Analysis of Host Authentication Mechanism in Current POD



- Slides: 10

Analysis of Host Authentication Mechanism in Current POD Copy Protection System Author: Hai-Bo Tian, Yang Zhan, Yu-Min Wang From: IEEE Transactions on Consumer Electronics, Vol. 51, No. 3, August 2005 ZHI-JIA CHEN /10 2007/01/03

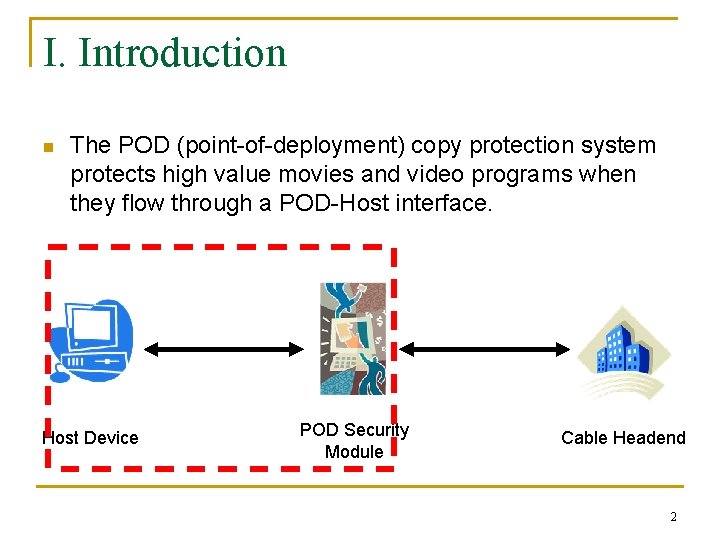
I. Introduction n The POD (point-of-deployment) copy protection system protects high value movies and video programs when they flow through a POD-Host interface. Host Device POD Security Module Cable Headend 2

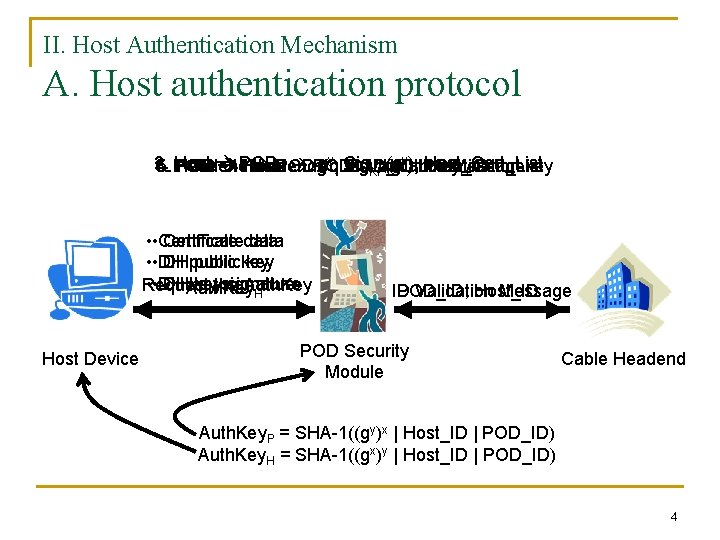
II. Host Authentication Mechanism A. Host authentication protocol n n It is designed to authenticate a host device. First phase: certificate verification and DH (Diffie-Hellman) key exchange Second phase: authentication key verification Third phase: the headend report back 3

II. Host Authentication Mechanism A. Host authentication protocol xy), 2. Host_Cert_List 4. POD: Host POD: Auth. Key 1. Host: gxy, Sig (g POD_Cert_List 3. 6. 5. POD Headend: POD: request ID POD_ID, Validation the authentication Host_ID Message key KH H KP • • Certificatedata • • DH DHpublickey • • DH DHAuth. Key keythe signature Request Auth. Key H Host Device ID Validation Message POD_ID, Host_ID POD Security Module Cable Headend Auth. Key. P = SHA-1((gy)x | Host_ID | POD_ID) Auth. Key. H = SHA-1((gx)y | Host_ID | POD_ID) 4

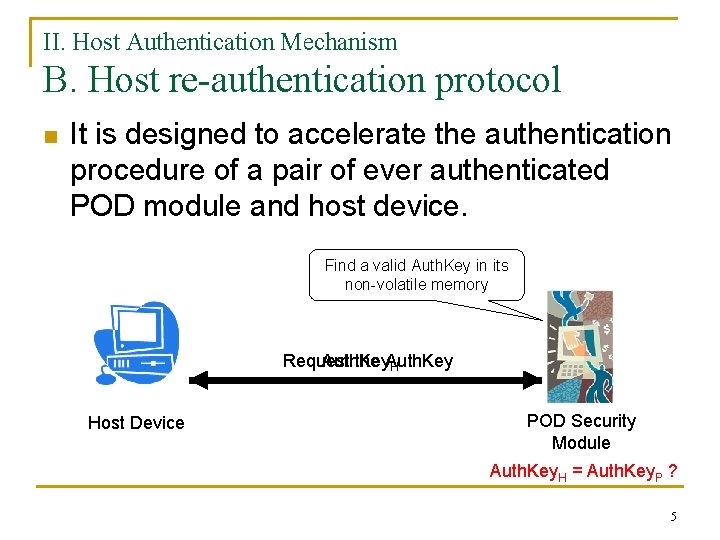
II. Host Authentication Mechanism B. Host re-authentication protocol n It is designed to accelerate the authentication procedure of a pair of ever authenticated POD module and host device. Find a valid Auth. Key in its non-volatile memory Request Auth. Key the Auth. Key H Host Device POD Security Module Auth. Key. H = Auth. Key. P ? 5

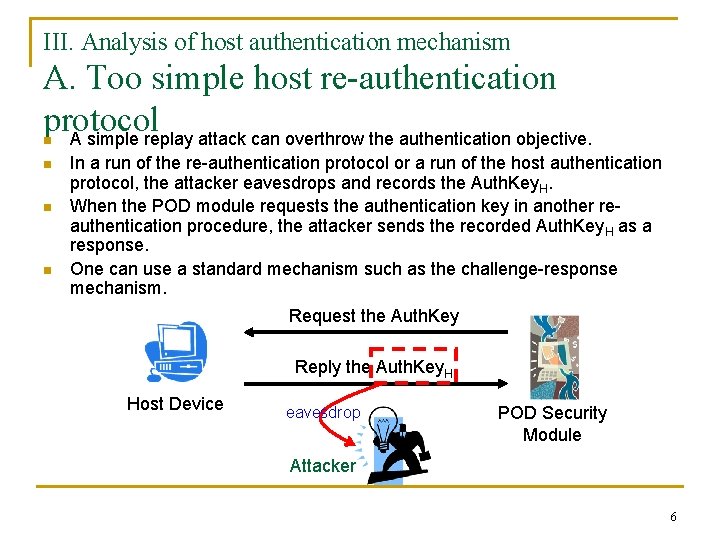
III. Analysis of host authentication mechanism A. Too simple host re-authentication protocol A simple replay attack can overthrow the authentication objective. n n In a run of the re-authentication protocol or a run of the host authentication protocol, the attacker eavesdrops and records the Auth. Key. H. When the POD module requests the authentication key in another reauthentication procedure, the attacker sends the recorded Auth. Key. H as a response. One can use a standard mechanism such as the challenge-response mechanism. Request the Auth. Key Reply the Auth. Key. H Host Device eavesdrop POD Security Module Attacker 6

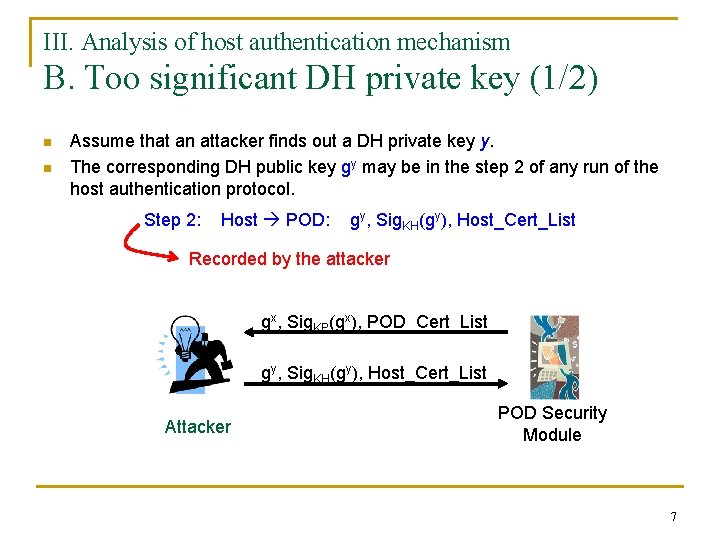
III. Analysis of host authentication mechanism B. Too significant DH private key (1/2) n n Assume that an attacker finds out a DH private key y. The corresponding DH public key gy may be in the step 2 of any run of the host authentication protocol. Step 2: Host POD: gy, Sig. KH(gy), Host_Cert_List Recorded by the attacker gx, Sig. KP(gx), POD_Cert_List gy, Sig. KH(gy), Host_Cert_List Attacker POD Security Module 7

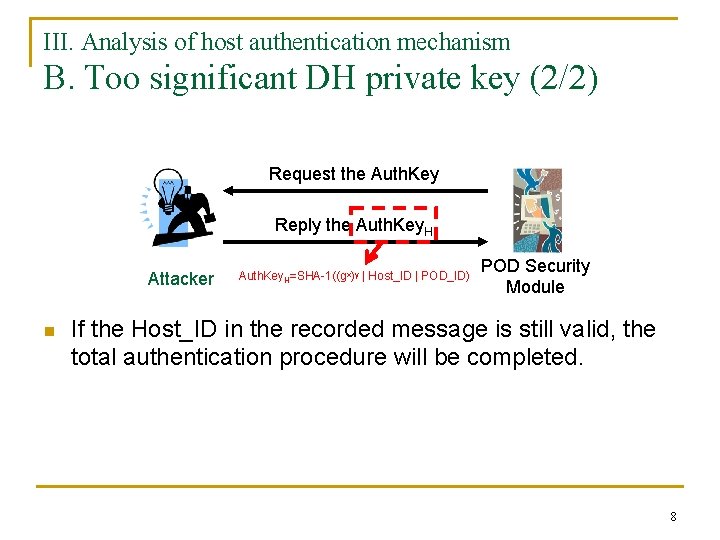
III. Analysis of host authentication mechanism B. Too significant DH private key (2/2) Request the Auth. Key Reply the Auth. Key. H Attacker n Auth. Key. H=SHA-1((gx)y | Host_ID | POD_ID) POD Security Module If the Host_ID in the recorded message is still valid, the total authentication procedure will be completed. 8

III. Analysis of host authentication mechanism C. Useless messages in the first step Step 1: POD Host: n n gx, Sig. KP(gx), POD_Cert_List There is no need for a POD module to show any credentials for the goal of host authentication. Any active attacker can record the first message. Any attacker can use a compromised certificate in a certificate revocation list to produce a valid step 1 message. A host device has no chance to know the certificate status. 9

IV. Discussion n An implementation of the POD copy protection system that wants a higher secure level should disable these steps or replace these steps. The leakage of a DH private key not only affects one run of the authentication protocol but also leads to authentication failure after this run. The signature and certification list of the POD module are useless. 10