Analysis of secure hash functions Attacks and Defense


































- Slides: 51

Analysis of secure hash functions Attacks and Defense

Agenda • Hash function • Types of Attack

Data security • Goals of Data Security – Confidentiality – data integrity – Authentication – non-repudiation • Cryptography and Cryptanalysis

Hash function • A “primitive” used in cryptographic applications. – To guarantee the data integrity in the message transfer. – To guarantee the security of digital signatures( no forgery). – Used to design many cryptographic algorithms and protocols. For example, digital signature , group signature, e-cash, e-vote, bit-commitment

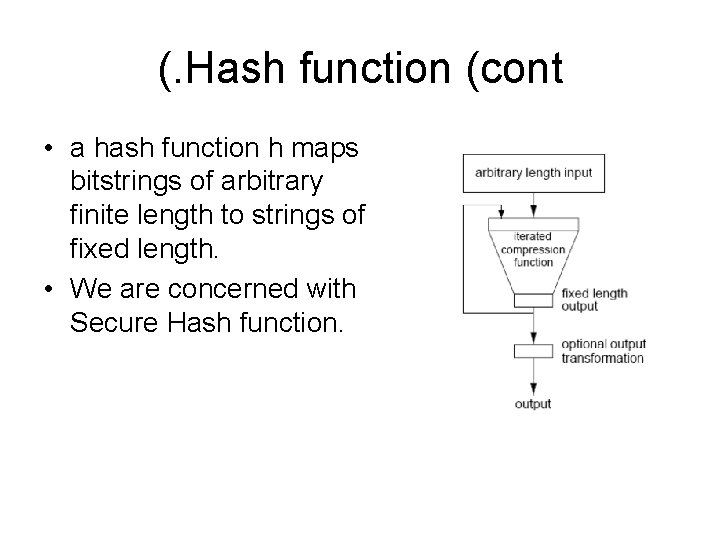
(. Hash function (cont • a hash function h maps bitstrings of arbitrary finite length to strings of fixed length. • We are concerned with Secure Hash function.

Secure Hash function • A h to be one-way hash function – Is a Hash function – Easy to compute – Hard to invert. • For collision Resistance – it is ‘hard’ to find two distinct messages that hash to the same result i. e. , find X 1 and X 2 (X 1≠ X 2) such that h(X 1) = h(X 2)

Methods to Construct Hash function • • Iterated Block cipher (slow) Modular Arithmetic (very slow) Dedicated hash function – MDx family – SHA-x family

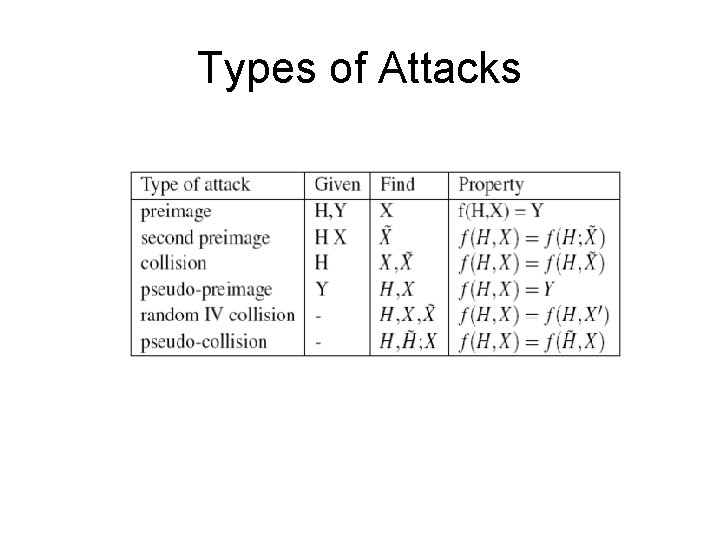
Types of Attacks

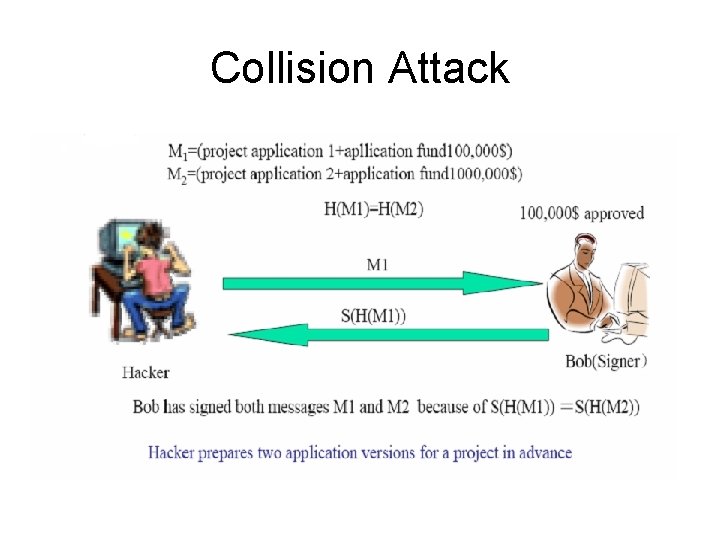
Collision Attack

(. Collision Attack (cont

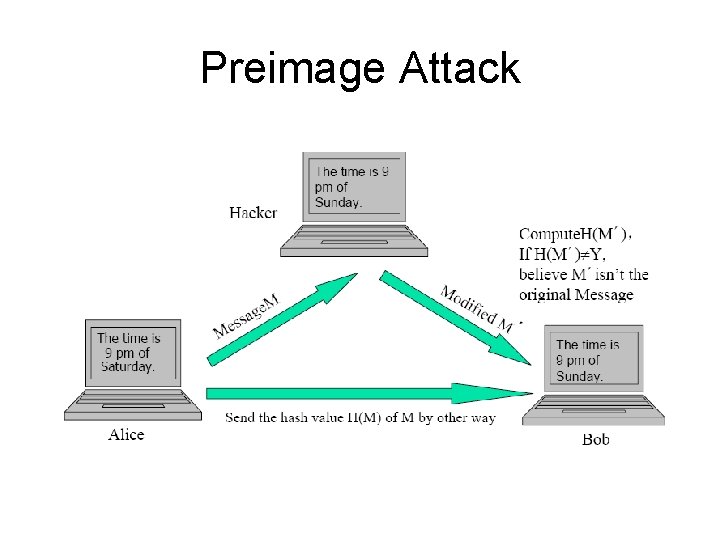
Preimage Attack

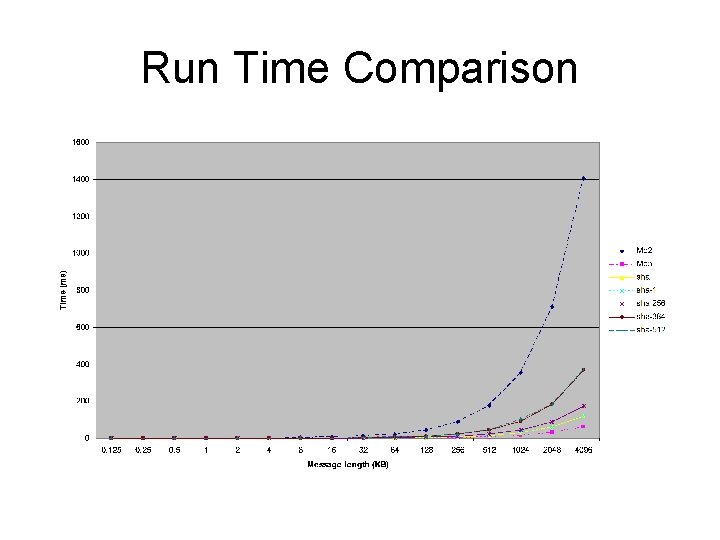
Run Time Comparison

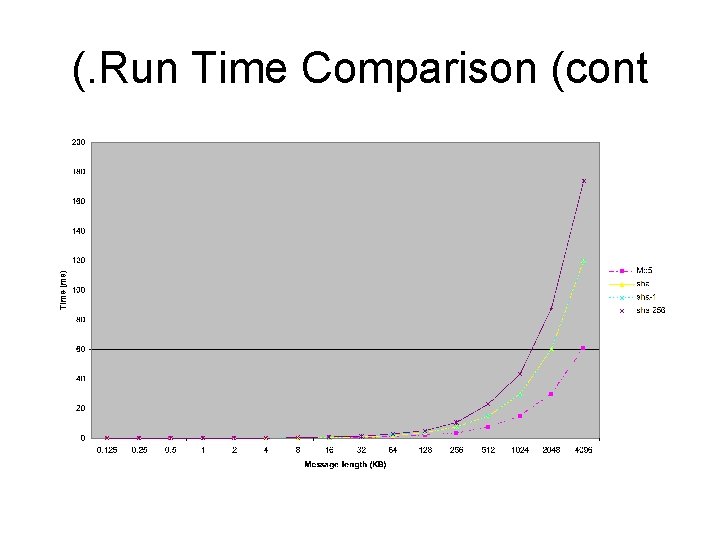
(. Run Time Comparison (cont

Security of Hash function • Merkle-Damagard • If the IV is fixed and if the padding procedure includes the length of the input into the padding bits, then h is collision-resistant if f is collisionresistant.

SHA-0 /SHA-1 • SHA-0 published in 1993 as the Secure Hash Standard, FIPS PUB 180, by US government standards agency NIST. • withdrawn after publication & replaced with SHA-1 in 1995.

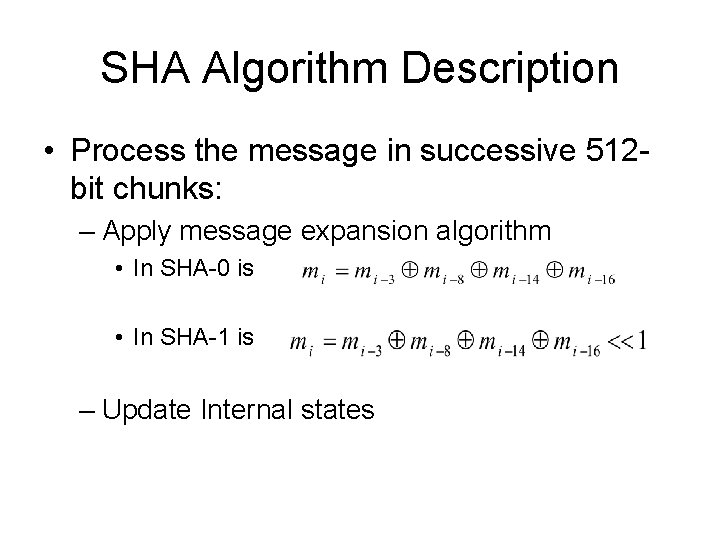
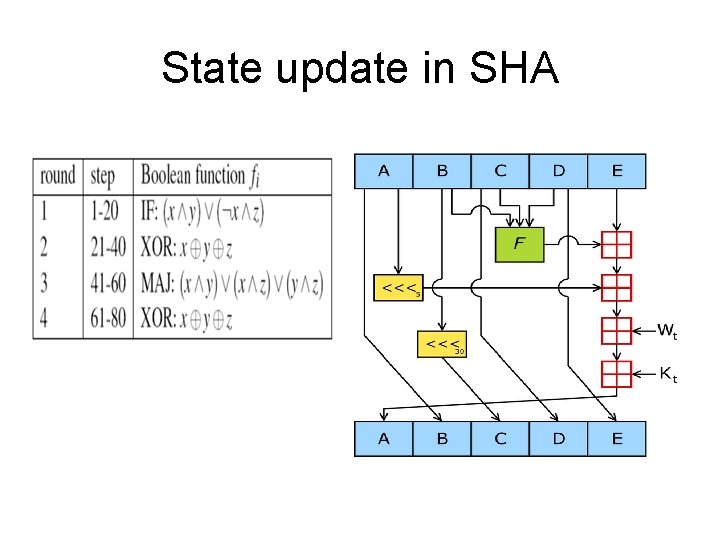
SHA Algorithm Description • Process the message in successive 512 bit chunks: – Apply message expansion algorithm • In SHA-0 is • In SHA-1 is – Update Internal states

State update in SHA

Cryptanalysis on SHA-0 • In CRYPTO 98, Chabaud and Joux collisions can be found with complexity 261 • Linear approximation SHA-0 and found a collision then map it back to original function.

(. Cryptanalysis on SHA-0(cont • Biham and Chen found near-collisions for SHA-0 (142 out of 160) Using algebraic method. • Wang made collision attack in O(239)

Cryptanalysis on SHA-1 • Oswald apply Joux work to SHA-1 found a collision for reduced version 53 out of 80 rounds • In February 2005, an attack by Xiaoyun Wang, Yiqun Lisa Yin, and Hongbo Yu was announced in O(269) • On 17 August 2005, Xiaoyun Wang, Andrew Yao lowering the complexity required for finding a collision in SHA-1 to O(263).

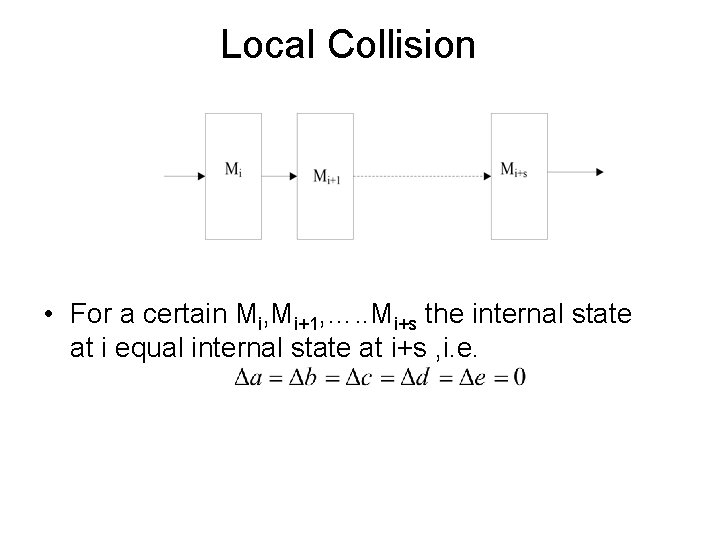
Local Collision • For a certain Mi, Mi+1, …. . Mi+s the internal state at i equal internal state at i+s , i. e.

Local collision for SHA • For Message m 6 -step local collision with 2 conditions on m mi, 2 ≠ mi+2, 2 (in step i+3) and mi, 2 ≠ mi+1, 7

Wang Attacks on SHA-x Family • • • Found a local collisions (1997) Attack on SHA-0 O(239) (2005) Attack on SHA-1 O(269) then O(263) (2005)

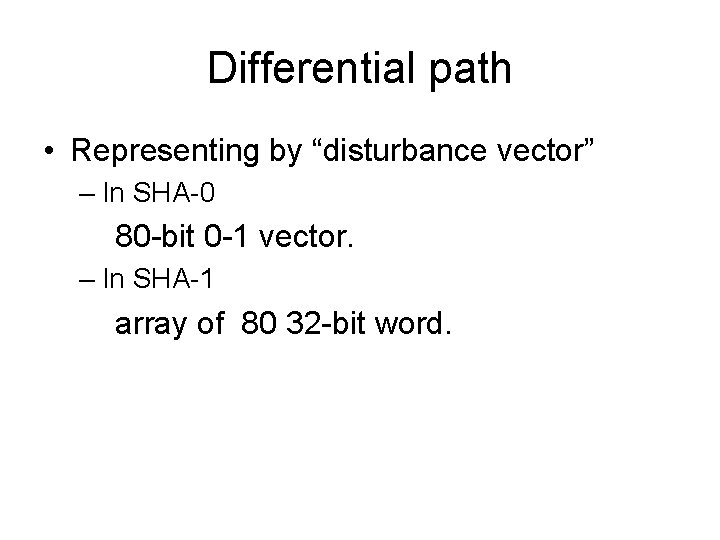
Wang Attack Outline 1. Find Differential path, the path is a sequence of local collisions joined together. 2. derive a set of sufficient conditions for the differential path to hold. 3. Apply message modification techniques satisfying derived conditions.

Differential path • Representing by “disturbance vector” – In SHA-0 80 -bit 0 -1 vector. – In SHA-1 array of 80 32 -bit word.

Wang Attack • disturbance vector leading to a collision of SHA 0.

Find Good Disturbance vector • Wang use condition I only.

Message modification techniques • Used to lower the attack order, by reducing conditions on message bits. • Consider a condition on m 17, 32. Instead of modifying m 16, which is dependent on four earlier message words, we modify m 15 in a way that will flip the bit m 16, 32 , which in turn flips the bit m 17, 32 in step 17.

NIST Response to Wang Attack • encourages a rapid adoption of the SHA-2 hash functions • Announce hash function competition, similar to the successful Advanced Encryption Standard (AES) development and selection process.

Contributions • Proposed solution to Prevent Wang attack • Proposed Improvement for MD 2 attack

Proposed Solution • In Addition to Response of NSIT • Truncate to SHA-256 output to 160 bits. • Re-design affected protocols

Proposed Solution • Attack is based on local collision. • If prevent this, whole the attack will fail.

preventing local collision • collision depends on certain conditions on message bit. • Recall mi, 2 ≠ mi+2, 2 (in step i+3) and mi, 2 ≠ mi+1, 7 • If any of them been violated the attack will fail.

Method to prevent local collision • Set mi, 2 = mi+2, 2 = 1 for each mi. • Construct Pad p by concatenating all bits at bit location 2.

• Correctness. – Proposed solution is 1 -to-1 function. – Required conditions will violated. • Overhead – The message will be stretched. – For each message word , overhead is 1 bit. Totaling About 3%.

Decreasing Overhead – Use mi, 2 = mi+1, 7 =1 need 2 bit (2, 7) to be padded but needed for each step in local collision. – Violating 6 consecutive messages needs 2 bit of overhead. – 1% overhead.

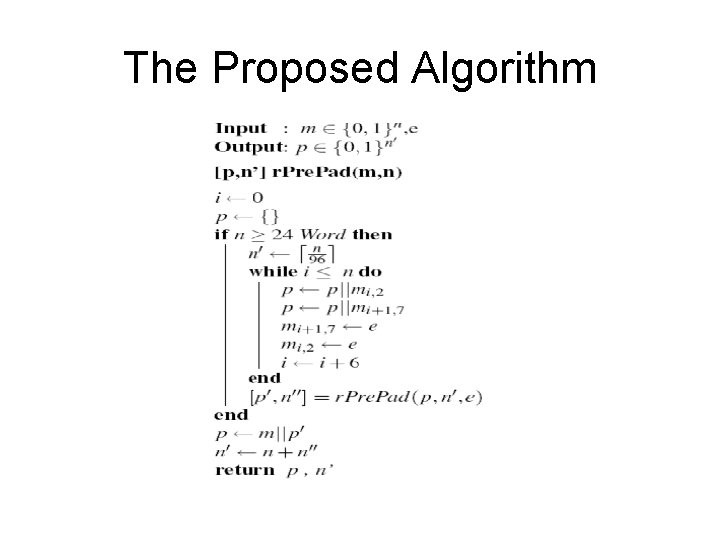
Prevent Collision in Padding – We guarantee no collision in Message m – What about the padding P ? – Do the algorithm recursively. The total overhead will be in less than 2%.

The Proposed Algorithm

Assessment of Proposed Modification • Pros – No Modification in SHA – Work with SHA-0 and SHA-1 – Can be generalized to other hash function. – Low overhead. • Cons – works on bit level. Many Bitwise ANDing , shifting ORing.

MD-2 • • Old 1990 by Rivest. Byte-Oriented. Inefficient Produce 128 bits “Strange” compression function. Not Merkle-Damagard construction MD 2 is still used in some certificates. No attack to full MD-2 till Muller (2004).

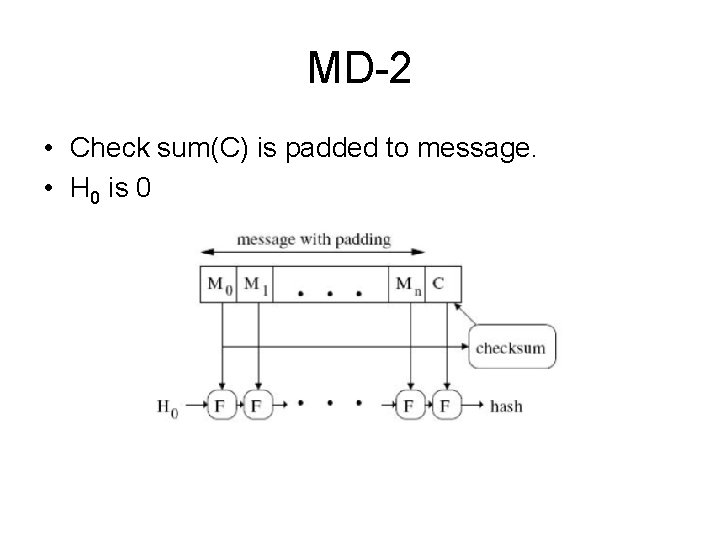
MD-2 • Check sum(C) is padded to message. • H 0 is 0

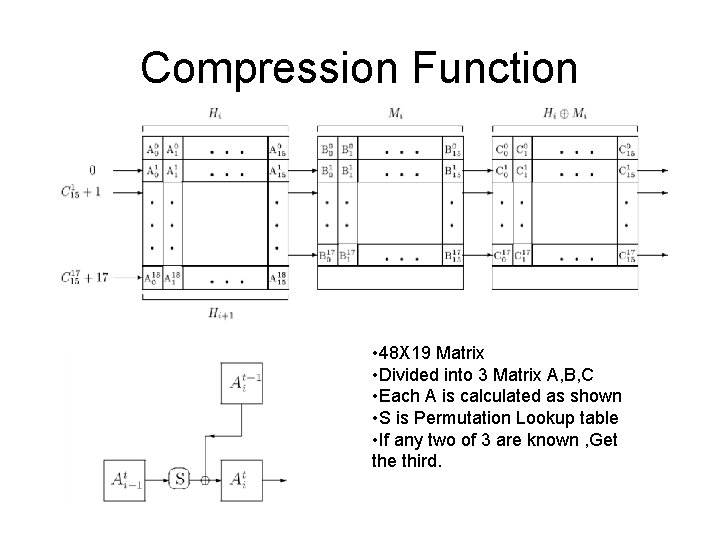
Compression Function • 48 X 19 Matrix • Divided into 3 Matrix A, B, C • Each A is calculated as shown • S is Permutation Lookup table • If any two of 3 are known , Get the third.

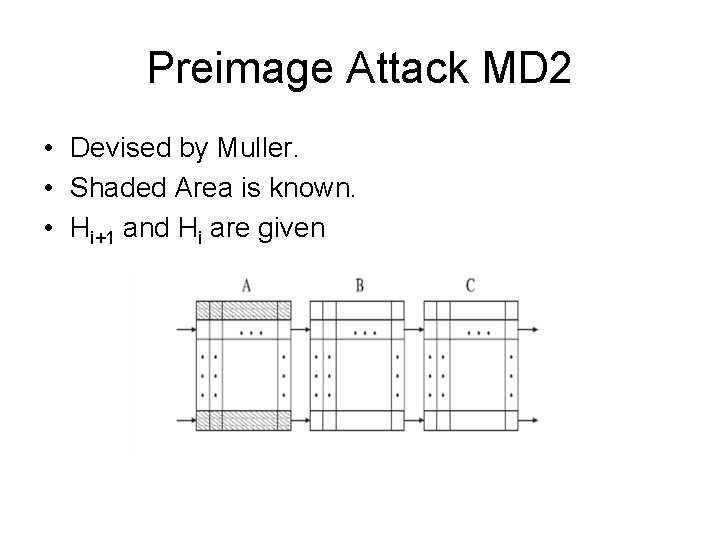
Preimage Attack MD 2 • Devised by Muller. • Shaded Area is known. • Hi+1 and Hi are given

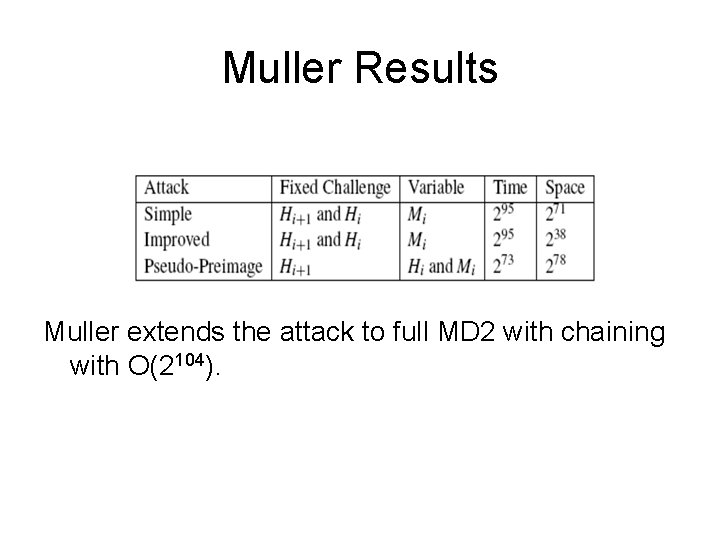
Muller Results Muller extends the attack to full MD 2 with chaining with O(2104).

Contributions • Proposed solution to Prevent Wang attack • Proposed Improvement for MD 2 attack

Proposed Attack • Given Hi, Hi+2. Find Mi Mi+1 , Hi+1. • Assume 2 message blocks • The attack is similar to Pseudo-Perimage attack.

Steps of Proposed Attack 1. Choose K 0, …, K 4 at random. 2. In step I – Try 288 message for mi – Compute Hi+1 if it on the form hi=(***, k 0, . . K 4) Add mi and hi+1 to Table T. T size is O(248) 3. In step i+1 -Pick 288 Message of Form Mi+1=(**, …*, K 0, K 1, …K 4). Complete the attack as pseudo preimage.

Proposed Attack • O(289). • Probability of Failure is 1/e =0. 3 • Improve the attack – In step I, I can found if H is not on required form after 11 row, speedup O(21. 4). – In computing C , We only calculated about half of C. speedup(26. 7) – In Thesis , Parallel version of algorithm is presented

Conclusions • Proposed Protection to SHA from Wang attack. • Proposed second Preimage attack on MD 2. • As pointed by NIST – A new hash function is required. – SHA-2 should be used.

Future work • Design securer hash function • Framework to estimate function security with Neural network

…Thank You