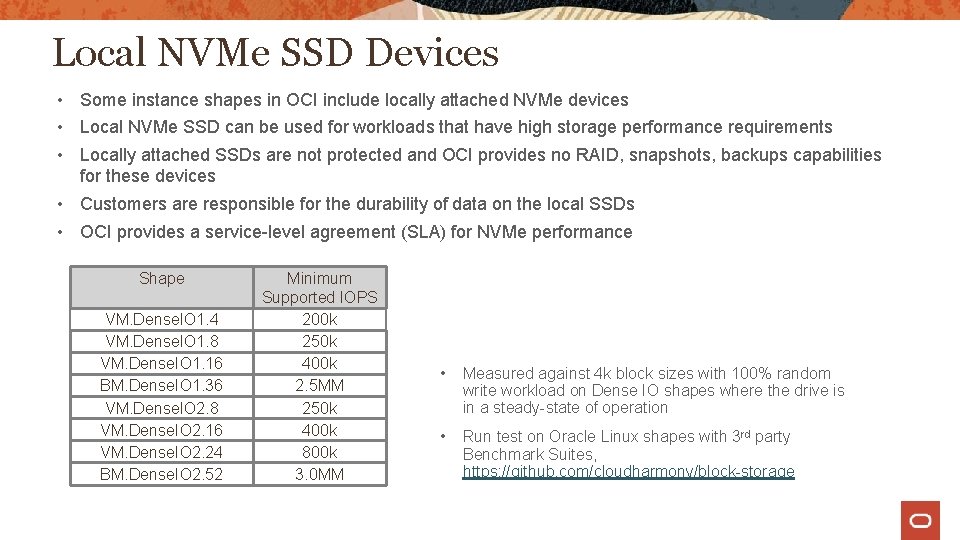
Local NVMe SSD Devices • Some instance shapes in OCI include locally attached NVMe devices • Local NVMe SSD can be used for workloads that have high storage performance requirements • Locally attached SSDs are not protected and OCI provides no RAID, snapshots, backups capabilities for these devices • Customers are responsible for the durability of data on the local SSDs • OCI provides a service-level agreement (SLA) for NVMe performance Shape VM. Dense. IO 1. 4 VM. Dense. IO 1. 8 VM. Dense. IO 1. 16 BM. Dense. IO 1. 36 VM. Dense. IO 2. 8 VM. Dense. IO 2. 16 VM. Dense. IO 2. 24 BM. Dense. IO 2. 52 Minimum Supported IOPS 200 k 250 k 400 k 2. 5 MM 250 k 400 k 800 k 3. 0 MM • Measured against 4 k block sizes with 100% random write workload on Dense IO shapes where the drive is in a steady-state of operation • Run test on Oracle Linux shapes with 3 rd party Benchmark Suites, https: //github. com/cloudharmony/block-storage

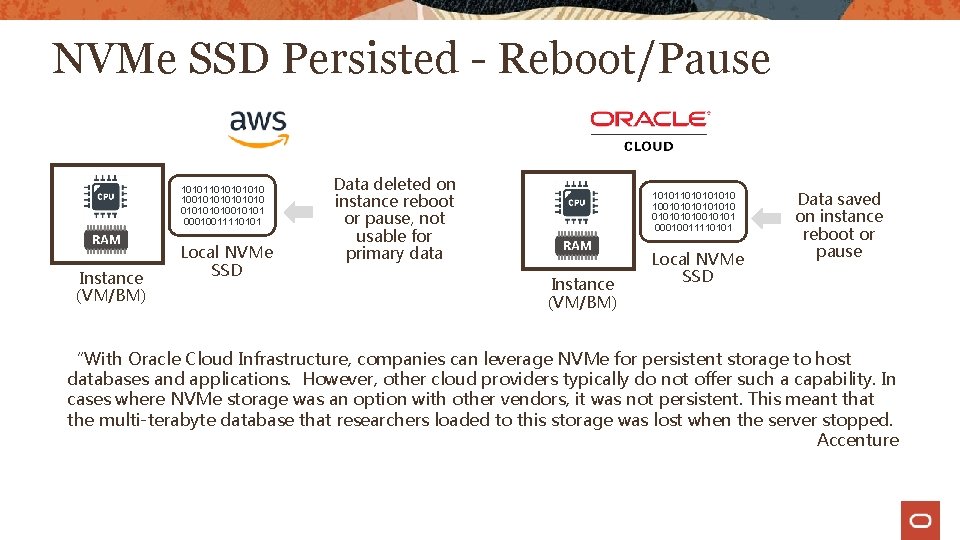
NVMe SSD Persisted - Reboot/Pause 1010101010 100101010010101 00010011110101 Instance (VM/BM) Local NVMe SSD Data deleted on instance reboot or pause, not usable for primary data 1010101010 100101010010101 00010011110101 Instance (VM/BM) Local NVMe SSD Data saved on instance reboot or pause “With Oracle Cloud Infrastructure, companies can leverage NVMe for persistent storage to host databases and applications. However, other cloud providers typically do not offer such a capability. In cases where NVMe storage was an option with other vendors, it was not persistent. This meant that the multi-terabyte database that researchers loaded to this storage was lost when the server stopped. Accenture

Block Volume Service • Block Volume Service let you store data on block volumes independently and beyond the lifespan of compute instances • Block Volume Service operates at the raw storage device level and manages data as a set of numbered, fixed-size blocks using a protocol such as i. SCSI • You can create, attach, connect, and move volumes, as needed, to meet your storage and application requirements • Typical Scenarios • Persistent and Durable Storage • Expand an Instance's Storage • Instance Scaling Capacity Perf: disk type Perf: IOPS Perf: Throughput/Vol Perf: Latency (P 95) Configurable: 50 GB to 32 TB (1 GB increments) NVMe SSD based 60 IOPS/GB - up to 25 K IOPS* 480 KBPS/GB - up to 320 MBPS** Sub-millisecond latencies Perf: Per-instance Limits Durability Security Restore from Backups (RTO) Backup Performance Multiple replicas across multiple storage servers within the AD Encrypted at rest and transit <1 minute, regardless of size * For Bare Metal or 8 -core+ VM compute instance, using 4 KB blocks. VM perf is limited by VM network bandwidth. ** At 256 KB block size

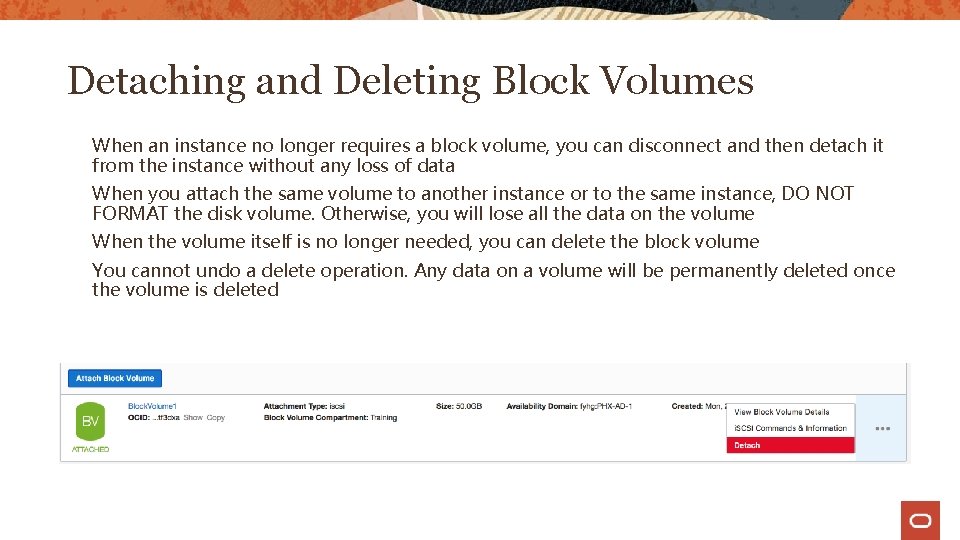
Detaching and Deleting Block Volumes When an instance no longer requires a block volume, you can disconnect and then detach it from the instance without any loss of data When you attach the same volume to another instance or to the same instance, DO NOT FORMAT the disk volume. Otherwise, you will lose all the data on the volume When the volume itself is no longer needed, you can delete the block volume You cannot undo a delete operation. Any data on a volume will be permanently deleted once the volume is deleted

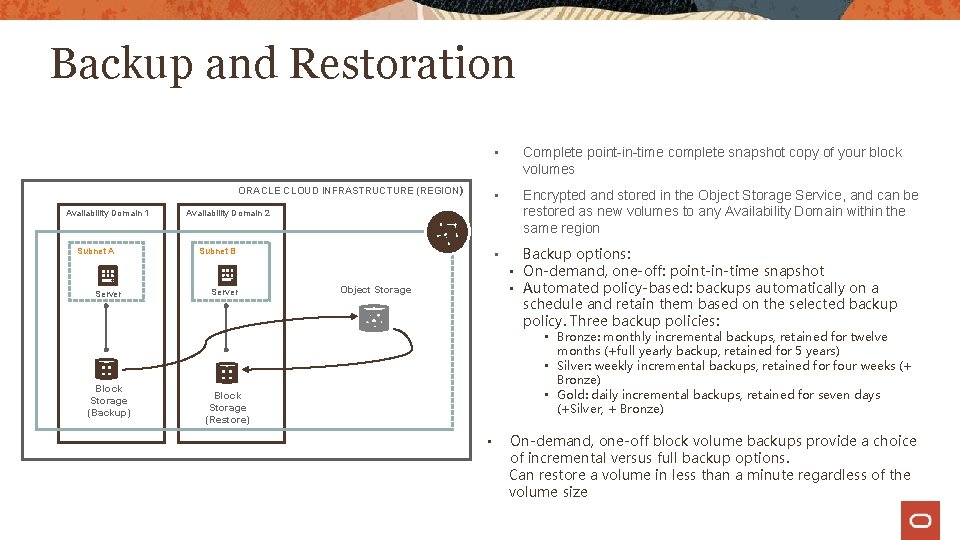
Backup and Restoration ORACLE CLOUD INFRASTRUCTURE (REGION ) Availability Domain 1 Subnet A Server Block Storage (Backup) • Complete point-in-time complete snapshot copy of your block volumes • Encrypted and stored in the Object Storage Service, and can be restored as new volumes to any Availability Domain within the same region Availability Domain 2 Subnet B Server • Object Storage Backup options: • On-demand, one-off: point-in-time snapshot • Automated policy-based: backups automatically on a schedule and retain them based on the selected backup policy. Three backup policies: • Bronze: monthly incremental backups, retained for twelve months (+full yearly backup, retained for 5 years) • Silver: weekly incremental backups, retained for four weeks (+ Bronze) • Gold: daily incremental backups, retained for seven days (+Silver, + Bronze) Block Storage (Restore) • On-demand, one-off block volume backups provide a choice of incremental versus full backup options. Can restore a volume in less than a minute regardless of the volume size

Clone Cloning allows copying an entire existing block volume to a new volume without needing to go through a backup and restore process Clone is a point-in-time direct disk-to-disk deep copy an of entire volume The clone operation is immediate, but actual copying of data happens in the background and can take up to 15 minutes for 1 TB volume A clone can only be created in the same AD with no need of detaching the source volume before cloning it A clone can be attached and used as regular volume when its lifecycle state changes from ”PROVISIONING” to "AVAILABLE", usually within seconds (At this time, the data is being copied in the background)

Volume Groups Group together block and boot volumes from multiple compartments across multiple compute instances in a volume group You can use volume groups to create volume group backups and clones that are point-in-time and crash-consistent Manually trigger a full or incremental backup of all the volumes in a volume group leveraging a coordinated snapshot across all the volumes

Block Volume Offline Resize The Oracle Cloud Infrastructure Block Volume service lets you expand the size of block volumes and boot volumes. You have three options to increase the size of your volumes: • Expand an existing volume in place with offline resizing. • Restore from a volume backup to a larger volume. • Clone an existing volume to a new, larger volume. You can only increase the size of the volume, you cannot decrease the size.

OCI Storage Services Local NVMe Block Volume File Storage Object Storage Archive Storage Type NVMe SSD based temporary storage NVMe SSD based block storage NFSv 3 compatible file system Highly durable Object storage Long-term archival and backup Durability Non-persistent; survives reboots Durable (multiple copies in an AD) Highly durable (multiple copies across ADs) Capacity Terabytes+ Petabytes+ Exabytes+ Petabytes+ Unit Size 51. 2 TB for BM, 6. 4 -25. 6 TB for VM 50 GB to 32 TB/vol 32 vols/instance Up to 8 Exabyte 10 TB/object Use cases Big Data, OLTP, high performance workloads Apps that require SAN like features (Oracle DB, VMW, Exchange) Apps that require shared file system (EBS, HPC) Unstructured data incl. logs, images, videos Long term archival and backups (Oracle DB backups)

File Storage service Features • AD-local service, available in all OCI regions and Availability Domains • Supports NFS v. 3 and Network Lock Management (NLM) for file locking • Full POSIX semantics • Data Protection: Snapshots capabilities; 10, 000 snapshots per file system • Security: 128 -bit, data-at-rest encryption for all file systems & metadata • Create 100 file systems and 2 mount targets per AD per account Oracle Applications General Purpose Lift and Shift File Systems Big Data & Analytics HPC Scale Out Apps Test / Dev Databases Micro. Services Containers

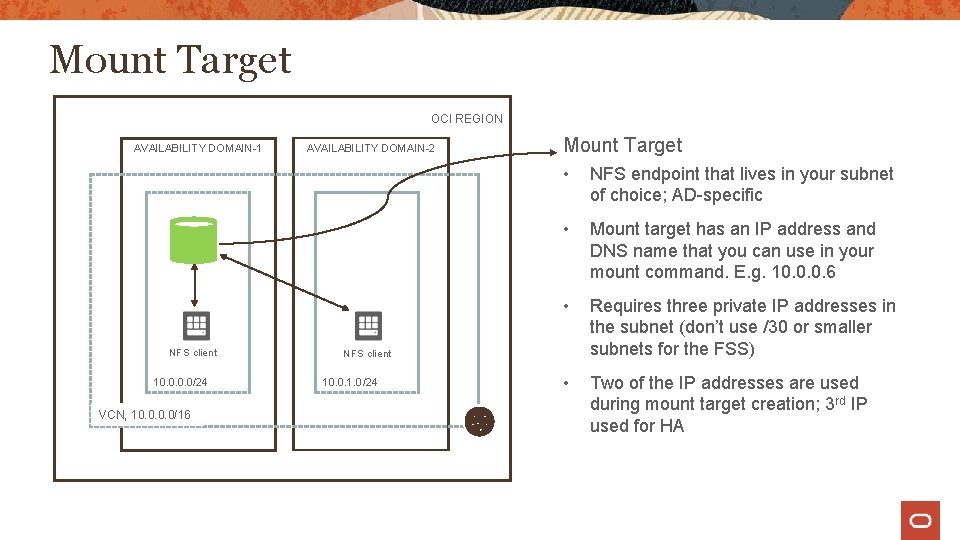
Mount Target OCI REGION AVAILABILITY DOMAIN-1 NFS client 10. 0/24 VCN, 10. 0/16 AVAILABILITY DOMAIN-2 Mount Target • NFS endpoint that lives in your subnet of choice; AD-specific • Mount target has an IP address and DNS name that you can use in your mount command. E. g. 10. 0. 0. 6 • Requires three private IP addresses in the subnet (don’t use /30 or smaller subnets for the FSS) • Two of the IP addresses are used during mount target creation; 3 rd IP used for HA NFS client 10. 0. 1. 0/24

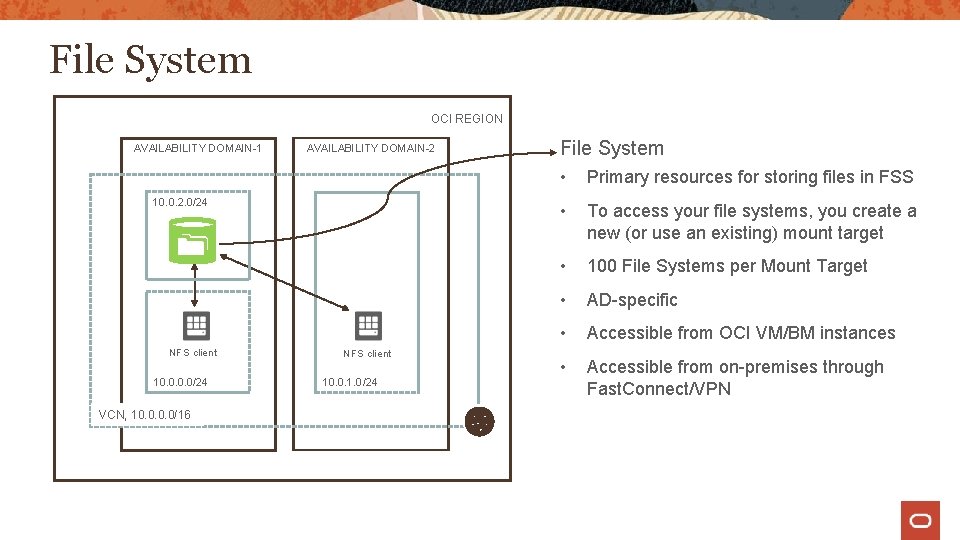
File System OCI REGION AVAILABILITY DOMAIN-1 AVAILABILITY DOMAIN-2 10. 0. 2. 0/24 NFS client 10. 0/24 VCN, 10. 0/16 NFS client 10. 0. 1. 0/24 File System • Primary resources for storing files in FSS • To access your file systems, you create a new (or use an existing) mount target • 100 File Systems per Mount Target • AD-specific • Accessible from OCI VM/BM instances • Accessible from on-premises through Fast. Connect/VPN

FSS Security Four distinct and separate layers of security with its own authorization entities and methods to consider when using FSS Security layer Uses these. . To control actions like these. . IAM Service OCI users, policies Creating instances (NFS clients) and FSS VCNs. Creating, listing, and associating file systems and mount targets Security Lists CIDR blocks Connecting the NFS client instance to the mount target Export Options Export options, CIDR blocks Applying access control per-file system based on source IP CIDR blocks that bridges the Security Lists layer and the NFS v. 3 Unix Security layer Unix users Mounting file systems 1, reading the writing files, file access security NFS v 3. Unix Security 1 When mounting file systems, don't use mount options such as nolock, rsize, or wsize. These options cause issues with performance and file locking

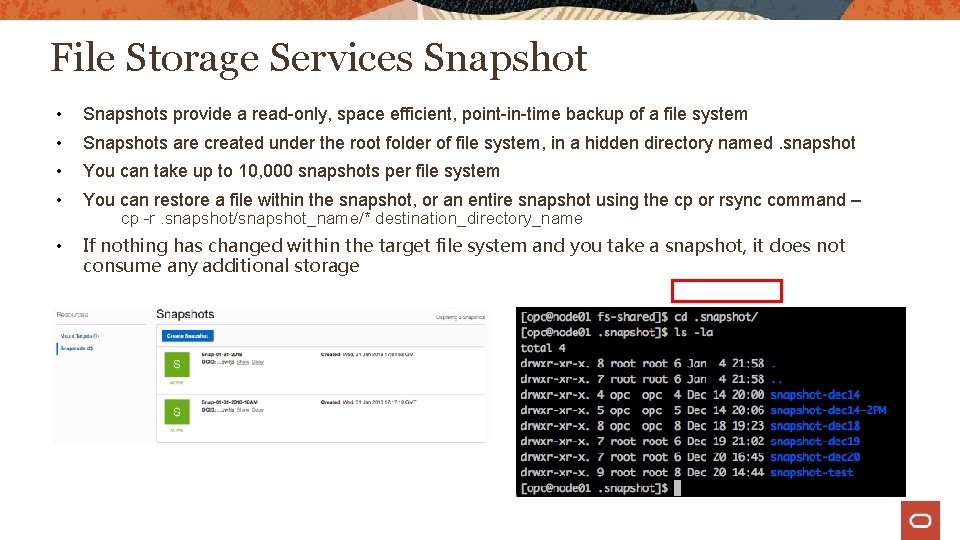
File Storage Services Snapshot • Snapshots provide a read-only, space efficient, point-in-time backup of a file system • Snapshots are created under the root folder of file system, in a hidden directory named. snapshot • You can take up to 10, 000 snapshots per file system • You can restore a file within the snapshot, or an entire snapshot using the cp or rsync command – • If nothing has changed within the target file system and you take a snapshot, it does not consume any additional storage cp -r. snapshot/snapshot_name/* destination_directory_name

OCI Storage Services Local NVMe Block Volume File Storage Object Storage Archive Storage Type NVMe SSD based temporary storage NVMe SSD based block storage NFSv 3 compatible file system Highly durable Object storage Long-term archival and backup Durability Non-persistent; survives reboots Durable (multiple copies in an AD) Highly durable (multiple copies across ADs) Capacity Terabytes+ Petabytes+ Exabytes+ Petabytes+ Unit Size 51. 2 TB for BM, 6. 4 -25. 6 TB for VM 50 GB to 32 TB/vol 32 vols/instance Up to 8 Exabyte 10 TB/object Use cases Big Data, OLTP, high performance workloads Apps that require SAN like features (Oracle DB, VMW, Exchange) Apps that require shared file system (EBS, HPC) Unstructured data incl. logs, images, videos Long term archival and backups (Oracle DB backups)

Object Storage Service An internet-scale, high-performance storage platform Ideal for storing unlimited amount of unstructured data (images, media files, logs, backups) Data is managed as objects using an API built on standard HTTP verbs Regional service, not tied to any specific compute instance Offers two distinct storage classes to address the need for performant, frequently accessed "hot" storage, and less frequently accessed "cold" storage Supports private access from Oracle Cloud Infrastructure resources in a VCN through a Service Gateway Supports advanced features such as cross-region copy, pre-authenticated requests, lifecycle rules and multipart upload Common Scenarios: • • • Content Repository - highly available and durable content repository for data, images, logs, and video etc. Archive/Backup - use of object storage for preserving data for longer periods of time Log Data - application log data for analysis and debugs/troubleshooting Large Data Sets - Large data e. g. pharmaceutical trials data, genome data, and Internet of Things (Io. T) Big Data/Hadoop Support o Use as a primary data repository for big data enables ~50% improvement in performance o HDFS connector provides connectivity to various big data analytic engines like Apache Spark and Map. Reduce

Object Storage Resources Object • All data, regardless of content type, is managed as objects (e. g. logs, videos) • Each Object is composed of object itself and metadata of the object Bucket • A logical container for storing objects; Each object is stored in a bucket Namespace • A logical entity that serves as a top-level container for all buckets and objects • Each tenancy is provided one unique namespace that is global, spanning all compartments and regions • Bucket names must be unique within your tenancy, but can be repeated across tenancies • Within a namespace, buckets and objects exist in flat hierarchy, but you can simulate a directory structure using prefixes and hierarchies

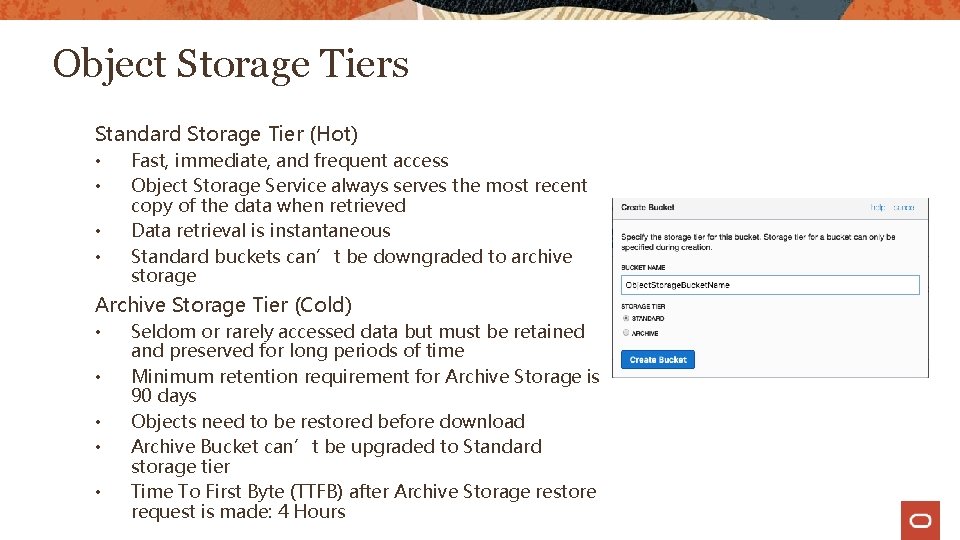
Object Storage Tiers Standard Storage Tier (Hot) • • Fast, immediate, and frequent access Object Storage Service always serves the most recent copy of the data when retrieved Data retrieval is instantaneous Standard buckets can’t be downgraded to archive storage Archive Storage Tier (Cold) • • • Seldom or rarely accessed data but must be retained and preserved for long periods of time Minimum retention requirement for Archive Storage is 90 days Objects need to be restored before download Archive Bucket can’t be upgraded to Standard storage tier Time To First Byte (TTFB) after Archive Storage restore request is made: 4 Hours

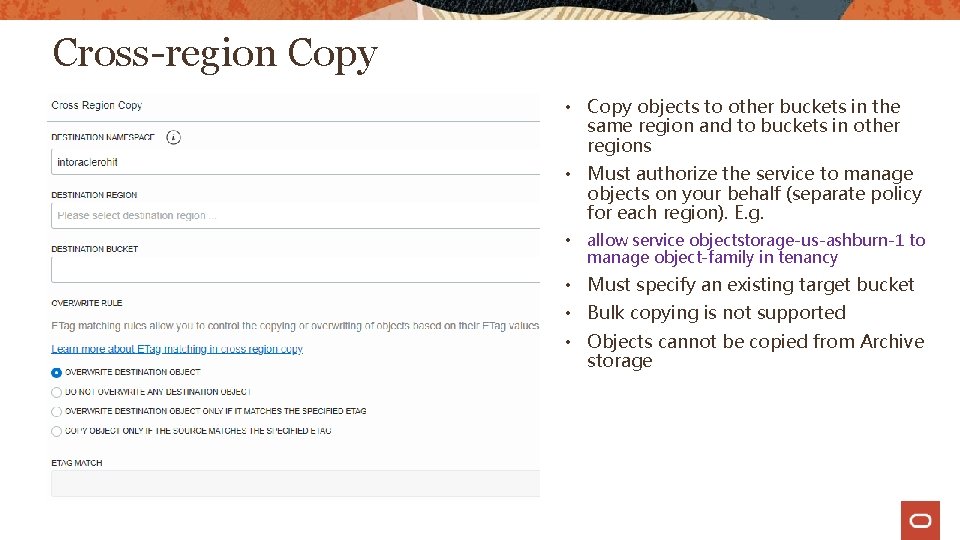
Cross-region Copy • Copy objects to other buckets in the same region and to buckets in other regions • Must authorize the service to manage objects on your behalf (separate policy for each region). E. g. • allow service objectstorage-us-ashburn-1 to manage object-family in tenancy • Must specify an existing target bucket • Bulk copying is not supported • Objects cannot be copied from Archive storage

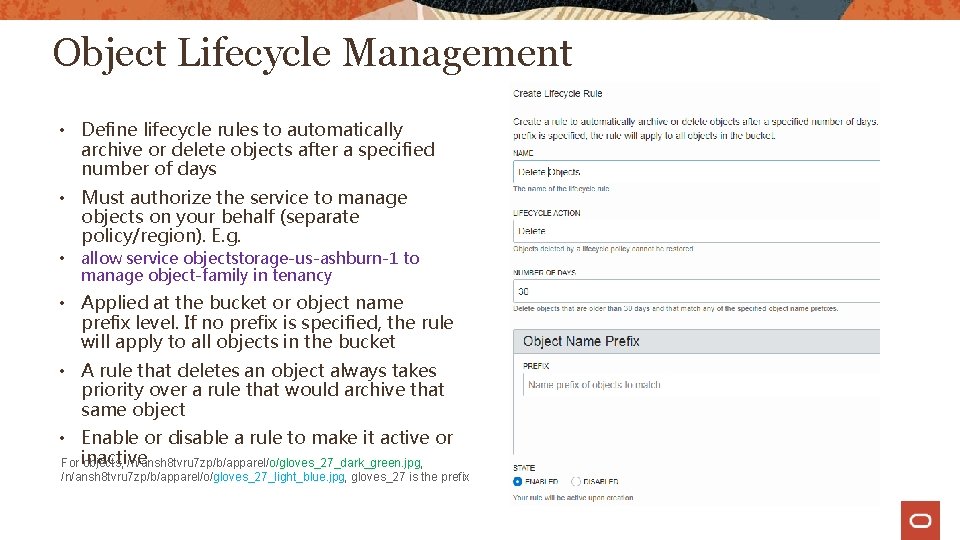
Object Lifecycle Management • Define lifecycle rules to automatically archive or delete objects after a specified number of days • Must authorize the service to manage objects on your behalf (separate policy/region). E. g. • allow service objectstorage-us-ashburn-1 to manage object-family in tenancy • Applied at the bucket or object name prefix level. If no prefix is specified, the rule will apply to all objects in the bucket • A rule that deletes an object always takes priority over a rule that would archive that same object • Enable or disable a rule to make it active or For inactive objects, /n/ansh 8 tvru 7 zp/b/apparel/o/gloves_27_dark_green. jpg, /n/ansh 8 tvru 7 zp/b/apparel/o/gloves_27_light_blue. jpg, gloves_27 is the prefix

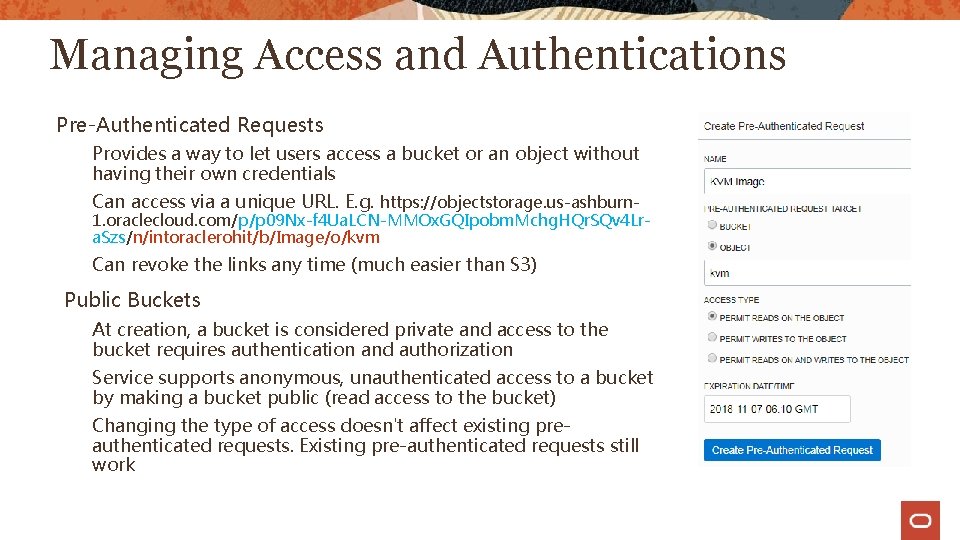
Managing Access and Authentications Pre-Authenticated Requests Provides a way to let users access a bucket or an object without having their own credentials Can access via a unique URL. E. g. https: //objectstorage. us-ashburn- 1. oraclecloud. com/p/p 09 Nx-f 4 Ua. LCN-MMOx. GQIpobm. Mchg. HQr. SQv 4 Lra. Szs/n/intoraclerohit/b/Image/o/kvm Can revoke the links any time (much easier than S 3) Public Buckets At creation, a bucket is considered private and access to the bucket requires authentication and authorization Service supports anonymous, unauthenticated access to a bucket by making a bucket public (read access to the bucket) Changing the type of access doesn't affect existing preauthenticated requests. Existing pre-authenticated requests still work

Managing Multipart Uploads With multipart uploads, individual parts of an object can be uploaded in parallel to reduce the amount of time you spend uploading. Steps involved Create object parts • Perform a multipart upload to upload objects larger than 100 Mi. B. Individual parts can be as • large as 50 Gi. B or as small as 10 MB Assign part numbers from 1 to 10, 000 Initiate an upload • Initiate a multipart upload by making a Create. Multipart. Upload REST API call Upload object parts • Make an Upload. Part request for each object part upload • If you have network issues, you can restart a failed upload for an individual part. You do not need to restart the entire upload Commit the upload • When you have uploaded all object parts, complete the multipart upload by committing it; add a bullet on checksum etc.

Load Balancing 72 Copyright © 2019, Oracle and/or its affiliates. All rights reserved.

OCI Load Balancing Service Load Balancer as-a-service, provides scale and HA Public and Private Load Balancer options Public Load Balancer service is regional in scope and provides High Availability across two ADs or FDs Supported Protocols – TCP, HTTP/1. 0, HTTP/1. 1, HTTP/2, Web. Socket Supports SSL Termination, End-to-End SSL, SSL Tunneling Supports advanced features such as session persistence and content based routing Key differentiators Private or Public Load Balancer (with Public IP address) Provisioned bandwidth – 100 Mbps, 400 Mbps, 8 Gbps Single load balancer for TCP (layer 4) and HTTP (layer 7) traffic

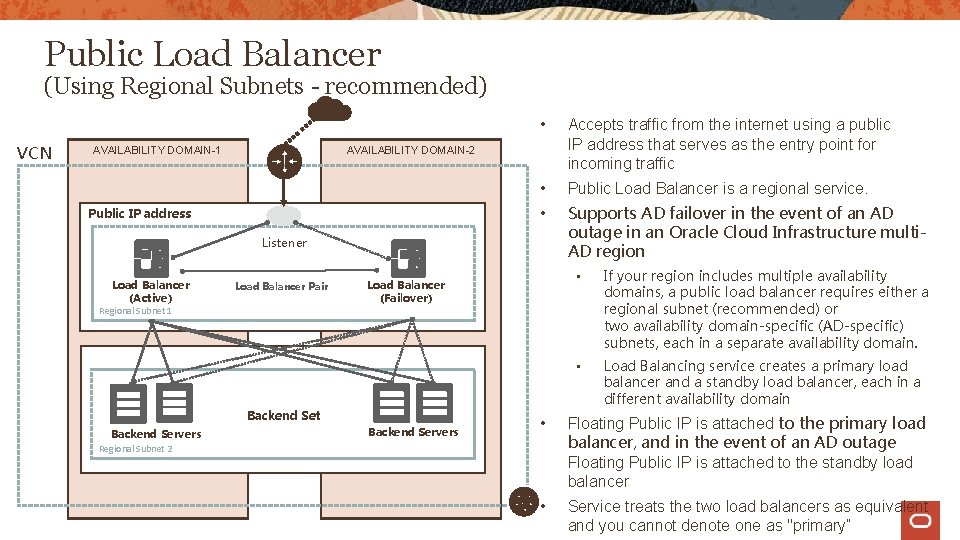
Public Load Balancer (Using Regional Subnets - recommended) VCN AVAILABILITY DOMAIN-1 • Accepts traffic from the internet using a public IP address that serves as the entry point for incoming traffic • Public Load Balancer is a regional service. • Supports AD failover in the event of an AD outage in an Oracle Cloud Infrastructure multi. AD region AVAILABILITY DOMAIN-2 Public IP address Listener Load Balancer (Active) Load Balancer Pair Regional Subnet 1 Load Balancer (Failover) Backend Set Backend Servers • If your region includes multiple availability domains, a public load balancer requires either a regional subnet (recommended) or two availability domain-specific (AD-specific) subnets, each in a separate availability domain. • Load Balancing service creates a primary load balancer and a standby load balancer, each in a different availability domain • Floating Public IP is attached to the primary load balancer, and in the event of an AD outage Floating Public IP is attached to the standby load balancer • Service treats the two load balancers as equivalent and you cannot denote one as "primary” Regional Subnet 2

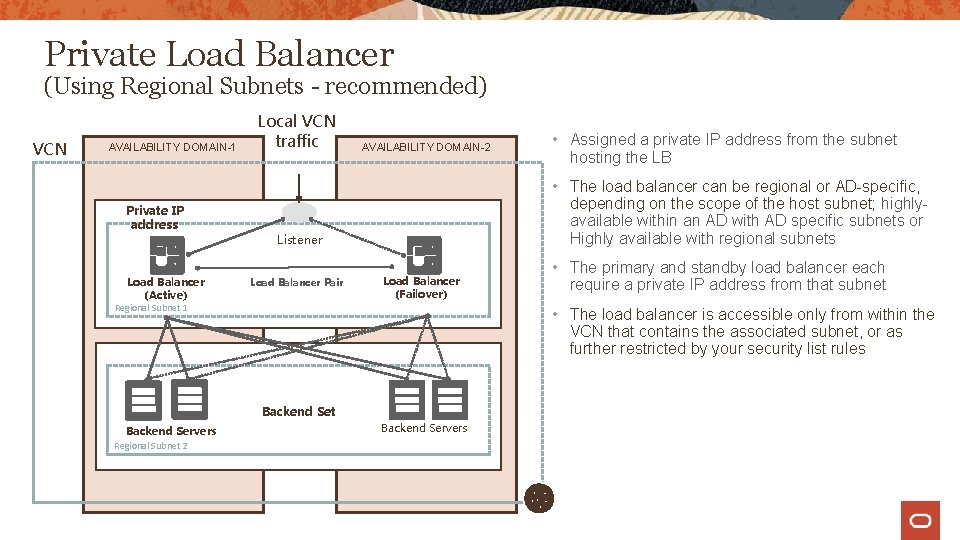
Private Load Balancer (Using Regional Subnets - recommended) VCN AVAILABILITY DOMAIN-1 Private IP address Load Balancer (Active) Local VCN traffic AVAILABILITY DOMAIN-2 • The load balancer can be regional or AD-specific, depending on the scope of the host subnet; highlyavailable within an AD with AD specific subnets or Highly available with regional subnets Listener Load Balancer Pair Regional Subnet 1 Load Balancer (Failover) Regional Subnet 2 • The primary and standby load balancer each require a private IP address from that subnet • The load balancer is accessible only from within the VCN that contains the associated subnet, or as further restricted by your security list rules Backend Set Backend Servers • Assigned a private IP address from the subnet hosting the LB Backend Servers

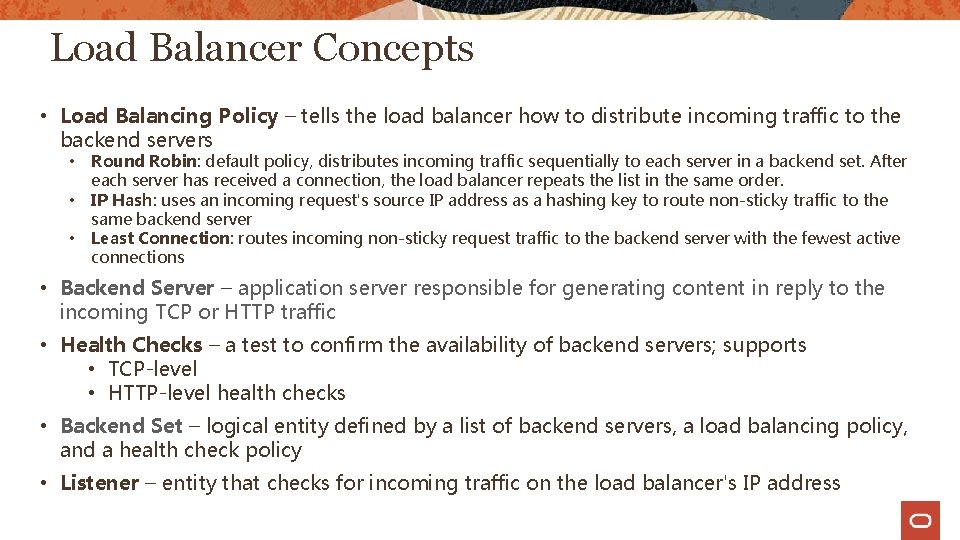
Load Balancer Concepts • Load Balancing Policy – tells the load balancer how to distribute incoming traffic to the backend servers • • • Round Robin: default policy, distributes incoming traffic sequentially to each server in a backend set. After each server has received a connection, the load balancer repeats the list in the same order. IP Hash: uses an incoming request's source IP address as a hashing key to route non-sticky traffic to the same backend server Least Connection: routes incoming non-sticky request traffic to the backend server with the fewest active connections • Backend Server – application server responsible for generating content in reply to the incoming TCP or HTTP traffic • Health Checks – a test to confirm the availability of backend servers; supports • TCP-level • HTTP-level health checks • Backend Set – logical entity defined by a list of backend servers, a load balancing policy, and a health check policy • Listener – entity that checks for incoming traffic on the load balancer's IP address

Database 77 Copyright © 2019, Oracle and/or its affiliates. All rights reserved.

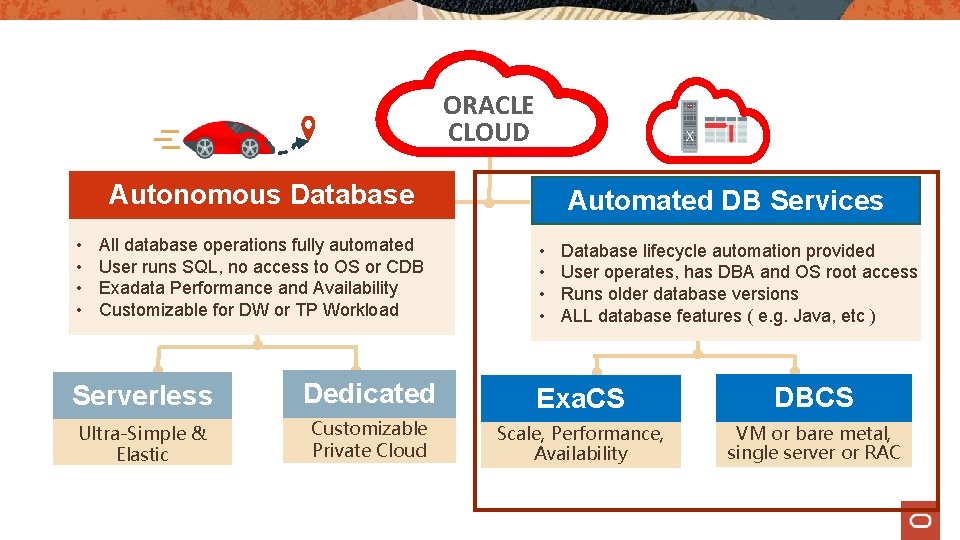
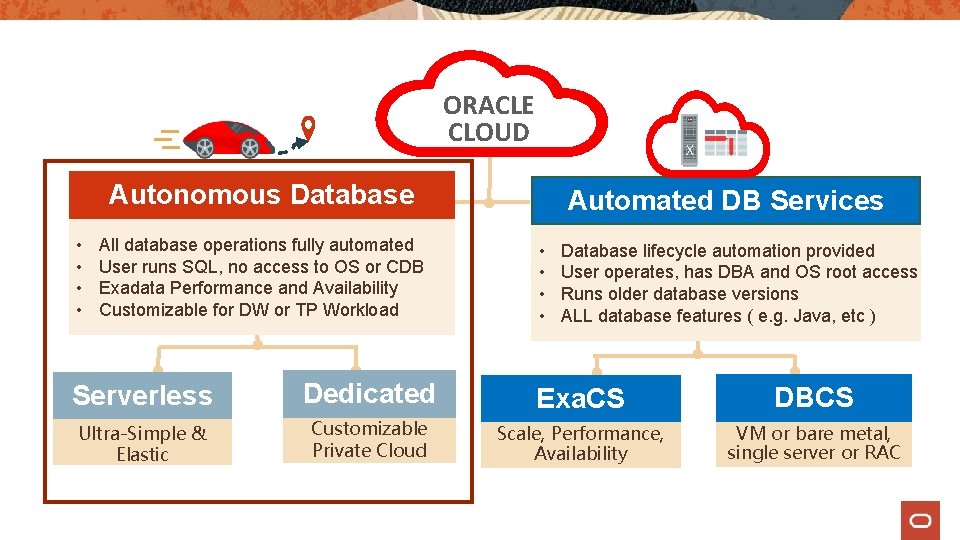
ORACLE CLOUD Autonomous Database • • All database operations fully automated User runs SQL, no access to OS or CDB Exadata Performance and Availability Customizable for DW or TP Workload Automated DB Services • • Database lifecycle automation provided User operates, has DBA and OS root access Runs older database versions ALL database features ( e. g. Java, etc ) Serverless Dedicated Exa. CS DBCS Ultra-Simple & Elastic Customizable Private Cloud Scale, Performance, Availability VM or bare metal, single server or RAC

OCI Database Service Mission critical, enterprise grade cloud database service with comprehensive offerings to cover all enterprise database needs Exadata, RAC, Bare Metal, VM Exadata X Complete Lifecycle Automation RAC High Availability and Scalability Block Volumes Provisioning, Patching, Backup & Restore RAC & Data Guard Dynamic CPU and Storage scaling Bare Metal Security Infrastructure (IAM, Security Lists, Audit logs) Database (TDE, RMAN backup / Block volume encryption) OCI Platform integration Tagging, Limits and Usage integration Bring Your Own License (BYOL) Virtual Machine

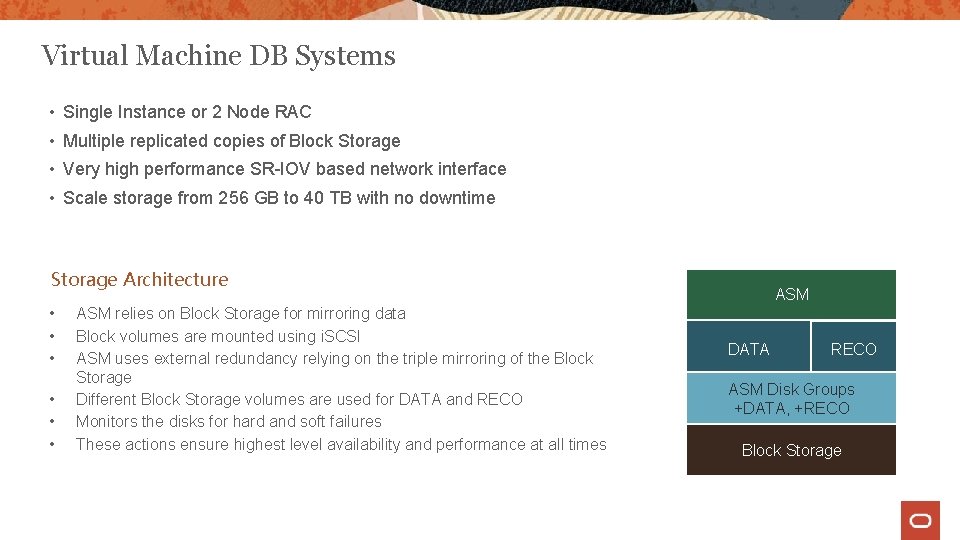
Virtual Machine DB Systems • Single Instance or 2 Node RAC • Multiple replicated copies of Block Storage • Very high performance SR-IOV based network interface • Scale storage from 256 GB to 40 TB with no downtime Storage Architecture • • • ASM relies on Block Storage for mirroring data Block volumes are mounted using i. SCSI ASM uses external redundancy relying on the triple mirroring of the Block Storage Different Block Storage volumes are used for DATA and RECO Monitors the disks for hard and soft failures These actions ensure highest level availability and performance at all times ASM DATA RECO ASM Disk Groups +DATA, +RECO Block Storage

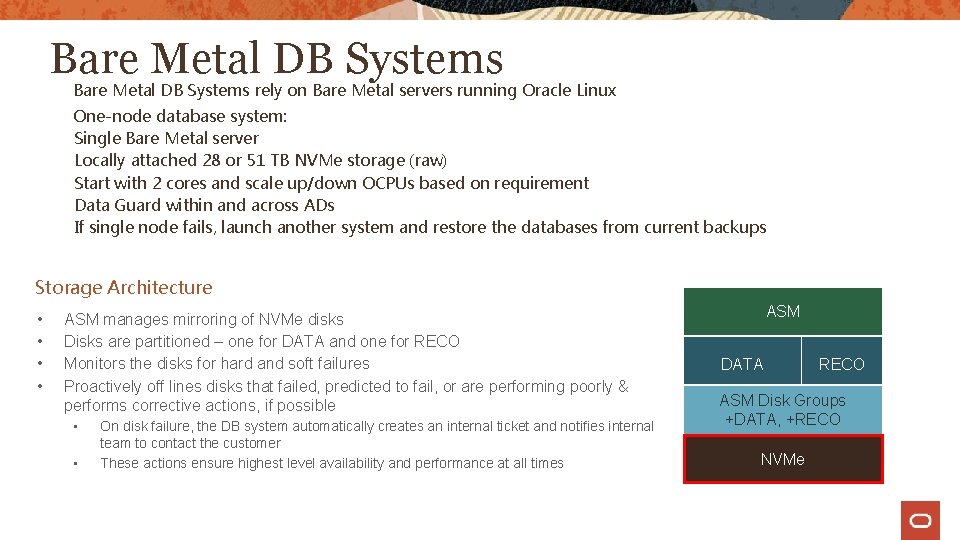
Bare Metal DB Systems rely on Bare Metal servers running Oracle Linux One-node database system: Single Bare Metal server Locally attached 28 or 51 TB NVMe storage (raw) Start with 2 cores and scale up/down OCPUs based on requirement Data Guard within and across ADs If single node fails, launch another system and restore the databases from current backups Storage Architecture • • ASM manages mirroring of NVMe disks Disks are partitioned – one for DATA and one for RECO Monitors the disks for hard and soft failures Proactively off lines disks that failed, predicted to fail, or are performing poorly & performs corrective actions, if possible • • On disk failure, the DB system automatically creates an internal ticket and notifies internal team to contact the customer These actions ensure highest level availability and performance at all times ASM DATA RECO ASM Disk Groups +DATA, +RECO NVMe

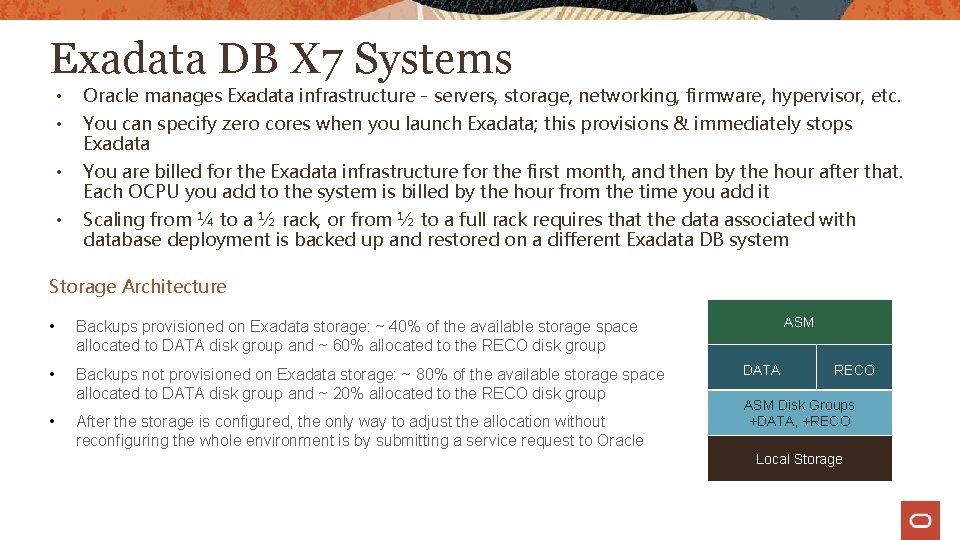
Exadata DB X 7 Systems • Oracle manages Exadata infrastructure - servers, storage, networking, firmware, hypervisor, etc. • You can specify zero cores when you launch Exadata; this provisions & immediately stops Exadata • You are billed for the Exadata infrastructure for the first month, and then by the hour after that. Each OCPU you add to the system is billed by the hour from the time you add it • Scaling from ¼ to a ½ rack, or from ½ to a full rack requires that the data associated with database deployment is backed up and restored on a different Exadata DB system Storage Architecture • Backups provisioned on Exadata storage: ~ 40% of the available storage space allocated to DATA disk group and ~ 60% allocated to the RECO disk group • Backups not provisioned on Exadata storage: ~ 80% of the available storage space allocated to DATA disk group and ~ 20% allocated to the RECO disk group • After the storage is configured, the only way to adjust the allocation without reconfiguring the whole environment is by submitting a service request to Oracle ASM DATA RECO ASM Disk Groups +DATA, +RECO Local Storage

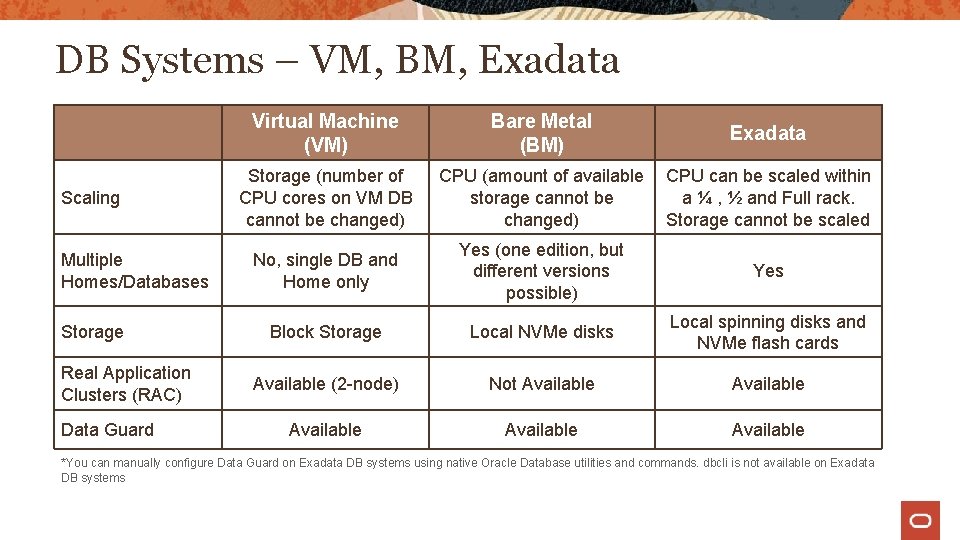
DB Systems – VM, BM, Exadata Scaling Multiple Homes/Databases Storage Real Application Clusters (RAC) Data Guard Virtual Machine (VM) Bare Metal (BM) Exadata Storage (number of CPU cores on VM DB cannot be changed) CPU (amount of available storage cannot be changed) CPU can be scaled within a ¼ , ½ and Full rack. Storage cannot be scaled No, single DB and Home only Yes (one edition, but different versions possible) Yes Block Storage Local NVMe disks Local spinning disks and NVMe flash cards Available (2 -node) Not Available Available *You can manually configure Data Guard on Exadata DB systems using native Oracle Database utilities and commands. dbcli is not available on Exadata DB systems

Patching DB Systems • Automated Applicable Patch Discovery: Automatic patch discovery and pre-flight checks/tests • On demand patching: N-1 patching (previous patch is available if it hasn’t been applied), pre-check and patching at the click of a button • Availability during patching: For Exadata and RAC shapes, patches are rolling. For single node systems if Active Data Guard is configured this can be leveraged by the patch service. • 2 step process – patching is a 2 step process, one for DB System and one for the database. DB System needs to be patched first before the database is patched • Identity and Access Controls: Granular Permissions – its possible to control who can list patches, apply them, etc. © 2019 Oracle

Backup / Restore • Managed backup and restore feature for VM/BM DB Systems; Exadata backup process requires creating a backup config file • Backups stored in Object or Local storage (recommended: Object storage for high durability) • DB System in private subnets can leverage Service Gateway • Backup options • • Automatic incremental – runs once/day, repeats the cycle every week; retained for 30 days On-demand, standalone/ full backups • Restore a DB © 2019 Oracle

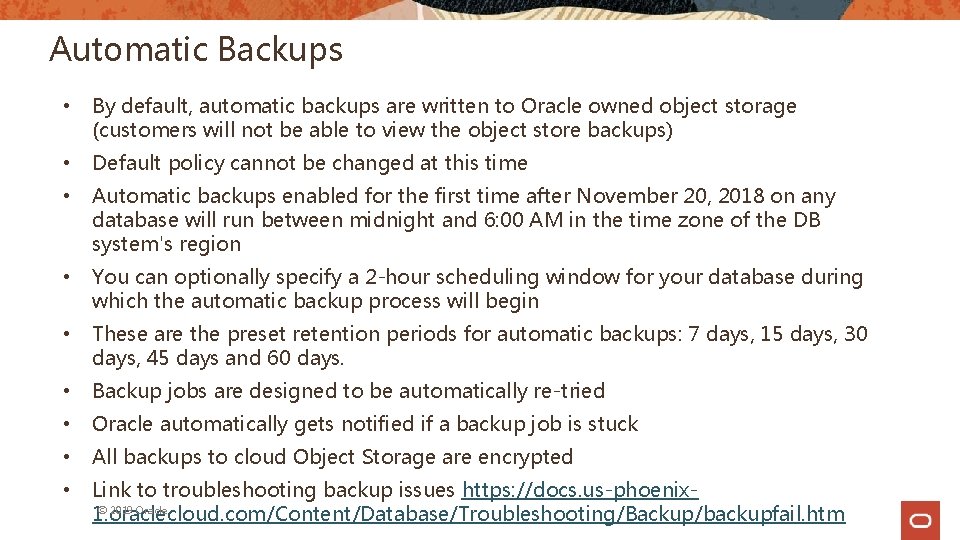
Automatic Backups • By default, automatic backups are written to Oracle owned object storage (customers will not be able to view the object store backups) • Default policy cannot be changed at this time • Automatic backups enabled for the first time after November 20, 2018 on any database will run between midnight and 6: 00 AM in the time zone of the DB system's region • You can optionally specify a 2 -hour scheduling window for your database during which the automatic backup process will begin • These are the preset retention periods for automatic backups: 7 days, 15 days, 30 days, 45 days and 60 days. • Backup jobs are designed to be automatically re-tried • Oracle automatically gets notified if a backup job is stuck • All backups to cloud Object Storage are encrypted • Link to troubleshooting backup issues https: //docs. us-phoenix© 2019 Oracle 1. oraclecloud. com/Content/Database/Troubleshooting/Backup/backupfail. htm

Oracle Data Guard Robust Infrastructure Supported on both Virtual Machine and Bare Metal DB Systems. Limited to one Standby database per Primary database on OCI. Standby database used for queries, reports, test, or backups (only for Active Data Guard) • Switchover • Planned role reversal, never any data loss • No database re-instantiation required • Used for database upgrades, tech refresh, data center moves, etc. • Manually invoked via Enterprise Manager, DGMGRL, or SQL*Plus • Failover • Unplanned failure of Primary • Flashback Database used to reinstate original Primary • Manually invoked via Enterprise Manager, DGMGRL, or SQL*Plus • May also be done automatically: Fast-Start Failover • • © 2019 Oracle

ORACLE CLOUD Autonomous Database • • All database operations fully automated User runs SQL, no access to OS or CDB Exadata Performance and Availability Customizable for DW or TP Workload Automated DB Services • • Database lifecycle automation provided User operates, has DBA and OS root access Runs older database versions ALL database features ( e. g. Java, etc ) Serverless Dedicated Exa. CS DBCS Ultra-Simple & Elastic Customizable Private Cloud Scale, Performance, Availability VM or bare metal, single server or RAC

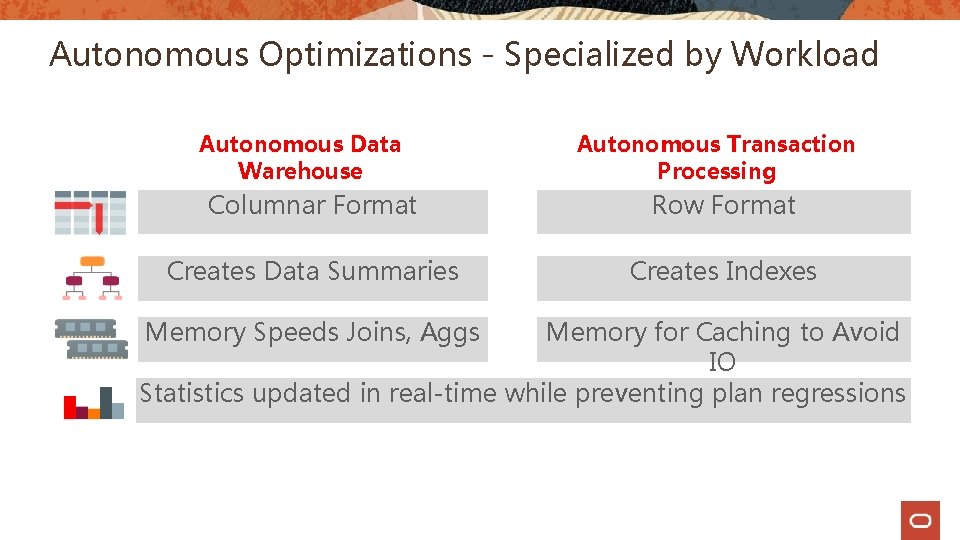
Autonomous Optimizations - Specialized by Workload Autonomous Data Warehouse Autonomous Transaction Processing Columnar Format Row Format Creates Data Summaries Creates Indexes Memory Speeds Joins, Aggs Memory for Caching to Avoid IO Statistics updated in real-time while preventing plan regressions

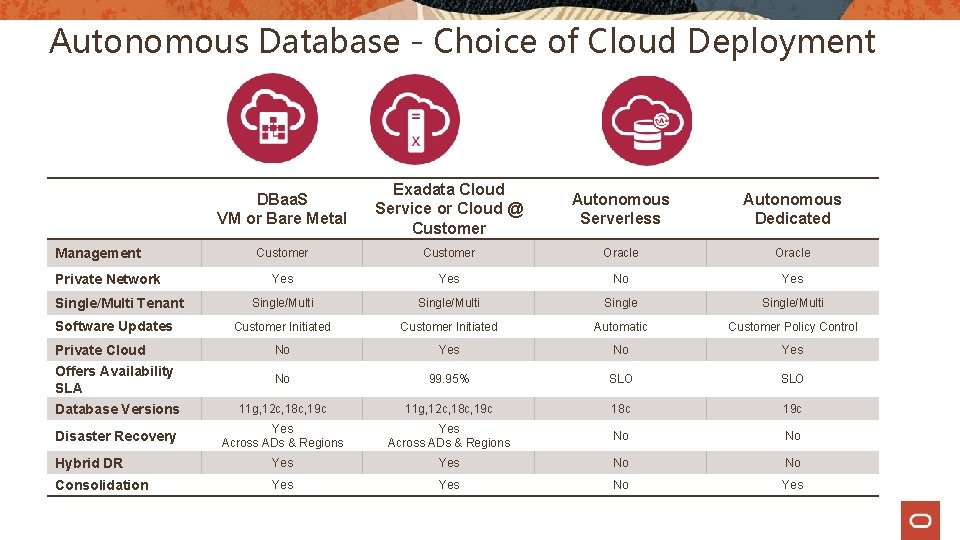
Autonomous Database - Choice of Cloud Deployment DBaa. S VM or Bare Metal Exadata Cloud Service or Cloud @ Customer Autonomous Serverless Autonomous Dedicated Customer Oracle Yes No Yes Single/Multi Customer Initiated Automatic Customer Policy Control Private Cloud No Yes Offers Availability SLA No 99. 95% SLO Database Versions 11 g, 12 c, 18 c, 19 c 18 c 19 c Disaster Recovery Yes Across ADs & Regions No No Hybrid DR Yes No No Consolidation Yes No Yes Management Private Network Single/Multi Tenant Software Updates

Autonomous Database Cloud Service – Deployment Options Oracle Autonomous Database can be deployed in 2 ways – dedicated and serverless. Dedicated deployment is a deployment choice that enables you to provision autonomous databases into their own dedicated Exadata cloud infrastructure, instead of a shared infrastructure with other tenants. With serverless deployment, the simplest configuration, you share the resources of an Exadata cloud infrastructure. You can quickly get started with no minimum commitment, enjoying quick database provisioning and independent scalability of compute and storage. Both deployment options are available for Autonomous Transaction Processing and Autonomous Data Warehouse.

Autonomous Database - Serverless Autonomous Data Warehouse & Autonomous Transaction Processing

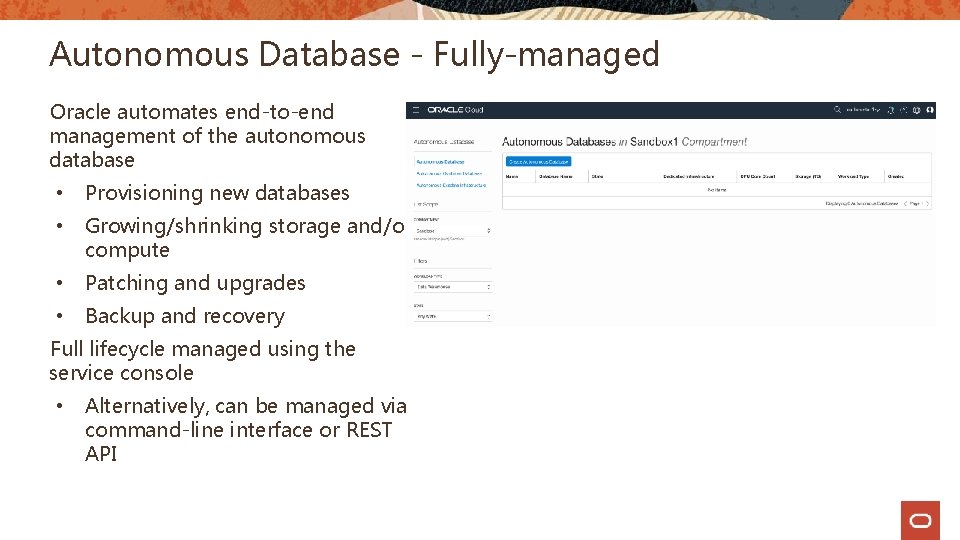
Autonomous Database - Fully-managed Oracle automates end-to-end management of the autonomous database • Provisioning new databases • Growing/shrinking storage and/or compute • Patching and upgrades • Backup and recovery Full lifecycle managed using the service console • Alternatively, can be managed via command-line interface or REST API

Automated Tuning in Autonomous Database “Load and go” • Define tables, load data, run queries — No tuning required — No special database expertise required No need to worry about tablespaces, partitioning, compression, in-memory, indexes, parallel execution — • Fast performance out of the box with zero tuning • Simple web-based monitoring console • Built-in resource-management plans

Autonomous Database – Fully-elastic Size the database to the exact compute and storage required • Not constrained by fixed building blocks, no predefined shapes Scale the database on demand • Independently scale compute or storage • Resizing occurs instantly, fully online Shut off idle compute to save money • Restart instantly Auto scaling: • Enable auto scaling to allow Autonomous Database to use more CPU and IO resources automatically when the workload requires it.

Full Support of Database Ecosystem Autonomous Database service supports : • Existing tools, running on-premises or in the cloud – Third-party BI tools – Third-party data-integration tools – Oracle BI and data-integration tools: BIEE, ODI, etc. • Oracle cloud services: Analytics Cloud Service, Golden. Gate Cloud Service, Integration Cloud Service, and others • Connectivity via SQL*Net, JDBC, ODBC

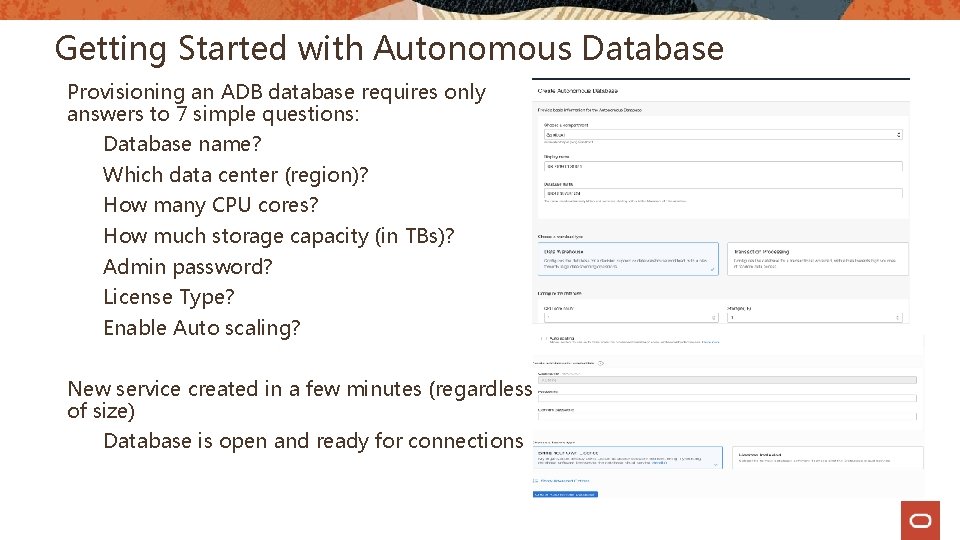
Getting Started with Autonomous Database Provisioning an ADB database requires only answers to 7 simple questions: Database name? Which data center (region)? How many CPU cores? How much storage capacity (in TBs)? Admin password? License Type? Enable Auto scaling? New service created in a few minutes (regardless of size) Database is open and ready for connections

Securing Autonomous Database (ADB) • Stores all data in encrypted format in the Oracle Database. Only authenticated users and applications can access the data when they connect to the database. • Database clients use SSL/TLS 1. 2 encrypted and mutually authenticated connections. This ensures that there is no unauthorized access to the ADB Cloud and that communications between the client and server are fully encrypted and cannot be intercepted or altered. • Certificate based authentication uses an encrypted key stored in a wallet on both the client (where the application is running) and the server (where your database service on the ADB Cloud is running). The key on the client must match the key on the server to make a connection. A wallet contains a collection of files, including the key and other information needed to connect to your database service in the ADB Cloud. • You can specify IP addresses (or CIDR block) allowed to access the ADB using the access control list. This access control list will block all IP addresses that are not in the list from accessing the database.

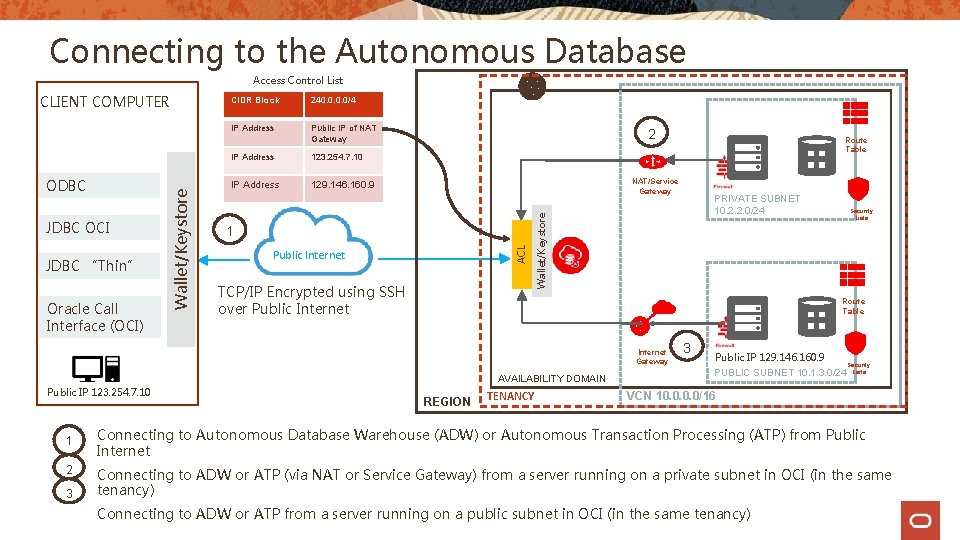
Connecting to the Autonomous Database Access Control List JDBC “Thin” Oracle Call Interface (OCI) 240. 0/4 IP Address Public IP of NAT Gateway IP Address 123. 254. 7. 10 IP Address 129. 146. 160. 9 2 NAT/Service Gateway 1 Public Internet TCP/IP Encrypted using SSH over Public Internet AVAILABILITY DOMAIN 1 2 3 PRIVATE SUBNET 10. 2. 2. 0/24 Security Lists Route Table Internet Gateway Public IP 123. 254. 7. 10 Route Table Wallet/Keystore JDBC OCI CIDR Block ACL ODBC Wallet/Keystore CLIENT COMPUTER REGION TENANCY 3 Public IP 129. 146. 160. 9 PUBLIC SUBNET 10. 1. 3. 0/24 Security Lists VCN 10. 0/16 Connecting to Autonomous Database Warehouse (ADW) or Autonomous Transaction Processing (ATP) from Public Internet Connecting to ADW or ATP (via NAT or Service Gateway) from a server running on a private subnet in OCI (in the same tenancy) Connecting to ADW or ATP from a server running on a public subnet in OCI (in the same tenancy)

Autonomous Database (ADB) Cloud – Backup and recovery • Autonomous Database Cloud automatically backs up your database for you. The retention period for backups is 60 days. You can restore and recover your database to any point-in-time in this retention period. • Autonomous Database Cloud automatic backups provide weekly full backups and daily incremental backups. • Manual backups for your ADB database is not needed. • But, you can do manual backups using the cloud console if you want to take backups before any major changes, for example before ETL processing, to make restore and recovery faster. The manual backups are put in your Cloud Object Storage bucket. When you initiate a point-in-time recovery Autonomous Database Cloud decides which backup to use for faster recovery. • You can initiate recovery for your Autonomous Database using the cloud console. Autonomous Database Cloud automatically restores and recovers your database to the point-in-time you specify. • Network Access Control Lists (ACL)s are stored in the database with other database metadata. If the database is restored to a point in time the network ACLs are reverted back to the list as of that point in time.

Autonomous Database Cloud – Cloning • Autonomous Database provides cloning where you can choose to clone either the full database or only the database metadata. • Full Clone: creates a new database with the source database’s data and metadata. • Metadata Clone: creates a new database with the source database’s metadata without the data. • When creating a Full Clone database, the minimum storage that you can specify is the source database’s actual used space rounded to the next TB. • You can only clone an Autonomous Database instance to the same tenancy and the same region as the source database. • During the provisioning for either a Full Clone or a Metadata Clone, the optimizer statistics are copied from the source database to the cloned database. • The following applies for optimizer statistics for tables in a cloned database: § Full Clone: loads into tables behave the same as loading into a table with statistics already in place. § Metadata Clone: the first load into a table after the clone clears the statistics for that table and updates the statistics with the new load.

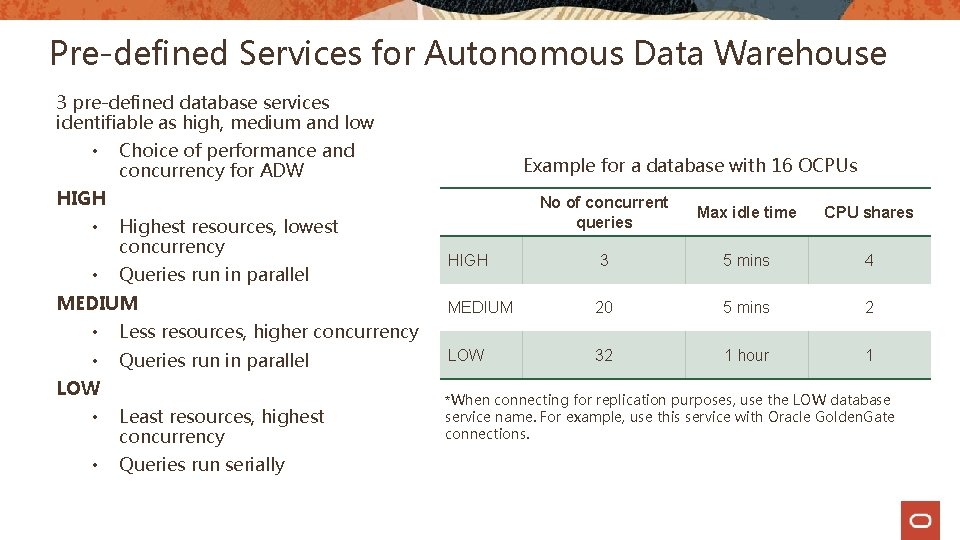
Pre-defined Services for Autonomous Data Warehouse 3 pre-defined database services identifiable as high, medium and low • Choice of performance and concurrency for ADW Example for a database with 16 OCPUs HIGH • • Highest resources, lowest concurrency Queries run in parallel MEDIUM • Less resources, higher concurrency • Queries run in parallel LOW • Least resources, highest concurrency • Queries run serially No of concurrent queries Max idle time CPU shares HIGH 3 5 mins 4 MEDIUM 20 5 mins 2 LOW 32 1 hour 1 *When connecting for replication purposes, use the LOW database service name. For example, use this service with Oracle Golden. Gate connections.

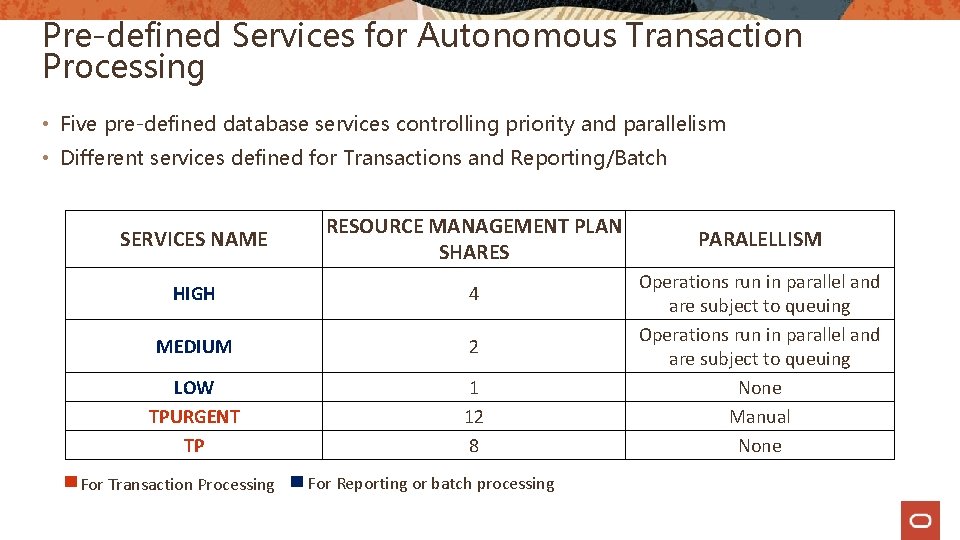
Pre-defined Services for Autonomous Transaction Processing • Five pre-defined database services controlling priority and parallelism • Different services defined for Transactions and Reporting/Batch SERVICES NAME RESOURCE MANAGEMENT PLAN SHARES HIGH 4 MEDIUM 2 LOW TPURGENT TP 1 12 8 For Transaction Processing For Reporting or batch processing PARALELLISM Operations run in parallel and are subject to queuing None Manual None

Autonomous Database - Dedicated Autonomous Data Warehouse & Autonomous Transaction Processing

Autonomous Database - Dedicated • The Autonomous Dedicated database service provides a private database cloud running on dedicated Exadata Infrastructure in the Public Cloud. • It has multiple levels of isolation protects you from noisy or hostile neighbors. • Customizable operational policies give you control of provisioning, software updates, availability and density.

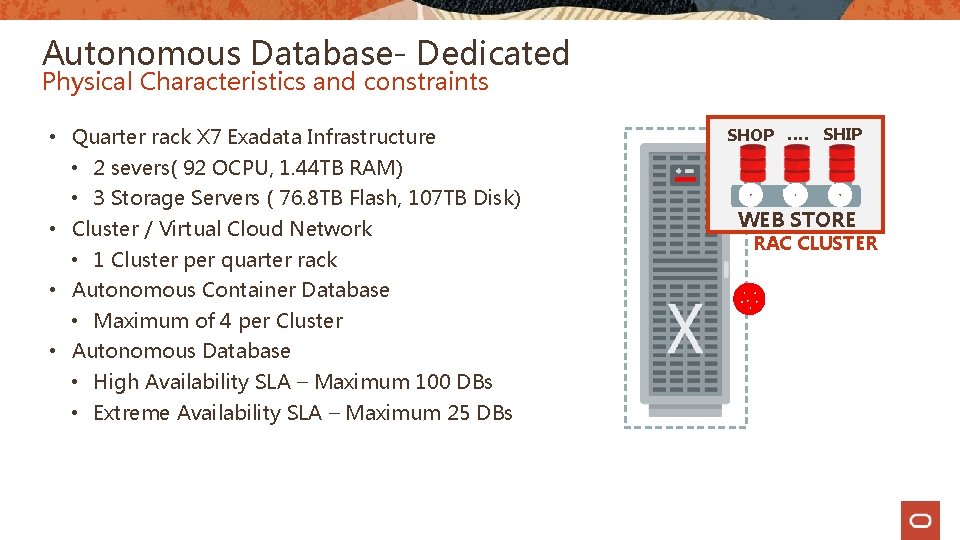
Autonomous Database- Dedicated Physical Characteristics and constraints • Quarter rack X 7 Exadata Infrastructure • 2 severs( 92 OCPU, 1. 44 TB RAM) • 3 Storage Servers ( 76. 8 TB Flash, 107 TB Disk) • Cluster / Virtual Cloud Network • 1 Cluster per quarter rack • Autonomous Container Database • Maximum of 4 per Cluster • Autonomous Database • High Availability SLA – Maximum 100 DBs • Extreme Availability SLA – Maximum 25 DBs SHOP …. SHIP WEB STORE RAC CLUSTER

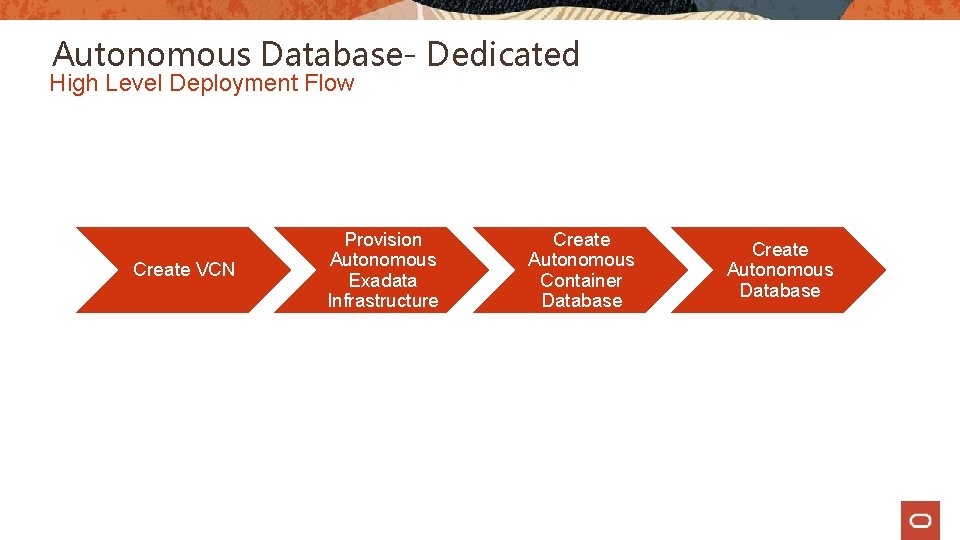
Autonomous Database- Dedicated High Level Deployment Flow Create VCN Provision Autonomous Exadata Infrastructure Create Autonomous Container Database Create Autonomous Database

Autonomous Database - Dedicated Security • • Databases always encrypted Reduced attack surface Automatic protection of customer data from Oracle operations staff Database Vault’s new Operations Control feature Oracle automatically applies security updates for the entire stack Quarterly, or off-cycle for high-impact security vulnerability Customer can separately use Database Vault for their own user data isolation

Oracle Cloud always free tier: oracle. com/cloud/free/ OCI training and certification: oracle. com/cloud/iaas/training/register-for-training. html oracle. com/cloud/iaas/training/certification. html OCI hands-on labs: ocitraining. qloudable. com/provider/oracle Oracle learning library videos on You. Tube: youtube. com/user/Oracle. Learning Copyright © 2019, Oracle and/or its affiliates. All rights reserved.