Analyzing Anonymity Protocols 1 Analyzing onionrouting security 1



















- Slides: 24

Analyzing Anonymity Protocols 1. Analyzing onion-routing security 1. Anonymity Analysis of Onion Routing in the Universally Composable Framework in Provable Privacy Workshop 2012 2. A Probabilistic Analysis of Onion Routing in a Black -box Model in TISSEC (forthcoming) by Joan Feigenbaum, Aaron Johnson, and Paul Syverson 2. Analyzing Dissent security 1. Ongoing work with Ewa Syta, Henry Corrigan. Gibbs, Shu-Chun Weng, and Bryan Ford 1

Analyzing Onion-Routing Security ● ● Abstract (black-box) model of onion routing Use Universally Composable (UC) framework Focus on information leaked Perform anonymity analysis on model 2

Onion-Routing Ideal Functionality Upon receiving destination d from user U x u with probability b ø with probability 1 -b y d with probability b ø with probability 1 -b Send (x, y) to the adversary. FOR 3

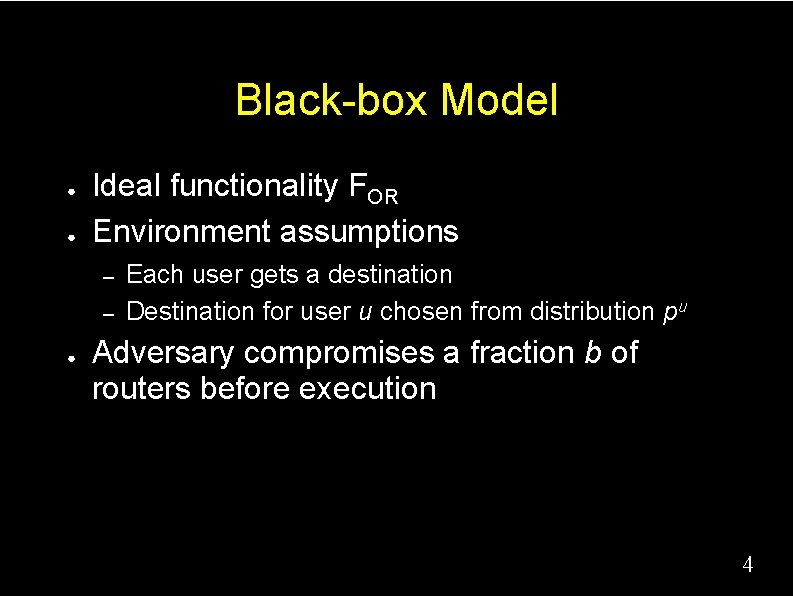
Black-box Model ● ● Ideal functionality FOR Environment assumptions – – ● Each user gets a destination Destination for user u chosen from distribution pu Adversary compromises a fraction b of routers before execution 4

Anonymity Analysis of Black Box ● ● Can lower bound expected anonymity with standard approximation: b 2 + (1 -b 2)pud Worst case for anonymity is when user acts exactly unlike or exactly like others Worst-case anonymity is typically as if √b routers compromised: b + (1 -b)pud Anonymity in typical situations approaches lower bound 5

Other ideal functionality ● ● ● Provably Secure and Practical Onion Routing by Backes, Kate, Goldberg, and Mohammadi Computer Security Foundations Symposium 2012 Functional primitive Shown to UC-emulate FOR 6

Analyzing Dissent security ● Fully rigorous definitions and proofs – – – ● ● Anonymity Accountability Integrity Standard sequence-of-games anonymity proofs Discovered flaws 7

Discovered flaws 1. Adversary can unaccountably duplicate honest users’ plaintexts. 2. Commitments must be non-malleable. 3. Adversary can submit self-duplicates to cause failure with no blame. 4. Equivocation during broadcast can cause inconsistent final state. 5. Some validation checks missing 8

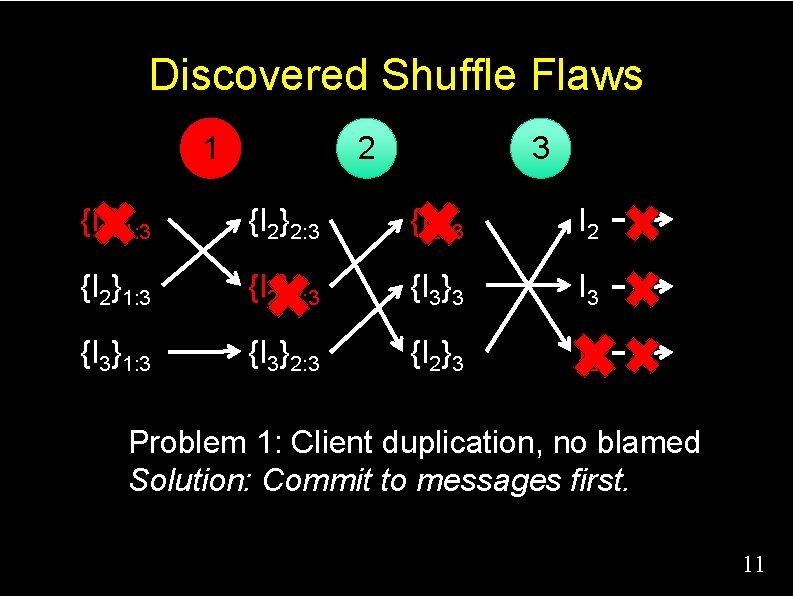
Discovered Shuffle Flaws 1 2 3 {I 1}1: 3 {I 2}2: 3 {I 1}3 I 2 m 2 {I 2}1: 3 {I 1}2: 3 {I 3}3 I 3 m 3 {I 3}1: 3 {I 3}2: 3 {I 2}3 I 1 m 1 9

Discovered Shuffle Flaws 1 2 3 ? {I 2}1: 3 {I 2}2: 3 {I 2}3 I 2 ? {I 2}1: 3 {I 2}2: 3 {I 3}3 I 3 {I 3}1: 3 {I 3}2: 3 {I 2}3 I 2 Problem 1: Client duplication, no blamed 10

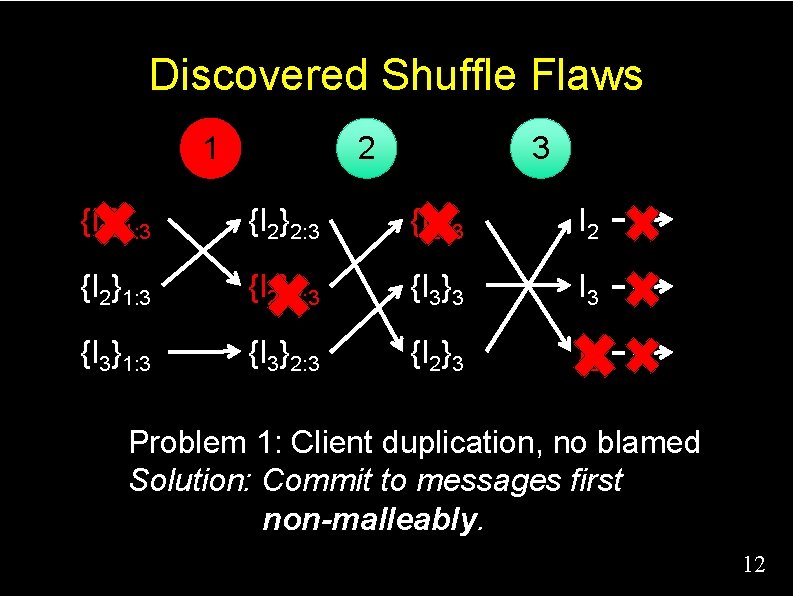
Discovered Shuffle Flaws 1 2 3 {I 2}1: 3 {I 2}2: 3 {I 2}3 I 2 {I 2}1: 3 {I 2}2: 3 {I 3}3 I 3 {I 3}1: 3 {I 3}2: 3 {I 2}3 I 2 Problem 1: Client duplication, no blamed Solution: Commit to messages first. 11

Discovered Shuffle Flaws 1 2 3 {I 2}1: 3 {I 2}2: 3 {I 2}3 I 2 {I 2}1: 3 {I 2}2: 3 {I 3}3 I 3 {I 3}1: 3 {I 3}2: 3 {I 2}3 I 2 Problem 1: Client duplication, no blamed Solution: Commit to messages first non-malleably. 12

Discovered flaws 1. Adversary can unaccountably duplicate honest users’ plaintexts. 2. Commitments must be non-malleable. 3. Adversary can submit self-duplicates to cause failure with no blame. 4. Equivocation during broadcast can cause inconsistent final state. 5. Some validation checks missing 13

Discovered flaws 1. Adversary can unaccountably duplicate honest users’ plaintexts. 2. Commitments must be non-malleable. 3. Adversary can submit self-duplicates to cause failure with no blame. 4. Equivocation during broadcast can cause inconsistent final state. 5. Some validation checks missing 14

Discovered flaws 1. Adversary can unaccountably duplicate honest users’ plaintexts. 2. Commitments must be non-malleable. 3. Adversary can submit self-duplicates to cause failure with no blame. 4. Equivocation during broadcast can cause inconsistent final state. 5. Some validation checks missing 15

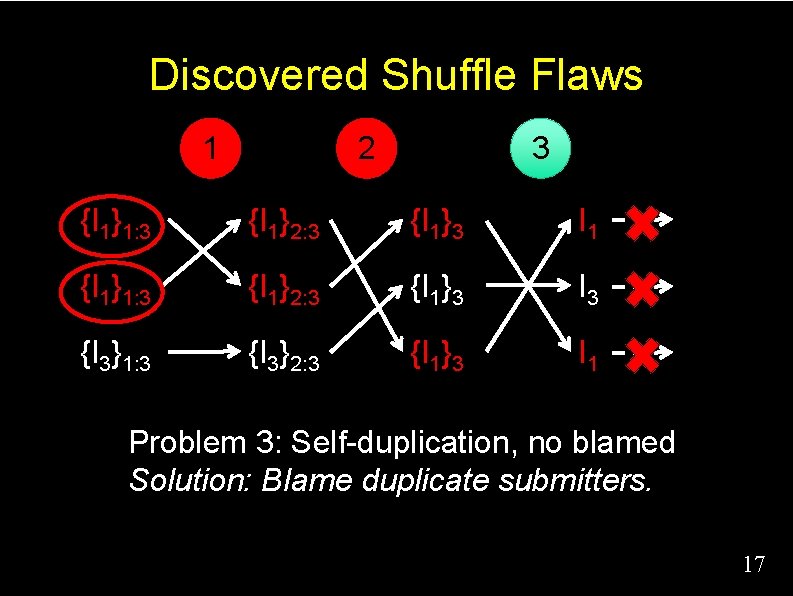
Discovered Shuffle Flaws 1 2 3 ? {I 1}1: 3 {I 1}2: 3 {I 1}3 I 1 ? {I 1}1: 3 {I 1}2: 3 {I 1}3 I 3 {I 3}1: 3 {I 3}2: 3 {I 1}3 I 1 Problem 3: Self-duplication, no blamed 16

Discovered Shuffle Flaws 1 2 3 {I 1}1: 3 {I 1}2: 3 {I 1}3 I 1 {I 1}1: 3 {I 1}2: 3 {I 1}3 I 3 {I 3}1: 3 {I 3}2: 3 {I 1}3 I 1 Problem 3: Self-duplication, no blamed Solution: Blame duplicate submitters. 17

Discovered flaws 1. Adversary can unaccountably duplicate honest users’ plaintexts. 2. Commitments must be non-malleable. 3. Adversary can submit self-duplicates to cause failure with no blame. 4. Equivocation during broadcast can cause inconsistent final state. 5. Some validation checks missing 18

Discovered flaws 1. Adversary can unaccountably duplicate honest users’ plaintexts. 2. Commitments must be non-malleable. 3. Adversary can submit self-duplicates to cause failure with no blame. 4. Equivocation during broadcast can cause inconsistent final state. 5. Some validation checks missing 19

Modified Dissent 1. Users non-malleably commit to messages before submission. 2. Duplicate submission punished 3. Explicit reliable broadcasts added 4. Several validation checks added with blame 5. Honest members guaranteed to agree on who to blame 20

UC Framework ● ● ● Express security primitive as an ideal functionality F Construct a protocol Π that UC emulates F Running Π can replace using F in any protocol – security composes 21

Sequence of Games Anonymity Proof ● ● Game 0: Original anonymity game Game 1: Replace encrypted descriptors during shuffle with encrypted fixed messages Game 2: Replace encrypted random seeds after shuffle with encrypted fixed messages Game 3: Replace pseudorandom sequences with random sequences 22

Discovered Shuffle Flaws 1 2 3 {I 1}1: 3 {I 2}2: 3 {I 2}3 I 2 m 2 {I 2}1: 3 {I 2}2: 3 {I 3}3 I 3 m 3 {I 3}1: 3 {I 3}2: 3 {I 2}3 I 2 m 2 Problem 0: Shuffle duplication attack 23

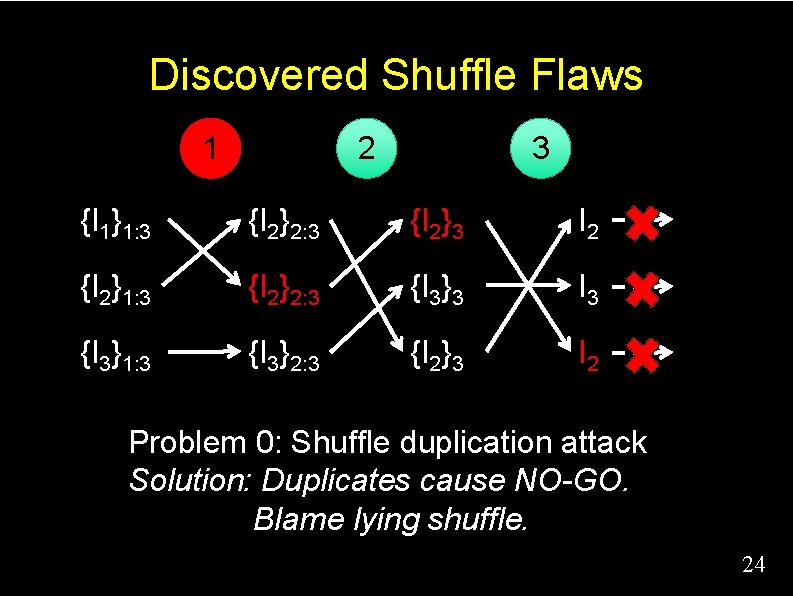
Discovered Shuffle Flaws 1 2 3 {I 1}1: 3 {I 2}2: 3 {I 2}3 I 2 {I 2}1: 3 {I 2}2: 3 {I 3}3 I 3 {I 3}1: 3 {I 3}2: 3 {I 2}3 I 2 Problem 0: Shuffle duplication attack Solution: Duplicates cause NO-GO. Blame lying shuffle. 24