APPROVED FOR PUBLIC RELEASE U S ARMY COMBAT

APPROVED FOR PUBLIC RELEASE U. S. ARMY COMBAT CAPABILITIES DEVELOPMENT COMMAND – AVIATION & MISSILE CENTER CONTROL SYSTEMS APPROVED PRODUCTS LIST Chris Lovejoy Distribution Statement A: Approved for public release; distribution is unlimited GS-15/Computer Scientist Cyber Technologies Division 27 Feb 2019 APPROVED FOR PUBLIC RELEASE

APPROVED FOR PUBLIC RELEASE PROBLEM U. S. critical infrastructure is at risk Extensive dependency on highly vulnerable information technology and industrial control systems equals unacceptable and growing risk The threat is pervasive Virtually any actor with substantial resources can now develop or buy the capability to attack elements of U. S. critical infrastructure/Do. D warfighting facilities with cyber weapons Do. D is not postured to stop most dangerous attacks The offensive cyber capabilities of our most capable potential adversaries are likely to far exceed our ability to defend Defense Science Board 2017 Due to numerous other Do. D priorities, a low-cost or no-cost solution is needed APPROVED FOR PUBLIC RELEASE 2
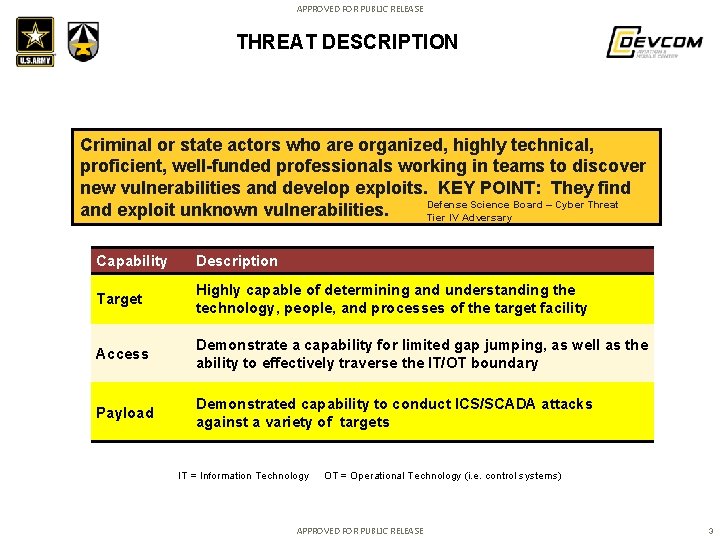
APPROVED FOR PUBLIC RELEASE THREAT DESCRIPTION Criminal or state actors who are organized, highly technical, proficient, well-funded professionals working in teams to discover new vulnerabilities and develop exploits. KEY POINT: They find Defense Science Board – Cyber Threat and exploit unknown vulnerabilities. Tier IV Adversary Capability Description Target Highly capable of determining and understanding the technology, people, and processes of the target facility Access Demonstrate a capability for limited gap jumping, as well as the ability to effectively traverse the IT/OT boundary Payload Demonstrated capability to conduct ICS/SCADA attacks against a variety of targets IT = Information Technology OT = Operational Technology (i. e. control systems) APPROVED FOR PUBLIC RELEASE 3

APPROVED FOR PUBLIC RELEASE VIGNETTE OF A PREVENTABLE CS FAILURE, EXAMPLE 1 Beginning on 23 December 2015, Ukraine lost power to 225, 000 people, and the U. S. Department of Energy, FBI, and others concluded that the outage was caused by remote cyber attackers The attackers were successful since they were able to: – Damage human-machine interface and other systems with malware, rendering them inoperable – Modify firmware on serial-to-ethernet devices at substations, causing them to not function properly – Disable control center backup power by remotely reconfiguring “uninterruptable power supplies” to fail. Do. D uses similar equipment, and these types of vulnerabilities in commercial systems would be identified and resolved by the CS APL APPROVED FOR PUBLIC RELEASE 4
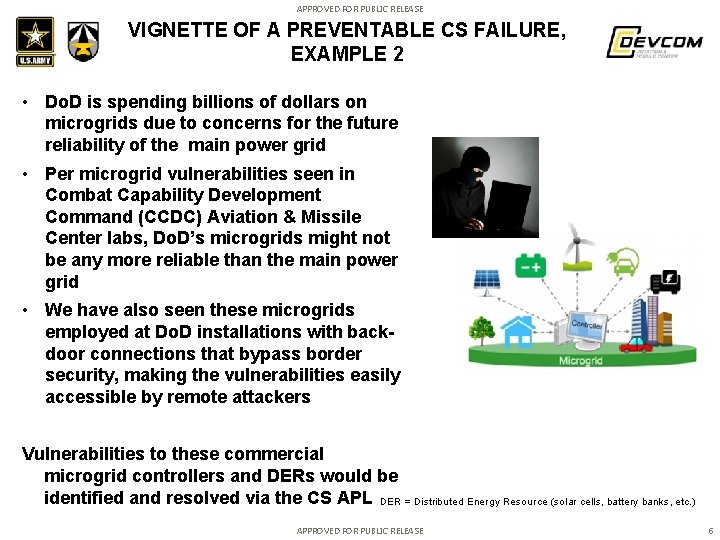
APPROVED FOR PUBLIC RELEASE VIGNETTE OF A PREVENTABLE CS FAILURE, EXAMPLE 2 • Do. D is spending billions of dollars on microgrids due to concerns for the future reliability of the main power grid • Per microgrid vulnerabilities seen in Combat Capability Development Command (CCDC) Aviation & Missile Center labs, Do. D’s microgrids might not be any more reliable than the main power grid • We have also seen these microgrids employed at Do. D installations with backdoor connections that bypass border security, making the vulnerabilities easily accessible by remote attackers Vulnerabilities to these commercial microgrid controllers and DERs would be identified and resolved via the CS APL DER = Distributed Energy Resource (solar cells, battery banks, etc. ) APPROVED FOR PUBLIC RELEASE 5
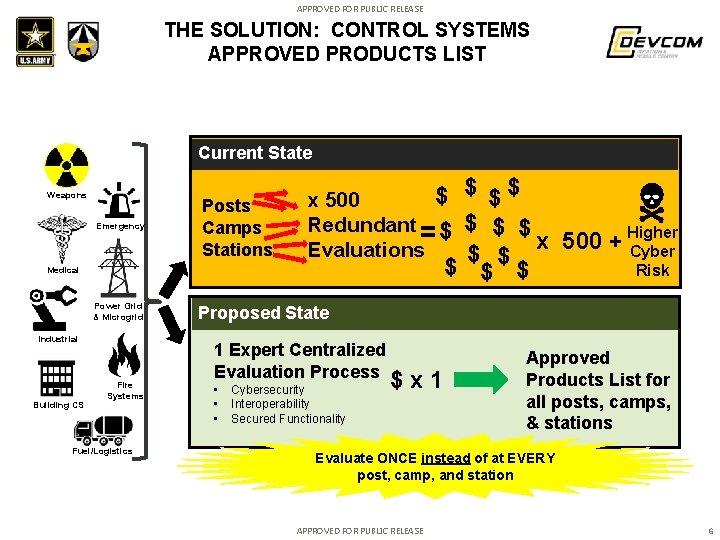
APPROVED FOR PUBLIC RELEASE THE SOLUTION: CONTROL SYSTEMS APPROVED PRODUCTS LIST Current State Weapons Emergency Posts Camps Stations Medical Power Grid & Microgrid Industrial Building CS Fire Systems Fuel/Logistics $ $ x 500 Redundant = $ $ Higher x 500 + Cyber Evaluations $ $ $ Risk Proposed State 1 Expert Centralized Evaluation Process • • • Cybersecurity Interoperability Secured Functionality $ x 1 Approved Products List for all posts, camps, & stations Evaluate ONCE instead of at EVERY post, camp, and station APPROVED FOR PUBLIC RELEASE 6
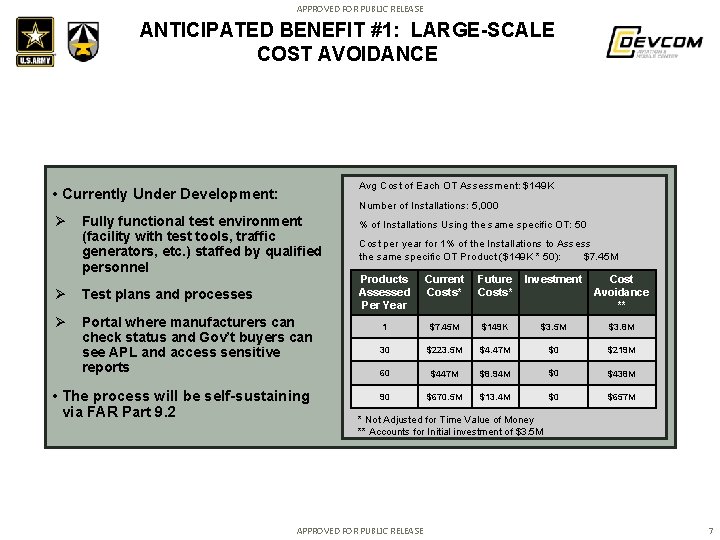
APPROVED FOR PUBLIC RELEASE ANTICIPATED BENEFIT #1: LARGE-SCALE COST AVOIDANCE Avg Cost of Each OT Assessment: $149 K • Currently Under Development: Ø Number of Installations: 5, 000 Fully functional test environment (facility with test tools, traffic generators, etc. ) staffed by qualified personnel Ø Test plans and processes Ø Portal where manufacturers can check status and Gov’t buyers can see APL and access sensitive reports • The process will be self-sustaining via FAR Part 9. 2 % of Installations Using the same specific OT: 50 Cost per year for 1% of the Installations to Assess the same specific OT Product ($149 K * 50): $7. 45 M Products Assessed Per Year Current Future Investment Costs* Cost Avoidance ** 1 $7. 45 M $149 K $3. 5 M $3. 8 M 30 $223. 5 M $4. 47 M $0 $219 M 60 $447 M $8. 94 M $0 $438 M 90 $670. 5 M $13. 4 M $0 $657 M * Not Adjusted for Time Value of Money ** Accounts for Initial investment of $3. 5 M APPROVED FOR PUBLIC RELEASE 7

APPROVED FOR PUBLIC RELEASE ANTICIPATED BENEFIT #2: MASSIVE IMPROVEMENT TO CYBERSECURITY FOR OUR NATION’S SENSITIVE UNDERBELLY Qualified test and assessment team – Garrisons and others have not been equipped to deal with the recent trend of connecting devices that have historically not been connected (e. g. “industrial internet of things”), so cybersecurity has either not properly been addressed, or not addressed at all – An expert team that knows how to test, assess, and secure control systems fills this gaping void Easy to use, and desired by numerous Do. D and other Federal organizations and CS manufacturers, so benefits will be achieved APPROVED FOR PUBLIC RELEASE 8

APPROVED FOR PUBLIC RELEASE STAKEHOLDERS CURRENTLY INVOLVED IN DEVELOPMENT OF THE PROCESS: APPROVED FOR PUBLIC RELEASE 9

APPROVED FOR PUBLIC RELEASE PROGRAM INCEPTION AND DEVELOPMENT • OASD, Energy and the Combat Capability Development Command (CCDC) Aviation & Missile Center conceived the program, and CCDC Aviation & Missile Center has been provided Do. D Reform start-up funds to develop the program • The aggressive program development is on schedule • Key CS APL dates: • Initial Operating Capability: 15 Dec 18 • Full Operational Capability: 8 Apr 19 Numerous Federal departments eagerly await the CS APL, and manufacturers are eager to participate APPROVED FOR PUBLIC RELEASE 10

APPROVED FOR PUBLIC RELEASE GRASSROOTS DEVELOPMENT • In addition to the CCDC Aviation & Missile Center’s efforts, a 98 -person group of participants from across the Do. D and the Federal Government meets every two months to discuss status • Tiger Teams meet twice a week to work through key challenges to ensure a program is developed that meets the needs of all Do. D and Federal Government organizations • Tiger team participants include volunteers from: • • • Army Navy Air Force Marine Corps Do. D Chief Information Office • Defense Information Systems Agency • Coast Guard • Washington Headers Services • General Services Administration • National Security Agency Numerous Federal departments eagerly await the CS APL, and manufacturers have said they are eager to participate APPROVED FOR PUBLIC RELEASE 11
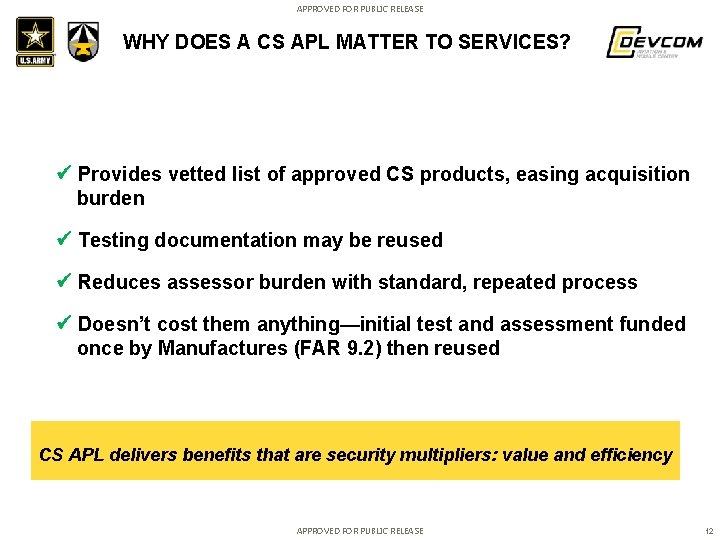
APPROVED FOR PUBLIC RELEASE WHY DOES A CS APL MATTER TO SERVICES? Provides vetted list of approved CS products, easing acquisition burden Testing documentation may be reused Reduces assessor burden with standard, repeated process Doesn’t cost them anything—initial test and assessment funded once by Manufactures (FAR 9. 2) then reused CS APL delivers benefits that are security multipliers: value and efficiency APPROVED FOR PUBLIC RELEASE 12
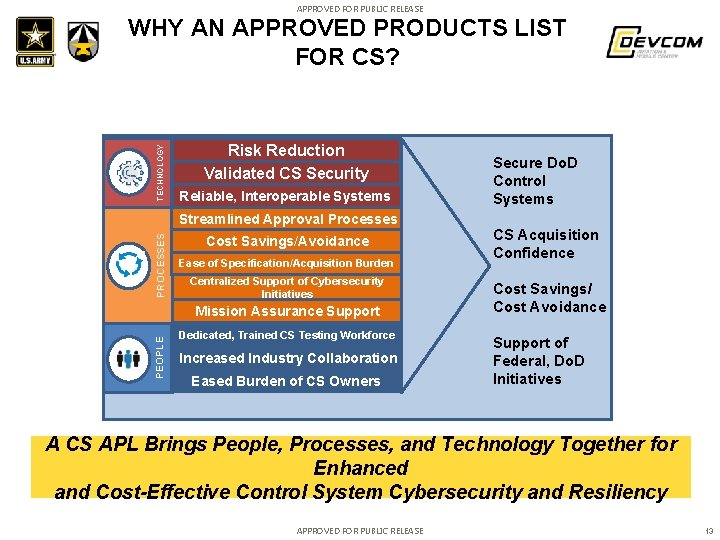
APPROVED FOR PUBLIC RELEASE TECHNOLOGY WHY AN APPROVED PRODUCTS LIST FOR CS? Risk Reduction Validated CS Security Reliable, Interoperable Systems PROCESSES Streamlined Approval Processes Cost Savings/Avoidance Ease of Specification/Acquisition Burden Centralized Support of Cybersecurity Initiatives PEOPLE Mission Assurance Support Dedicated, Trained CS Testing Workforce Increased Industry Collaboration Eased Burden of CS Owners Secure Do. D Control Systems CS Acquisition Confidence Cost Savings/ Cost Avoidance Support of Federal, Do. D Initiatives A CS APL Brings People, Processes, and Technology Together for Enhanced and Cost-Effective Control System Cybersecurity and Resiliency APPROVED FOR PUBLIC RELEASE 13
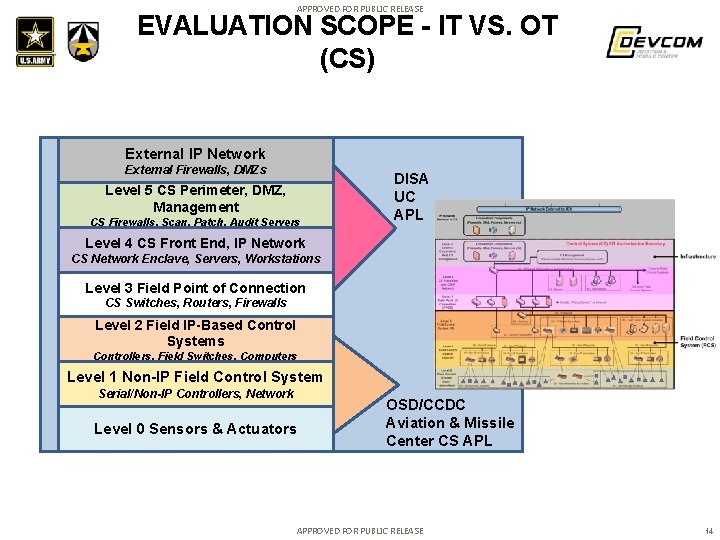
APPROVED FOR PUBLIC RELEASE EVALUATION SCOPE - IT VS. OT (CS) External IP Network External Firewalls, DMZs Level 5 CS Perimeter, DMZ, Management CS Firewalls, Scan, Patch, Audit Servers DISA UC APL Level 4 CS Front End, IP Network CS Network Enclave, Servers, Workstations Level 3 Field Point of Connection CS Switches, Routers, Firewalls Level 2 Field IP-Based Control Systems Controllers, Field Switches, Computers Level 1 Non-IP Field Control System Serial/Non-IP Controllers, Network Level 0 Sensors & Actuators OSD/CCDC Aviation & Missile Center CS APL APPROVED FOR PUBLIC RELEASE 14
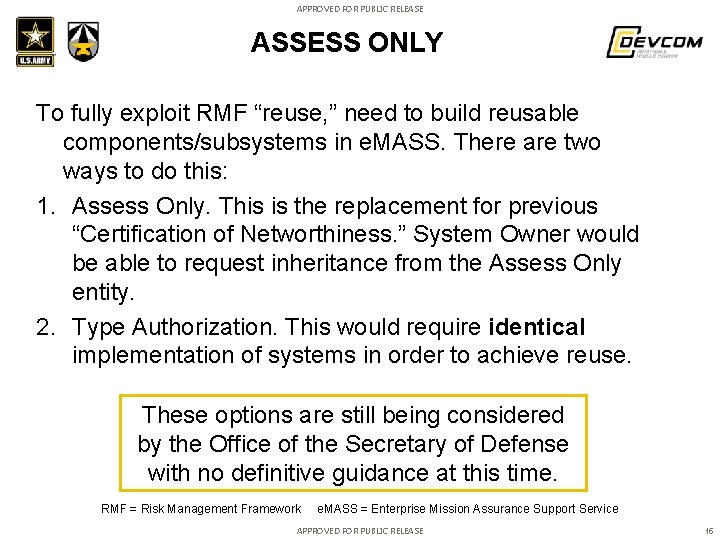
APPROVED FOR PUBLIC RELEASE ASSESS ONLY To fully exploit RMF “reuse, ” need to build reusable components/subsystems in e. MASS. There are two ways to do this: 1. Assess Only. This is the replacement for previous “Certification of Networthiness. ” System Owner would be able to request inheritance from the Assess Only entity. 2. Type Authorization. This would require identical implementation of systems in order to achieve reuse. These options are still being considered by the Office of the Secretary of Defense with no definitive guidance at this time. RMF = Risk Management Framework e. MASS = Enterprise Mission Assurance Support Service APPROVED FOR PUBLIC RELEASE 15

APPROVED FOR PUBLIC RELEASE WHAT ELSE DO MANUFACTURERS NEED TO KNOW? • Test and assessments to be funded by manufactures via FAR Part 9. 2—start budgeting now (costs to be announced later) • Comply with applicable NIST requirements (e. g. SP 80053) as a baseline • Planned start for test and assessment: 8 April 2019 • More information coming. Possible distribution channels include: • www. fbo. gov • www. cs-apl. com • www. serdp-estcp. org APPROVED FOR PUBLIC RELEASE 16

APPROVED FOR PUBLIC RELEASE CONCLUSION The CS APL will reduce RMF costs while also increasing security Do. D and other Federal organizations are helping to develop it and are eager for it Manufacturers are eager to participate (and fund it) CS APL will be self-sustaining, though funding a PMO will save even more cost and will fill the second gaping cybersecurity hole of not knowing where control system equipment is located Massive Cost Avoidance AND Massive Cybersecurity Improvements APPROVED FOR PUBLIC RELEASE 17

APPROVED FOR PUBLIC RELEASE QUESTIONS? There will be a CS APL table in the lobby for the rest of the day. Please stop by if you have remaining questions. APPROVED FOR PUBLIC RELEASE 18
APPROVED FOR PUBLIC RELEASE Web Site www. amrdec. army. mil Facebook www. facebook. com/rdecom. amrdec Instagram www. instagram. com/USARMYAMRDEC Twitter @usarmyamrdec Public Affairs usarmy. redstone. rdecom-amrdec. mbx. pao@mail. mil APPROVED FOR PUBLIC RELEASE 19
- Slides: 19