Any Connect Per App VPN 2015 Cisco andor







- Slides: 30


Any. Connect Per. App VPN © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 2

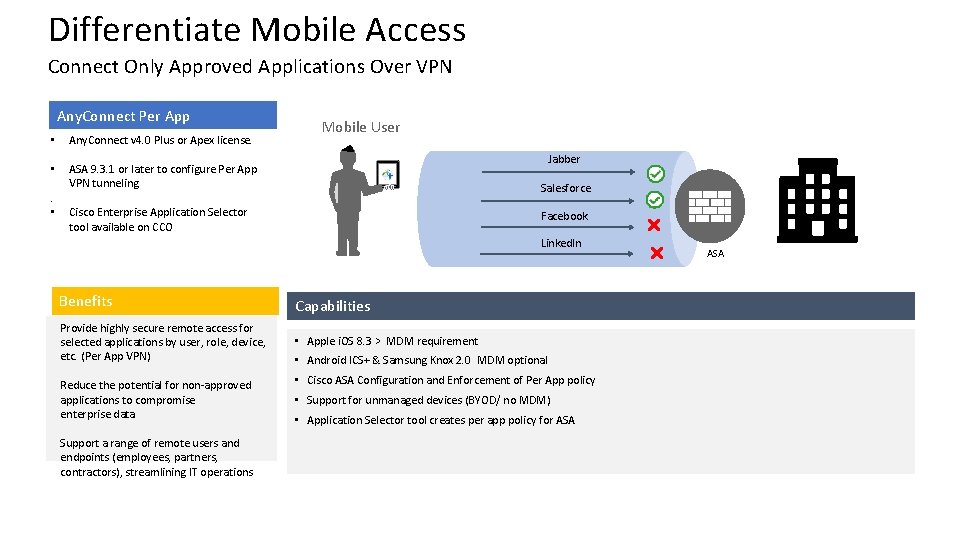
Differentiate Mobile Access Connect Only Approved Applications Over VPN Any. Connect Per App • Any. Connect v 4. 0 Plus or Apex license. • ASA 9. 3. 1 or later to configure Per App VPN tunneling . • Mobile User Jabber Salesforce Cisco Enterprise Application Selector tool available on CCO Facebook Linked. In Benefits Capabilities Provide highly secure remote access for selected applications by user, role, device, etc. (Per App VPN) • Apple i. OS 8. 3 > MDM requirement Reduce the potential for non-approved applications to compromise enterprise data Support a range of remote users and endpoints (employees, partners, contractors), streamlining IT operations • Android ICS+ & Samsung Knox 2. 0 MDM optional • Cisco ASA Configuration and Enforcement of Per App policy • Support for unmanaged devices (BYOD/ no MDM) • Application Selector tool creates per app policy for ASA

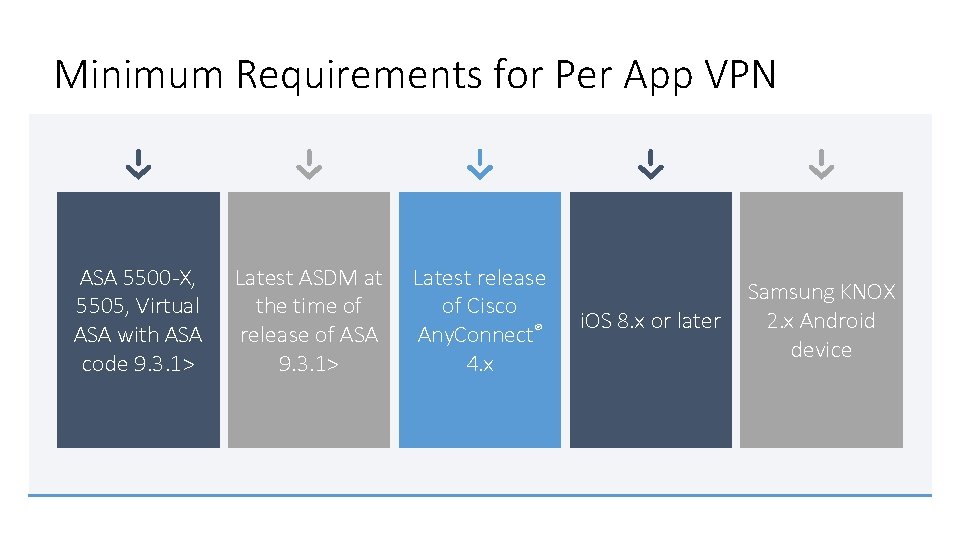
Minimum Requirements for Per App VPN ASA 5500 -X, 5505, Virtual ASA with ASA code 9. 3. 1> Latest ASDM at the time of release of ASA 9. 3. 1> Latest release of Cisco Any. Connect® 4. x Samsung KNOX i. OS 8. x or later 2. x Android device

Policy provisioned by third-party MDM vendor Allows application policy enforcement by Cisco® ASA and Cisco Any. Connect® Allows wildcard application package identifiers to equal com. anybird. * Per App Managed The lifetime of VPN is not necessarily in users’ control

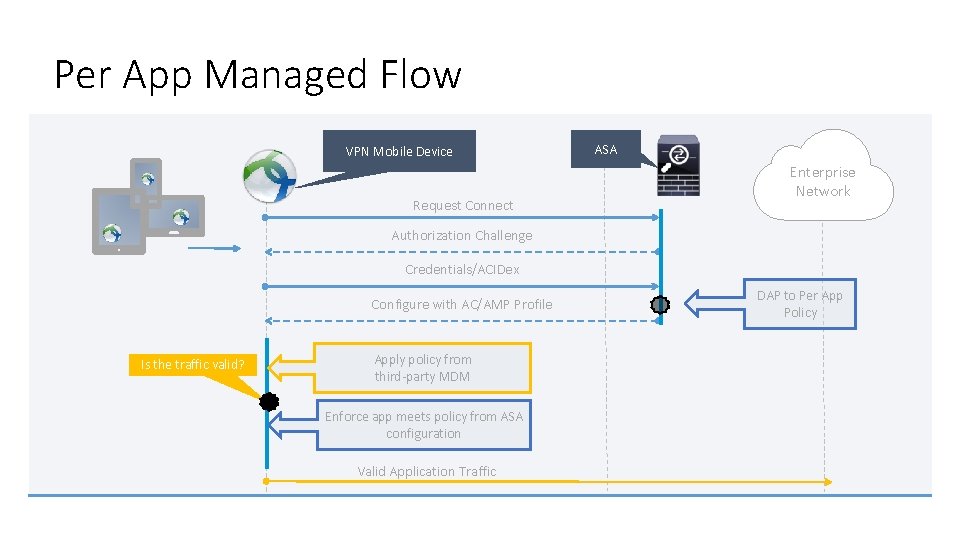
Per App Managed Flow VPN Mobile Device Request Connect ASA Enterprise Network Authorization Challenge Credentials/ACIDex Configure with AC/AMP Profile Is the traffic valid? Apply policy from third-party MDM Enforce app meets policy from ASA configuration Valid Application Traffic DAP to Per App Policy

Managed (MDM) Per App VPN i. OS Use Case Requirements § Cisco Any. Connect® Enterprise Application Selector Tool § Cisco® ASA 9. 3. 2 or newer § ASDM 7. 3. 1 - Any. Connect custom attribute enhancement § Any. Connect 4. 0. 03004 or newer § This capability must be used in conjunction with an MDM or EMM vendor § A Plus or Apex license Note: Android is also supported in the managed (MDM) use case

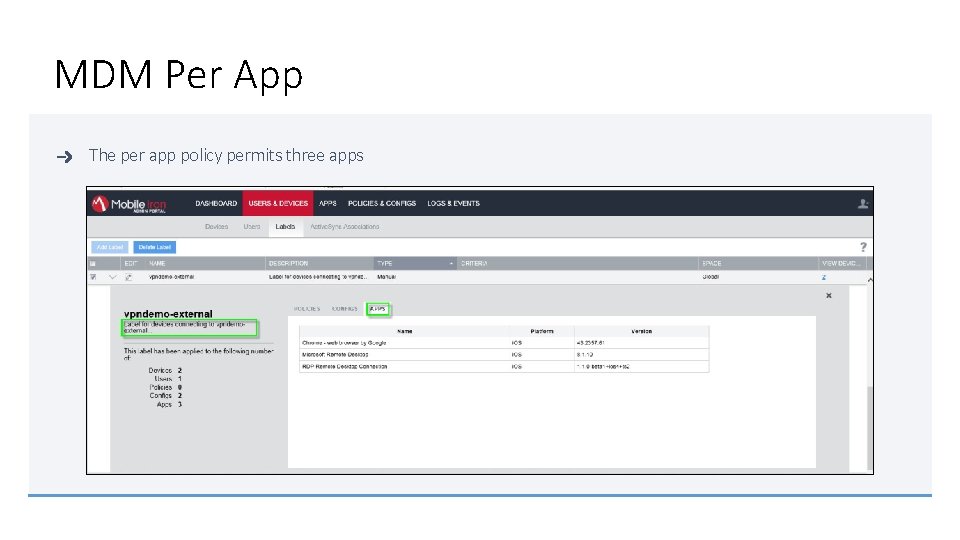
MDM Per App The per app policy permits three apps

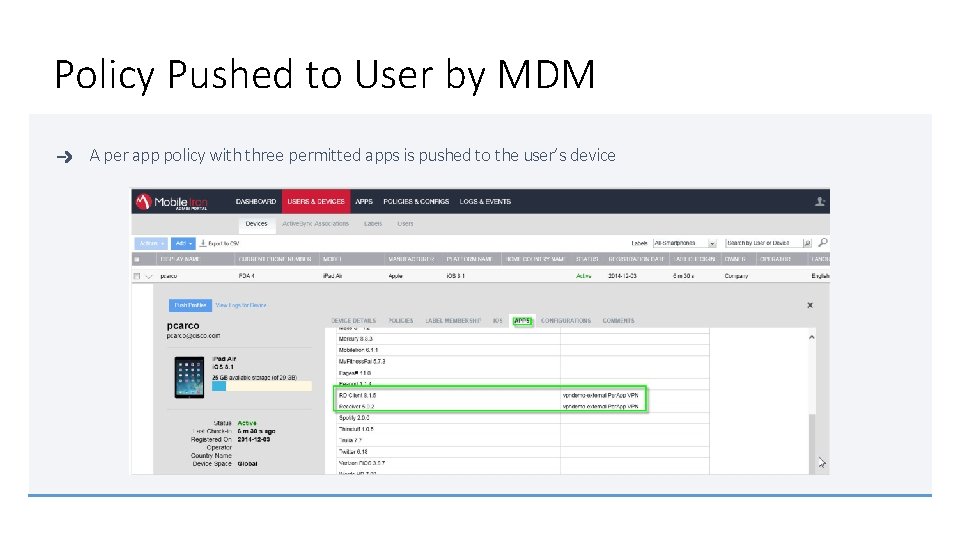
Policy Pushed to User by MDM A per app policy with three permitted apps is pushed to the user’s device

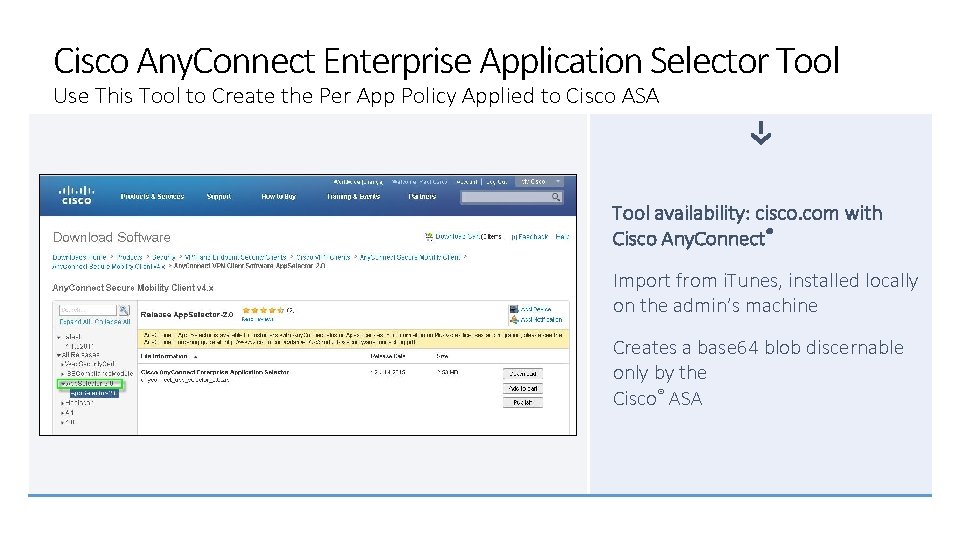
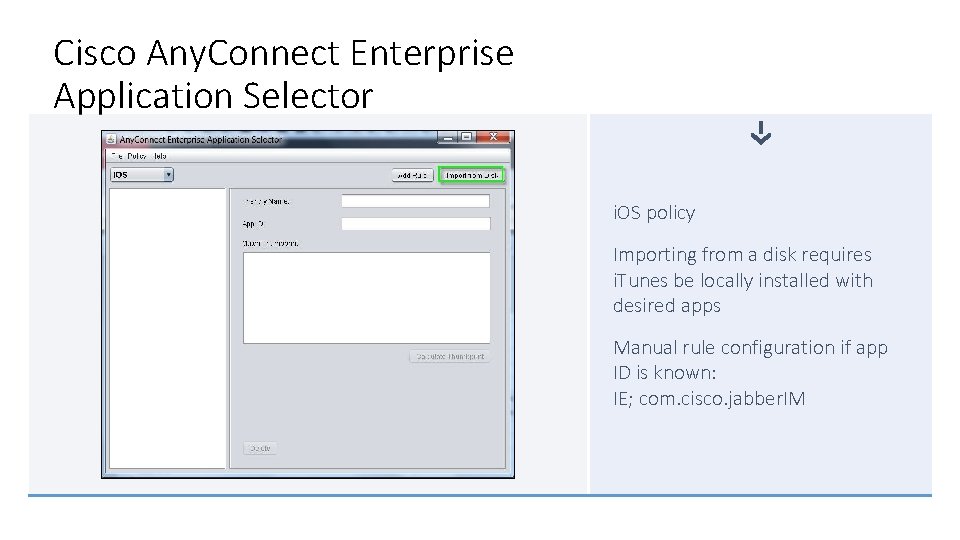
Cisco Any. Connect Enterprise Application Selector Tool Use This Tool to Create the Per App Policy Applied to Cisco ASA Tool availability: cisco. com with Cisco Any. Connect® Import from i. Tunes, installed locally on the admin’s machine Creates a base 64 blob discernable only by the Cisco® ASA

Cisco Any. Connect Enterprise Application Selector i. OS policy Importing from a disk requires i. Tunes be locally installed with desired apps Manual rule configuration if app ID is known: IE; com. cisco. jabber. IM

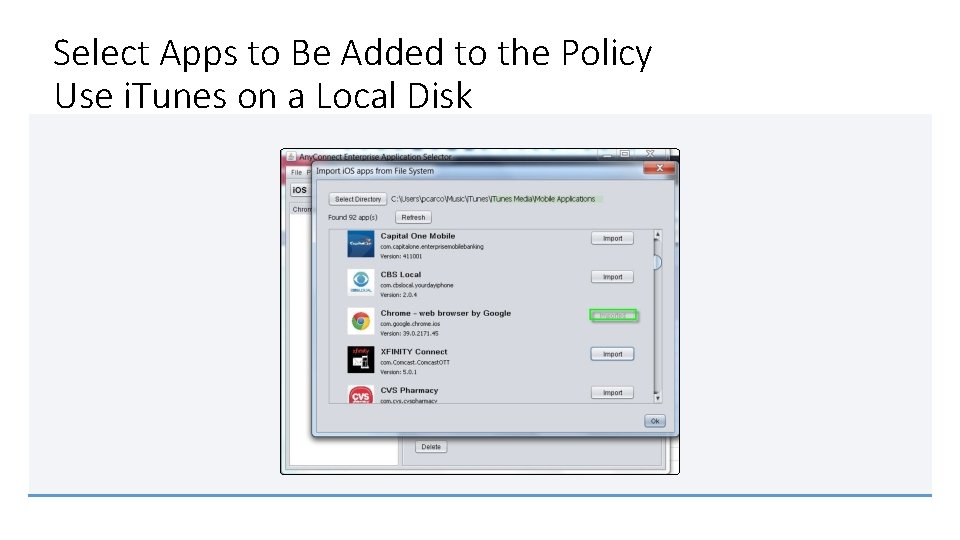
Select Apps to Be Added to the Policy Use i. Tunes on a Local Disk

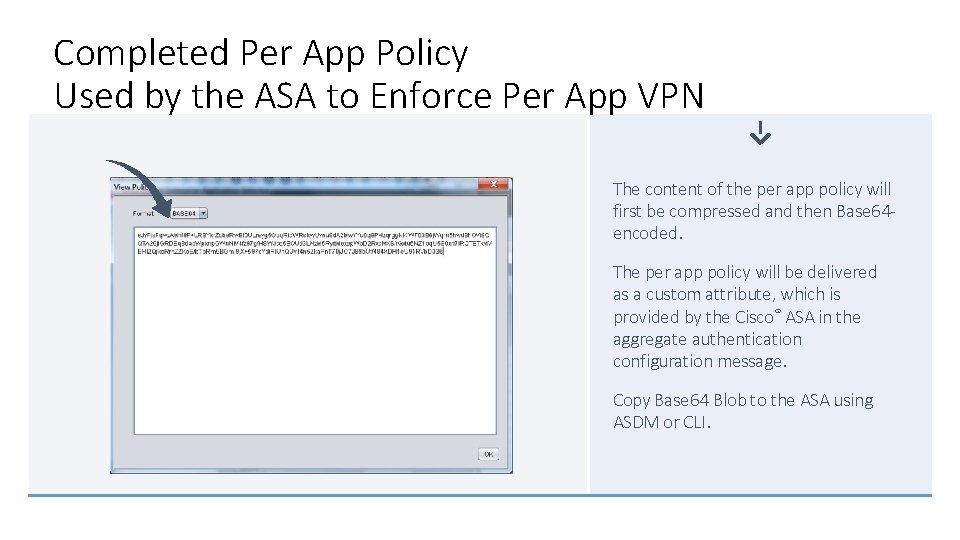
Completed Per App Policy Used by the ASA to Enforce Per App VPN The content of the per app policy will first be compressed and then Base 64 encoded. The per app policy will be delivered as a custom attribute, which is provided by the Cisco® ASA in the aggregate authentication configuration message. Copy Base 64 Blob to the ASA using ASDM or CLI.

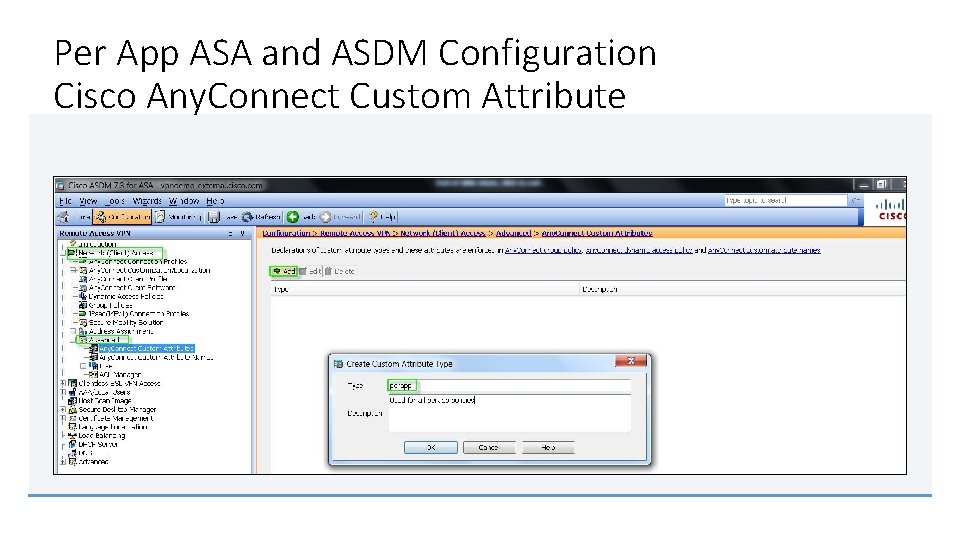
Per App ASA and ASDM Configuration Cisco Any. Connect Custom Attribute

Per App ASA and ASDM Configuration Cisco Any. Connect Custom Name (Policy) Copy and paste the Base 64 Blob from the application selector tool here This policy can be applied to either a group policy or dynamic access policy

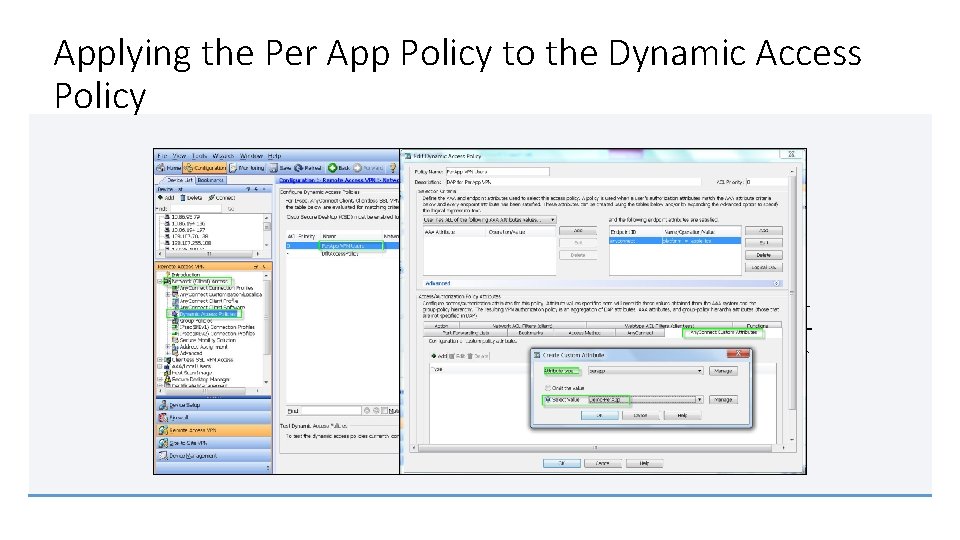
Applying the Per App Policy to the Dynamic Access Policy

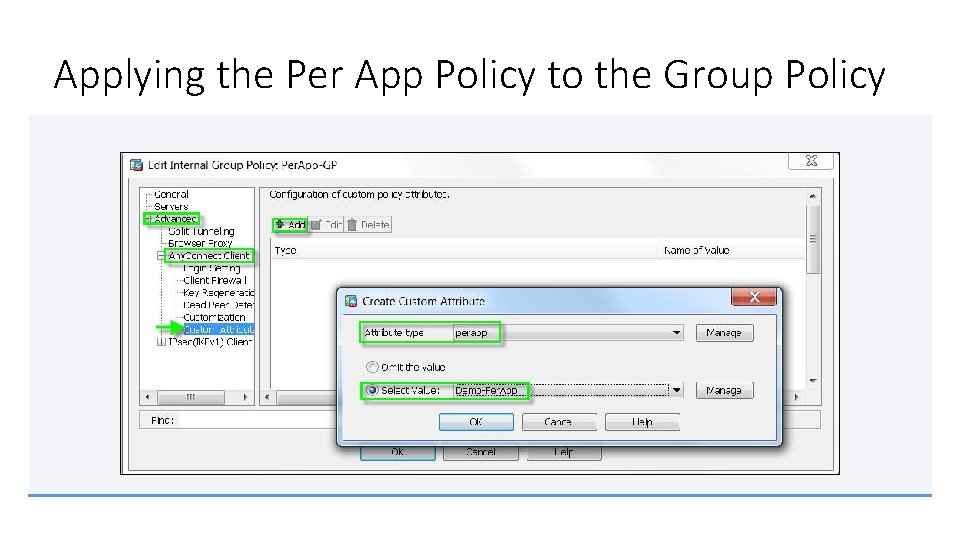
Applying the Per App Policy to the Group Policy

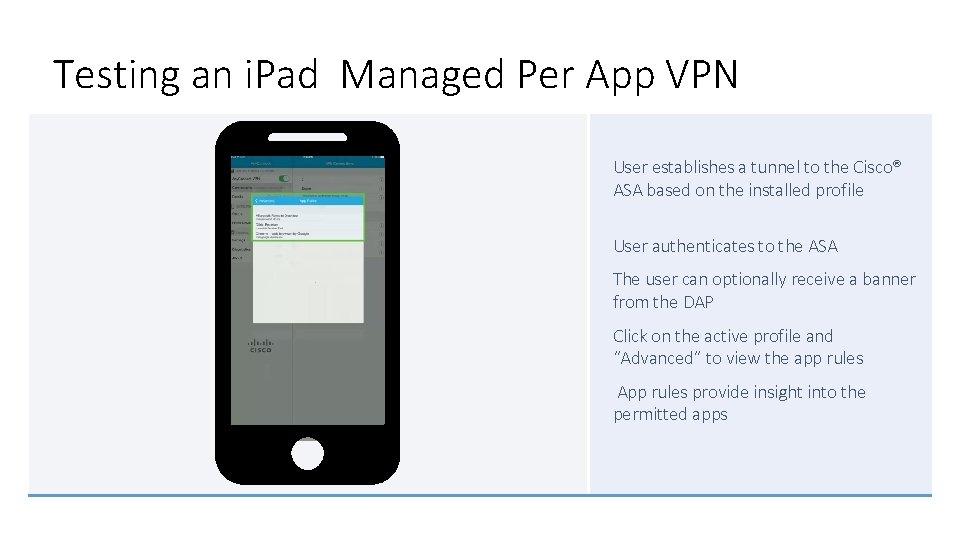
Testing an i. Pad Managed Per App VPN User establishes a tunnel to the Cisco® ASA based on the installed profile User authenticates to the ASA The user can optionally receive a banner from the DAP Click on the active profile and “Advanced” to view the app rules App rules provide insight into the permitted apps

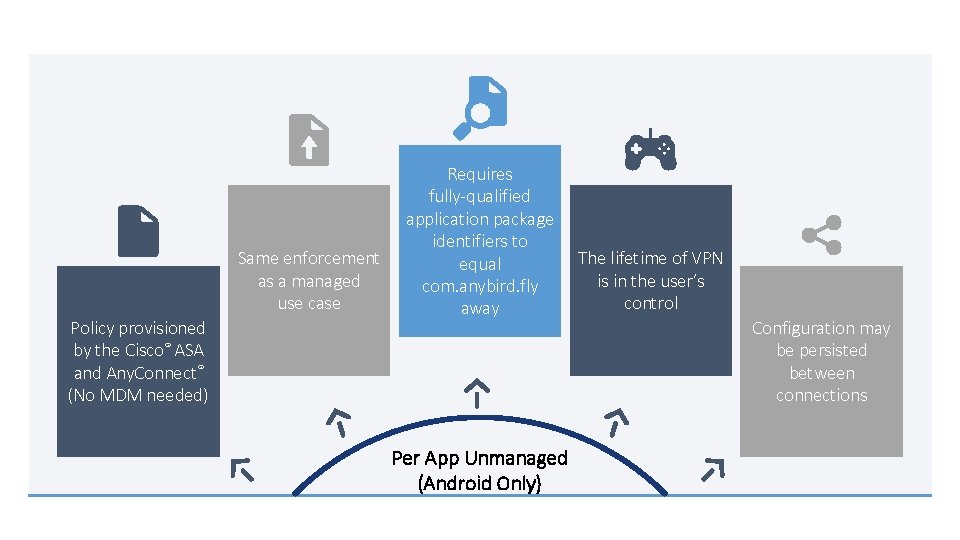
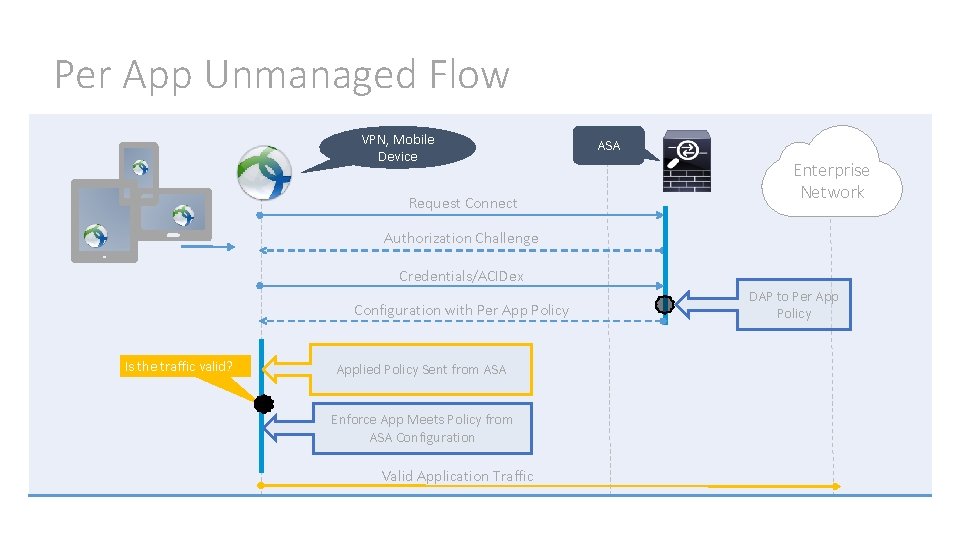
Same enforcement as a managed use case Policy provisioned by the Cisco® ASA and Any. Connect® (No MDM needed) Requires fully-qualified application package identifiers to equal com. anybird. fly away Per App Unmanaged (Android Only) The lifetime of VPN is in the user’s control Configuration may be persisted between connections

Per App Unmanaged Flow VPN, Mobile Device Request Connect ASA Enterprise Network Authorization Challenge Credentials/ACIDex Configuration with Per App Policy Is the traffic valid? Applied Policy Sent from ASA Enforce App Meets Policy from ASA Configuration Valid Application Traffic DAP to Per App Policy

Unmanaged Per App VPN Use Case Android Only A Cisco Any. Connect® client will be required to configure the device for Per App tunneling. The Per App configuration will be derived from the Per App policy provided by the ASA. The Per App policy will be used both to configure which applications are tunneled and validate the application when it attempts to pass traffic. Any. Connect ICS+ Android 4. x ICS+ Android 5. 0 Lolipop Any. Connect for Samsung KNOX Android 4. 3 + Note: If not using KNOX, it is recommended to use Cisco® Any. Connect ICS+ on Samsung devices

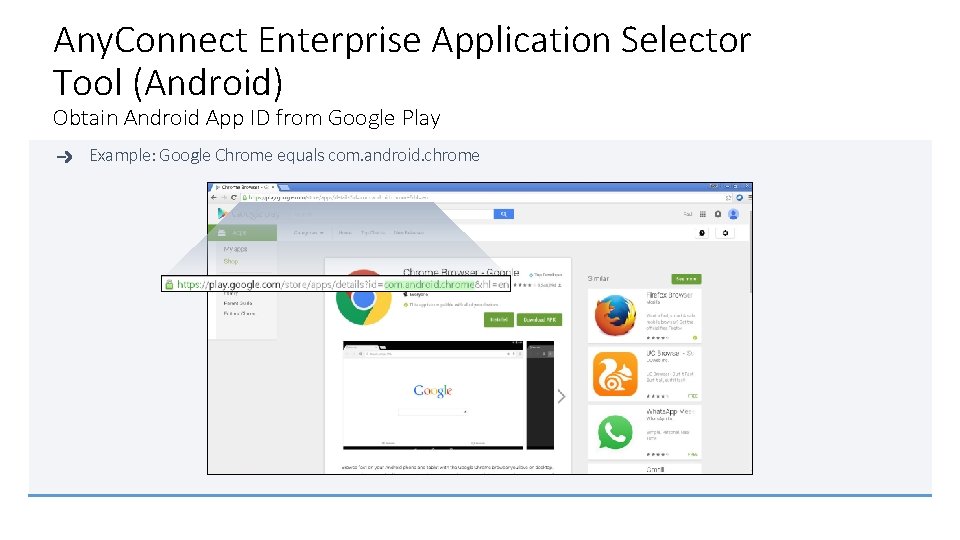
Any. Connect Enterprise Application Selector Tool (Android) Obtain Android App ID from Google Play Example: Google Chrome equals com. android. chrome

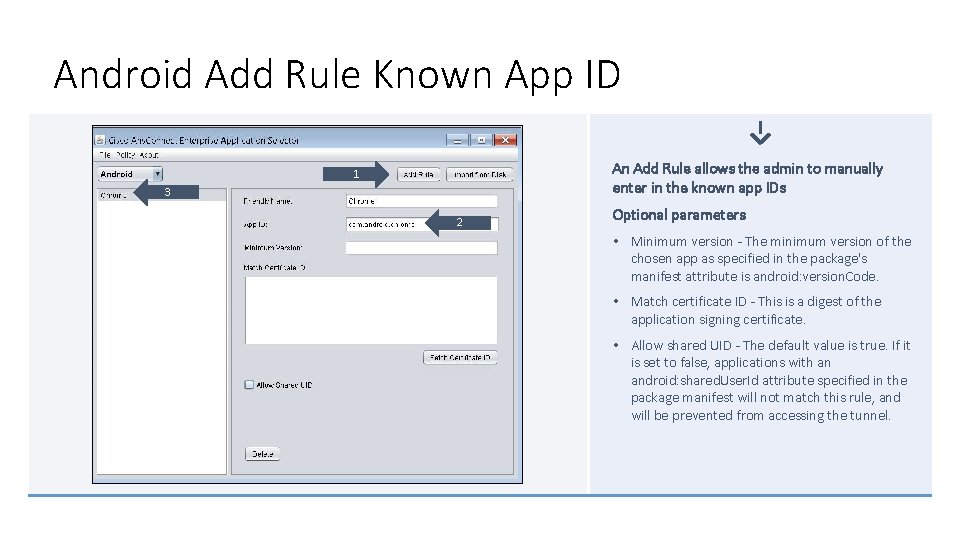
Android Add Rule Known App ID An Add Rule allows the admin to manually enter in the known app IDs 1 3 2 Optional parameters • Minimum version - The minimum version of the chosen app as specified in the package's manifest attribute is android: version. Code. • Match certificate ID - This is a digest of the application signing certificate. • Allow shared UID - The default value is true. If it is set to false, applications with an android: shared. User. Id attribute specified in the package manifest will not match this rule, and will be prevented from accessing the tunnel.

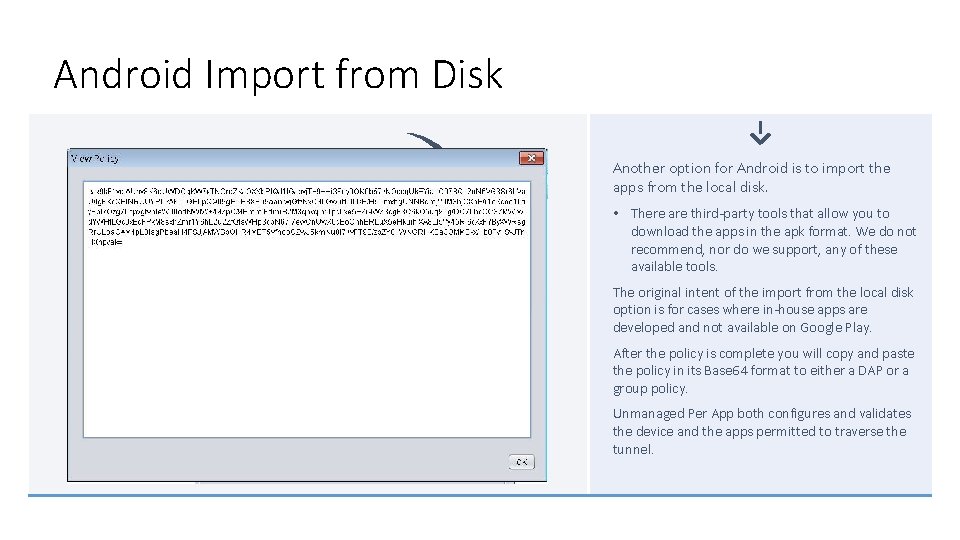
Android Import from Disk Another option for Android is to import the apps from the local disk. • There are third-party tools that allow you to download the apps in the apk format. We do not recommend, nor do we support, any of these available tools. The original intent of the import from the local disk option is for cases where in-house apps are developed and not available on Google Play. After the policy is complete you will copy and paste the policy in its Base 64 format to either a DAP or a group policy. Unmanaged Per App both configures and validates the device and the apps permitted to traverse the tunnel.

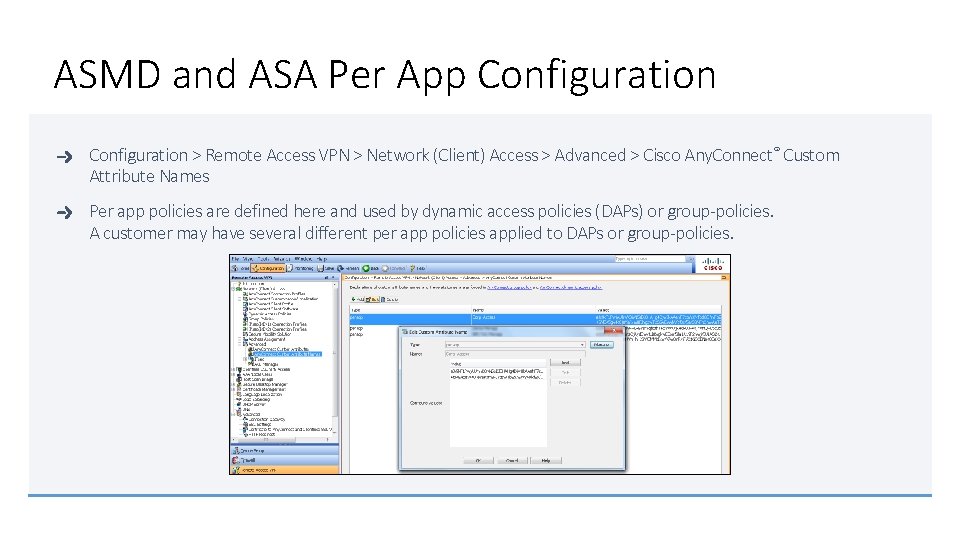
ASDM and ASA Per App Configuration > Remote Access VPN > Network (Client) Access > Advanced > Cisco Any. Connect® Custom Attributes Defined once and used for all per app policies

ASMD and ASA Per App Configuration > Remote Access VPN > Network (Client) Access > Advanced > Cisco Any. Connect® Custom Attribute Names Per app policies are defined here and used by dynamic access policies (DAPs) or group-policies. A customer may have several different per app policies applied to DAPs or group-policies.

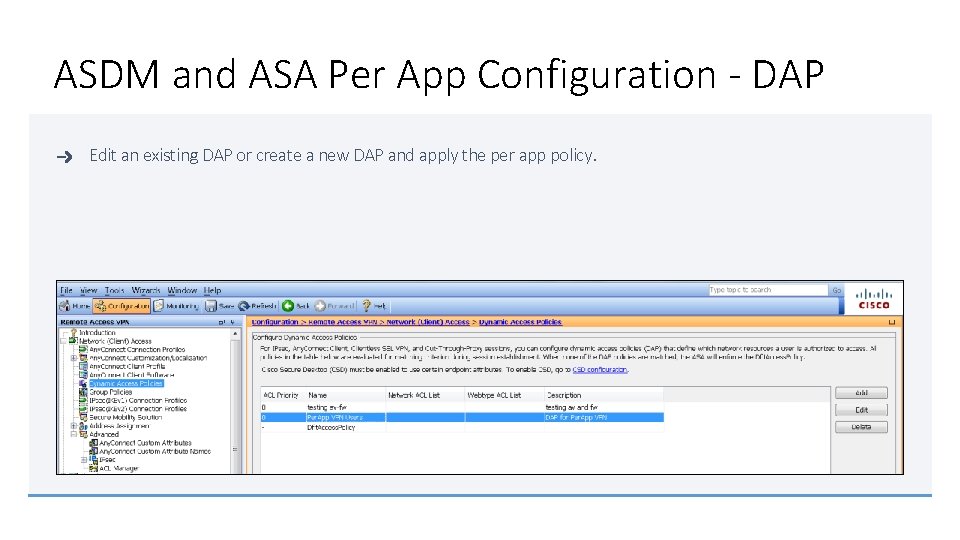
ASDM and ASA Per App Configuration - DAP Edit an existing DAP or create a new DAP and apply the per app policy.

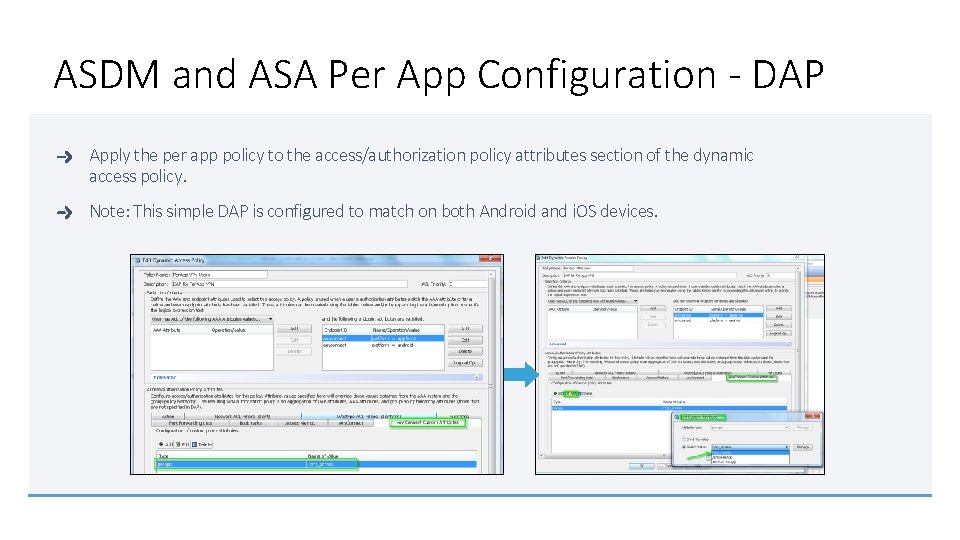
ASDM and ASA Per App Configuration - DAP Apply the per app policy to the access/authorization policy attributes section of the dynamic access policy. Note: This simple DAP is configured to match on both Android and i. OS devices.

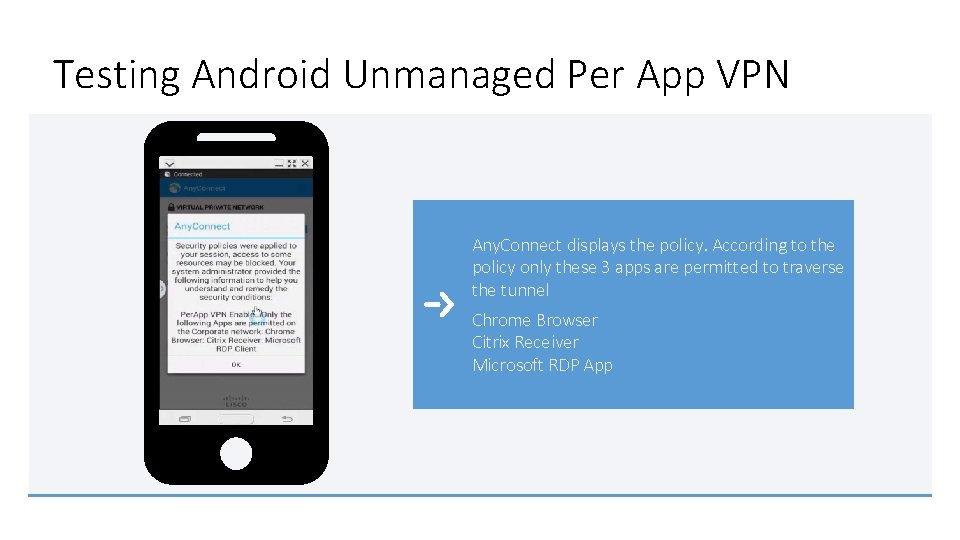
Testing Android Unmanaged Per App VPN Any. Connect displays the policy. According to the This connection is configured to use a certificate for authentication to the Cisco Adaptive Security policy only these 3 apps are permitted to traverse This banner is the result of the Dynamic Access Appliance (ASA) which makes the session the tunnel Policy assigned to the session. We optionally establishment seamless for the user. added text to indicate what apps are permitted to Chrome Browser traverse the tunnel. Note: Certificate Authentication is only of several Citrix Receiver ways to authenticate to the ASA. Microsoft RDP App

Where Is This Applied on the ASA? 1. webvpn Command for the "Attribute Type": anyconnect-custom-attr <Attribute. Type> description <Attribute. Types. Description> NOTE: The Attriburte. Type MUST be lower case and called: perapp anyconnect-custom-attr perapp description Used for Apple i. OS Per. App VPN functionality 2. Global Command - This defines the "Attribute Name" and its "Value" (Opaque Blob): (syntex) anyconnect-custom-data <Attribute. Type> <Attribute. Names. Value> anyconnect-custom-data perapp i. OSPer. App. VPN This. Is. The. White. List. Blob 1 anyconnect-custom-data perapp i. OSPer. App. VPN This. Is. The. White. List. Blob 2 anyconnect-custom-data perapp Droid. Per. App. VPN This. Is. The. White. List. Blob. For. Android 1 anyconnect-custom-data perapp Droid. Per. App. VPN This. Is. The. White. List. Blob. For. Android 2 3. Group-Policy Command - This CLI is used to set the value of a custom Any. Connect ® attribute in a group policy: group-p i. OSPer. App. VPN att (syntex) anyconnect-custom <Attribute. Type> value <Attribute. Name (which maps to the Opaque. Blob)> anyconnect-custom perapp value i. OSPer. App. VPN 4. Dynamic-Access-Policy Command - This CLI is used to set the value of a custom Any. Connect attribute in a DAP record: dynamic-access-policy-record Applei. OSPer. App. VPN anyconnect-custom <Attribute. Type> value <Attribute. Name (which maps to the Opaque. Blob)> anyconnect-custom perapp value i. OSPer. App. VPN
 Cisco per app vpn
Cisco per app vpn Edu gtk bme
Edu gtk bme Andor planet
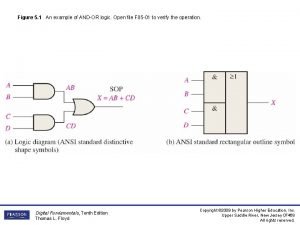
Andor planet Andor logic
Andor logic Andor györgy üzleti gazdaságtan
Andor györgy üzleti gazdaságtan Levophenol
Levophenol Andor györgy üzleti gazdaságtan
Andor györgy üzleti gazdaságtan Andor györgy üzleti gazdaságtan
Andor györgy üzleti gazdaságtan Whatever text
Whatever text Python andor
Python andor Andor matlab
Andor matlab Ssl vpn vs ipsec
Ssl vpn vs ipsec Ncsu vpn
Ncsu vpn Uf vpn
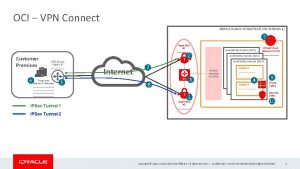
Uf vpn Outline vpn oracle cloud
Outline vpn oracle cloud Waterloo vpn
Waterloo vpn Connectvpn
Connectvpn Cisco connect 2019
Cisco connect 2019 Angelo state university tuition per semester
Angelo state university tuition per semester Drdp measures examples
Drdp measures examples No, there aren't
No, there aren't Any to any connectivity
Any to any connectivity Pertanyaan terbuka
Pertanyaan terbuka Chrome river login
Chrome river login Intune mdm
Intune mdm Villa doria dangri
Villa doria dangri Moltiplicazioni con numeri periodici
Moltiplicazioni con numeri periodici Coop per me e per te
Coop per me e per te Il mio diletto canto
Il mio diletto canto Eina per ugni nedega
Eina per ugni nedega 186 282 miles per second into meters per second
186 282 miles per second into meters per second