Applications of Quantum Cryptography QKD CS 551851 CRyptography















- Slides: 27

Applications of Quantum Cryptography – QKD CS 551/851 CRyptography. Applications. Bistro Mike Mc. Nett 6 April 2004 Paper: Chip Elliott, David Pearson, and Gregory Troxel. “Quantum Cryptography in Practice”

Outline • • Basics of QKD History of QKD Protocols for QKD BB 84 Protocol DARPA / BBN Implementation Other Implementations Pro’s & Con’s Conclusion

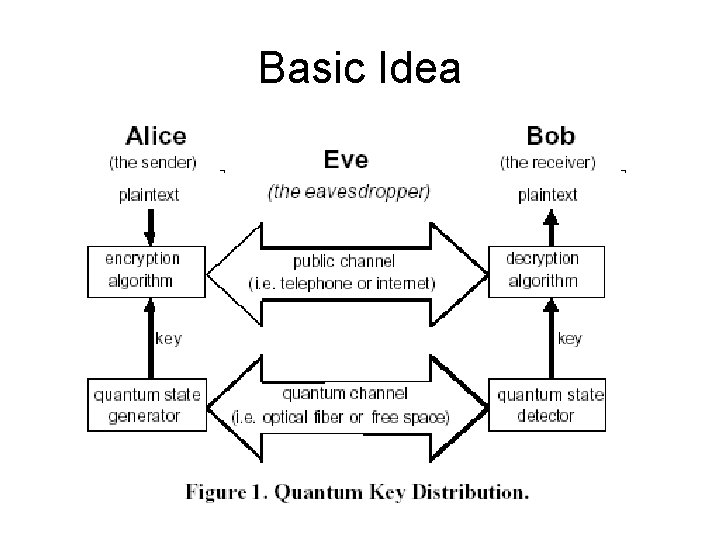
Quantum Cryptography • Better Name – Quantum Key Distribution (QKD) – It’s NOT a new crypto algorithm! • Two physically separated parties can create and share random secret keys. • Allows them to verify that the key has not been intercepted.

Basic Idea

History of QKD • Stephen Wiesner – early 1970 s wrote paper "Conjugate Coding” • Paper by Charles Bennett and Gilles Brassard in 1984 is the basis for QKD protocol BB 84. Prototype developed in 1991. • Another QKD protocol was invented independently by Artur Ekert in 1991.

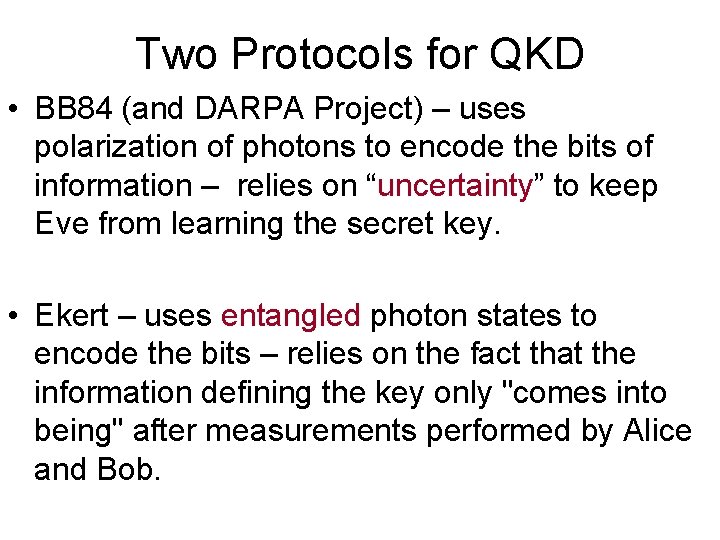
Two Protocols for QKD • BB 84 (and DARPA Project) – uses polarization of photons to encode the bits of information – relies on “uncertainty” to keep Eve from learning the secret key. • Ekert – uses entangled photon states to encode the bits – relies on the fact that the information defining the key only "comes into being" after measurements performed by Alice and Bob.

BB 84 • Original Paper: Bennett: “Quantum cryptography using any two nonorthogonal states”, Physical Review Letters, Vol. 68, No. 21, 25 May 1992, pp 3121 -3124

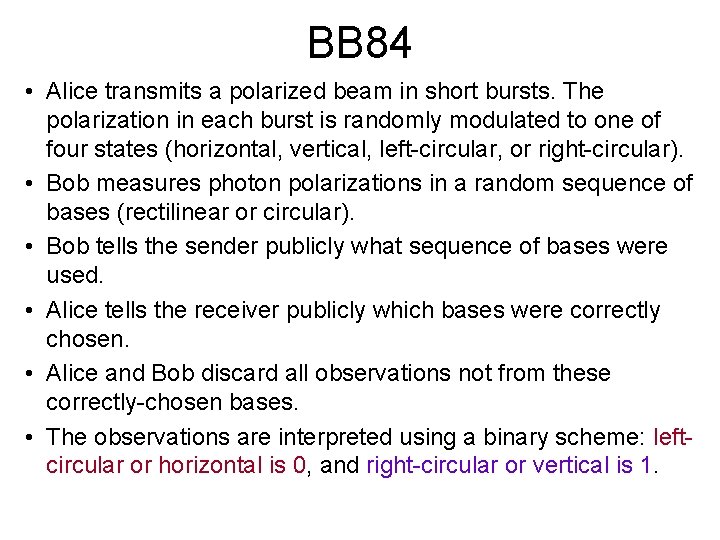
BB 84 • Alice transmits a polarized beam in short bursts. The polarization in each burst is randomly modulated to one of four states (horizontal, vertical, left-circular, or right-circular). • Bob measures photon polarizations in a random sequence of bases (rectilinear or circular). • Bob tells the sender publicly what sequence of bases were used. • Alice tells the receiver publicly which bases were correctly chosen. • Alice and Bob discard all observations not from these correctly-chosen bases. • The observations are interpreted using a binary scheme: leftcircular or horizontal is 0, and right-circular or vertical is 1.

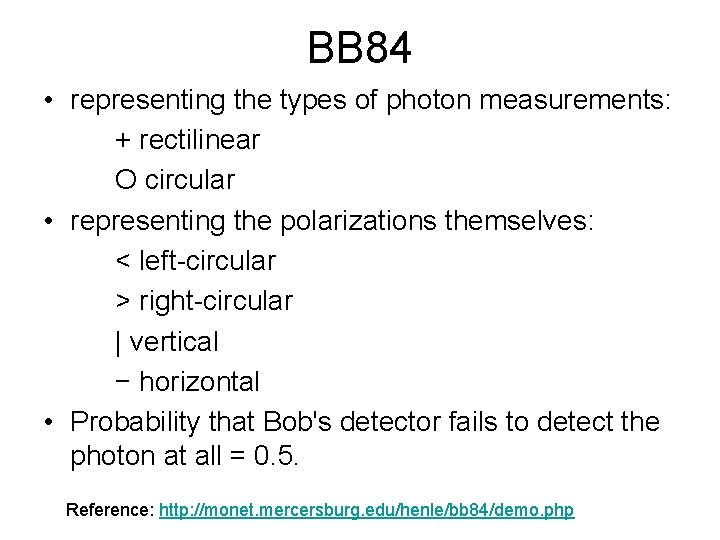
BB 84 • representing the types of photon measurements: + rectilinear O circular • representing the polarizations themselves: < left-circular > right-circular | vertical − horizontal • Probability that Bob's detector fails to detect the photon at all = 0. 5. Reference: http: //monet. mercersburg. edu/henle/bb 84/demo. php

BB 84 – No Eavesdropping • A B: |<−−−<<−−<>>−<>||−−< • Bob randomly decides detector: ++++O+O+OO+O+++++O+O • For each measurement, P(failure to detect photon) = 0. 5 • The results of Bob's measurements are: − >− −<< ||| • B A: types of detectors used and successfully made (but not the measurements themselves): + O+ +OO +++ • Alice tells Bob which measurements were of the correct type: . . (key = 0 0 0 1) • Bob only makes the same kind of measurement as Alice about half the time. Given that the P(B detector fails) = 0. 5, you would expect about 5 out of 20 usable shared digits to remain. In fact, this time there were 4 usable digits generated.

BB 84 – With Eavesdropping • A B: <|<−>−<<|<><−<|<−|−< • Eavesdropping occurs. To detect eavesdropping: • Bob only makes the same kind of measurement as Alice about half the time. Given that the P(B detector fails) = 0. 5, you would expect about 5 out of 20 usable shared digits to remain. • A B: reveals 50% (randomly) of the shared digits. • B A: reveals his corresponding check digits. • If > 25% of the check digits are wrong, Alice and Bob know that somebody (Eve) was listening to their exchange. • NOTE – 20 photons doesn’t provide good guarantees of detection.

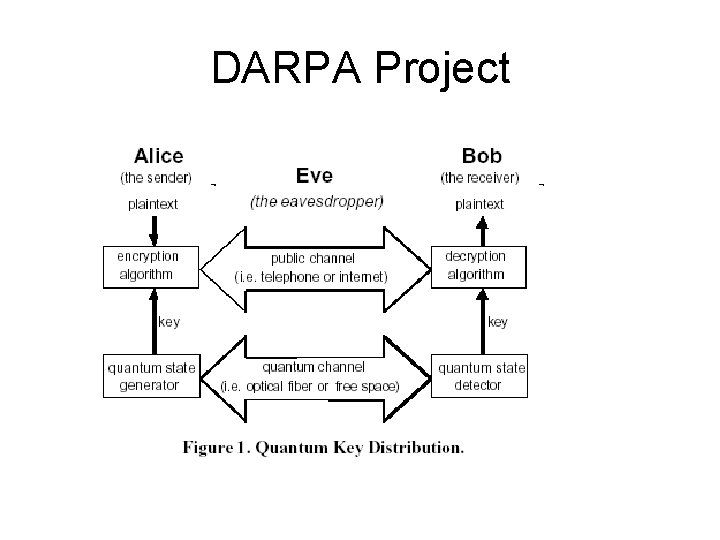
DARPA Project

DARPA Project Overview • Combined Effort – BBN, Harvard, Boston University • DARPA Project • Provides “high speed” QKD. Keys are used by a VPN. • Tests against eavesdropping attacks

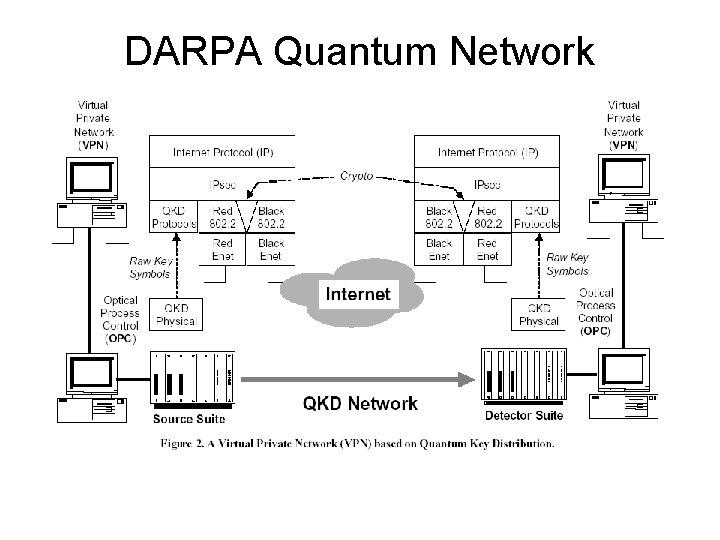
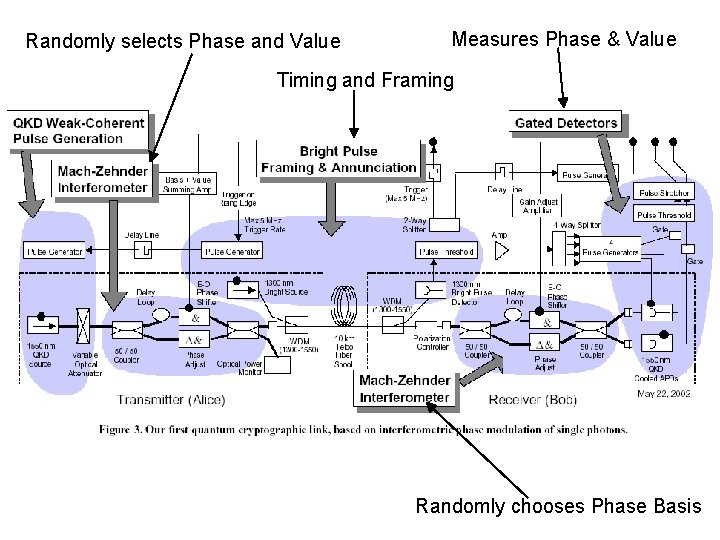
DARPA Project Overview • QKD Network – Requires a set of trusted network relays • Uses Phase Shifting instead of Polarization • Uses a VPN – Uses QKD to generate VPN keys • Fully compatible with conventional hosts, routers, firewalls, etc. • Quantum Channel also used for timing and framing • Eve is very capable – just can’t violate Quantum Physics

QKD Attributes • Key Confidentiality • Authentication – Not directly provided by QKD – need alternative methods • “Sufficiently” Rapid Key Delivery • Robustness • Distance (and Location) Independence • Resistant to Traffic Analysis

DARPA Quantum Network

Randomly selects Phase and Value Measures Phase & Value Timing and Framing Randomly chooses Phase Basis

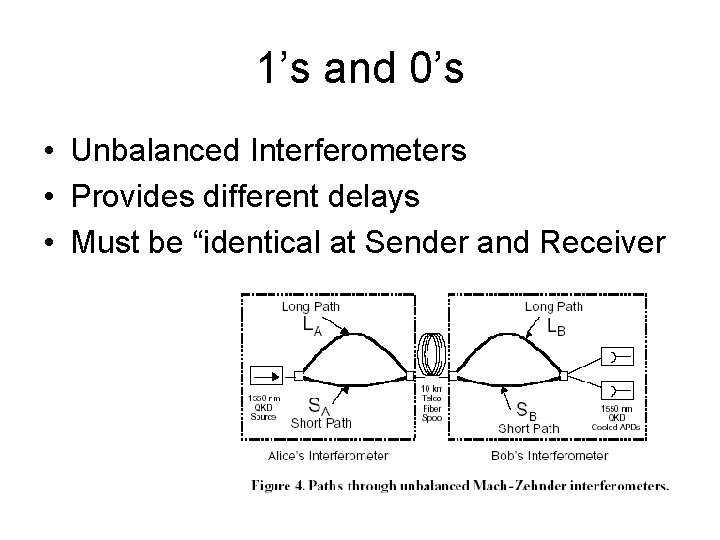
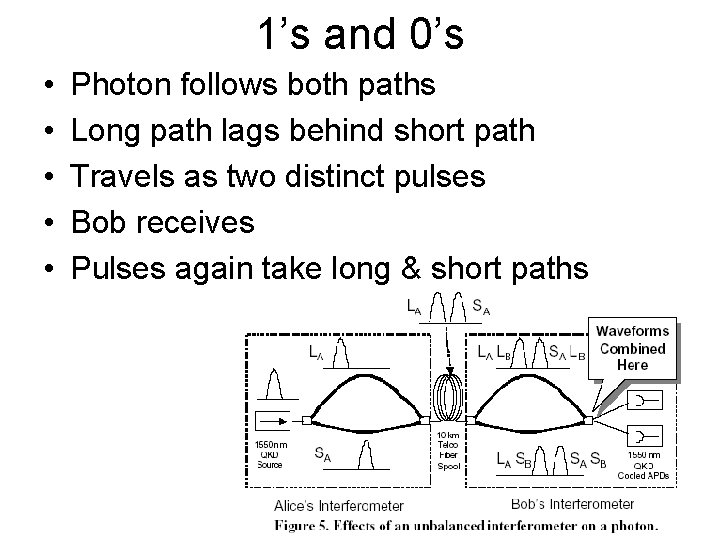
1’s and 0’s • Unbalanced Interferometers • Provides different delays • Must be “identical at Sender and Receiver

1’s and 0’s • • • Photon follows both paths Long path lags behind short path Travels as two distinct pulses Bob receives Pulses again take long & short paths

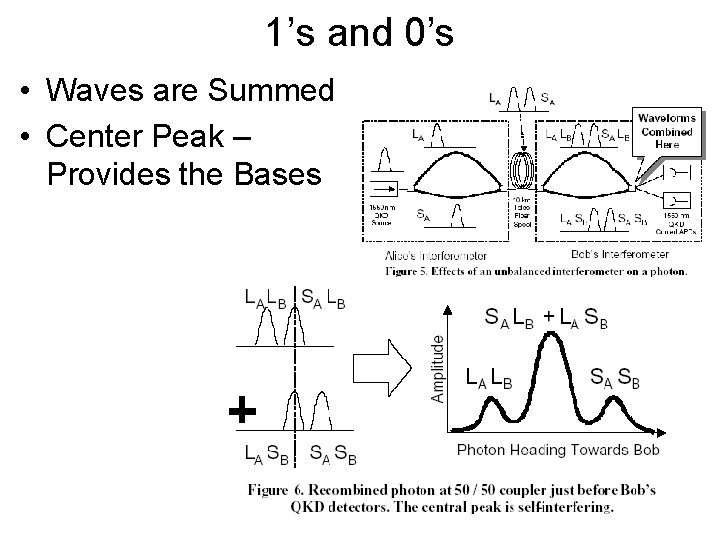
1’s and 0’s • Waves are Summed • Center Peak – Provides the Bases

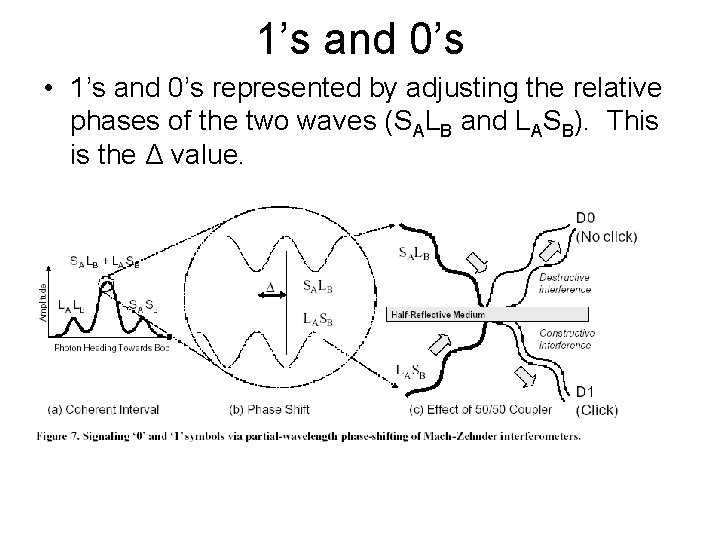
1’s and 0’s • 1’s and 0’s represented by adjusting the relative phases of the two waves (SALB and LASB). This is the Δ value.

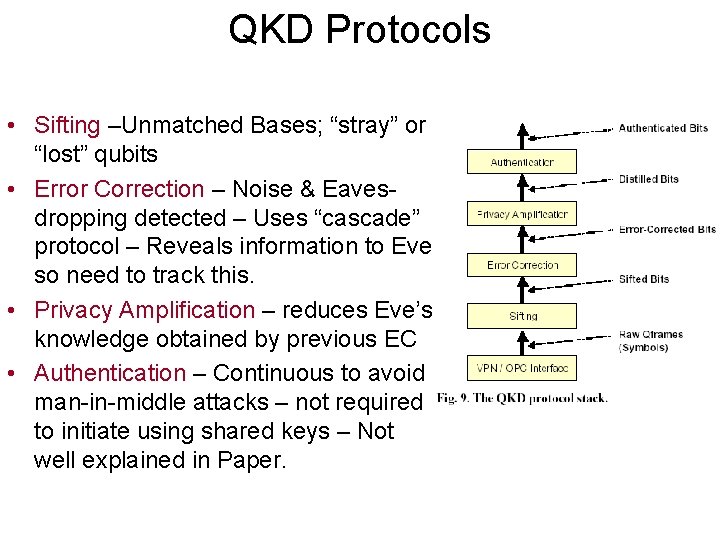
QKD Protocols • Sifting –Unmatched Bases; “stray” or “lost” qubits • Error Correction – Noise & Eavesdropping detected – Uses “cascade” protocol – Reveals information to Eve so need to track this. • Privacy Amplification – reduces Eve’s knowledge obtained by previous EC • Authentication – Continuous to avoid man-in-middle attacks – not required to initiate using shared keys – Not well explained in Paper.

IPSEC • “Continually” uses new keys obtained from QKD • Used in IPSEC Phase 2 hash to update AES keys about once / minute • Can support: – Rapid reseeding, or – One-time pad • Supports multiple tunnels, each uniquely configured

Issues • Time outs (due to insufficient bits available) • Noise affects on key establishment. This can’t be detected by IKE.

Other Implementations • Two Other Implementations of Quantum Key Distribution: – D Stucki, N Gisin, O Guinnard, G Ribordy, and H Zbinden. Quantum key distribution over 67 km with a plug&play system. New Journal of Physics 4 (2002) 41. 1– 41. 8. – ID Quantine: http: //www. idquantique. com/files/introduction. pdf • Magi. Q. Whitepaper: http: //www. magiqtech. com/registration/Magi. QWhite. Pape r. pdf • Satellite-based QKD: http: //ej. iop. org/links/q 68/BKUv. FWVrm 756, uxc 76 l. U, Q/nj 2182. pdf

Pros & Cons • Nearly Impossible to steal • Detect if someone is listening • “Secure” • Distance Limitations • Availability – vulnerable to DOS – keys can’t keep up with plaintext

Questions? • Back to Richard!