Applying Support Vector Machines for Intrusion Detection on

![References [1] R. Bace and P. Mell. Intrusion Detection Systems. NIST Special Publications SP References [1] R. Bace and P. Mell. Intrusion Detection Systems. NIST Special Publications SP](https://slidetodoc.com/presentation_image_h2/106aa227d723c551179ad55da22d5ce4/image-38.jpg)
- Slides: 38

Applying Support Vector Machines for Intrusion Detection on Virtual Machines Lecture 6 John Cavazos Dept of Computer & Information Sciences University of Delaware www. cis. udel. edu/~cavazos/cisc 879 CISC 879 - Machine Learning for Solving Systems Problems

Outline ► Background and Motivation ► Intrusion Detection Systems ► Support Vector Machines (SVMs) ► Dataset ► Results ► Conclusions Slides adapted from presentation by Fatemeh Azmandian (http: //www. ece. neu. edu/~fazmandi) CISC 879 - Machine Learning for Solving Systems Problems

Background ► Virtual Machine: ► ► A software implementation of a machine (computer) that executes programs like a real machine Virtual Machine Monitor (VMM) or hypervisor: ► ► The software layer providing the virtualization Allows the multiplexing of the underlying physical machine between different virtual machines, each running its own operating system CISC 879 - Machine Learning for Solving Systems Problems

Background (cont’d) ► Intrusion Detection: ► ► The process of monitoring the events occurring in a computer system or network and analyzing them for signs of intrusions Intrusion: ► ► An attempt to compromise: ► Confidentiality ► Integrity ► Availability An attempt to bypass the security mechanisms of a computer or network [1] CISC 879 - Machine Learning for Solving Systems Problems

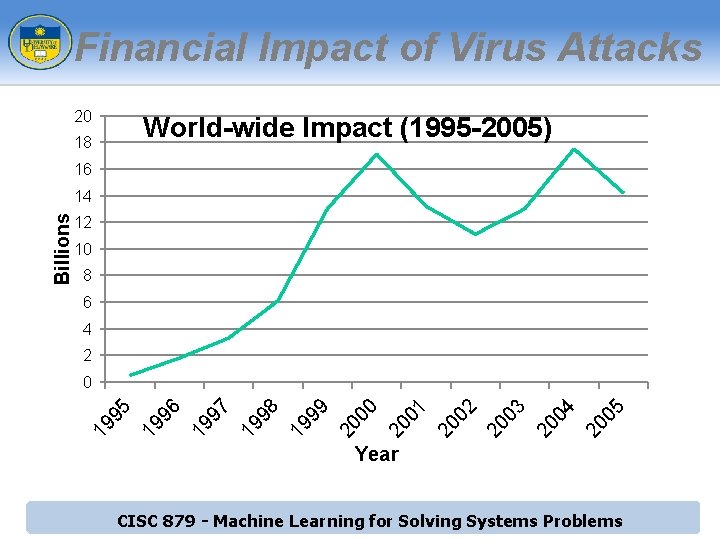
Background (cont’d) ► Intrusion Detection System (IDS): ► ► Software or hardware system that automates the process of monitoring the events occurring in a computer system or network, analyzing them for signs of security problems Why is it important? ► Every year, billions of dollars are lost due to virus attacks CISC 879 - Machine Learning for Solving Systems Problems

Financial Impact of Virus Attacks 20 World-wide Impact (1995 -2005) 18 16 12 10 8 6 4 2 05 20 04 20 03 20 02 20 01 20 00 20 99 19 98 19 97 19 19 96 0 19 95 Billions 14 Year CISC 879 - Machine Learning for Solving Systems Problems

Intrusion Detection Approaches ► Misuse Detection ► ► ► Identifies intrusions based on known patterns for the malicious activity Known patterns are referred to as signatures Anomaly Detection ► ► ► Identifies intrusions based on deviations from established normal behavior Capable of identifying new (previously unseen) attacks New normal behavior may be misclassified as abnormal, producing false positives CISC 879 - Machine Learning for Solving Systems Problems

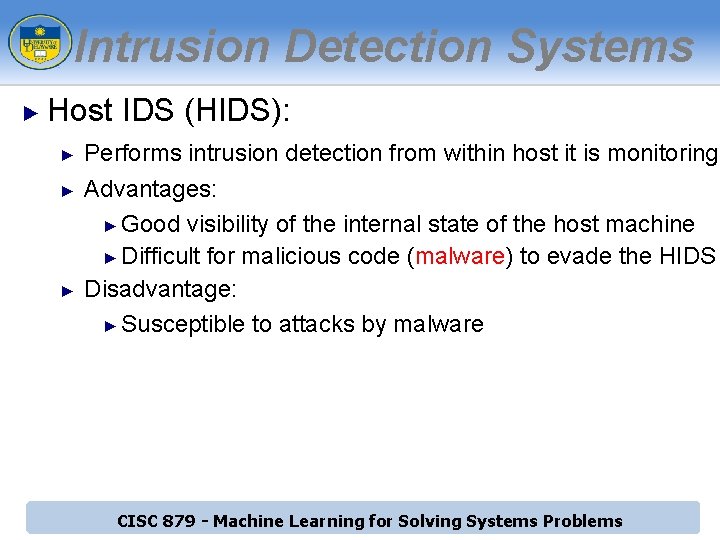
Intrusion Detection Systems ► Host IDS (HIDS): ► ► ► Performs intrusion detection from within host it is monitoring Advantages: ► Good visibility of the internal state of the host machine ► Difficult for malicious code (malware) to evade the HIDS Disadvantage: ► Susceptible to attacks by malware CISC 879 - Machine Learning for Solving Systems Problems

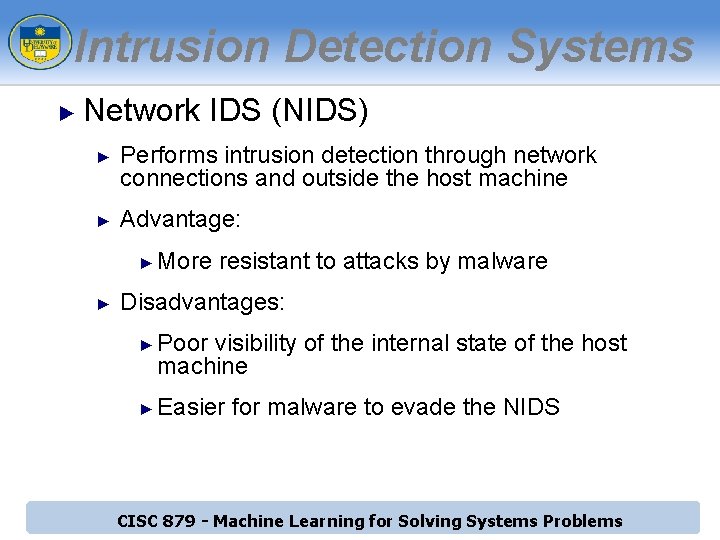
Intrusion Detection Systems ► Network IDS (NIDS) ► ► Performs intrusion detection through network connections and outside the host machine Advantage: ► ► More resistant to attacks by malware Disadvantages: ► ► Poor visibility of the internal state of the host machine Easier for malware to evade the NIDS CISC 879 - Machine Learning for Solving Systems Problems

Intrusion Detection Systems ► VMM-based IDS: ► ► Performs intrusion detection for a virtual machine through the Virtual Machine Monitor (VMM) Advantages: Better visibility of the internal state of the host machine, compared to an NIDS ► Harder for malware to evade the IDS ► Less susceptible to attacks by malware ► ► Our goal is to create a VMM-based IDS using machine learning techniques ► Support Vector Machines (SVMs) CISC 879 - Machine Learning for Solving Systems Problems

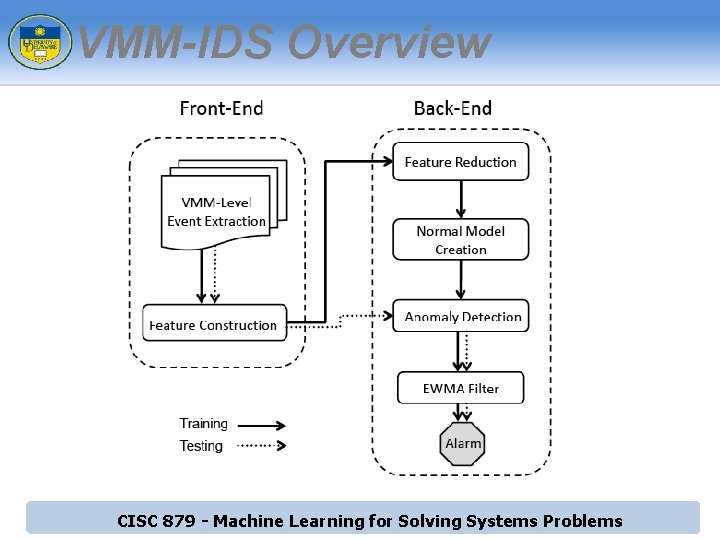
VMM-IDS Overview CISC 879 - Machine Learning for Solving Systems Problems

Support Vector Machines (SVMs) ► Machine learning to classify data points into one of two classes ► Two-Class SVMs ► ► Training is done on data from two classes One-Class SVMs ► ► Training is done on data from only one class During the testing phase, the origin and data points close to it are considered part of the second class CISC 879 - Machine Learning for Solving Systems Problems

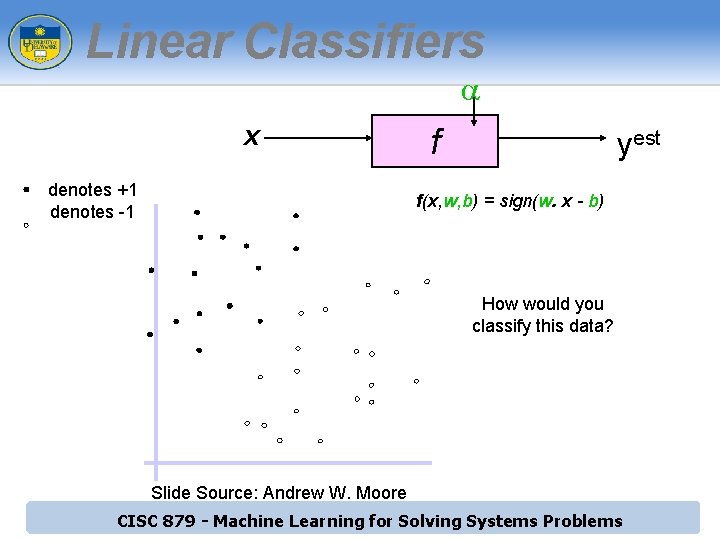
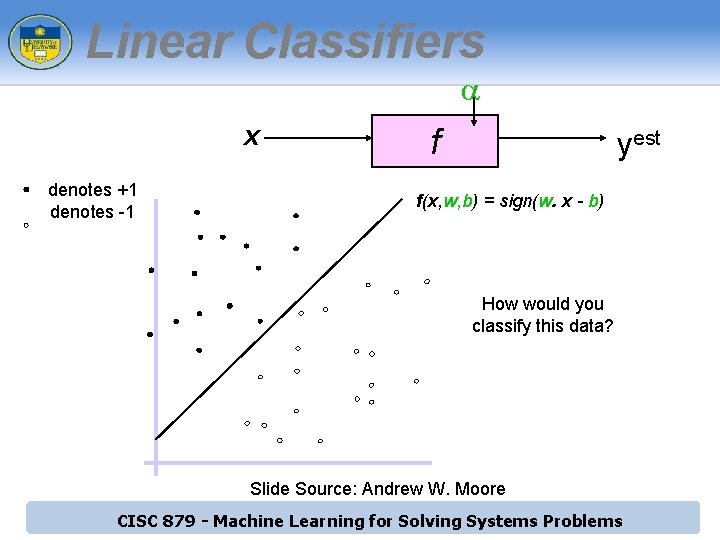
Linear Classifiers a x denotes +1 denotes -1 f yest f(x, w, b) = sign(w. x - b) How would you classify this data? Slide Source: Andrew W. Moore CISC 879 - Machine Learning for Solving Systems Problems

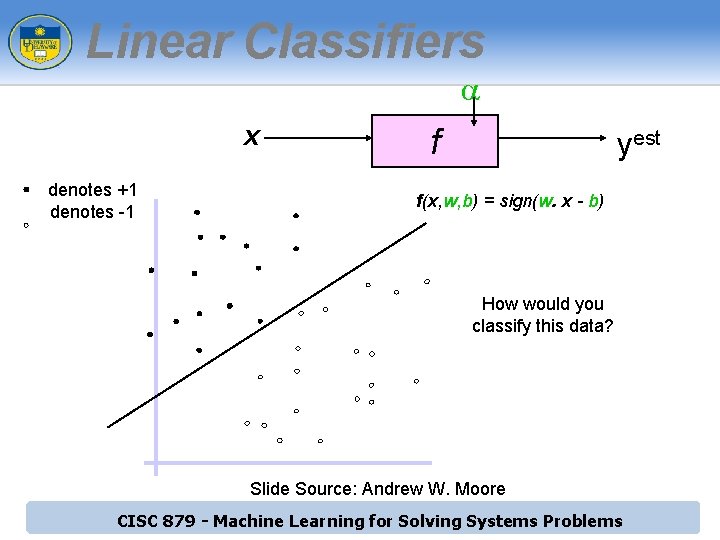
Linear Classifiers a x denotes +1 denotes -1 f yest f(x, w, b) = sign(w. x - b) How would you classify this data? Slide Source: Andrew W. Moore CISC 879 - Machine Learning for Solving Systems Problems

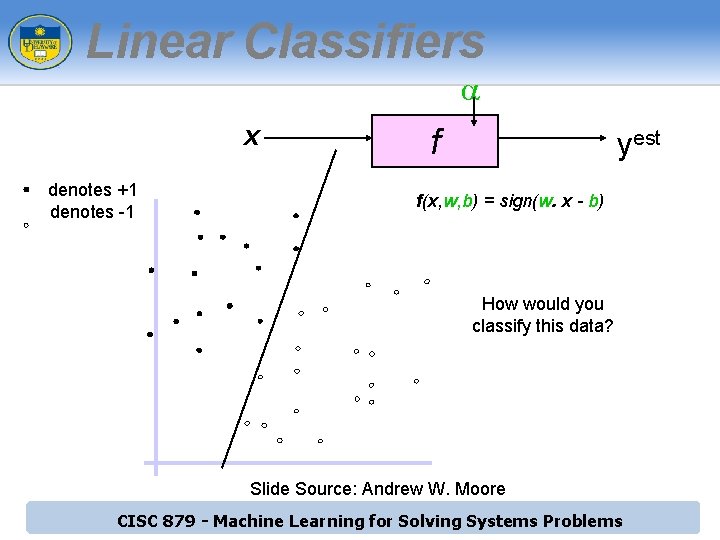
Linear Classifiers a x denotes +1 denotes -1 f yest f(x, w, b) = sign(w. x - b) How would you classify this data? Slide Source: Andrew W. Moore CISC 879 - Machine Learning for Solving Systems Problems

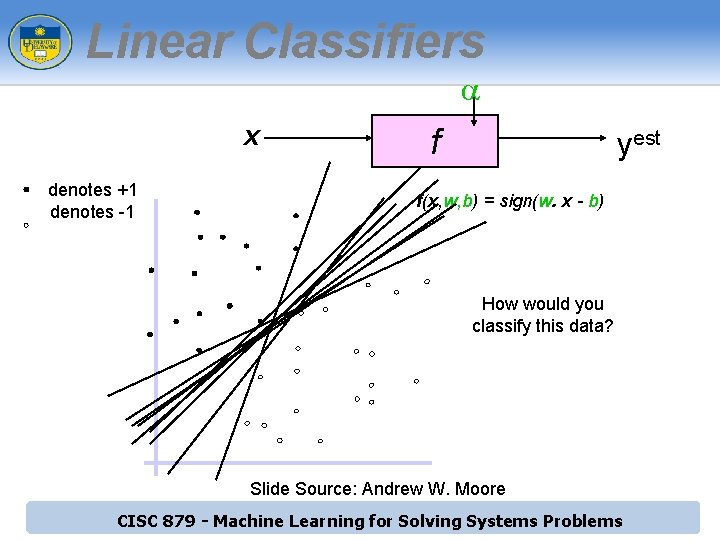
Linear Classifiers a x denotes +1 denotes -1 f yest f(x, w, b) = sign(w. x - b) How would you classify this data? Slide Source: Andrew W. Moore CISC 879 - Machine Learning for Solving Systems Problems

Linear Classifiers a x denotes +1 denotes -1 f yest f(x, w, b) = sign(w. x - b) How would you classify this data? Slide Source: Andrew W. Moore CISC 879 - Machine Learning for Solving Systems Problems

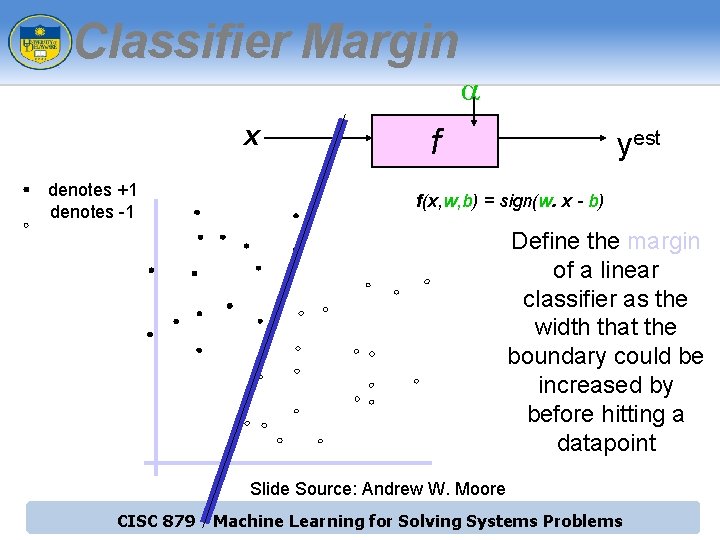
Classifier Margin a x denotes +1 denotes -1 f yest f(x, w, b) = sign(w. x - b) Define the margin of a linear classifier as the width that the boundary could be increased by before hitting a datapoint Slide Source: Andrew W. Moore CISC 879 - Machine Learning for Solving Systems Problems

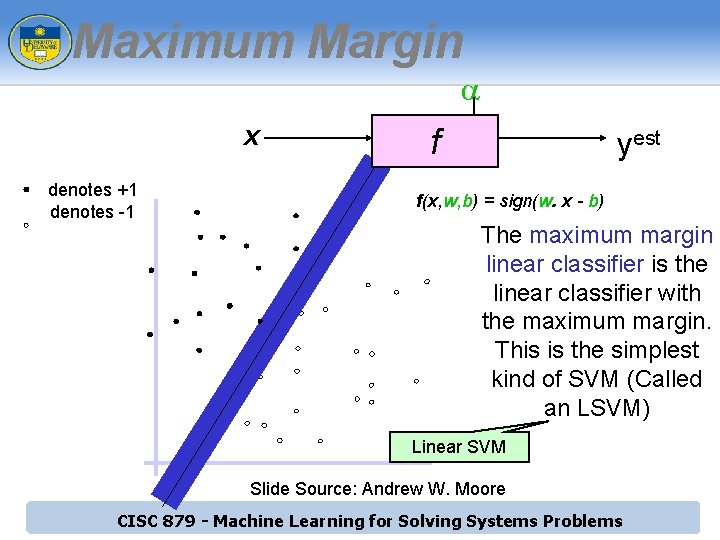
Maximum Margin a x denotes +1 denotes -1 f yest f(x, w, b) = sign(w. x - b) The maximum margin linear classifier is the linear classifier with the maximum margin. This is the simplest kind of SVM (Called an LSVM) Linear SVM Slide Source: Andrew W. Moore CISC 879 - Machine Learning for Solving Systems Problems

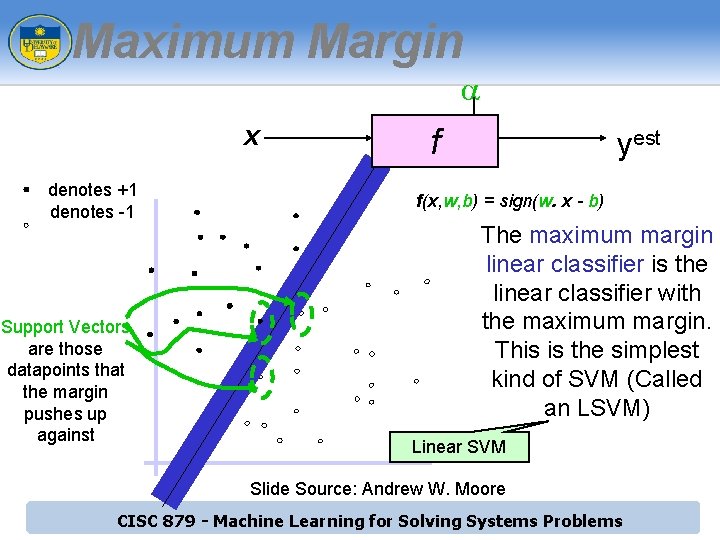
Maximum Margin a x denotes +1 denotes -1 Support Vectors are those datapoints that the margin pushes up against f yest f(x, w, b) = sign(w. x - b) The maximum margin linear classifier is the linear classifier with the maximum margin. This is the simplest kind of SVM (Called an LSVM) Linear SVM Slide Source: Andrew W. Moore CISC 879 - Machine Learning for Solving Systems Problems

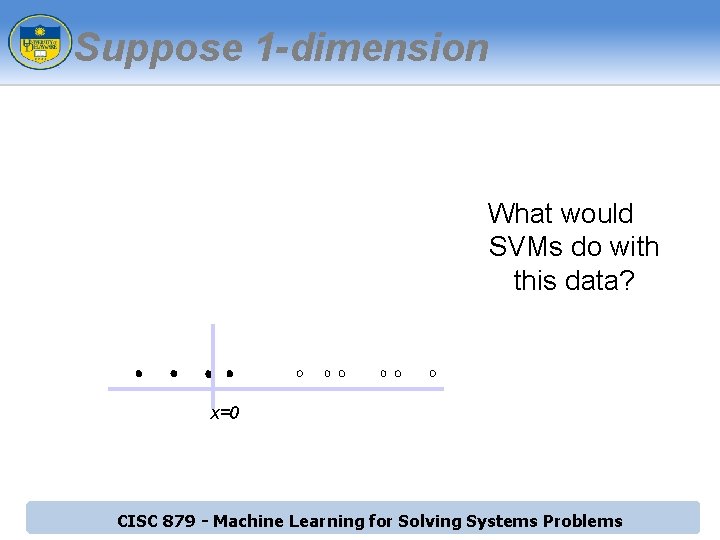
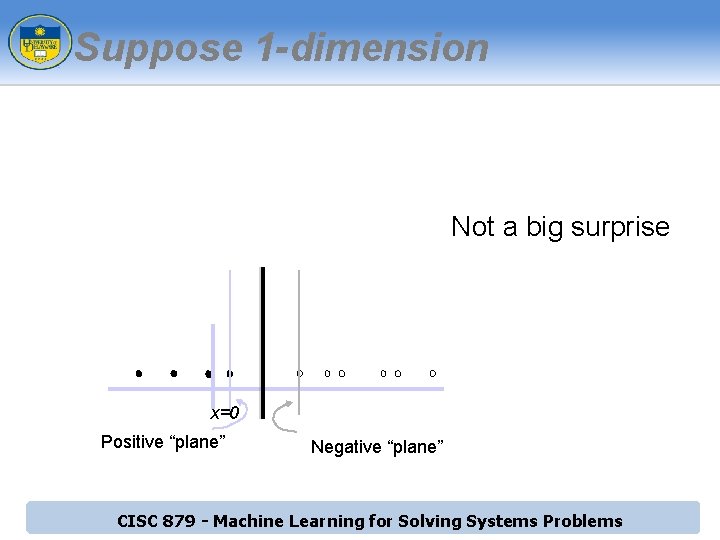
Suppose 1 -dimension What would SVMs do with this data? x=0 CISC 879 - Machine Learning for Solving Systems Problems

Suppose 1 -dimension Not a big surprise x=0 Positive “plane” Negative “plane” CISC 879 - Machine Learning for Solving Systems Problems

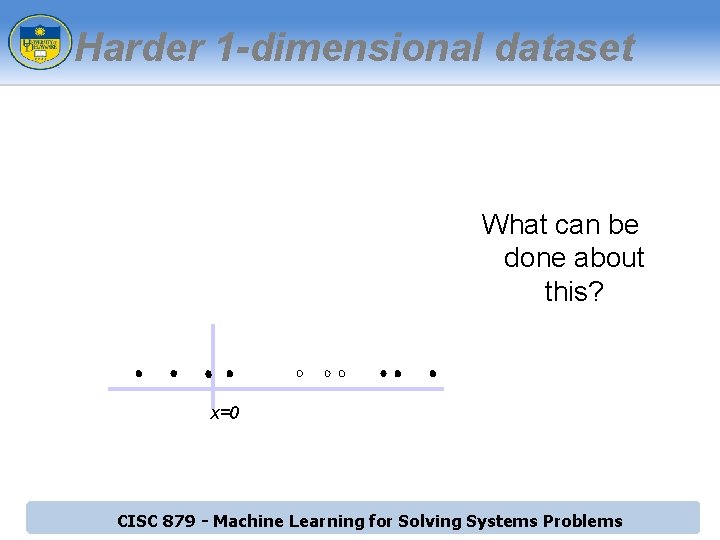
Harder 1 -dimensional dataset What can be done about this? x=0 CISC 879 - Machine Learning for Solving Systems Problems

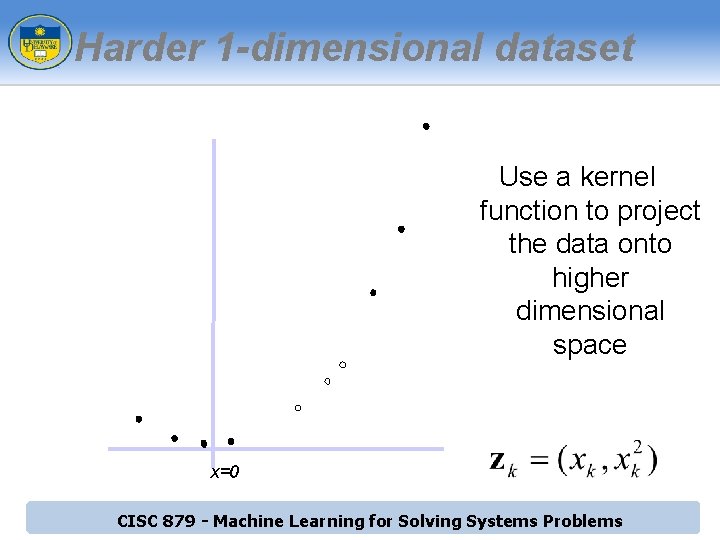
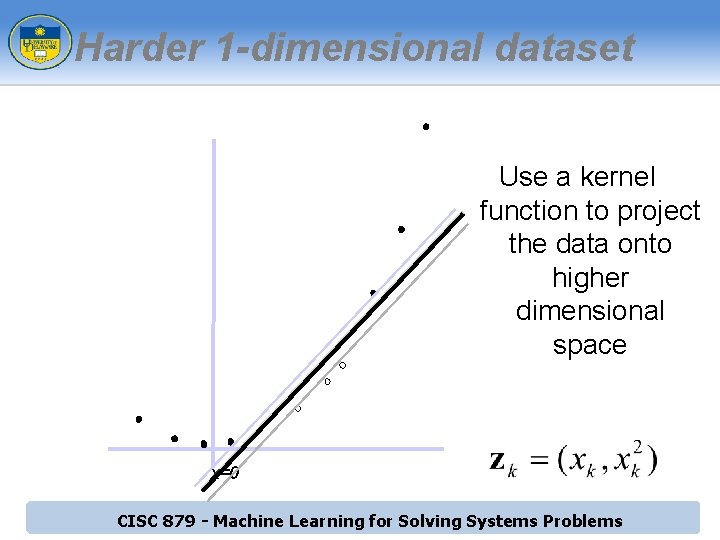
Harder 1 -dimensional dataset Use a kernel function to project the data onto higher dimensional space x=0 CISC 879 - Machine Learning for Solving Systems Problems

Harder 1 -dimensional dataset Use a kernel function to project the data onto higher dimensional space x=0 CISC 879 - Machine Learning for Solving Systems Problems

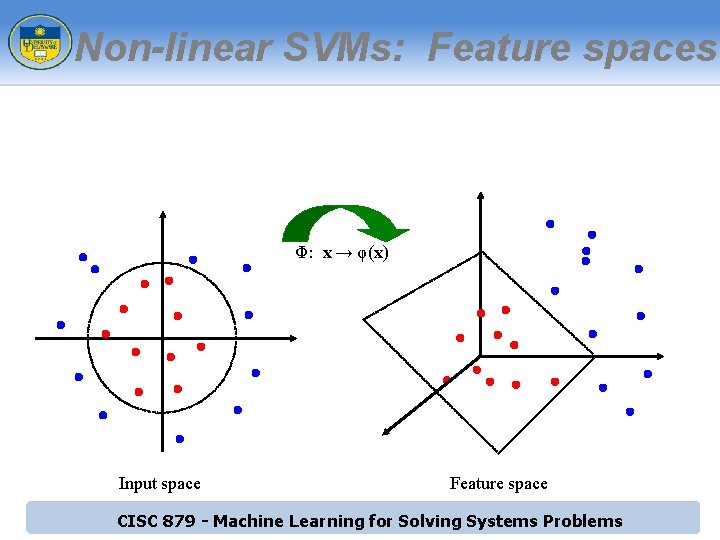
Non-linear SVMs: Feature spaces Φ: x → φ(x) Input space Feature space CISC 879 - Machine Learning for Solving Systems Problems

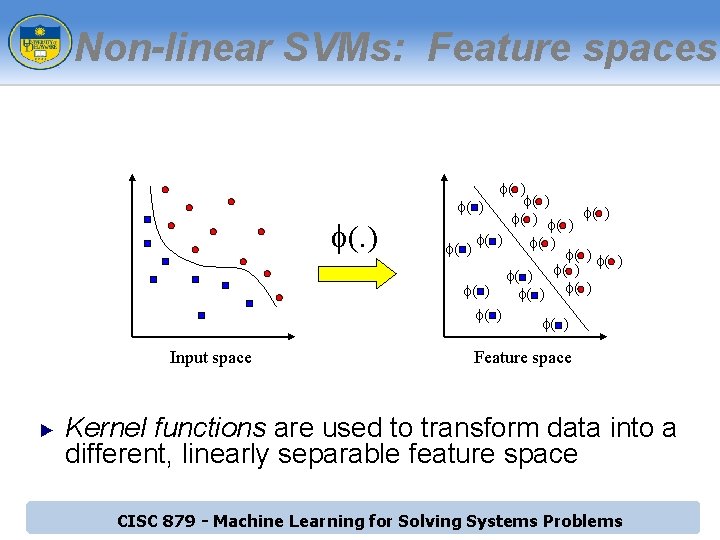
Non-linear SVMs: Feature spaces f(. ) Input space ► f( ) f( ) f( ) f( ) f( ) Feature space Kernel functions are used to transform data into a different, linearly separable feature space CISC 879 - Machine Learning for Solving Systems Problems

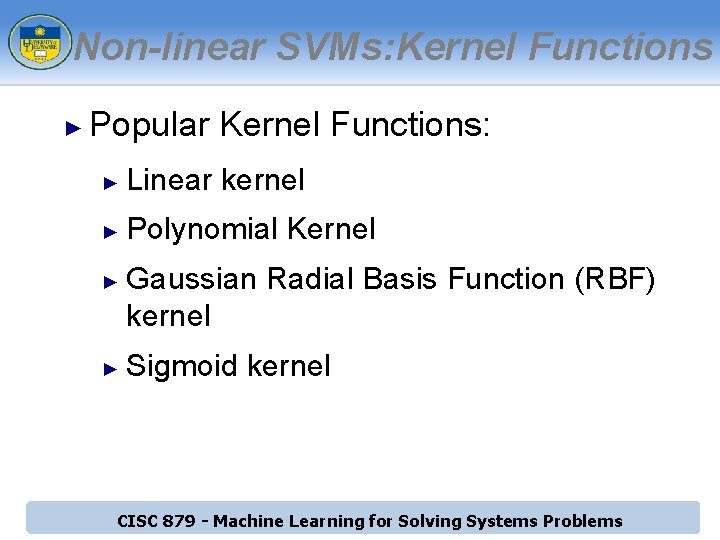
Non-linear SVMs: Kernel Functions ► Popular Kernel Functions: ► Linear kernel ► Polynomial Kernel ► ► Gaussian Radial Basis Function (RBF) kernel Sigmoid kernel CISC 879 - Machine Learning for Solving Systems Problems

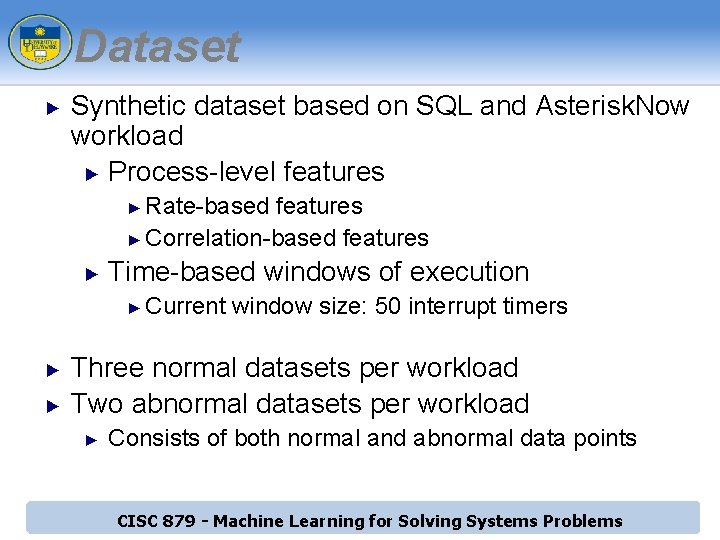
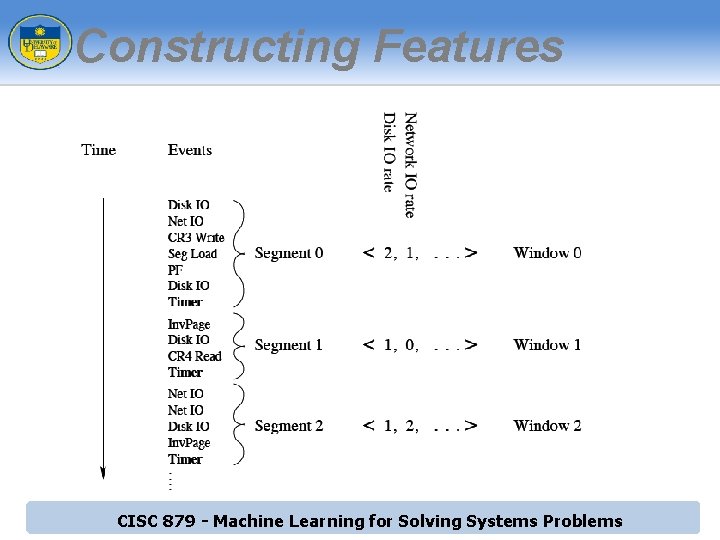
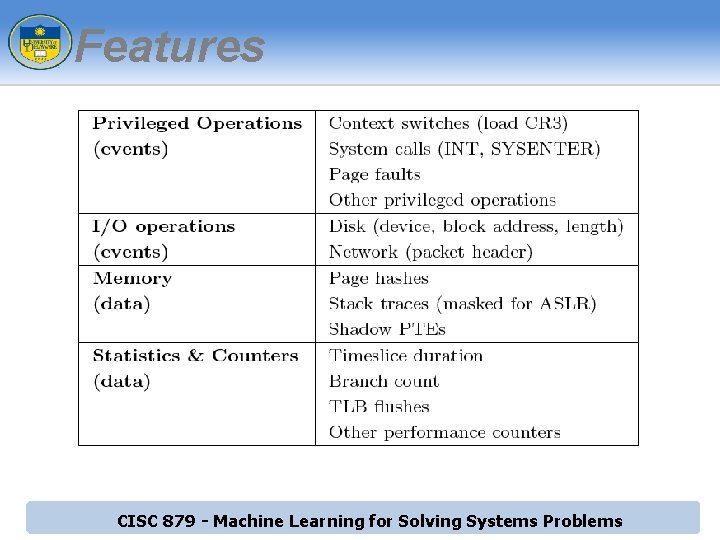
Dataset ► Synthetic dataset based on SQL and Asterisk. Now workload ► Process-level features Rate-based features ► Correlation-based features ► ► Time-based windows of execution ► ► ► Current window size: 50 interrupt timers Three normal datasets per workload Two abnormal datasets per workload ► Consists of both normal and abnormal data points CISC 879 - Machine Learning for Solving Systems Problems

Constructing Features CISC 879 - Machine Learning for Solving Systems Problems

Features CISC 879 - Machine Learning for Solving Systems Problems

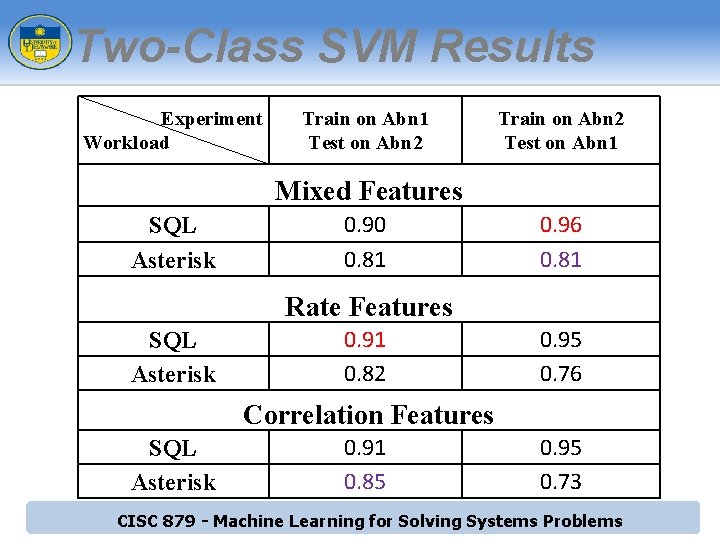
Two-Class SVM Results Experiment Workload Train on Abn 1 Test on Abn 2 Train on Abn 2 Test on Abn 1 Mixed Features SQL Asterisk 0. 90 0. 81 0. 96 0. 81 Rate Features SQL Asterisk 0. 91 0. 82 0. 95 0. 76 Correlation Features SQL Asterisk 0. 91 0. 85 0. 95 0. 73 CISC 879 - Machine Learning for Solving Systems Problems

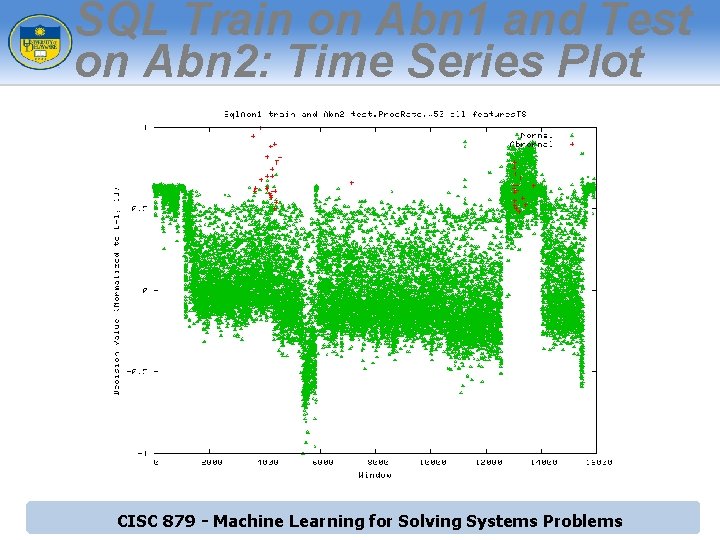
SQL Train on Abn 1 and Test on Abn 2: Time Series Plot CISC 879 - Machine Learning for Solving Systems Problems

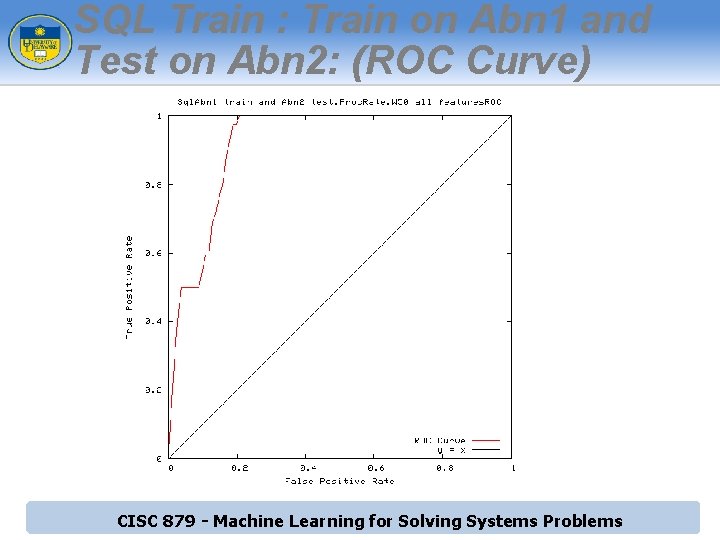
SQL Train : Train on Abn 1 and Test on Abn 2: (ROC Curve) CISC 879 - Machine Learning for Solving Systems Problems

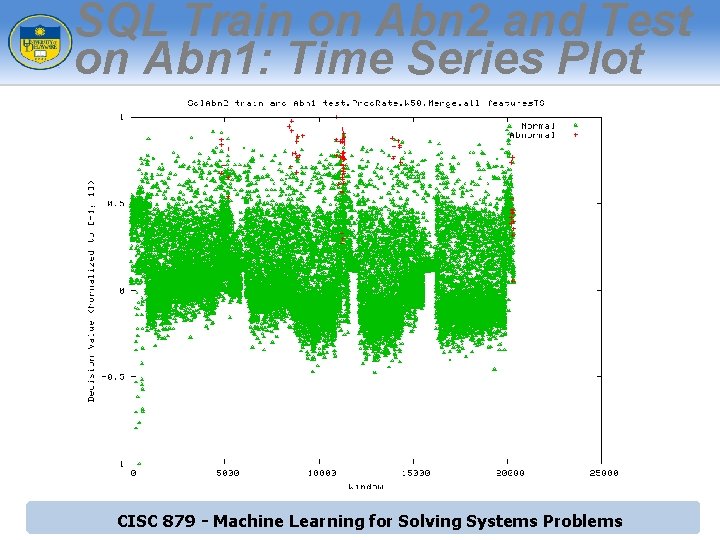
SQL Train on Abn 2 and Test on Abn 1: Time Series Plot CISC 879 - Machine Learning for Solving Systems Problems

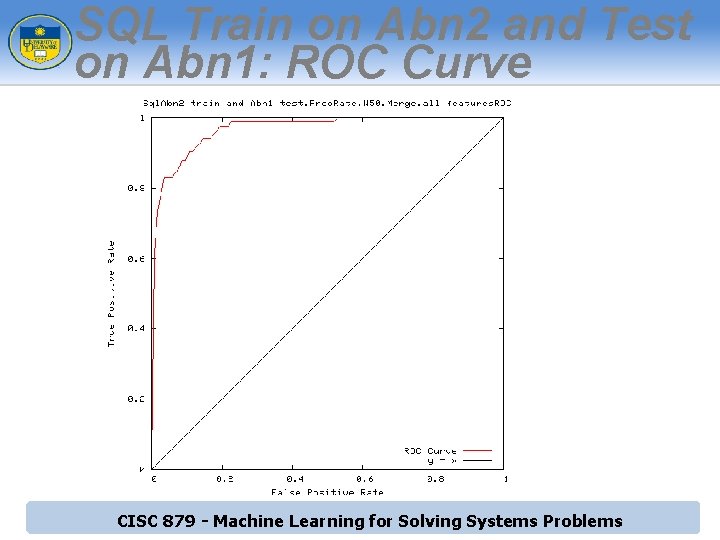
SQL Train on Abn 2 and Test on Abn 1: ROC Curve CISC 879 - Machine Learning for Solving Systems Problems

Conclusions ► ► Two-class SVM can perform well in detecting intrusions in virtual machine environments Goal to develop accurate intrusion detection system for VMs based on machine learning techniques CISC 879 - Machine Learning for Solving Systems Problems
![References 1 R Bace and P Mell Intrusion Detection Systems NIST Special Publications SP References [1] R. Bace and P. Mell. Intrusion Detection Systems. NIST Special Publications SP](https://slidetodoc.com/presentation_image_h2/106aa227d723c551179ad55da22d5ce4/image-38.jpg)
References [1] R. Bace and P. Mell. Intrusion Detection Systems. NIST Special Publications SP 80031, November, 2001. [2] T. Garfinkel and M. Rosenblum. A Virtual Machine Introspection Based Architecture for Intrusion Detection. Proceedings of the Network and Distributed Systems Security Symposium, 2003. [3] Andrew Moore’s slides on Support Vector Machines http: //www. cs. cmu. edu/~awm/tutorials [4] Prasad’s slides on Support Vector Machines www. cs. wright. edu/~tkprasad/courses/cs 499/L 18 SVM. ppt [5] 2005 Malware Report: Executive Summary http: //www. computereconomics. com/article. cfm? id=1090 [6] Virtual Machine http: //en. wikipedia. org/wiki/Virtual_machine CISC 879 - Machine Learning for Solving Systems Problems