An Overview of Biometrics Dr Charles C Tappert
An Overview of Biometrics Dr. Charles C. Tappert Seidenberg School of CSIS, Pace University http: //csis. pace. edu/~ctappert/ SUBTITLE 2015 Gen. Cybersecurity Workshop
Biometrics Information Sources Most of the images and material contained here are from: Guide to Biometrics Bolle, et al. , Springer 2004 And our conference, journal, and book publications, see http: //www. csis. pace. edu/~ctappert/tappe rt/pubs. htm 2015 Gen. Cybersecurity Workshop
What is Biometrics? The science of identifying, or verifying the identity of, a person based on physiological or behavioral characteristics/traits Physical traits Fingerprint, Behavioral Face, Iris traits Signature/handwriting, Voice Keyboard and mouse input Websites and videos http: //www. biometrics. gov/ Biometric Security 2015 Gen. Cybersecurity Workshop
Technologies Used in Biometrics Pattern Recognition (Ph. D Course, JPR) Machine Learning Artificial Intelligence Data Mining Beer and Diapers Target Figured Out A Teen Girl Was Pregnant Before Her Father Did 2015 Gen. Cybersecurity Workshop
Pattern Recognition What is pattern recognition? The act of taking in raw data and taking an action based on the “category” of the pattern We gain an understanding and appreciation for pattern recognition in the real world – visual scenes, noises, etc. Human senses: sight, hearing, taste, smell, touch Recognition not an exact match like a password 2015 Gen. Cybersecurity Workshop
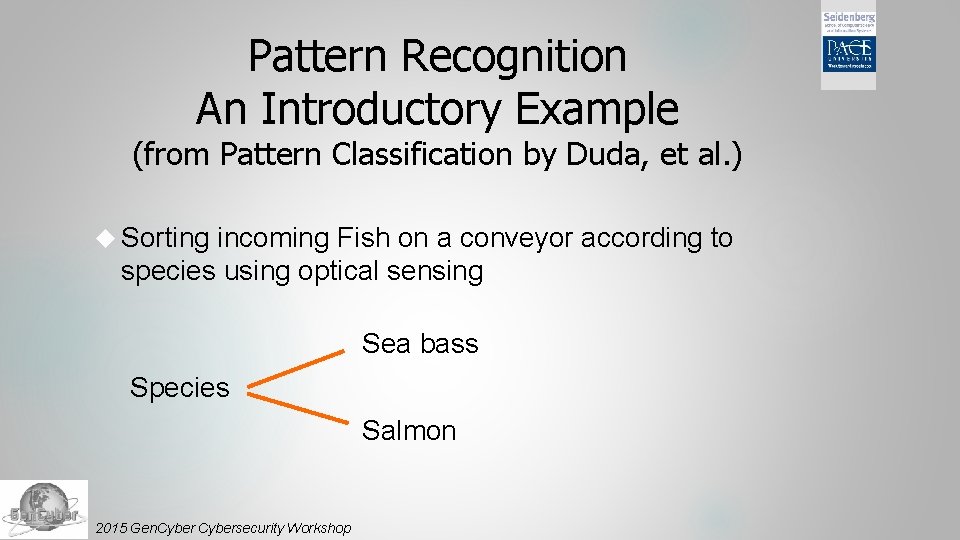
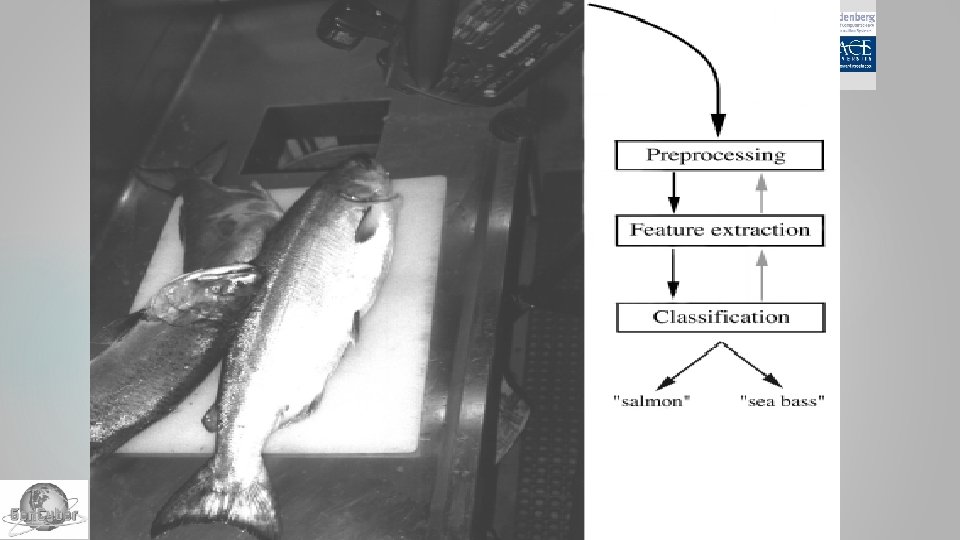
Pattern Recognition An Introductory Example (from Pattern Classification by Duda, et al. ) Sorting incoming Fish on a conveyor according to species using optical sensing Sea bass Species Salmon 2015 Gen. Cybersecurity Workshop
Pattern Recognition Problem Analysis Set up a camera and take some sample images to extract features Length Lightness Width Number and shape of fins Position of the mouth, etc… 2015 Gen. Cybersecurity Workshop
Pattern Recognition Pattern Classification System Preprocessing Segment (isolate) fishes from one another and from the background Feature Extraction Reduce the data by measuring certain features Classification Divide the feature space into decision regions 2015 Gen. Cybersecurity Workshop
2015 Gen. Cybersecurity Workshop

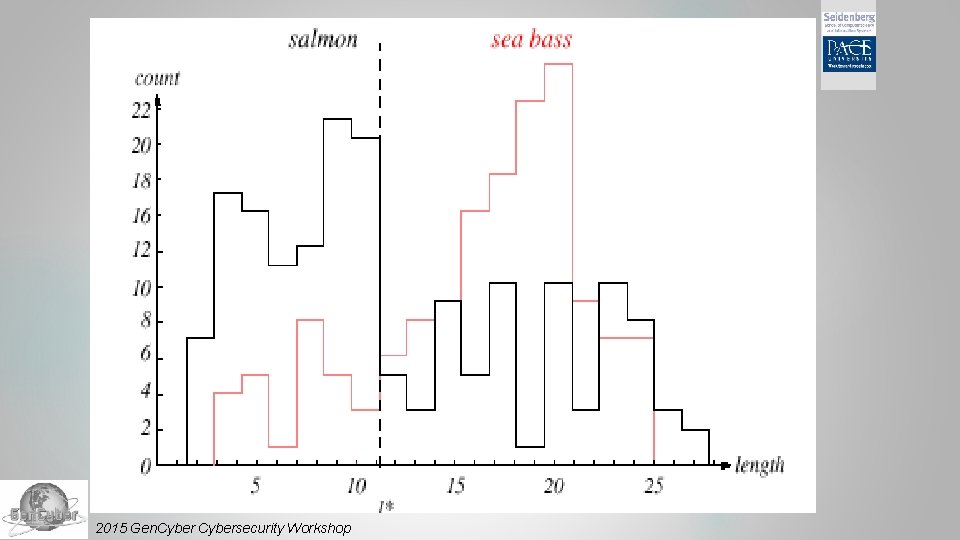
Pattern Recognition Classification Initially use the length of the fish as a possible feature for discrimination 2015 Gen. Cybersecurity Workshop
2015 Gen. Cybersecurity Workshop

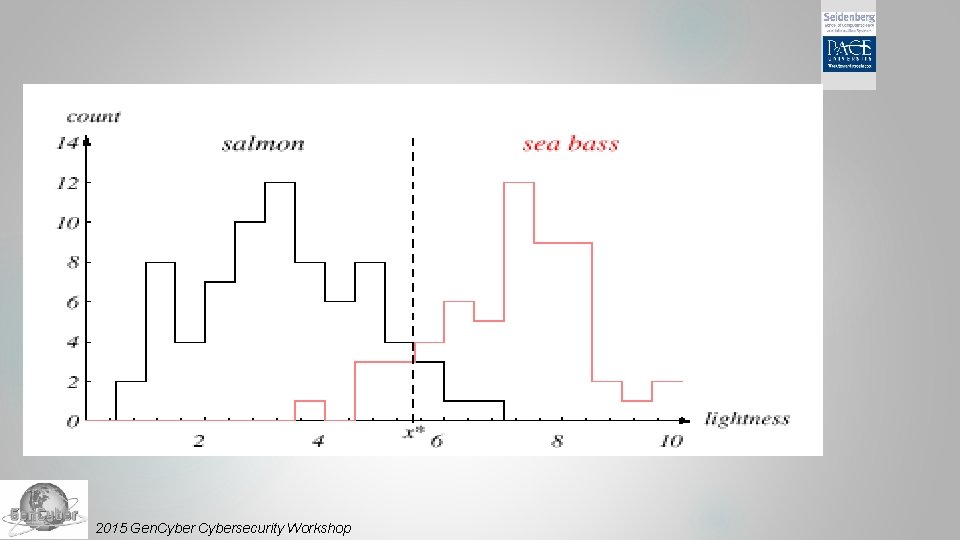
Pattern Recognition Feature Selection The length is a poor feature alone! Select the lightness as a possible feature 2015 Gen. Cybersecurity Workshop
2015 Gen. Cybersecurity Workshop
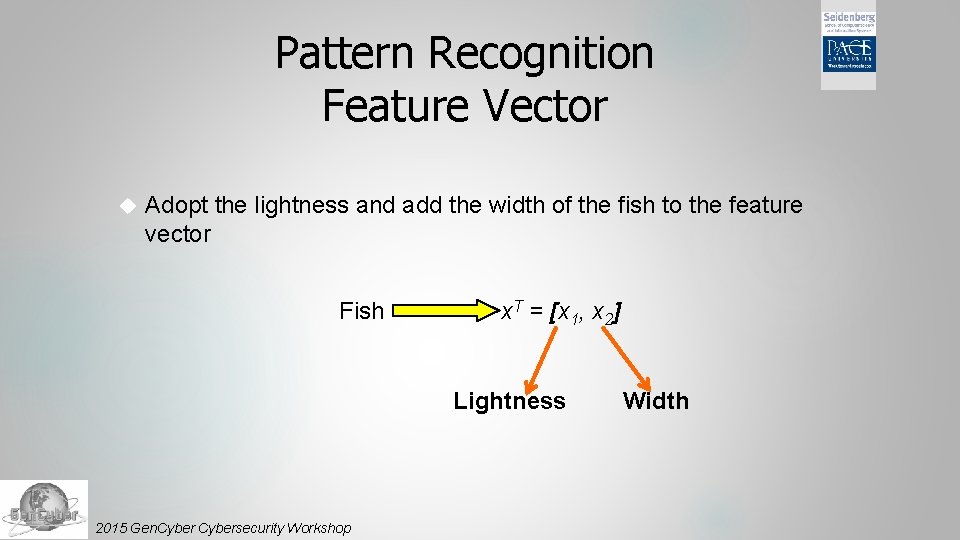
Pattern Recognition Feature Vector Adopt the lightness and add the width of the fish to the feature vector Fish x. T = [x 1, x 2] Lightness 2015 Gen. Cybersecurity Workshop Width
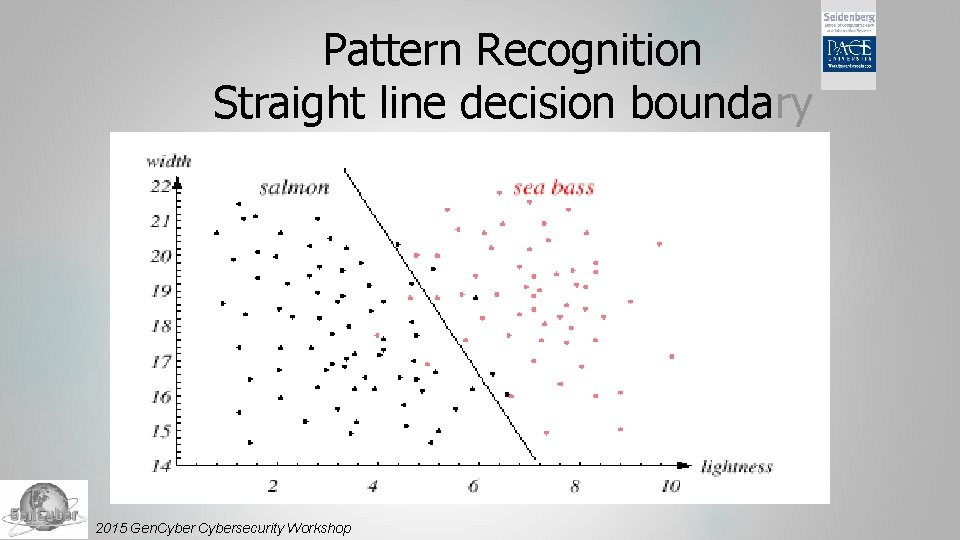
Pattern Recognition Straight line decision boundary 2015 Gen. Cybersecurity Workshop
Pattern Recognition Stages Sensing Use of a transducer (camera or microphone) PR system depends on the bandwidth, the resolution sensitivity distortion of the transducer What A Drone Can See From 17, 000 Feet Preprocessing Segmentation and grouping – patterns should be well separated and not overlap 2015 Gen. Cybersecurity Workshop
Pattern Recognition Stages (cont) Feature extraction Discriminative Ideally features invariant wrt translation, rotation, scale Classification Use the feature vector provided by a feature extractor to assign the object to a category Post Processing Exploit context-dependent information to improve performance 2015 Gen. Cybersecurity Workshop

Pattern Recognition Post Processing – for example, OCR The following sentence has many spelling errors. Right click on a word to get suggested correct spelling choices. We cant allign teh wonds corektly in htis sentance. On right clicking, most of correct spellings of the words are listed as first choice. Now, type the sentence above with the spelling errors into Microsoft Word. Many of the misspelled words are almost instantaneously autocorrected. 2015 Gen. Cybersecurity Workshop

Traditional Modes of Person Authentication Possessions Keys, – what you have passports, smartcards, etc. Knowledge Secret – what you know information: passwords, etc. Biometrics – what you are/do Characteristics of the human body and human actions that differentiate people from each other 2015 Gen. Cybersecurity Workshop
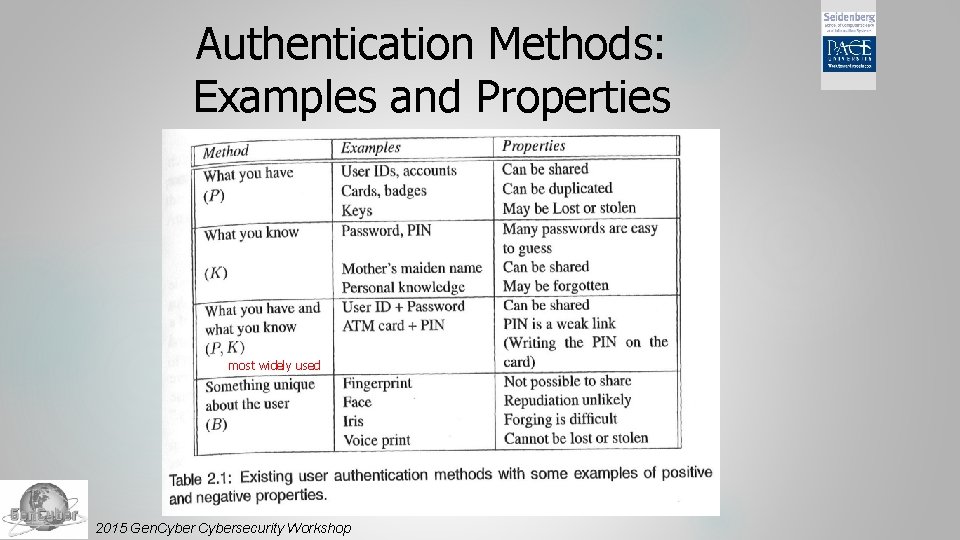
Authentication Methods: Examples and Properties most widely used 2015 Gen. Cybersecurity Workshop
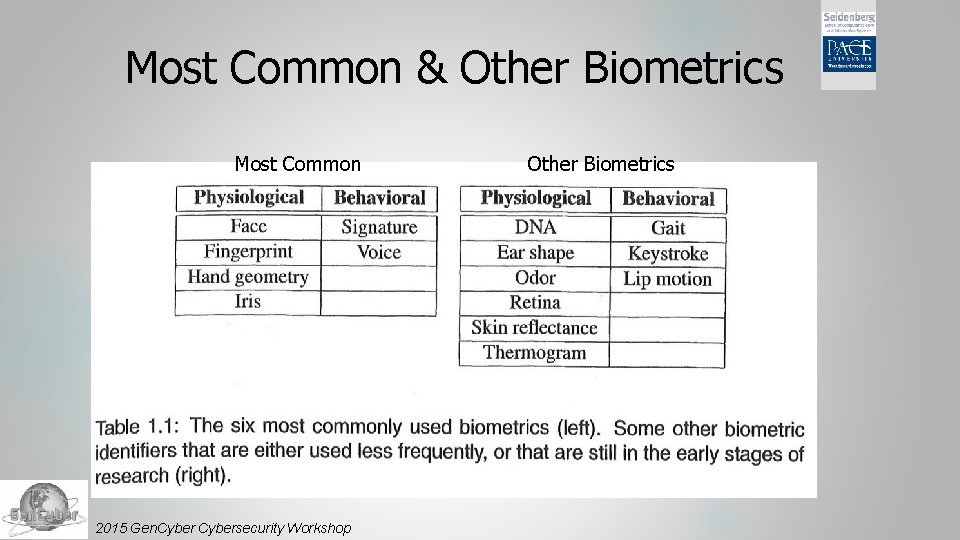
Most Common & Other Biometrics Most Common 2015 Gen. Cybersecurity Workshop Other Biometrics
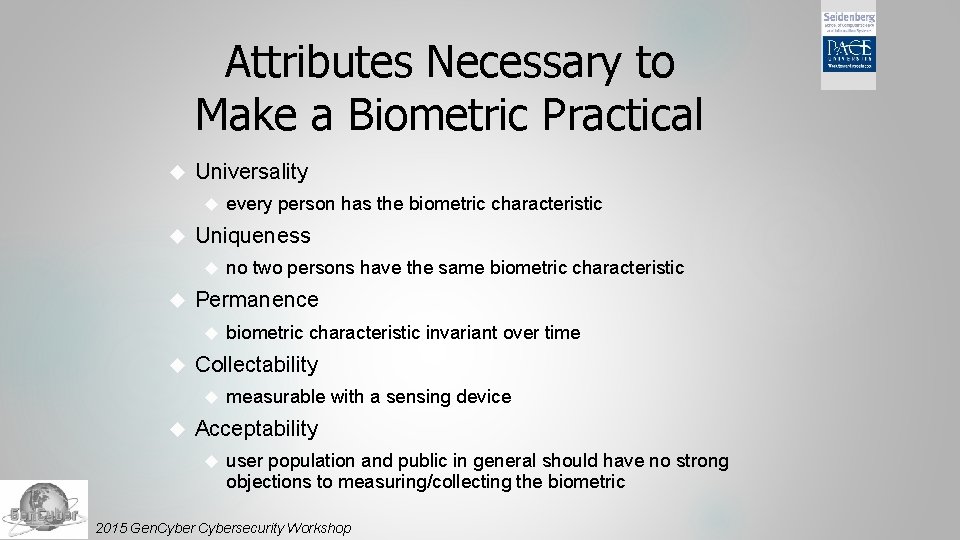
Attributes Necessary to Make a Biometric Practical Universality Uniqueness biometric characteristic invariant over time Collectability no two persons have the same biometric characteristic Permanence every person has the biometric characteristic measurable with a sensing device Acceptability user population and public in general should have no strong objections to measuring/collecting the biometric 2015 Gen. Cybersecurity Workshop
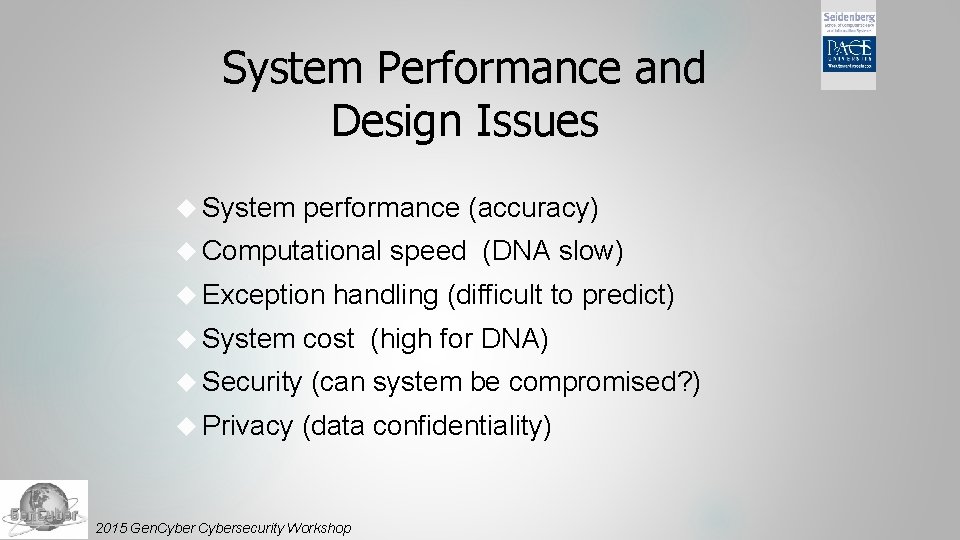
System Performance and Design Issues System performance (accuracy) Computational Exception System handling (difficult to predict) cost (high for DNA) Security Privacy speed (DNA slow) (can system be compromised? ) (data confidentiality) 2015 Gen. Cybersecurity Workshop
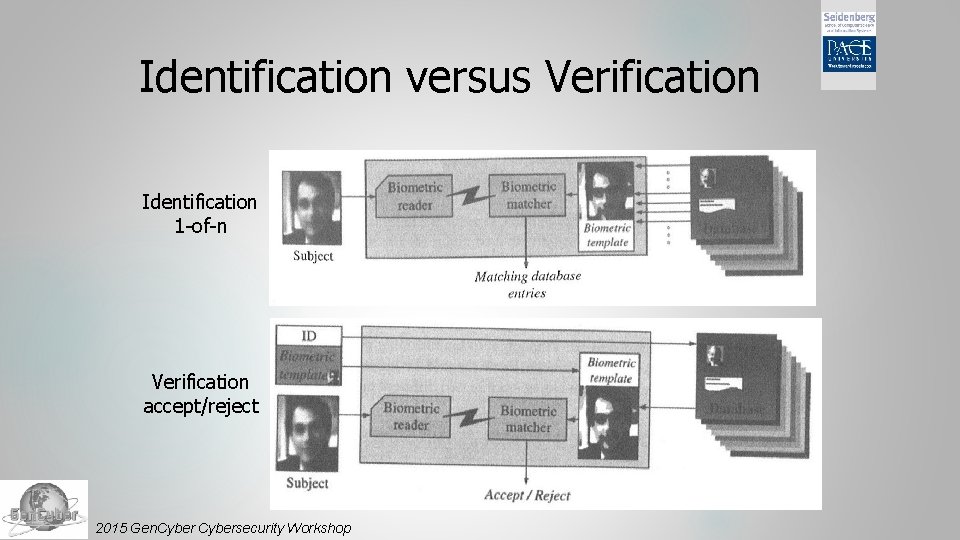
Identification versus Verification Identification 1 -of-n Verification accept/reject 2015 Gen. Cybersecurity Workshop
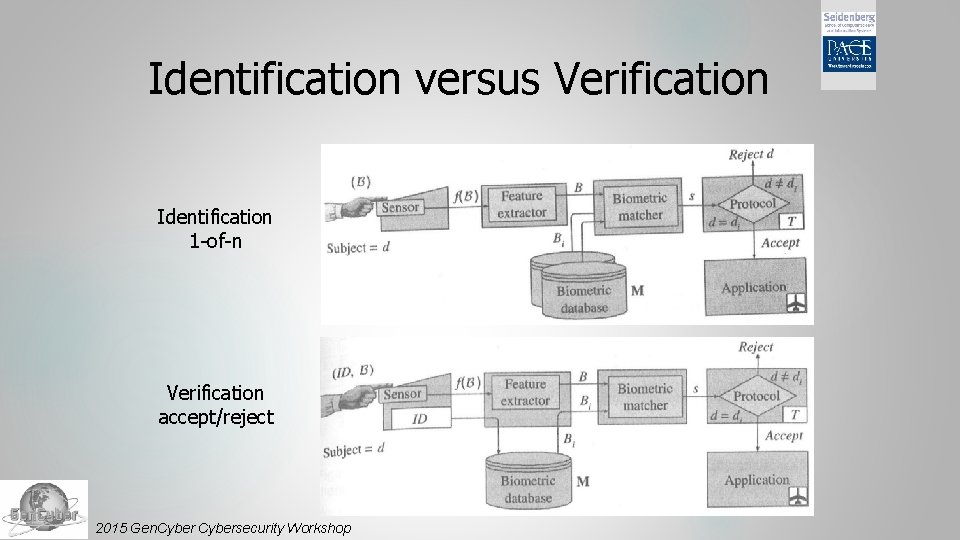
Identification versus Verification Identification 1 -of-n Verification accept/reject 2015 Gen. Cybersecurity Workshop

Face Biometric Acquisition Single 2 D image Video sequence 3 D image via stereo imaging, etc. Michigan State University – Anil Jain http: //biometrics. cse. msu. edu/Presentations/Anil. Jain_ Face. Recognition_KU 10. pdf 2015 Gen. Cybersecurity Workshop

Face Recognition Each person has a unique face? 2015 Gen. Cybersecurity Workshop
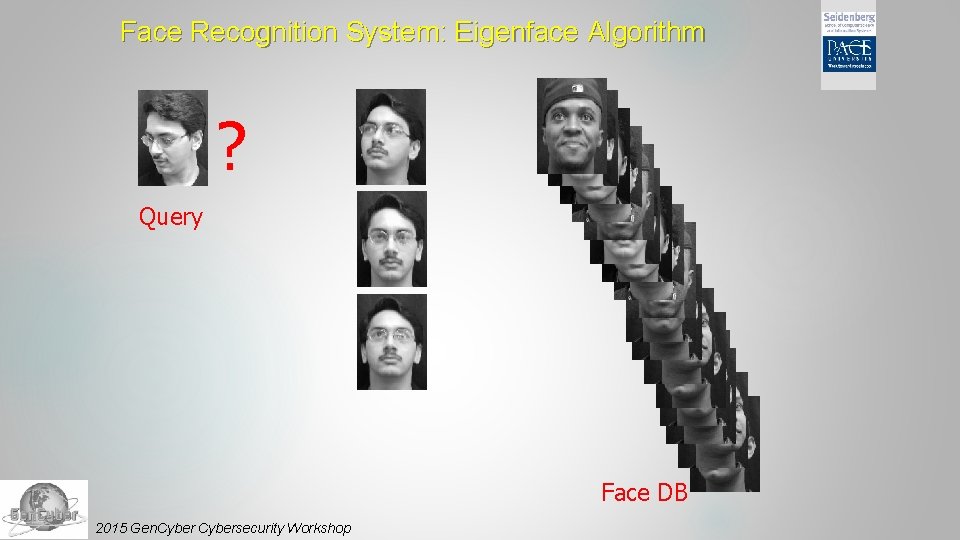
Face Recognition System: Eigenface Algorithm ? Query Face DB 2015 Gen. Cybersecurity Workshop

Inspirational Portrait of Individuality 2015 Gen. Cybersecurity Workshop

Face Recognition: National Security 2015 Gen. Cybersecurity Workshop
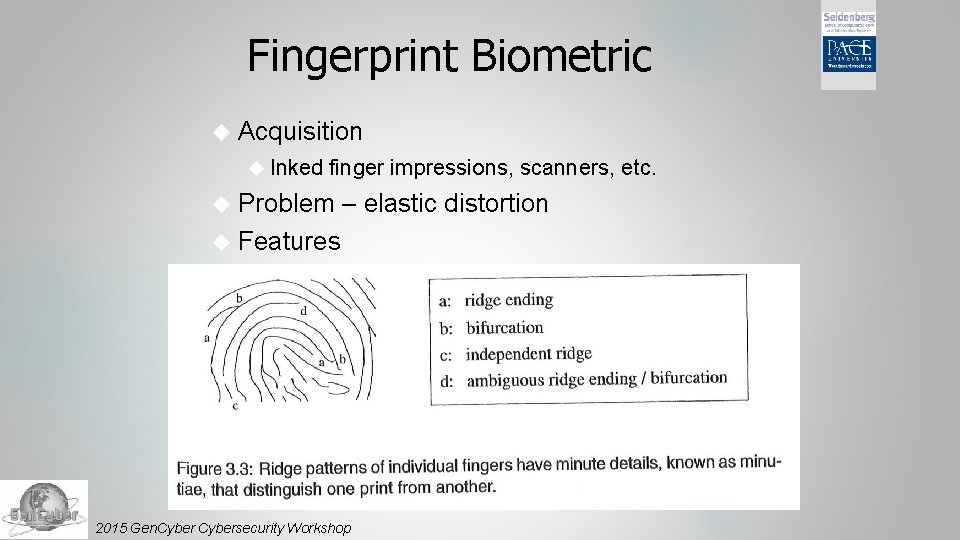
Fingerprint Biometric Acquisition Inked finger impressions, scanners, etc. Problem – elastic distortion Features 2015 Gen. Cybersecurity Workshop

Fingerprint Verification 2015 Gen. Cybersecurity Workshop
Iris Authentication: Data Left Train Man Test Train Wo man Test 2015 Gen. Cybersecurity Workshop Right

Iris Authentication: Image Processing 2015 Gen. Cybersecurity Workshop

Biometric Authentication A robot identifies a suspect, from the movie “Minority Report. ” 2015 Gen. Cybersecurity Workshop
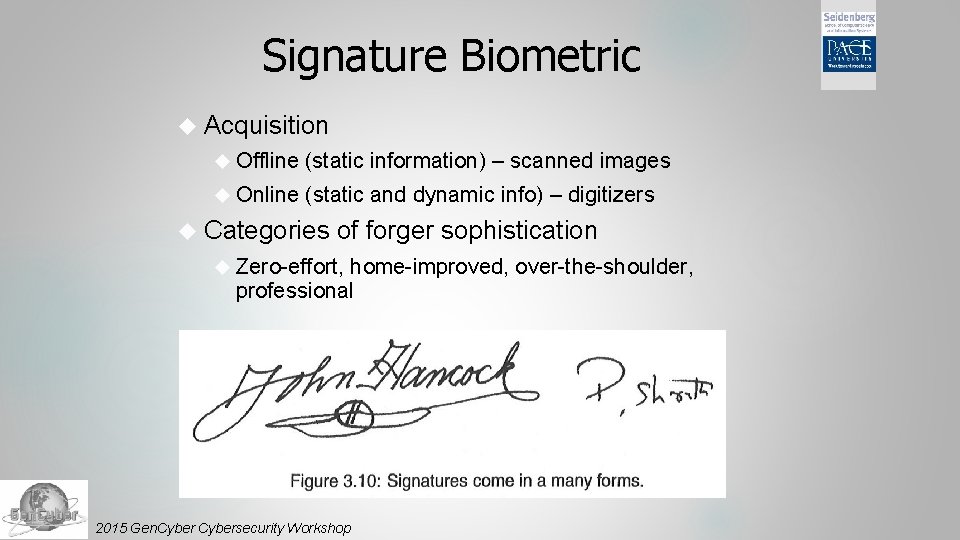
Signature Biometric Acquisition Offline (static information) – scanned images Online (static and dynamic info) – digitizers Categories of forger sophistication Zero-effort, home-improved, over-the-shoulder, professional 2015 Gen. Cybersecurity Workshop
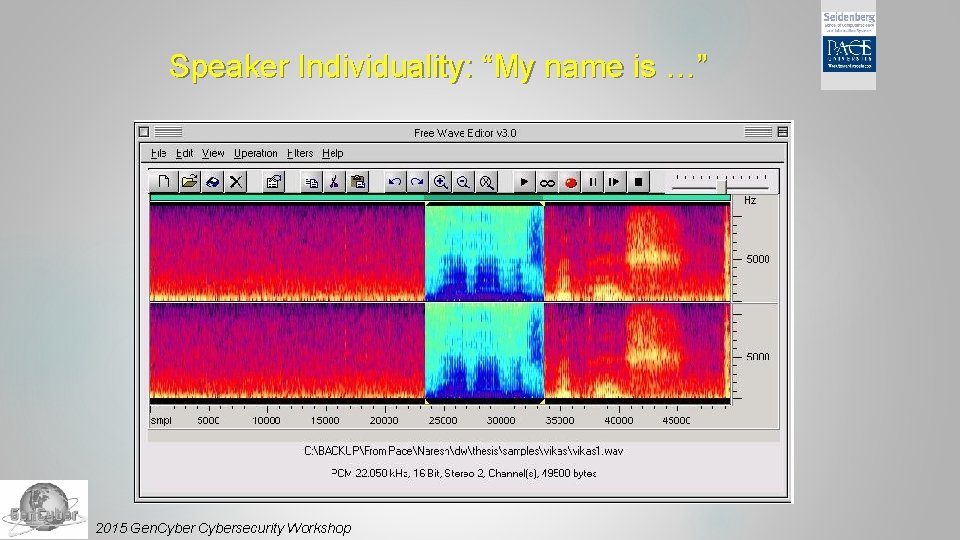
Speaker Individuality: “My name is …” 2015 Gen. Cybersecurity Workshop
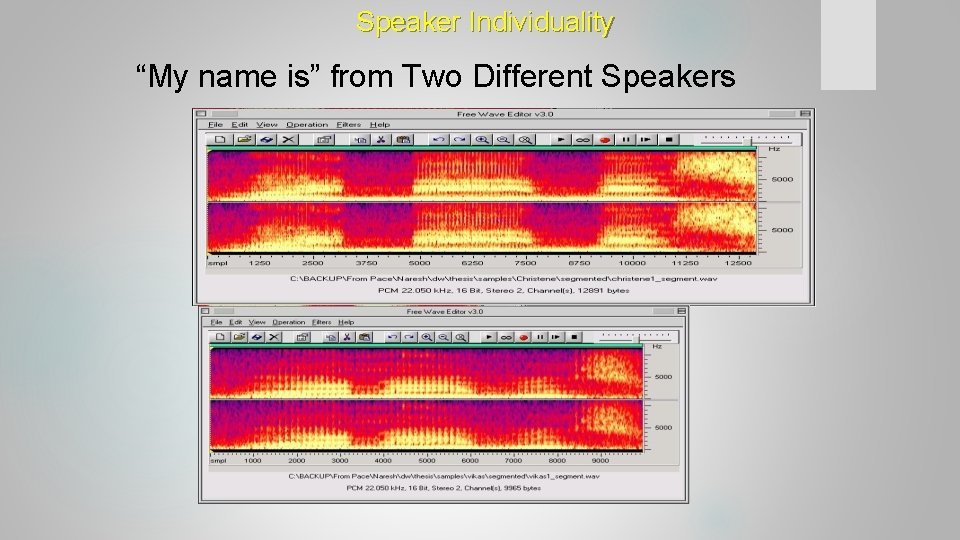
Speaker Individuality “My name is” from Two Different Speakers

Speech Biometric – Voiceprint Acquisition Microphone “My – inexpensive, ubiquitous name is” divided into seven sound units 2015 Gen. Cybersecurity Workshop
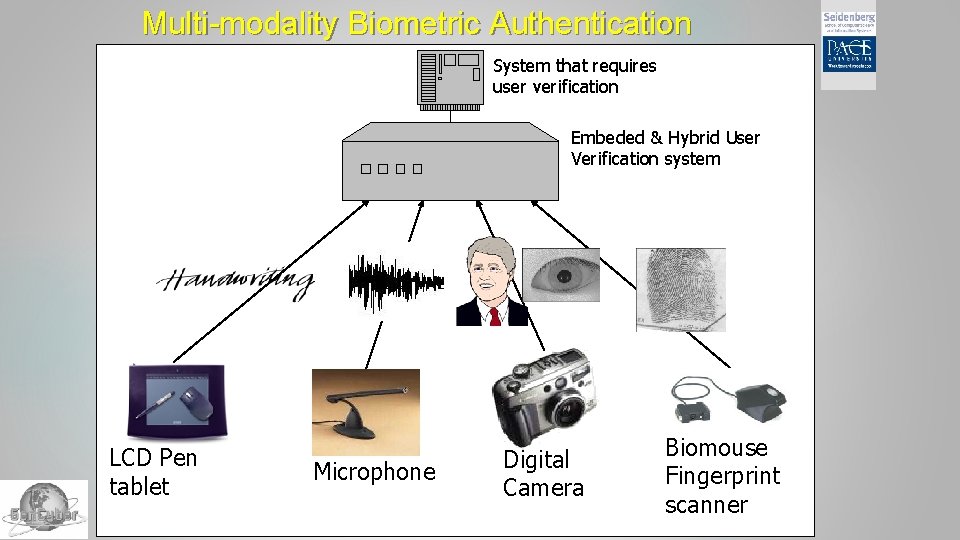
Multi-modality Biometric Authentication System that requires user verification Embeded & Hybrid User Verification system LCD Pen tablet Microphone 2015 Gen. Cybersecurity Workshop Digital Camera Biomouse Fingerprint scanner
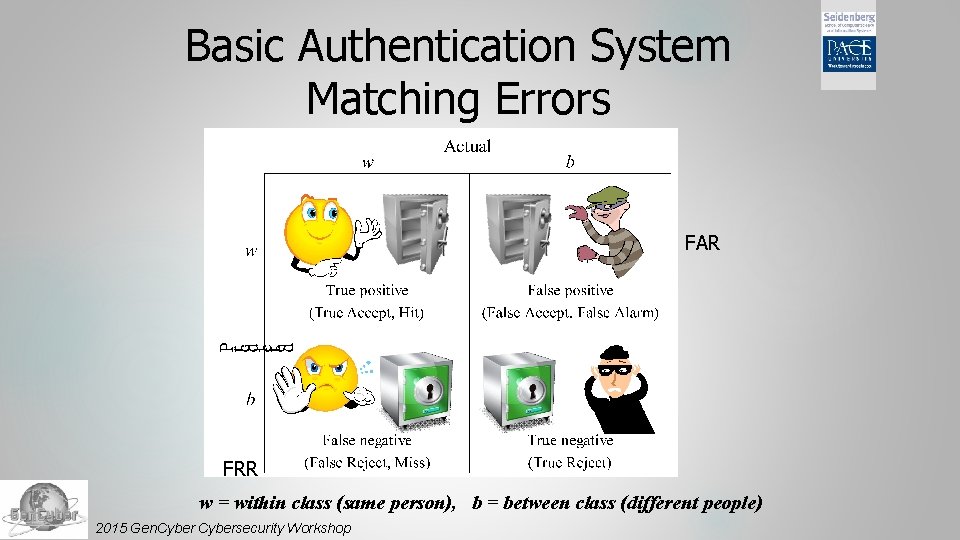
Basic Authentication System Matching Errors FAR FRR w = within class (same person), b = between class (different people) 2015 Gen. Cybersecurity Workshop
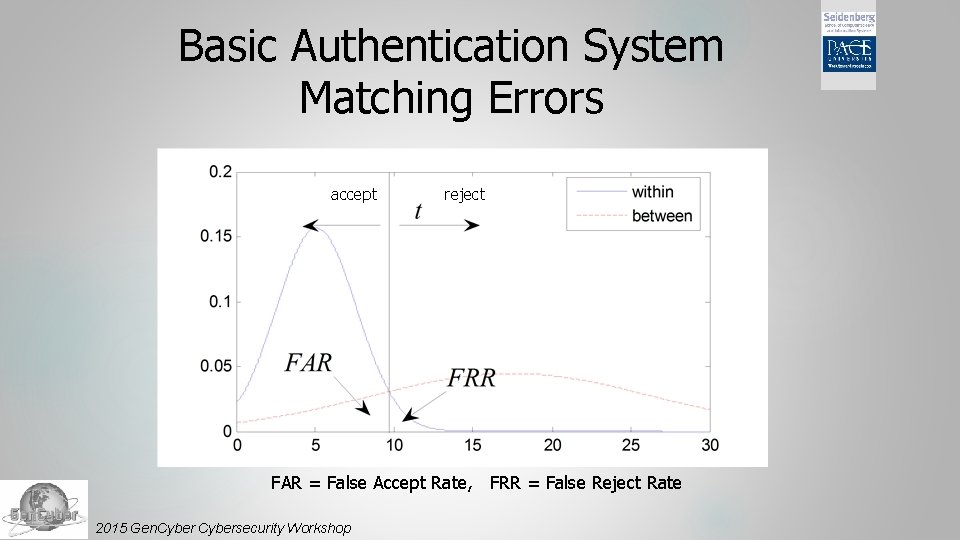
Basic Authentication System Matching Errors accept reject FAR = False Accept Rate, FRR = False Reject Rate 2015 Gen. Cybersecurity Workshop
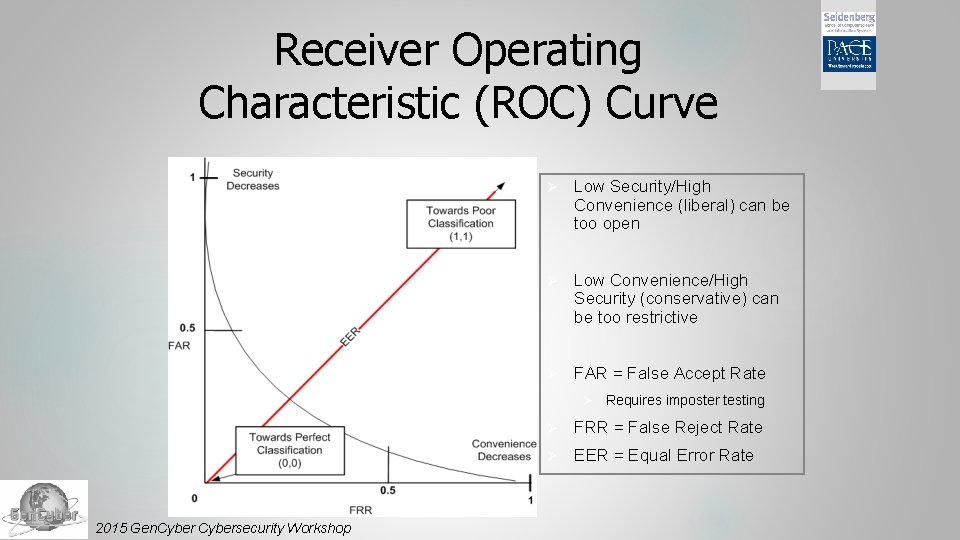
Receiver Operating Characteristic (ROC) Curve Ø Low Security/High Convenience (liberal) can be too open Ø Low Convenience/High Security (conservative) can be too restrictive Ø FAR = False Accept Rate Ø 2015 Gen. Cybersecurity Workshop Requires imposter testing Ø FRR = False Reject Rate Ø EER = Equal Error Rate
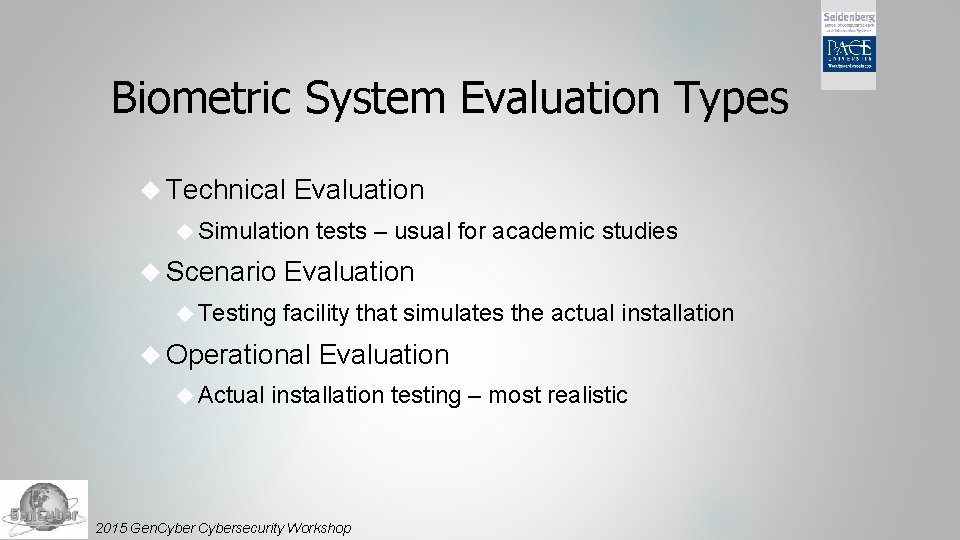
Biometric System Evaluation Types Technical Evaluation Simulation Scenario Testing Evaluation facility that simulates the actual installation Operational Actual tests – usual for academic studies Evaluation installation testing – most realistic 2015 Gen. Cybersecurity Workshop
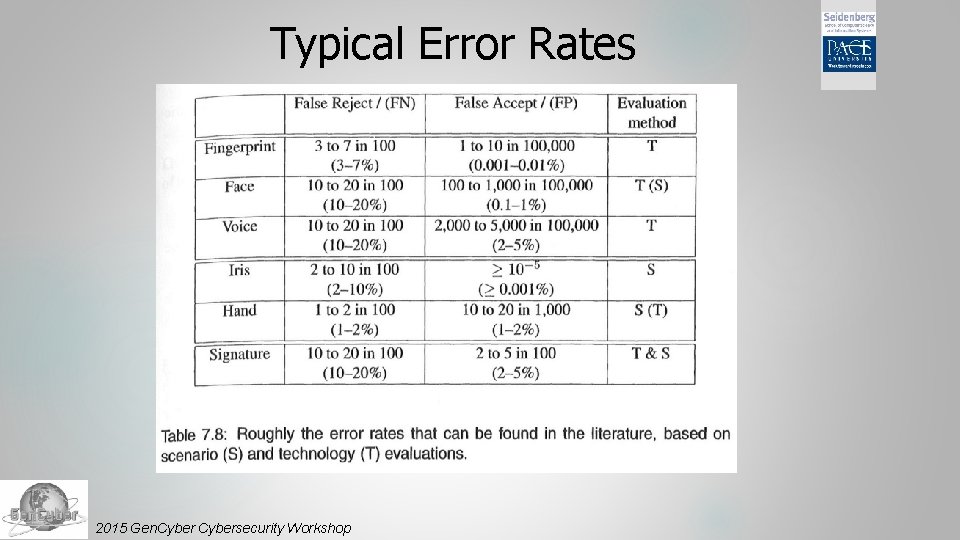
Typical Error Rates 2015 Gen. Cybersecurity Workshop

Biometric Zoo Sheep Dominant group, systems perform well for them Goats Weak distinctive traits, produce many False Rejects Lambs Easy to imitate, cause “passive” False Accepts Wolves Good at imitating, cause “active” False Accepts Chameleons Easy to imitate and good at imitating others 2015 Gen. Cybersecurity Workshop
Many Biometric Systems and Interesting Articles on the Internet Microsoft's Key. Trac Secret keystroke demos: passwords, any text Lock Michigan DNA Age Estimator State University Generated Face – NYT science section article Building a Face, and Case, on DNA – March 2015 Gen. Cybersecurity Workshop

Project Ideas List and describe various biometrics, can you think of new ones? What is the government doing in biometrics? Define and describe various technologies used in biometrics Find interesting Web and news items related to biometrics – e. g. , beer and diapers, Target’s pregnant girl, DNA generated face, secret lock, age estimation Find or go deeper into interesting technologies – e. g. , spelling correction, Siri’s voice command system List and describe the ways people use the usual authentication method of combining what you have and what you know Investigate the biometric zoo – what biometrics are easy to spoof? 2015 Gen. Cybersecurity Workshop
Verizon Funding – 2015 Reduce UID/Password Dependency Most people have many UID/Passwords for access Bank accounts, smartphone/computer, social websites, etc. Location Component Near Field Communication (NFC) Geofencing Near-field communication uses electromagnetic induction between two loop antennas located within each other's near field Uses the global positioning system (GPS) or radio frequency identification (RFID) to define geographical boundaries Biometrics Explore the use of several biometrics for use in this problem area 2015 Gen. Cybersecurity Workshop

Copyright for Material Reuse Copyright© 2015 Charles Tappert (ctappert@pace. edu), Pace University. Please properly acknowledge the source for any reuse of the materials as below. Charles Tappert, 2015 Gen. Cybersecurity Workshop, Pace University Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1. 3 or any later version published by the Free Software Foundation. A copy of the license is available at http: //www. gnu. org/copyleft/fdl. html. 2015 Gen. Cybersecurity Workshop

Acknowledgment The authors would like to acknowledge the support from the National Science Foundation under Grant No. 1027400 and from the Gen. Cyber program in the National Security Agency. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the National Science Foundation, the National Security Agency or the U. S. government. 2015 Gen. Cybersecurity Workshop
- Slides: 51