Analyzing Key Distribution and Authentication Protocols 2015 Richard

Analyzing Key Distribution and Authentication Protocols © 2015 Richard Newman

Analysis of Key Distribution Protocols Ways to break cryptographic controls: 1. The cipher algorithm is broken 2. The keyspace is too small 3. The protocol is broken 4. The implementation is broken 5. The system does not protect the keys adequately
Analysis of Key Distribution Protocols The cipher algorithm is broken Use good, tested algorithms 2. The keyspace is too small Use large enough keys Make sure key selection has sufficient entropy 1.

Analysis of Key Distribution Protocols The implementation is broken Take care about random numbers Take care about key gen & rotation Take care about leaks 5. The system does not protect the keys adequately Enforce adequate security policies and use good controls in rest of system 4.
Analysis of Key Distribution Protocols 3. The protocol is broken Analyze the protocol Prove its properties Determine its assumptions Identify the obligations it places on the environment Make sure requirements are satisfied!
Analysis of Key Distribution Protocols If the protocol is broken, no amount of patching will fix it What does it expect/require of underlying cryptographic functions? What does it require of generated variables (e. g. , nonces, random numbers) What does it expect of the system
Analysis of Key Distribution Protocols If the protocol is broken, no amount of patching will fix it By definition, protocols are used by multiple parties Require parties to use same protocol Protocol change requires all parties using it to change also – how to coordinate? Need to make new protocol (version)
How do We Analyze Protocols? Burroughs, Abadi, and Needham introduced BAN Logic Many other logics since then Many other analysis techniques also But BAN logic is relatively simple and suffices to expose much of what we want: assumptions vulnerabilities flaws

BAN Logic See DES SRC-039 Tech Report Steps: 1. Transform protocol to idealized protocol 2. State initial assumptions 3. Associate assertions with messages 4. Apply postulates to beliefs and assertions to derive additional beliefs

BAN Logic 1. 2. 3. Monotonic logic: Only add, never subtract belief Questions it helps answer: What does this protocol achieve? Does this protocol require more assumptions than another one? Does this protocol do anything unnecessary (e. g. , encryption)?
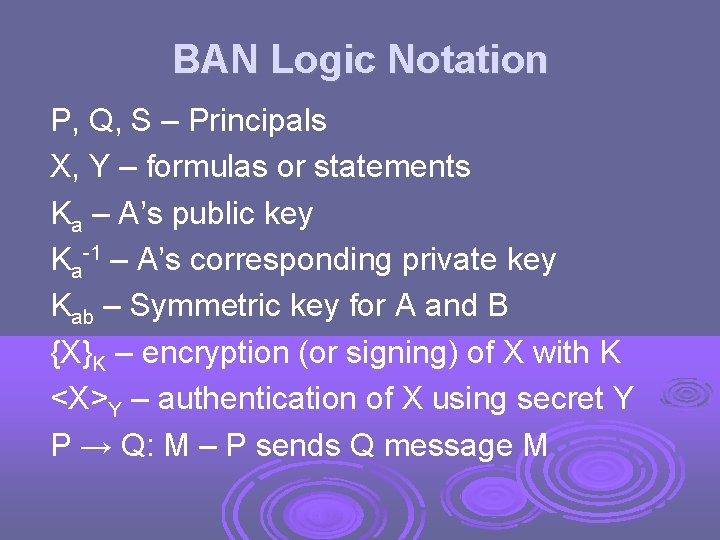
BAN Logic Notation P, Q, S – Principals X, Y – formulas or statements Ka – A’s public key Ka-1 – A’s corresponding private key Kab – Symmetric key for A and B {X}K – encryption (or signing) of X with K <X>Y – authentication of X using secret Y P → Q: M – P sends Q message M
- Slides: 11