APPLIED CRYPTOGRAPHY Quantum Cryptography SCHOOL OF MATHEMATICS 1







- Slides: 24

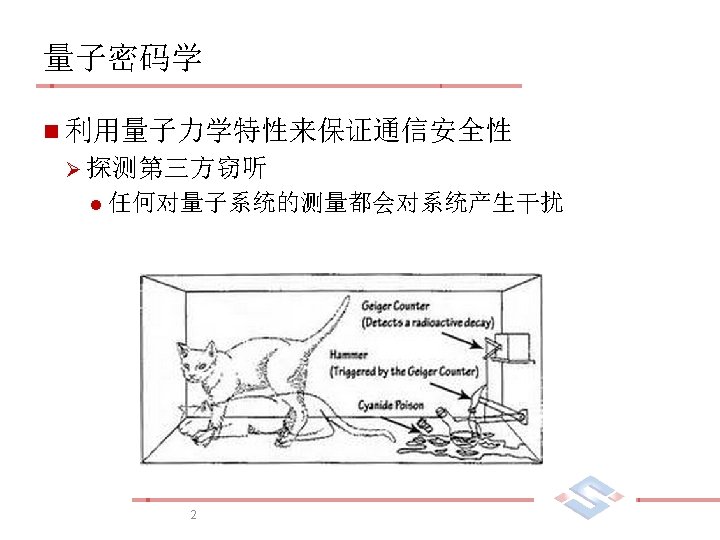
APPLIED CRYPTOGRAPHY 量子密码学 Quantum Cryptography SCHOOL OF MATHEMATICS 1


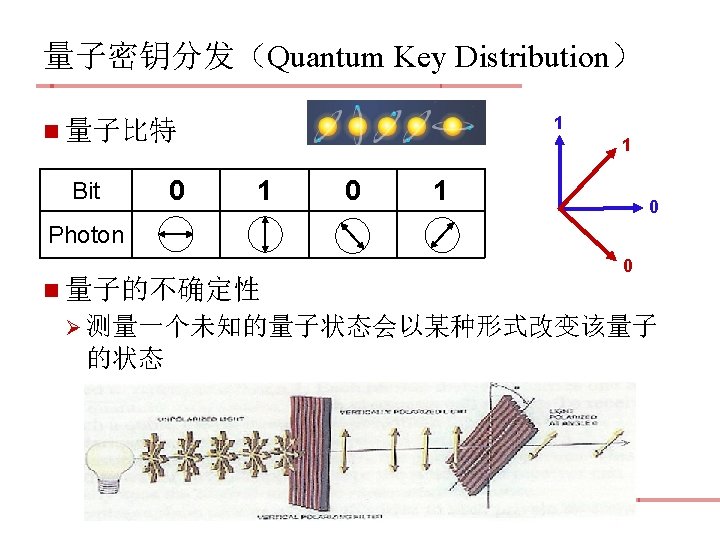
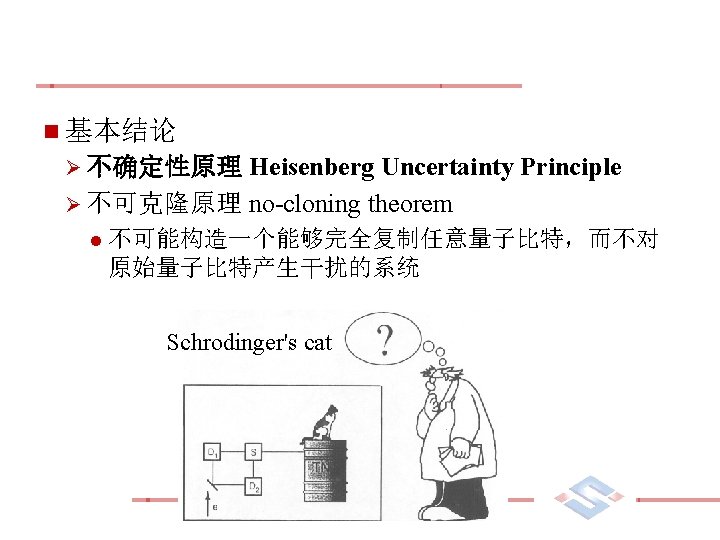
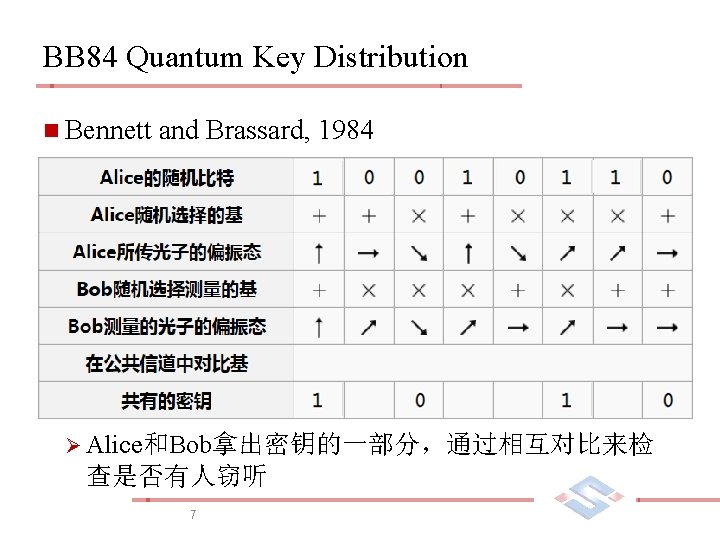
量子密钥分发(Quantum Key Distribution) n BB 84 developed by Charles Bennett and Gilles Brassard in 1984. Ø The first quantum cryptography protocol. Ø Rely on the quantum property that information gain is only possible at the expense of disturbing the signal if the two states one is trying to distinguish are not orthogonal 3




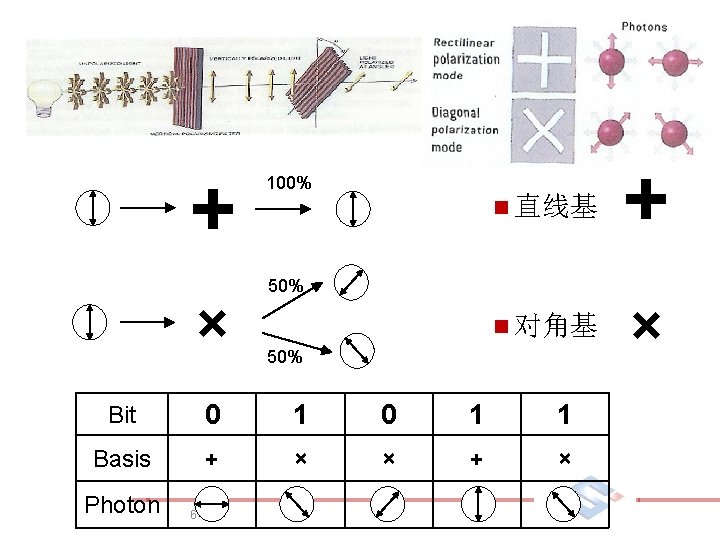
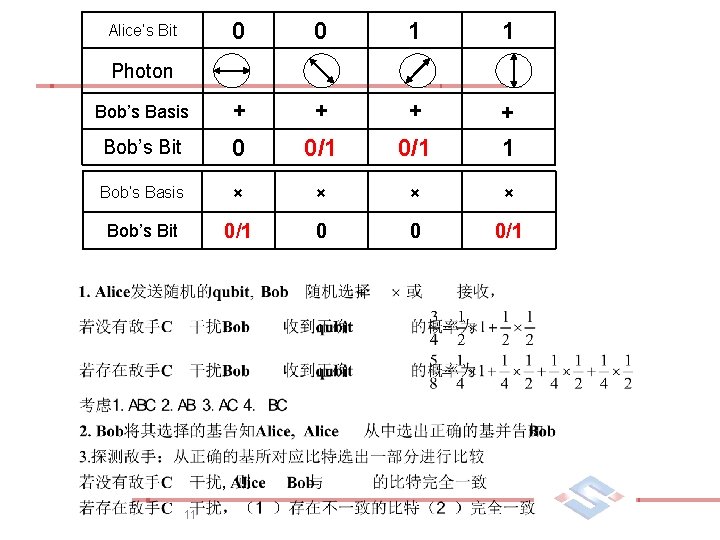
BB 84 Quantum Key Distribution n Bennett and Brassard, 1984 Ø Alice和Bob拿出密钥的一部分,通过相互对比来检 查是否有人窃听 7

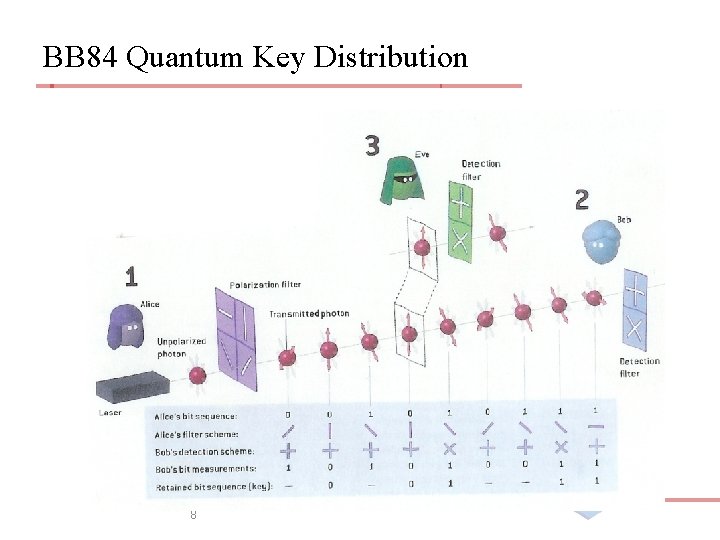
BB 84 Quantum Key Distribution 8


n 10

0 0 1 1 Bob’s Basis + + Bob’s Bit 0 0/1 1 Bob’s Basis × × Bob’s Bit 0/1 0 0 0/1 Alice’s Bit Photon 11

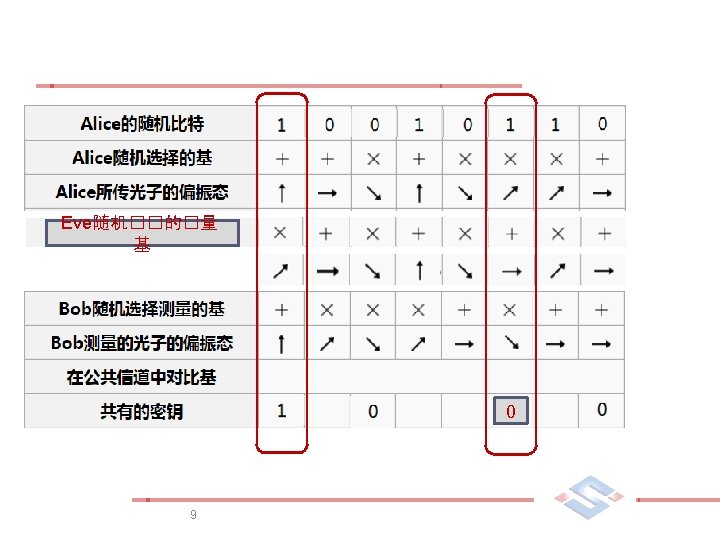
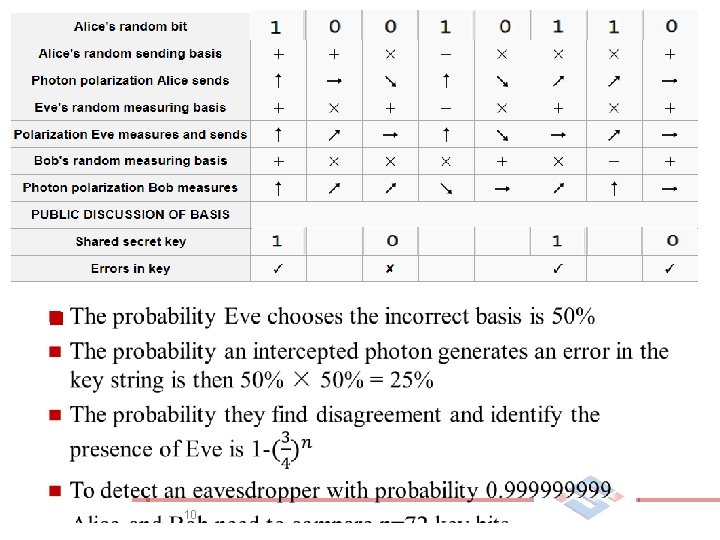
攻击 n Man-in-the-middle attack n Photon number splitting attack Ø If the pulse contains more than one photon, then Eve can split off the extra photons and transmit the remaining single photon to Bob 12

量子计算机 Quantum Computer 13

Timeline n n n n In 1959 Richard Feynman in his lecture "There's Plenty of Room at the Bottom" states the possibility of using quantum effects for computation. In 1984, BB 84 is published, the world's first quantum cryptography protocol by IBM scientists Charles Bennett and Gilles Brassard. In 2001, researchers demonstrated Shor's algorithm to factor 15 using a 7 -qubit NMR computer In 2011, D-Wave Systems announced the first commercial quantum annealer, the D-Wave One, claiming a 128 qubit processor. In May 2016, IBM Research announced[101] that for the first time ever it is making quantum computing available to members of the public via the cloud, who can access and run experiments on IBM’s quantum processor. In March 2017, IBM announced an industry-first initiative to build commercially available universal quantum computing systems called IBM Q. In March 2018, Google Quantum AI Lab announced a 72 qubit processor called Bristlecone 14

15

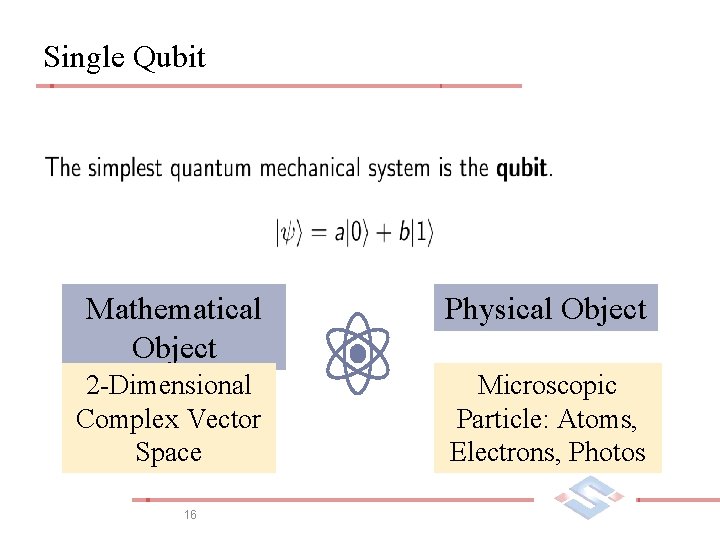
Single Qubit Mathematical Object Physical Object 2 -Dimensional Complex Vector Space Microscopic Particle: Atoms, Electrons, Photos 16

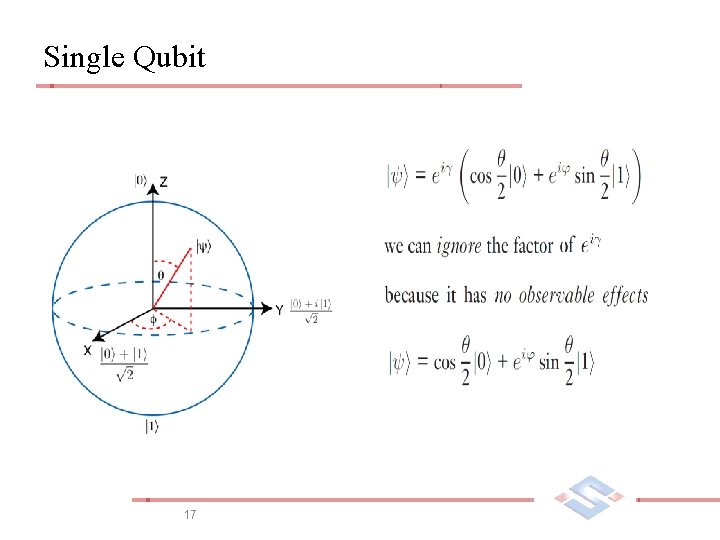
Single Qubit 17

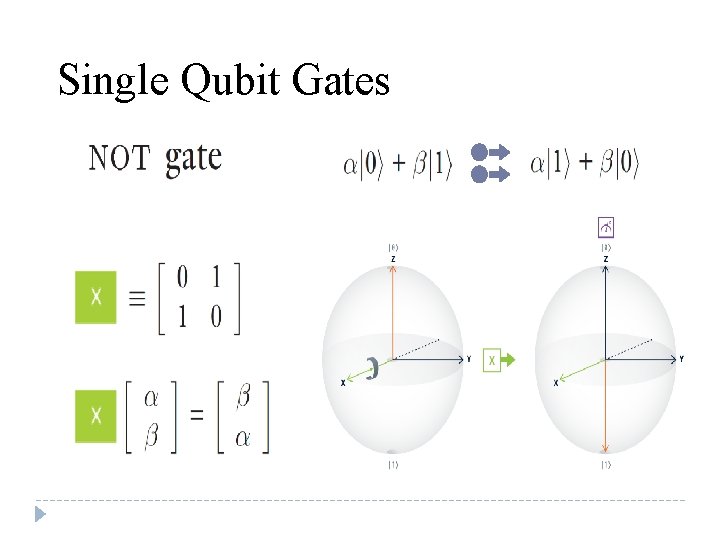
Single Qubit Gates

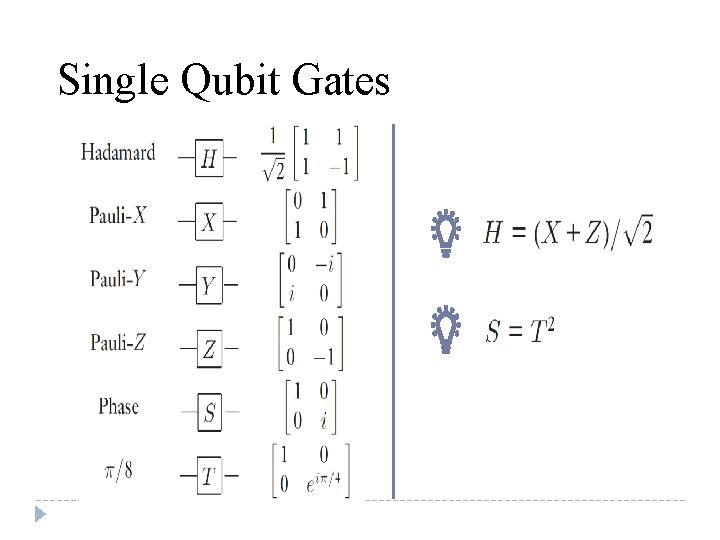
Single Qubit Gates

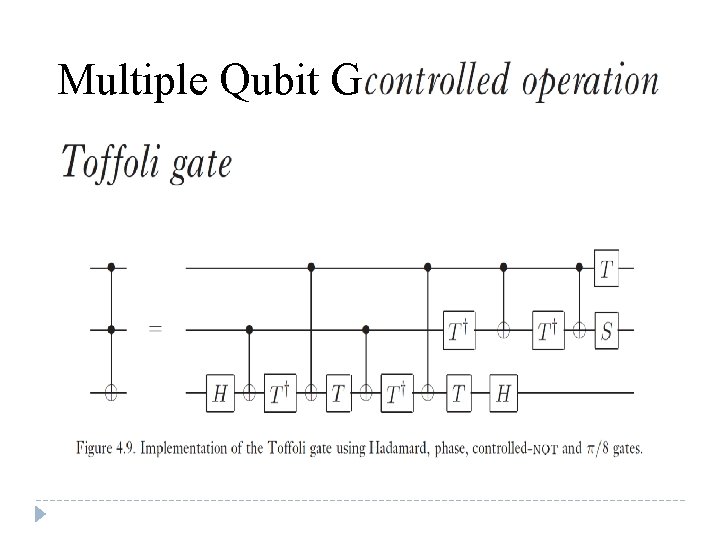
Multiple Qubit Gates

Quantum algorithm n 21

Quantum supremacy n John Preskill has introduced the term quantum supremacy to refer to the hypothetical speedup advantage that a quantum computer would have over a classical computer in a certain field. 22

Obstacles n Requirements Ø scalable for a practical quantum computer physically to increase the number of qubits; Ø qubits that can be initialized to arbitrary values; Ø quantum gates that are faster than decoherence time; Ø universal gate set; Ø qubits that can be read easily 23

References n http: //zh. wikipedia. org/zh- cn/%E 9%87%8 F%E 5%AD%90%E 5%AF%86%E 7%A 2%BC%E 5%AD%B 8 n http: //en. wikipedia. org/wiki/Quantum_key_distribution #Photon_number_splitting_attack n https: //en. wikipedia. org/wiki/Quantum_computing 24