Application Security Models for Mobile Agent Systems The

Application Security Models for Mobile Agent Systems The 1 st International Workshop on Security and Trust Management (STM’ 05) Sept 15, 2005 Milan, Italy J. Todd Mc. Donald Alec Yasinsac Department of Computer Science Florida State University 1

Overview n n Motivation Defining mobile agent trust Defining trust-enhanced security Defining application security models q q q n Military model Trade model Neutral-services model Questions 2

Motivation n Defining Security q q n Defining Trust q q q n Requirements = Confidentiality, integrity, authentication… Mechanisms = Enforce security requirements Subjective non-Boolean expectation of behavior Non-reflexive, changing, context-driven Acquired or delegated Using Trust with Mobile Agent Security q q Consider all mobile agent principals Link requirements to mechanisms Reason about trust for generic mechanisms Initialize trust model based on context 3

Overview n n Motivation Defining mobile agent trust Defining trust-enhanced security Defining application security models q q q n Military model Trade model Neutral-services model Questions 4
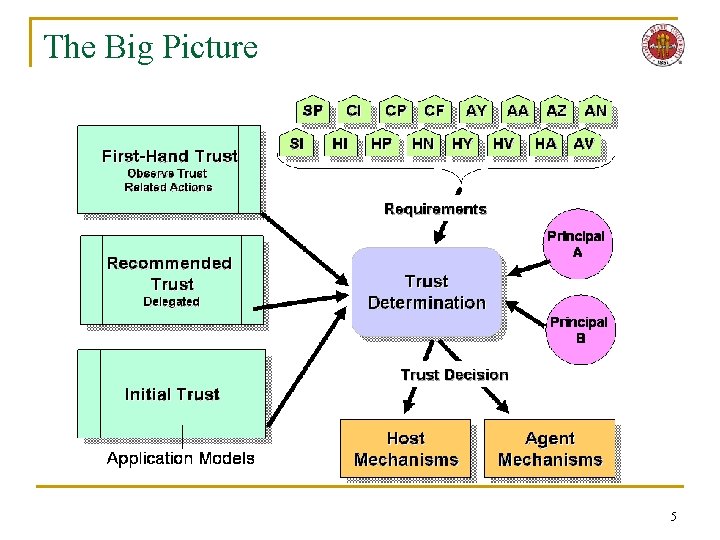
The Big Picture 5
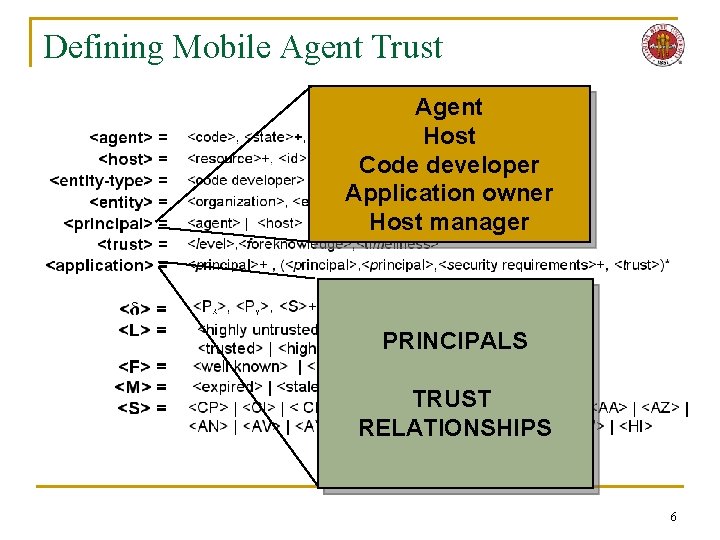
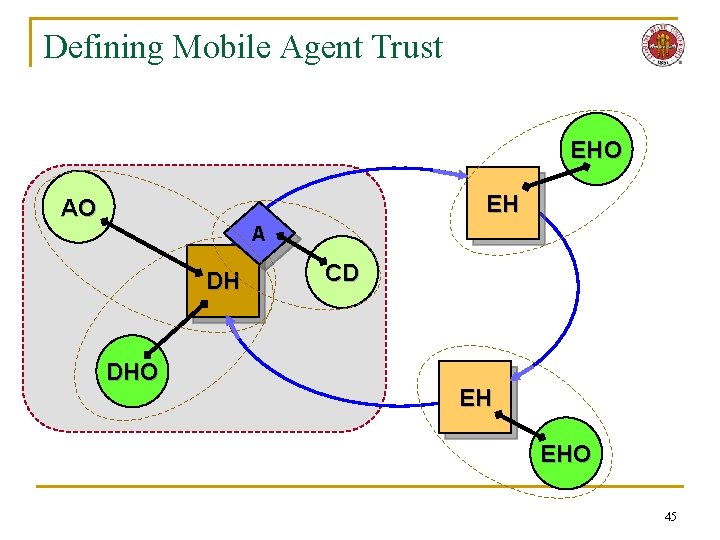
Defining Mobile Agent Trust Agent Host Code developer Application owner Host manager PRINCIPALS TRUST RELATIONSHIPS 6
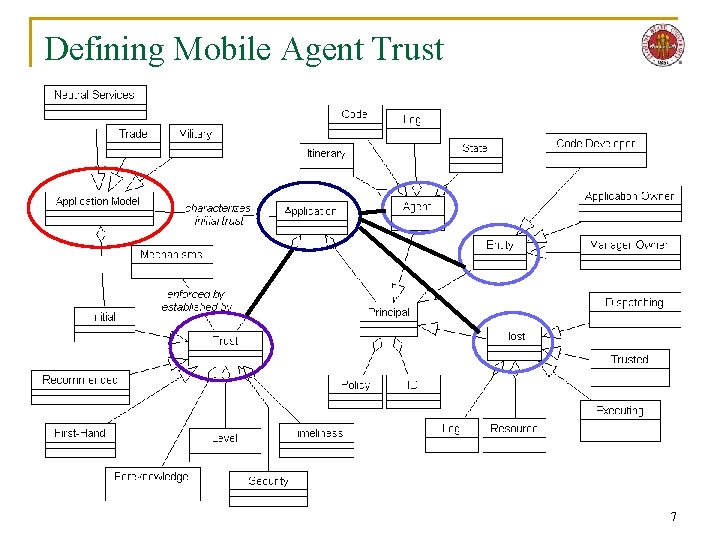
Defining Mobile Agent Trust 7
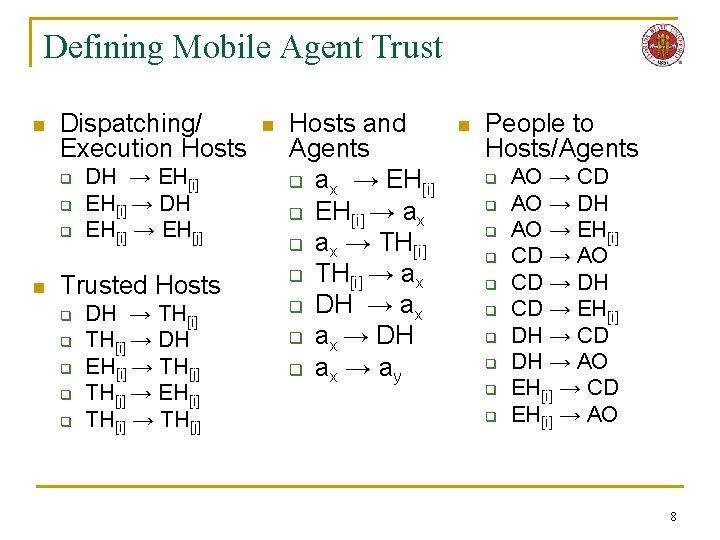
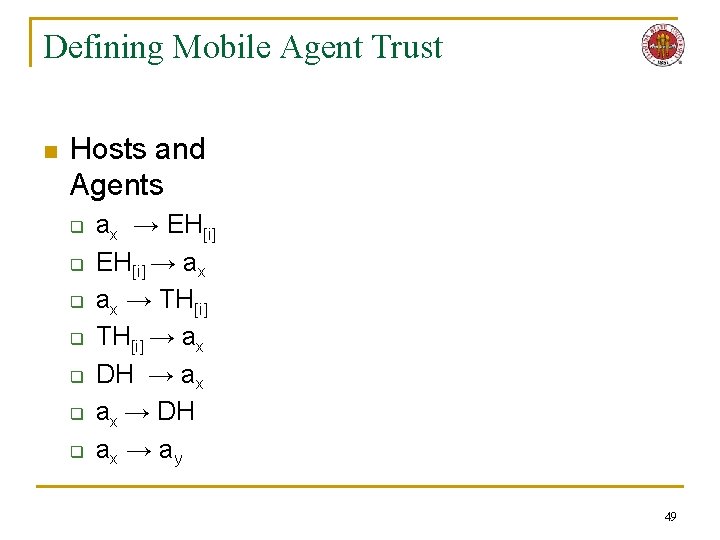
Defining Mobile Agent Trust n Dispatching/ Execution Hosts q q q n DH → EH[i] → DH EH[i] → EH[j] Trusted Hosts q q q DH → TH[i] → DH EH[i] → TH[j] → EH[i] TH[i] → TH[j] n Hosts and Agents q ax → EH[i] q EH[i] → ax q ax → TH[i] q TH[i] → ax q DH → ax q ax → DH q ax → a y n People to Hosts/Agents q q q q q AO → CD AO → DH AO → EH[i] CD → AO CD → DH CD → EH[i] DH → CD DH → AO EH[i] → CD EH[i] → AO 8
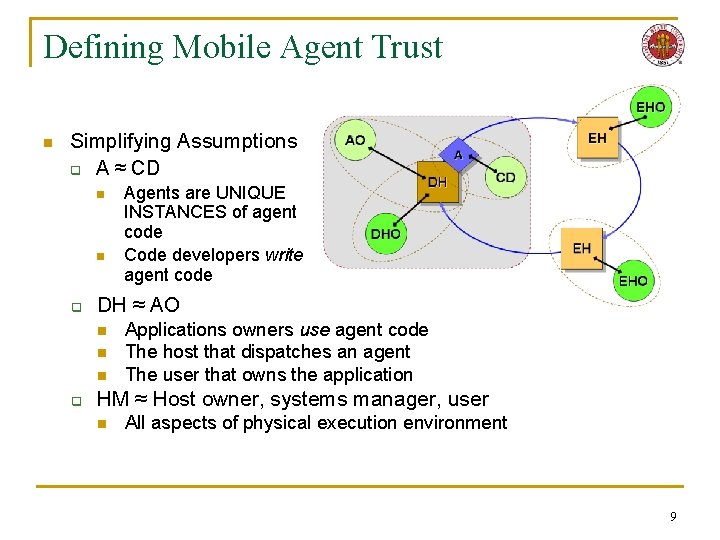
Defining Mobile Agent Trust n Simplifying Assumptions q A ≈ CD n n q DH ≈ AO n n n q Agents are UNIQUE INSTANCES of agent code Code developers write agent code Applications owners use agent code The host that dispatches an agent The user that owns the application HM ≈ Host owner, systems manager, user n All aspects of physical execution environment 9
Overview n n Motivation Defining mobile agent trust Defining trust-enhanced security Defining application security models q q q n Military model Trade model Neutral-services model Questions 10
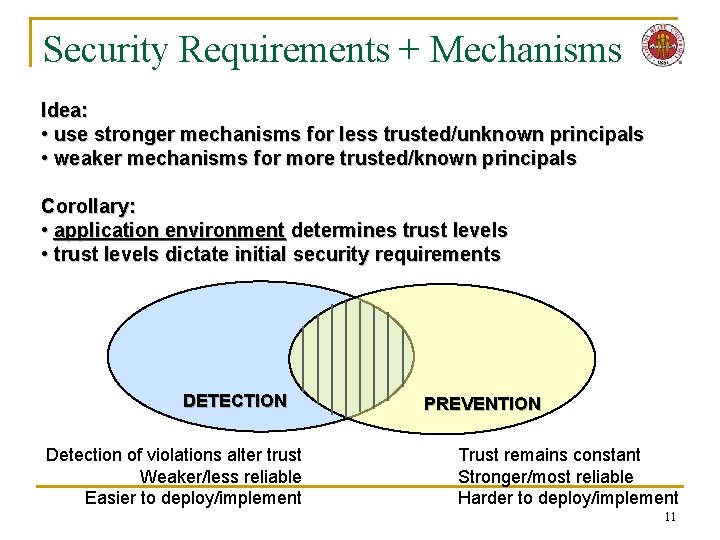
Security Requirements + Mechanisms Idea: • use stronger mechanisms for less trusted/unknown principals • weaker mechanisms for more trusted/known principals Corollary: • application environment determines trust levels • trust levels dictate initial security requirements DETECTION Detection of violations alter trust Weaker/less reliable Easier to deploy/implement PREVENTION Trust remains constant Stronger/most reliable Harder to deploy/implement 11
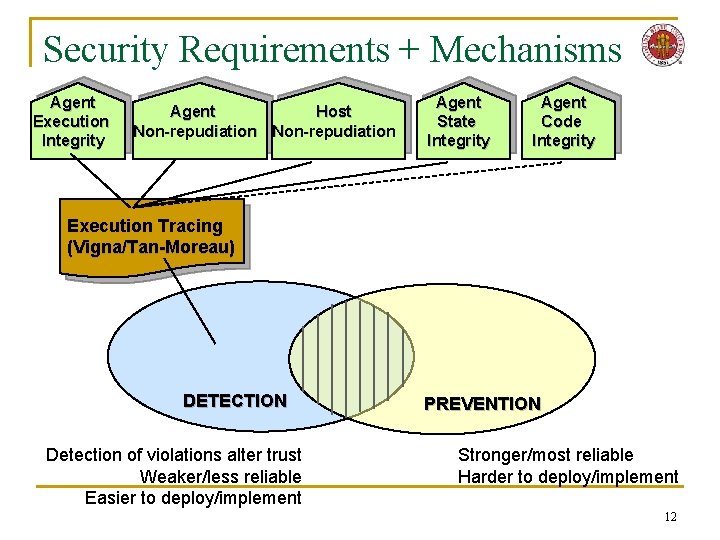
Security Requirements + Mechanisms Agent Execution Integrity Agent Host Non-repudiation Agent State Integrity Agent Code Integrity Execution Tracing (Vigna/Tan-Moreau) DETECTION Detection of violations alter trust Weaker/less reliable Easier to deploy/implement PREVENTION Stronger/most reliable Harder to deploy/implement 12
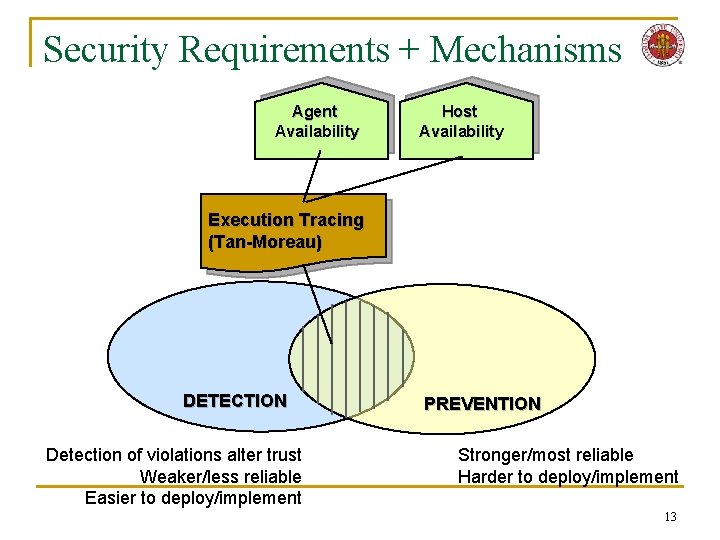
Security Requirements + Mechanisms Agent Availability Host Availability Execution Tracing (Tan-Moreau) DETECTION Detection of violations alter trust Weaker/less reliable Easier to deploy/implement PREVENTION Stronger/most reliable Harder to deploy/implement 13
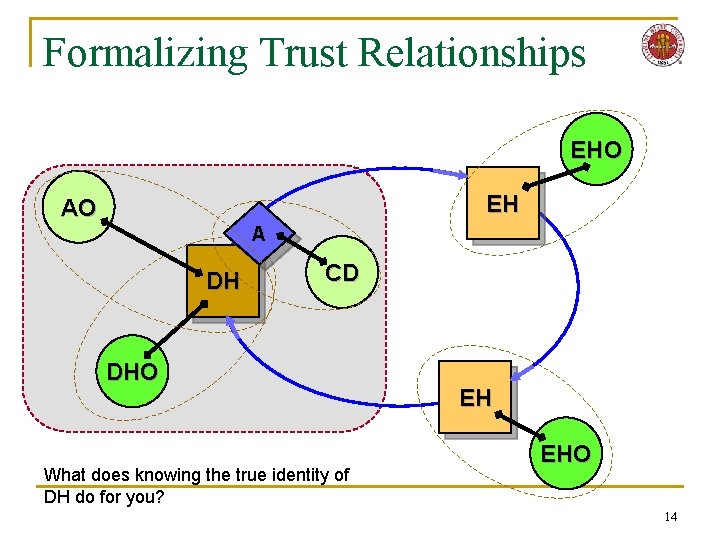
Formalizing Trust Relationships EHO EH AO A DH CD DHO What does knowing the true identity of DH do for you? EH EHO 14
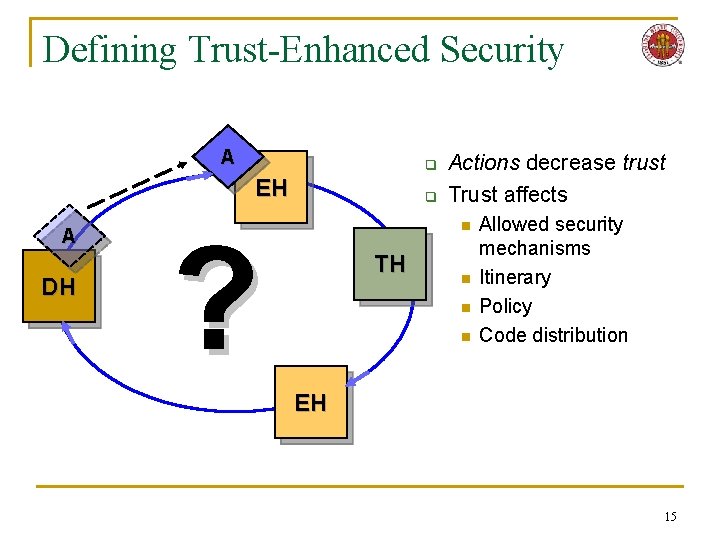
Defining Trust-Enhanced Security A q EH A DH q Actions decrease trust Trust affects n ? TH n n n Allowed security mechanisms Itinerary Policy Code distribution EH 15
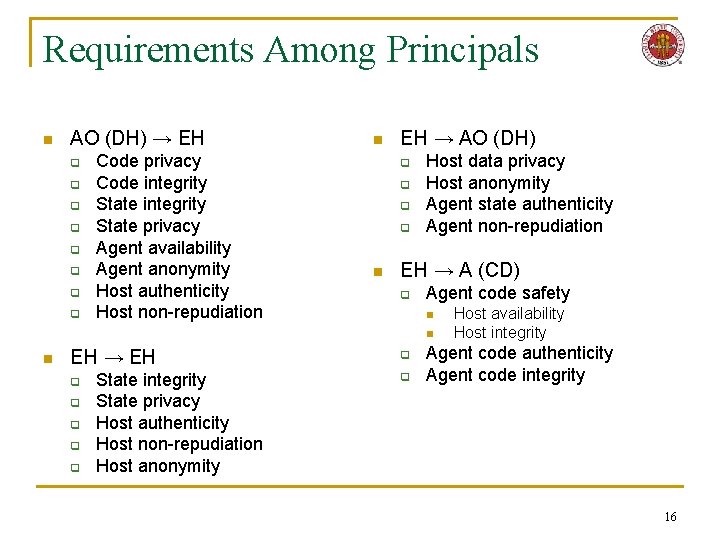
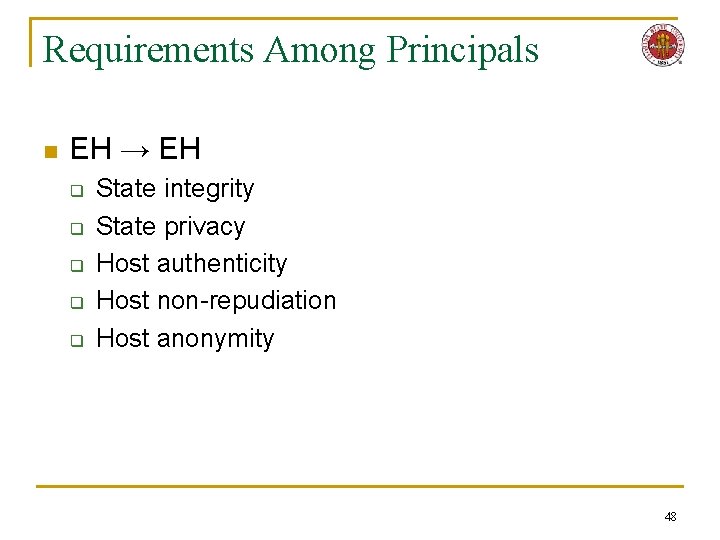
Requirements Among Principals n AO (DH) → EH q q q q Code privacy Code integrity State privacy Agent availability Agent anonymity Host authenticity Host non-repudiation n EH → AO (DH) q q n Host data privacy Host anonymity Agent state authenticity Agent non-repudiation EH → A (CD) q Agent code safety n n n EH → EH q q q State integrity State privacy Host authenticity Host non-repudiation Host anonymity q q Host availability Host integrity Agent code authenticity Agent code integrity 16
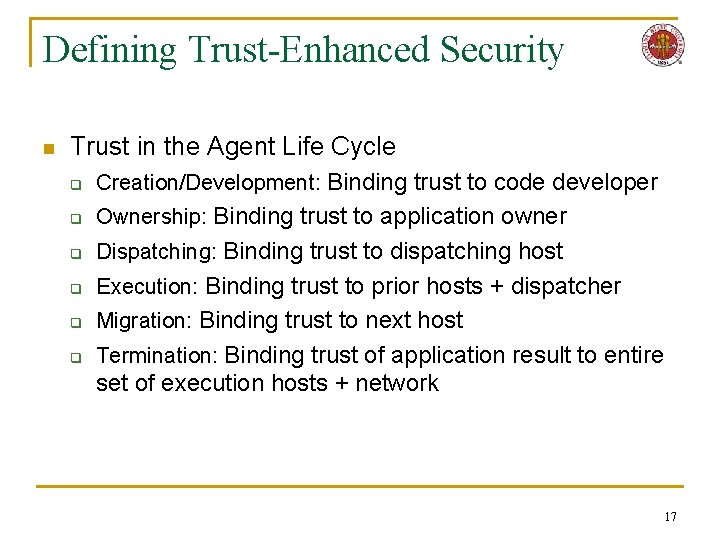
Defining Trust-Enhanced Security n Trust in the Agent Life Cycle q Creation/Development: Binding trust to code developer q Ownership: Binding trust to application owner q Dispatching: Binding trust to dispatching host q Execution: Binding trust to prior hosts + dispatcher q Migration: Binding trust to next host q Termination: Binding trust of application result to entire set of execution hosts + network 17
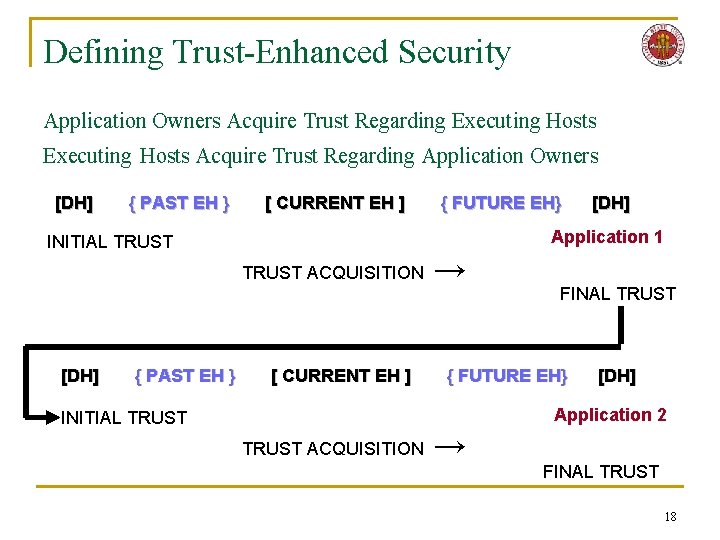
Defining Trust-Enhanced Security Application Owners Acquire Trust Regarding Executing Hosts Acquire Trust Regarding Application Owners [DH] { PAST EH } [ CURRENT EH ] TRUST ACQUISITION { PAST EH } [DH] Application 1 INITIAL TRUST [DH] { FUTURE EH} [ CURRENT EH ] → FINAL TRUST { FUTURE EH} [DH] Application 2 INITIAL TRUST ACQUISITION → FINAL TRUST 18
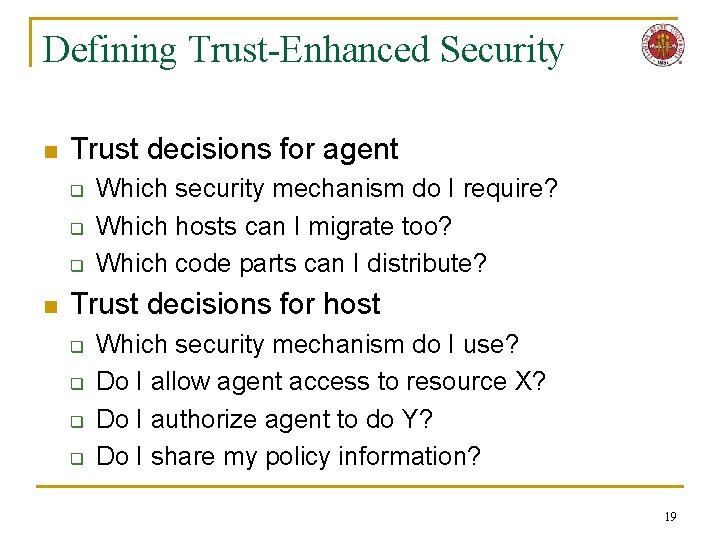
Defining Trust-Enhanced Security n Trust decisions for agent q q q n Which security mechanism do I require? Which hosts can I migrate too? Which code parts can I distribute? Trust decisions for host q q Which security mechanism do I use? Do I allow agent access to resource X? Do I authorize agent to do Y? Do I share my policy information? 19
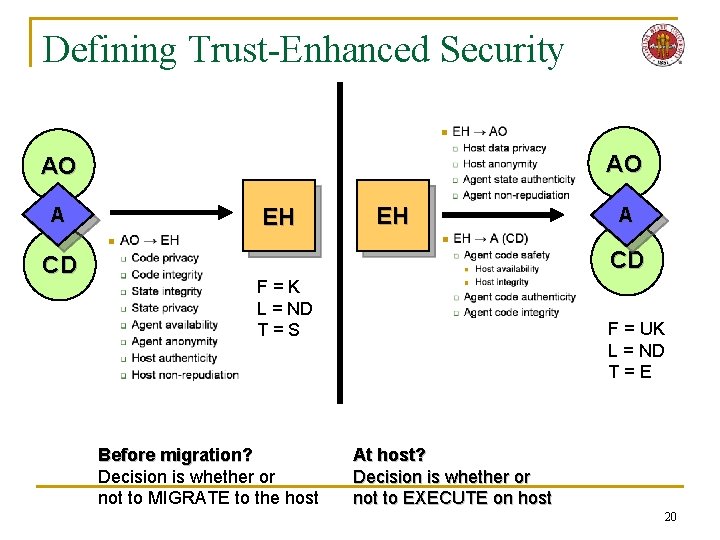
Defining Trust-Enhanced Security AO AO A CD EH EH A CD F=K L = ND T=S Before migration? Decision is whether or not to MIGRATE to the host F = UK L = ND T=E At host? Decision is whether or not to EXECUTE on host 20

Defining Trust-Enhanced Security n Trusted Third Parties (Trusted Hosts) q q Increase/decrease trust among one or more principles Based on their services: n n n q Allow hosts to trust agents more/less Allow agents to trust hosts more/less Allow hosts to trust other hosts more/less May provide implementation or PART of a particular security mechanism 21
Overview n n Motivation Defining mobile agent trust Defining trust-enhanced security Defining application security models q q q n Military model Trade model Neutral-services model Questions 22
Defining Application Security Models n Essence of Military Model q q q “Maginot” line Dispatching Hosts Executing Hosts Trusted Hosts ≠ Only “known” principles allowed Static (ordered/unordered) itineraries “Centralized” management domain n q Overarching management of code Members of C (codebase) known a priori Safety of C (codebase) evaluated a priori Single and multiple agent applications 23
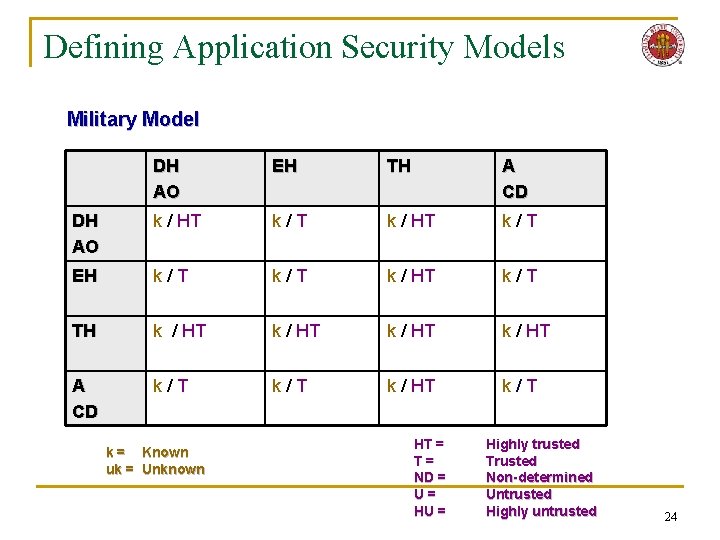
Defining Application Security Models Military Model DH AO EH TH A CD DH AO k / HT k/T EH k/T k / HT k/T TH k / HT A CD k/T k / HT k/T k = Known uk = Unknown HT = T= ND = U= HU = Highly trusted Trusted Non-determined Untrusted Highly untrusted 24

Defining Application Security Models n Variance of Strong Military Model q q ALL execution hosts are equipped with tamperproof hardware Have equivalent trust levels as that of trusted host (highly trusted) 25
Defining Application Security Models n Essence of Trade Model q q q q E-commerce: buyers/sellers Dispatching Hosts ∩ Executing Hosts = Trusted Hosts = Unknown principles Dynamic and static itineraries Single agent applications No infrastructure for code management n Members and safety of C (codebase) not known a priori 26
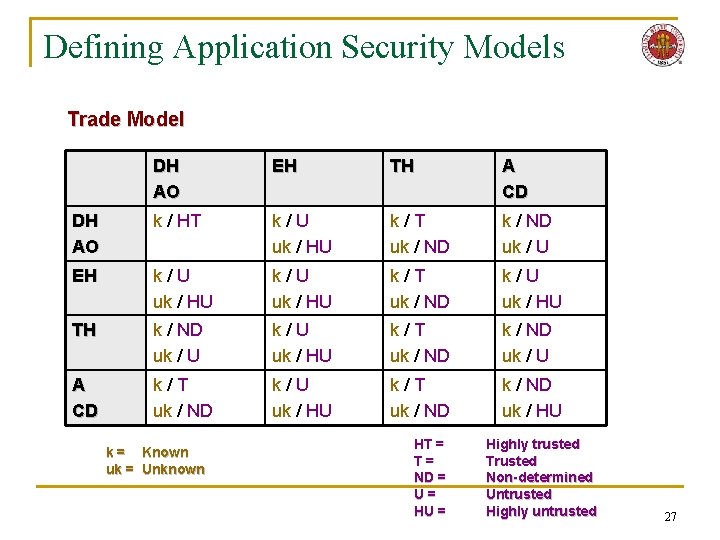
Defining Application Security Models Trade Model DH AO EH TH A CD DH AO k / HT k/U uk / HU k/T uk / ND uk / U EH k/U uk / HU k/T uk / ND k/U uk / HU TH k / ND uk / U k/U uk / HU k/T uk / ND uk / U A CD k/T uk / ND k/U uk / HU k/T uk / ND uk / HU k = Known uk = Unknown HT = T= ND = U= HU = Highly trusted Trusted Non-determined Untrusted Highly untrusted 27

Questions 28
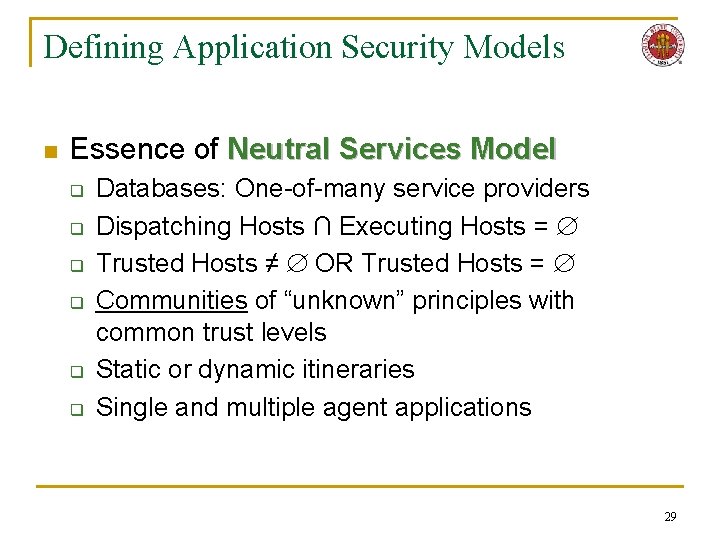
Defining Application Security Models n Essence of Neutral Services Model q q q Databases: One-of-many service providers Dispatching Hosts ∩ Executing Hosts = Trusted Hosts ≠ OR Trusted Hosts = Communities of “unknown” principles with common trust levels Static or dynamic itineraries Single and multiple agent applications 29
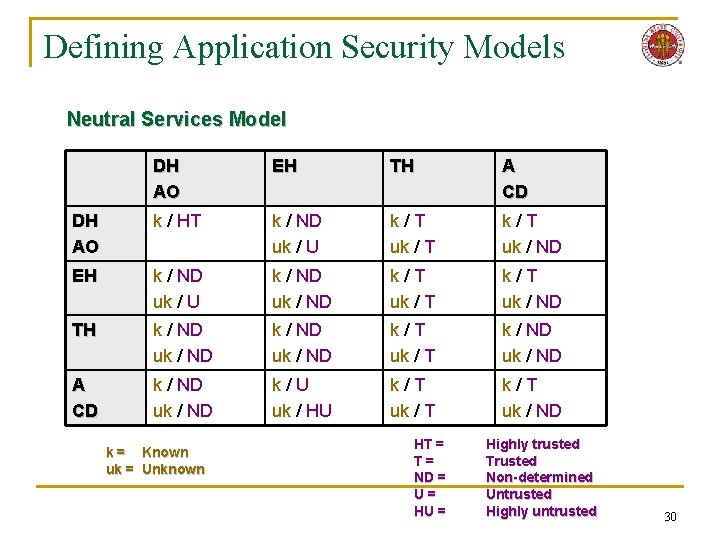
Defining Application Security Models Neutral Services Model DH AO EH TH A CD DH AO k / HT k / ND uk / U k/T uk / T k/T uk / ND EH k / ND uk / U k / ND uk / ND k/T uk / T k/T uk / ND TH k / ND uk / ND k/T uk / T k / ND uk / ND A CD k / ND uk / ND k/U uk / HU k/T uk / T k/T uk / ND k = Known uk = Unknown HT = T= ND = U= HU = Highly trusted Trusted Non-determined Untrusted Highly untrusted 30
Related Works n Trust: Distributed, Decentralized, Ad-hoc q q q q q Gambetta (1990) Yahalom, Klein, Beth (1993) Rasmusson and Jansson (1996) Blaze, Feigenbaum, Lacy (1996) Grandison and Sloman (2000) – Survey Kagal et al. (2001) Cahill et al. (2003) Capra (2004) Burmester and Yasinsac (2004) 31

Related Works n General mobile agent security q q q n Mc. Donald, Yasinsac, Thompson (2005) Claessens, Preneel, Vandewalle (2003) Bierman and Cloete (2002) Jansen & Karygiannis (2000) Chess (1998) Mobile agent security and trust q q q Tripathi, Ahmed, Karnik (2001) Tan and Moreau (2001) Robles & Borrell (2002) Patrick (2002) Lin et al. (2004) 32
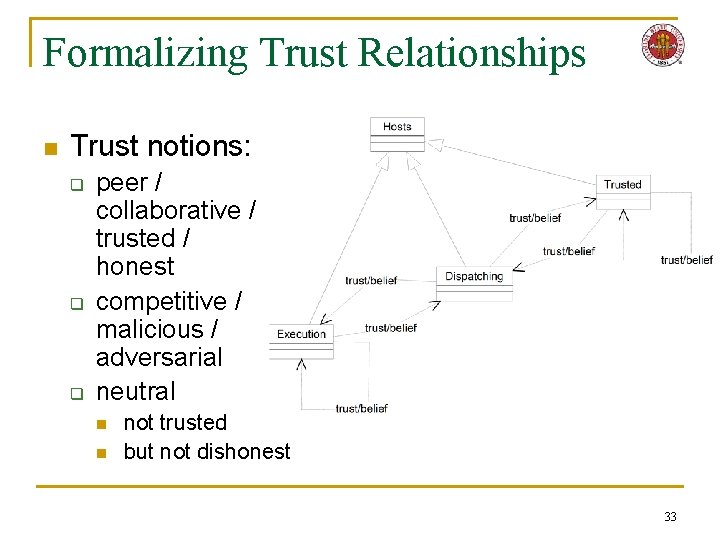
Formalizing Trust Relationships n Trust notions: q q q peer / collaborative / trusted / honest competitive / malicious / adversarial neutral n n not trusted but not dishonest 33

Formalizing Trust Levels n Trust notions q q q n Unidirectional: The trust one way is not necessarily the corresponding trust the other way Limited: Specific only to a given security objective (you could be trustworthy in one respect but not another) Specific: Trust can encompass entire sets of agents/hosts or deal with specific hosts and specific agents and specific people Goal: Given initial trust relationships, derive new ones according to rules 34
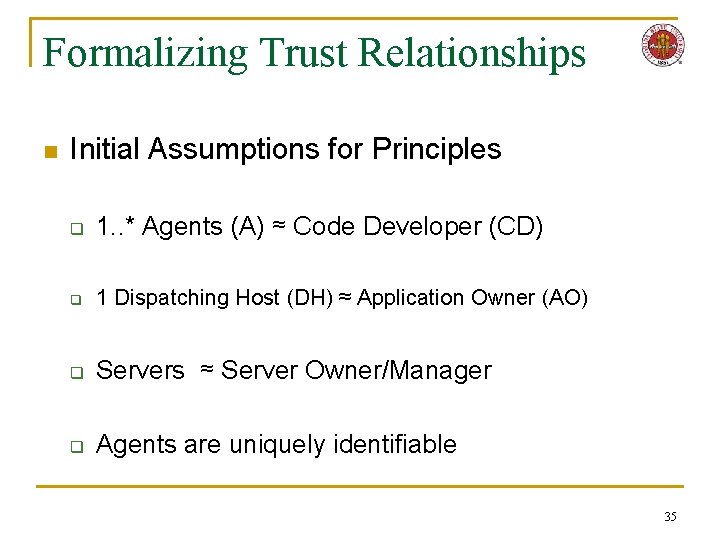
Formalizing Trust Relationships n Initial Assumptions for Principles q 1. . * Agents (A) ≈ Code Developer (CD) q 1 Dispatching Host (DH) ≈ Application Owner (AO) q Servers ≈ Server Owner/Manager q Agents are uniquely identifiable 35
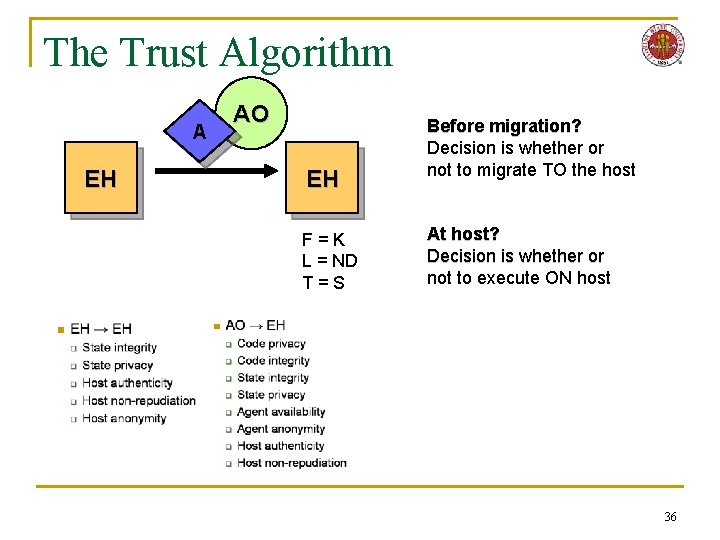
The Trust Algorithm A EH AO EH F=K L = ND T=S Before migration? Decision is whether or not to migrate TO the host At host? Decision is whether or not to execute ON host 36
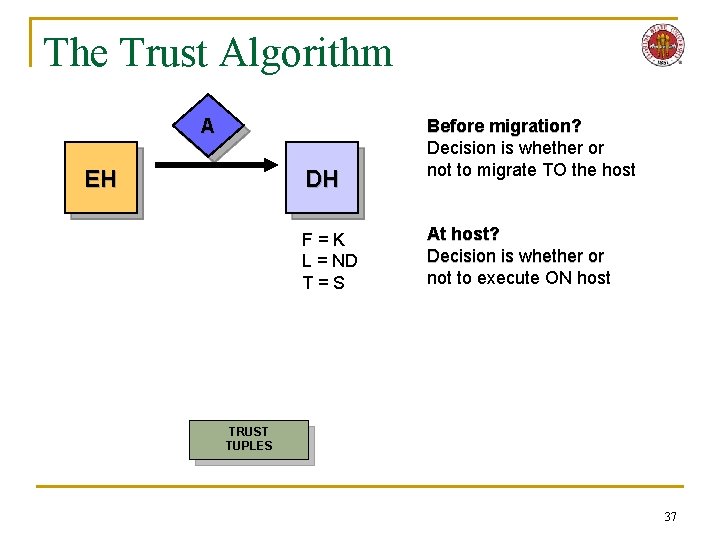
The Trust Algorithm A EH DH F=K L = ND T=S Before migration? Decision is whether or not to migrate TO the host At host? Decision is whether or not to execute ON host TRUST TUPLES 37
The Trust Algorithm A DH TH Before migration? Decision is whether or not to migrate TO the host At host? Decision is whether or not to execute ON host TRUST TUPLES 38
The Trust Algorithm A TH TH Before migration? Decision is whether or not to migrate TO the host At host? Decision is whether or not to execute ON host TRUST TUPLES 39
The Trust Algorithm A TH EH Before migration? Decision is whether or not to migrate TO the host At host? Decision is whether or not to execute ON host TRUST TUPLES 40
The Trust Algorithm A EH TH Before migration? Decision is whether or not to migrate TO the host At host? Decision is whether or not to execute ON host TRUST TUPLES 41
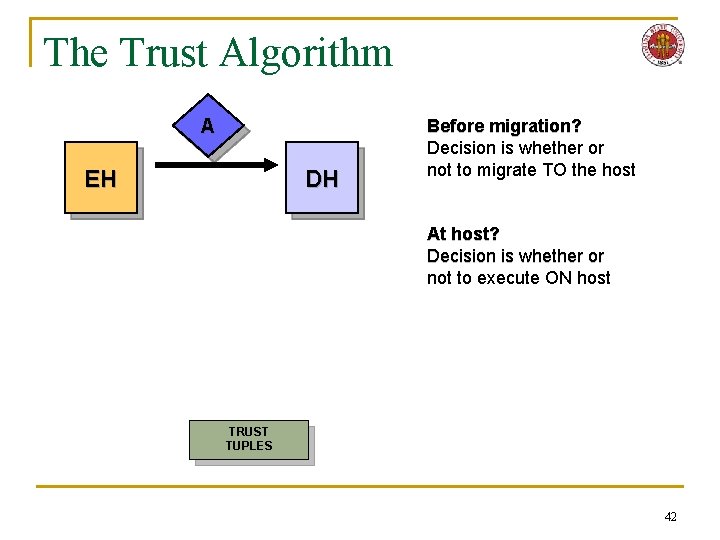
The Trust Algorithm A EH DH Before migration? Decision is whether or not to migrate TO the host At host? Decision is whether or not to execute ON host TRUST TUPLES 42
![Formalizing Trust Relationships [Principle] [Trust Level] → [Foreknowledge] [Principle] [Timeliness] with (O) q q Formalizing Trust Relationships [Principle] [Trust Level] → [Foreknowledge] [Principle] [Timeliness] with (O) q q](http://slidetodoc.com/presentation_image_h2/9bbb6a255cca1682c8a6b05bc0263f39/image-43.jpg)
Formalizing Trust Relationships [Principle] [Trust Level] → [Foreknowledge] [Principle] [Timeliness] with (O) q q P = { p 1, p 2 }: p 1, p 2 { DH | EH | TH | A } F = { K | UK } n n q TL = { HT | UK | U | HU } n n n q K = known, UK = unknown Associate? Acquaintance? Third-hand? HT = Highly trusted T = Trusted UK = Unknown U = Untrusted HU = highly untrusted O: Security Objective n Set of 1 or more? 43

Defining Mobile Agent Trust n Trustworthiness of the agent code might be expressed in terms of three requirements: q q q Authentication of the code’s designer and the code’s identity Integrity verification that code received is the same as code transmitted by an application owner Probabilistic proofs that code meets some predefined security policy or safety requirements 44
Defining Mobile Agent Trust EHO EH AO A DH DHO CD EH EHO 45
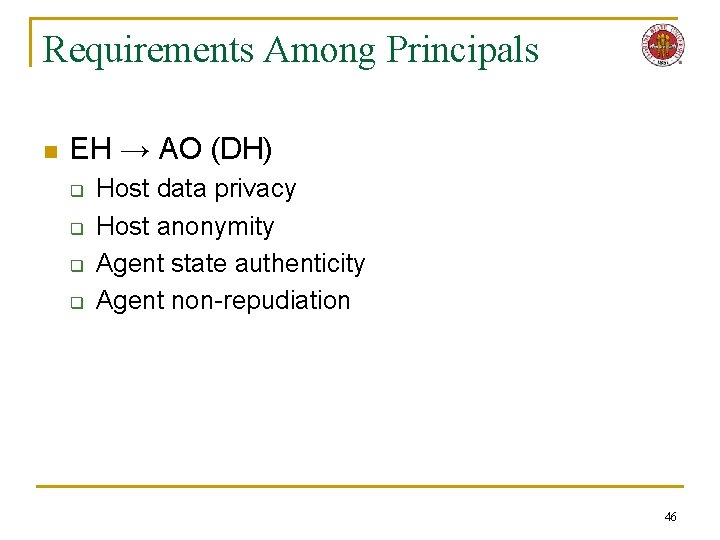
Requirements Among Principals n EH → AO (DH) q q Host data privacy Host anonymity Agent state authenticity Agent non-repudiation 46
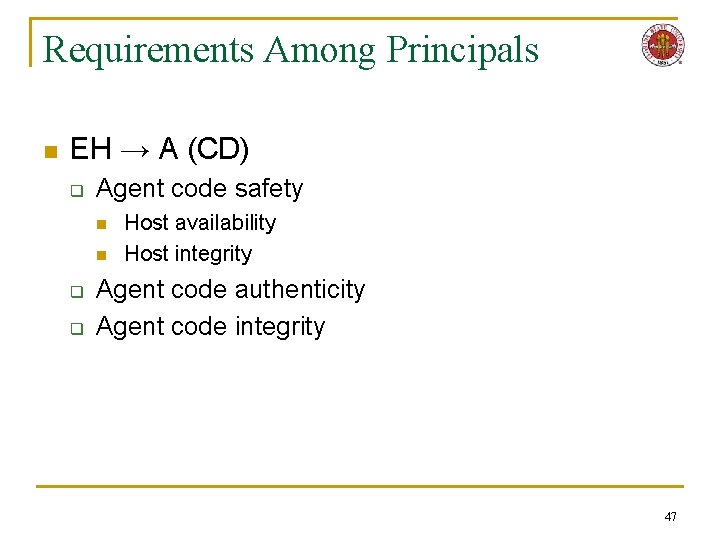
Requirements Among Principals n EH → A (CD) q Agent code safety n n q q Host availability Host integrity Agent code authenticity Agent code integrity 47
Requirements Among Principals n EH → EH q q q State integrity State privacy Host authenticity Host non-repudiation Host anonymity 48
Defining Mobile Agent Trust n Hosts and Agents q q q q ax → EH[i] → ax ax → TH[i] → ax DH → ax ax → DH ax → a y 49
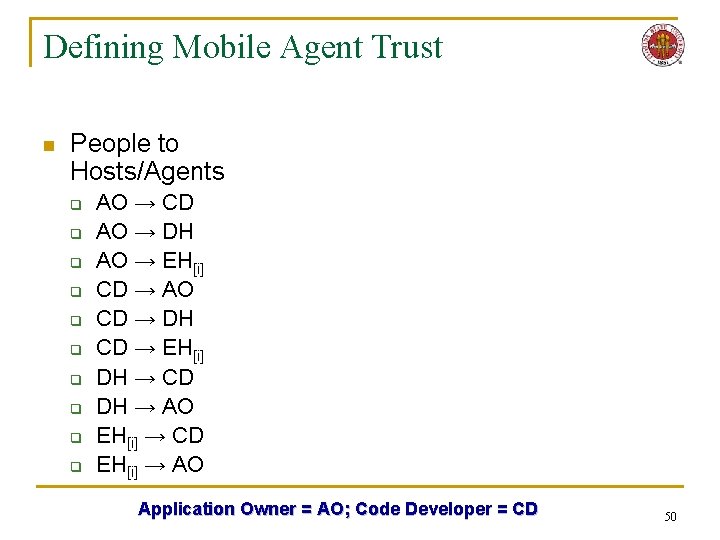
Defining Mobile Agent Trust n People to Hosts/Agents q q q q q AO → CD AO → DH AO → EH[i] CD → AO CD → DH CD → EH[i] DH → CD DH → AO EH[i] → CD EH[i] → AO Application Owner = AO; Code Developer = CD 50
![Defining Trust-Enhanced Security Executing Hosts Acquire Trust Regarding Application Owners [ALL PRIOR APPS] [ Defining Trust-Enhanced Security Executing Hosts Acquire Trust Regarding Application Owners [ALL PRIOR APPS] [](http://slidetodoc.com/presentation_image_h2/9bbb6a255cca1682c8a6b05bc0263f39/image-51.jpg)
Defining Trust-Enhanced Security Executing Hosts Acquire Trust Regarding Application Owners [ALL PRIOR APPS] [ CURRENT APP ] Host 1 INITIAL TRUST ACQUISITION [ALL PRIOR APPS] → FINAL TRUST [ CURRENT APP ] Host 1 INITIAL TRUST ACQUISITION → FINAL TRUST 51
- Slides: 51