Anomaly Detection Carolina Ruiz Department of Computer Science





- Slides: 28

Anomaly Detection Carolina Ruiz Department of Computer Science WPI Slides based on Chapter 10 of “Introduction to Data Mining” textbook by Tan, Steinbach, Kumar (all figures and some slides taken from this chapter)

Class Discussion Points • What's an anomaly (or outlier)? • Give an example of a situation in which an anomaly should be removed during pre-processing of the dataset, and another example of a situation in which an anomaly is an interesting data instance worth keeping and/or studying in more detail. • Define each of the following approaches to anomaly detection, and describe the differences between each pair: – Model-based, Proximity-based, and Density-based techniques. • Can visualization be used to detect outliers? If so, how? – – Give specific examples of visualization techniques that can be used for anomaly detection. For each one, explain whether or not the visualization technique can be considered a Model-based (which includes Statistical), Proximity-based, or Density-based technique for anomaly detection.

Class Discussion Points (cont. ) • Define each of the following modes to anomaly detection, and describe the differences between pairs: • supervised, unsupervised, and semi-supervised. • Consider the case of a dataset that has labels identifying the anomalies and the task is to learn how to detect similar anomalies in unlabeled data. • Is that supervised or unsupervised anomaly detection? Explain. • Consider the case of a dataset that doesn't have labels identifying the anomalies and the task is to find how to assign a sound anomaly score, f(x), to each instance x in the dataset. – Is that supervised or unsupervised anomaly detection? Explain. • Precision, recall, and false positive rate are mentioned in the textbook as appropriate metrics to evaluate anomaly detection algorithms – What are those metrics and how can they be used to evaluate anomaly detection?

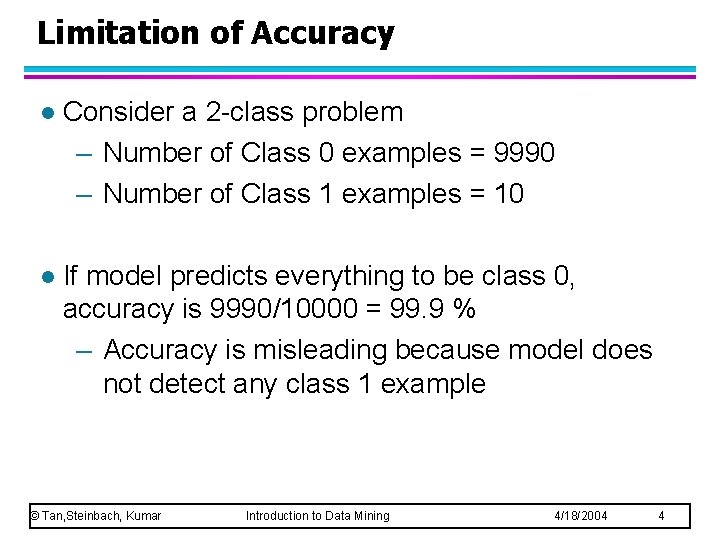
Limitation of Accuracy l Consider a 2 -class problem – Number of Class 0 examples = 9990 – Number of Class 1 examples = 10 l If model predicts everything to be class 0, accuracy is 9990/10000 = 99. 9 % – Accuracy is misleading because model does not detect any class 1 example © Tan, Steinbach, Kumar Introduction to Data Mining 4/18/2004 4

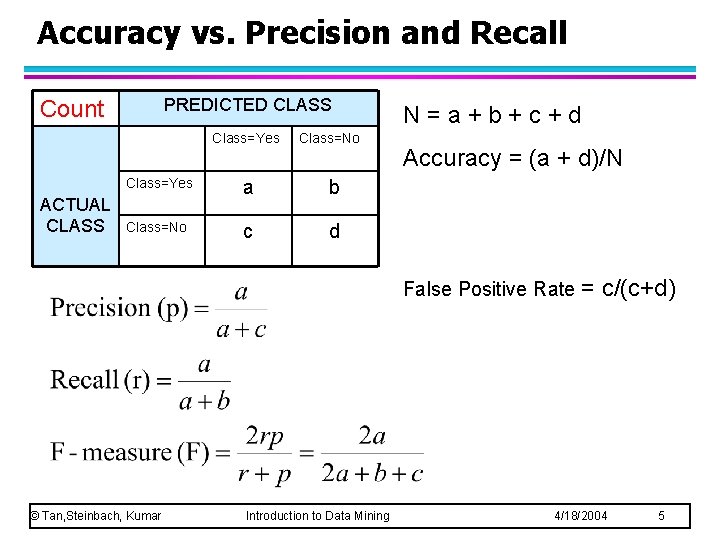
Accuracy vs. Precision and Recall PREDICTED CLASS Count Class=Yes ACTUAL CLASS Class=No Class=Yes a b Class=No c d N=a+b+c+d Accuracy = (a + d)/N False Positive Rate = © Tan, Steinbach, Kumar Introduction to Data Mining c/(c+d) 4/18/2004 5

Anomaly/Outlier Detection l What are anomalies/outliers? – The set of data points that are considerably different than the remainder of the data l Variants of Anomaly/Outlier Detection Problems – Given a database D, find all the data points x D with anomaly scores greater than some threshold t – Given a database D, find all the data points x D having the topn largest anomaly scores f(x) – Given a database D, containing mostly normal (but unlabeled) data points, and a test point x, compute the anomaly score of x with respect to D l Applications: – Credit card fraud detection, telecommunication fraud detection, network intrusion detection, fault detection © Tan, Steinbach, Kumar Introduction to Data Mining 4/18/2004 6

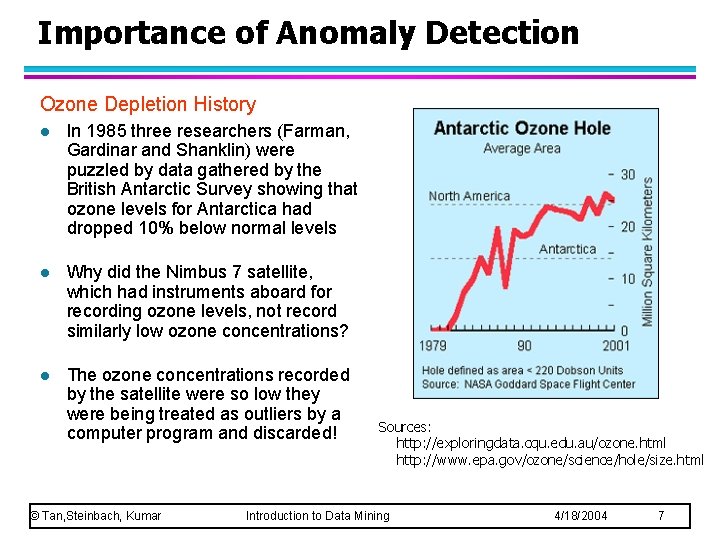
Importance of Anomaly Detection Ozone Depletion History l In 1985 three researchers (Farman, Gardinar and Shanklin) were puzzled by data gathered by the British Antarctic Survey showing that ozone levels for Antarctica had dropped 10% below normal levels l Why did the Nimbus 7 satellite, which had instruments aboard for recording ozone levels, not record similarly low ozone concentrations? l The ozone concentrations recorded by the satellite were so low they were being treated as outliers by a computer program and discarded! © Tan, Steinbach, Kumar Sources: http: //exploringdata. cqu. edu. au/ozone. html http: //www. epa. gov/ozone/science/hole/size. html Introduction to Data Mining 4/18/2004 7

Anomaly Detection l Challenges – How many outliers are there in the data? – Method is unsupervised u Validation can be quite challenging (just like for clustering) – Finding needle in a haystack l Working assumption: – There are considerably more “normal” observations than “abnormal” observations (outliers/anomalies) in the data © Tan, Steinbach, Kumar Introduction to Data Mining 4/18/2004 8

Anomaly Detection Schemes l General Steps – Build a profile of the “normal” behavior u Profile can be patterns or summary statistics for the overall population – Use the “normal” profile to detect anomalies u l Anomalies are observations whose characteristics differ significantly from the normal profile Types of anomaly detection schemes – Graphical & Statistical-based – Distance-based – Model-based © Tan, Steinbach, Kumar Introduction to Data Mining 4/18/2004 9

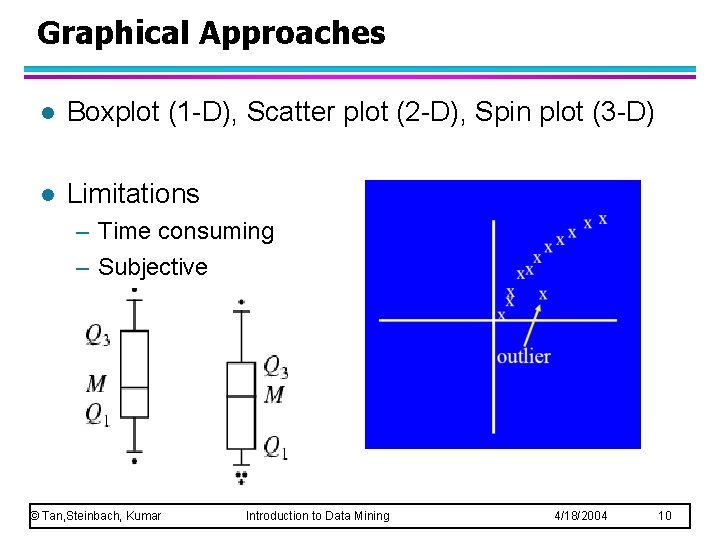
Graphical Approaches l Boxplot (1 -D), Scatter plot (2 -D), Spin plot (3 -D) l Limitations – Time consuming – Subjective © Tan, Steinbach, Kumar Introduction to Data Mining 4/18/2004 10

Anomaly Detection: General Approach For each of the anomaly detection approaches (statistical-based, proximity-based, density-based, and clustering-based) do 1. State the definition(s) of outlier used by the approach 2. How can this be definition used to assign an anomaly score to each data instance? 3. How does this anomaly detection approach work in general? Give an example to illustrate your description.

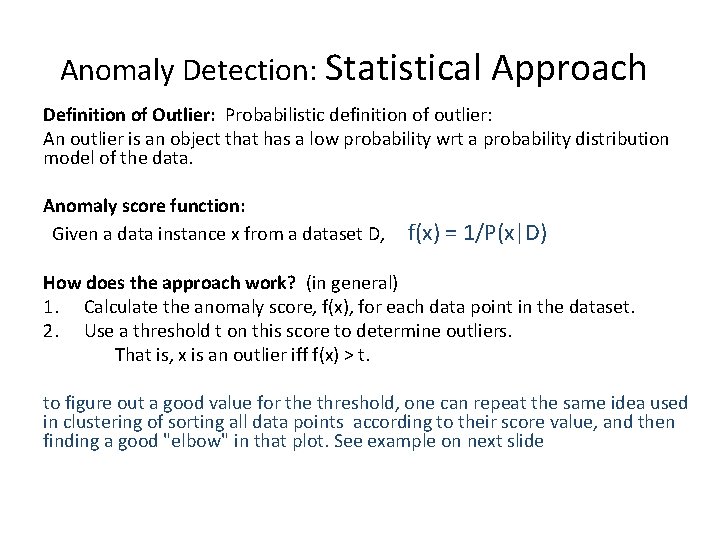
Anomaly Detection: Statistical Approach Definition of Outlier: Probabilistic definition of outlier: An outlier is an object that has a low probability wrt a probability distribution model of the data. Anomaly score function: Given a data instance x from a dataset D, f(x) = 1/P(x|D) How does the approach work? (in general) 1. Calculate the anomaly score, f(x), for each data point in the dataset. 2. Use a threshold t on this score to determine outliers. That is, x is an outlier iff f(x) > t. to figure out a good value for the threshold, one can repeat the same idea used in clustering of sorting all data points according to their score value, and then finding a good "elbow" in that plot. See example on next slide

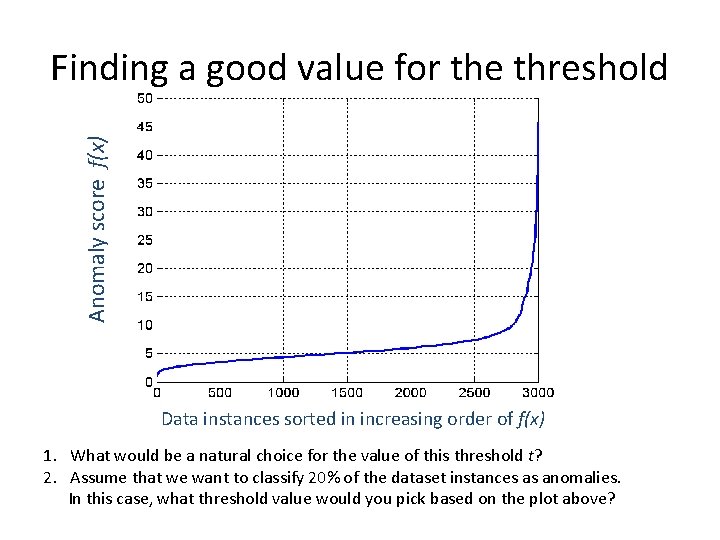
Anomaly score f(x) Finding a good value for the threshold Data instances sorted in increasing order of f(x) 1. What would be a natural choice for the value of this threshold t? 2. Assume that we want to classify 20% of the dataset instances as anomalies. In this case, what threshold value would you pick based on the plot above?

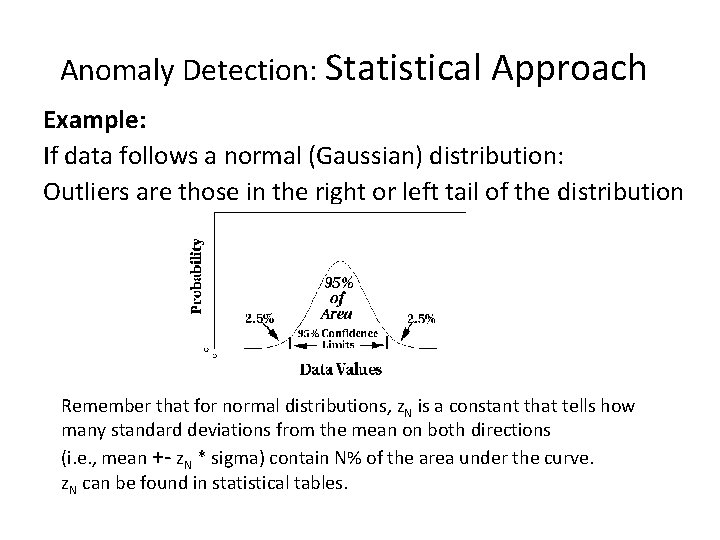
Anomaly Detection: Statistical Approach Example: If data follows a normal (Gaussian) distribution: Outliers are those in the right or left tail of the distribution Remember that for normal distributions, z. N is a constant that tells how many standard deviations from the mean on both directions (i. e. , mean +- z. N * sigma) contain N% of the area under the curve. z. N can be found in statistical tables.

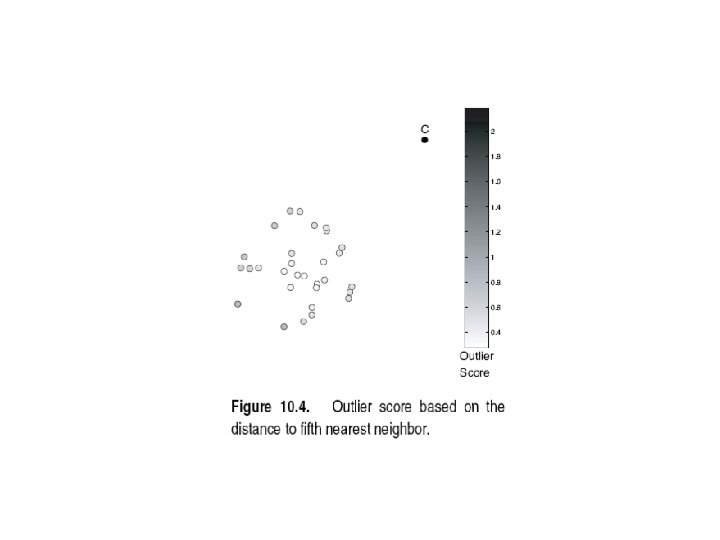
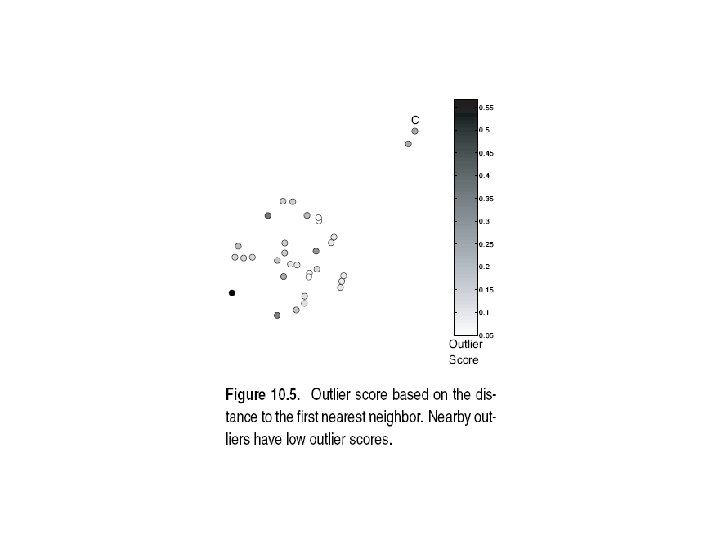
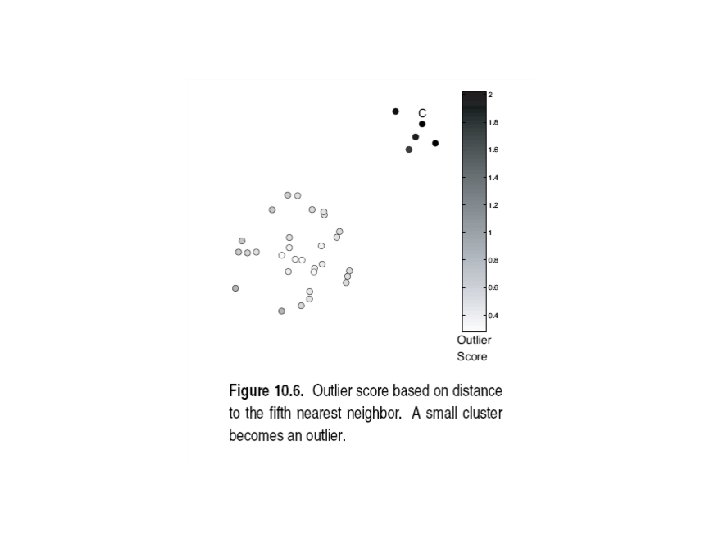
Anomaly Detection: Proximity Approach Definition of Outlier: Proximity-based definition of outlier using distance to k-nearest neighbor Anomaly score function: Given a data instance x from a dataset D and a value k, Alternate definitions: • • f(x) = Distance between x and its k-nearest neighbor f(x) = Average distance between x and its k-nearest neighbors How does the approach work? (in general): 1. Calculate the anomaly score, f(x), for each data point in the dataset. 2. Use a threshold t on this score to determine outliers. That is, x is an outlier iff f(x) > t. - To figure out a good value for k, one can repeat the same idea used in clustering: Run experiments with different values of k - To figure out a good value for the threshold, one can repeat the same idea used in clustering of sorting all data points according to their score value, and then finding a good "elbow" in that plot.

Anomaly Detection: Proximity Approach Examples: Next 4 slides





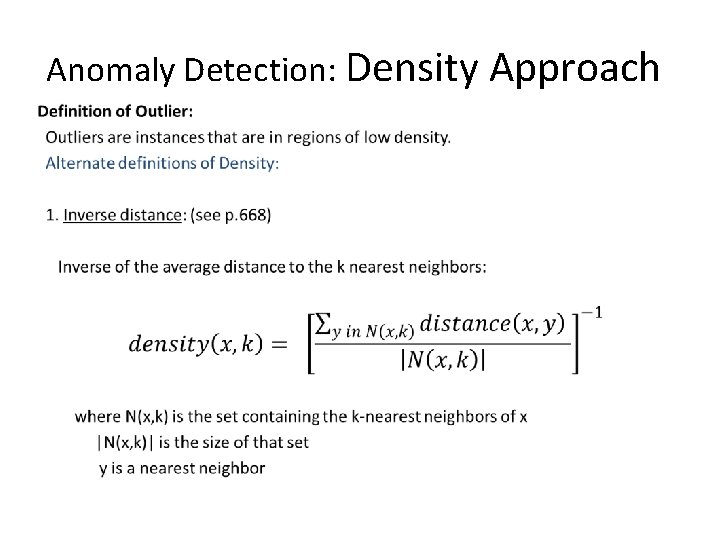
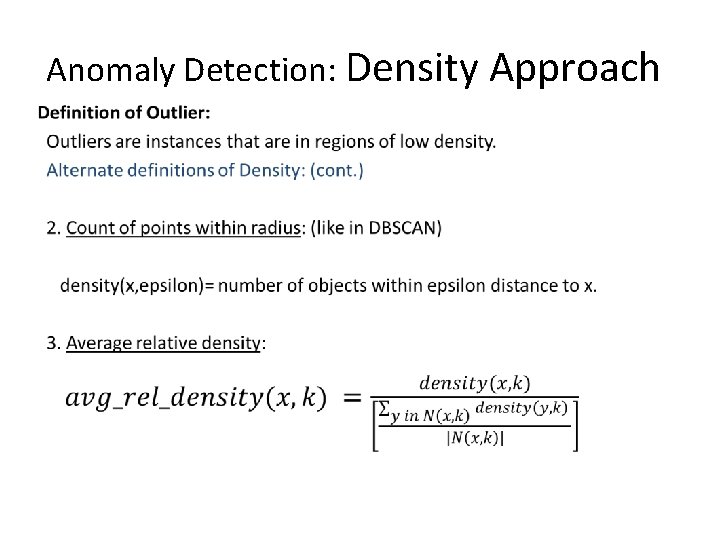
Anomaly Detection: Density Approach •

Anomaly Detection: Density Approach •

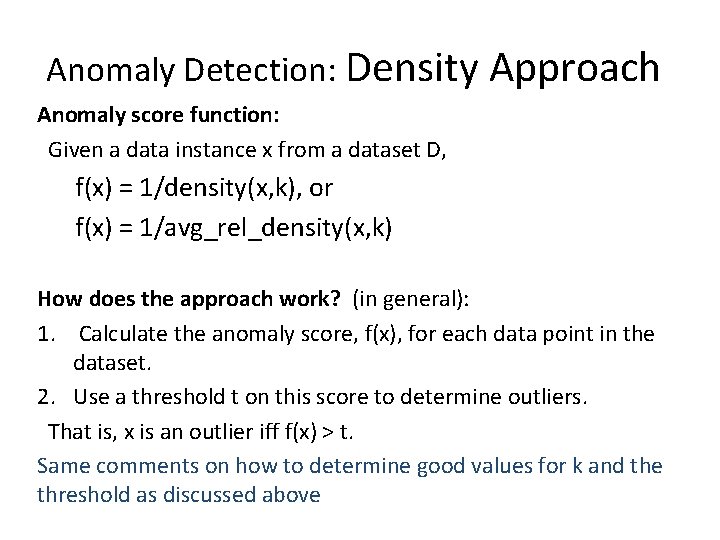
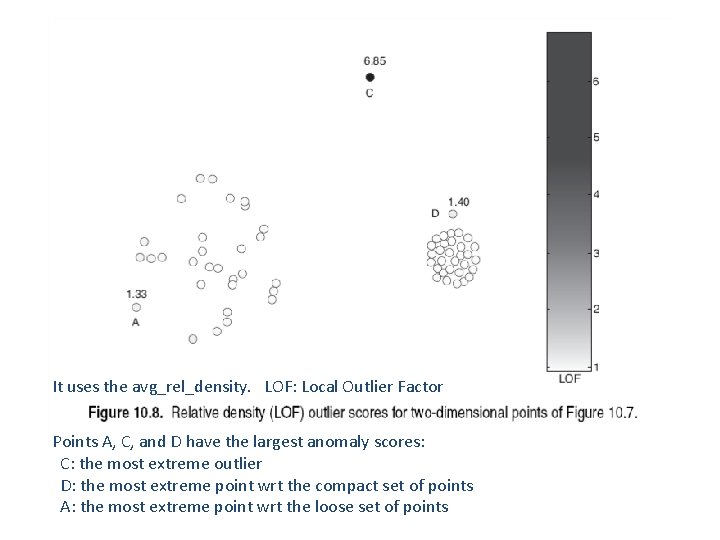
Anomaly Detection: Density Approach Anomaly score function: Given a data instance x from a dataset D, f(x) = 1/density(x, k), or f(x) = 1/avg_rel_density(x, k) How does the approach work? (in general): 1. Calculate the anomaly score, f(x), for each data point in the dataset. 2. Use a threshold t on this score to determine outliers. That is, x is an outlier iff f(x) > t. Same comments on how to determine good values for k and the threshold as discussed above

It uses the avg_rel_density. LOF: Local Outlier Factor Points A, C, and D have the largest anomaly scores: C: the most extreme outlier D: the most extreme point wrt the compact set of points A: the most extreme point wrt the loose set of points

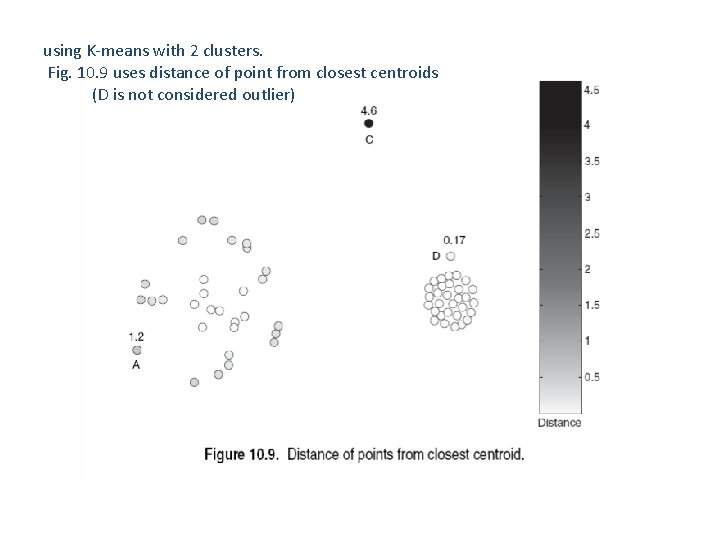
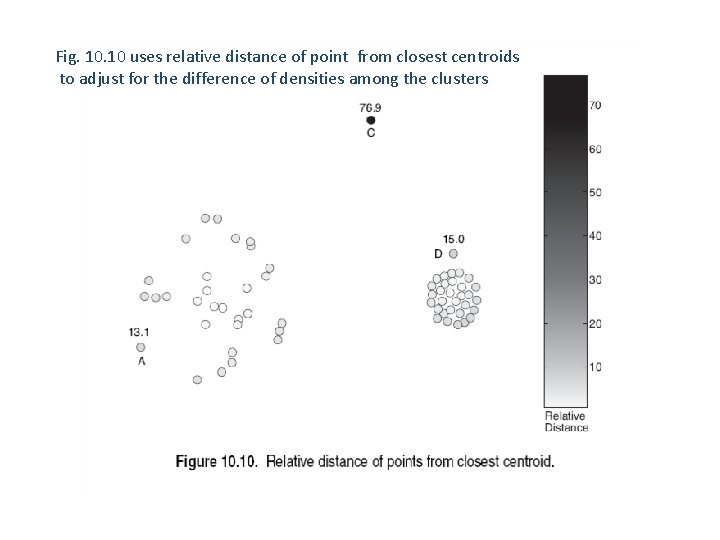
Anomaly Detection: Clustering Approach Definition of Outlier: Clustering-based definition of outlier: A data instance is a cluster-based outlier if the instance does not strongly belong to any cluster. Anomaly score function: Given a data instance x from a dataset D, Alternate definitions: 1. f(x) = distance between x and its closest centroid 2. f(x) : (called relative distance) = ratio between the point's distance from the centroid to the median distance of all points in the cluster from the centroid 3. f(x) = improvement in the goodness of a cluster (as measured by an objective function) when x is removed

Anomaly Detection: Clustering Approach How does the approach work? (in general): 1. Calculate the anomaly score, f(x), for each data point in the dataset. 2. Use a threshold t on this score to determine outliers. That is, x is an outlier iff f(x) > t. Same comments on how to determine good values for k and the threshold as discussed above.

using K-means with 2 clusters. Fig. 10. 9 uses distance of point from closest centroids (D is not considered outlier)

Fig. 10 uses relative distance of point from closest centroids to adjust for the difference of densities among the clusters
 Anomaly detection in google analytics
Anomaly detection in google analytics Anomaly detection spark
Anomaly detection spark Agrima seth
Agrima seth Elasticsearch anomaly detection
Elasticsearch anomaly detection Flink anomaly detection
Flink anomaly detection System log analysis for anomaly detection
System log analysis for anomaly detection Carolina ruiz wpi
Carolina ruiz wpi Carolina ruiz wpi
Carolina ruiz wpi Boosting in data mining
Boosting in data mining Carolina ruiz wpi
Carolina ruiz wpi Chapel hill computer science
Chapel hill computer science Georgia, south carolina, north carolina, virginia, maryland
Georgia, south carolina, north carolina, virginia, maryland Map of north carolina and south carolina
Map of north carolina and south carolina Maryland virginia north carolina south carolina and georgia
Maryland virginia north carolina south carolina and georgia Virginia, maryland, north carolina, south carolina, georgia
Virginia, maryland, north carolina, south carolina, georgia Mathematical computation ucl
Mathematical computation ucl Electrical engineering northwestern
Electrical engineering northwestern Computer science department rutgers
Computer science department rutgers Meredith hutchin stanford
Meredith hutchin stanford Florida state university ms in cs
Florida state university ms in cs Ubc computer science department
Ubc computer science department Bhargavi goswami
Bhargavi goswami Computer science department columbia
Computer science department columbia Describe your favourite subject english
Describe your favourite subject english Checksum in computer networks with example
Checksum in computer networks with example Forwarding in computer architecture
Forwarding in computer architecture Hazard detection and resolution in computer architecture
Hazard detection and resolution in computer architecture What is crc in computer network
What is crc in computer network Error detection and correction in computer networks
Error detection and correction in computer networks