Analysis of Security Protocols John C Mitchell Stanford


![Anomaly in Needham-Schroeder [Lowe] { A, Na }K A E { Na, Nb }Ka Anomaly in Needham-Schroeder [Lowe] { A, Na }K A E { Na, Nb }Ka](https://slidetodoc.com/presentation_image_h2/132f17e0df1ca75b2850673a36584126/image-6.jpg)


![Existential Quantification l Natural-deduction proof rule [y/x] ( elim) x. y not free in Existential Quantification l Natural-deduction proof rule [y/x] ( elim) x. y not free in](https://slidetodoc.com/presentation_image_h2/132f17e0df1ca75b2850673a36584126/image-15.jpg)
![Common Intruder Model l Derived from Dolev-Yao model [1989] w Adversary is nondeterministic process Common Intruder Model l Derived from Dolev-Yao model [1989] w Adversary is nondeterministic process](https://slidetodoc.com/presentation_image_h2/132f17e0df1ca75b2850673a36584126/image-20.jpg)


![Malleability l [Dolev, Dwork, Naor] Idealized assumption w If intruder produces Network(enc(k, x)) then Malleability l [Dolev, Dwork, Naor] Idealized assumption w If intruder produces Network(enc(k, x)) then](https://slidetodoc.com/presentation_image_h2/132f17e0df1ca75b2850673a36584126/image-27.jpg)


![Spi-Calculus l l [AG 97, . . . ] Write protocol in process calculus Spi-Calculus l l [AG 97, . . . ] Write protocol in process calculus](https://slidetodoc.com/presentation_image_h2/132f17e0df1ca75b2850673a36584126/image-34.jpg)





- Slides: 42

Analysis of Security Protocols John C. Mitchell Stanford University

Outline l Introduction to protocols and security w Security vs correctness w Examples and general concepts l Standard approach: analyze protocol+intruder w Unifying protocol formalism w Communication and intruder model l Specific projects based on standard approach w Theorem-proving, state enumeration methods, . . . l Mention some of own projects, results

Correctness vs Security l Program or System Correctness w Program satisfies specification For reasonable input, get reasonable output l Program or System Security w Program resists attack For unreasonable input, output not completely disastrous l Main differences w Active interference from environment w Refinement techniques may fail

Important Modeling Decisions l How powerful is the adversary? w w l Simple replay of previous messages Block messages; Decompose, reassemble and resend Statistical analysis, partial info from network traffic Timing attacks How much detail in underlying data types? w Plaintext, ciphertext and keys atomic data or bit sequences w Encryption and hash functions “perfect” cryptography algebraic properties: encr(x*y) = encr(x) * encr(y) for RSA encrypt(k, msg) = msg k mod N

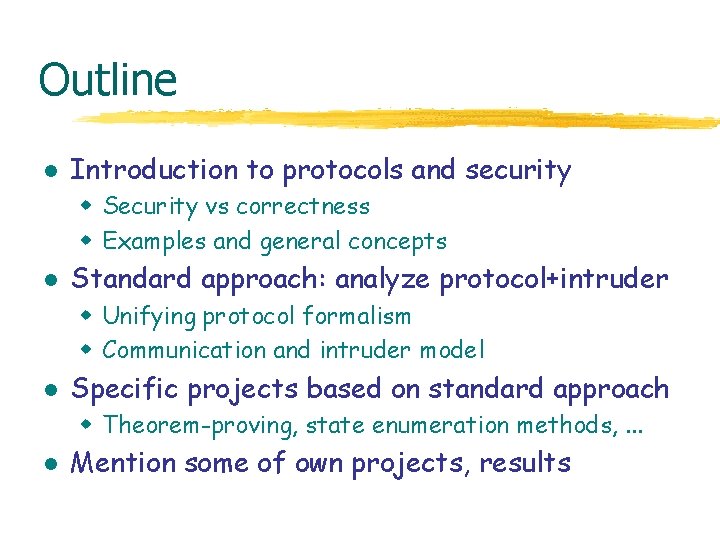
Needham-Schroeder Key Exchange { A, Noncea } K A b { Noncea, Nonceb } K { Nonceb} K a B b Result: A and B share two private numbers not known to any observer without Ka-1, Kb -1
![Anomaly in NeedhamSchroeder Lowe A Na K A E Na Nb Ka Anomaly in Needham-Schroeder [Lowe] { A, Na }K A E { Na, Nb }Ka](https://slidetodoc.com/presentation_image_h2/132f17e0df1ca75b2850673a36584126/image-6.jpg)
Anomaly in Needham-Schroeder [Lowe] { A, Na }K A E { Na, Nb }Ka { Nb }K Evil agent E tricks honest A into revealing private key Nb from B. Evil E can then fool B. e e { A, Na } { N a, N b } Kb Ka B

Outline l Introduction to protocols and security w Security vs correctness w Examples and general concepts èStandard approach: analyze protocol+intruder w Unifying protocol formalism w Communication and intruder model l Specific projects based on standard approach w Theorem-proving, state enumeration methods, . . . l Mention some of own projects, results

Analyzing Security Protocols l Non-formal approaches (can be useful, but no tools…) w Some crypto-based proofs [Bellare, Rogaway] l BAN and related logics w Axiomatic semantics of protocol steps H Methods based on operational semantics w Intruder model derived from Dolev-Yao w Protocol gives rise to set of traces w Perfect encryption Possible to include known algebraic properties

Example projects and tools l Prove protocol correct w w l Paulson’s “Inductive method”, others in HOL, PVS, etc. Bolignano -- Abstraction methods MITRE -- Strand spaces Process calculus approach: Abadi-Gordon spi-calculus Search using symbolic representation of states w Meadows: NRL Analyzer, Millen: Interrogator l Exhaustive finite-state analysis w FDR, based on CSP [Lowe, Roscoe, Schneider, …] w Mur -- specialized input language w Clarke et al. -- state search with axiomatic intruder model

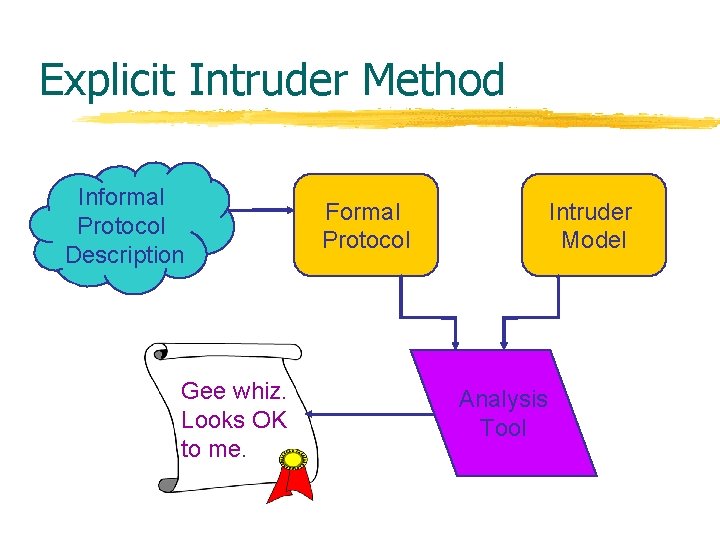
Explicit Intruder Method Informal Protocol Description Gee whiz. Looks OK to me. Formal Protocol Intruder Model Analysis Tool

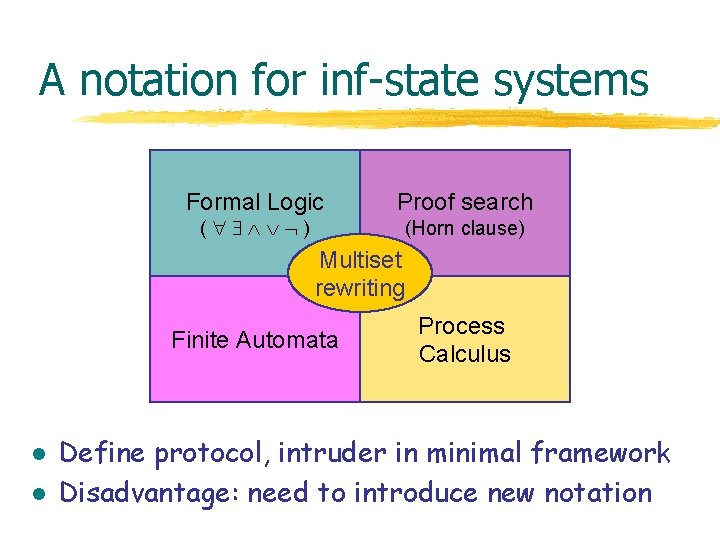
A notation for inf-state systems Formal Logic ( ) Proof search (Horn clause) Multiset rewriting Finite Automata l l Process Calculus Define protocol, intruder in minimal framework Disadvantage: need to introduce new notation

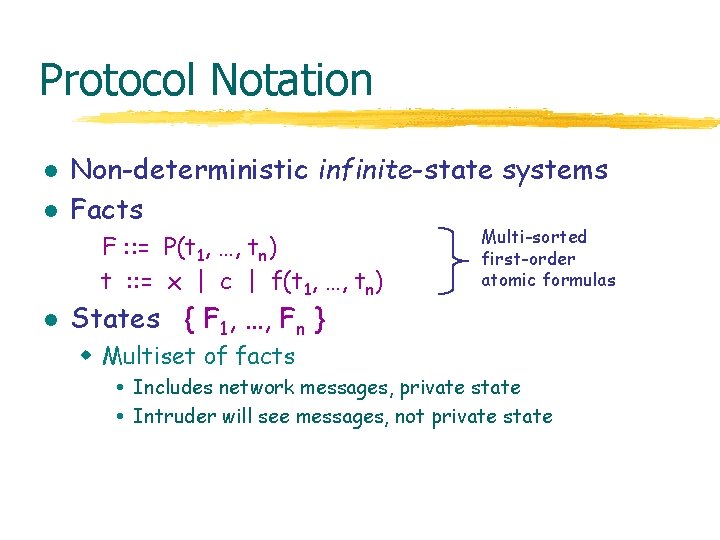
Protocol Notation l l Non-deterministic infinite-state systems Facts F : : = P(t 1, …, tn) t : : = x | c | f(t 1, …, tn) l Multi-sorted first-order atomic formulas States { F 1, …, Fn } w Multiset of facts Includes network messages, private state Intruder will see messages, not private state

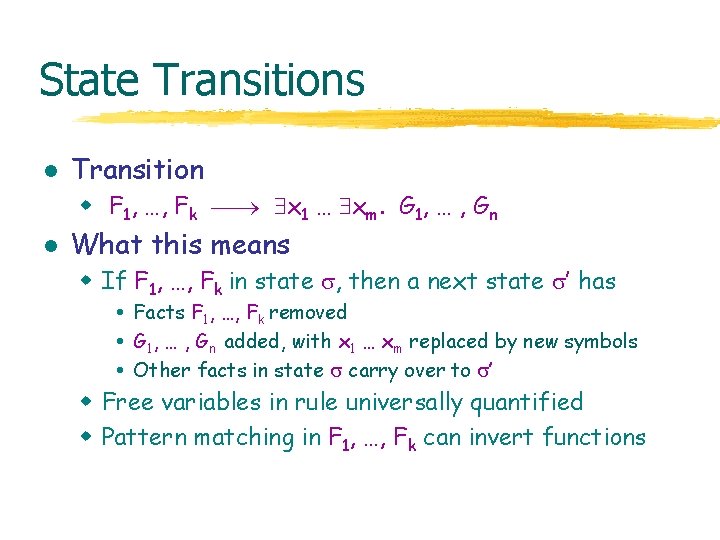
State Transitions l Transition w F 1, …, Fk x 1 … xm. G 1, … , Gn l What this means w If F 1, …, Fk in state , then a next state ’ has Facts F 1, …, Fk removed G 1, … , Gn added, with x 1 … xm replaced by new symbols Other facts in state carry over to ’ w Free variables in rule universally quantified w Pattern matching in F 1, …, Fk can invert functions

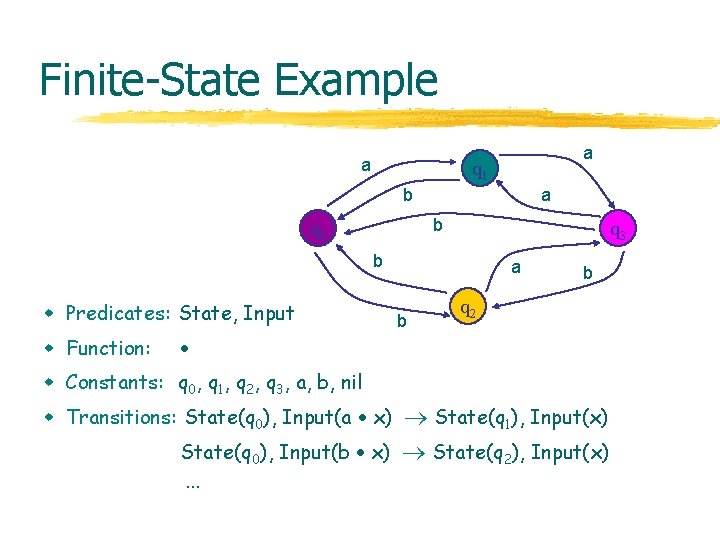
Finite-State Example a a q 1 b a b q 0 q 3 b w Predicates: State, Input w Function: a b b q 2 w Constants: q 0, q 1, q 2, q 3, a, b, nil w Transitions: State(q 0), Input(a x) State(q 1), Input(x) State(q 0), Input(b x). . . State(q 2), Input(x)
![Existential Quantification l Naturaldeduction proof rule yx elim x y not free in Existential Quantification l Natural-deduction proof rule [y/x] ( elim) x. y not free in](https://slidetodoc.com/presentation_image_h2/132f17e0df1ca75b2850673a36584126/image-15.jpg)
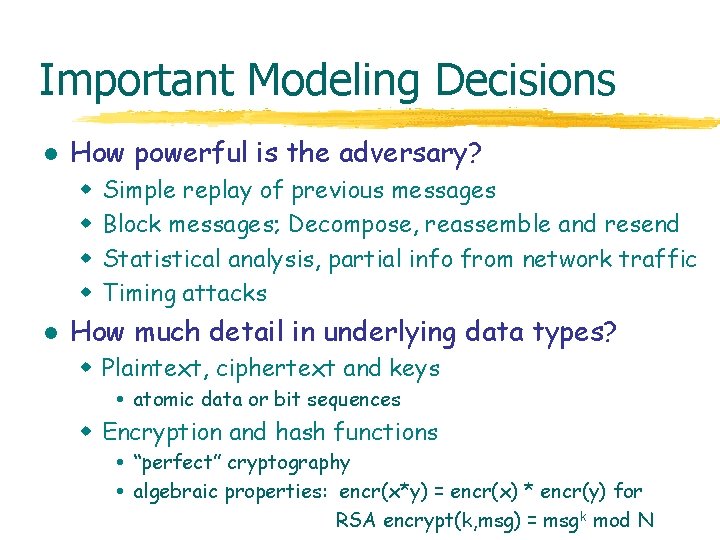
Existential Quantification l Natural-deduction proof rule [y/x] ( elim) x. y not free in any other hypothesis l Summary: for proof from x. , choose new symbol and proceed from [y/x]

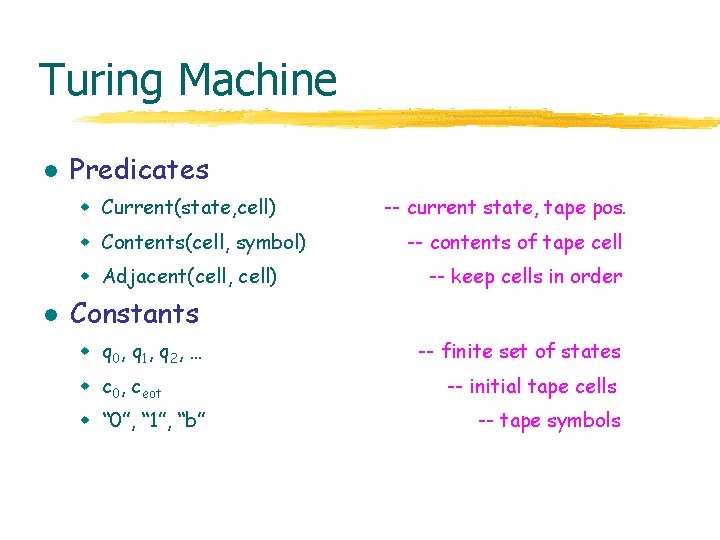
Turing Machine l Predicates w Current(state, cell) w Contents(cell, symbol) w Adjacent(cell, cell) l -- current state, tape pos. -- contents of tape cell -- keep cells in order Constants w q 0, q 1, q 2, … w c 0, ceot w “ 0”, “ 1”, “b” -- finite set of states -- initial tape cells -- tape symbols

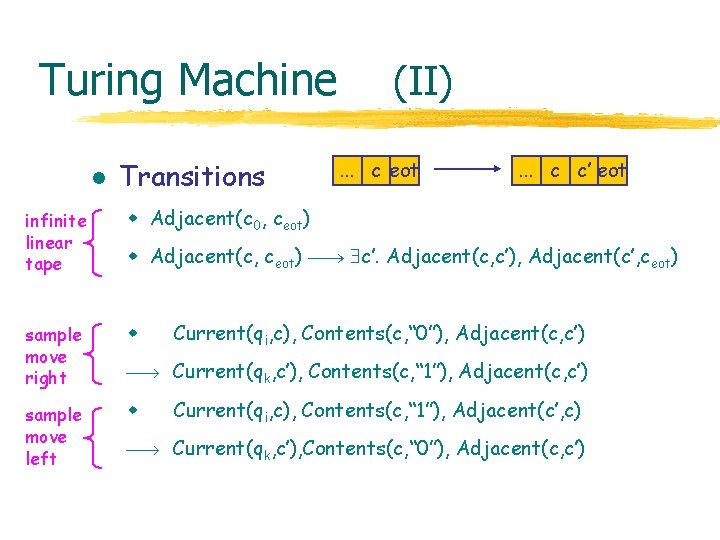
Turing Machine l Transitions (II). . . c eot . . . c c’ eot infinite linear tape w Adjacent(c 0, ceot) sample move right w Current(qi, c), Contents(c, “ 0”), Adjacent(c, c’) Current(qk, c’), Contents(c, “ 1”), Adjacent(c, c’) sample move left w Current(qi, c), Contents(c, “ 1”), Adjacent(c’, c) Current(qk, c’), Contents(c, “ 0”), Adjacent(c, c’) w Adjacent(c, ceot) c’. Adjacent(c, c’), Adjacent(c’, ceot)

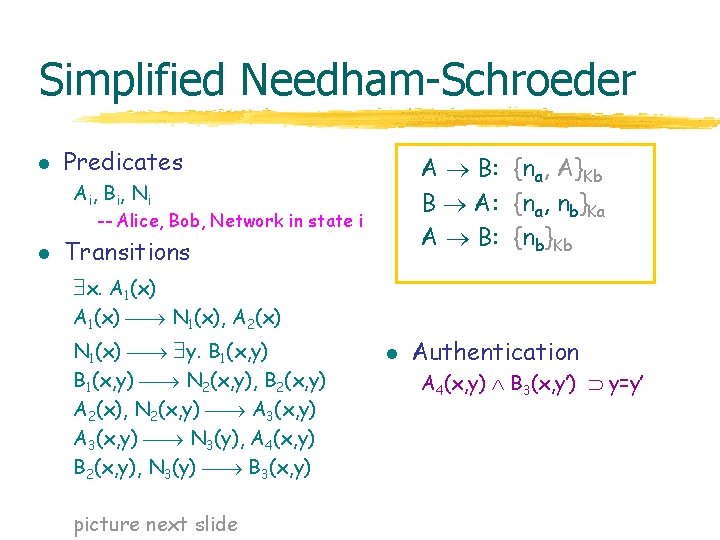
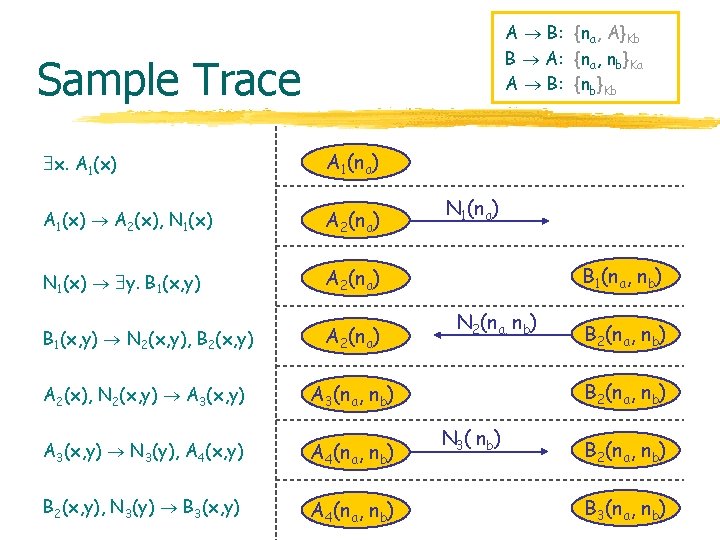
Simplified Needham-Schroeder l Predicates A B: {na, A}Kb B A: {na, nb}Ka A B: {nb}Kb Ai , B i , N i -- Alice, Bob, Network in state i l Transitions x. A 1(x) N 1(x), A 2(x) N 1(x) y. B 1(x, y) N 2(x, y), B 2(x, y) A 2(x), N 2(x, y) A 3(x, y) N 3(y), A 4(x, y) B 2(x, y), N 3(y) B 3(x, y) picture next slide l Authentication A 4(x, y) B 3(x, y’) y=y’

A B: {na, A}Kb B A: {na, nb}Ka A B: {nb}Kb Sample Trace x. A 1(x) A 1(na) A 1(x) A 2(x), N 1(x) A 2(na) N 1(x) y. B 1(x, y) A 2(na) B 1(x, y) N 2(x, y), B 2(x, y) A 2(na) A 2(x), N 2(x, y) A 3(x, y) A 3(na, nb) A 3(x, y) N 3(y), A 4(x, y) A 4(na, nb) B 2(x, y), N 3(y) B 3(x, y) A 4(na, nb) N 1(na) B 1(na, nb) N 2(na, nb) B 2(na, nb) N 3( nb) B 2(na, nb) B 3(na, nb)
![Common Intruder Model l Derived from DolevYao model 1989 w Adversary is nondeterministic process Common Intruder Model l Derived from Dolev-Yao model [1989] w Adversary is nondeterministic process](https://slidetodoc.com/presentation_image_h2/132f17e0df1ca75b2850673a36584126/image-20.jpg)
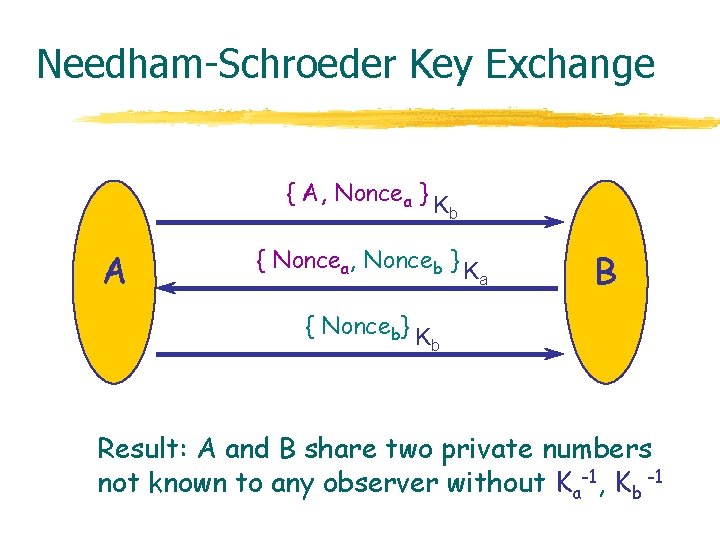
Common Intruder Model l Derived from Dolev-Yao model [1989] w Adversary is nondeterministic process w Adversary can Block network traffic Read any message, decompose into parts Decrypt if key is known to adversary Insert new message from data it has observed w Adversary cannot Gain partial knowledge Guess part of a key Perform statistical tests, …

Formalize Intruder Model l Intercept and remember messages N 1(x) M(x) N 3(x) M(x) l N 2(x, y) M(x), M(y) Send messages from “known” data M(x) N 1(x), M(x), M(y) N 2(x, y), M(x), M(y) M(x) N 3(x), M(x) l Generate new data as needed x. M(x) Highly nondeterministic, same for any protocol

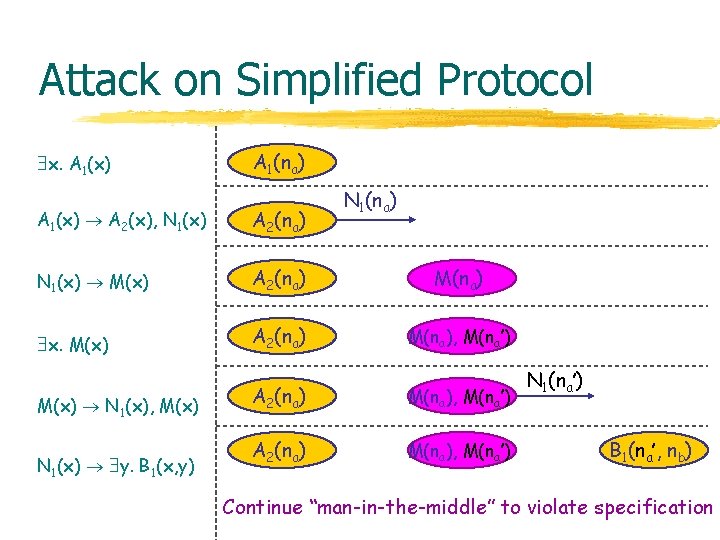
Attack on Simplified Protocol x. A 1(x) A 1(na) N 1(na) A 1(x) A 2(x), N 1(x) A 2(na) N 1(x) M(x) A 2(na) M(na) x. M(x) A 2(na) M(na), M(na’) M(x) N 1(x), M(x) N 1(x) y. B 1(x, y) A 2(na) M(na), M(na’) N 1(na’) B 1(na’, nb) Continue “man-in-the-middle” to violate specification

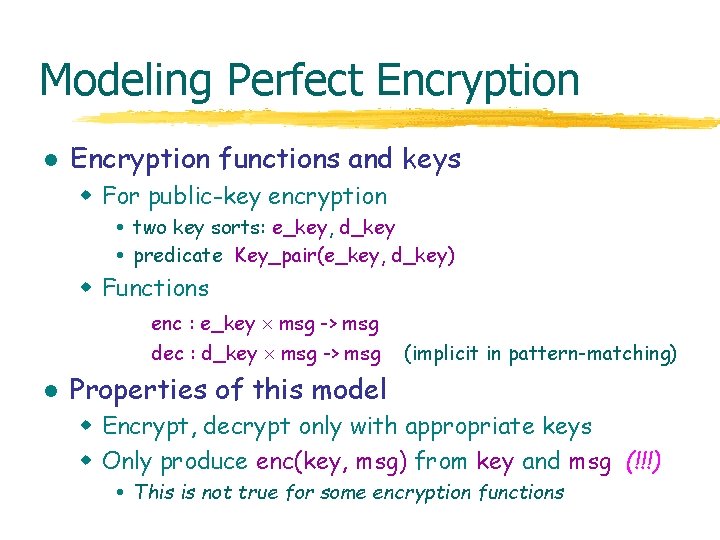
Modeling Perfect Encryption l Encryption functions and keys w For public-key encryption two key sorts: e_key, d_key predicate Key_pair(e_key, d_key) w Functions enc : e_key msg -> msg dec : d_key msg -> msg l (implicit in pattern-matching) Properties of this model w Encrypt, decrypt only with appropriate keys w Only produce enc(key, msg) from key and msg (!!!) This is not true for some encryption functions

Steps in public-key protocol l l Bob generates key pair and publishes w e_key u. d_key v. Bob 1(u, v) w Bob 1(u, v) NAnnounce(u), Bob 2(u, v) Alice sends encrypted message to Bob w Alice 1(e, d, x), NAnnounce(e’) Alice 2(e, d, x, e’) w Alice 2(e, d, x, e’) N 1(enc(e’, x, e )), Alice 3(u, v, x, w) l Bob decrypts w Bob 1(u, v), N 1(enc(u, x, y )) y. Bob 1(u, v, x, y)

Intruder Encryption Capabilities l Intruder can encrypt with encryption key w Me(k), Mdata(x) Ni(enc(k, x)), Me(k), Mdata(x) l Intruder can decrypt with decryption key w Nj(enc(k, x)), Key_pair(k, k’), Md(k’), Mdata(x), . . . l Add to previous intruder model Assumes sorts data, e_key, d_key with typed predicates Mdata(data), Me(e_key), Md(d_key)

Intruder: power and limitations l Can find some attacks w Needham-Schroeder by exhaustive search l Other attacks are outside model w Interaction between protocol and encryption l Some protocols cannot be modeled w Probabilistic protocols w Steps that require specific property of encryption l Possible to prove erroneous protocol correct w Requires property that crypto does not provide
![Malleability l Dolev Dwork Naor Idealized assumption w If intruder produces Networkenck x then Malleability l [Dolev, Dwork, Naor] Idealized assumption w If intruder produces Network(enc(k, x)) then](https://slidetodoc.com/presentation_image_h2/132f17e0df1ca75b2850673a36584126/image-27.jpg)
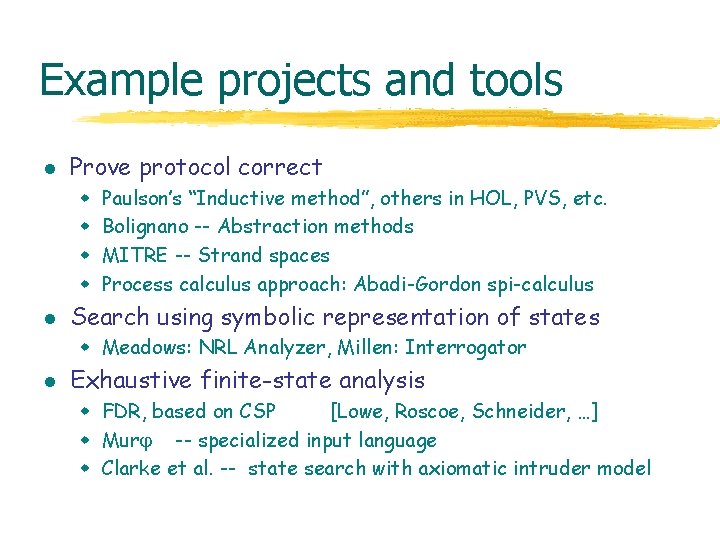
Malleability l [Dolev, Dwork, Naor] Idealized assumption w If intruder produces Network(enc(k, x)) then either Network(enc(k, x)) M(k), M(x) M (enc(k, x)) l (replay) (knows parts) Not true for RSA w encrypt(k, msg) = msgk mod N w property encr(x*y) = encr(x) * encr(y) l Model Network(enc(k, x)) M (…). . . Network (enc(k, c*x)) Can send encrypted message without “knowing” message Finite state ?

Outline l Introduction to protocols and security w Security vs correctness w Examples and general concepts l Standard approach: analyze protocol+intruder w Unifying protocol formalism w Communication and intruder model èSpecific projects based on standard approach w Theorem-proving, state enumeration methods, . . . l Mention some of own projects, results

Analysis of Protocol+Intruder l Prove properties of protocols w Unbounded # of participants, message space w Prove that system satisfies specification Paulson, etc: prove invariant holds at all reachable states Spi-calculus: prove protocol equivalent ideal protocol l Symbolic search with pruning w Search backward from error w Prune search by proving forward invariants l Exhaustive finite-state methods w Approximate infinite-state system by finite one w Search all states, perhaps with optimizations

Example description languages l First- or Higher-order Logic w Define set of traces, prove protocol correct l Horn-clause Logic x… (A 1 A 2 … B) w Symbolic search methods l Process calculus w FDR model checker based on CSP w Spi-calculus proof methods based on pi-calculus l Additional formalisms w CAPSL protocol description language [Millen] w Mur language for finite-state systems

Paulson’s Inductive Method l Define set TR of traces of protocol+intruder w Similar to traces in unifying formalism w Transition F 1, …, Fk x 1 … xm. G 1, … , Gn gives one way of extending trace l Auxiliary functions mapping traces to sets w Analz(trace) = data visible to intruder w Synth(trace) = messages intruder can synthesize l Definitions and proofs use induction w Similar inductive arguments for many protocols

Symbolic Search Methods l l Examples: NRL Protocol Analyzer, Interrogator Main idea w Write protocol as set of Horn clauses Transition F 1, …, Fk x 1 … xm. G 1, … , Gn can be Skolemized and translated to Prolog clauses w Search back from possible error for contradiction This is usual Prolog refutation procedure l Important pruning technique w Prove invariants by forward reasoning w Use these to avoid searching unreachable states

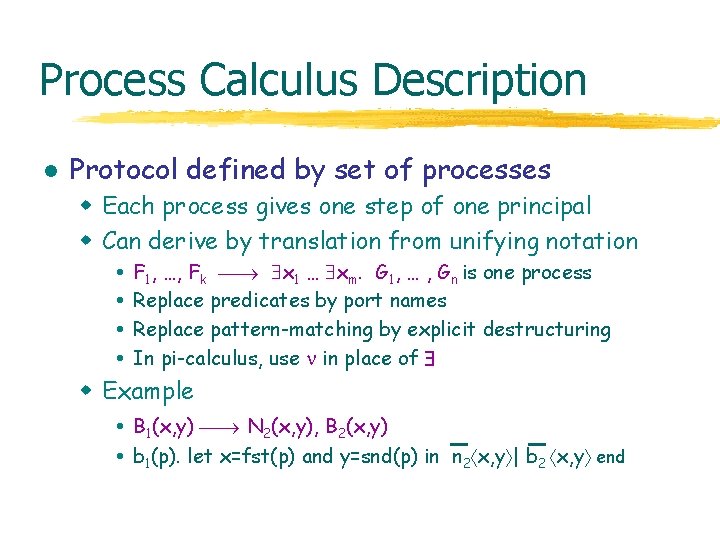
Process Calculus Description l Protocol defined by set of processes w Each process gives one step of one principal w Can derive by translation from unifying notation F 1, …, Fk x 1 … xm. G 1, … , Gn is one process Replace predicates by port names Replace pattern-matching by explicit destructuring In pi-calculus, use in place of w Example B 1(x, y) N 2(x, y), B 2(x, y) b 1(p). let x=fst(p) and y=snd(p) in n 2 x, y | b 2 x, y end
![SpiCalculus l l AG 97 Write protocol in process calculus Spi-Calculus l l [AG 97, . . . ] Write protocol in process calculus](https://slidetodoc.com/presentation_image_h2/132f17e0df1ca75b2850673a36584126/image-34.jpg)
Spi-Calculus l l [AG 97, . . . ] Write protocol in process calculus Express security using observ. equivalence w Standard relation from programming language theory P Q iff for all contexts C[ ], same observations about C[P] and C[Q] w Context (environment) represents adversary l Use proof rules for to prove security w Protocol is secure if no adversary can distinguish it from an idealized version of the protocol

Finite-state methods l Two sources of infinite behavior w Many instances of participants, multiple runs w Message space or data space may be infinite l Finite approximation w Transitions: F 1, …, Fk x 1 … xm. G 1, … , Gn choose fixed number of Skolem constants w Terms: restrict repeated functions f(f(x)))) l Can express finite-state protocol + intruder in w CSP : FDR-based model checking projects w Other notations: Mur project, Clarke et al. , . . .

Outline l Introduction to protocols and security w Security vs correctness w Examples and general concepts l Standard approach: analyze protocol+intruder w Unifying protocol formalism w Communication and intruder model l Specific projects based on standard approach w Theorem-proving, state enumeration methods, . . . èMention some of own projects, results

Security Protocols in Mur l Standard “benchmark” protocols w Needham-Schroeder, TMN, … w Kerberos l Study of Secure Sockets Layer (SSL) w Versions 2. 0 and 3. 0 of handshake protocol w Include protocol resumption l l Discovered all known or suspected attacks Recent work on tool optimization [Shmatikov, Stern, . . . ]

State Reduction on N-S Protocol

Another current project l Probabilisitic polynomial-time analysis w Drop simplifying assumption of perfect crypto w Use complexity-based assumptions instead l Use spi-calculus framework w Probabilistic poly-time process calculus w Specification by observational equivalence l l Many technical problems Some promise Given protocol, identify properties required of cryptographic primitives [Lincon, Mitchell 2, Scedrov]

Authentication and Secrecy for Handshake Protocols l How many protocols are there to verify? w w l Average length Data fields per message Distinct ways to fill a field Number of possible combinations 7 steps 5 fields 50 entries 1750 protocols Research directions w w Get the monkeys and typewriters going Easier description and specification, faster tools Improved analysis of timestamps, . . . Interaction between protocol and crypto primitives

Beyond “standard” protocols l Protocols for other purposes w Electronic commerce, fair commitment, . . . l Modularity w How to compose secure systems? w Which module performs security check? l Isolation and Infiltration w Firewalls and tunneling w Intrusion detection, survival, recovery w Mobile code New forms of interaction, new risks; need new model l Economic security: more costly to attack than worth

Conclusion l l Security problems can be fun Many scientific, engineering challenges w Model intruder, properties of cryptography l Results that matter See short paper in proceedings, web site for references to other work Mur DEMO !