Anatomy of the Attack How Cybersecurity Investigations Actually


Anatomy of the Attack – How Cybersecurity Investigations Actually Work Jessica Payne Microsoft Global Incident Response and Recovery WIN 433


This is the FIB. We noticed your server at x. x is communicating with a server associated with a malicious actor. Good luck with that. . Contoso CISO



Typical Attack Power: Domain Controllers 1. Bad guy targets workstations with malware 2. User is compromised, Bad guy elevates privilege and harvests credentials. Data: Servers and Applications 3. Bad guy starts “credentials crabwalk” 4. Bad guy finds host with domain privileged credentials, steals, and elevates privileges Access: Users and Workstations 5. Bad guy owns network, can do what he wants.
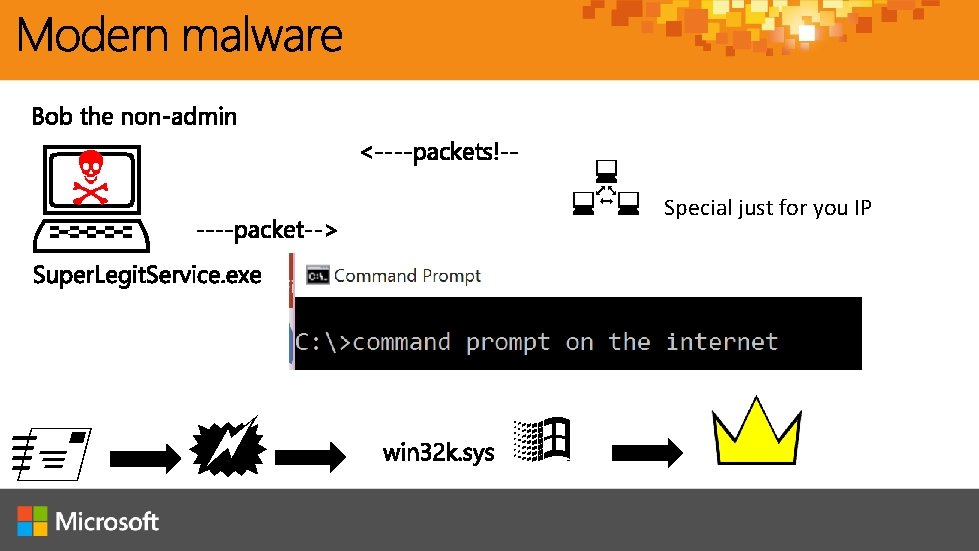
Special just for you IP

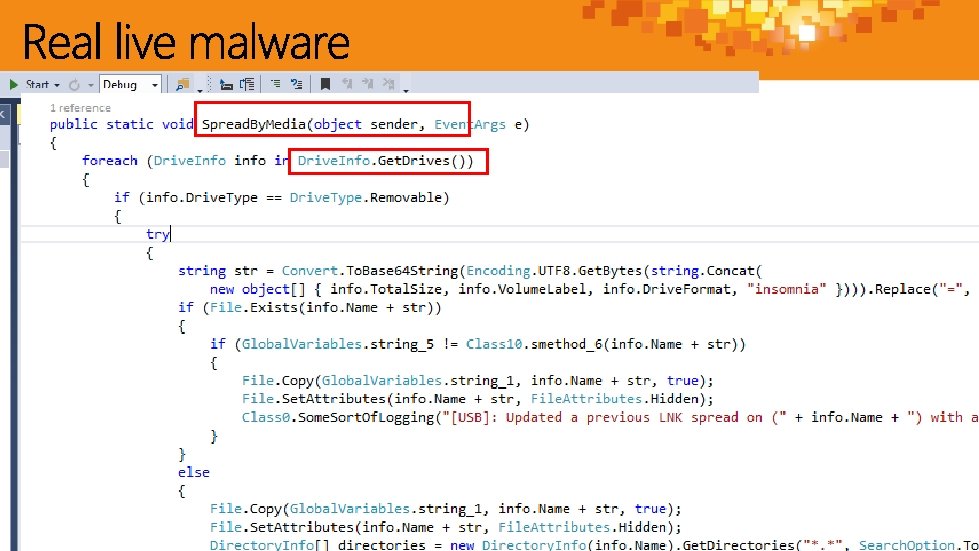
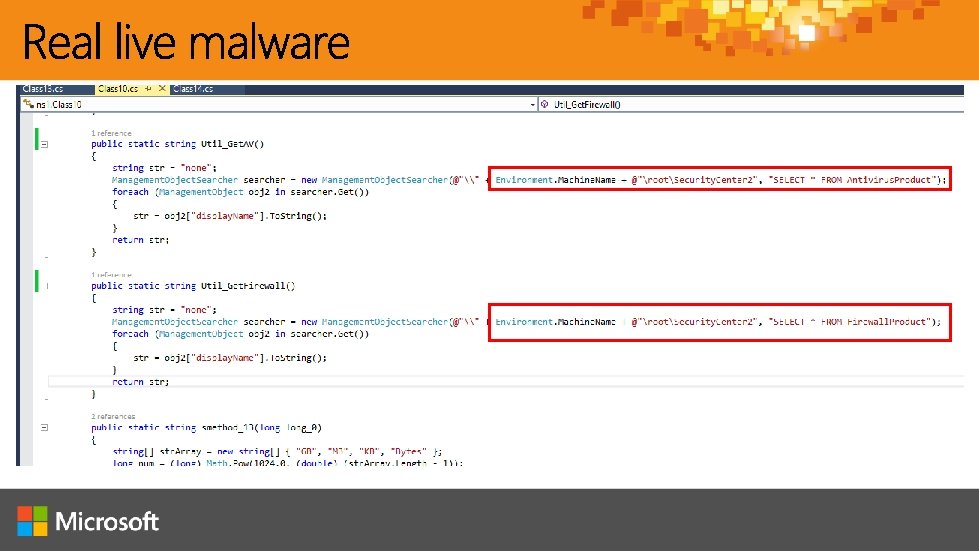
FIB FLASH FIB Liason Alert #NC-1701 FIB has obtained information that the actor known as APT 2005 “Rapid Rhino” has begun attacks against the kitty litter industry vector. Technical Details : Chri. Kit is a first generation Trojan that has full remote shell capabilities and credential theft toolsets. Traffic is beaconed over typical HTTP/HTTPs ports with minimal identifying strings. The Trojan is installed as a service, where the name varies.







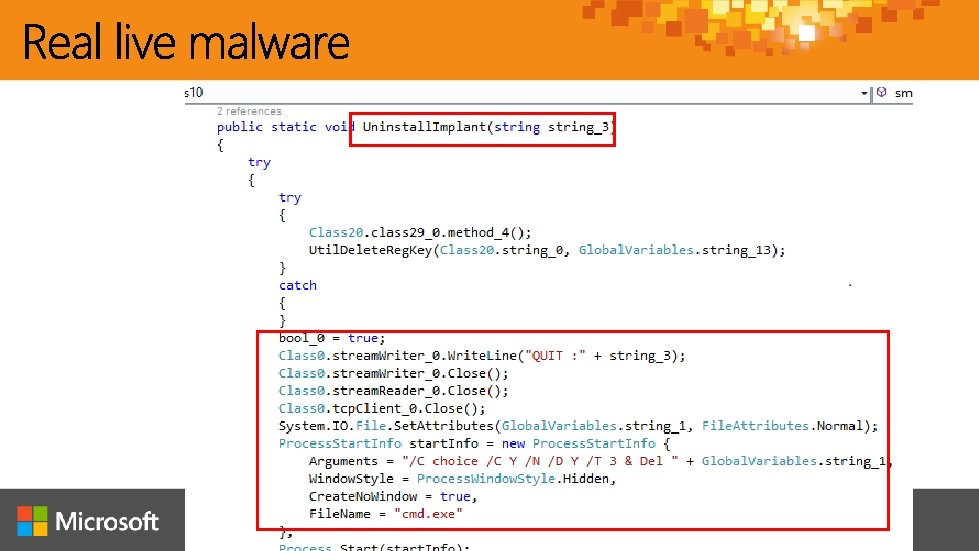
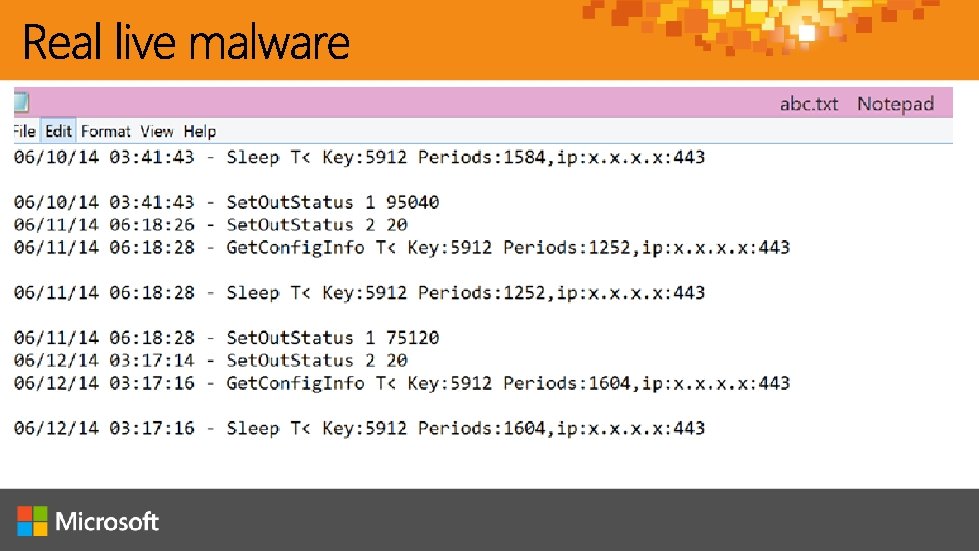
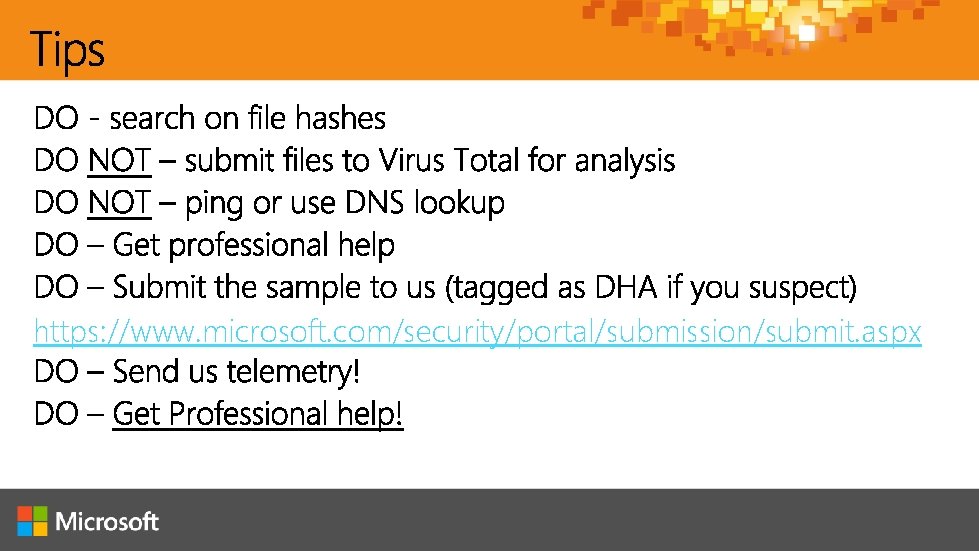
https: //www. microsoft. com/security/portal/submission/submit. aspx
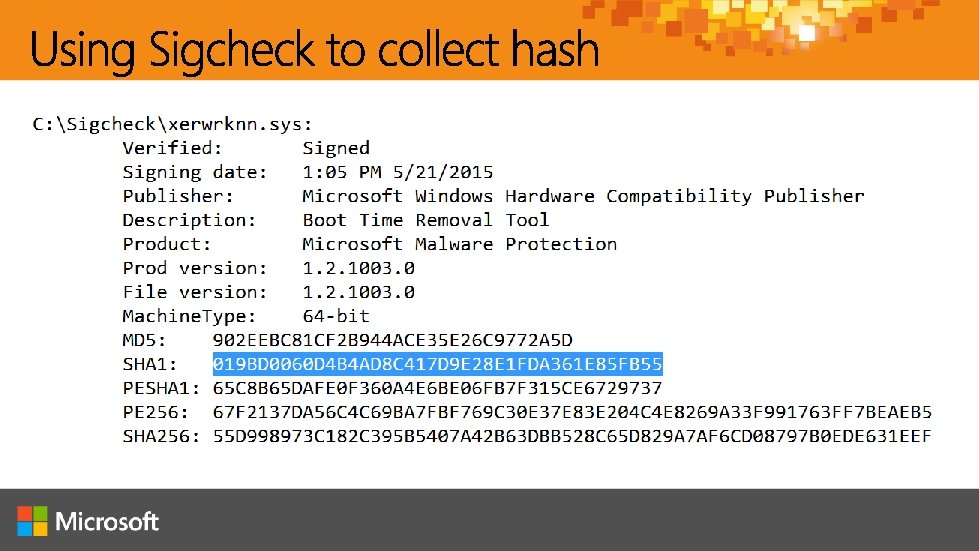
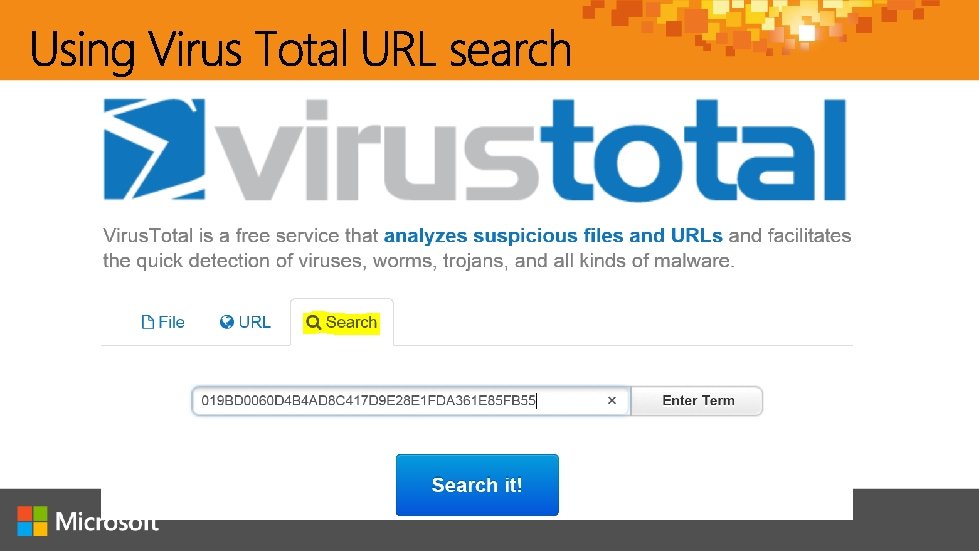
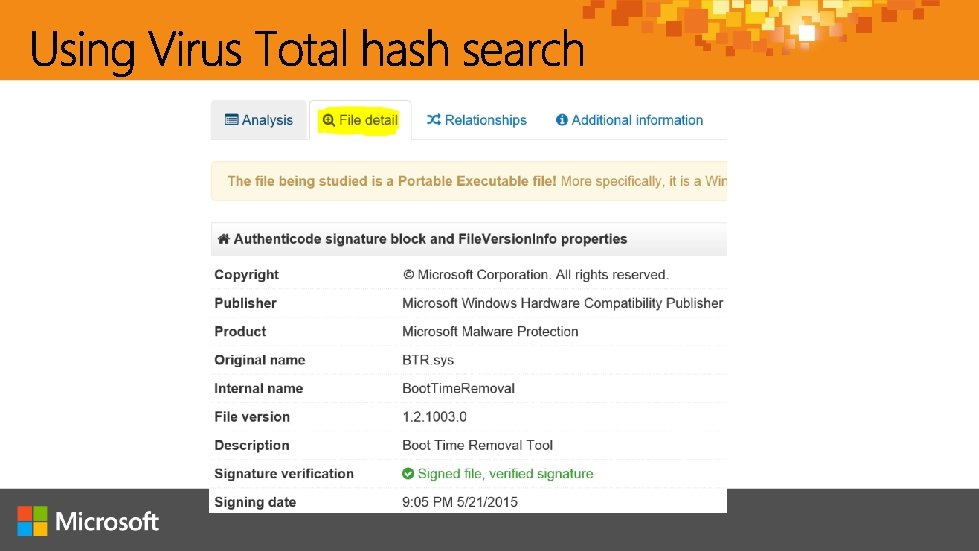
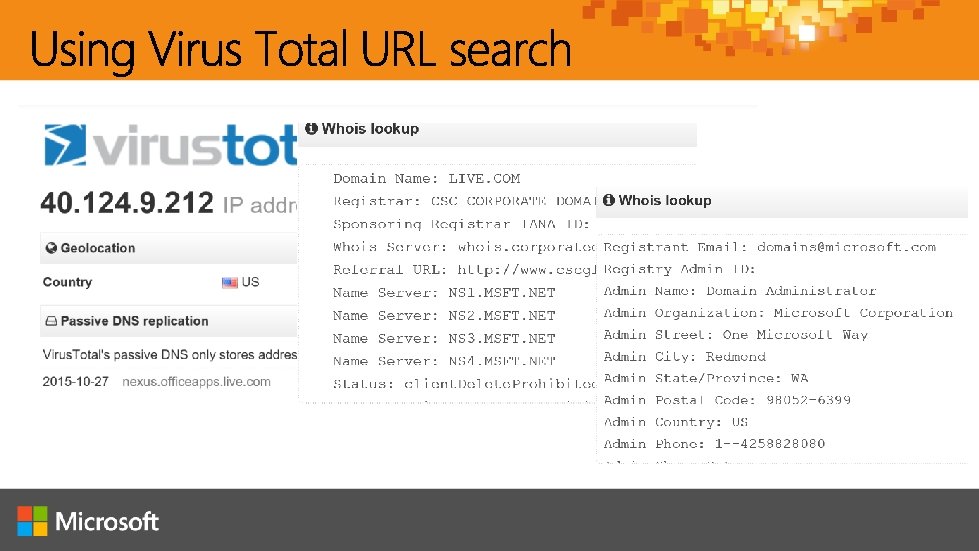




http: //aka. ms/jessica @jepayne. MSFT

My Ignite

Continue your Ignite learning path Visit Microsoft Virtual Academy for free online training visit https: //www. microsoftvirtualacademy. com Visit Channel 9 to access a wide range of Microsoft training and event recordings https: //channel 9. msdn. com/ Head to the Tech. Net Eval Centre to download trials of the latest Microsoft products http: //Microsoft. com/en-us/evalcenter/

© 2015 Microsoft Corporation. All rights reserved. Microsoft, Windows and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.
- Slides: 33