Applied Architectures And Styles Software Architecture Foundations Theory


![Software Architecture: Foundations, Theory, and Practice REST Principles l l l [RP 1] The Software Architecture: Foundations, Theory, and Practice REST Principles l l l [RP 1] The](https://slidetodoc.com/presentation_image_h2/6bf1202fbf5dede1008a36bf87a0813a/image-9.jpg)
![Software Architecture: Foundations, Theory, and Practice REST Principles (cont’d) l [RP 4] Components perform Software Architecture: Foundations, Theory, and Practice REST Principles (cont’d) l [RP 4] Components perform](https://slidetodoc.com/presentation_image_h2/6bf1202fbf5dede1008a36bf87a0813a/image-10.jpg)
![Software Architecture: Foundations, Theory, and Practice REST Principles (cont’d) l l [RP 5] Idempotent Software Architecture: Foundations, Theory, and Practice REST Principles (cont’d) l l [RP 5] Idempotent](https://slidetodoc.com/presentation_image_h2/6bf1202fbf5dede1008a36bf87a0813a/image-11.jpg)





- Slides: 34

Applied Architectures And Styles Software Architecture: Foundations, Theory and Practice Chapter 11 Copyright © Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy. All rights reserved.

Software Architecture: Foundations, Theory, and Practice Objectives l l l Illustrate how principles have been used to solve challenging problems u Usually means combining elements Highlight some critical issues u I. e. , ignore them at your peril Show architecture can be used to explain and analyze common commercial systems 2

Software Architecture: Foundations, Theory, and Practice Outline l l Distributed and networked architectures u Limitations u REST u Commercial Internet-scale applications Decentralized applications u Peer-to-peer 3

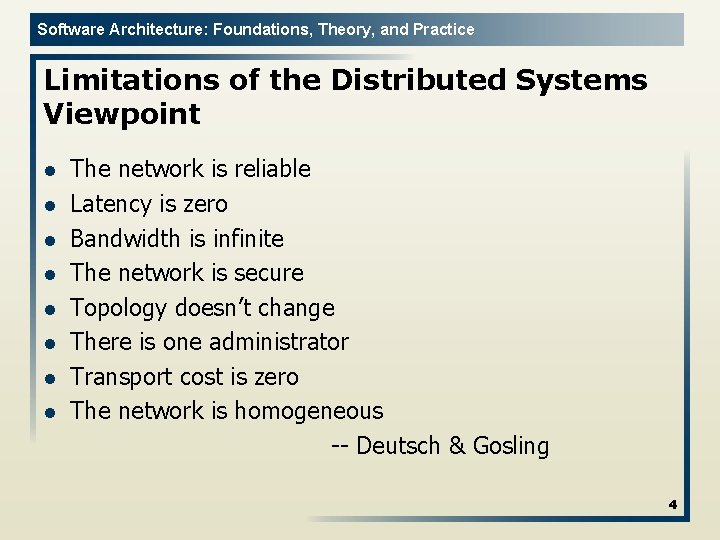
Software Architecture: Foundations, Theory, and Practice Limitations of the Distributed Systems Viewpoint l l l l The network is reliable Latency is zero Bandwidth is infinite The network is secure Topology doesn’t change There is one administrator Transport cost is zero The network is homogeneous -- Deutsch & Gosling 4

Software Architecture: Foundations, Theory, and Practice Architecture in Action: WWW l This is the Web 5 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

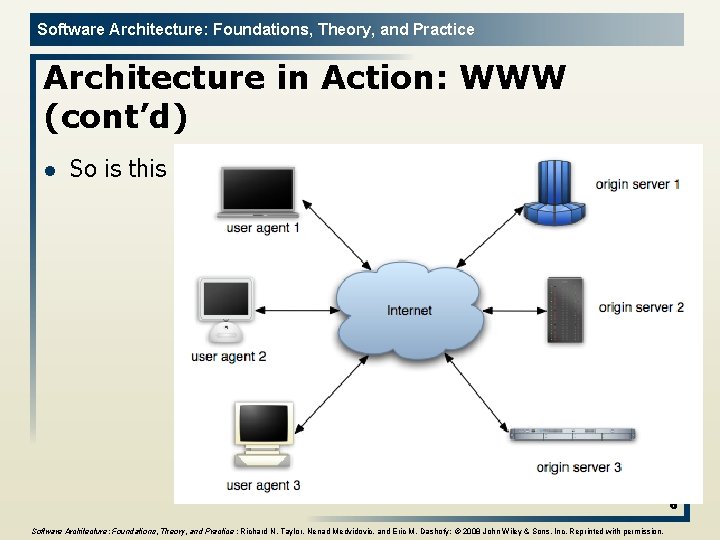
Software Architecture: Foundations, Theory, and Practice Architecture in Action: WWW (cont’d) l So is this 6 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

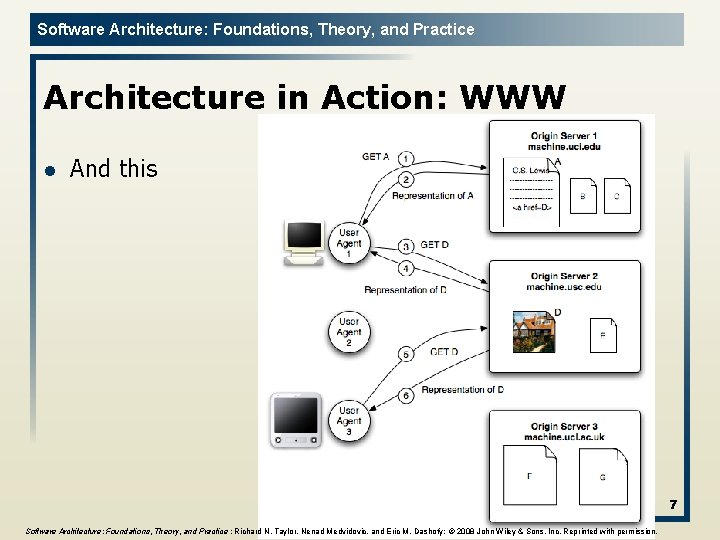
Software Architecture: Foundations, Theory, and Practice Architecture in Action: WWW l And this 7 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture: Foundations, Theory, and Practice WWW’s Architecture l l l The application is distributed (actually, decentralized) hypermedia Architecture of the Web is wholly separate from the code There is no single piece of code that implements the architecture. There are multiple pieces of code that implement the various components of the architecture. u E. g. , different Web browsers Stylistic constraints of the Web’s architectural style are not apparent in the code u The effects of the constraints are evident in the Web One of the world’s most successful applications is only understood adequately from an architectural vantage point. 8
![Software Architecture Foundations Theory and Practice REST Principles l l l RP 1 The Software Architecture: Foundations, Theory, and Practice REST Principles l l l [RP 1] The](https://slidetodoc.com/presentation_image_h2/6bf1202fbf5dede1008a36bf87a0813a/image-9.jpg)
Software Architecture: Foundations, Theory, and Practice REST Principles l l l [RP 1] The key abstraction of information is a resource, named by an URL. Any information that can be named can be a resource. [RP 2] The representation of a resource is a sequence of bytes, plus representation metadata to describe those bytes. The particular form of the representation can be negotiated between REST components. [RP 3] All interactions are context-free: each interaction contains all of the information necessary to understand the request, independent of any requests that may have preceded it. 9
![Software Architecture Foundations Theory and Practice REST Principles contd l RP 4 Components perform Software Architecture: Foundations, Theory, and Practice REST Principles (cont’d) l [RP 4] Components perform](https://slidetodoc.com/presentation_image_h2/6bf1202fbf5dede1008a36bf87a0813a/image-10.jpg)
Software Architecture: Foundations, Theory, and Practice REST Principles (cont’d) l [RP 4] Components perform only a small set of welldefined methods on a resource producing a representation to capture the current or intended state of that resource and transfer that representation between components. These methods are global to the specific architectural instantiation of REST; for instance, all resources exposed via HTTP are expected to support each operation identically. 10
![Software Architecture Foundations Theory and Practice REST Principles contd l l RP 5 Idempotent Software Architecture: Foundations, Theory, and Practice REST Principles (cont’d) l l [RP 5] Idempotent](https://slidetodoc.com/presentation_image_h2/6bf1202fbf5dede1008a36bf87a0813a/image-11.jpg)
Software Architecture: Foundations, Theory, and Practice REST Principles (cont’d) l l [RP 5] Idempotent operations and representation metadata are encouraged in support of caching and representation reuse. [RP 6] The presence of intermediaries is promoted. Filtering or redirection intermediaries may also use both the metadata and the representations within requests or responses to augment, restrict, or modify requests and responses in a manner that is transparent to both the user agent and the origin server. 11

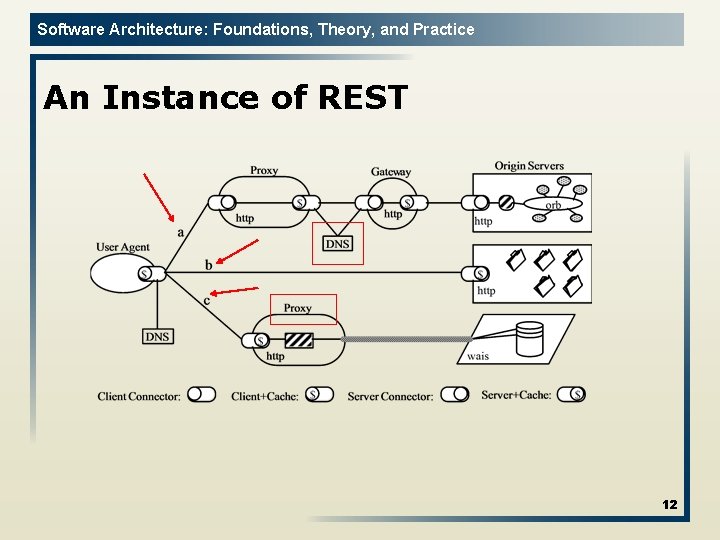
Software Architecture: Foundations, Theory, and Practice An Instance of REST 12

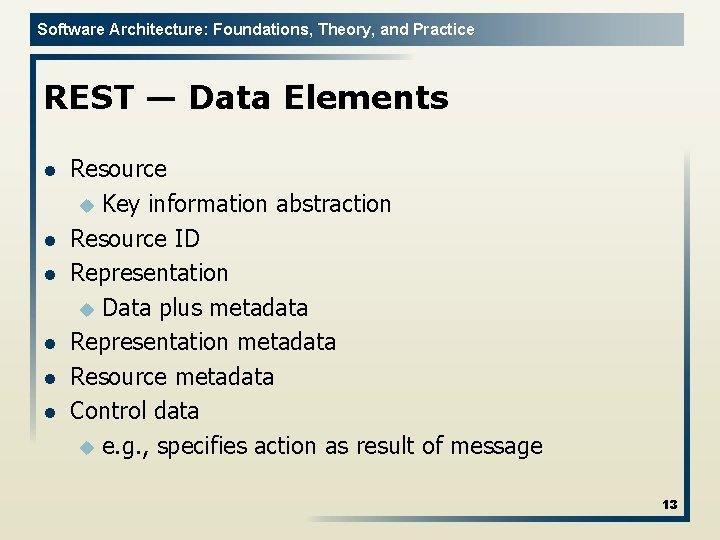
Software Architecture: Foundations, Theory, and Practice REST — Data Elements l l l Resource u Key information abstraction Resource ID Representation u Data plus metadata Representation metadata Resource metadata Control data u e. g. , specifies action as result of message 13

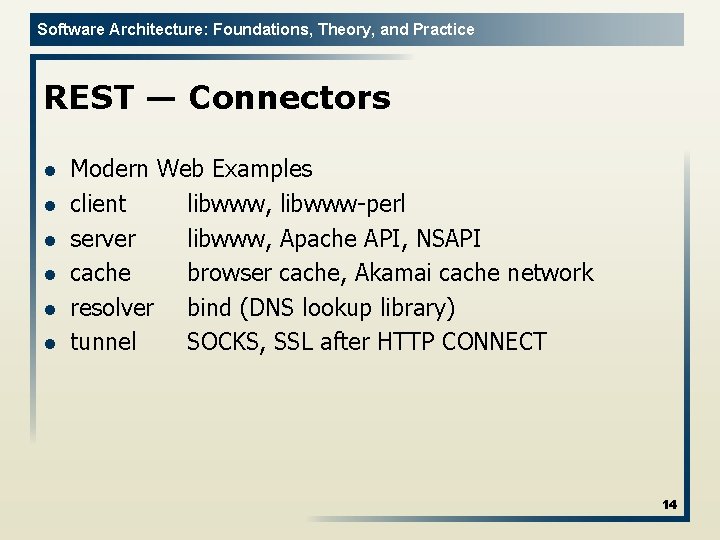
Software Architecture: Foundations, Theory, and Practice REST — Connectors l l l Modern Web Examples client libwww, libwww-perl server libwww, Apache API, NSAPI cache browser cache, Akamai cache network resolver bind (DNS lookup library) tunnel SOCKS, SSL after HTTP CONNECT 14

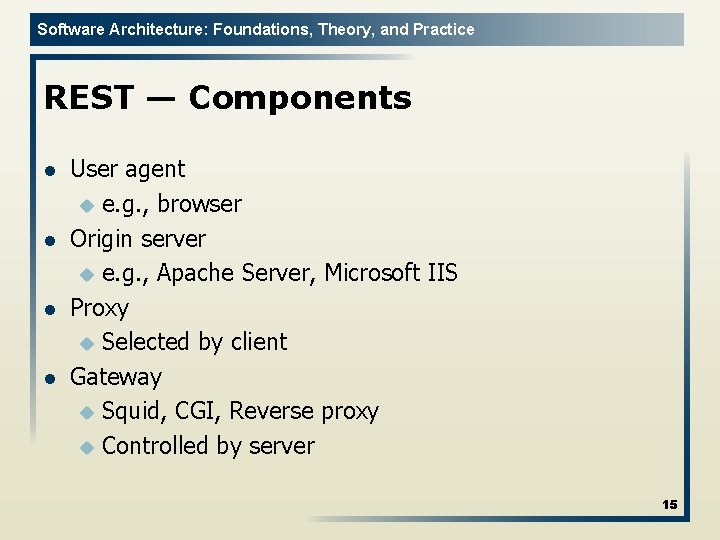
Software Architecture: Foundations, Theory, and Practice REST — Components l l User agent u e. g. , browser Origin server u e. g. , Apache Server, Microsoft IIS Proxy u Selected by client Gateway u Squid, CGI, Reverse proxy u Controlled by server 15

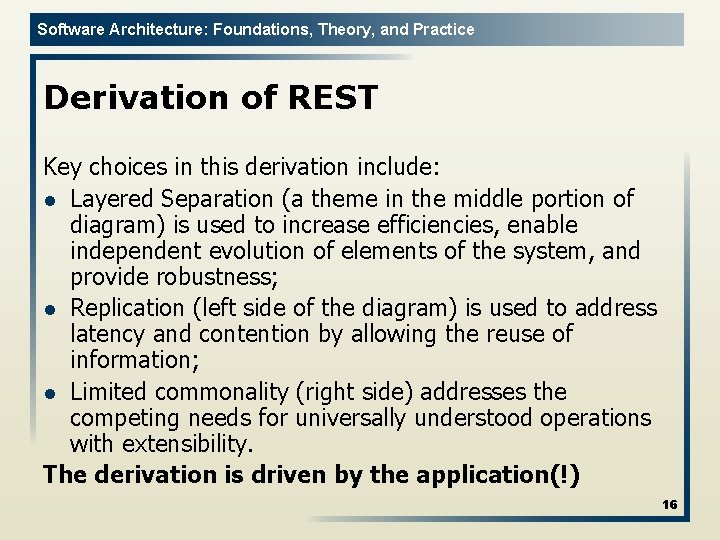
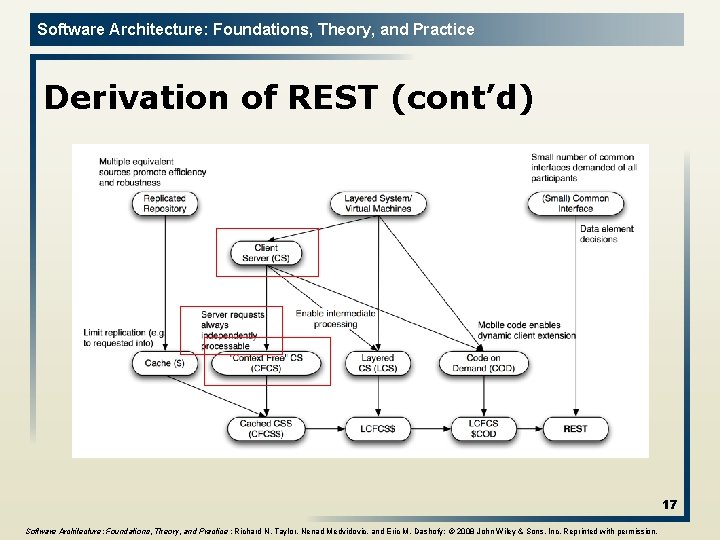
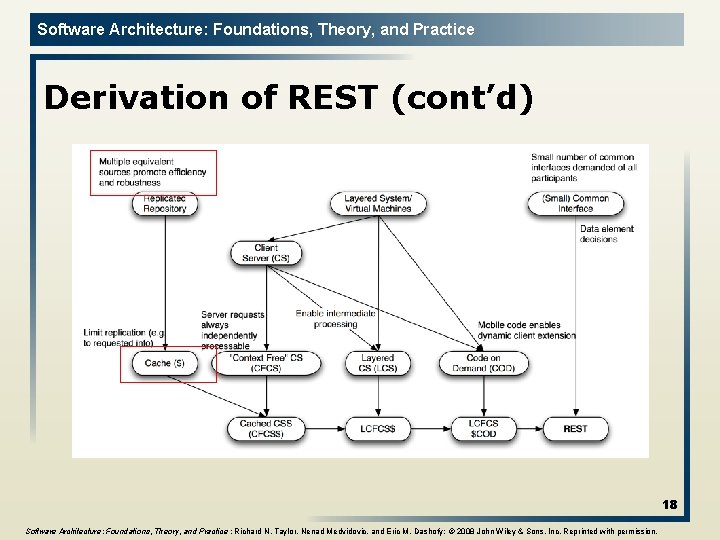
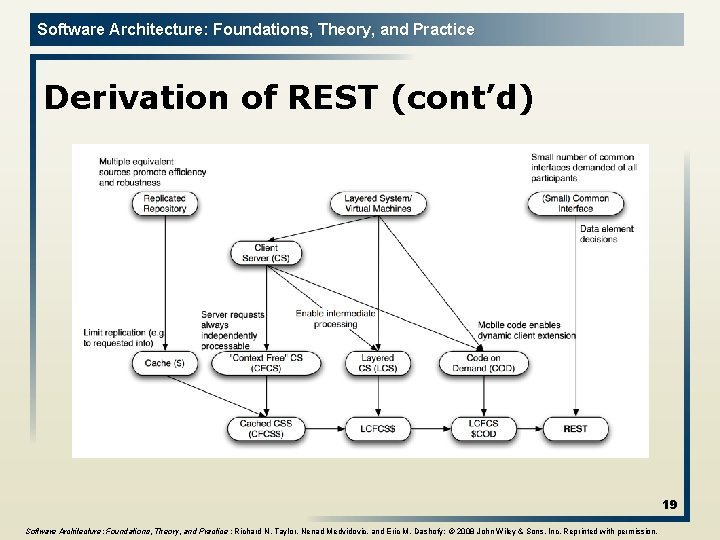
Software Architecture: Foundations, Theory, and Practice Derivation of REST Key choices in this derivation include: l Layered Separation (a theme in the middle portion of diagram) is used to increase efficiencies, enable independent evolution of elements of the system, and provide robustness; l Replication (left side of the diagram) is used to address latency and contention by allowing the reuse of information; l Limited commonality (right side) addresses the competing needs for universally understood operations with extensibility. The derivation is driven by the application(!) 16

Software Architecture: Foundations, Theory, and Practice Derivation of REST (cont’d) 17 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture: Foundations, Theory, and Practice Derivation of REST (cont’d) 18 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture: Foundations, Theory, and Practice Derivation of REST (cont’d) 19 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture: Foundations, Theory, and Practice REST: Final Thoughts l l l REpresentational State Transfer Style of modern web architecture u Web architecture one of many in style Web diverges from style on occasion u e. g. , Cookies, frames u Doesn’t explain mashups 20

Software Architecture: Foundations, Theory, and Practice Commercial Internet-Scale Applications l l Akamai u Caching to the max Google u Google distributed file system (GFS) u Map. Reduce l Data selection and reduction l All parallelization done automatically 21

Software Architecture: Foundations, Theory, and Practice Architectural Lessons from Google l l l Abstraction layers abound: GFS hides details of data distribution and failure, for instance; Map. Reduce hides the intricacies of parallelizing operations; By designing, from the outset, for living with failure of processing, storage, and network elements, a highly robust system can be created; Scale is everything: Google’s business demands that everything be built with scaling issues in mind; 22

Software Architecture: Foundations, Theory, and Practice Architectural Lessons from Google (cont’d) l l By specializing the design to the problem domain, rather than taking the generic “industry standard” approach, high performance and very cost-effective solutions can be developed; By developing a general approach (Map. Reduce) to the data extraction/reduction problem, a highly reusable service was created. 23

Software Architecture: Foundations, Theory, and Practice Decentralized Architectures l l Networked applications where there are multiple authorities In other words u Computation is distributed u Parts of the network may behave differently, and vary over time It’s just like collaboration in the real world 24

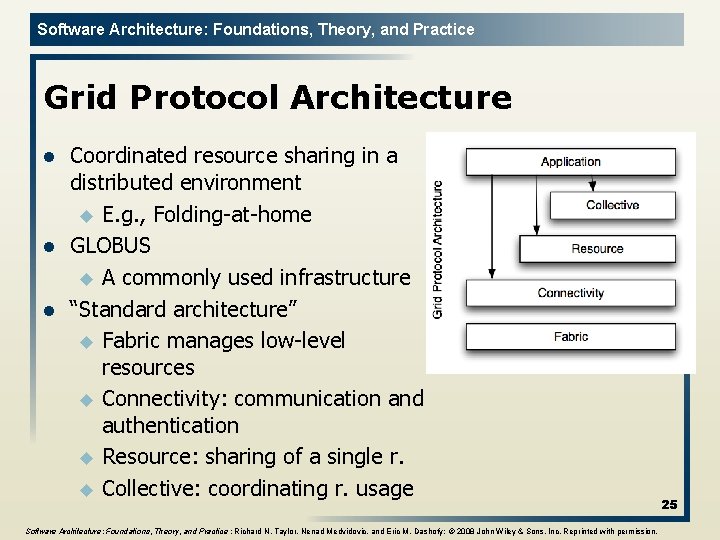
Software Architecture: Foundations, Theory, and Practice Grid Protocol Architecture l l l Coordinated resource sharing in a distributed environment u E. g. , Folding-at-home GLOBUS u A commonly used infrastructure “Standard architecture” u Fabric manages low-level resources u Connectivity: communication and authentication u Resource: sharing of a single r. u Collective: coordinating r. usage Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission. 25

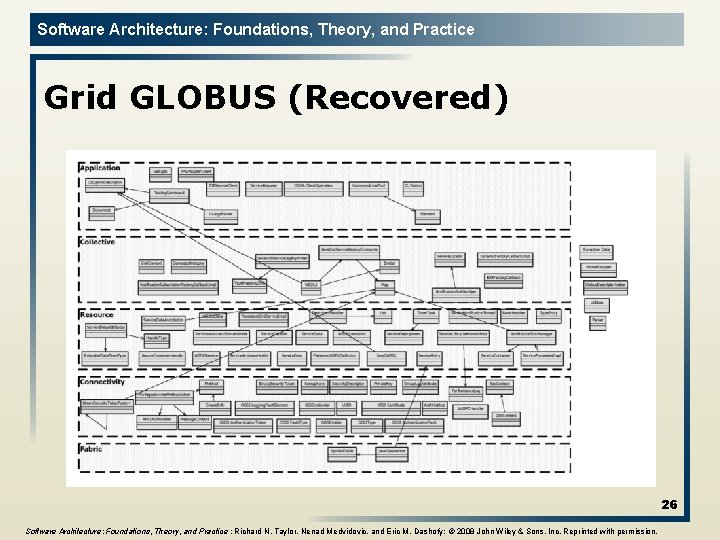
Software Architecture: Foundations, Theory, and Practice Grid GLOBUS (Recovered) 26 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture: Foundations, Theory, and Practice Peer-to-Peer Architectures l l Decentralized resource sharing and discovery u Napster u Gnutella P 2 P that works: Skype u And Bit. Torrent 27

Software Architecture: Foundations, Theory, and Practice Peer-to-Peer Style l l l State and behavior are distributed among peers which can act as either clients or servers. Peers: independent components, having their own state and control thread. Connectors: Network protocols, often custom. Data Elements: Network messages Topology: Network (may have redundant connections between peers); can vary arbitrarily and dynamically Supports decentralized computing with flow of control and resources distributed among peers. Highly robust in the face of failure of any given node. Scalable in terms of access to resources and computing power. But caution on the protocol! 28

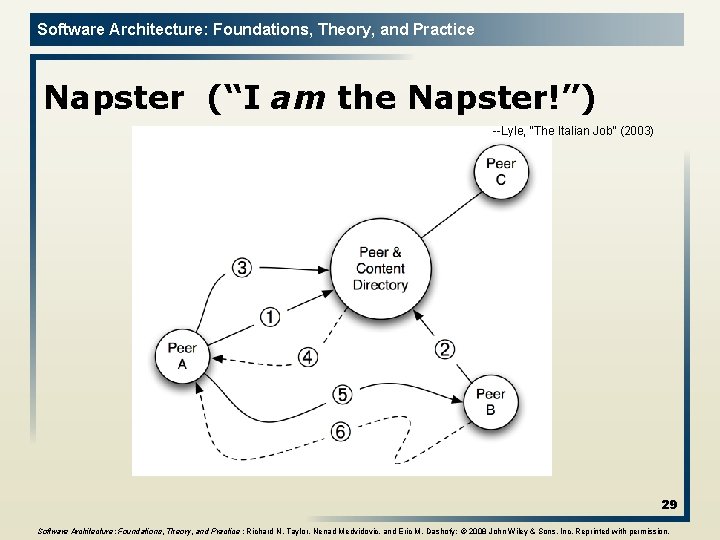
Software Architecture: Foundations, Theory, and Practice Napster (“I am the Napster!”) --Lyle, “The Italian Job” (2003) 29 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

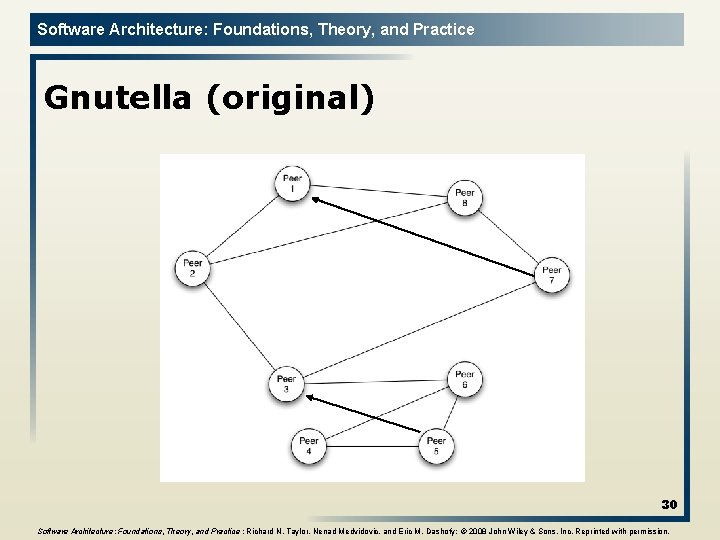
Software Architecture: Foundations, Theory, and Practice Gnutella (original) 30 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

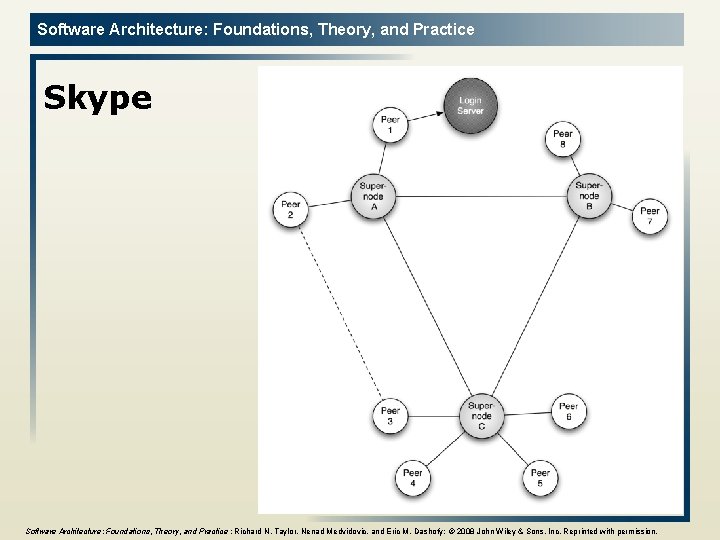
Software Architecture: Foundations, Theory, and Practice Skype 31 Software Architecture: Foundations, Theory, and Practice ; Richard N. Taylor, Nenad Medvidovic, and Eric M. Dashofy; © 2008 John Wiley & Sons, Inc. Reprinted with permission.

Software Architecture: Foundations, Theory, and Practice Insights from Skype l l l A mixed client-server and peer-to-peer architecture addresses the discovery problem. Replication and distribution of the directories, in the form of supernodes, addresses the scalability problem and robustness problem encountered in Napster. Promotion of ordinary peers to supernodes based upon network and processing capabilities addresses another aspect of system performance: “not just any peer” is relied upon for important services. A proprietary protocol employing encryption provides privacy for calls that are relayed through supernode intermediaries. Restriction of participants to clients issued by Skype, and making those clients highly resistant to inspection or modification, prevents malicious clients from entering the network. 32

Software Architecture: Foundations, Theory, and Practice Insights from Bit. Torrent l l l Responsibility for the discovery of content is outside scope of Bit. Torrent. Use web searches to find content. A designated machine, called a tracker, is used to oversee the process by which a file is distributed to interested peers. Tracker performs no data transfer. Only used to identify other peers Meta-data is associated with the file and is used in download process. Describes how the large file is “pieced”, the attributes of those pieces, and location of the tracker. 33

Software Architecture: Foundations, Theory, and Practice More Insights from Bit. Torrent l l Each peer runs a Bit. Torrent application (Azure, u. Torrent, etc. ). Application determines what piece of the file to download next and which peer to obtain that piece from. All participating peers maintain knowledge of which peers have which pieces. The algorithms designed for the fastest delivery of the file. Peers that do not upload are penalized through deprioritization of access to the pieces they need 34