Analyzing and Detecting Network Security Vulnerability Weekly report

Analyzing and Detecting Network Security Vulnerability Weekly report Fan-Cheng Wu 1

Approach 1. Do some statistics on Cisco Advisories. – Classification methodology (on-going) 2. Classify the Advisories in various ways. – Read and classify Cisco advisories (on-going) 3. Select one Advisory from each category. 4. Find the root cause by reading program diff files, engineering notes, or interview development engineers. 5. For each Advisory/vulnerability category, develop ways to parse programs to look for such vulnerability. 6. Write the parser with the above detection capability. Fan-Cheng Wu 2
Initial start Weekly report 2007/08/17 Fan-Cheng Wu 3
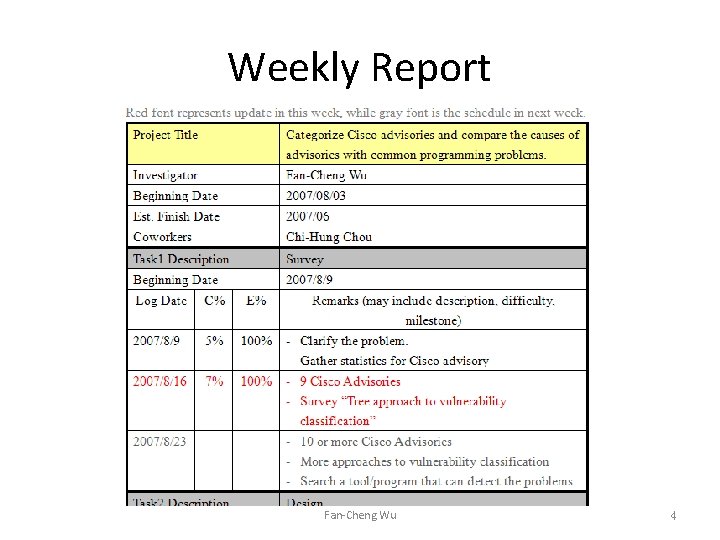
Weekly Report Fan-Cheng Wu 4
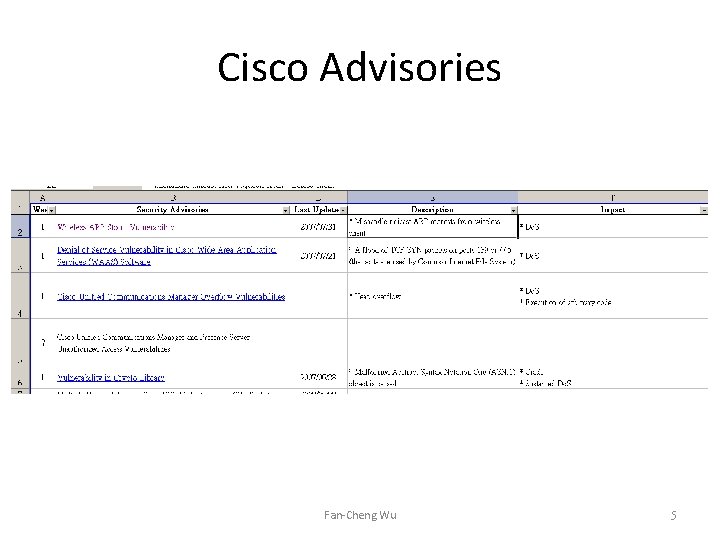
Cisco Advisories Fan-Cheng Wu 5
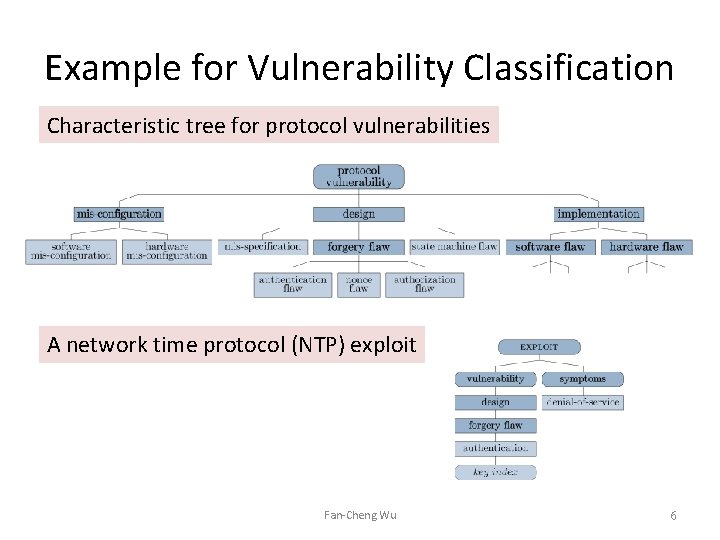
Example for Vulnerability Classification Characteristic tree for protocol vulnerabilities A network time protocol (NTP) exploit Fan-Cheng Wu 6

Analyzing Cisco Advisories Weekly report 2007/08/23 Fan-Cheng Wu 7

Outline • • Overview Cisco advisories Classifying Cisco advisories Tools to detect problems in code Secure coding Fan-Cheng Wu 8

Overview Cisco Advisories • What information does Cisco advisory provide? – For example: [Multiple Vulnerabilities in the IOS FTP server] Table of Content Fan-Cheng Wu 9
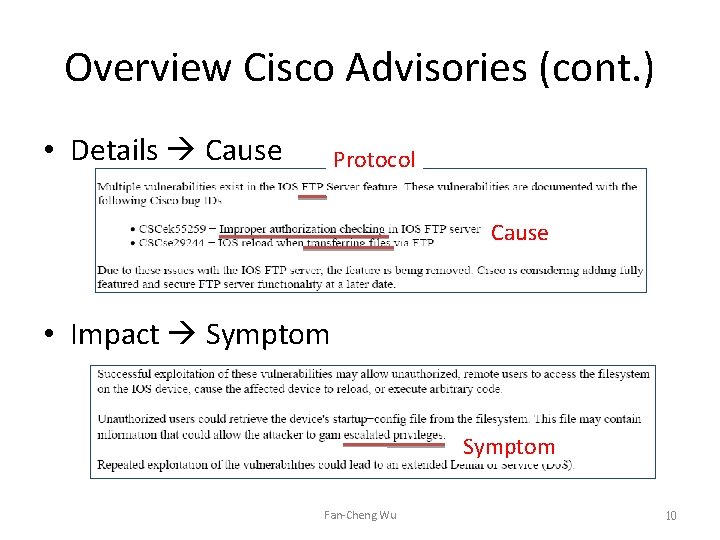
Overview Cisco Advisories (cont. ) • Details Cause Protocol Cause • Impact Symptom Fan-Cheng Wu 10
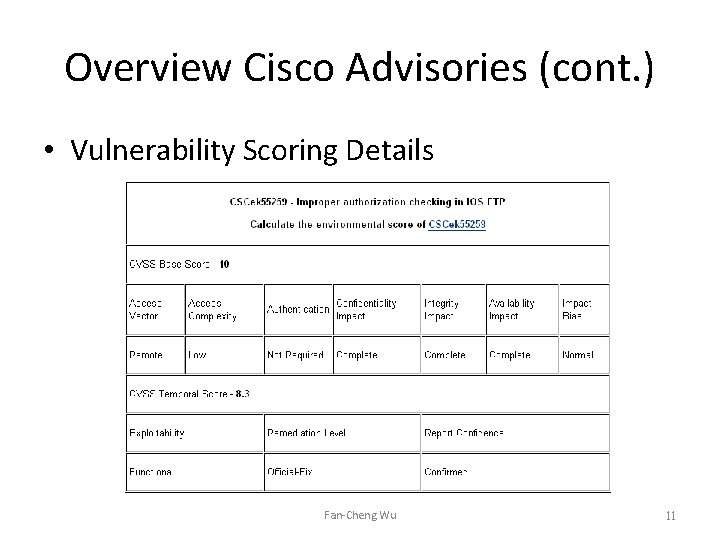
Overview Cisco Advisories (cont. ) • Vulnerability Scoring Details Fan-Cheng Wu 11
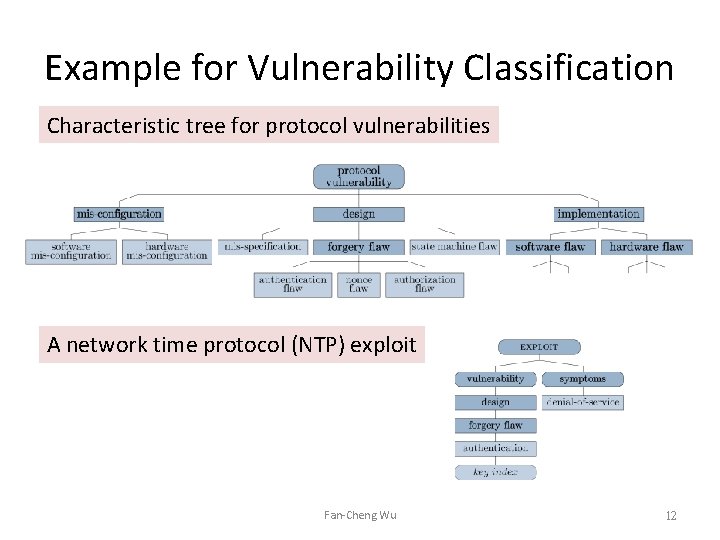
Example for Vulnerability Classification Characteristic tree for protocol vulnerabilities A network time protocol (NTP) exploit Fan-Cheng Wu 12
![Classifying Cisco Advisory • For example: [Multiple Vulnerabilities in the IOS FTP server] – Classifying Cisco Advisory • For example: [Multiple Vulnerabilities in the IOS FTP server] –](http://slidetodoc.com/presentation_image_h2/d74597ebbb2757e2fbe2d9f4bc3886c7/image-13.jpg)
Classifying Cisco Advisory • For example: [Multiple Vulnerabilities in the IOS FTP server] – Information in advisory • Protocol, Cause, Symptom, Access, Impact … – Impossible to classify advisory by Improper authorization checking in IOS FTP server Fan-Cheng Wu IOS reload when transferring files via FTP Design flaw? Implementation flaw? 13
![Detecting Vulnerability • Design flaw – Function extraction [1] • Implementation flaw – Secure Detecting Vulnerability • Design flaw – Function extraction [1] • Implementation flaw – Secure](http://slidetodoc.com/presentation_image_h2/d74597ebbb2757e2fbe2d9f4bc3886c7/image-14.jpg)
Detecting Vulnerability • Design flaw – Function extraction [1] • Implementation flaw – Secure coding [2] [1] Pleszkoch, M. & Linger, R. “Improving Network System Security with Function Extraction Technology for Automated Calculation of Program Behavior. ” IEEE Computer Society Press, 2004. [2] “Secure coding, ” http: //www. securecoding. cert. org/ Fan-Cheng Wu 14
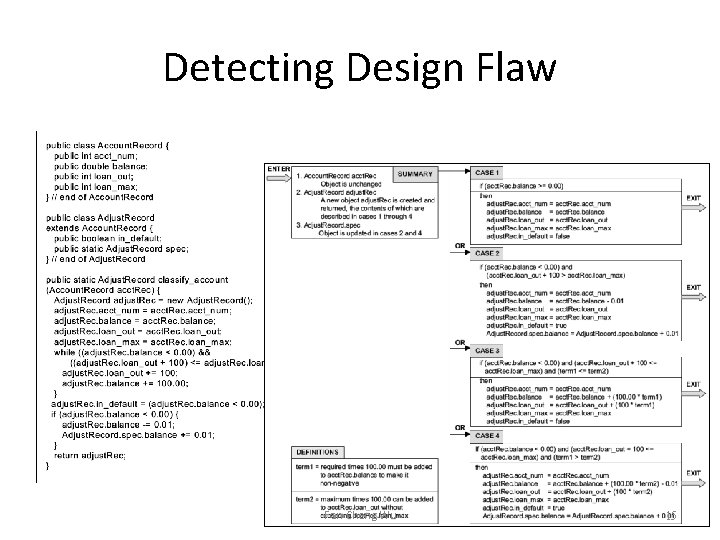
Detecting Design Flaw Fan-Cheng Wu 15
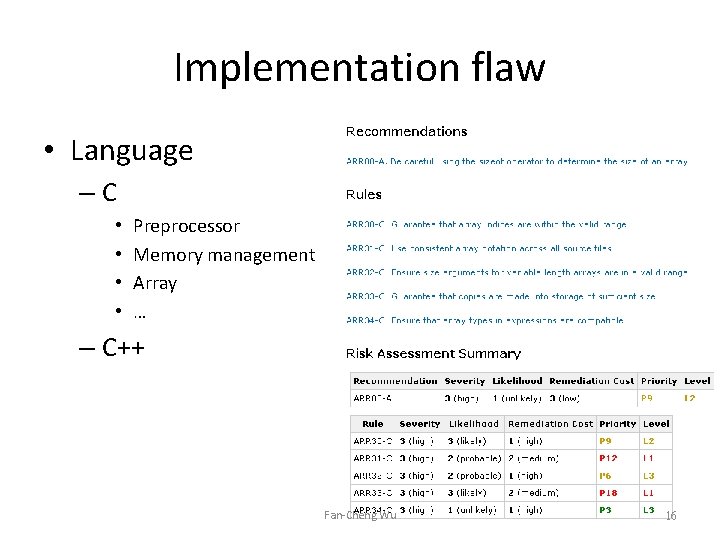
Implementation flaw • Language –C • • Preprocessor Memory management Array … – C++ Fan-Cheng Wu 16

Classification Methodology for Vulnerability Weekly report 2007/09/14 Fan-Cheng Wu 17
![Outline • Previous work – Landwehr’s taxonomies [1] – Bishop’s taxonomies [2] – Piessen’s Outline • Previous work – Landwehr’s taxonomies [1] – Bishop’s taxonomies [2] – Piessen’s](http://slidetodoc.com/presentation_image_h2/d74597ebbb2757e2fbe2d9f4bc3886c7/image-18.jpg)
Outline • Previous work – Landwehr’s taxonomies [1] – Bishop’s taxonomies [2] – Piessen’s taxonomy [4] – Du’s categorization [3] – Engle’s tree classification[5] Consider single dimension Consider multiple dimensions • Applying Engle’s scheme to Cisco advisory Fan-Cheng Wu 18
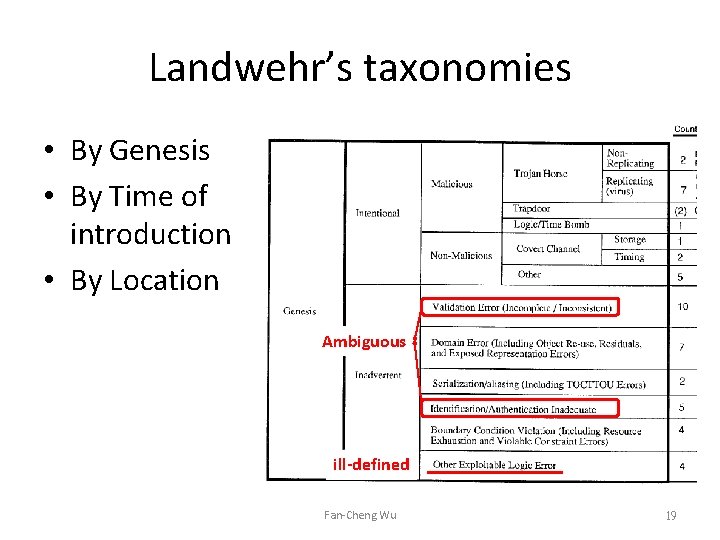
Landwehr’s taxonomies • By Genesis • By Time of introduction • By Location Ambiguous ill-defined Fan-Cheng Wu 19

Bishop’s taxonomies • Describing the vulnerabilities in a form which useful for the intrusion detection mechanisms • Each vulnerability is classified by – The nature of the flaw – The time of introduction – The exploitation domain of the vulnerability – The effect domain –… Fan-Cheng Wu 20
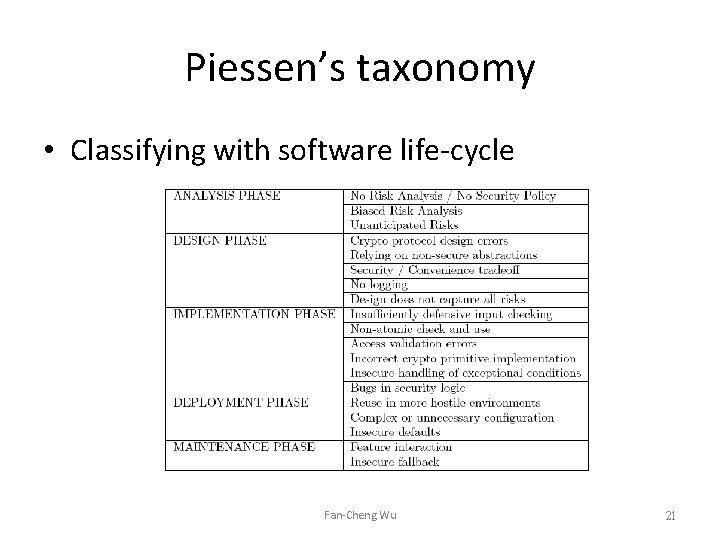
Piessen’s taxonomy • Classifying with software life-cycle Fan-Cheng Wu 21
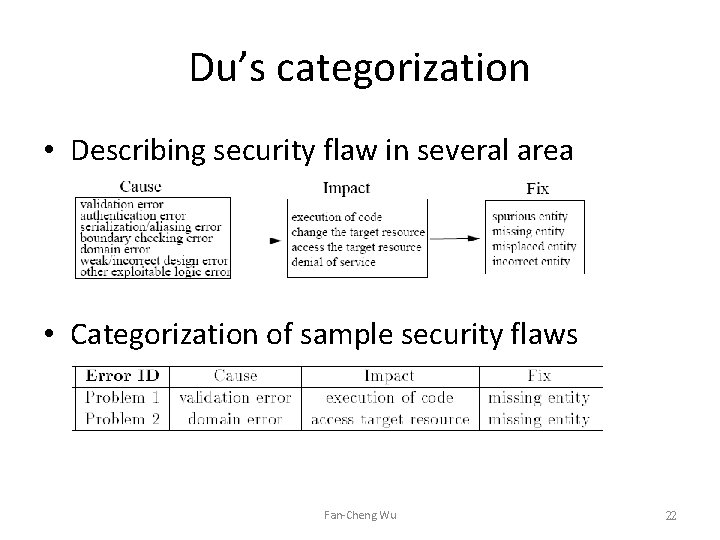
Du’s categorization • Describing security flaw in several area • Categorization of sample security flaws Fan-Cheng Wu 22
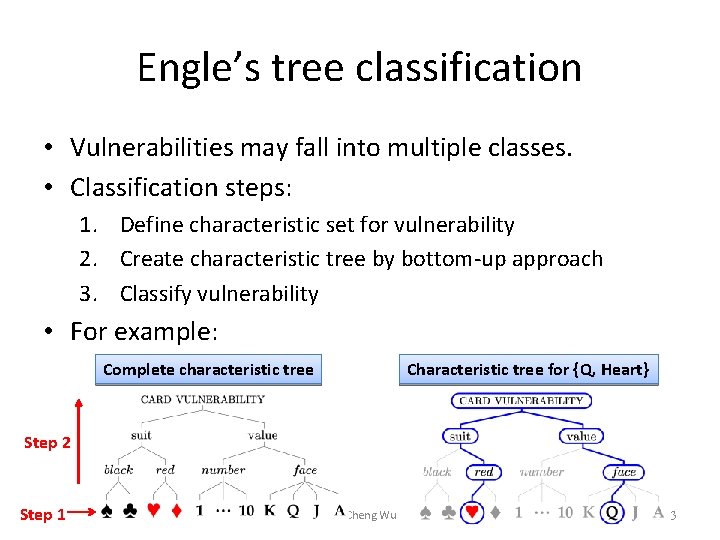
Engle’s tree classification • Vulnerabilities may fall into multiple classes. • Classification steps: 1. Define characteristic set for vulnerability 2. Create characteristic tree by bottom-up approach 3. Classify vulnerability • For example: Complete characteristic tree Characteristic tree for {Q, Heart} Step 2 Step 1 Fan-Cheng Wu 23

Previous Works • A table for summarizing previous works (not ready) Fan-Cheng Wu 24
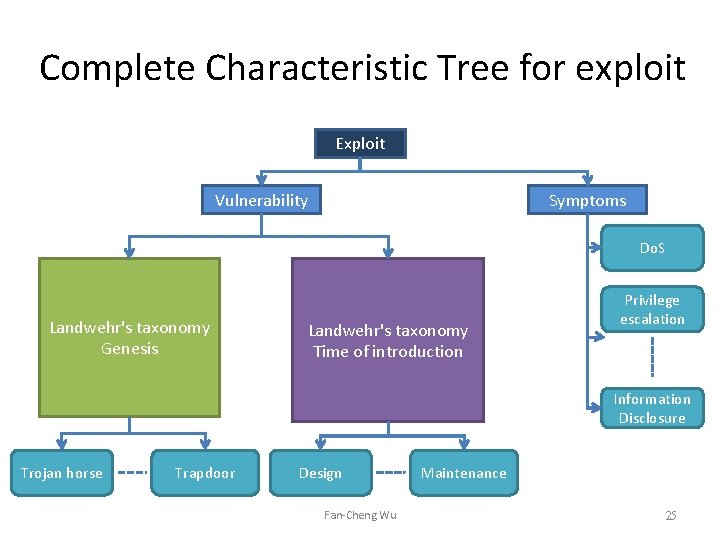
Complete Characteristic Tree for exploit Exploit Vulnerability Symptoms Do. S Landwehr's taxonomy Genesis Landwehr's taxonomy Time of introduction Privilege escalation Information Disclosure Trojan horse Trapdoor Design Fan-Cheng Wu Maintenance 25
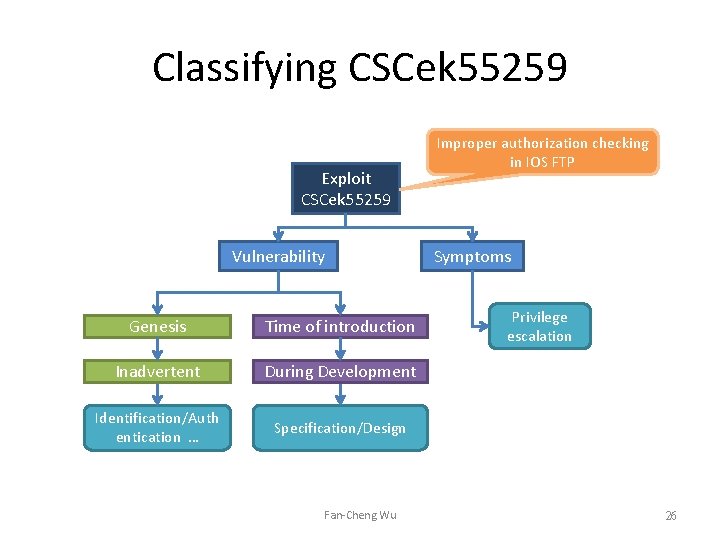
Classifying CSCek 55259 Exploit CSCek 55259 Vulnerability Genesis Time of introduction Inadvertent During Development Identification/Auth entication … Specification/Design Fan-Cheng Wu Improper authorization checking in IOS FTP Symptoms Privilege escalation 26

Reference 1. 2. 3. 4. 5. Landwehr CE, Bull AR, Mc. Dermott JP, et al. "A Taxonomy of Computer Program Security Flaws, " ACM Computing Surveys, 1994, 26(3): 211 -254. Matt Bishop, "A Taxonomy of UNIX System and Network Vulnerabilities, " Technical Report CSE-95 -10, Department of Computer Science, University of California at Davis, May 1995. Du W, Mathur A P, "Categorization of software errors that led to security breaches, " Proceedings of the 21 st National Information Systems Security Conference (NISSC' 98), 1998. F. Piessens, "A taxonomy of causes of software vulnerabilities in Internet software, " Proceedings of the. 13 th International Symposium on Software Reliability Engineering, Annapolis, Maryland, USA, November 2002. Sophie Engle, Sean Whalen, Damien Howard, "Tree Approach to Vulnerability Classification", Technical Report CSE-2006 -10, Dept. of Computer Science, University of California at Davis, May 2006. Fan-Cheng Wu 27
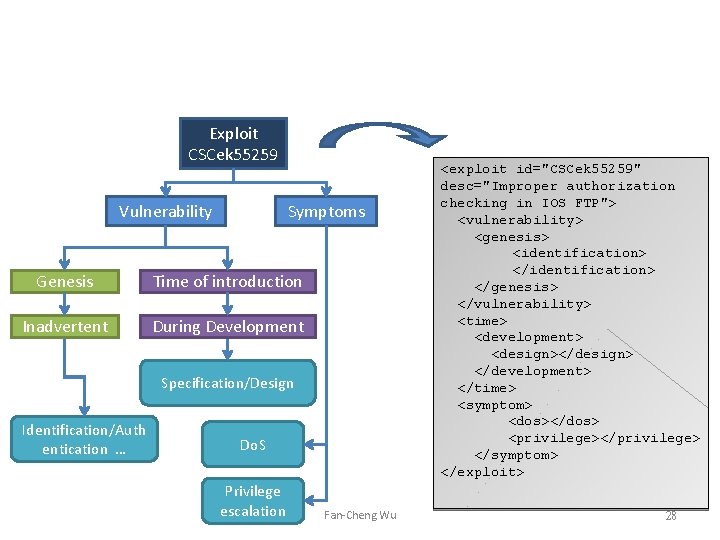
Exploit CSCek 55259 Vulnerability Symptoms Genesis Time of introduction Inadvertent During Development Specification/Design Identification/Auth entication … Do. S Privilege escalation Fan-Cheng Wu <exploit id="CSCek 55259" desc="Improper authorization checking in IOS FTP"> <vulnerability> <genesis> <identification> </genesis> </vulnerability> <time> <development> <design></design> </development> </time> <symptom> <dos></dos> <privilege></privilege> </symptom> </exploit> 28
![Dynamic Taint Analysis for Automatic Detection, Analysis, and Signature Generation of Exploits [1] Weekly Dynamic Taint Analysis for Automatic Detection, Analysis, and Signature Generation of Exploits [1] Weekly](http://slidetodoc.com/presentation_image_h2/d74597ebbb2757e2fbe2d9f4bc3886c7/image-29.jpg)
Dynamic Taint Analysis for Automatic Detection, Analysis, and Signature Generation of Exploits [1] Weekly report 2007/09/28 [1] Newsome J, Song D. Dynamic Taint Analysis for Automatic Detection, Analysis, and Signature Generation of Exploits on Commodity Software. Proceedings of the 12 th Annual Network and Distributed System Security Symposium(NDSS 2005), 2005 Fan-Cheng Wu 29

Outline • Goal – Fine-grained attack detector for commodity software – Automatic tools for signature generation • Design and Implementation • Evaluation – Precision – Performance • Attack Detector • Automatic Signature Generation Fan-Cheng Wu 30

Goal • Fine-grained attack detector for commodity software – Fine-grained attack detector – No need to recompile source code and libraries • Automatic tools for signature generation Fan-Cheng Wu 31
Monitoring program in run-time • In order to monitor program in run-time, we run PUT(program under test) on a virtual machine. • Valgrind [2] – An open-source virtual machine on Linux – Providing skin(tool) mechanism to instrument program in various ways • Taint. Check, a skin of Valgrind that – marks untruthful input as tainted (Taint. Seed) – traces tainted data (Taint. Tracker) – checks whether policies is violated by instructions (Taint. Assert) [2] Valgrind, http: //valgrind. org/ Fan-Cheng Wu 32
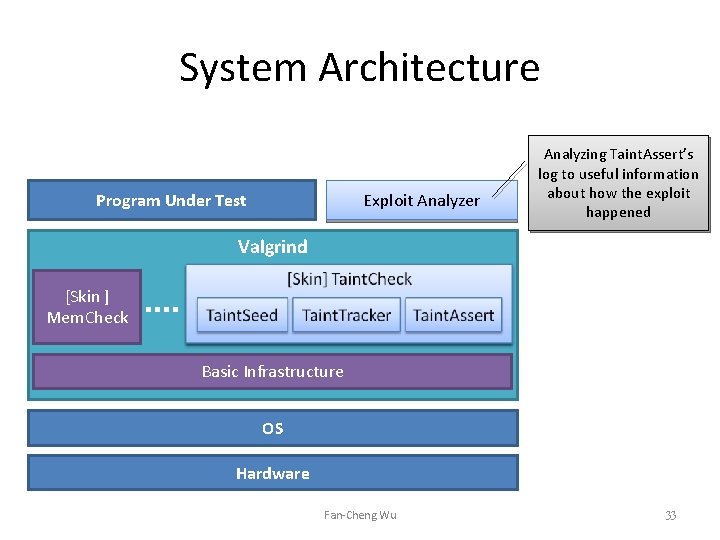
System Architecture Program Under Test Exploit Analyzer Analyzing Taint. Assert’s log to useful information about how the exploit happened Valgrind [Skin ] Mem. Check Basic Infrastructure OS Hardware Fan-Cheng Wu 33

False Positive • Possible cause of false positive – The program contains a vulnerability that should be fixed – The program performs sanity checks on the tainted data before it is used • Evaluation – Tested 13 programs – False positive is produced in 2 programs when reading data from configuration file as an offset to a jump address Fan-Cheng Wu 34
False Negative • Possible cause of false negative – Tainted attribute of flags is not considered, for example: Suppose x is tainted if ( x == 1 ) y=1; else if ( x == 2 ) y=2; … is semantically the same as x=y – Tainted data is used as an index into a table. – Taint. Check is configured to trust input that should not be trusted. Fan-Cheng Wu 35
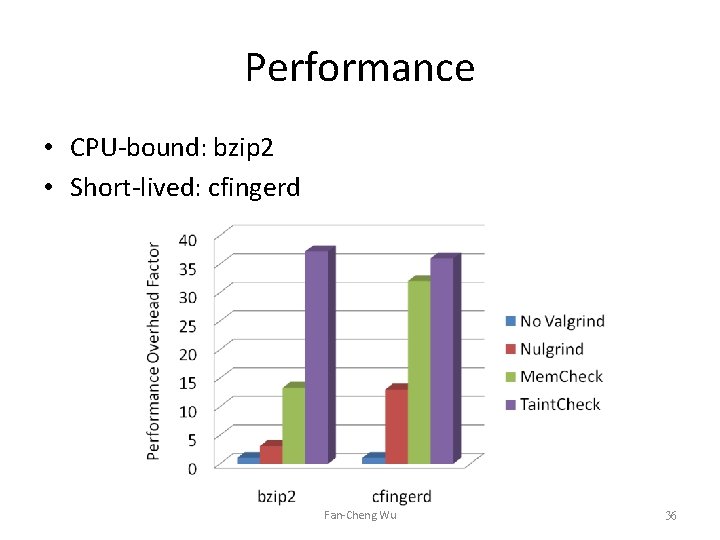
Performance • CPU-bound: bzip 2 • Short-lived: cfingerd Fan-Cheng Wu 36
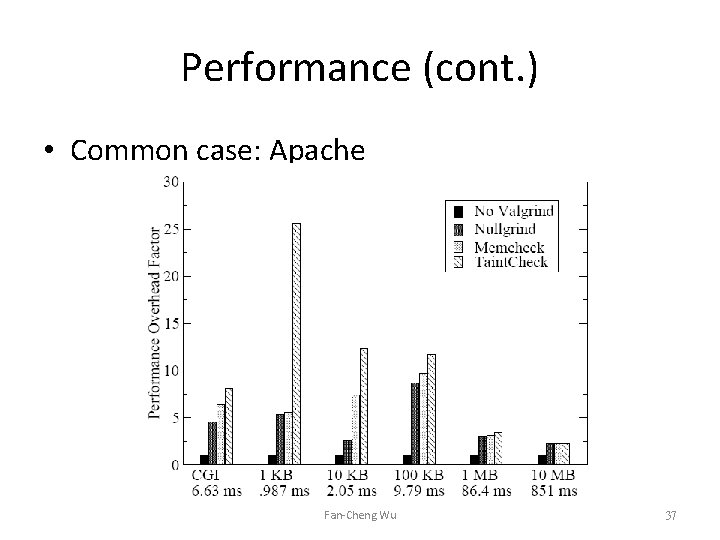
Performance (cont. ) • Common case: Apache Fan-Cheng Wu 37

Attack Detector • Performance overhead • Using Taint. Check with – sampling – anomaly detection Fan-Cheng Wu 38
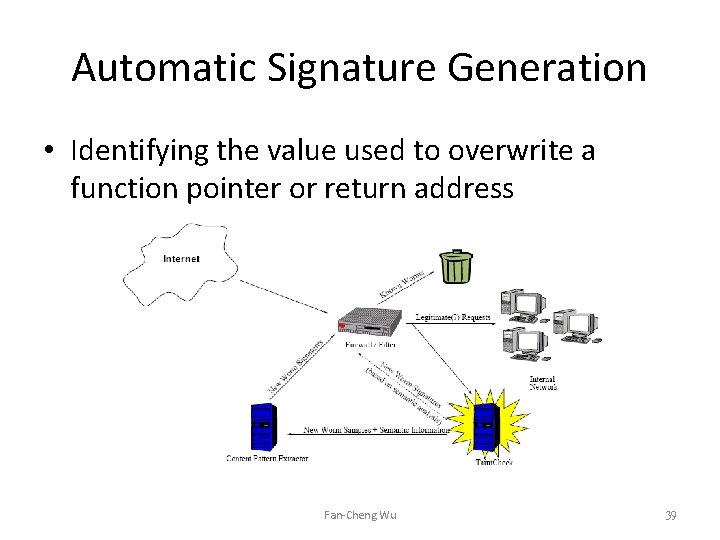
Automatic Signature Generation • Identifying the value used to overwrite a function pointer or return address Fan-Cheng Wu 39
- Slides: 39