Applications and Use Cases for the Quantum Internet




- Slides: 11

Applications and Use Cases for the Quantum Internet https: //www. ietf. org/id/draft-wang-qirg-quantum-internet-use-cases-05. txt Chonggang Wang, Akbar Rahman, Ruidong Li IETF Interim Meeting, QIRG, April 8, 2020

Background of Present I-D • v 00 was initiated on January 15, 2020 – https: //tools. ietf. org/id/draft-wang-qirg-quantum-internet-use-cases-00. txt • Since then, we have received many constructive comments and feedback, which were used to generate the present v 05 • Thanks to the following people in an alphabetical order for their valuable input – Melchior Aelmans – Mathias Van Den Bossche – Xavier de Foy – Patrick Gelard – Wojciech Kozlowski – Rodney Van Meter – Joseph Touch IETF, Interim Meeting, April 2020 draft-wang-qirg-quantum-internet-use-cases-05 2

Main Content in Present I-D • Quantum Internet Applications – Classification by Application Usage • Quantum Cryptography Applications • Quantum Sensor Applications • Quantum Computing Applications – Control vs Data Plane Classification • Control Plane Applications • Data Plane Applications • Selected Quantum Internet Use Cases • General Requirements IETF, Interim Meeting, April 2020 draft-wang-qirg-quantum-internet-use-cases-05 3

Quantum Cryptography Applications • Refers to the use of quantum information technology to ensure secure communications: – Secure communication setup: Refers to secure cryptographic key distribution between two or more end-nodes • The most well-known method is referred to as Quantum Key Distribution (QKD) – Fast Byzantine negotiation: Refers to a quantum network based method for fast agreement in Byzantine negotiations • This can be used for the popular financial blockchain feature as well as other distributed computing features which use Byzantine negotiations IETF, Interim Meeting, April 2020 draft-wang-qirg-quantum-internet-use-cases-05 4

Quantum Sensor Applications • Refers to the use of quantum information technology for supporting distributed sensors or Internet of Things (Io. T) devices (e. g. , clock synchronization): – Network clock synchronization: Refers to a world wide set of atomic clocks connected by the Quantum Internet to achieve an ultra precise clock signal IETF, Interim Meeting, April 2020 draft-wang-qirg-quantum-internet-use-cases-05 5

Quantum Computing Applications • Refers to the use of quantum information technology for supporting remote quantum computing facilities (e. g. , distributed quantum computing): – Distributed quantum computing: Refers to a collection of remote small capacity quantum computers (i. e. , each supporting a few qubits) that are connected and working together in a coordinated fashion so as to simulate a virtual large capacity quantum computer – Secure quantum computing with privacy preservation: Refers to private, or blind, quantum computation, which provides a way for a client to delegate a computation task to one or more remote quantum computers without disclosing the source data to be computed over IETF, Interim Meeting, April 2020 draft-wang-qirg-quantum-internet-use-cases-05 6

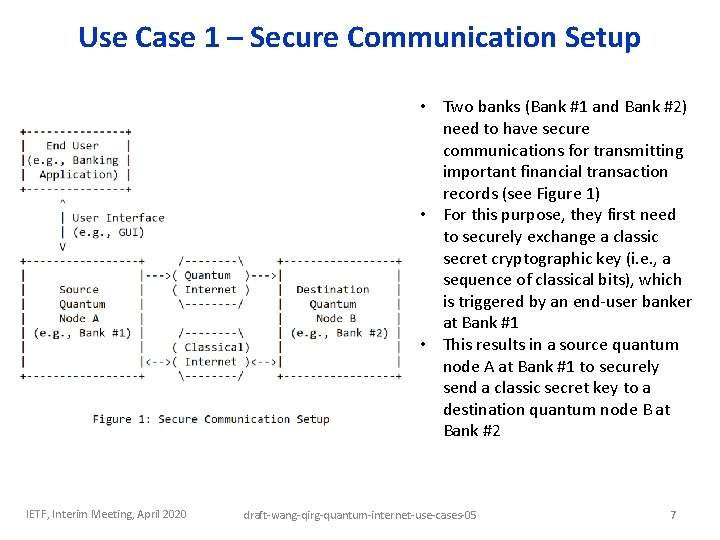
Use Case 1 – Secure Communication Setup • Two banks (Bank #1 and Bank #2) need to have secure communications for transmitting important financial transaction records (see Figure 1) • For this purpose, they first need to securely exchange a classic secret cryptographic key (i. e. , a sequence of classical bits), which is triggered by an end-user banker at Bank #1 • This results in a source quantum node A at Bank #1 to securely send a classic secret key to a destination quantum node B at Bank #2 IETF, Interim Meeting, April 2020 draft-wang-qirg-quantum-internet-use-cases-05 7

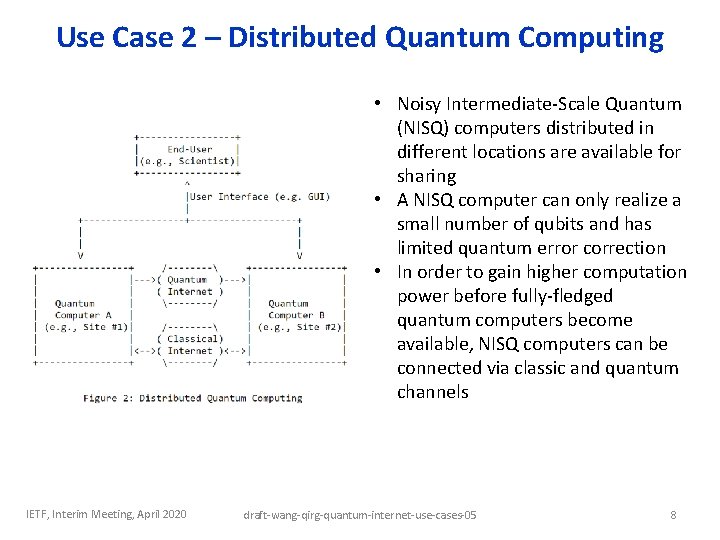
Use Case 2 – Distributed Quantum Computing • Noisy Intermediate-Scale Quantum (NISQ) computers distributed in different locations are available for sharing • A NISQ computer can only realize a small number of qubits and has limited quantum error correction • In order to gain higher computation power before fully-fledged quantum computers become available, NISQ computers can be connected via classic and quantum channels IETF, Interim Meeting, April 2020 draft-wang-qirg-quantum-internet-use-cases-05 8

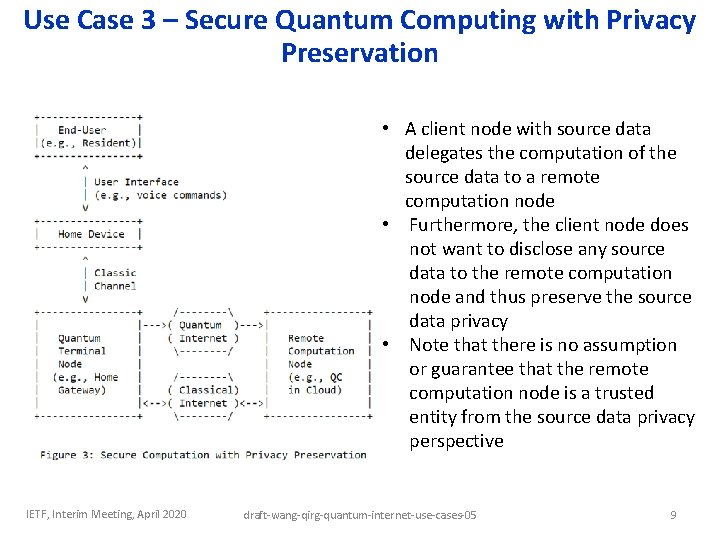
Use Case 3 – Secure Quantum Computing with Privacy Preservation • A client node with source data delegates the computation of the source data to a remote computation node • Furthermore, the client node does not want to disclose any source data to the remote computation node and thus preserve the source data privacy • Note that there is no assumption or guarantee that the remote computation node is a trusted entity from the source data privacy perspective IETF, Interim Meeting, April 2020 draft-wang-qirg-quantum-internet-use-cases-05 9

General Requirements 1) Methods for facilitating quantum applications to interact efficiently with entanglement qubits are necessary 2) Quantum repeaters/routers should support robust and efficient entanglement distribution 3) Quantum end-nodes must send additional information on classical channels to aid in transmission of qubits across quantum repeaters/receivers TO-DO: Some performance indicators need to be defined and described, for instance, the tolerance to lower fidelity of the qubits, etc. IETF, Interim Meeting, April 2020 draft-wang-qirg-quantum-internet-use-cases-05 10

Next Steps • Address a few pending comments from Melchior Aelmans and Mathias Van Den Bossche – “Control Plane vs Data Plane” – “General Requirements” • Continue to collect feedback from QIRG and improve the present I-D • Questions for QIRG – How much details should be given in this I-D for performance indicators? • e. g. , just a few high level metrics? – Is this I-D ready for WG adoption? IETF, Interim Meeting, April 2020 draft-wang-qirg-quantum-internet-use-cases-05 11