AOS CPPM INTEGRATION CONFIGURATION TESTING EAP TLS EAP























- Slides: 72

AOS & CPPM INTEGRATION CONFIGURATION & TESTING EAP TLS & EAP PEAP by Abilash Soundararajan CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

EAP-TLS CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

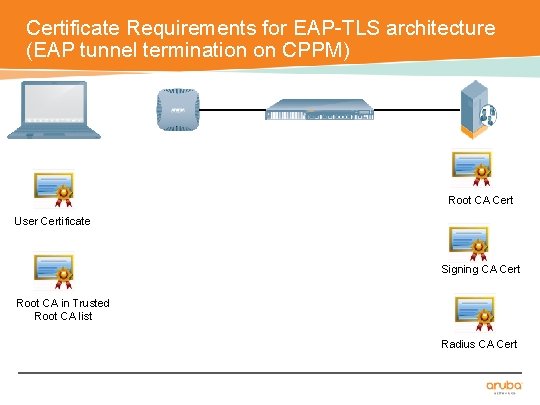
Certificate Requirements for EAP-TLS architecture (EAP tunnel termination on CPPM) Root CA Cert User Certificate Signing CA Cert Root CA in Trusted Root CA list Radius CA Cert

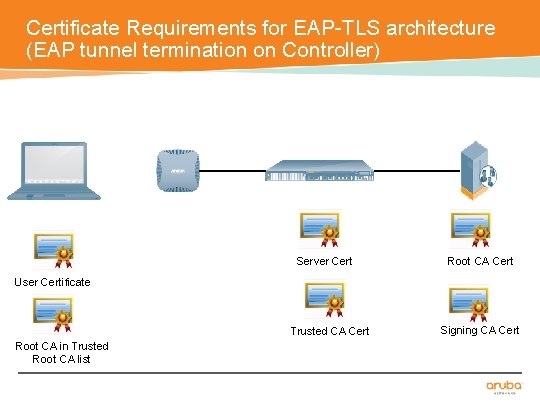
Certificate Requirements for EAP-TLS architecture (EAP tunnel termination on Controller) Server Cert Root CA Cert User Certificate Trusted CA Cert Root CA in Trusted Root CA list Signing CA Cert

SETTING UP EAP-TLS TERMINATION ON CPPM CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Steps for EAP-TLS (Termination on CPPM) • Creating CA & Signing CA on CPPM • Configuring Controller – SSID profile – Dot 1 x profile – Server & Server Group – AAA profile – VAP Profile – Mapping to AP-group • • • Configuring Device & Services in CPPM Creating CSR, Radius cert and uploading it Creating User in CPPM Creating Client Certificates Checking Access Tracker Troubleshooting from Controller

Creating CA & Signing CA on CPPM CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Creating CA & Signing CA on CPPM CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

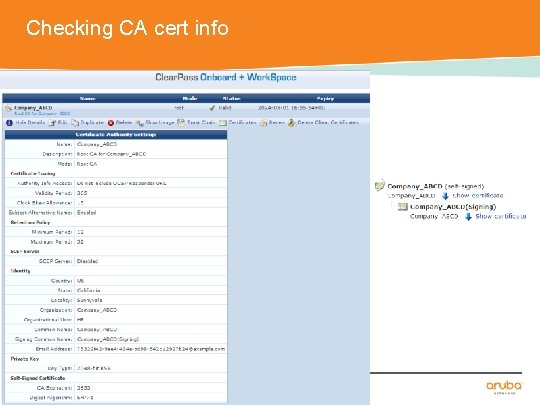
Checking CA cert info CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

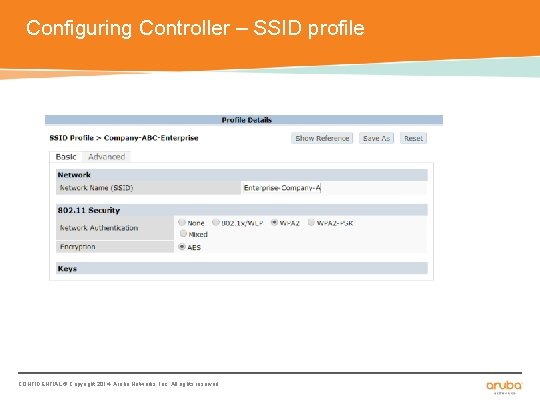
Configuring Controller – SSID profile CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

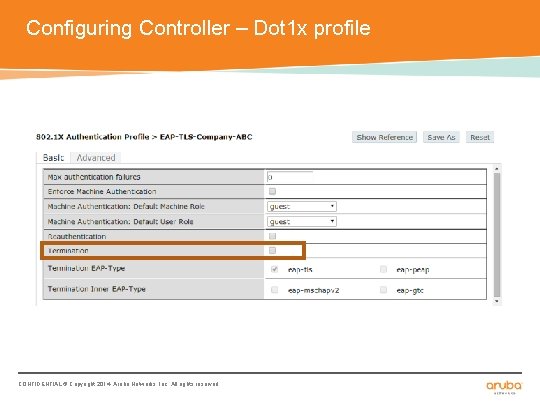
Configuring Controller – Dot 1 x profile CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

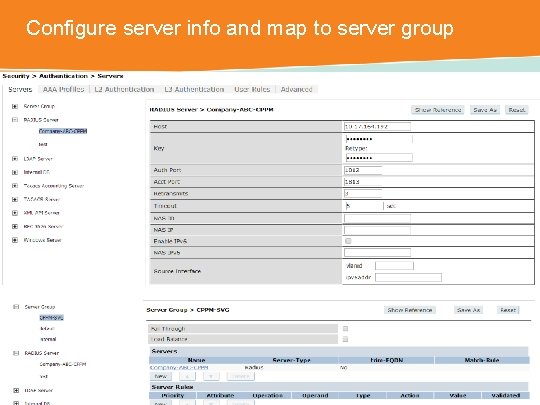
Configure server info and map to server group CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

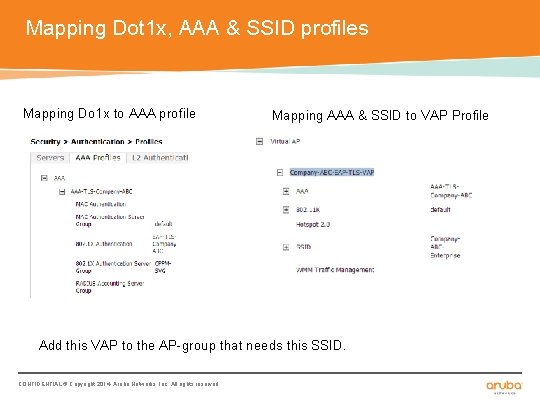
Mapping Dot 1 x, AAA & SSID profiles Mapping Do 1 x to AAA profile Mapping AAA & SSID to VAP Profile Add this VAP to the AP-group that needs this SSID. CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

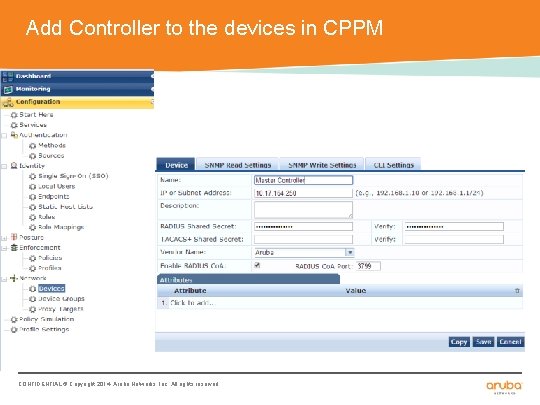
Add Controller to the devices in CPPM CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

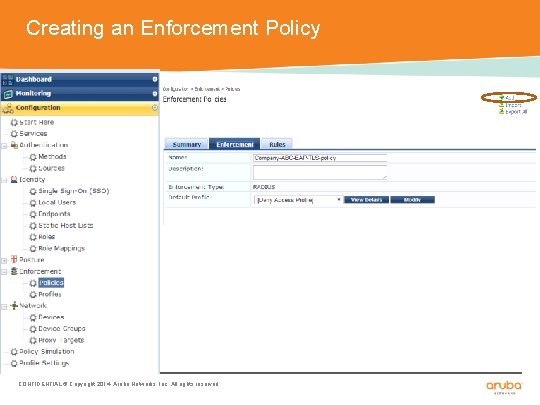
Creating an Enforcement Policy CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

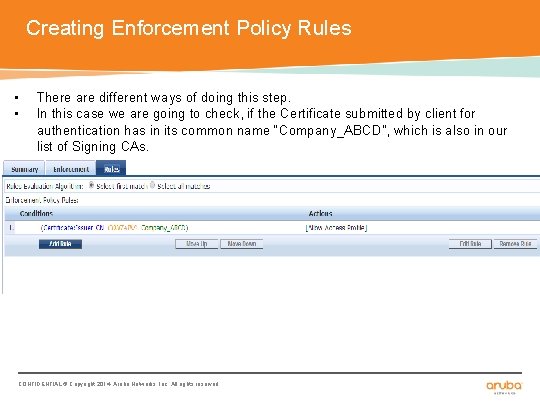
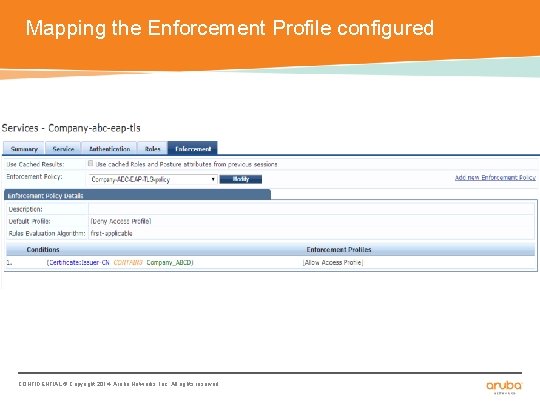
Creating Enforcement Policy Rules • • There are different ways of doing this step. In this case we are going to check, if the Certificate submitted by client for authentication has in its common name “Company_ABCD”, which is also in our list of Signing CAs. CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

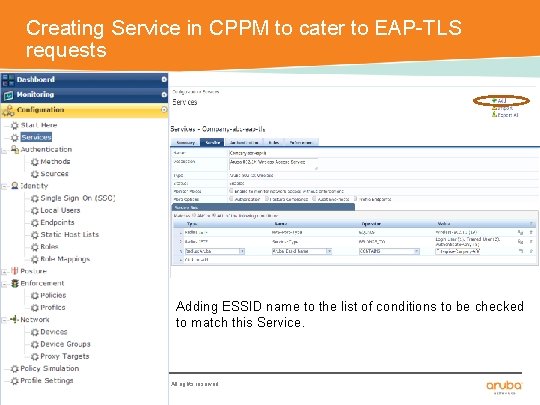
Creating Service in CPPM to cater to EAP-TLS requests Adding ESSID name to the list of conditions to be checked to match this Service. CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

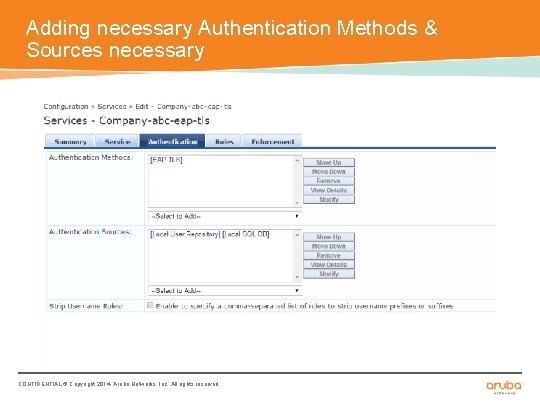
Adding necessary Authentication Methods & Sources necessary CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Mapping the Enforcement Profile configured CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

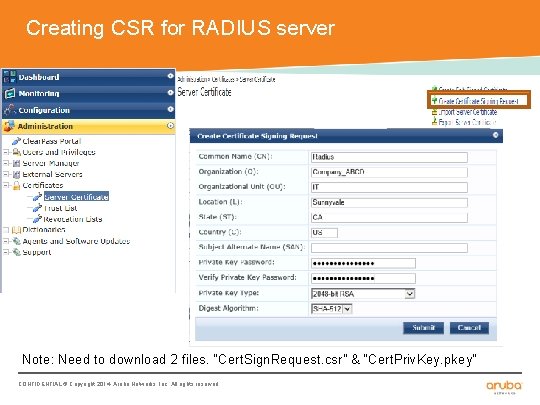
Creating CSR for RADIUS server Note: Need to download 2 files. “Cert. Sign. Request. csr” & “Cert. Priv. Key. pkey” CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Creating Radius server cert with corresponding CA CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

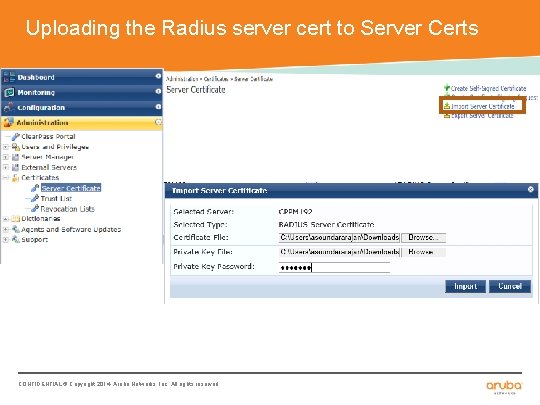
Uploading the Radius server cert to Server Certs CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

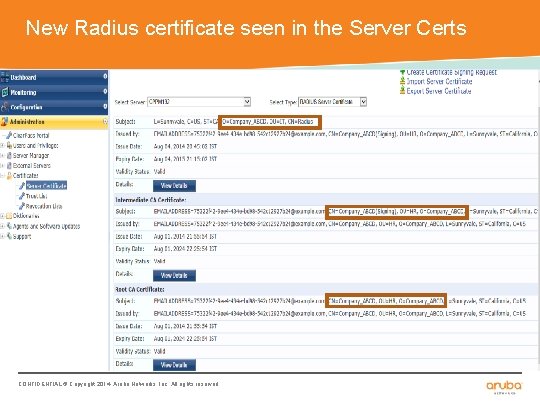
New Radius certificate seen in the Server Certs CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

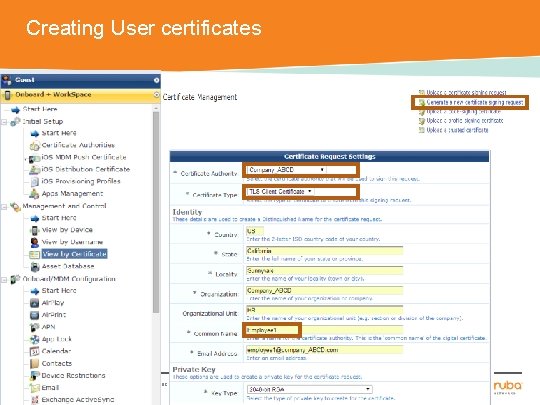
Creating User certificates CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

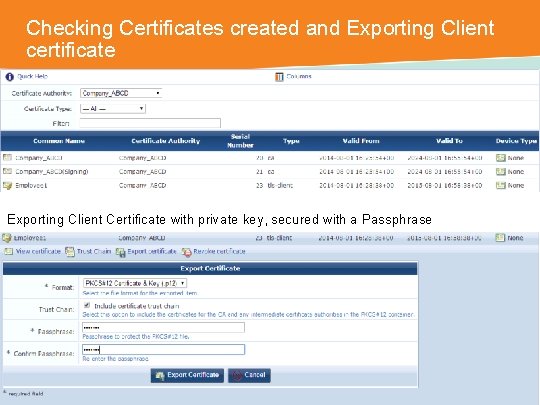
Checking Certificates created and Exporting Client certificate Exporting Client Certificate with private key, secured with a Passphrase CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

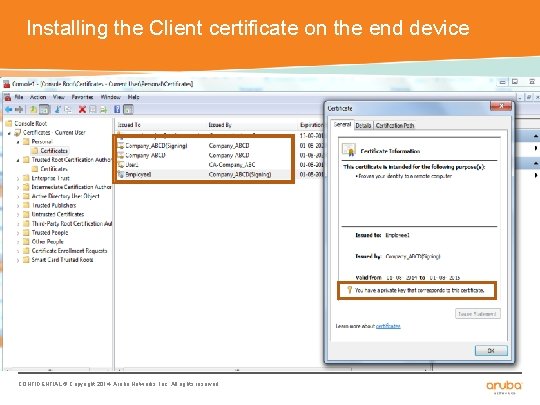
Installing the Client certificate on the end device CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

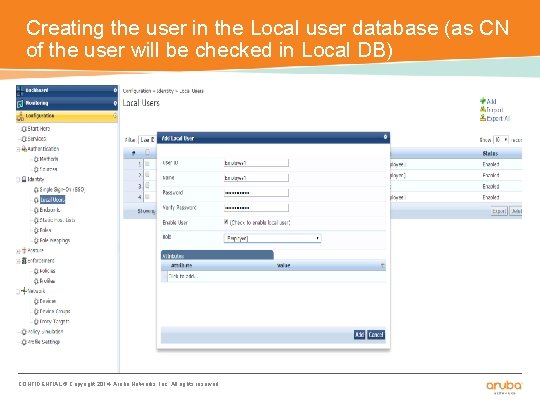
Creating the user in the Local user database (as CN of the user will be checked in Local DB) CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Troubleshooting Radius Service from Controller • Current service will not help in doing aaa test-server – As its only meant for EAP-TLS & EAP-PEAP • Below addition in services can help in doing an MSChapv 2 as well – Disable it post testing for stricter security compliance CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Checking logs on CPPM for successful test authentication CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

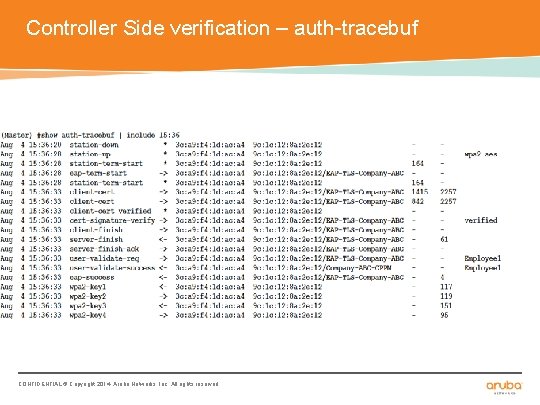
Checking logs on Controller for Successful/ failed test authentication (Master) #show log security 30 | include User, server, fail Aug 4 10: 55: 53 : 124004: <DBUG> |authmgr| Auth server 'Company-ABC-CPPM' response=0 Aug 4 10: 55: 53 : 124019: <INFO> |authmgr| Test server response: Authentication Successful Aug 4 11: 02: 52 : 124011: <INFO> |authmgr| Test authenticating user Employee 1: ****** using server Company-ABC-CPPM Aug 4 11: 02: 57 : 124004: <DBUG> |authmgr| Auth server 'Company-ABC-CPPM' response=1 Aug 4 11: 02: 57 : 124019: <INFO> |authmgr| Test server response: Authentication failed Aug 4 11: 05: 15 : 124011: <INFO> |authmgr| Test authenticating user Employee 1: ****** using server Company-ABC-CPPM Aug 4 11: 05: 20 : 124004: <DBUG> |authmgr| Auth server 'Company-ABC-CPPM' response=1 Aug 4 11: 05: 20 : 124019: <INFO> |authmgr| Test server response: Authentication failed Aug 4 11: 06: 20 : 124011: <INFO> |authmgr| Test authenticating user Employee 1: ****** using server Company-ABC-CPPM Aug 4 11: 06: 20 : 121041: <DBUG> |authmgr| User Employee 1 MAC=00: 00: 00: 00 not found. Aug 4 11: 06: 20 : 124004: <DBUG> |authmgr| Auth server 'Company-ABC-CPPM' response=0 Aug 4 11: 06: 20 : 124019: <INFO> |authmgr| Test server response: Authentication Successful Aug 4 11: 07: 09 : 124011: <INFO> |authmgr| Test authenticating user Employee 1: ****** using server Company-ABC-CPPM Aug 4 11: 07: 14 : 124004: <DBUG> |authmgr| Auth server 'Company-ABC-CPPM' response=1 Aug 4 11: 07: 14 : 124019: <INFO> |authmgr| Test server response: Authentication failed Aug 4 11: 14: 50 : 124011: <INFO> |authmgr| Test authenticating user Employee 1: ****** using server Company-ABC-CPPM Aug 4 11: 14: 50 : 121041: <DBUG> |authmgr| User Employee 1 MAC=00: 00: 00: 00 not found. Aug 4 11: 14: 50 : 124004: <DBUG> |authmgr| Auth server 'Company-ABC-CPPM' response=0 Aug 4 11: 14: 50 : 124019: <INFO> |authmgr| Test server response: Authentication Successful Aug 4 11: 15: 56 : 124011: <INFO> |authmgr| Test authenticating user Employee 1: ****** using server Company-ABC-CPPM Aug 4 11: 15: 56 : 121041: <DBUG> |authmgr| User Employee 1 MAC=00: 00: 00: 00 not found. Aug 4 11: 15: 56 : 124004: <DBUG> |authmgr| Auth server 'Company-ABC-CPPM' response=0 Aug 4 11: 15: 56 : 124019: <INFO> |authmgr| Test server response: Authentication Successful Aug 4 11: 16: 36 : 124011: <INFO> |authmgr| Test authenticating user Employee 1: ****** using server Company-ABC-CPPM Aug 4 11: 16: 36 : 121041: <DBUG> |authmgr| User Employee 1 MAC=00: 00: 00: 00 not found. Aug 4 11: 16: 36 : 124004: <DBUG> |authmgr| Auth server 'Company-ABC-CPPM' response=0 Aug 4 11: 16: 36 : 124019: <INFO> |authmgr| Test server response: Authentication Successful CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Download & Install Root CA Certificate to the list of Trusted CAs in the EAP-TLS client CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

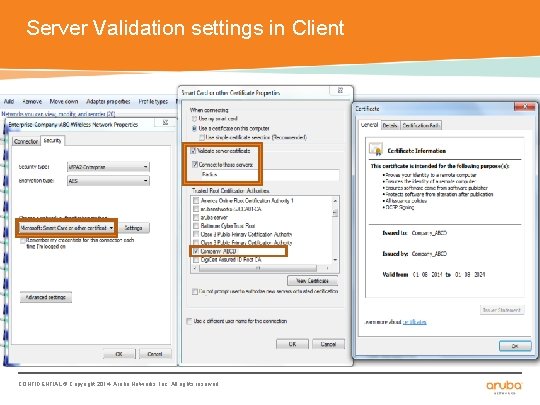
Server Validation settings in Client CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

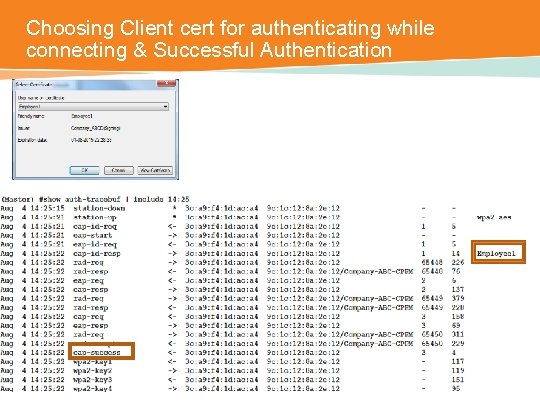
Choosing Client cert for authenticating while connecting & Successful Authentication CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Checking Security logs for the EAP-TLS event CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

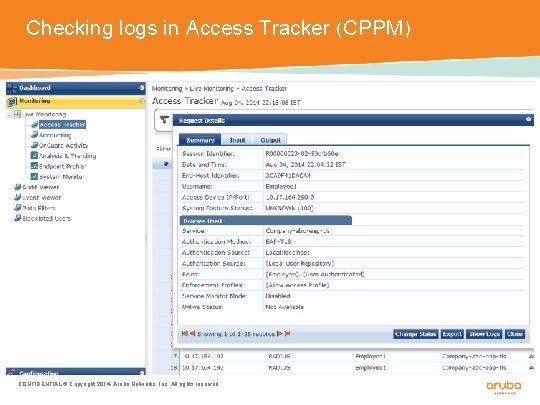
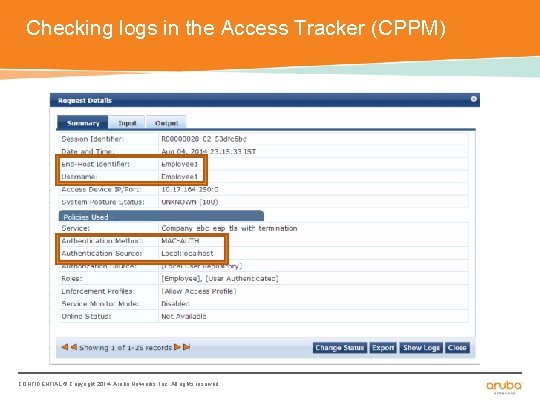
Checking logs in Access Tracker (CPPM) CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

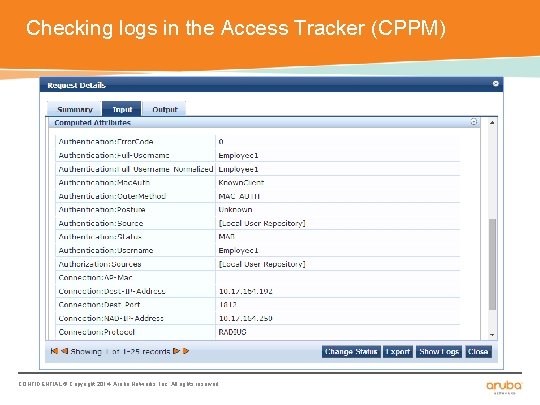
Client Attributes sent and Authentication Sources used CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

EAP-TLS WITH TERMINATION ON CONTROLLER CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

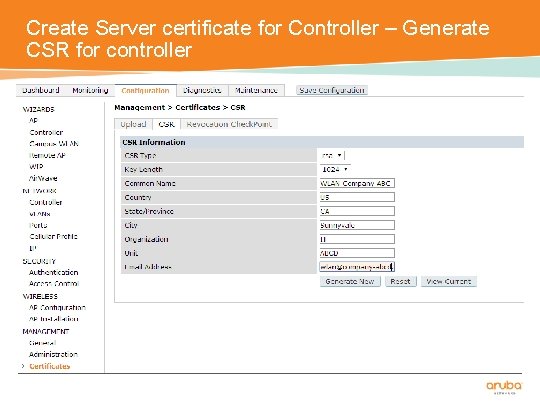
Create Server certificate for Controller – Generate CSR for controller

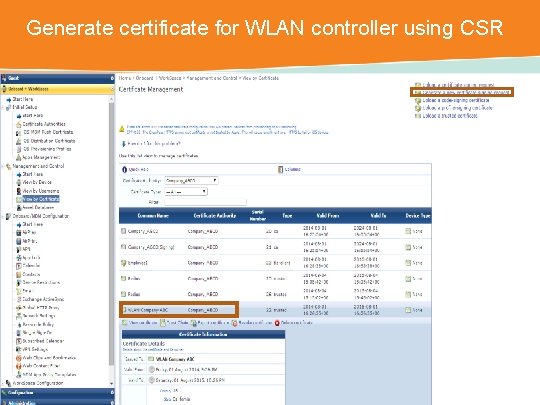
Generate certificate for WLAN controller using CSR CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

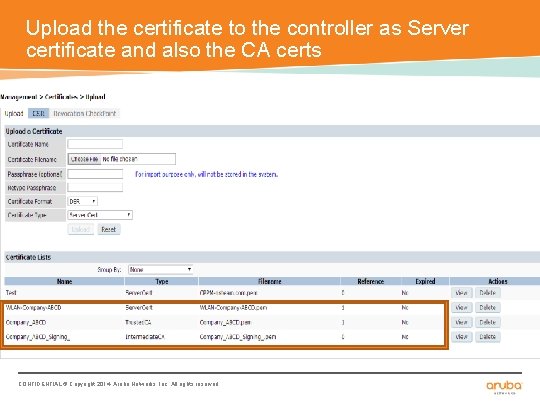
Upload the certificate to the controller as Server certificate and also the CA certs CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

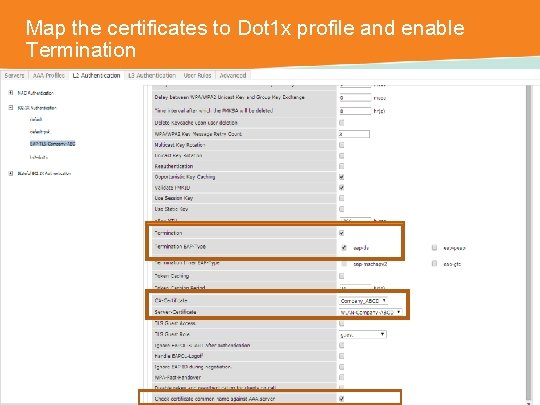
Map the certificates to Dot 1 x profile and enable Termination CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

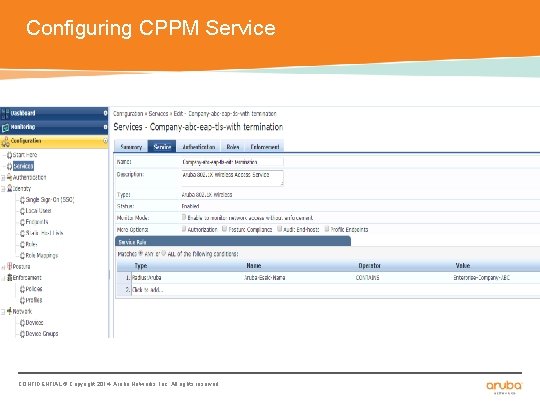
Configuring CPPM Service CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Configuring Authentication Method for Service CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

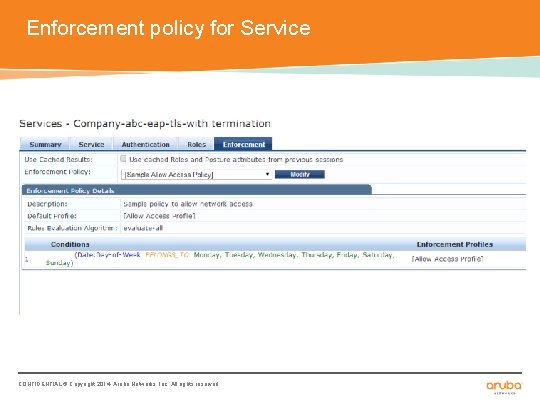
Enforcement policy for Service CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

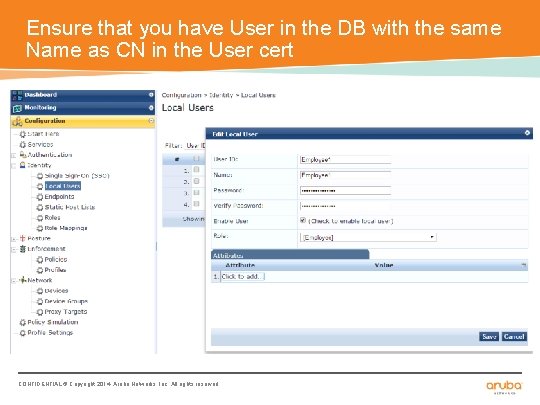
Ensure that you have User in the DB with the same Name as CN in the User cert CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Controller Side verification – auth-tracebuf CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Controller side log verification – Security logs CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Checking logs in the Access Tracker (CPPM) CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Checking logs in the Access Tracker (CPPM) CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

EAP-PEAP CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

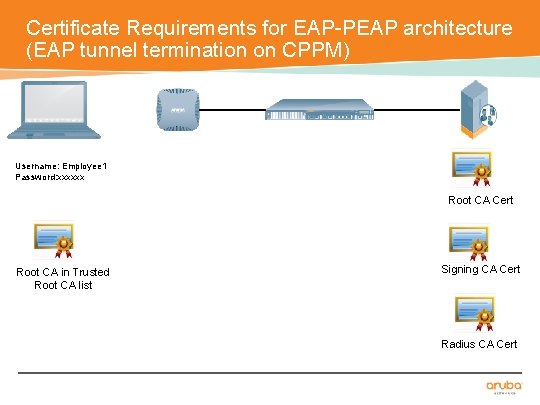
Certificate Requirements for EAP-PEAP architecture (EAP tunnel termination on CPPM) Username: Employee 1 Password: xxxxxx Root CA Cert Root CA in Trusted Root CA list Signing CA Cert Radius CA Cert

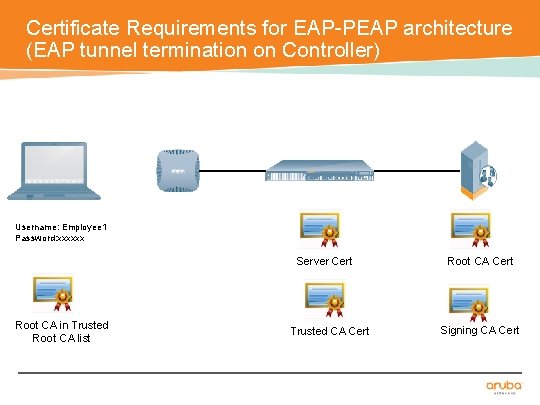
Certificate Requirements for EAP-PEAP architecture (EAP tunnel termination on Controller) Username: Employee 1 Password: xxxxxx Server Cert Root CA in Trusted Root CA list Trusted CA Cert Root CA Cert Signing CA Cert

EAP-PEAP WITH TERMINATION ON CPPM CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

No change in controller config when compared to EAP-TLS setup (Termination on CPPM) Option disabled as termination is disabled

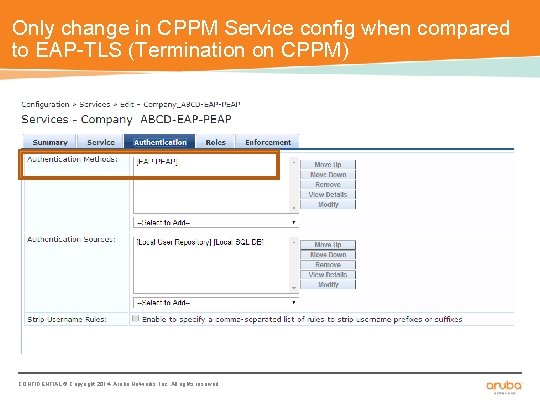
Only change in CPPM Service config when compared to EAP-TLS (Termination on CPPM) CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

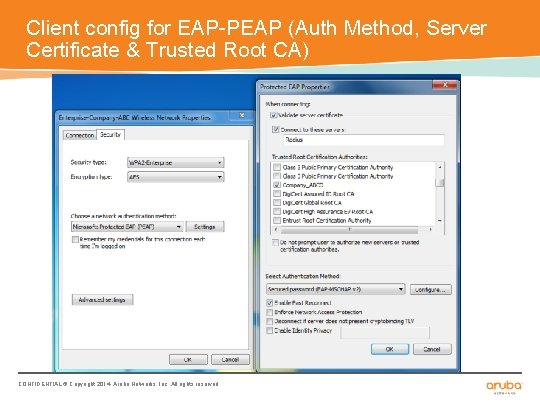
Client config for EAP-PEAP (Auth Method, Server Certificate & Trusted Root CA) CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Checking the steps of EAP-PEAP with termination on CPPM CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

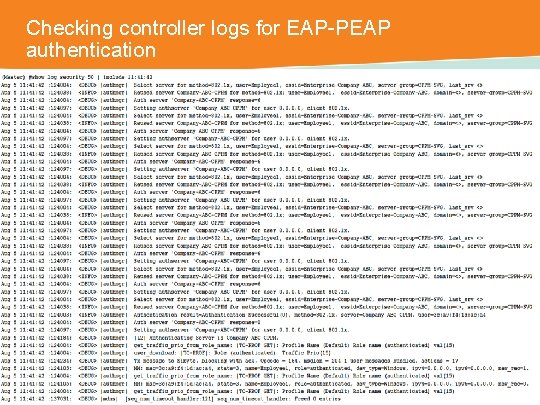
Checking controller logs for EAP-PEAP authentication CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

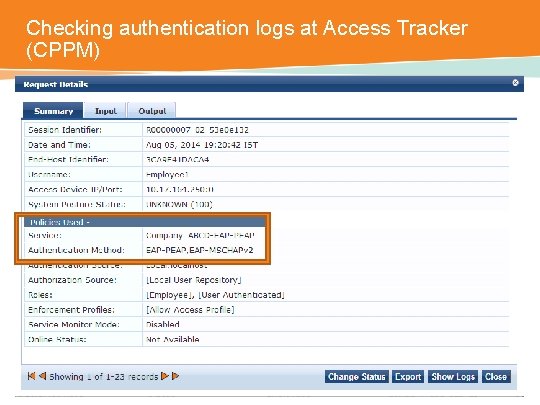
Checking authentication logs at Access Tracker (CPPM) CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

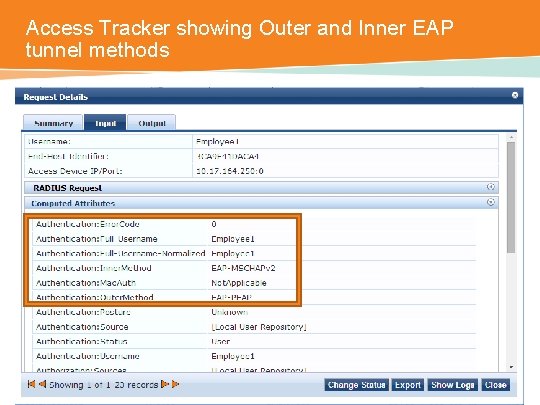
Access Tracker showing Outer and Inner EAP tunnel methods CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

EAP-PEAP WITH TERMINATION ON CONTROLLER CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

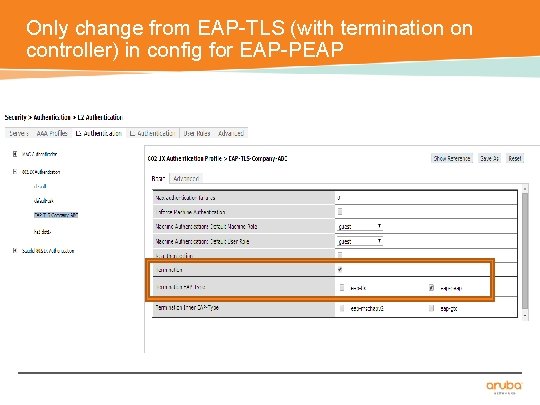
Only change from EAP-TLS (with termination on controller) in config for EAP-PEAP

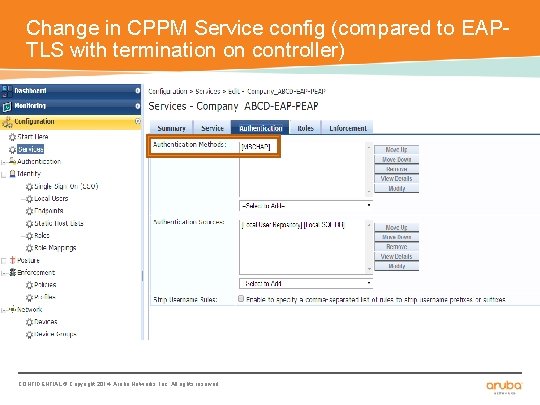
Change in CPPM Service config (compared to EAPTLS with termination on controller) CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

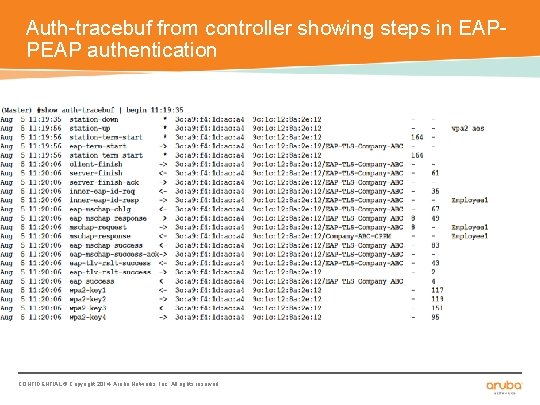
Auth-tracebuf from controller showing steps in EAPPEAP authentication CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Checking security logs in controller for the authentication CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

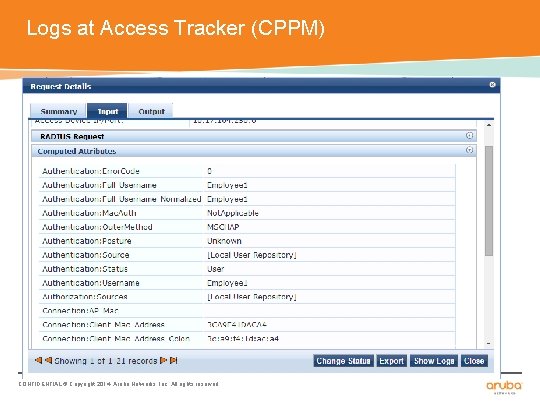
Logs at Access Tracker (CPPM) CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

Logs at Access Tracker (CPPM) CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

MISCELLANEOUS TROUBLESHOOTING TIPS CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

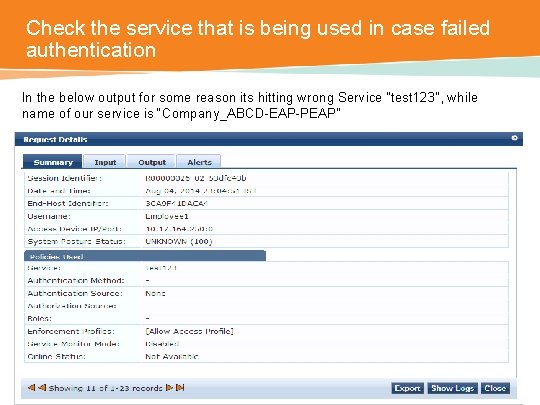
Check the service that is being used in case failed authentication In the below output for some reason its hitting wrong Service “test 123”, while name of our service is “Company_ABCD-EAP-PEAP”

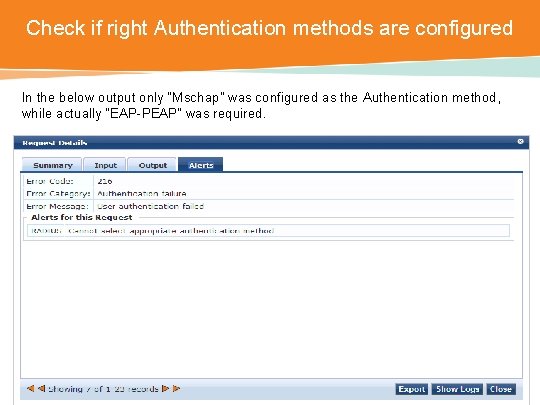
Check if right Authentication methods are configured In the below output only “Mschap” was configured as the Authentication method, while actually “EAP-PEAP” was required. CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

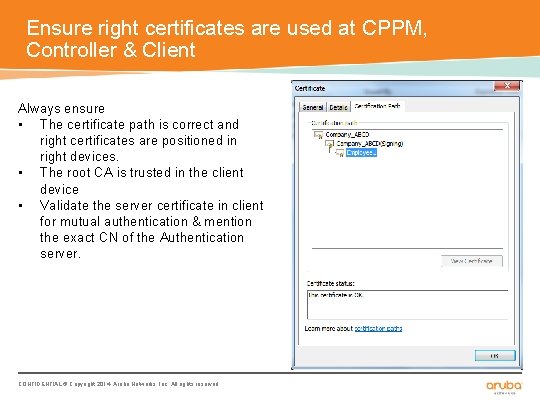
Ensure right certificates are used at CPPM, Controller & Client Always ensure • The certificate path is correct and right certificates are positioned in right devices. • The root CA is trusted in the client device • Validate the server certificate in client for mutual authentication & mention the exact CN of the Authentication server. CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved

THANK YOU!!! CONFIDENTIAL © Copyright 2014. Aruba Networks, Inc. All rights reserved