Applying Digital Watermarking Technology to Control CD copying

















- Slides: 23

Applying Digital Watermarking Technology to Control CD copying BY CHAYAN RATTANAVIJAI

Problem Descriptions • Software piracy • Software industry lost billions of dollars each year • Discourages individuals and businesses to create innovative software • Discourages technology transfers between nations Source: SIIA’s Report on Global Software Piracy 2000

Motivations of pirates • Low cost of reproduction • • • Price of CD writer is about $200 • Price of CD-Duplicator is about $2000 Easily access to tools • CD-R, CD-RW, CD-Duplicator Take short time • Take about 7 mins with speed of 8 x CD-R to copy • Take less than 1 min to copy with CD-Duplicator Ineffective of intellectual property law • Not enough law enforcement High Demand

Ordinary Pirates • You make copies of a software to your three best friends • Each of your best friends make copies of the software to his three best friends

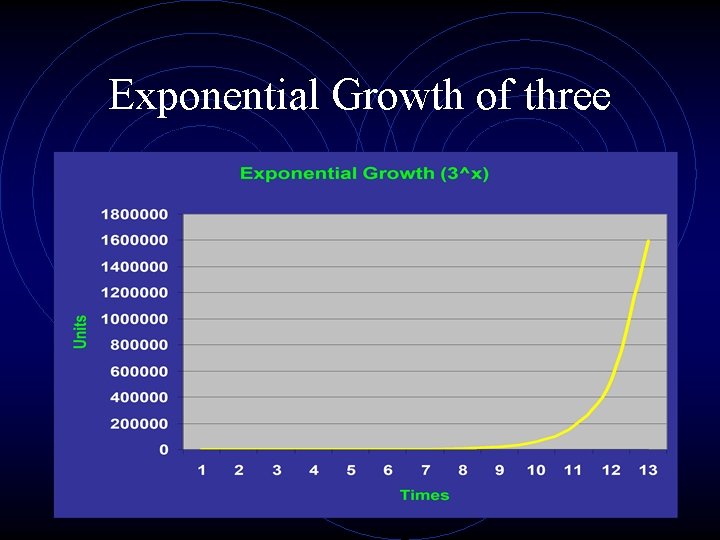
Exponential Growth of three

Objectives • To review the components that are being built in to consumer devices • To study how the components are working • To study how to apply the components to software industry

Goal • To help reduce the number of software piracy

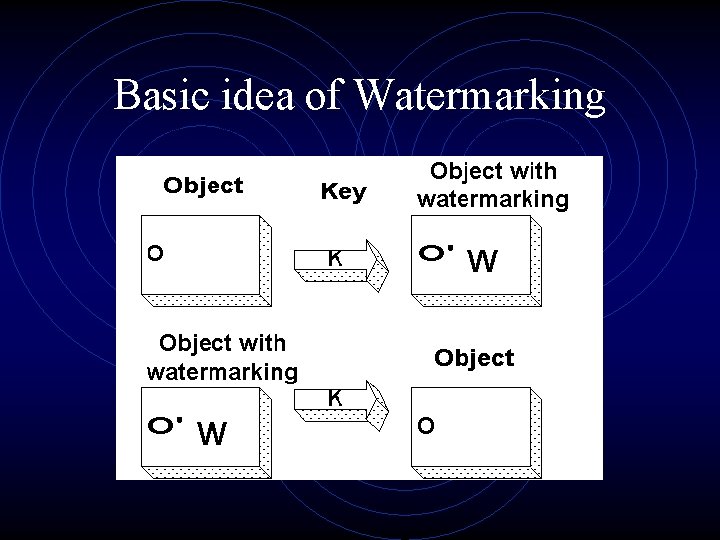
Basic idea of Watermarking

What is Digital Watermarking? • A digital watermark is a piece of information embedded inside a digital object. • It is either visible or invisible.

Digital marks can be used to: • Identify the origin of the data or uniquely • • establish ownership Identify the recipient of the data Check integrity of the data

Terminology • Content Scrambling System (CSS) developed by Matsushita, a device requires a pair of keys, is used to descramble data. • Secure Transmission System provides a mechanism for pair of compliant devices on a computer bus to exchange keys.

Terminology (continues) • Copy Generation Management System (CGMS) is simply a pair of bits in the header of data stream that encode one of three possible rules for copying: “copyalways”, “copy-never”, “copy-once”.

Terminology (continues) • Analog Protection System (APS) , developed by Macrovision, is a method of modifying NTSC signals so that they can be displayed on television, but cannot be recorded on VCR’s

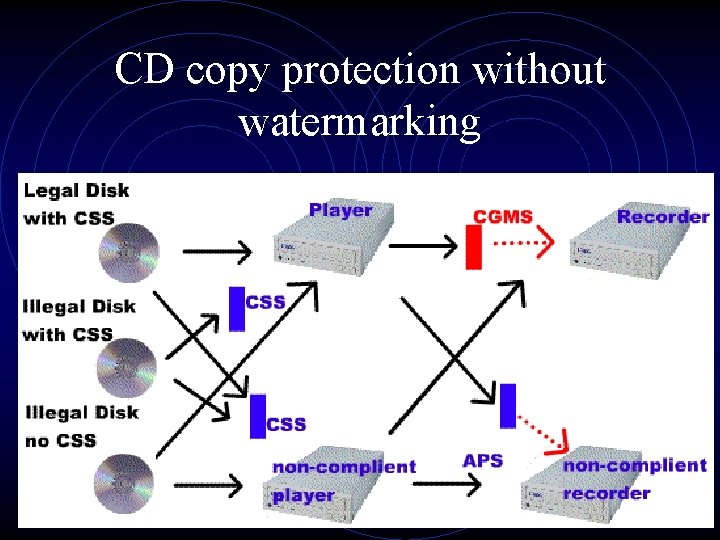
CD copy protection without watermarking • Legal disks will be scrambled with CSS and can be played only on compliant devices. Bit-for-bit copies of these disks won’t be playable on any devices, because they won’t contain the descrambling keys. This in ensured by storing the keys on the lead-in area of the legal disk, which is only read by compliant drives.

CD copy protection without watermarking

Problem • CGMS in intended to prevent illegal copies, • however a non compliant player may strip out these copy control bits from the header, leaving the data unprotected. APS works only when the display device is a compliant. A pirate can simply route it into an appropriate non-compliant recorder and make an unencrypted copy. Such a copy would not contain the CGMS bits.

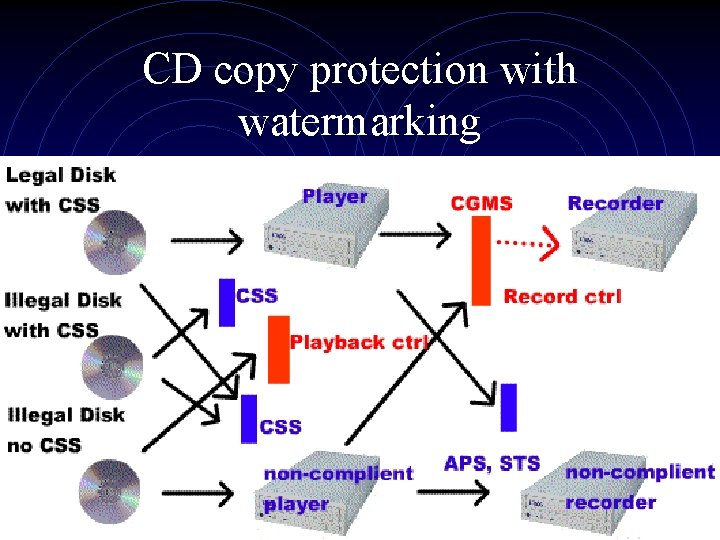
CD copy protection with watermarking • Record control takes over the job of CGMS. It works regardless of how the data reaches the compliant recorder, since the watermark that contains the CGMS data is never removed by normal processing.

CD copy protection with watermarking

Purpose of introducing watermarking into the system • To improve the protection provided by • CGMS by making the copy control information harder to remove To make unencrypted copies unplayable on compliant devices

Facilities & Resources • Need a laboratory • Need experts to help implement the prototype • Need the special hardware and technology

Future implementation • The watermark system requires enforcement to the device manufacturers to implement watermark detectors in their products • Better encryption algorithm in the watermark (IBM-Data Hiding)

Conclusion • This research shows how to apply the watermarking to make it harder to reproduce the illegal software • The experiment from the laboratory will give us the result. • The prototype may be developed to help reduce the numbers of software piracy.

THE END