An Overview of Computer Security csci 5233 computer




















- Slides: 26

An Overview of Computer Security csci 5233 computer security & integrity 1

Outline n Components of computer security n Threats n Policies and mechanisms n The role of trust n Assurance n Operational Issues n Human Issues csci 5233 computer security & integrity 2

Status of security in computing n In terms of security, computing is very close to the wild west days. n Some computing professionals & managers do not even recognize the value of the resources they use or control. n In the event of a computing crime, some companies do not investigate or prosecute. csci 5233 computer security & integrity 3

Characteristics of Computer Intrusion A computing system: a collection of hardware, software, data, and people that an organization uses to do computing tasks n Any piece of the computing system can become the target of a computing crime. n The weakest point is the most serious vulnerability. n The principles of easiest penetration n csci 5233 computer security & integrity 4

Security Breaches - Terminology n Exposure – a form of possible loss or harm n Vulnerability – a weakness in the system Attack n Threats n – Human attacks, natural disasters, errors n Control – a protective measure n Assets – h/w, s/w, data csci 5233 computer security & integrity 5

Types of Security Breaches n Disclosure: unauthorized access to info – Snooping n Deception: acceptance of false data – Modification, spoofing, repudiation of origin, denial of receipt n Disruption: prevention of correct operation – Modification, man-in-the-middle attack n Usurpation: unauthorized control of some part of the system (usurp: take by force or without right) – Modification, spoofing, delay, denial of service csci 5233 computer security & integrity 6

Security Components n Confidentiality: The assets are accessible only by authorized parties. – Keeping data and resources hidden n Integrity: The assets are modified only by authorized parties, and only in authorized ways. – Data integrity (integrity) – Origin integrity (authentication) n Availability: Assets are accessible to authorized parties. – Enabling access to data and resources csci 5233 computer security & integrity 7

Computing System Vulnerabilities n Hardware vulnerabilities n Software vulnerabilities n Data vulnerabilities n Human vulnerabilities ? csci 5233 computer security & integrity 8

Software Vulnerabilities n Destroyed (deleted) software n Stolen (pirated) software n Altered (but still run) software – Logic bomb – Trojan horse – Virus – Trapdoor – Information leaks csci 5233 computer security & integrity 9

Data Security n The principle of adequate protection n Storage of encryption keys n Software versus hardware methods csci 5233 computer security & integrity 10

Other Exposed Assets n Storage media n Networks n Access n Key people csci 5233 computer security & integrity 11

People Involved in Computer Crimes n Amateurs n Crackers n Career Criminals csci 5233 computer security & integrity 12

Methods of Defense n Encryption n Software controls n Hardware controls n Policies n Physical controls csci 5233 computer security & integrity 13

Encryption n at the heart of all security methods n Confidentiality of data n Some protocols rely on encryption to ensure availability of resources. n Encryption does not solve all computer security problems. csci 5233 computer security & integrity 14

Software controls n Internal program controls n OS controls n Development controls n Software controls are usually the 1 st aspects of computer security that come to mind. csci 5233 computer security & integrity 15

Policies and Mechanisms n Policy says what is, and is not, allowed – This defines “security” for the site/system/etc. Mechanisms enforce policies n Mechanisms can be simple but effective n – Example: frequent changes of passwords n Composition of policies – If policies conflict, discrepancies may create security vulnerabilities n Legal and ethical controls – Gradually evolving and maturing csci 5233 computer security & integrity 16

Principle of Effectiveness n Controls must be used to be effective. – Efficient • Time, memory space, human activity, … – Easy to use – appropriate csci 5233 computer security & integrity 17

Overlapping Controls n Several different controls may apply to one potential exposure. H/w control + S/w control + Data control csci 5233 computer security & integrity 18

Goals of Security n Prevention – Prevent attackers from violating security policy n Detection – Detect attackers’ violation of security policy n Recovery – Stop attack, assess and repair damage – Continue to function correctly even if attack succeeds csci 5233 computer security & integrity 19

Trust and Assumptions n Underlie all aspects of security n Policies – Unambiguously partition system states – Correctly capture security requirements n Mechanisms – Assumed to enforce policy – Support mechanisms work correctly csci 5233 computer security & integrity 20

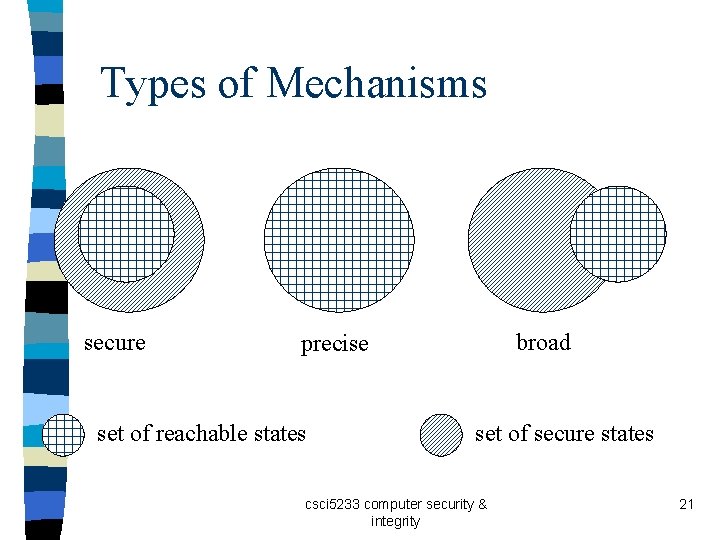
Types of Mechanisms secure broad precise set of reachable states set of secure states csci 5233 computer security & integrity 21

Assurance n Specification – Requirements analysis – Statement of desired functionality n Design – How system will meet specification n Implementation – Programs/systems that carry out design csci 5233 computer security & integrity 22

Operational Issues n Cost-Benefit Analysis – Is it cheaper to prevent or to recover? n Risk Analysis – Should we protect something? – How much should we protect this thing? n Laws and Customs – Are desired security measures illegal? – Will people do them? csci 5233 computer security & integrity 23

Human Issues n Organizational Problems – Power and responsibility – Financial benefits n People problems – Outsiders and insiders – Social engineering csci 5233 computer security & integrity 24

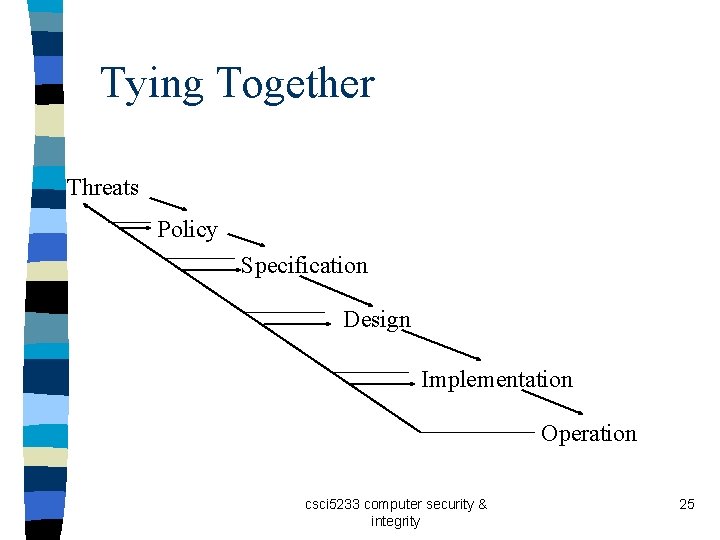
Tying Together Threats Policy Specification Design Implementation Operation csci 5233 computer security & integrity 25

Key Points n Policy defines security, and mechanisms enforce security – Confidentiality – Integrity – Availability n Trust and knowing assumptions n Importance of assurance n The human factor csci 5233 computer security & integrity 26