Analyzing Tactical Effectiveness for AntiTerrorist Force Protection AT

















![References Cont’d -[Hennings, 2001] Hennings, C. , Designing Realistic Human Behavior into Multi-Agent Systems References Cont’d -[Hennings, 2001] Hennings, C. , Designing Realistic Human Behavior into Multi-Agent Systems](https://slidetodoc.com/presentation_image_h2/768254da94f2b40e279ddce805d758df/image-29.jpg)
- Slides: 29

Analyzing Tactical Effectiveness for Anti-Terrorist Force Protection (AT/ FP) using X 3 D Graphics and Agent-Based Simulation LT James Harney, USN jwharney@nps. navy. mil 15 October 2002 1

Talk Outline Introduction and Background Motivation Problem Statement Method Current Status Ongoing and Future Work Demo 2

Background: Naval Postgraduate School “Navy’s University” Monterey California n n USN, USMC, USAF, allied officers, civil service Two-year masters’ degrees with theses MOVES Institute n n Modeling, Virtual Environments & Simulation Mix of computer science & ops research simulation 3

NPS Continued Wayne E. Meyer Institute of Systems Engineering n n n Integrates and enhances existing systems engineer programs at NPS Provides unique Graduate Education and research opportunities through experiement design, coordination, and execution. Primary liason between MOVES and USN ATFP schoolhouse and Commander Third Fleet executed Limited Objective Experiment’s. 4

Introduction and Background Thesis Advisor: Dr. Don Brutzman (brutzman@nps. navy. mil) Co-Advisors: Dr. Gordon Schacher (gschacher@nps. navy. mil) Prof. John Hiles (jhiles@mindspring. com) Research Associate Curt Blais (clblais@nps. navy. mil) 5

Background Cont’d My Background: B. S. Computer Science US Naval Academy (1996) Damage Control Assistant, USS ROSS (DDG 71) Combat Information Center Officer USS PETERSON (DD 969) NPS through March 2003 6

Motivation • 12 October 2000 - Attack on USS COLE (DDG 67) 7

Problem Statement What Insights can be gained for U. S. Navy Anti-Terrorism Force Protection Doctrine through the use of Web-Centric Modeling and Simulation Technologies and Agent. Based Simulation for defending against the surface-borne terrorist threat? 8

Method -User Centric Design Process -Original Simulation Design Based on Limited Objective Experiment setup for Port Hueneme, California. -Allows user’s to visualize defense setups against threats and gain insight on ‘Continuum of Force’ considerations. -Extendable to other warfare areas as a possible long term project through other student’s research. 9

User Created Scenarios - We want the warfighter to be able to play ‘what-if’s’ at the Tactical Level of War. -Utilize dynamic scenario generation -Current research focus is modeling against the surface threat, while incorporating ‘Continuum of Force’ Ideals. -Potential follow-on student looking at Radar Visualization and Threat analysis. 10

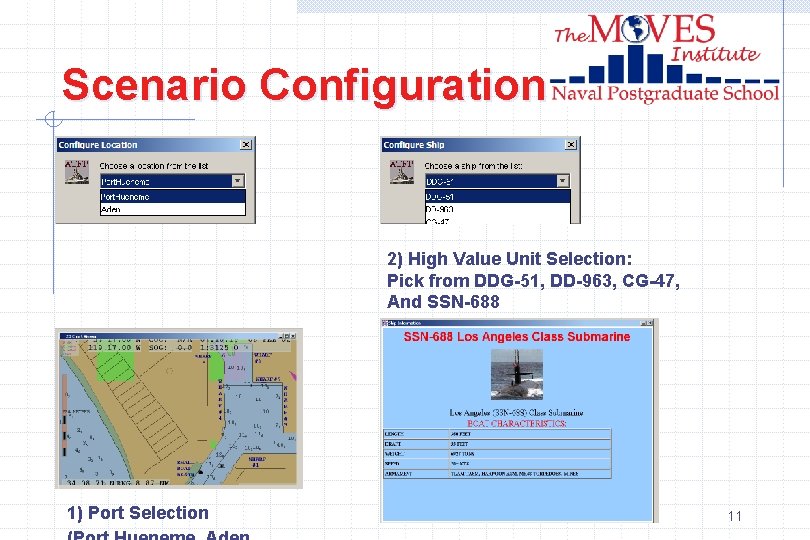
Scenario Configuration 2) High Value Unit Selection: Pick from DDG-51, DD-963, CG-47, And SSN-688 1) Port Selection 11

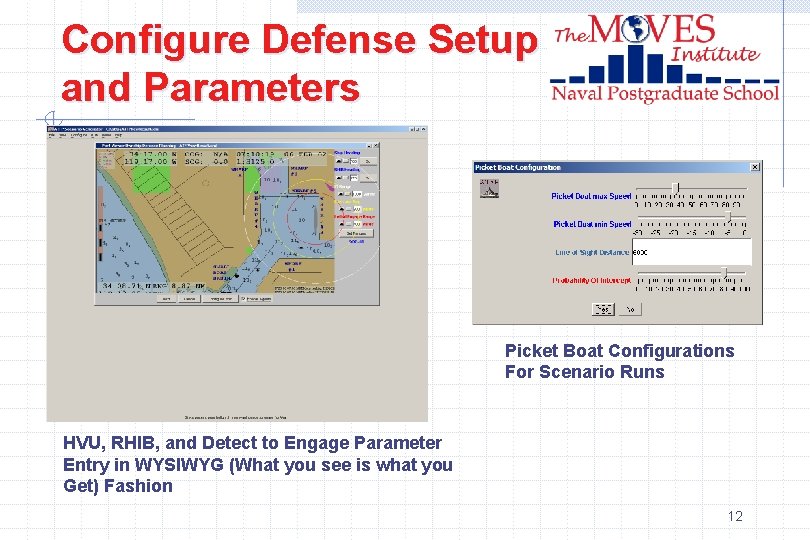
Configure Defense Setup and Parameters Picket Boat Configurations For Scenario Runs HVU, RHIB, and Detect to Engage Parameter Entry in WYSIWYG (What you see is what you Get) Fashion 12

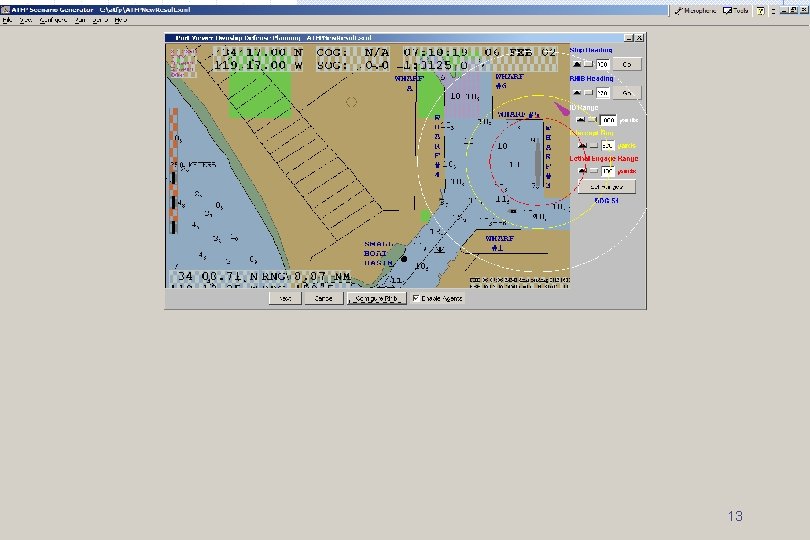
Larger Screen Snapshot of Defensive Setup 13

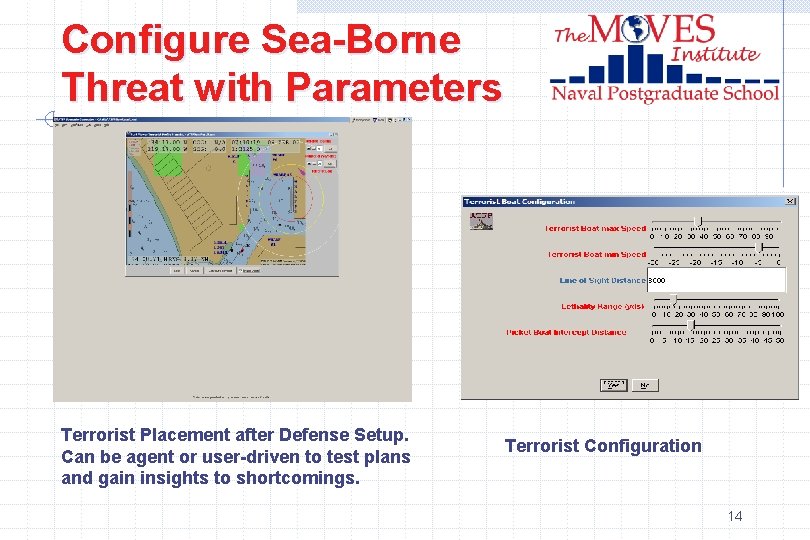
Configure Sea-Borne Threat with Parameters Terrorist Placement after Defense Setup. Can be agent or user-driven to test plans and gain insights to shortcomings. Terrorist Configuration 14

Scenario View -Current configuration allows for gaining insight on the relationship for various parameters with light or no background shipping against a single threat (depicted in the next slide). -’Continuim of Force’ ideas allow the operator then to input delay in action times for defenses to see if there is a detrimental impact on what was thought to be a good defense. 15

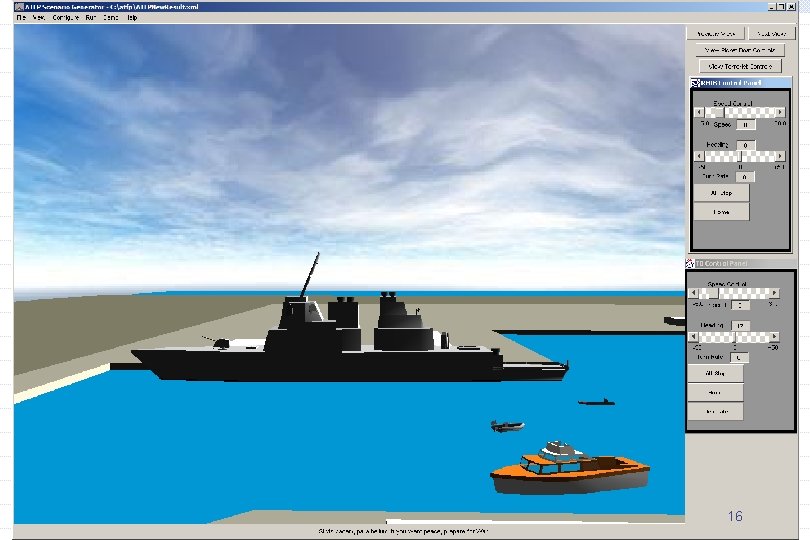
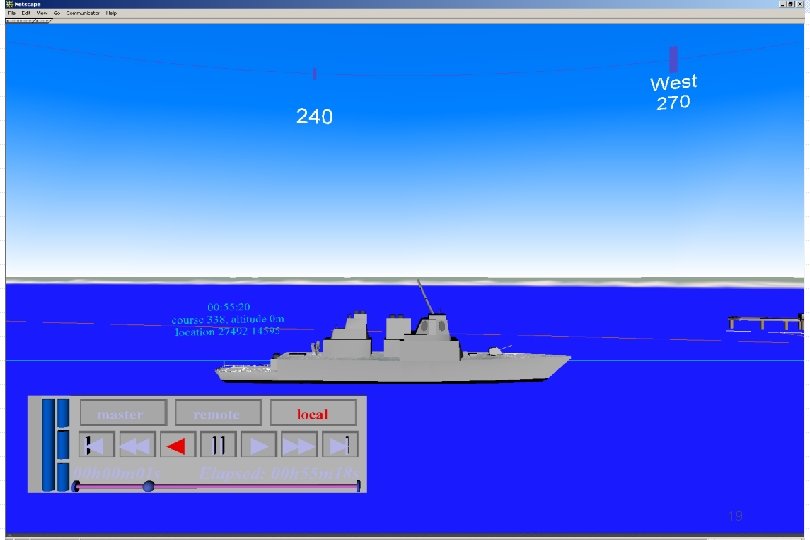
Screen Snapshot of Scenario w/Light Background Shipping 3 D View 25 Sept 2002 16

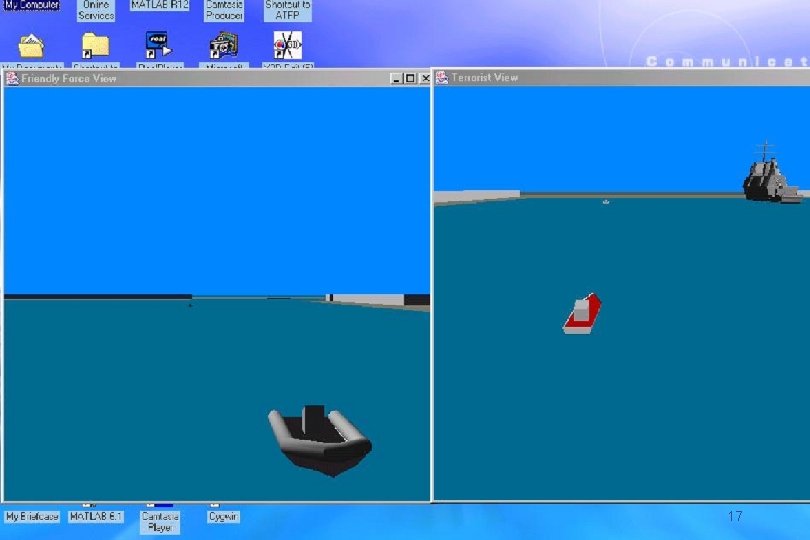
‘Stereo Rendering’ of a scenario. 17

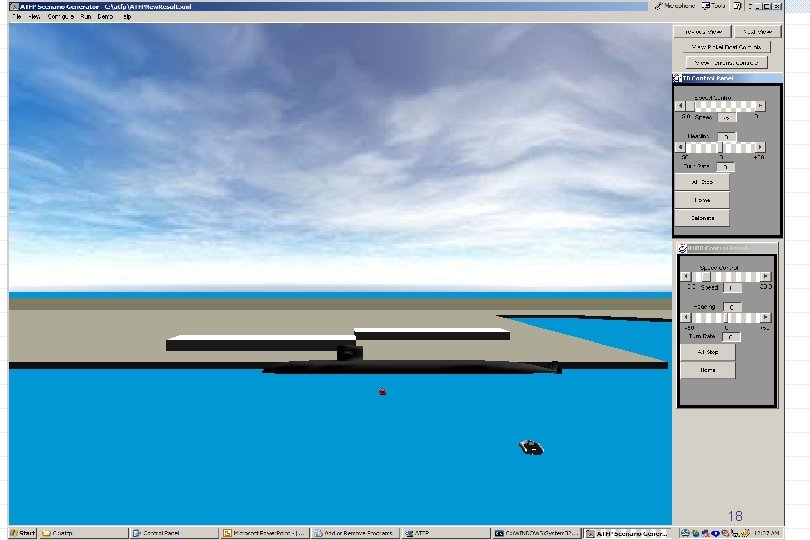
Screen Capture 18

Screen Pics II Screen Snapshot of Exemplar of Web. Browser Content From Attack on the Cole Recreation. (http: //web. nps. navy. mil/~brutzman/Savage/S cenarios/Uss. Cole. Terrorist. Attack/ 19

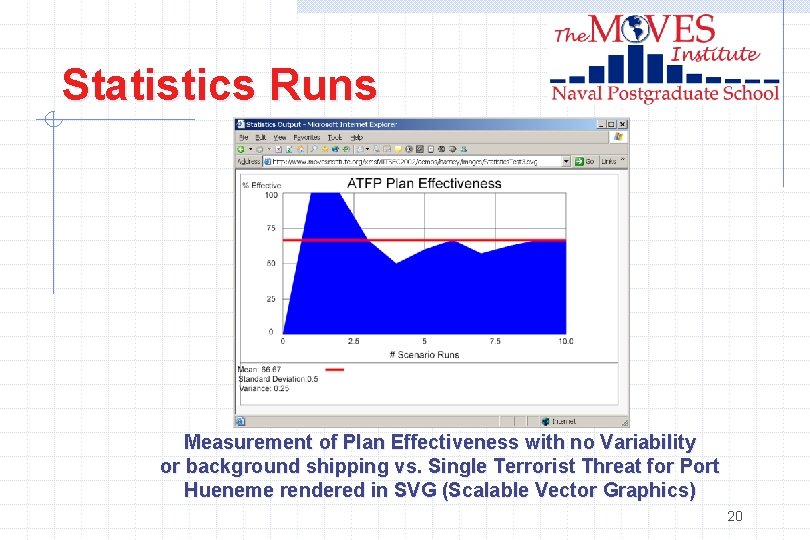
Statistics Runs Measurement of Plan Effectiveness with no Variability or background shipping vs. Single Terrorist Threat for Port Hueneme rendered in SVG (Scalable Vector Graphics) 20

Preliminary Results -Insight to Defensive Picket Boat Placement relative to High Value Unit being protected and Identification and Interception Ranges so far. -With Background shipping just being explored, expect to gain more insight on the relationship of background shipping to required id and warning ranges to amount of seaborne assets required under current doctrine. -Coordinated multi-axis attacks, etc. 21

Ongoing Work -Further work on Autonomous Agent development wrt more complex attacking and defensive paradigms and behaviors. -Background Shipping configuration panel for the user. -Continued Integration of Continuim of Force Concepts --Field test and further development with ATFP Schoolhouse. 22

Ongoing Work -Further usability and other application refinement. -Examination of design requirements for follow on students to study other threat areas (ie undersea, shore, air, or combinations) -Graphics quality improvements and additions as needed. 23

Ongoing Work Cont’d -Capt Khaled Mnif, Tunisian Army – XML Tactical Database storage, and service providing for the operator. --Examining emerging XML database technologies and working towards a proof of concept for how to provide web-based M&S services to the operator in the context of my thesis service, outputs, etc for Anti. Terrorism/Force Protection. -XMSF – Extensible Modeling and Simulation Framework http: //www. Moves. Institute. org/xmsf 24

Future Work -Tie in Message generation and editing for Ship Plans possible. -Incorporation of other Academic disciplines to see affects on analysis as well as Usability (Physics, OR, etc). Currently 1 prospective SWO, EE student with Computer Visualization experience is looking to follow on with Radar and Sensor modeling. Other’s interested. -Further research in any warfare area in Modeling and Simulation geared to tactical employment of military doctrine. -More usability work can always be done with this and other work geared for others to use. 25

Demo 26

References http: //www. web 3 d. org/Task. Groups/source/xj 3 d. html - Xj 3 D Open Source Project http: //www. web 3 d. org/x 3 d. html - Web 3 D X 3 D website http: //web. nps. navy. mil/~brutzman - Dr. Brutzman’s website http: //web. nps. navy. mil/~brutzman/Savage/contents. html SAVAGE model library http: //www. sun. com/developers - Sun Microsystems Java tm Developer’s web site http: //xml. apache. org/batik/ - Scalable Vector Graphics (2 D Xml Graphics) 27

References Cont’d - http: //www. web 3 d. org/Working. Groups/vrtp/dis-javavrml/ ( DIS-JAVA-VRML Web. Page) - http: //www. movesinstitute. org - http: // www. fas. org (Federation of American Scientists) - http: //www. sourceforge. net/projects/npsnetv ( NPSNET V Project Web Site) - http: //www. xj 3 d. org – Xj 3 D Developer’s web site 28
![References Contd Hennings 2001 Hennings C Designing Realistic Human Behavior into MultiAgent Systems References Cont’d -[Hennings, 2001] Hennings, C. , Designing Realistic Human Behavior into Multi-Agent Systems](https://slidetodoc.com/presentation_image_h2/768254da94f2b40e279ddce805d758df/image-29.jpg)
References Cont’d -[Hennings, 2001] Hennings, C. , Designing Realistic Human Behavior into Multi-Agent Systems Master’s thesis, Naval Postgraduate School, Monterey, CA, 2001. -[Hiles, 1999] Hiles, J. , Course Notes for MV-4015 Agent. Based Autonomous Behavior for Simulations. Winter, 2000, Naval Postgraduate School, 1999. -[Ilachinski, 1997] Ilachinski, A. , Center for Naval Analyses, Irreducible Semi-Autonomous Adaptive Combat (ISAAC): An Artificial-Life Approach to Land Warfare, CRM 97 -61. 10/August 1997. 29