Anatomy of a Network Hack How To Get






![But Wait, It Gets Better int row. Count = ds. Tables["Users"]. Rows. Count; if(row. But Wait, It Gets Better int row. Count = ds. Tables["Users"]. Rows. Count; if(row.](https://slidetodoc.com/presentation_image_h2/3686d5bc37cdcc1c170e3e152d16c36d/image-8.jpg)






- Slides: 18

Anatomy of a Network Hack: How To Get Your Network Hacked in Ten Easy Steps! Jesper M. Johansson Enterprise Security Architect Security Business & Technology Unit jesperjo @ microsoft. com

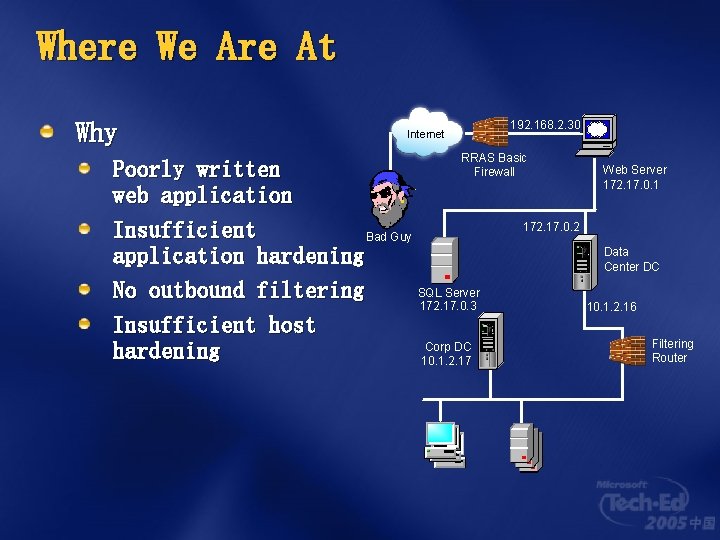
This Presentation… … is about operational security The easy way is not always the secure way Networks are usually designed in particular ways In many cases, these practices simplify attacks In some cases these practices enable attacks You need to know the methods of your adversary to stop them

This Presentation is Not… …a hacking tutorial Hacking networks you own can be enlightening Hacking networks you do not own is illegal! …a demonstration of Windows vulnerabilities Everything we show stems from operational security or custom applications Knowing how the platform operates is critical All platforms can get hacked …for the faint of heart

The Tools Four categories of tools used “Co-opted” ordinary components Windows Resource Kit tools Commonly available hacking/administration tools Custom-written tools The difference between hackers and script kiddies is that hackers write their own tools

By the Way… I will not give you my tools. It does not matter what you do for a living or who you work for If you do not ask, I don’t have to say no

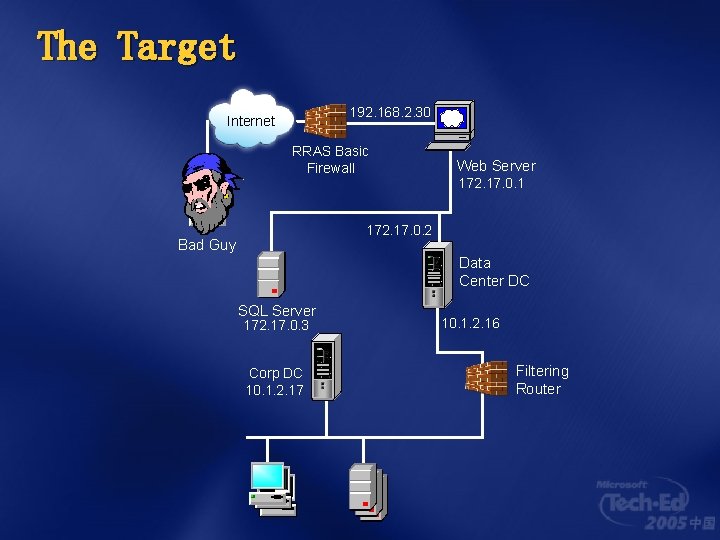
The Target 192. 168. 2. 30 Internet RRAS Basic Firewall Web Server 172. 17. 0. 1 172. 17. 0. 2 Bad Guy Data Center DC SQL Server 172. 17. 0. 3 Corp DC 10. 1. 2. 17 10. 1. 2. 16 Filtering Router

Knocking Down The Side Door //Three mistakes in this statement alone: Sql. Connection conn = new Sql. Connection(); conn. Connection. String = Bad: not a trusted connection "data source=PYN-SQL; " + "initial catalog=pubs; " + Worse, privileged user… "user id=sa; " + "password=password; " + …with a lame password "persist security info=True; “+ "packet size=4096"; conn. Open(); //Don't do this at home folks: SQL Query Composition string str. Query; str. Query = "select * from Users where User. Name = '" + username. Text + Completely un"' and Password ='" + validated user input! password. Text + "'; ";
![But Wait It Gets Better int row Count ds TablesUsers Rows Count ifrow But Wait, It Gets Better int row. Count = ds. Tables["Users"]. Rows. Count; if(row.](https://slidetodoc.com/presentation_image_h2/3686d5bc37cdcc1c170e3e152d16c36d/image-8.jpg)
But Wait, It Gets Better int row. Count = ds. Tables["Users"]. Rows. Count; if(row. Count > 0) // If we get back something. . . { //. . . we must be succesfully logged in Session["Logged. In"] = true; // Store the username in a session variable Session["username"] = username. Text; This is the. . . user name from the form <body> <asp: Label id="Username" runat="server"> Label </asp: Label>. . . Which we cross-site private void Page_Load(object sender, System. Event. Args e) script onto the page! {. . . Username. Text = Session["username"]. To. String(); }

How to Make Use of This Note: This network is entirely fictitious Any similarity with any real network is completely accidental

Where We Are At Why 192. 168. 2. 30 Internet RRAS Basic Firewall Poorly written web application Insufficient Bad Guy application hardening SQL Server No outbound filtering 172. 17. 0. 3 Insufficient host Corp DC hardening 10. 1. 2. 17 Web Server 172. 17. 0. 1 172. 17. 0. 2 Data Center DC 10. 1. 2. 16 Filtering Router

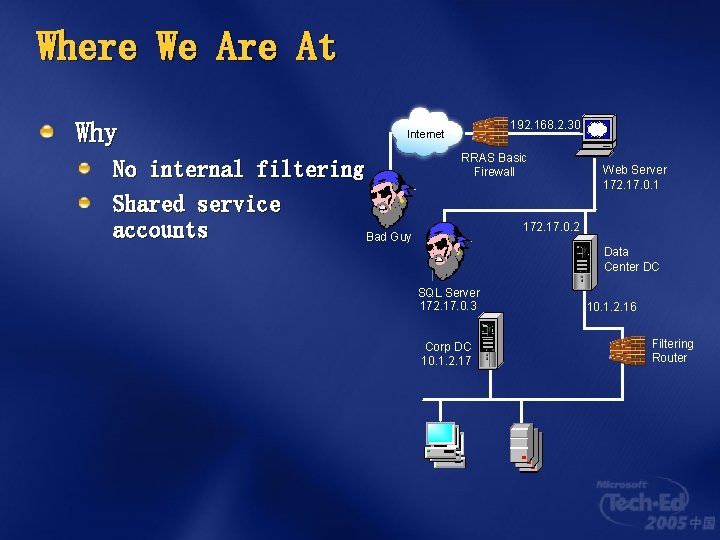
Where We Are At Why 192. 168. 2. 30 Internet No internal filtering Shared service accounts Bad Guy RRAS Basic Firewall Web Server 172. 17. 0. 1 172. 17. 0. 2 Data Center DC SQL Server 172. 17. 0. 3 Corp DC 10. 1. 2. 17 10. 1. 2. 16 Filtering Router

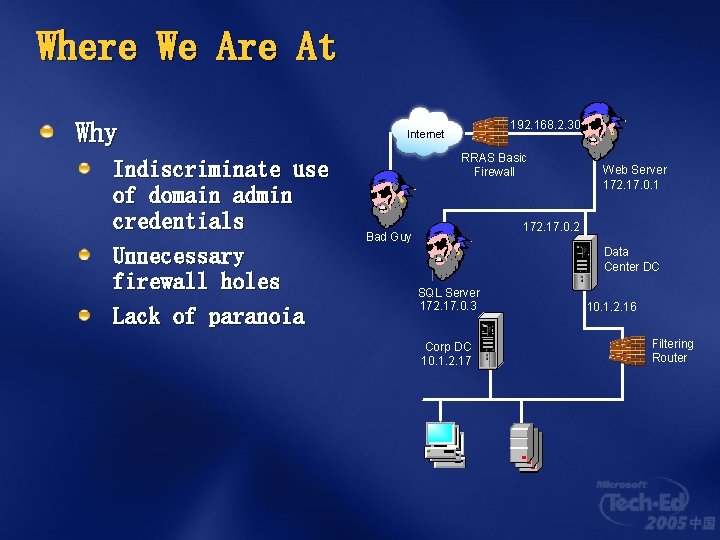
Where We Are At Why Indiscriminate use of domain admin credentials Unnecessary firewall holes Lack of paranoia 192. 168. 2. 30 Internet RRAS Basic Firewall Web Server 172. 17. 0. 1 172. 17. 0. 2 Bad Guy Data Center DC SQL Server 172. 17. 0. 3 Corp DC 10. 1. 2. 17 10. 1. 2. 16 Filtering Router

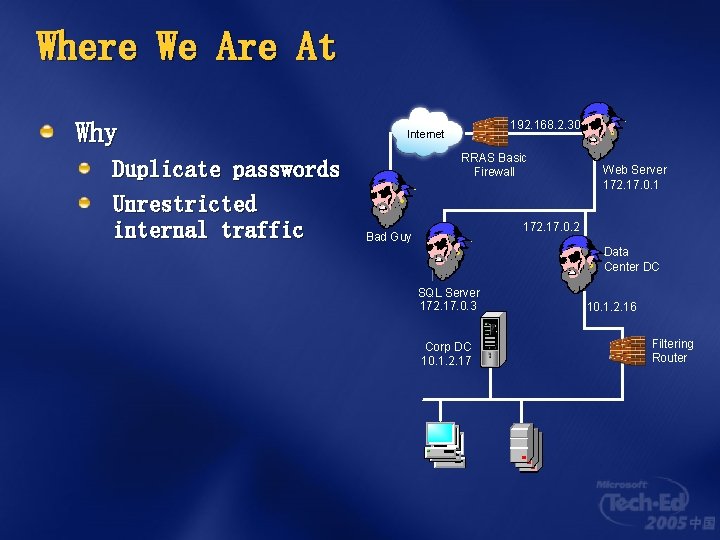
Where We Are At Why Duplicate passwords Unrestricted internal traffic 192. 168. 2. 30 Internet RRAS Basic Firewall Web Server 172. 17. 0. 1 172. 17. 0. 2 Bad Guy Data Center DC SQL Server 172. 17. 0. 3 Corp DC 10. 1. 2. 17 10. 1. 2. 16 Filtering Router

The Moral of the Story Initial entry is everything Most networks are designed like egg shells Hard and crunchy on the outside Soft and chewy on the inside Once an attacker is inside the network, you can… …update resume …hope he does a good job running it …drain it

How To Get Your Network Hacked in 10 Easy Steps Don’t patch anything Run unhardened applications Use one admin account, everywhere Open lots of holes in the firewall Allow unrestricted internal traffic Allow all outbound traffic Don’t harden servers Reuse your passwords Use high-level service accounts, in multiple places 10. Assume everything is OK 1. 2. 3. 4. 5. 6. 7. 8. 9.

10 Things Attackers Don’t Want You To Do 1. Ensure everything is fully patched 2. Use properly hardened applications 3. Use least privilege 4. Open only necessary holes in firewalls 5. Restrict internal traffic 6. Restrict outbound traffic 7. Harden servers 8. Use unique pass phrases or smart cards 9. Micro-manage service accounts 10. Maintain a healthy level of paranoia

For more information Jesper and Steve finally wrote a book! Order online: http: //www. awprofessional. com/ title/0321336437 Use promo code JJSR 6437 jesperjo@microsoft. com

Jesper M. Johansson jesperjo@microsoft. com © 2005 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.