Applying MESE processes to Improve Online EVoting Prototype









![Cryptographic Techniques Implemented by Brett Wilson to PTC Web Services Paillier Crypto. System [15] Cryptographic Techniques Implemented by Brett Wilson to PTC Web Services Paillier Crypto. System [15]](https://slidetodoc.com/presentation_image_h/b299530e9d7eb4d808d24a06618ce021/image-12.jpg)
![Cryptographic Techniques Implemented Threshold Encryption [15] ◦ Public key encryption as usual ◦ Distribute Cryptographic Techniques Implemented Threshold Encryption [15] ◦ Public key encryption as usual ◦ Distribute](https://slidetodoc.com/presentation_image_h/b299530e9d7eb4d808d24a06618ce021/image-13.jpg)
![Operation of E-Voting System [15] 2. SOAP/XML Request for PTC Parameters Hakan Evecek/SE 2 Operation of E-Voting System [15] 2. SOAP/XML Request for PTC Parameters Hakan Evecek/SE 2](https://slidetodoc.com/presentation_image_h/b299530e9d7eb4d808d24a06618ce021/image-14.jpg)



![References [1] http: //cris. joongbu. ac. kr/publication/evoting_implementation-APIEMS 2004. pdf Implementation issues in a secure References [1] http: //cris. joongbu. ac. kr/publication/evoting_implementation-APIEMS 2004. pdf Implementation issues in a secure](https://slidetodoc.com/presentation_image_h/b299530e9d7eb4d808d24a06618ce021/image-28.jpg)
- Slides: 28

Applying MESE processes to Improve Online E-Voting Prototype System with PTC Web Services Master Project Defense Hakan Evecek 5/29/2007 Hakan Evecek/SE 2 Evote 1

Outline of the Talk Introduction Document overview prepared for this project. Related Work Paillier Threshold Cryptography (PTC) PTC Web Services Online E-Voting System Suggested Improvement ◦ Encryption/Decryption Optimization ◦ User Interface Future Directions Conclusion 5/29/2007 Hakan Evecek/SE 2 Evote 2

Introduction The online E-Voting system generated within this project was based on an idea put forward in the ‘Future Suggestions’ section of the Master’s Thesis of Mr. Brett Wilson. (http: //cs. uccs. edu/~gsc/pub/master/bswilson/doc/) As a result, augmentation of the demo application for PTC Web Services was undertaken. 5/29/2007 Hakan Evecek/SE 2 Evote 3

Continued… Scope of E-Voting: The world is heading in this direction as currently many nations and large companies are seeking EVoting solutions. ◦ Similar to manual voting - only much faster and cheaper, however Is the voter confident with the process? Can Administrators monitoring verify that one vote is recorded for each voter? How trustable is the tally process? Is it socially acceptable? 5/29/2007 Hakan Evecek/SE 2 Evote 4

E-Voting Requirements • Basic requirements for electronic voting • Privacy – All votes should be kept secret • Completeness – All valid votes should be counted correctly • Soundness – Any invalid vote should not be counted • Unreusability – No voter can vote twice • Eligibility – Only authorized voters can cast a vote • Fairness – Nothing can affect the voting 5/29/2007 Hakan Evecek/SE 2 Evote 5

E-Voting Requirements • Extended Requirements for electronic voting • Robustness – faulty behavior of any reasonably sized coalition of participants can be tolerated. In other words, the system must be able to tolerate to certain faulty conditions and must be able to manage these situations. • Universal Verifiability – any party can verify the result of the voting • Receipt-freeness – Voters are unable to prove the content of his/her vote • Incoercibility – Voter cannot be coerced into casting a particular vote by a coercer. 5/29/2007 Hakan Evecek/SE 2 Evote 6

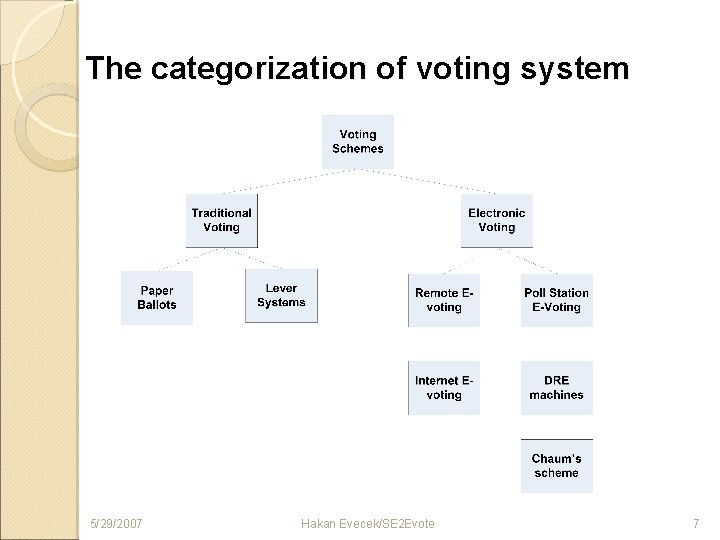
The categorization of voting system 5/29/2007 Hakan Evecek/SE 2 Evote 7

MESE Processes Applied for Online EVoting System Project Proposal and Plan Software Requirements Document (SRS) Software Design Specification (SDS) Testing Document Defects List Project Report 5/29/2007 Hakan Evecek/SE 2 Evote 8

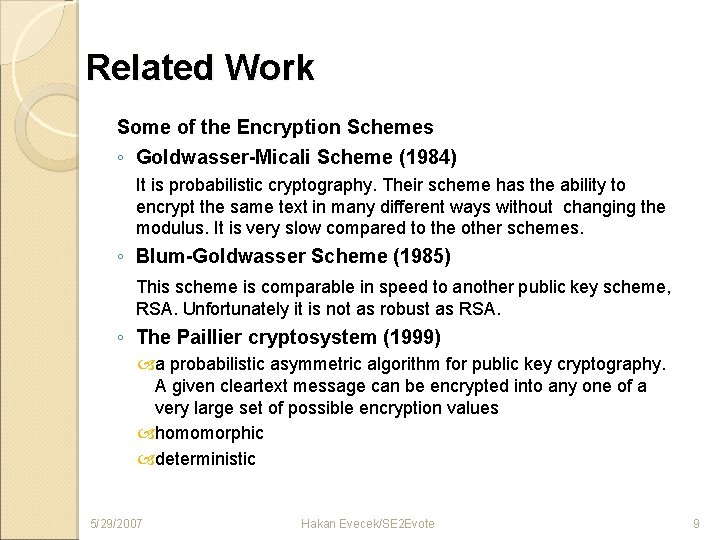
Related Work Some of the Encryption Schemes ◦ Goldwasser-Micali Scheme (1984) It is probabilistic cryptography. Their scheme has the ability to encrypt the same text in many different ways without changing the modulus. It is very slow compared to the other schemes. ◦ Blum-Goldwasser Scheme (1985) This scheme is comparable in speed to another public key scheme, RSA. Unfortunately it is not as robust as RSA. ◦ The Paillier cryptosystem (1999) a probabilistic asymmetric algorithm for public key cryptography. A given cleartext message can be encrypted into any one of a very large set of possible encryption values homomorphic deterministic 5/29/2007 Hakan Evecek/SE 2 Evote 9

Continued… ◦ Uses of Paillier Cryptography Electronic Voting Anonymous Mix Nets (due to self-blinding property) Electronic Auctions Electronic Lotteries ◦ Damgard-Jurick Scheme (2000) Just a modification of Paillier's scheme. It is also called Generalized Paillier System. It allows a user to increase the size of the encrypted value. Like Paillier it is probabilistic and homomorphic. 5/29/2007 Hakan Evecek/SE 2 Evote 10

Continued… ◦ Homomorphic Encryption A special type of cryptography in which the sum of two encrypted values is equal to the encrypted sum of the values. ◦ Public Key Cryptography Asymmetric cryptography, is a form of cryptography in which each user will have a key that didn’t have to be kept secret. ◦ Threshold Cryptography A cryptographic function can be distributed amongst several participants in such a way that the operation can be performed only through cooperation of a specified subset of the participants. In addition, if less than the required number of participants’ attempts to perform the action, no useful information can be constructed or obtained.
![Cryptographic Techniques Implemented by Brett Wilson to PTC Web Services Paillier Crypto System 15 Cryptographic Techniques Implemented by Brett Wilson to PTC Web Services Paillier Crypto. System [15]](https://slidetodoc.com/presentation_image_h/b299530e9d7eb4d808d24a06618ce021/image-12.jpg)
Cryptographic Techniques Implemented by Brett Wilson to PTC Web Services Paillier Crypto. System [15] ◦ Trapdoor Discrete Logarithm Scheme ◦ c = g. Mrn mod n 2 n is an RSA modulus (modulus of 2 safe primes) Safe prime - p = 2 q + 1 where q is also prime g is an integer of order nα mod n 2 r is a random number in Z * n ◦ M = L(cλ(n) mod n 2)/L(gλ(n) mod n 2) mod n ◦ L(u) = (u-1)/n, λ(n)=lcm((p-1)(q-1)) ◦ Important Properties Probabilistic (randomness of E(M)) Homomorphic E(M 1 + M 2) = E(M 1) x E(M 2), E(k x M) = E(M)k Self-blinding 5/29/2007 D(E(M) rn mod n 2 ) = m Hakan Evecek/SE 2 Evote Continued… 12
![Cryptographic Techniques Implemented Threshold Encryption 15 Public key encryption as usual Distribute Cryptographic Techniques Implemented Threshold Encryption [15] ◦ Public key encryption as usual ◦ Distribute](https://slidetodoc.com/presentation_image_h/b299530e9d7eb4d808d24a06618ce021/image-13.jpg)
Cryptographic Techniques Implemented Threshold Encryption [15] ◦ Public key encryption as usual ◦ Distribute secret key “shares” among i participants ◦ Decryption can only be accomplished if a threshold number t of the i participants cooperate No information about m can be obtained with less than t participants cooperating Shamir Secret Sharing ◦ Lagrange Interpolation formula ◦ f(X) = Σti=0 ai. Xi ◦ a 0 is secret, ai are random, f(X) are “secret shares” X is share index (1 to number of servers) ◦ If enough f(X) available it is possible to recover a 0 5/29/2007 Hakan Evecek/SE 2 Evote 13
![Operation of EVoting System 15 2 SOAPXML Request for PTC Parameters Hakan EvecekSE 2 Operation of E-Voting System [15] 2. SOAP/XML Request for PTC Parameters Hakan Evecek/SE 2](https://slidetodoc.com/presentation_image_h/b299530e9d7eb4d808d24a06618ce021/image-14.jpg)
Operation of E-Voting System [15] 2. SOAP/XML Request for PTC Parameters Hakan Evecek/SE 2 Evote 4. RSA Encrypted Secret Key Shares 7. Paillier Encrypted Vote Tally 5/29/2007 1. Election Authorities RSA Public Keys 6. Paillier Encrypted Vote 3. SOAP/XML Response containing RSA encrypted PTC Parameters 8. Partial Decryption Shares of Vote Tally/Proofs of Correct Decryption 5. Paillier Public Key 14

5/29/2007 Hakan Evecek/SE 2 Evote 15

User Login Page Assumed that users has registered previously and has secure login credentials provided. Admin Users Voters Completely Automated Public Turing test to tell Computers and Humans Apart (CAPTCHA) 5/29/2007 Hakan Evecek/SE 2 Evote 16

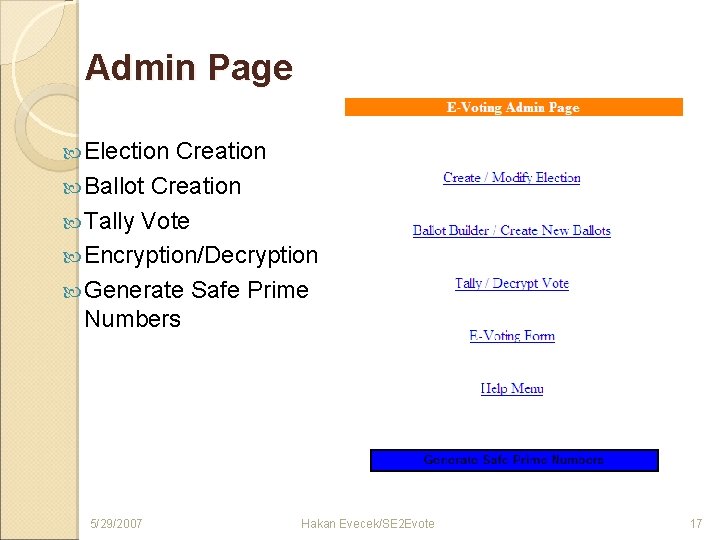
Admin Page Election Creation Ballot Creation Tally Vote Encryption/Decryption Generate Safe Prime Numbers 5/29/2007 Hakan Evecek/SE 2 Evote 17

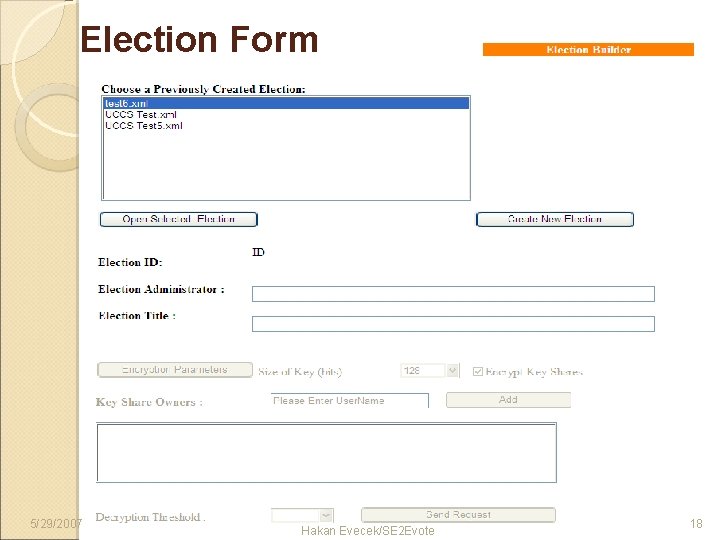
Election Form 5/29/2007 Hakan Evecek/SE 2 Evote 18

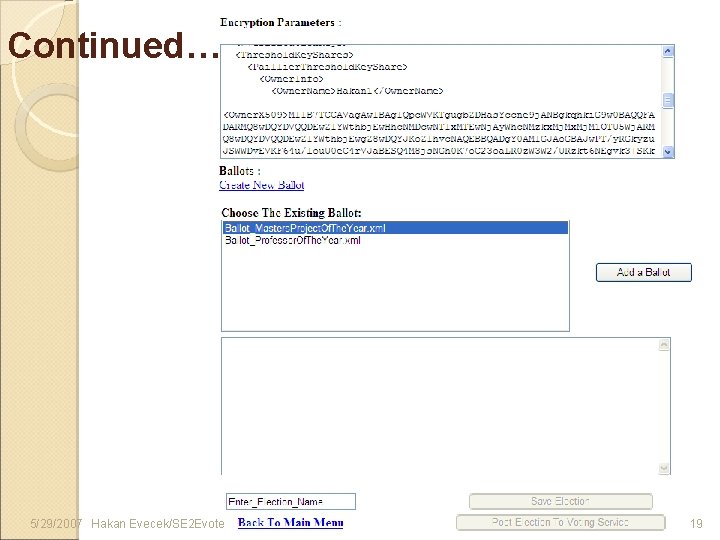
Continued… 5/29/2007 Hakan Evecek/SE 2 Evote 19

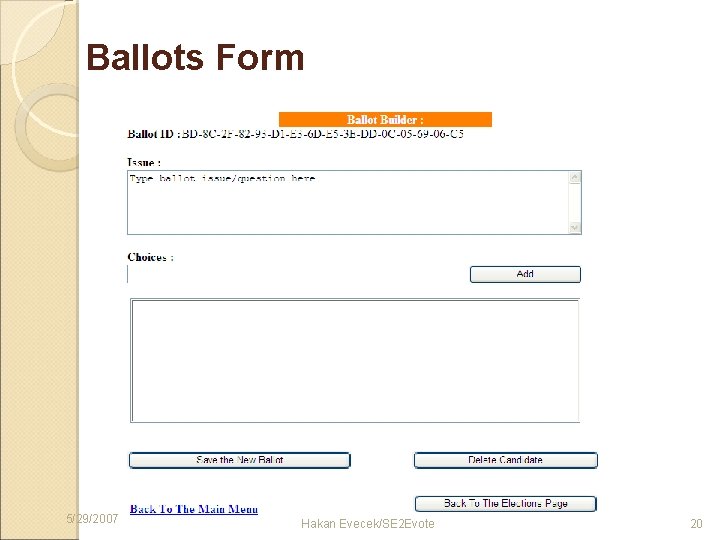
Ballots Form 5/29/2007 Hakan Evecek/SE 2 Evote 20

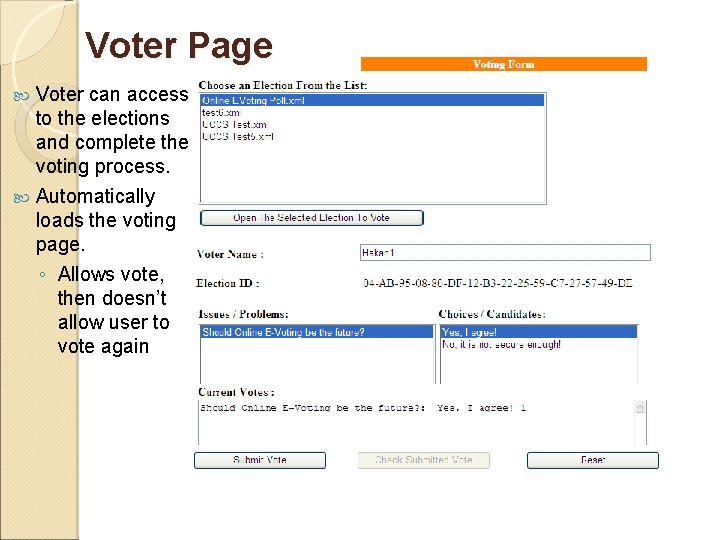
Voter Page Voter can access to the elections and complete the voting process. Automatically loads the voting page. ◦ Allows vote, then doesn’t allow user to vote again

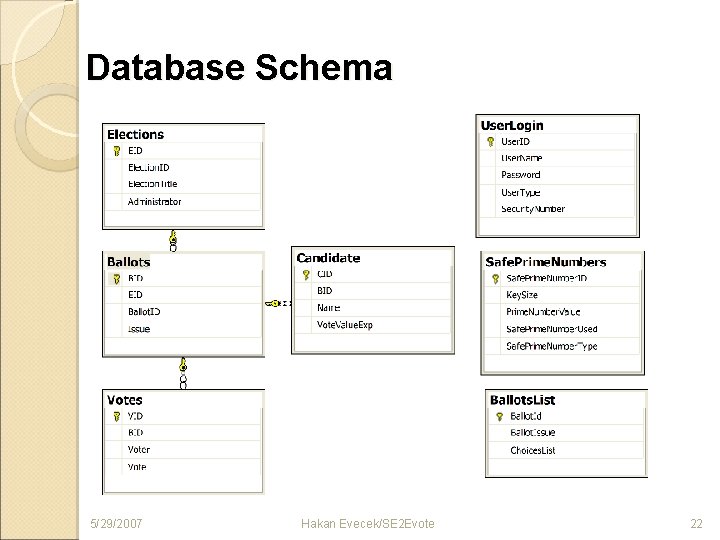
Database Schema 5/29/2007 Hakan Evecek/SE 2 Evote 22

Suggested Key Generation, Encryption/Decryption Optimization Safe Prime Numbers Pre-Computation Process. • Chinese Remainder Theorem to calculate p, q separately and then multiply for n. • • Paillier Scheme Pre-Computation for decryption. 5/29/2007 Hakan Evecek/SE 2 Evote 23

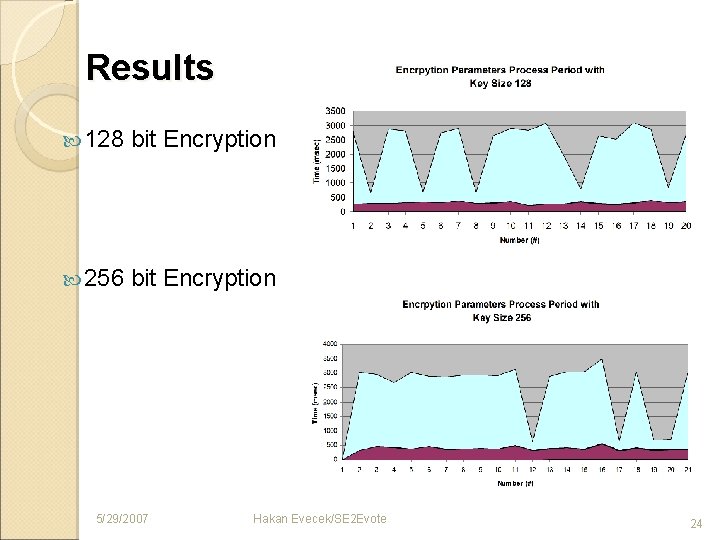
Results 128 bit Encryption 256 bit Encryption 5/29/2007 Hakan Evecek/SE 2 Evote 24

Lessons Learned The SE processes applied in this project has set precedence which can be used for the future projects. Ensure that the SRS, SDS and test documents can be easily modified any future enhancements can be made with ease. Security issues involved in E-voting systems. CRT is a very useful theorem that can be applied on other theorems to improve the efficiency and increase the speed of the computations. Pre-computation is always an improvement to the systems as long as they are designed and architected properly like running a thread on the background to generate prime numbers in this case. Setting up read/write access permissions for the folders is important in ASP. Net. It is very important to follow the processes on this setup. Certificate registration and confirmation requires additional processes for the internet solutions. 5/29/2007 Hakan Evecek/SE 2 Evote 25

Future Direction Implement the suggested CRT improvement into the code. Implement constant value pre-computation for decryption process. Fix XML solution in the code. Add more web application security protocols and processes. Implement registration and voter identity verification process. ◦ Authenticity of election parameters/ballots not currently guaranteed Implement signing of election parameters/ballots by admin 5/29/2007 Hakan Evecek/SE 2 Evote 26

Conclusion Encryption parameters creation process improvements with the application of pre-computation to the web services. Alternate processes are also available to improve the efficiency further, such as: CRT Theorem, applying pre-computation to other constants in the Paillier’s scheme and also using 3 rd scheme instead of the 1 st scheme as explained in many researches. The online E-Voting system with Paillier Cryptosystem Web Services implemented in this project brings a more secure evoting environment one step closer. Online E-Voting systems need to be considered as an enterprise solution when security, from the registration till the end of the Tally process, is to be considered. 5/29/2007 Hakan Evecek/SE 2 Evote 27
![References 1 http cris joongbu ac krpublicationevotingimplementationAPIEMS 2004 pdf Implementation issues in a secure References [1] http: //cris. joongbu. ac. kr/publication/evoting_implementation-APIEMS 2004. pdf Implementation issues in a secure](https://slidetodoc.com/presentation_image_h/b299530e9d7eb4d808d24a06618ce021/image-28.jpg)
References [1] http: //cris. joongbu. ac. kr/publication/evoting_implementation-APIEMS 2004. pdf Implementation issues in a secure e-voting schemes, Riza Aditya, Byoungcheon Lee, Colin Boyd and Ed Dawson. [3] http: //www. cs. virginia. edu/~pev 5 b/writing/academic/thesis. html Vote Early, Vote Often, and Vote. Here: A Security Analysis of Vote. Here, Philip E. Varner, May 11, 2001. [5] http: //www. trustycom. fr/pdf/Fo. Po. St 00. pdf P. Fouque, G. Poupard, J. Stern, Sharing Decryption in the Context of Voting or Lotteries, Financial Cryptography 2000 Proceedings. [6] http: //www. captcha. net/ , the Official CAPTCHA web site. [7] http: //www. vote. caltech. edu/reports/alv-nag_loyola. pdf R. Michael Alvarez, Jonathan Nagler, The Likely consequences of Internet Voting for Political Representations. [15] B. Wilson, C. E. Chow, Paillier Threshold Cryptography Web Service User’s Guide, University of Colorado – Colorado Springs Master’s Project, 2006. [16]http: //www. cs. rit. edu: 8080/ms/static/spr/2005/4/kar 1141/report. pdf , Progress on Probabilistic Encryption Schemes, Kert Richardson, July 2006. [17] http: //www. cs. umd. edu/~jkatz/THESES/staub. pdf. gz An Analysis of Chaum’s voter-verifiable election scheme, Julie Ann Staub, 2005 [18] http: //www. brics. dk/RS/00/45/BRICS-RS-00 -45. pdf Ivan Damgard and Mads J. Jurik, A Generalization, a Simplification and Some Applications of Paillier’s Probabilistic Public-Key System, PKC 2001. [ [20] http: //www. rsa. com/rsalabs/cryptobytes/Crypto. Bytes_January_2002_final. pdf Crypto. Bytes, Dan Boneh, Hovav Shacham, Spring 2002. [21] http: //www. gemplus. com/smart/rd/publications/pdf/Pai 99 pai. pdf Public-Key Crypto. Systems Based on Composite Degree Residuosity Classes, Pascal Paillier, 1999 [22] http: //en. wikipedia. org/wiki/Paillier_cryptosystem , Paillier Crytosystem from Wikipedia, the free encyclopedia. 5/29/2007 Hakan Evecek/SE 2 Evote 28