Appendix 2 1 RDS and TLS An Overview














- Slides: 26

Appendix 2. 1: RDS and TLS An Overview of Probability-Based Sampling Methods For Key Populations

Session Overview Discussion of Sampling Hard to Reach Populations Presentation, comparison, and discussion of: Time Location Sampling (TLS) Respondent Driven Sampling (RDS)

How to Reach Hard to Reach Populations …. . Let’s Discuss!

What Makes RDS and TLS Unique for Sampling Key Populations? They are probability-based sampling methods Every respondent has a non-zero, known probability of being selected to participate in the study With weighting, the sample can be made representative of the target population Characteristics of the sample are valid estimates of the characteristics of the target population

Time Location Sampling (TLS) The method is known by several names Venue Day Time (VDT) sampling Temporal-spatial sampling (TSS) Time Venue Sampling (TVS) Variation of Targeted Sampling (TS) Venue-Based Sampling (VBS) The idea is to sample the target population at randomly selected venues where members of the population are known to congregate

Basic Principles of TLS Approximates random cluster sampling 1. 2. 3. Target population is divided into clusters or groups Groups of individuals are randomly selected for sampling Individuals in selected groups are randomly sampled In TLS, the sampling clusters are known as venueday-times (VDTs). VDTs are the: Places Day of the Week And times where target population can be found

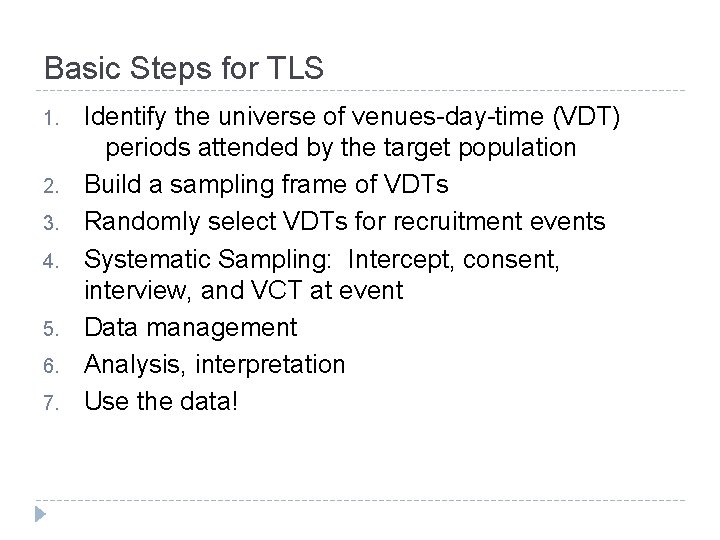
Basic Steps for TLS 1. 2. 3. 4. 5. 6. 7. Identify the universe of venues-day-time (VDT) periods attended by the target population Build a sampling frame of VDTs Randomly select VDTs for recruitment events Systematic Sampling: Intercept, consent, interview, and VCT at event Data management Analysis, interpretation Use the data!

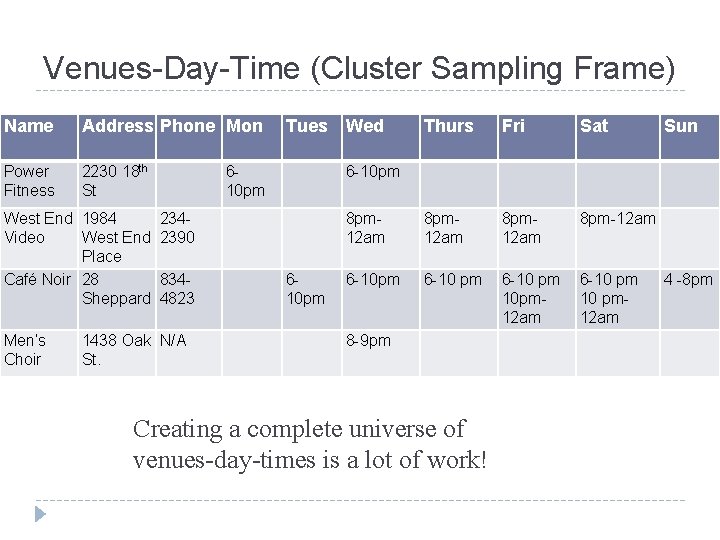
Venues-Day-Time (Cluster Sampling Frame) Name Address Phone Mon Power Fitness 2230 18 th St West End 1984 Video West End Place Café Noir 28 Sheppard Men’s Choir Tues 610 pm 1438 Oak N/A St. Thurs Fri Sat 8 pm 12 am 8 pm-12 am 6 -10 pm 6 -10 pm 10 pm 12 am 6 -10 pm 12 am Sun 6 -10 pm 2342390 8344823 Wed 610 pm 8 -9 pm Creating a complete universe of venues-day-times is a lot of work! 4 -8 pm

Assumptions of TLS “Map universe” of all the places where and when the target population can be found Randomly sampling enough places and times provides everyone in the target population equal chance of being in study If not equal chance, there are methods to “weight” sample according to who are more or less likely to be at the venues

Ethical Challenges in TLS Ensuring anonymity Returning results, ensuring appropriate care Drawing unwanted attention to safe havens (police, public) Intoxicated participants Balancing random sample with outreach and prevention

Chain-Referral (Snowball) Sampling Recruitment through a network Strength: Participants recruit individuals from their personal network to participate Reaches respondents who avoid public venues and institutions May have greater coverage because respondents are reached through their social networks Weakness: This is a convenience sample rather than a probability sample Characteristics of the sample are NOT valid estimates of the characteristics of the target population

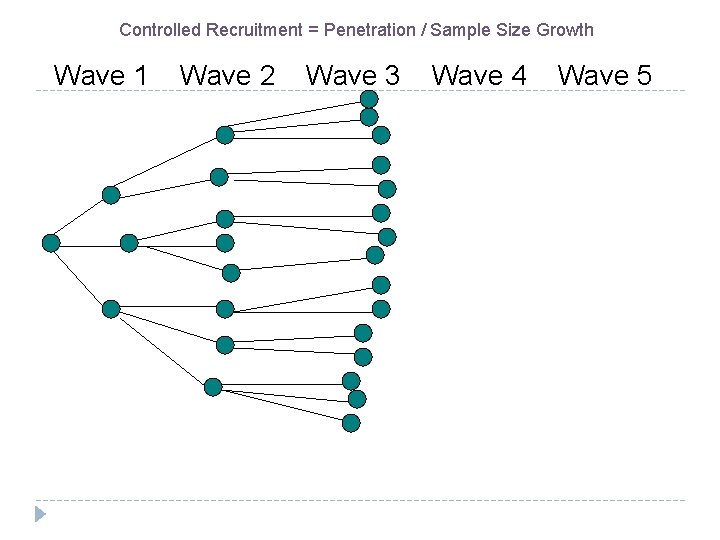
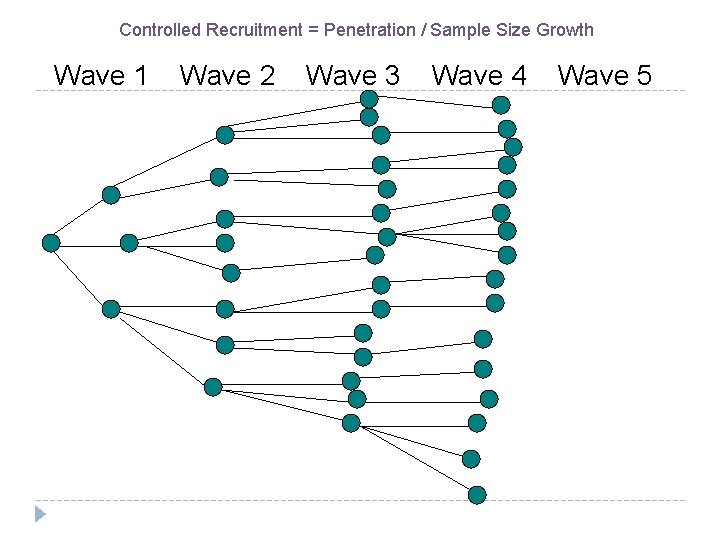
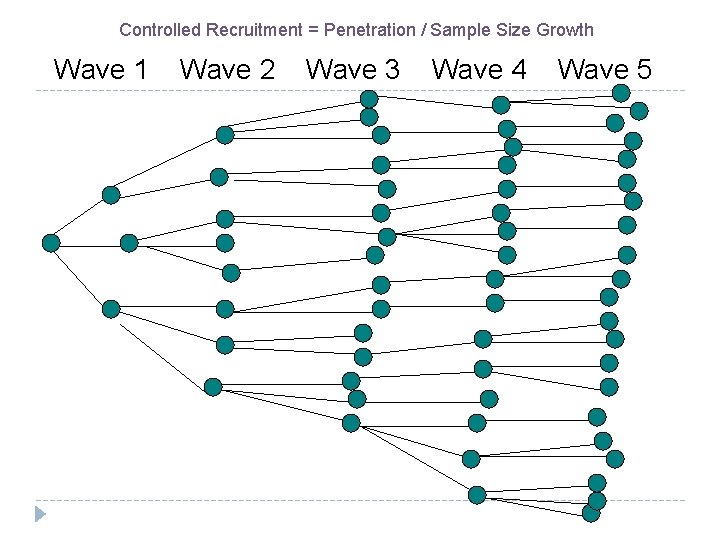
Respondent-Driven Sampling (RDS) RDS combines sampling coverage and probability sampling methods Combines a modified form of chain-referral with a mathematical system for weighting the sample to compensate for its not having been drawn randomly Based on the premise that peers are better able than outreach workers and researchers to locate and recruit other members of a hidden population Unlike other chain referral methods, gives valid population point estimates with standard errors

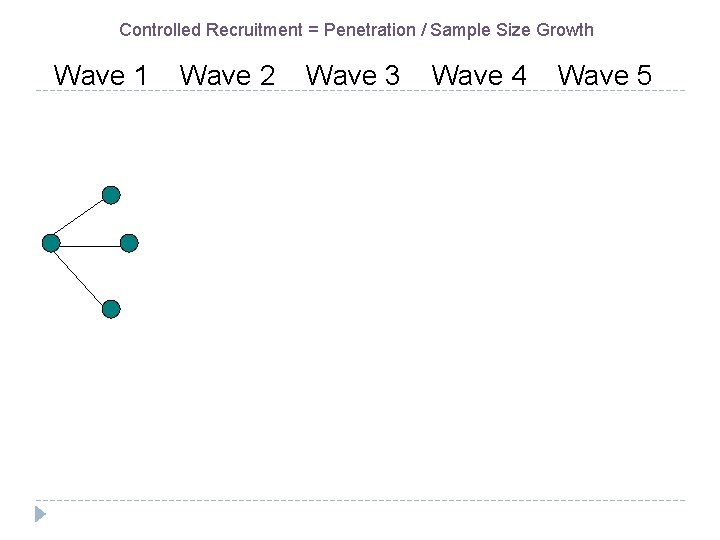
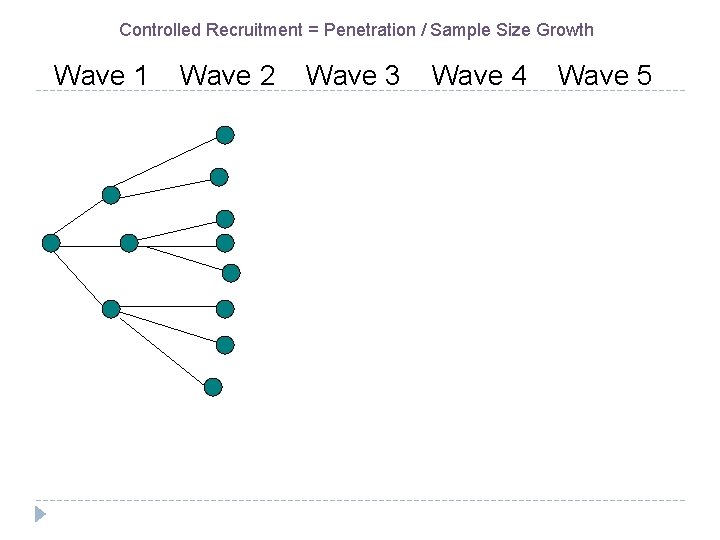
Controlled Recruitment = Penetration / Sample Size Growth Wave 1 Wave 2 Wave 3 Wave 4 Wave 5

Controlled Recruitment = Penetration / Sample Size Growth Wave 1 Wave 2 Wave 3 Wave 4 Wave 5

Controlled Recruitment = Penetration / Sample Size Growth Wave 1 Wave 2 Wave 3 Wave 4 Wave 5

Controlled Recruitment = Penetration / Sample Size Growth Wave 1 Wave 2 Wave 3 Wave 4 Wave 5

Controlled Recruitment = Penetration / Sample Size Growth Wave 1 Wave 2 Wave 3 Wave 4 Wave 5

Controlled Recruitment = Penetration / Sample Size Growth Wave 1 Wave 2 Wave 3 Wave 4 Wave 5

RDS Weighting RDS has two types of weighting: Recruitment pattern weighting Used to adjust for differential recruitment between groups Network size weighting Well-connected individuals tend to be over-sampled because many recruitment paths lead to them

Requirements of RDS Four requirements: Document who recruited whom Recruiter and recruit must know one another Ration recruitment so a few cannot do all the recruiting (i. e. , three recruits/recruiter) Must ask recruiter and recruit about personal network sizes If a study does not include these features, it is not RDS

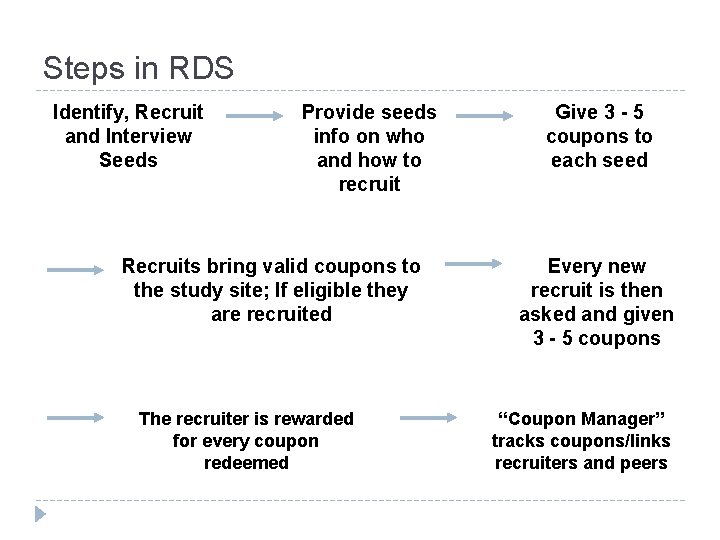
Steps in RDS Identify, Recruit and Interview Seeds Provide seeds info on who and how to recruit Recruits bring valid coupons to the study site; If eligible they are recruited The recruiter is rewarded for every coupon redeemed Give 3 - 5 coupons to each seed Every new recruit is then asked and given 3 - 5 coupons “Coupon Manager” tracks coupons/links recruiters and peers

RDS Assumption (Heckathorn) 1. 2. 3. 4. 5. Individuals know each other as members of the population in question Target population forms one single large network Report network size accurately Recruit randomly from network Sampling with replacement

Advantages of RDS Maintains privacy of population Team can be centrally located Less logistical needs Ease of field operations Moderate formative research/mapping Target members recruit for you Reach less visible segments of population Good external validity Minimal number of additional questions needed Computer software available Generally lower cost

Challenges of RDS Coupons can be slow in being redeemed Population must be networked Must be able to verify group membership Must track links between recruiters and recruitscoupon management Appropriate incentive levels Very difficult to deal with selective non response bias Analysis is complex

Breakout (20 minutes): TLS vs. RDS Which methodology might be more appropriate for the target population here in the Bahamas? a) b) c) d) e) f) g) h) i) Do individuals in the target population frequent venues? Could the target population be identified at these venues? Could the target population be accessed at these venues without drawing them unwanted attention? Might we miss some population groups at these venues? Are individuals in the target population well-networked? Are there distinct sub-populations? Do sub-populations interact with each other? Can members of the target population identify each other? Will the target population be motivated to participate?

Thank You Working Together to Plan, Implement, and Use HIV Surveillance Systems