Applying Continuous Monitoring and Cyber Best Practice to

Applying Continuous Monitoring and Cyber Best Practice to the Texas Cyber Framework Northrop Grumman Information Systems (NGIS) Calvin Smith 20 May 2015 Approved for Public Release #15 -0906; Unlimited Distribution

Agenda • Introduction • About Northrop Grumman • Texas Cybersecurity Framework • Federal Continuous Monitoring Program • Dynamic Texas Cyber Monitoring Framework Dashboard • Cyber Best Practice / Defensive In Depth • Q&A 2 Approved for Public Release #15 -0906; Unlimited Distribution
Northrop Grumman Information Sector Snapshot Focus Areas At a Glance • $6. 2 B business • Cyber • More than 16, 000 employees • Communications • 50 states, 21 countries • Command Control • Integrated Air and Missile Defense • Intelligence, Surveillance, Reconnaissance • Civil • Health 3 Approved for Public Release #15 -0906; Unlimited Distribution Approved for Public Release, #15 -0507; Unlimited Distribution
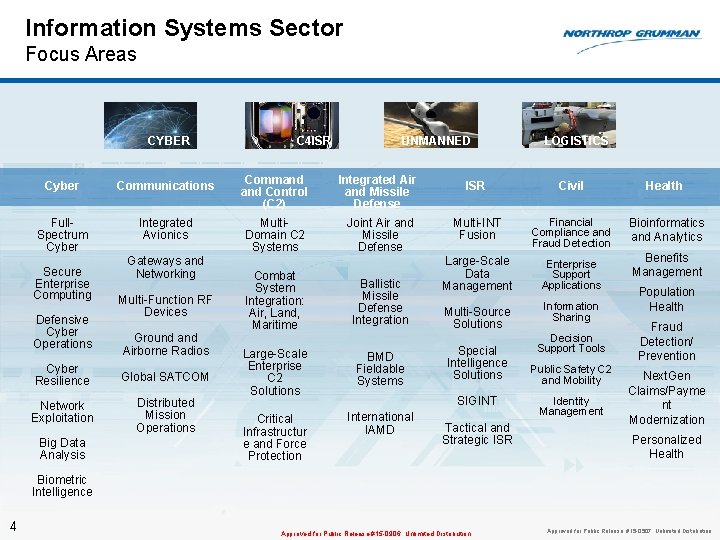
Information Systems Sector Focus Areas CYBER Cyber Communications Full. Spectrum Cyber Integrated Avionics Secure Enterprise Computing Defensive Cyber Operations Gateways and Networking Multi-Function RF Devices Ground and Airborne Radios Cyber Resilience Global SATCOM Network Exploitation Distributed Mission Operations Big Data Analysis C 4 ISR UNMANNED Command Control (C 2) Integrated Air and Missile Defense Multi. Domain C 2 Systems Joint Air and Missile Defense Combat System Integration: Air, Land, Maritime Ballistic Missile Defense Integration Large-Scale Enterprise C 2 Solutions BMD Fieldable Systems Critical Infrastructur e and Force Protection International IAMD LOGISTICS ISR Civil Health Multi-INT Fusion Financial Compliance and Fraud Detection Bioinformatics and Analytics Large-Scale Data Management Enterprise Support Applications Multi-Source Solutions Information Sharing Special Intelligence Solutions SIGINT Tactical and Strategic ISR Decision Support Tools Public Safety C 2 and Mobility Identity Management Benefits Management Population Health Fraud Detection/ Prevention Next. Gen Claims/Payme nt Modernization Personalized Health Biometric Intelligence 4 Approved for Public Release #15 -0906; Unlimited Distribution Approved for Public Release, #15 -0507; Unlimited Distribution

About Me The End-to-End Monitoring team supports federal, state and local government programs, specializing in cyber and performance monitoring. v Cal - 28+ years in networking & cyber, 10 years in continuous & end-to-end monitoring architectures. v Currently supporting US CERT as Cyber Technologist and Solution Architect for Texas State Agencies v Previously worked as Cyber Architect for U. S. Department of State, Department of Homeland Security, Department of Justice and Patent Trademark Office. v In his spare time he is an avid music collector, IT cloud tech enthusiast and road warrior. 5 Approved for Public Release #15 -0906; Unlimited Distribution

Revised TAC 202 • Method to standardize and prioritize cyber risk from the state of Texas perspective • Standardizes a cyber approach and establishes a baseline for minimum cyber security • Tailorable or customizable for each state agency • Enables structure to fuse people, process and technology (tools) • Provides a phased approach to align with FISMA / NIST 800 -53 • Control Catalog for mapping Federal / Texas laws, guidance and instruction 6 Approved for Public Release #15 -0906; Unlimited Distribution
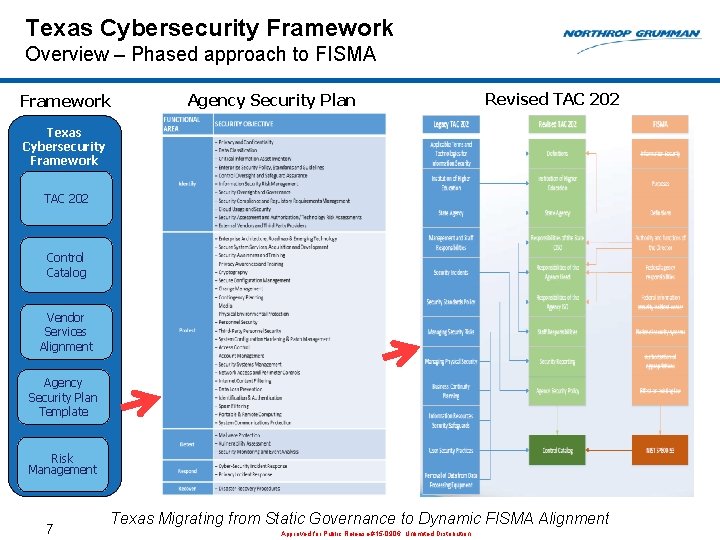
Texas Cybersecurity Framework Overview – Phased approach to FISMA Framework Agency Security Plan Revised TAC 202 Texas Cybersecurity Framework TAC 202 Control Catalog Vendor Services Alignment Agency Security Plan Template Risk Management 7 Texas Migrating from Static Governance to Dynamic FISMA Alignment Approved for Public Release #15 -0906; Unlimited Distribution
Federal Continuous Monitoring Program Continuous Diagnostics & Mitigation (CDM) • Leveraging automated tools and processes to continually assess IT systems, networks and programs • Capture real-time security information to effectively manage risk while reducing cost • Security controls are assessed continuously to provide real-time security posture instead of the traditional “snapshot-in-time • Real-time risk assessment is based on how well security controls mitigate known threats and vulnerabilities • Enables real-time risk management decision-making via continuous streaming of system state intelligence • Maps to 11 NIST Continuous Monitoring Domains, 15 DHS CDM Domains, NIST 800 -53 Controls Federal Policy Rapidly Moving Towards Real-time Cyber Monitoring 8 Approved for Public Release #15 -0906; Unlimited Distribution
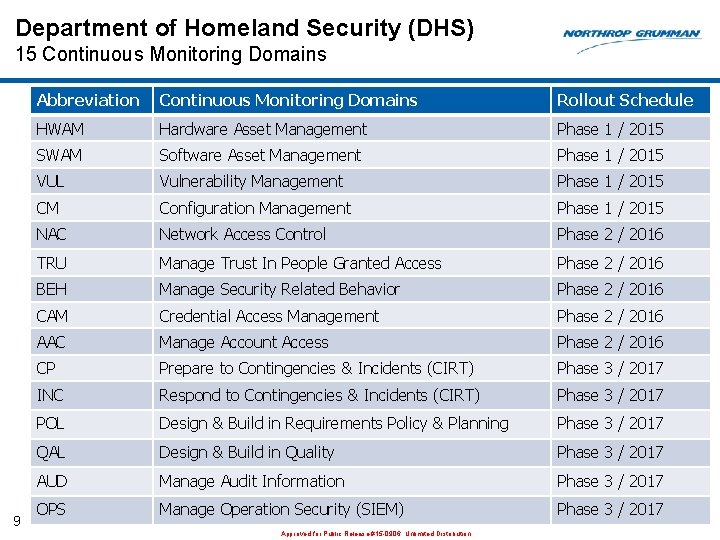
Department of Homeland Security (DHS) 15 Continuous Monitoring Domains 9 Abbreviation Continuous Monitoring Domains Rollout Schedule HWAM Hardware Asset Management Phase 1 / 2015 SWAM Software Asset Management Phase 1 / 2015 VUL Vulnerability Management Phase 1 / 2015 CM Configuration Management Phase 1 / 2015 NAC Network Access Control Phase 2 / 2016 TRU Manage Trust In People Granted Access Phase 2 / 2016 BEH Manage Security Related Behavior Phase 2 / 2016 CAM Credential Access Management Phase 2 / 2016 AAC Manage Account Access Phase 2 / 2016 CP Prepare to Contingencies & Incidents (CIRT) Phase 3 / 2017 INC Respond to Contingencies & Incidents (CIRT) Phase 3 / 2017 POL Design & Build in Requirements Policy & Planning Phase 3 / 2017 QAL Design & Build in Quality Phase 3 / 2017 AUD Manage Audit Information Phase 3 / 2017 OPS Manage Operation Security (SIEM) Phase 3 / 2017 Approved for Public Release #15 -0906; Unlimited Distribution
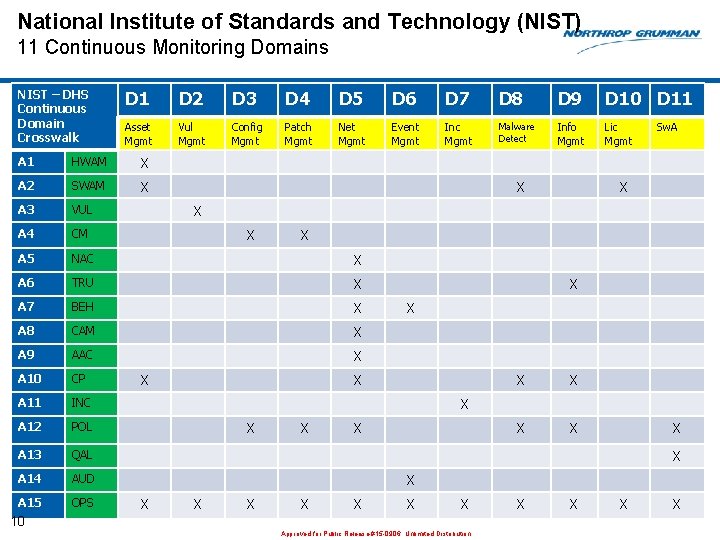
National Institute of Standards and Technology (NIST) 11 Continuous Monitoring Domains NIST – DHS Continuous Domain Crosswalk D 1 D 2 D 3 D 4 D 5 D 6 D 7 D 8 D 9 D 10 D 11 Asset Mgmt Vul Mgmt Config Mgmt Patch Mgmt Net Mgmt Event Mgmt Inc Mgmt Malware Detect Info Mgmt Lic Mgmt A 1 HWAM X A 2 SWAM X A 3 VUL A 4 CM A 5 NAC X A 6 TRU X A 7 BEH X A 8 CAM X A 9 AAC X A 10 CP A 11 INC A 12 POL A 13 QAL A 14 AUD A 15 OPS X Sw. A X X X X X X X 10 Approved for Public Release #15 -0906; Unlimited Distribution X X
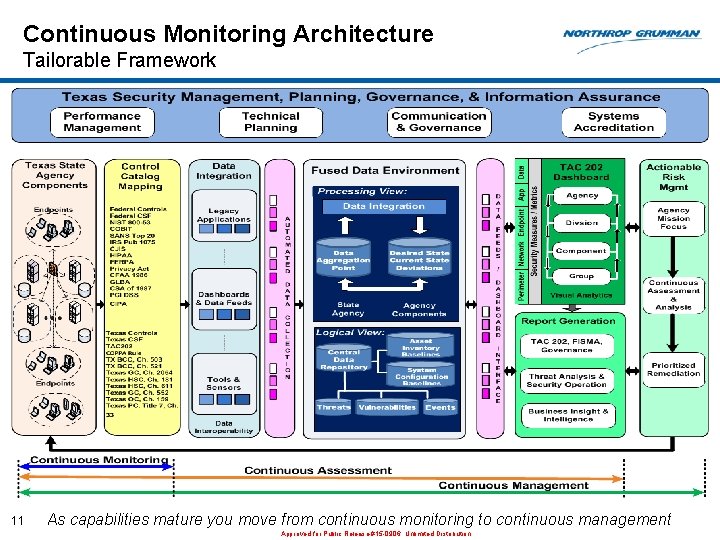
Continuous Monitoring Architecture Tailorable Framework 11 As capabilities mature you move from continuous monitoring to continuous management Approved for Public Release #15 -0906; Unlimited Distribution

Dynamic TAC 202 Cyber Dashboard Features & Capabilities • Acceptable Cyber Risk (ACR) – The ACR is dynamically determined based on advanced analytics. It is continuously generated based on historical and real-time data. There are no static, defined thresholds. • Advanced Analytics – Display of meaningful and hidden patterns in unstructured security data using statistics, metrics, and algorithms. Big Data analytics is best “visualized” to show insights normally not seen in tabular data displays, i. e, visual analytics. Cyber measures / metrics are dynamically reported in real-time • Dynamic Color Coding – A color scheme using green, yellow and red applied to dashboard metrics and maps based on dynamic changes in the ACR. • Predictive Analytics (Machine-Learning) – The dashboard dynamically extracts and learns from security control, defense in depth protection and incident information (i. e. , historical and real-time) in order to predict future cyber events and ability to respond and mitigate. • Quality of Protection (Qo. P)– A derived metric capturing end-to-end cyber protection based on security controls and defense-in-depth cyber protection profiles. Key Cyber Indicators (KCIs) are calculated, combined and weighted to measure potential risk factors contributing to lack/failure of end-user or critical asset protection. 12 Approved for Public Release #15 -0906; Unlimited Distribution
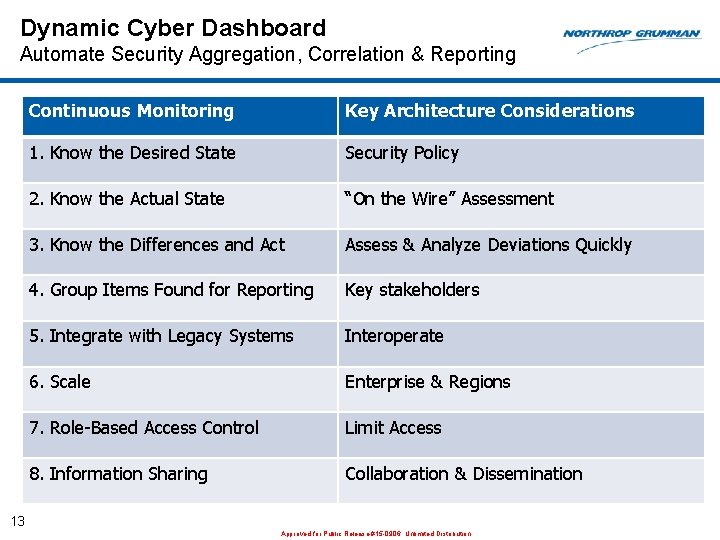
Dynamic Cyber Dashboard Automate Security Aggregation, Correlation & Reporting Continuous Monitoring Key Architecture Considerations 1. Know the Desired State Security Policy 2. Know the Actual State “On the Wire” Assessment 3. Know the Differences and Act Assess & Analyze Deviations Quickly 4. Group Items Found for Reporting Key stakeholders 5. Integrate with Legacy Systems Interoperate 6. Scale Enterprise & Regions 7. Role-Based Access Control Limit Access 8. Information Sharing Collaboration & Dissemination 13 Approved for Public Release #15 -0906; Unlimited Distribution
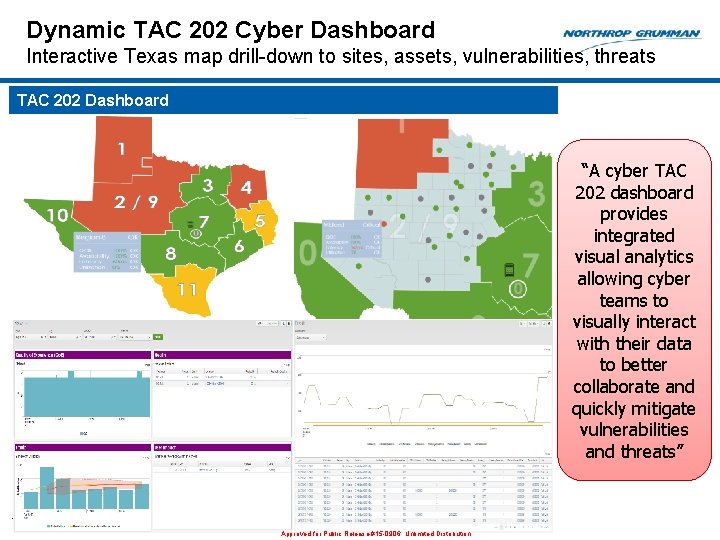
Dynamic TAC 202 Cyber Dashboard Interactive Texas map drill-down to sites, assets, vulnerabilities, threats TAC 202 Dashboard “A cyber TAC 202 dashboard provides integrated visual analytics allowing cyber teams to visually interact with their data to better collaborate and quickly mitigate vulnerabilities and threats” 14 Approved for Public Release #15 -0906; Unlimited Distribution
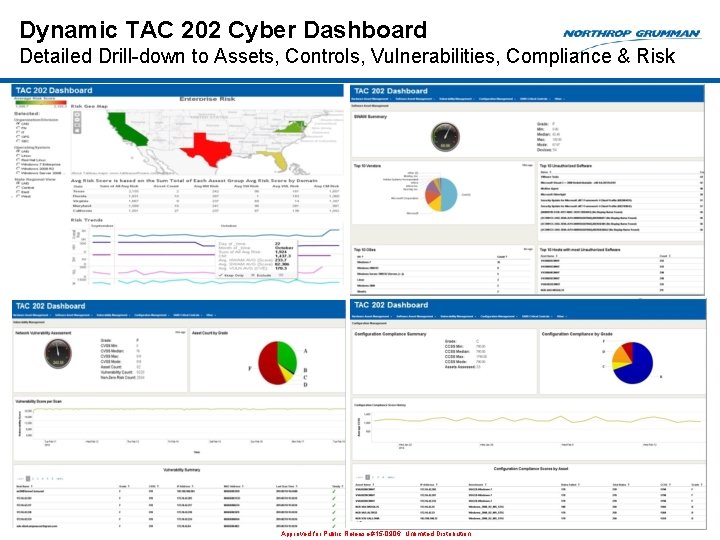
Dynamic TAC 202 Cyber Dashboard Detailed Drill-down to Assets, Controls, Vulnerabilities, Compliance & Risk 15 Approved for Public Release #15 -0906; Unlimited Distribution
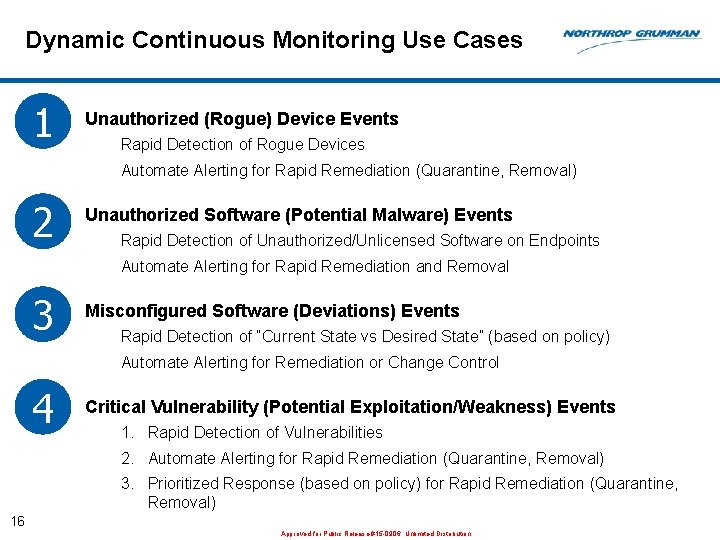
Dynamic Continuous Monitoring Use Cases 1 Unauthorized (Rogue) Device Events Rapid Detection of Rogue Devices Automate Alerting for Rapid Remediation (Quarantine, Removal) 2 Unauthorized Software (Potential Malware) Events Rapid Detection of Unauthorized/Unlicensed Software on Endpoints Automate Alerting for Rapid Remediation and Removal 3 Misconfigured Software (Deviations) Events Rapid Detection of “Current State vs Desired State” (based on policy) Automate Alerting for Remediation or Change Control 4 Critical Vulnerability (Potential Exploitation/Weakness) Events 1. Rapid Detection of Vulnerabilities 2. Automate Alerting for Rapid Remediation (Quarantine, Removal) 3. Prioritized Response (based on policy) for Rapid Remediation (Quarantine, Removal) 16 Approved for Public Release #15 -0906; Unlimited Distribution
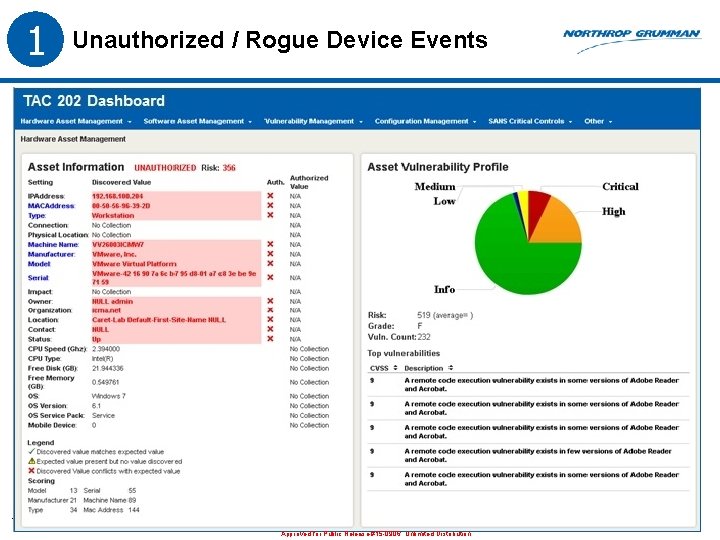
1 Unauthorized / Rogue Device Events 17 Approved for Public Release #15 -0906; Unlimited Distribution
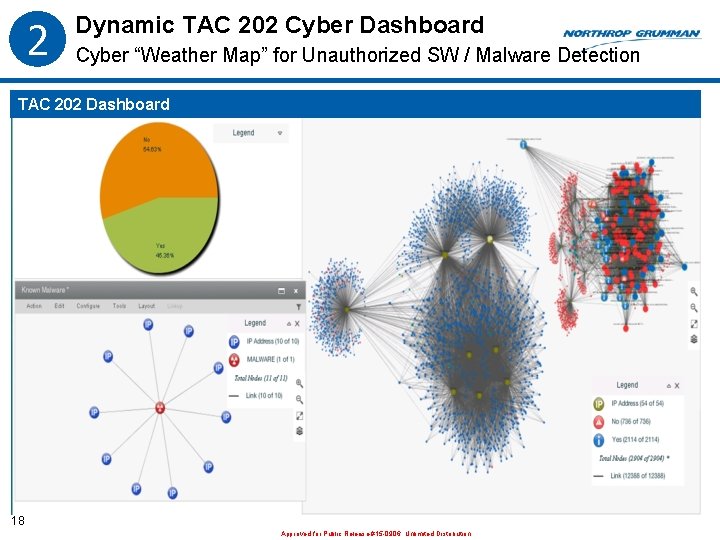
2 Dynamic TAC 202 Cyber Dashboard Cyber “Weather Map” for Unauthorized SW / Malware Detection TAC 202 Dashboard 18 Approved for Public Release #15 -0906; Unlimited Distribution
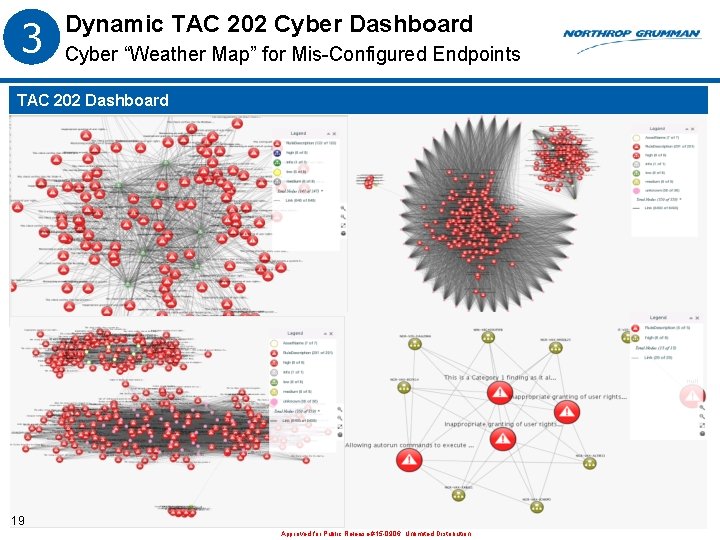
3 Dynamic TAC 202 Cyber Dashboard Cyber “Weather Map” for Mis-Configured Endpoints TAC 202 Dashboard 19 Approved for Public Release #15 -0906; Unlimited Distribution
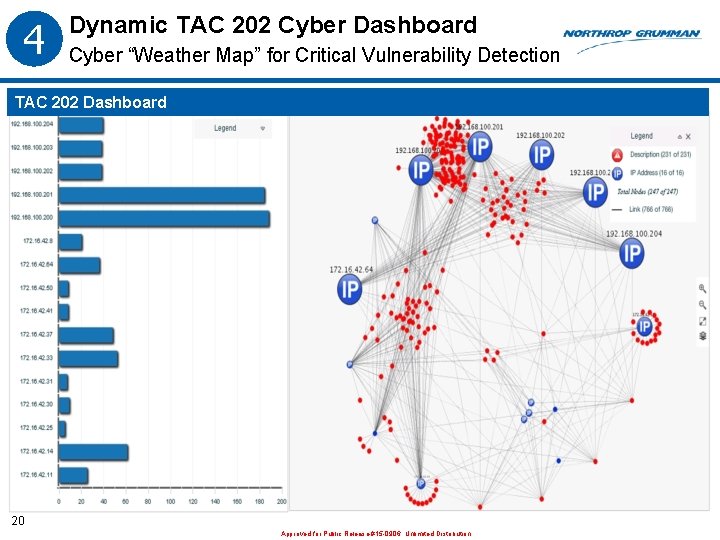
4 Dynamic TAC 202 Cyber Dashboard Cyber “Weather Map” for Critical Vulnerability Detection TAC 202 Dashboard 20 Approved for Public Release #15 -0906; Unlimited Distribution
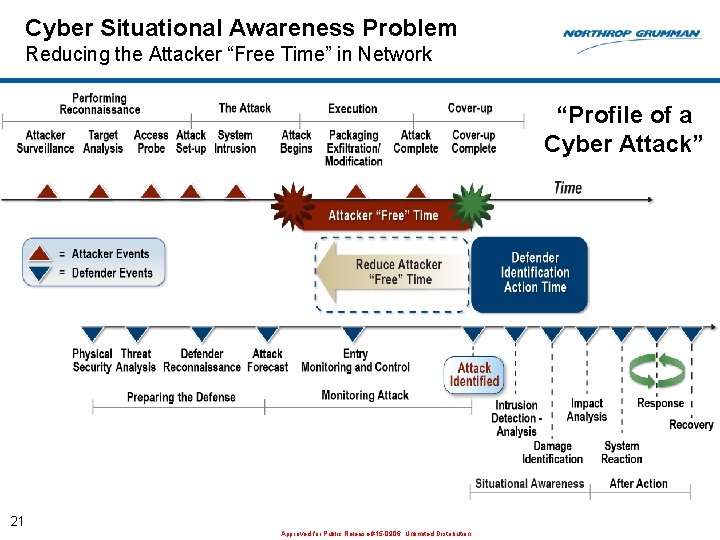
Cyber Situational Awareness Problem Reducing the Attacker “Free Time” in Network “Profile of a Cyber Attack” 21 Approved for Public Release #15 -0906; Unlimited Distribution
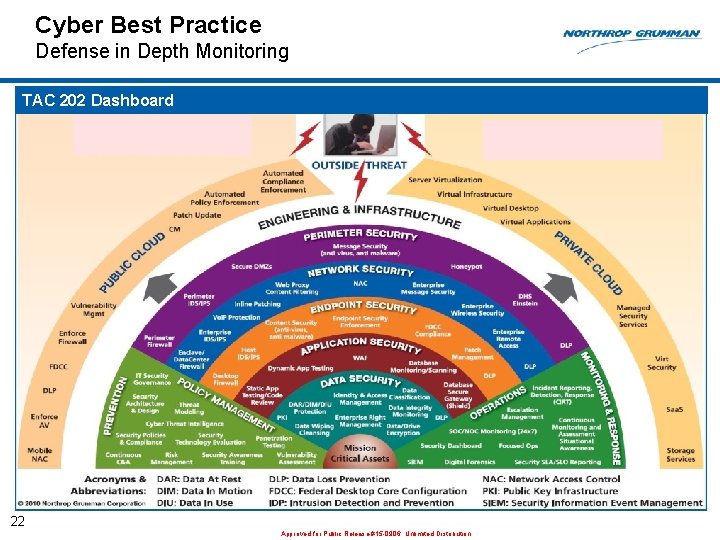
Cyber Best Practice Defense in Depth Monitoring TAC 202 Dashboard 22 Approved for Public Release #15 -0906; Unlimited Distribution
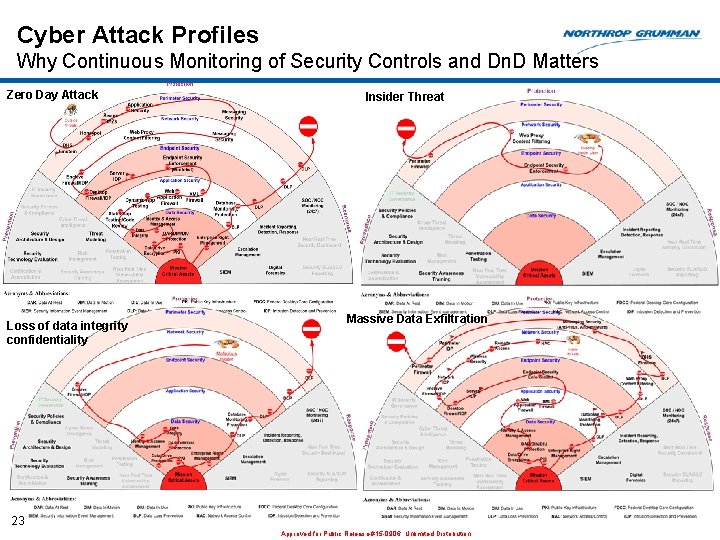
Cyber Attack Profiles Why Continuous Monitoring of Security Controls and Dn. D Matters Zero Day Attack Loss of data integrity confidentiality Insider Threat Massive Data Exfiltration 23 Approved for Public Release #15 -0906; Unlimited Distribution
Best Cyber Practice • Know your cyber requirements – Understand policy – Operationalize policy and apply to cyber tools and processes to make it more “actionable” – Design defense in depth monitoring architecture based on the business • Understand the threat – External bad actors – Insider threat – Know tactics, techniques and procedures • Understand your data… – Create data plan/data architecture – Map to security controls and defense in depth – “Listen” to your data • And how this applies to your agency’s core mission – What’s important to your business? – What are you trying to accomplish? – What, Who and How to report? 24 Implement Continuous Monitoring Approved for Public Release #15 -0906; Unlimited Distribution
Points of Contact Keri Mc. Clellan Program Manager Cell: 817 -240 -4693 Email: Keri. Mc. Clellan@ngc. com Calvin Smith Cyber Technologist, Solutions Architect & Project Manager Office: 512 -374 -4136 Email: ch. smith@ngc. com 25

Q&A 26 Northropfor Grumman Private/Proprietary Level 1 Distribution Approved Public Release #15 -0906; Unlimited

- Slides: 27