Anatomy of an Attack Copyright 2011 EMC Corporation



- Slides: 7

Anatomy of an Attack © Copyright 2011 EMC Corporation. All rights reserved. 1

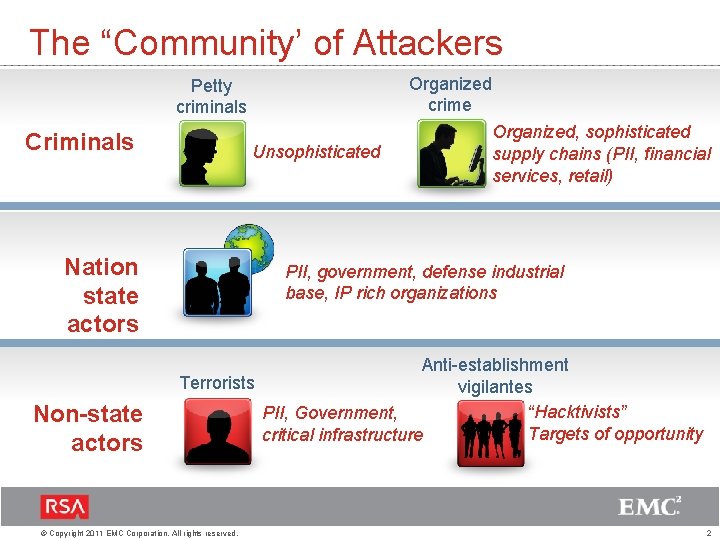
The “Community’ of Attackers Organized crime Petty criminals Criminals Unsophisticated Nation state actors Non-state actors Organized, sophisticated supply chains (PII, financial services, retail) PII, government, defense industrial base, IP rich organizations Anti-establishment Terrorists vigilantes “Hacktivists” PII, Government, Targets of opportunity critical infrastructure © Copyright 2011 EMC Corporation. All rights reserved. 2

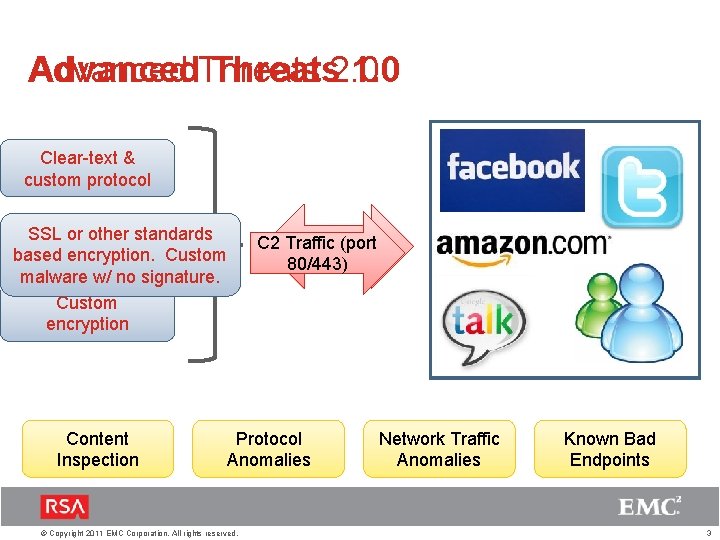
Advanced. Threats 2. 0 1. 0 Advanced Clear-text & custom protocol abc. com SSL or other standards Clear-text & normal basedprotocol encryption. Custom malware w/ no signature. Custom encryption C 2 Traffic (port C 2 Traffic 80/443) 1. 2. 3. 4 def. com 3. 7. 9. 1 1. 2. 3. 4 8. 2. 3. 3 Content Inspection Protocol Anomalies © Copyright 2011 EMC Corporation. All rights reserved. Network Traffic Anomalies Known Bad Endpoints 3

© Copyright 2011 EMC Corporation. All rights reserved. 5

Executive Checklist • Is your IT security organization functionally aligned with the greater IT infrastructure? – Outsourcer > Insourced Capabilities > SOC > etc. • Do you monitor the crown jewels of your organization and know where your most high value programs and assets are? • Does your organization have & practice a breach readiness plan, incident response, discovery & remediation process/procedures? • In addition to perimeter defenses (ingress), does there exist an egress defense strategy and approach to mitigate data exfiltration? • Is there a consistent 360 degree governance, risk and compliance practice in your organization? – Compliance, Regulatory, Legal, Corporate Policy, Communications & HR © Copyright 2011 EMC Corporation. All rights reserved. 6

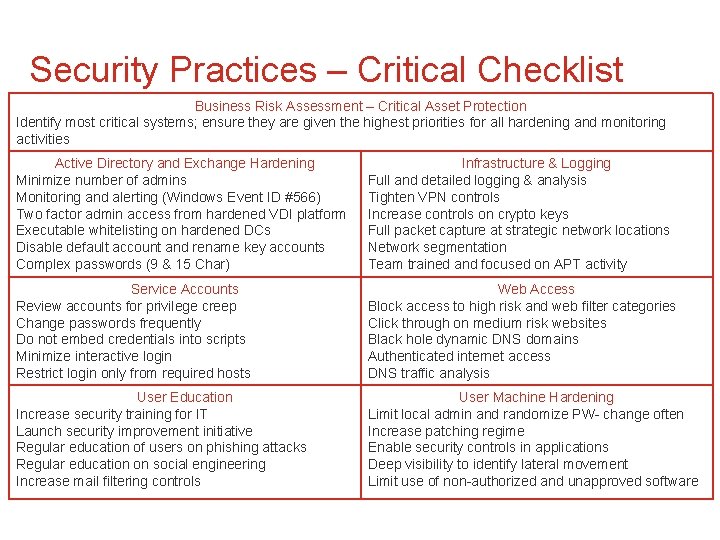
Security Practices – Critical Checklist Business Risk Assessment – Critical Asset Protection Identify most critical systems; ensure they are given the highest priorities for all hardening and monitoring activities Active Directory and Exchange Hardening Minimize number of admins Monitoring and alerting (Windows Event ID #566) Two factor admin access from hardened VDI platform Executable whitelisting on hardened DCs Disable default account and rename key accounts Complex passwords (9 & 15 Char) Infrastructure & Logging Full and detailed logging & analysis Tighten VPN controls Increase controls on crypto keys Full packet capture at strategic network locations Network segmentation Team trained and focused on APT activity Service Accounts Review accounts for privilege creep Change passwords frequently Do not embed credentials into scripts Minimize interactive login Restrict login only from required hosts Web Access Block access to high risk and web filter categories Click through on medium risk websites Black hole dynamic DNS domains Authenticated internet access DNS traffic analysis User Education Increase security training for IT Launch security improvement initiative Regular education of users on phishing attacks Regular education on social engineering Increase mail filtering controls User Machine Hardening Limit local admin and randomize PW- change often Increase patching regime Enable security controls in applications Deep visibility to identify lateral movement Limit use of non-authorized and unapproved software © Copyright 2011 EMC Corporation. All rights reserved. 7

THANK YOU © Copyright 2011 EMC Corporation. All rights reserved. 8













