Analog OnTag Hashing Towards Selective Reading as Hashing













- Slides: 32

Analog On-Tag Hashing: Towards Selective Reading as Hashing Primitives in Gen 2 RFID System Lei Yang, Qiongzheng Lin, Chunhui Duan, Zhenlin An The Hong Kong Polytechnic University 18, July, 2017

1. Background & Motivation More info

1. What is RFID? Air Protocol Tag Ta Reader IDTech. Ex: 18. 2 billion tags have been sold so far in 2017. RFID Systems have been widely employed for various applications!

1. 1 The-State-of-Art: UHF RFID Standards GEN 2 EPCglobal Gen 2 has become the widely adopted air protocol.

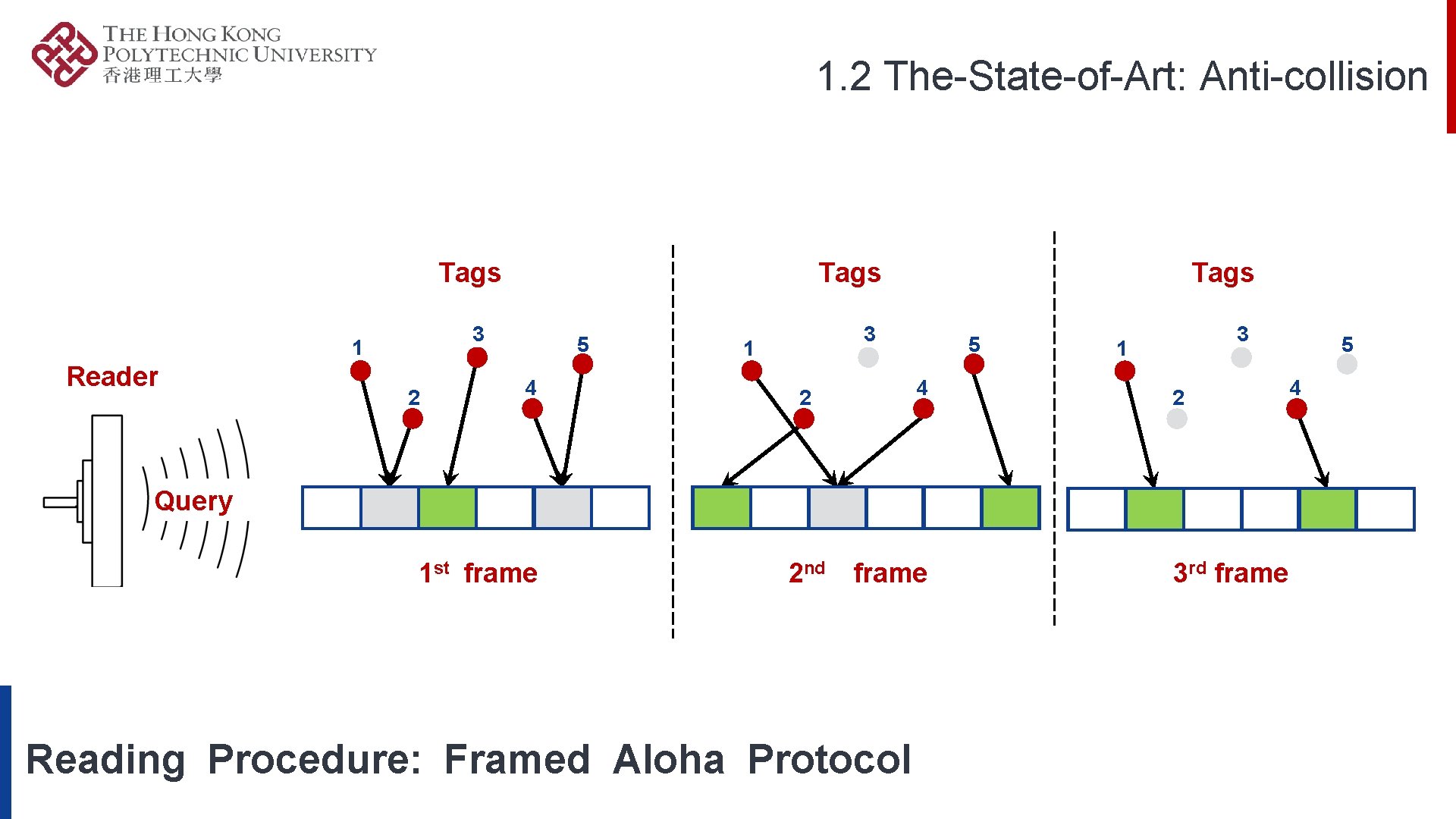
1. 2 The-State-of-Art: Anti-collision Tags 3 1 Reader Tags 2 5 4 Tags 3 1 5 4 2 3 1 2 Query 1 st frame 2 nd frame Reading Procedure: Framed Aloha Protocol 3 rd frame 5 4

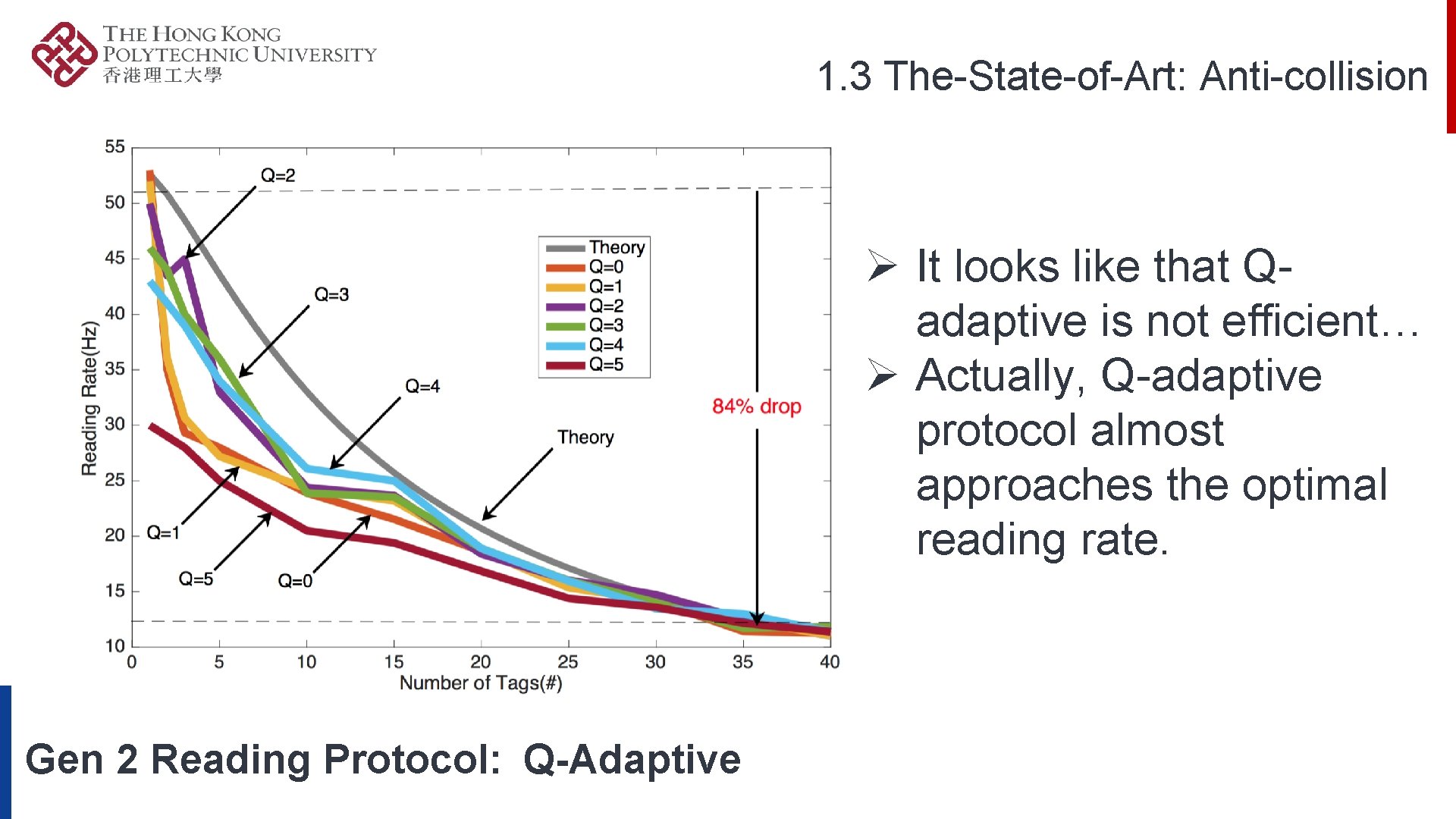
1. 3 The-State-of-Art: Anti-collision Ø It looks like that Qadaptive is not efficient… Ø Actually, Q-adaptive protocol almost approaches the optimal reading rate. Gen 2 Reading Protocol: Q-Adaptive

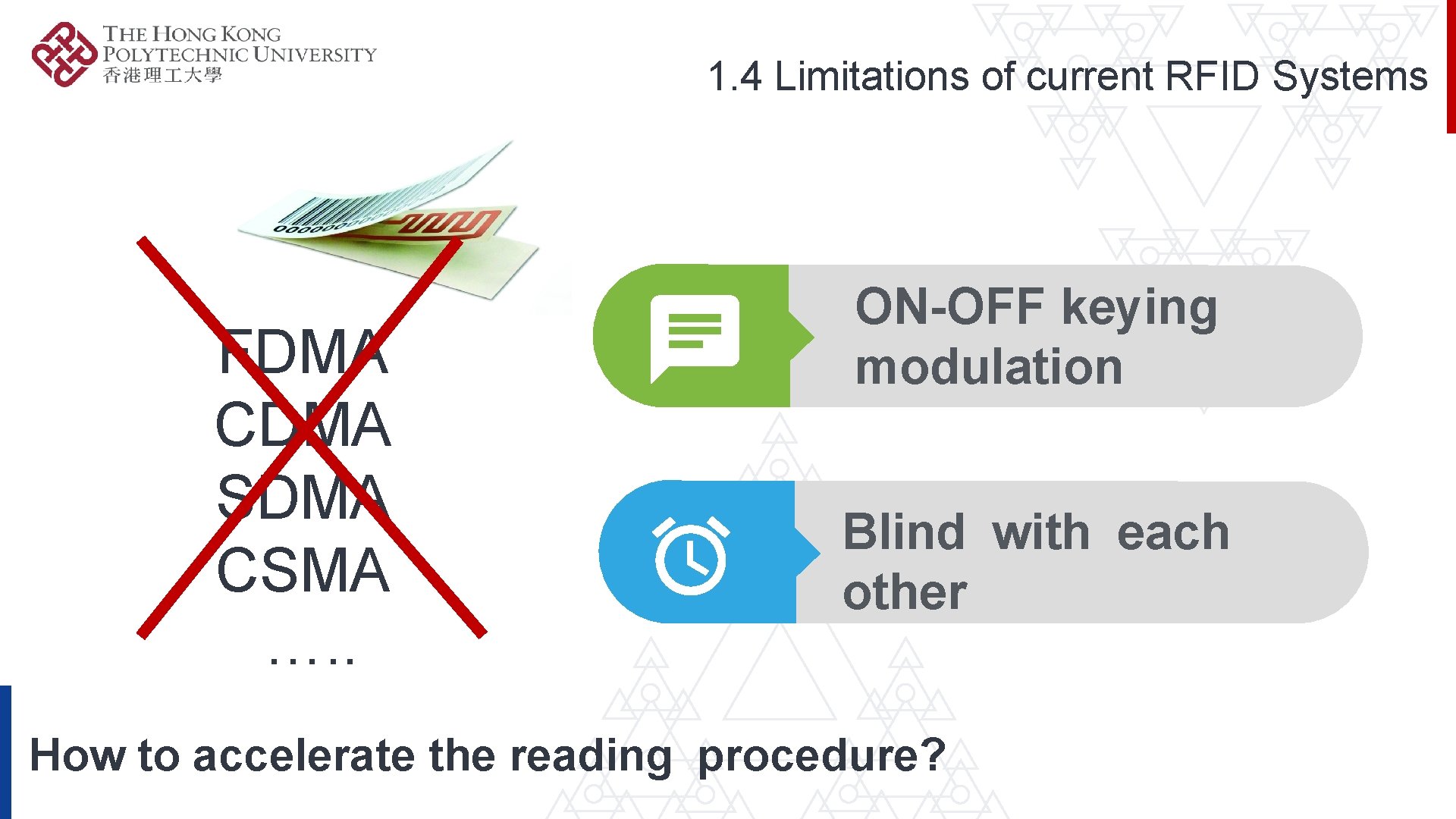
1. 4 Limitations of current RFID Systems FDMA CDMA SDMA CSMA …. . ON-OFF keying modulation Blind with each other How to accelerate the reading procedure?

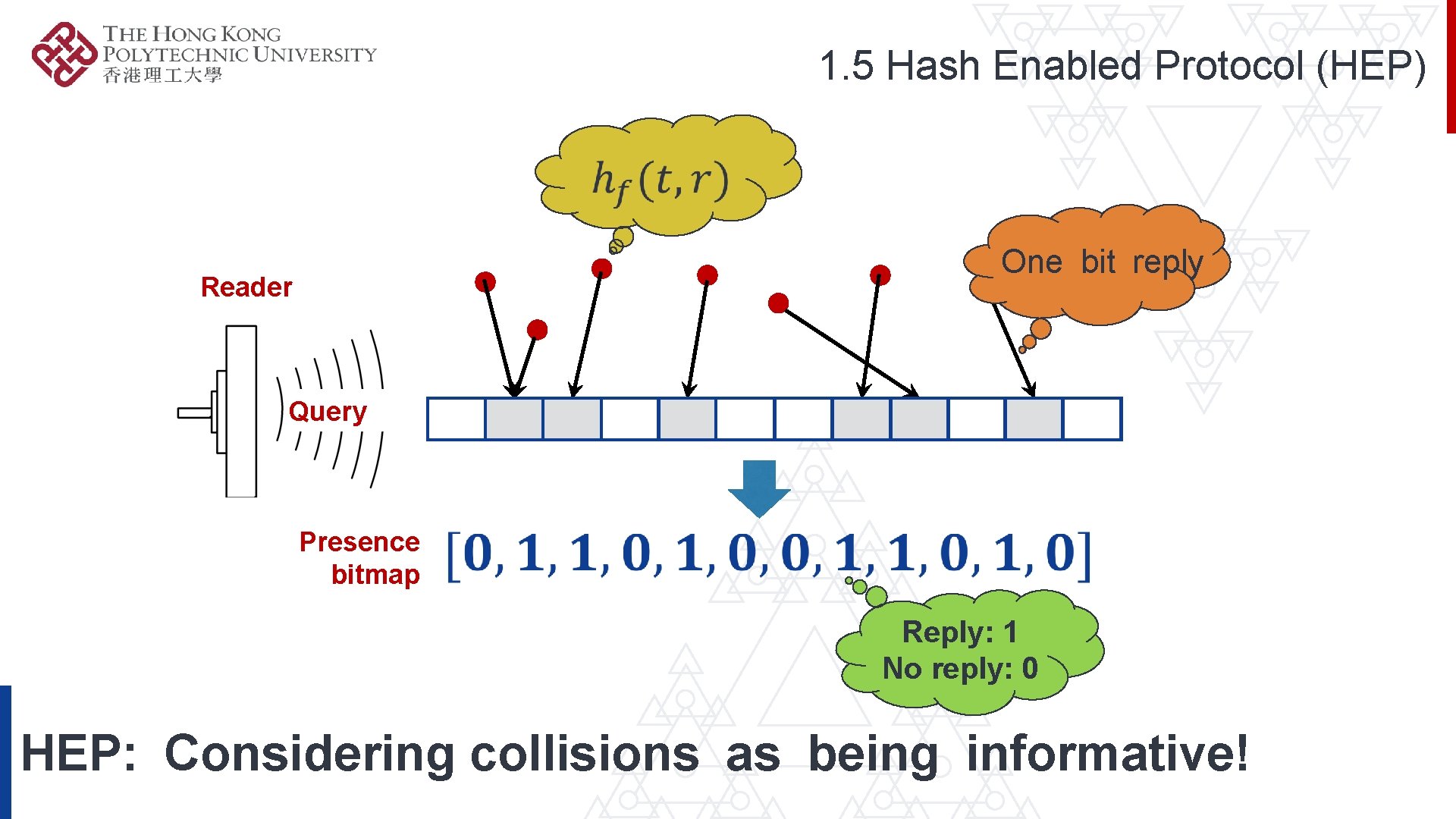
1. 5 Hash Enabled Protocol (HEP) One bit reply Reader Query Presence bitmap Reply: 1 No reply: 0 HEP: Considering collisions as being informative!

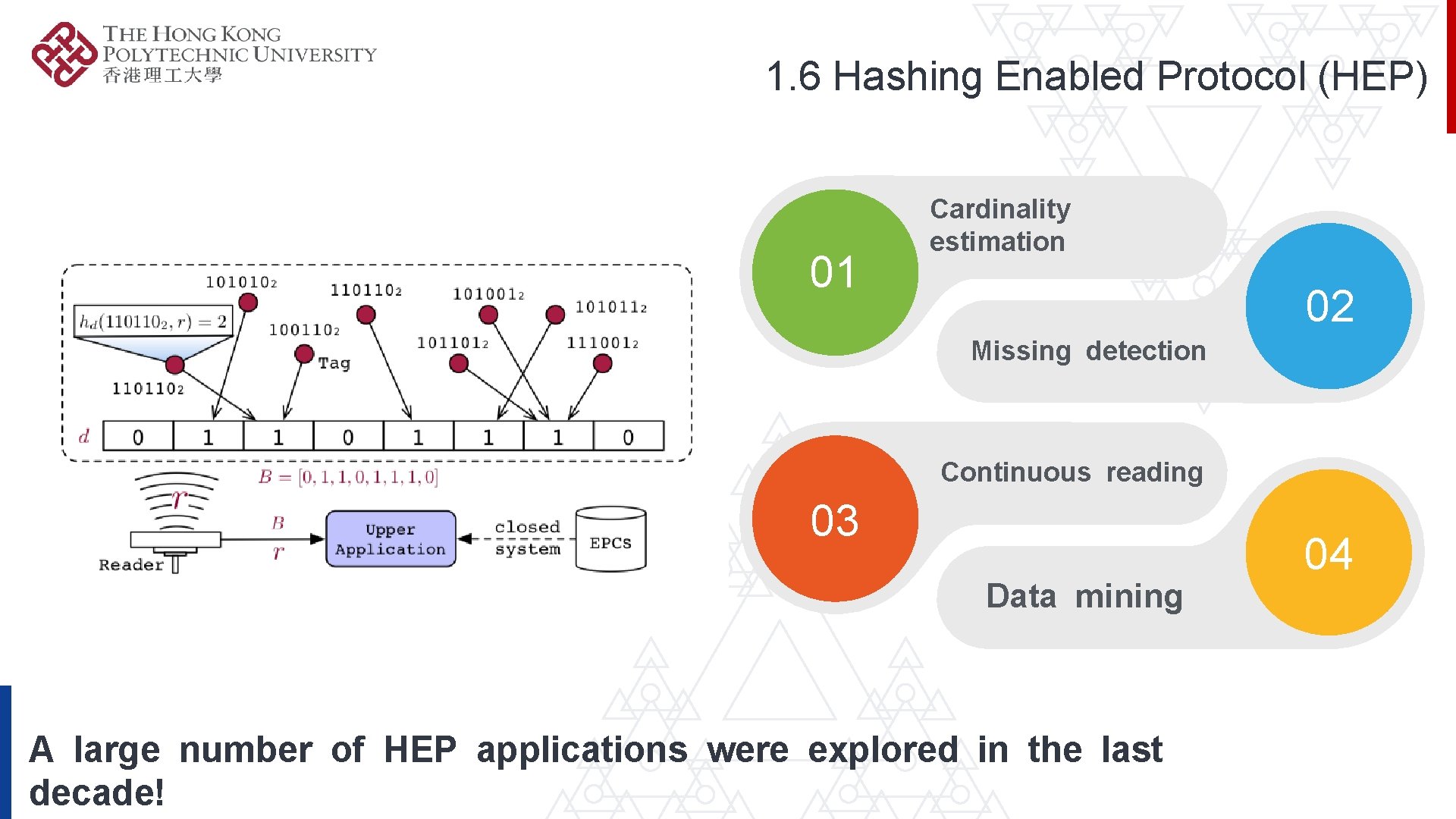
1. 6 Hashing Enabled Protocol (HEP) 01 Cardinality estimation 02 Missing detection Continuous reading 03 Data mining A large number of HEP applications were explored in the last decade! 04

1. 7 Hashing Enabled Protocol (HEP) Idealism Advantages Reality Overview of Hash Functions Performance boost 01 Privacy Preservation 02 After 10 years of enthusiastic discussion about the opportunities that HEPs provide, the reality is beginning to settle down: each tag requires a hash function.

1. 8 HEP: The-Art-Of-State The first HEP was proposed in 2007. HEP likes a 10 -year untouchable mirage in practice. 10 -YEAR MIRAGE OF HEP

2. Design of Hash Primitives over Gen 2 RFID System More info

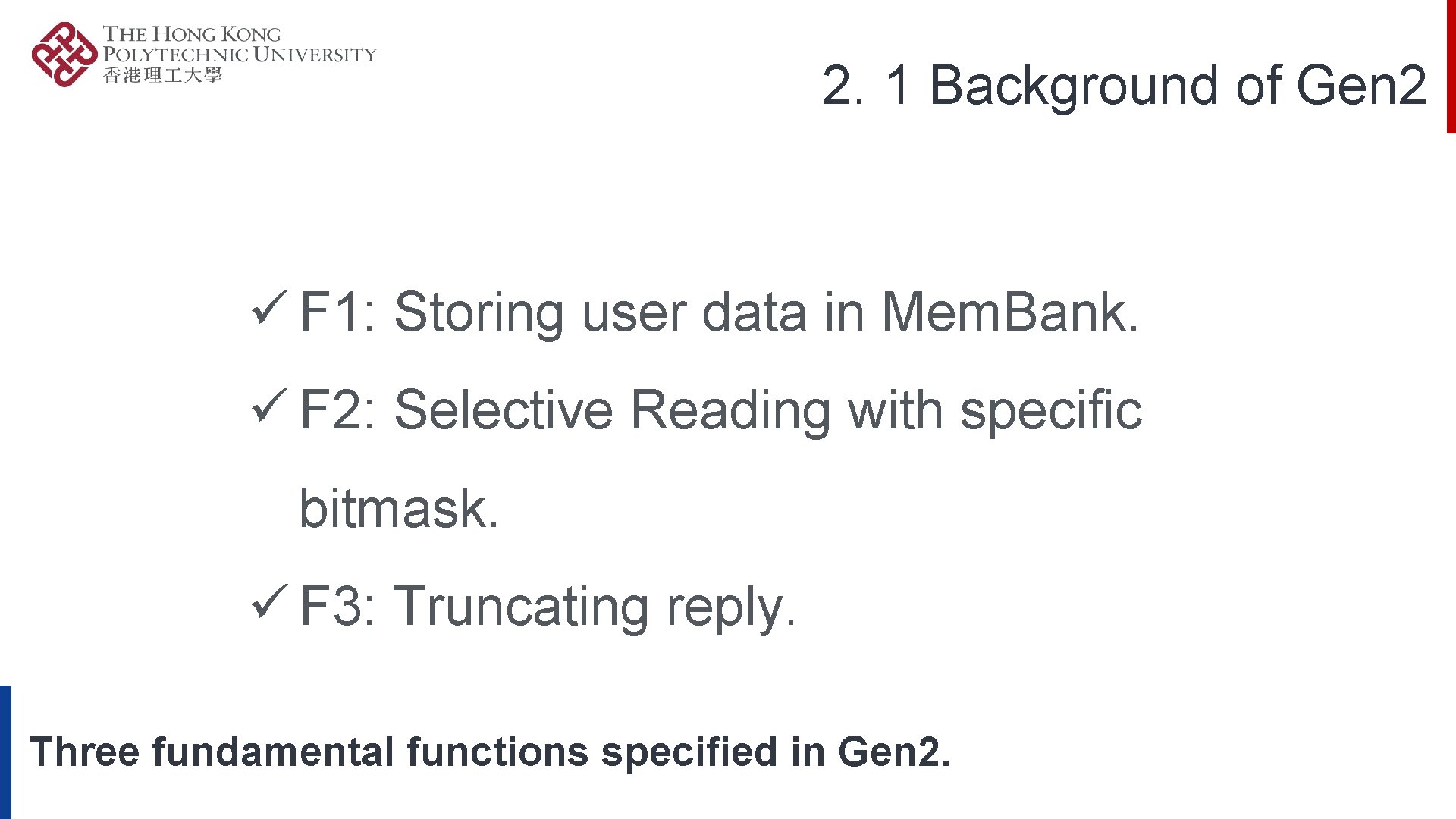
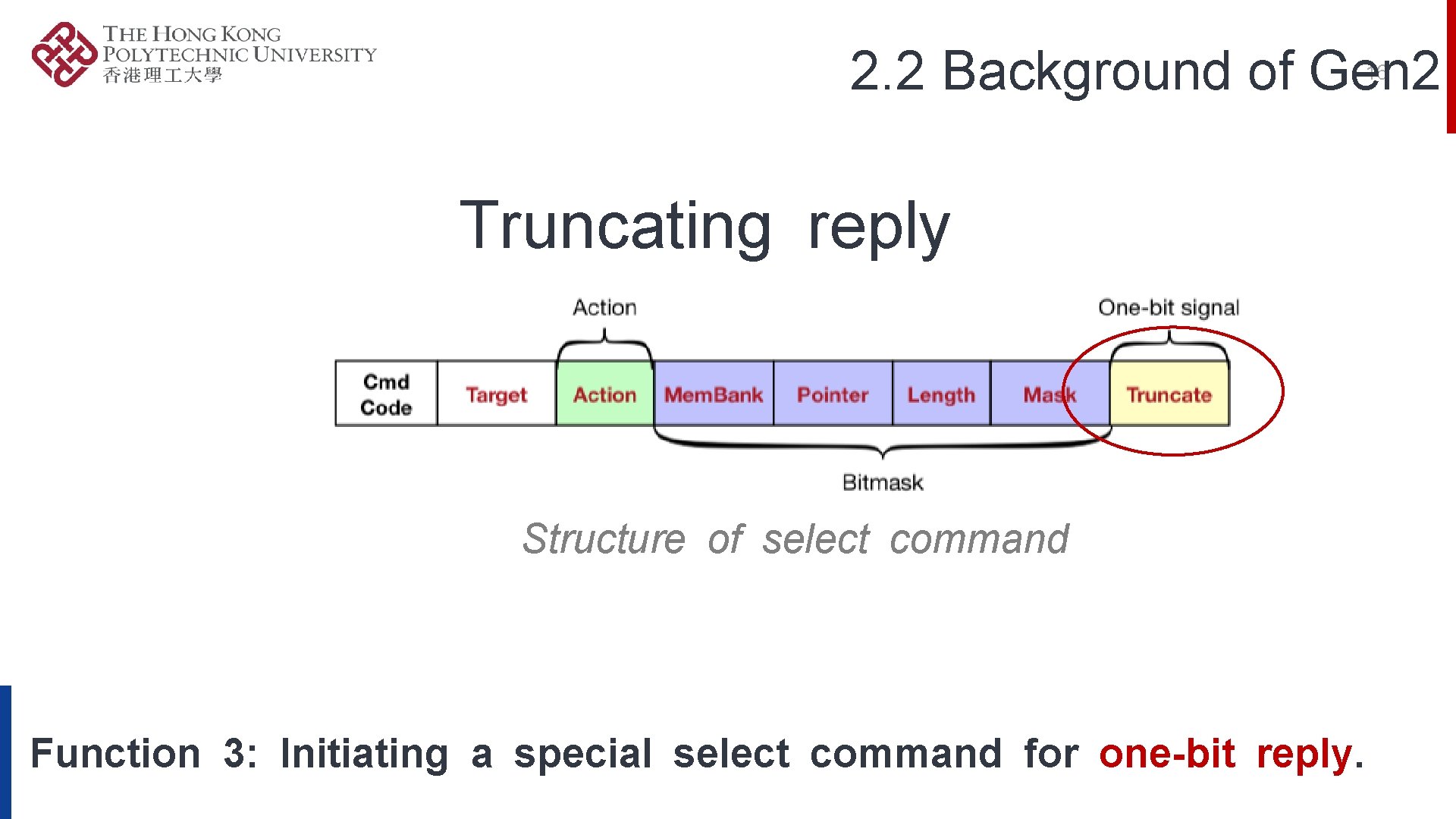
2. 1 Background of Gen 2 ü F 1: Storing user data in Mem. Bank. ü F 2: Selective Reading with specific bitmask. ü F 3: Truncating reply. Three fundamental functions specified in Gen 2.

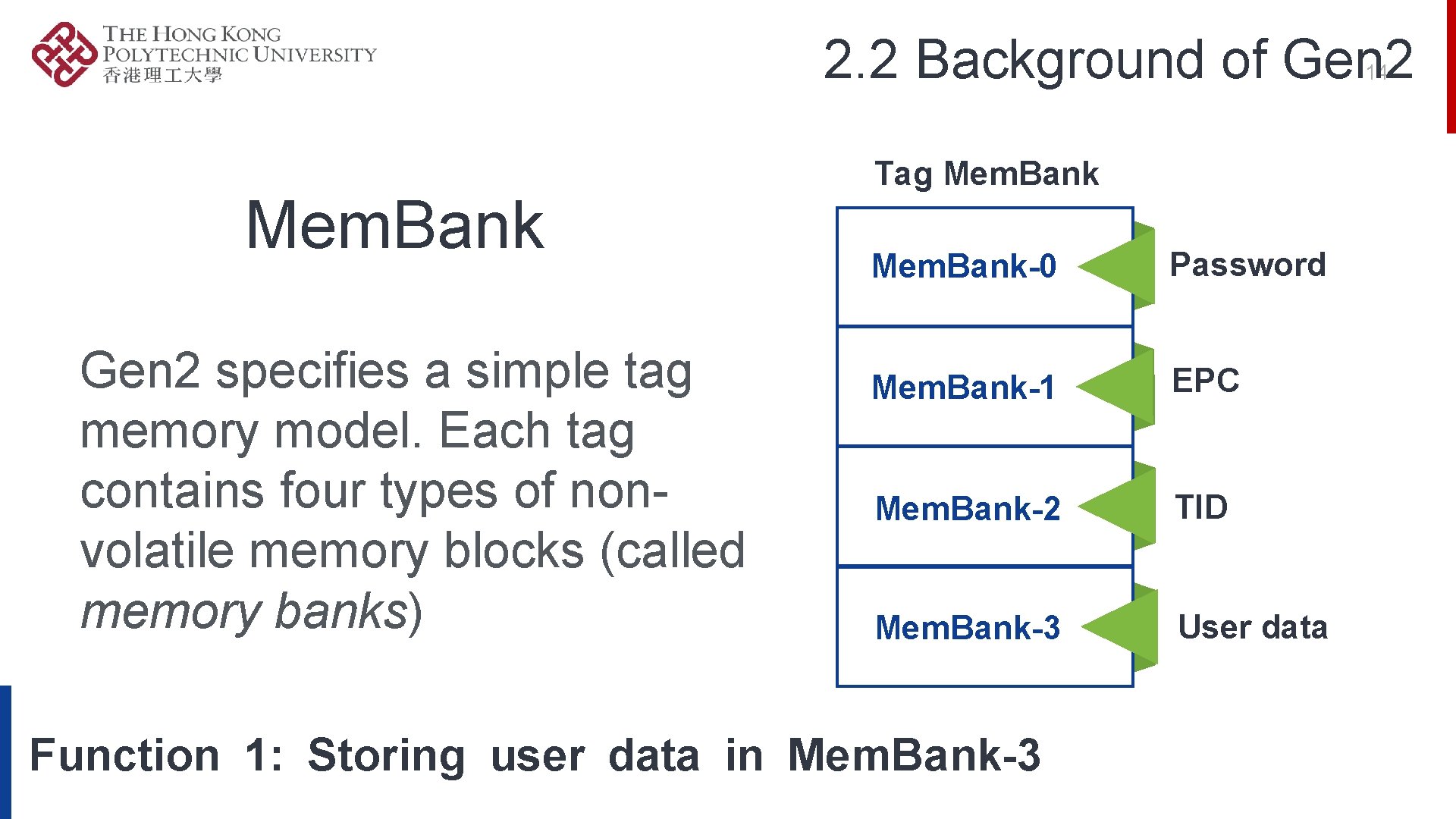
2. 2 Background of Gen 2 14 Mem. Bank Gen 2 specifies a simple tag memory model. Each tag contains four types of nonvolatile memory blocks (called memory banks) Tag Mem. Bank-0 Password Mem. Bank-1 EPC Mem. Bank-2 TID Mem. Bank-3 User data Function 1: Storing user data in Mem. Bank-3

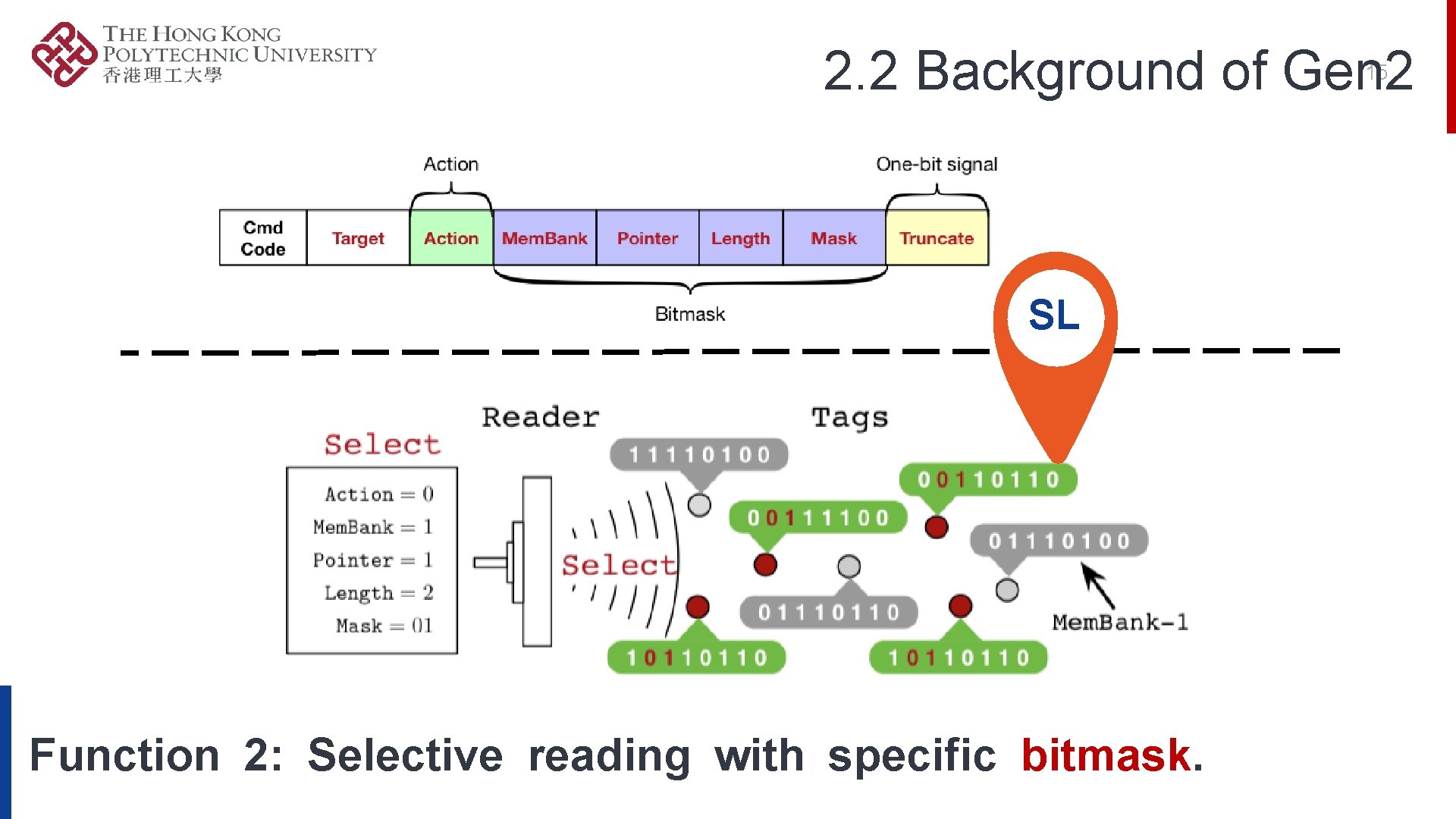
2. 2 Background of Gen 2 15 SL Function 2: Selective reading with specific bitmask.

2. 2 Background of Gen 2 16 Truncating reply Structure of select command Function 3: Initiating a special select command for one-bit reply.

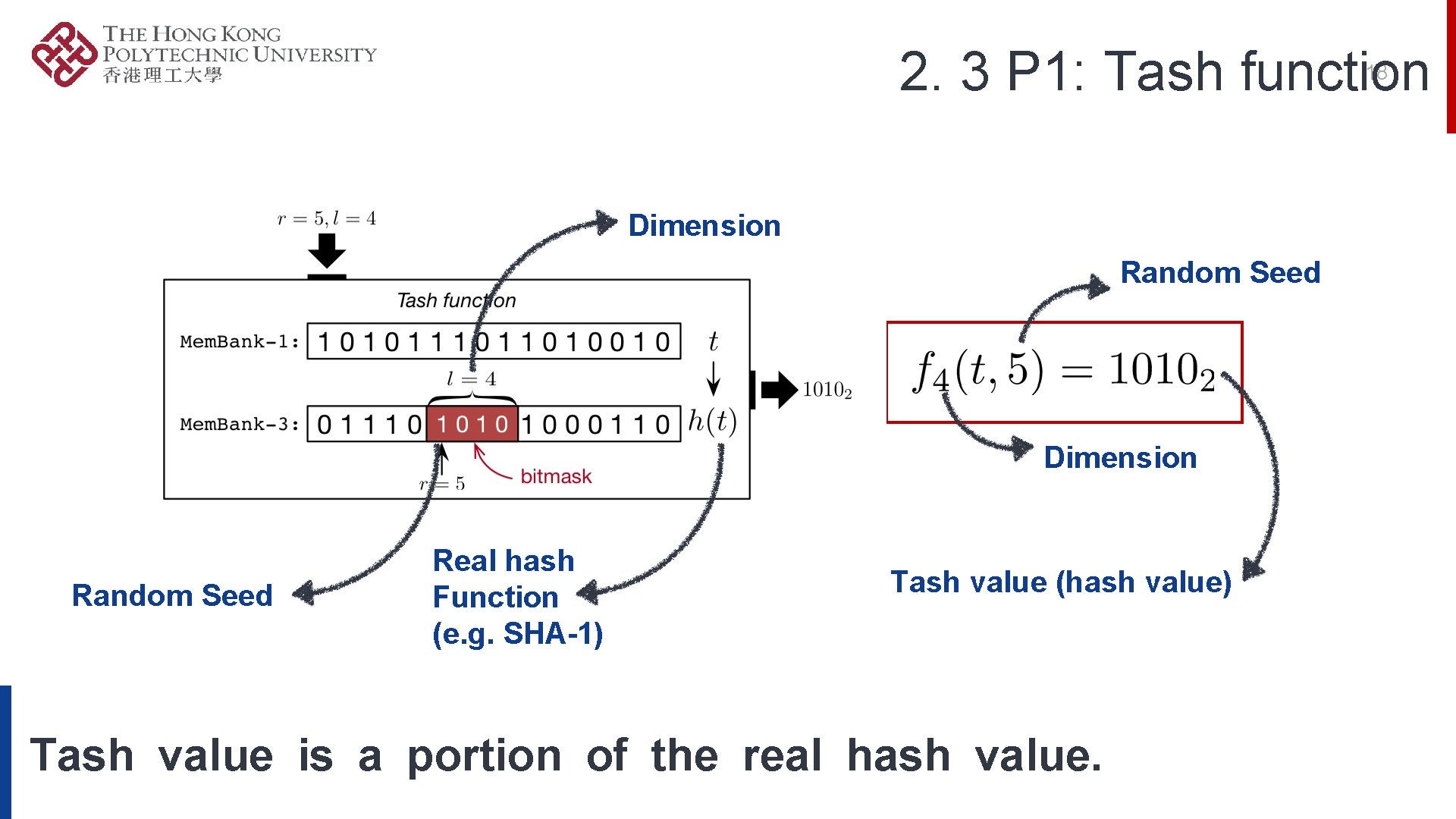
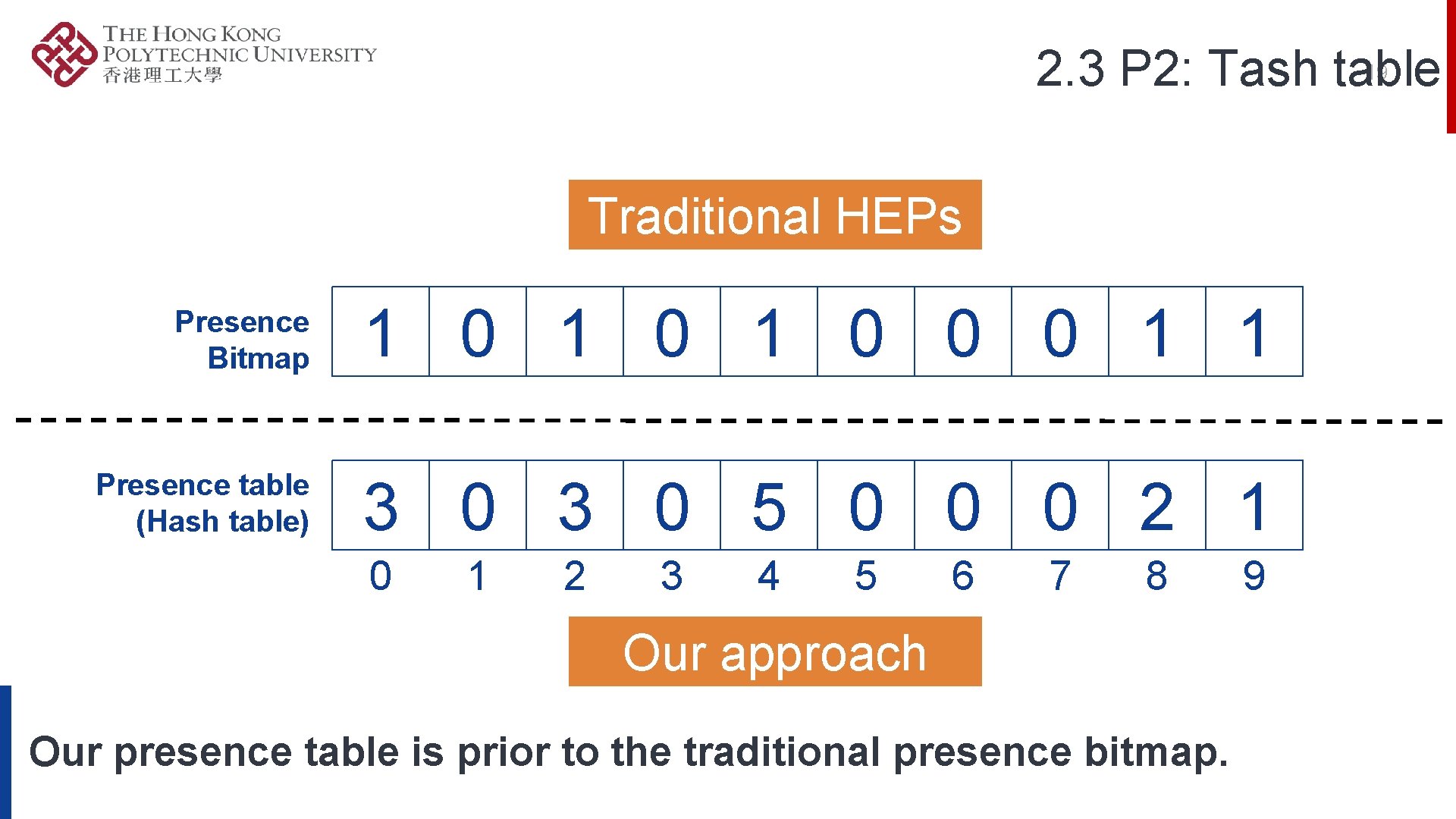
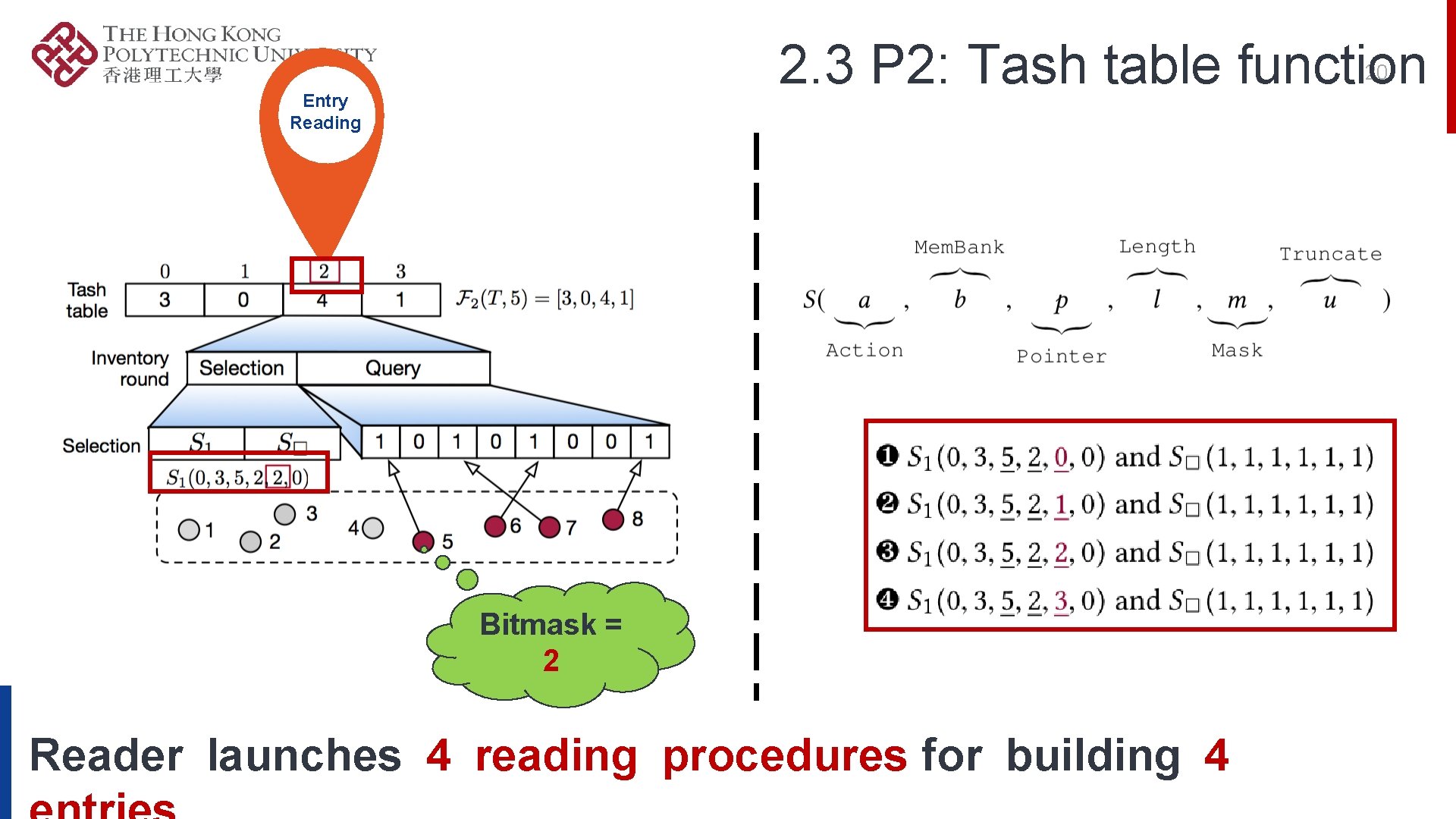
2. 1 Definition of Hash Primitives P 2: TASH TABLE FUNCTION (HASH TABLE FUNCTION) P 1: TASH FUNCTION (HASH FUNCTION) P 3: TASH OPERATOR Hash Primitives: Tash function, Tash table function, Tash operator

2. 3 P 1: Tash function 18 Dimension Random Seed Real hash Function (e. g. SHA-1) Tash value (hash value) Tash value is a portion of the real hash value.

19 2. 3 P 2: Tash table Traditional HEPs Presence Bitmap 1 0 1 0 0 0 1 1 Presence table (Hash table) 3 0 5 0 0 0 2 1 0 1 2 3 4 5 6 7 8 Our approach Our presence table is prior to the traditional presence bitmap. 9

2. 3 P 2: Tash table function 20 Entry Reading Bitmask = 2 Reader launches 4 reading procedures for building 4

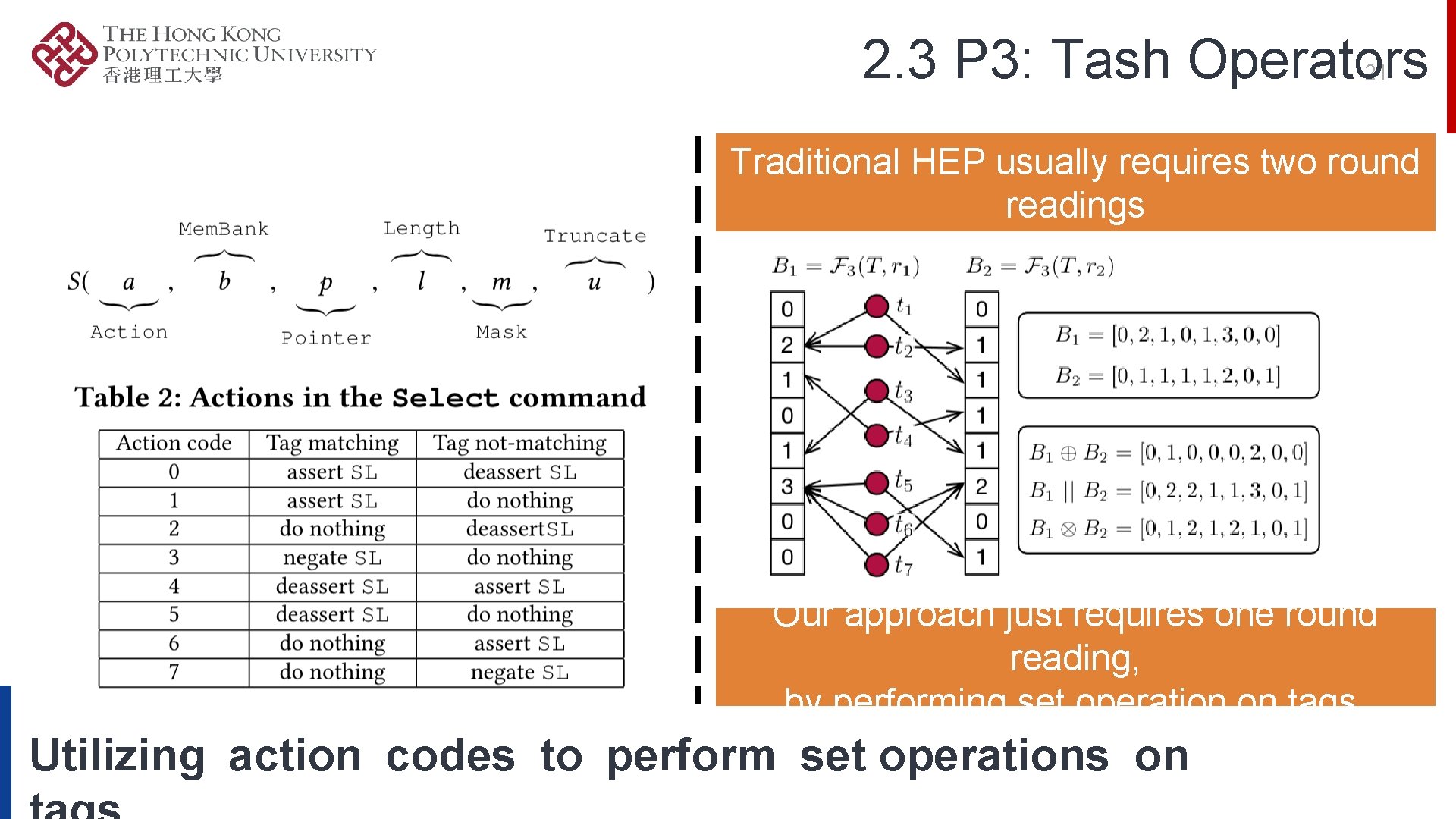
2. 3 P 3: Tash Operators 21 Traditional HEP usually requires two round readings Our approach just requires one round reading, by performing set operation on tags. Utilizing action codes to perform set operations on

3. Implementation & Evaluation More info

3. 1 Implementation 23 Gen 2 v. s. LLRP

24 3. 2 Implementation READER IMPINJ R 420 READER. TAG ALIEN 2 × 2 INLAY SOFTWARE EPCGLOBAL LLRP JAVA DIRECTIONAL ANTENNA ALIEN SQUIGGLE INLAY Completely using COTS RFID devices

25 3. 3 Experimental Setup Totally using COTS RFID devices

26 3. 4 Compatibility Investigation Current COTS Gen 2 System well supports functions we require.

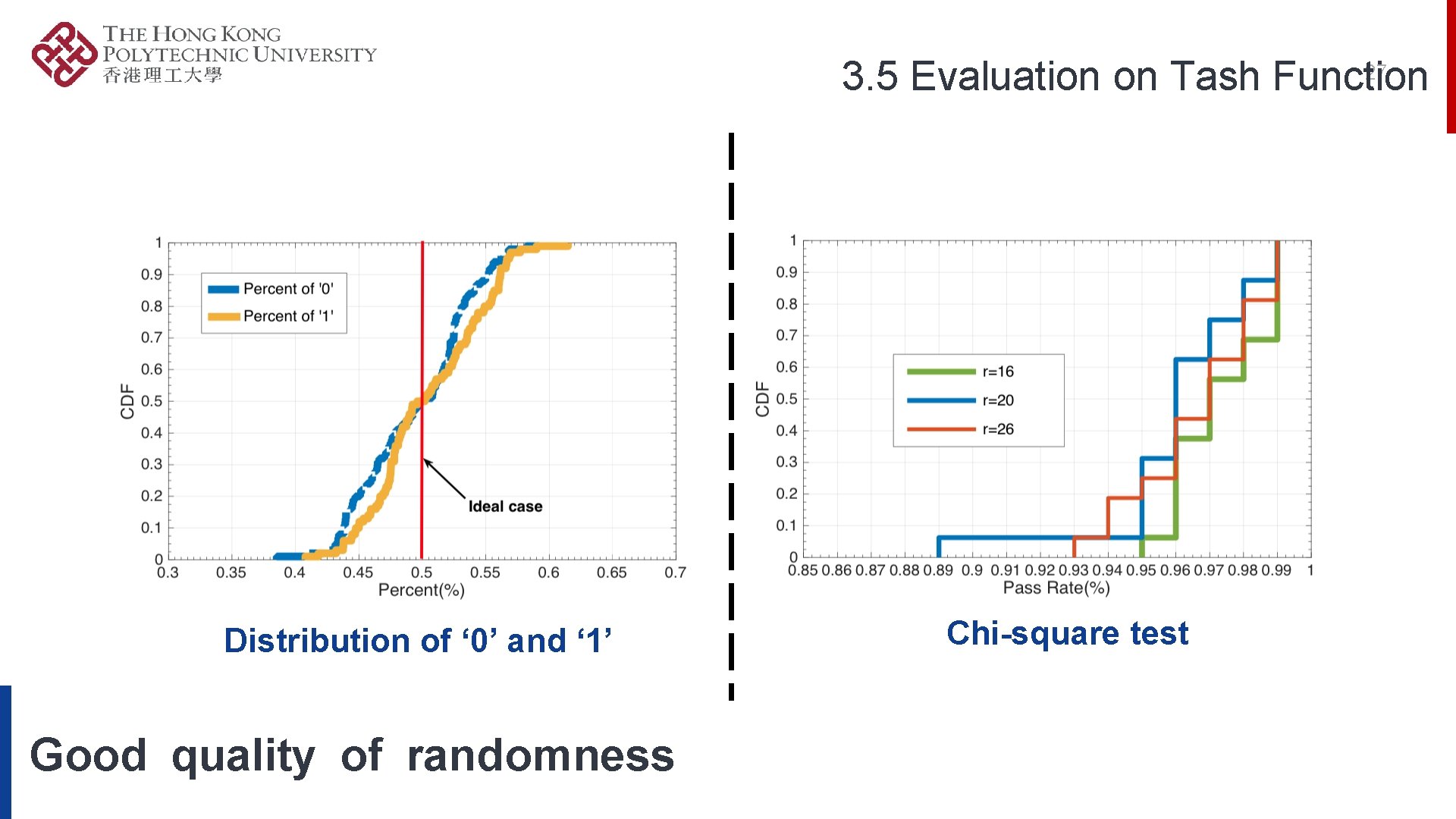
27 3. 5 Evaluation on Tash Function Distribution of ‘ 0’ and ‘ 1’ Good quality of randomness Chi-square test

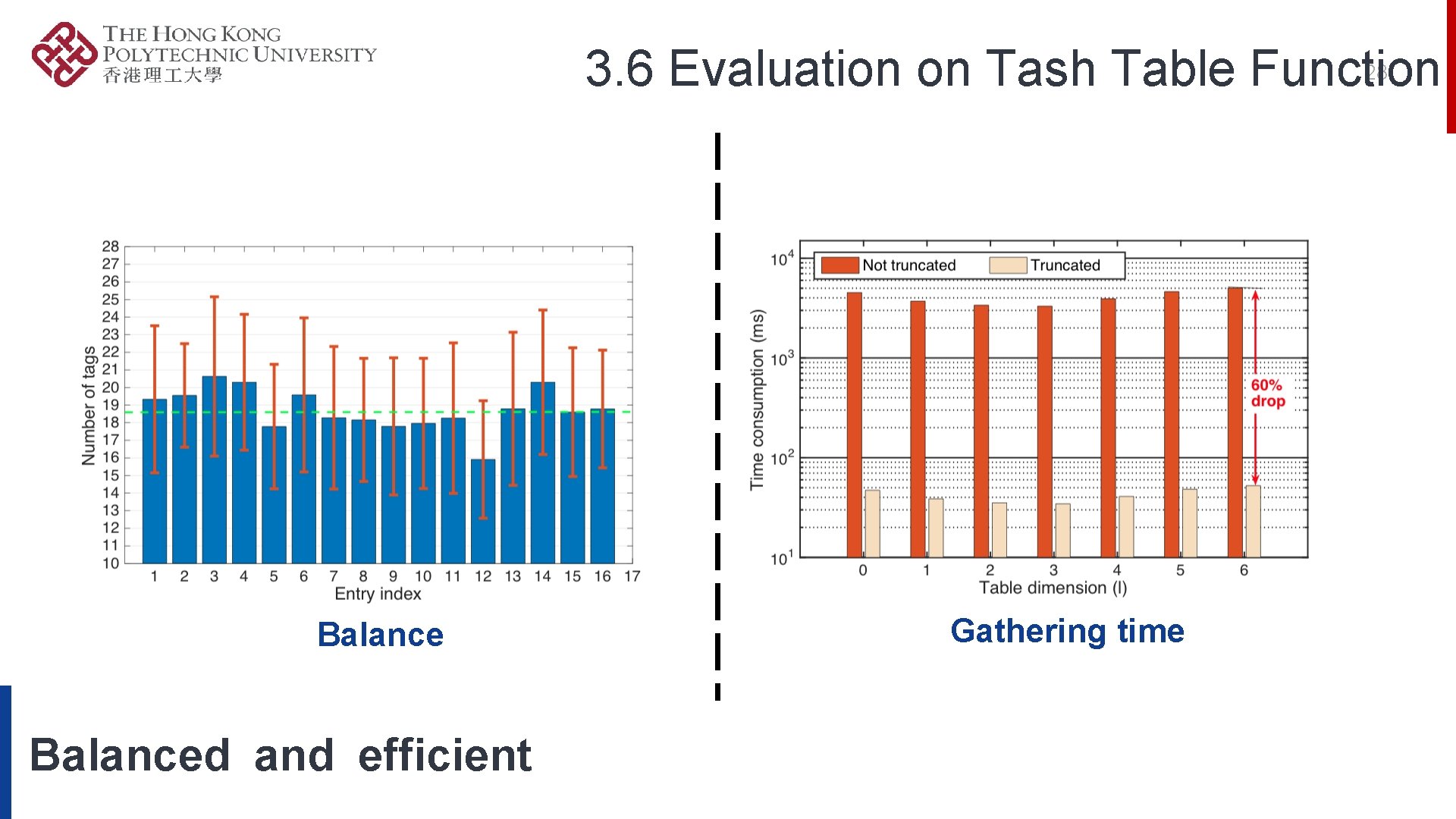
28 3. 6 Evaluation on Tash Table Function Balanced and efficient Gathering time

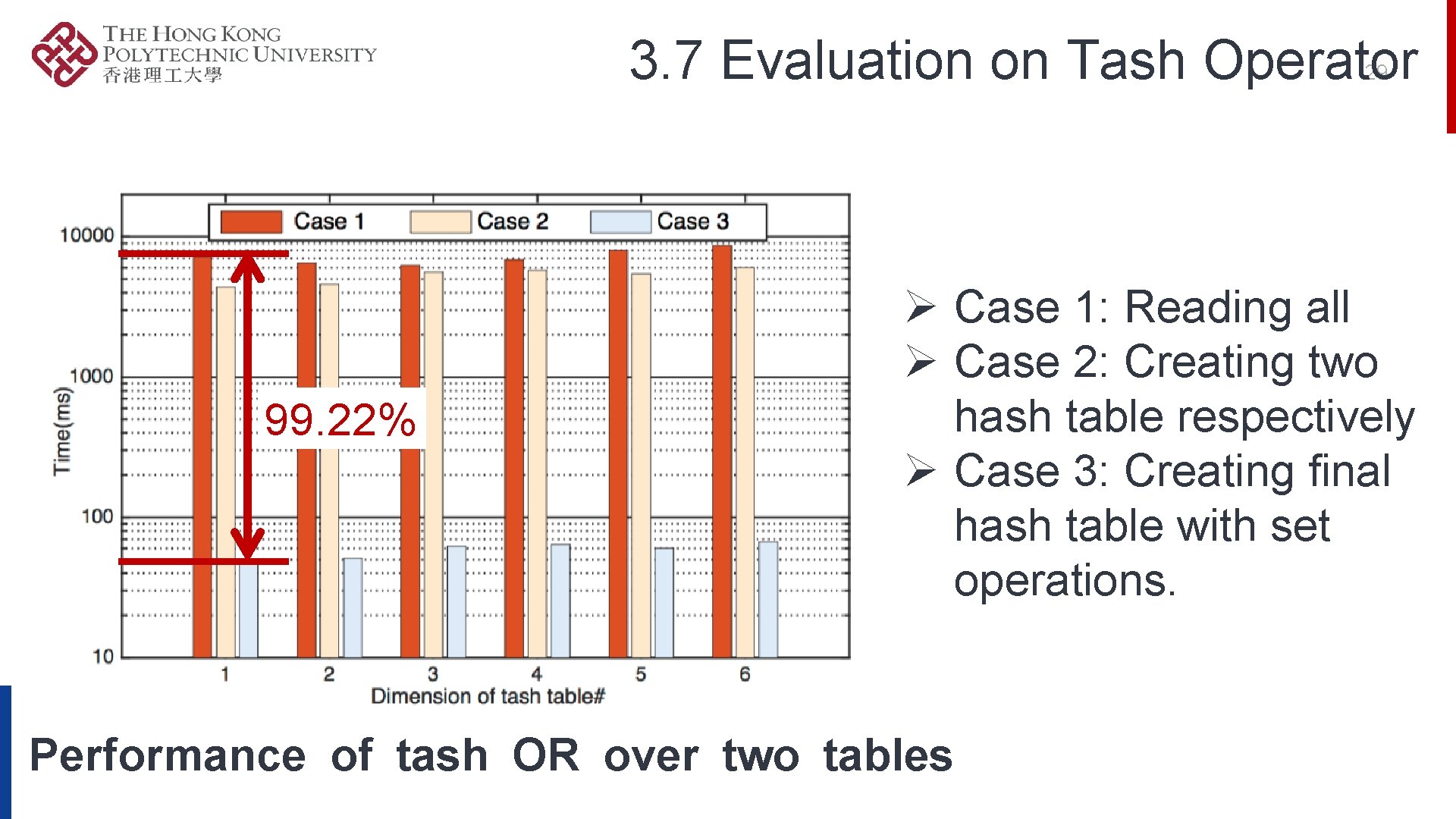
3. 7 Evaluation on Tash Operator 29 99. 22% Ø Case 1: Reading all Ø Case 2: Creating two hash table respectively Ø Case 3: Creating final hash table with set operations. Performance of tash OR over two tables

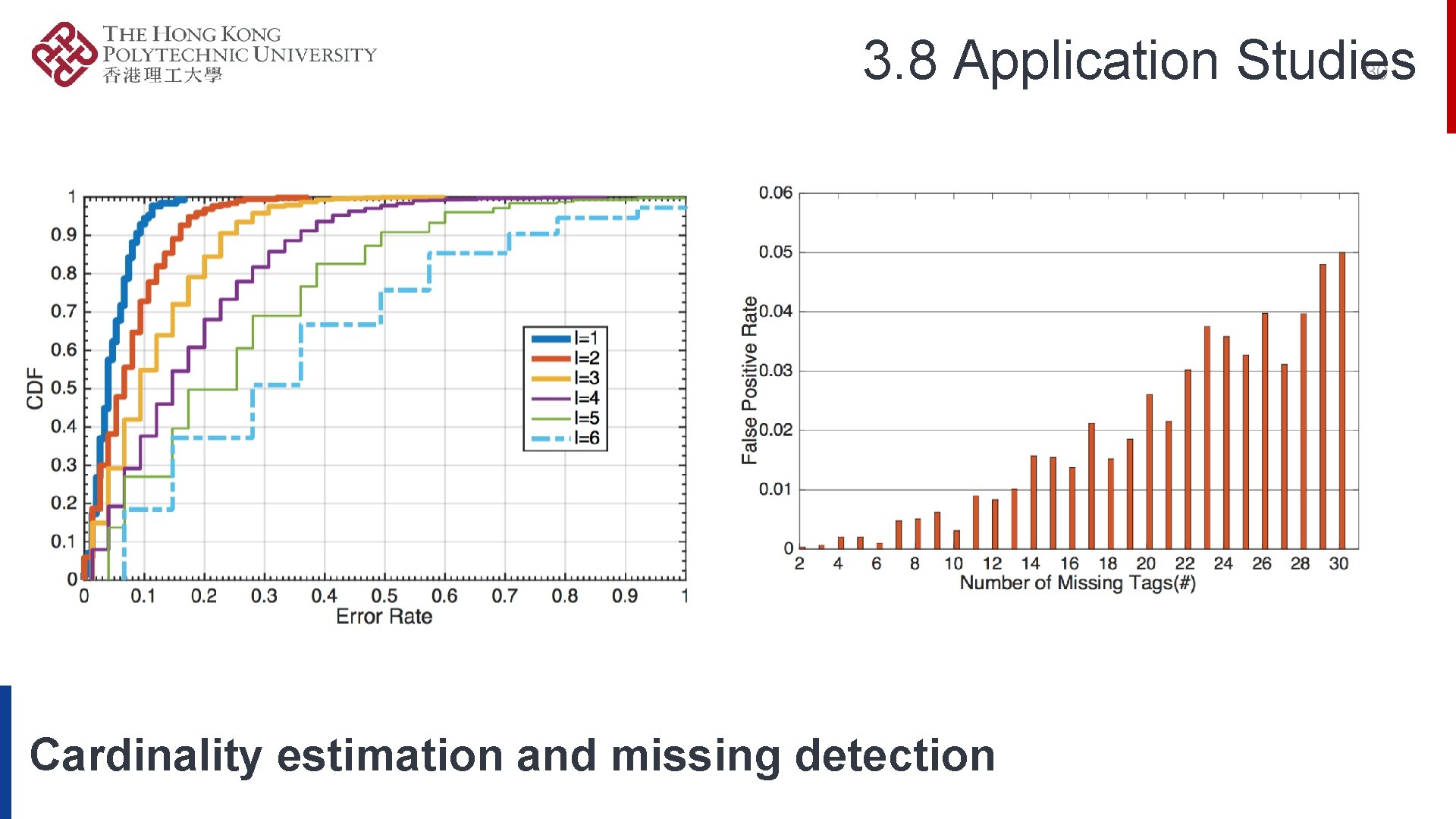
3. 8 Application Studies 30 Cardinality estimation and missing detection

Conclusion Ø We design a hash function (aka tash function) over existing COTS Gen 2 tags. function) over all tags in the scene. HEP Ø We design a hash table function (aka tash table Ø We design three tash operators to perform entry-wise set operations over multiple tash tables on tag in the physical layer, which offers a one-stop acquisition solution. REVIVING “HEPS” Tash

Thank You!