An Introduction To Packet Storm IP Network Emulators











- Slides: 61

An Introduction To Packet. Storm IP Network Emulators Specifications and features are subject to change. Contact your local Packet. Storm Representative for updated information, specifications and pricing. All names, products, services, logos, trademarks or registered trademarks are the property of their respective owners. This presentation is not to be re-transmitted, duplicated or distributed without written permission from Packet. Storm Communications. Joerg Klehe DHS El. Mea Tools Gmb. H jklehe@dhs-tools. de JDK 9/11/2006 - Packet. Storm Confidential -

Packet. Storm emulators test your product or application to be sure it will perform as required At first, some thought they could just connect their product to the Internet, run some tests and be confident it would perform as designed. ? However, many soon realized that using the Internet as a testing environment didn’t work because: -They couldn’t control the test parameters and -They couldn’t create repeatable tests - Packet. Storm Confidential -

Packet. Storm IP Network Emulators were developed to emulate IP Network conditions in a repeatable, easily configurable environment. Ø Impair packets Ø Modify and corrupt packets Ø Emulate any network condition Ø Repeatable testing Ø Easy to use - Packet. Storm Confidential -

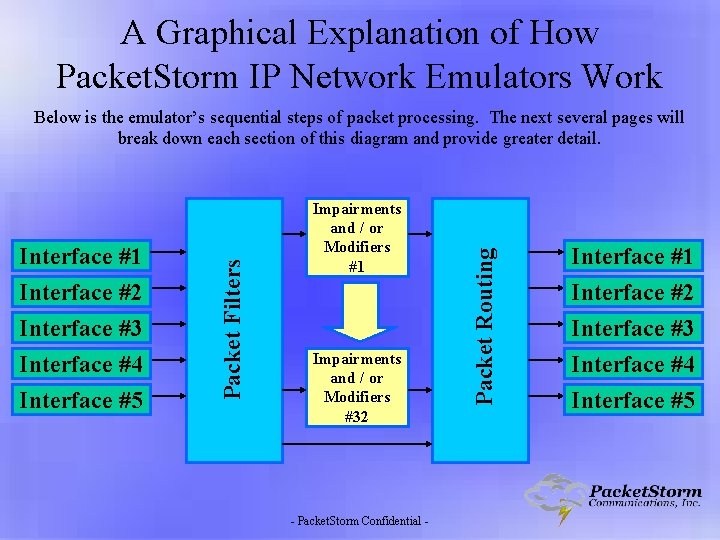
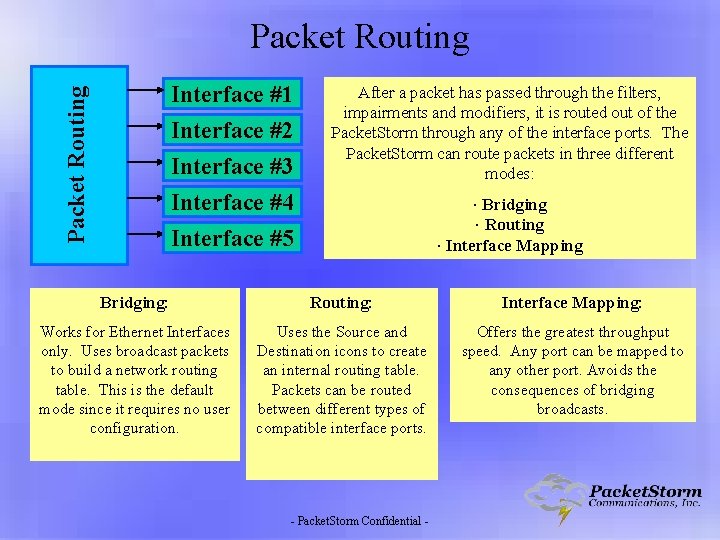
A Graphical Explanation of How Packet. Storm IP Network Emulators Work Interface #2 Interface #3 Interface #4 Interface #5 Impairments and / or Modifiers #1 Impairments and / or Modifiers #32 - Packet. Storm Confidential - Packet Routing Interface #1 Packet Filters Below is the emulator’s sequential steps of packet processing. The next several pages will break down each section of this diagram and provide greater detail. Interface #1 Interface #2 Interface #3 Interface #4 Interface #5

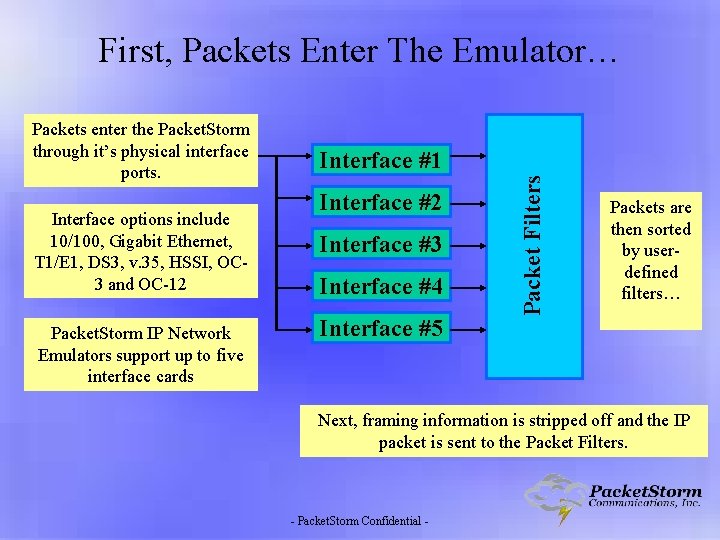
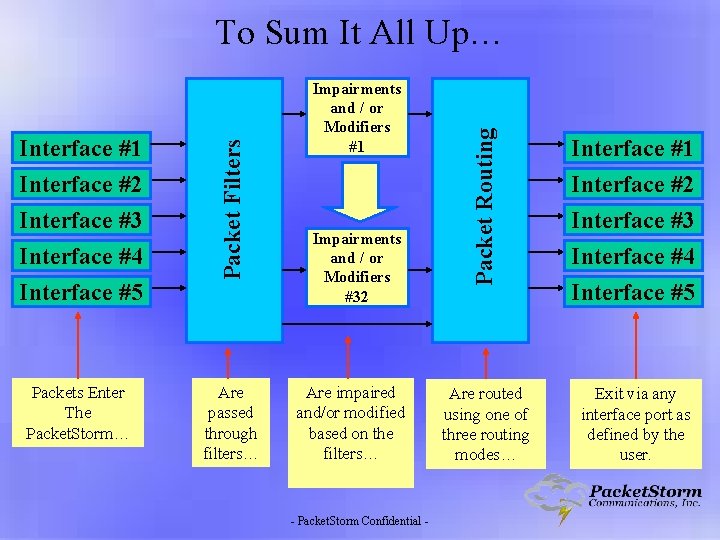
First, Packets Enter The Emulator… Interface options include 10/100, Gigabit Ethernet, T 1/E 1, DS 3, v. 35, HSSI, OC 3 and OC-12 Packet. Storm IP Network Emulators support up to five interface cards Interface #1 Interface #2 Interface #3 Interface #4 Interface #5 Packet Filters Packets enter the Packet. Storm through it’s physical interface ports. Packets are then sorted by userdefined filters… Next, framing information is stripped off and the IP packet is sent to the Packet Filters. - Packet. Storm Confidential -

Packet Filters Up to 32 user definable filters Packet Filters Standard Filters Optional Filters Ø Source Address Ø Bit Pattern Ø Destination Address Ø Universal Ø Port Numbers Ø MPLS Ø Protocol Ø VLAN Ø Packet Length Ø MAC Ø Input Port Ø IPv 6 Ø Type of Service (To. S) Ø ATM PVC Ø Diff Serv - Packet. Storm Confidential -

RTP Filter (Part of Bit Pattern Filter Option) - Packet. Storm Confidential -

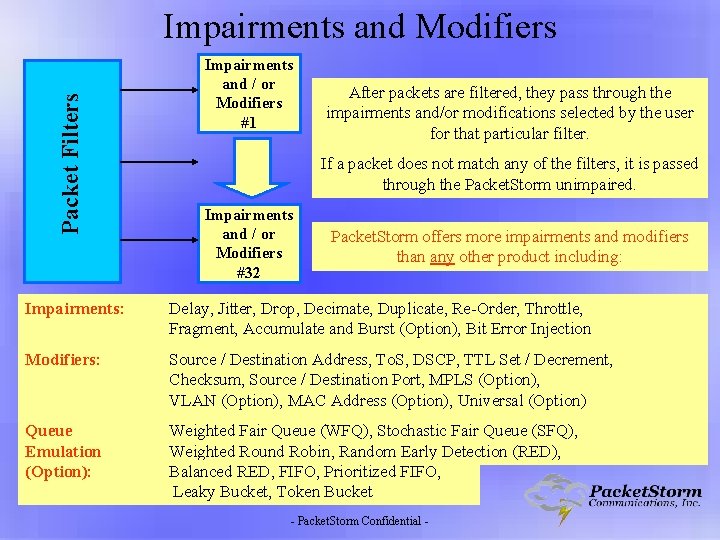
Packet Filters Impairments and Modifiers Impairments and / or Modifiers #1 After packets are filtered, they pass through the impairments and/or modifications selected by the user for that particular filter. If a packet does not match any of the filters, it is passed through the Packet. Storm unimpaired. Impairments and / or Modifiers #32 Packet. Storm offers more impairments and modifiers than any other product including: Impairments: Delay, Jitter, Drop, Decimate, Duplicate, Re-Order, Throttle, Fragment, Accumulate and Burst (Option), Bit Error Injection Modifiers: Source / Destination Address, To. S, DSCP, TTL Set / Decrement, Checksum, Source / Destination Port, MPLS (Option), VLAN (Option), MAC Address (Option), Universal (Option) Queue Emulation (Option): Weighted Fair Queue (WFQ), Stochastic Fair Queue (SFQ), Weighted Round Robin, Random Early Detection (RED), Balanced RED, FIFO, Prioritized FIFO, Leaky Bucket, Token Bucket - Packet. Storm Confidential -

Packet Routing Interface #1 Interface #2 Interface #3 Interface #4 Interface #5 After a packet has passed through the filters, impairments and modifiers, it is routed out of the Packet. Storm through any of the interface ports. The Packet. Storm can route packets in three different modes: ∙ Bridging ∙ Routing ∙ Interface Mapping Bridging: Routing: Interface Mapping: Works for Ethernet Interfaces only. Uses broadcast packets to build a network routing table. This is the default mode since it requires no user configuration. Uses the Source and Destination icons to create an internal routing table. Packets can be routed between different types of compatible interface ports. Offers the greatest throughput speed. Any port can be mapped to any other port. Avoids the consequences of bridging broadcasts. - Packet. Storm Confidential -

Interface #5 Packets Enter The Packet. Storm… Are passed through filters… Impairments and / or Modifiers #1 Impairments and / or Modifiers #32 Are impaired and/or modified based on the filters… - Packet. Storm Confidential - Packet Routing Interface #1 Interface #2 Interface #3 Interface #4 Packet Filters To Sum It All Up… Interface #1 Interface #2 Interface #3 Interface #4 Are routed using one of three routing modes… Exit via any interface port as defined by the user. Interface #5

Graphical User Interface (GUI) Two Operation Modes Ø Basic Easier to use interface Simple networks emulation Ø Standard Additional functions and capabilities Complex networks emulation - Packet. Storm Confidential -

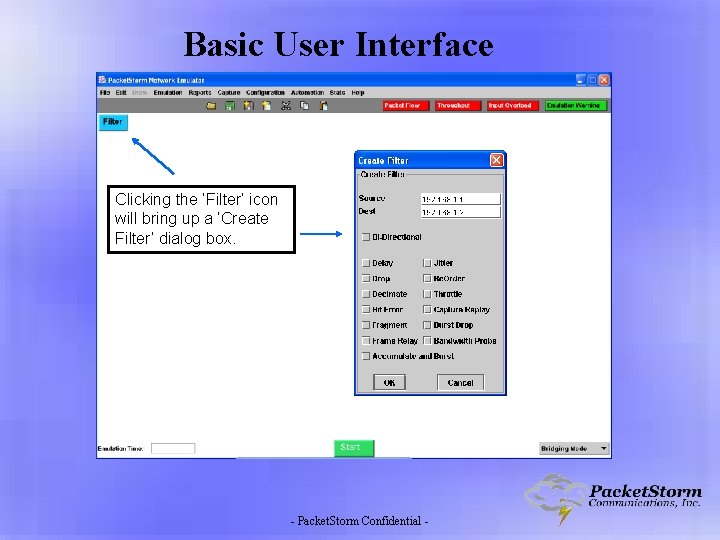
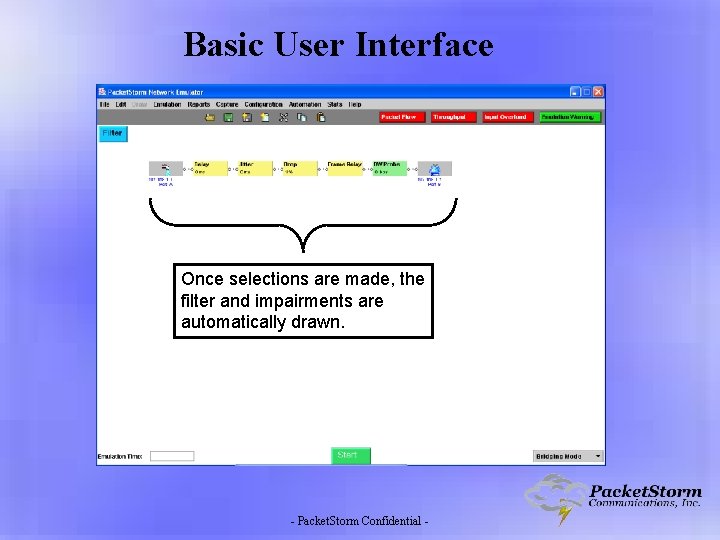
Basic User Interface Clicking the ‘Filter’ icon will bring up a ‘Create Filter’ dialog box. - Packet. Storm Confidential -

Basic User Interface Once selections are made, the filter and impairments are automatically drawn. - Packet. Storm Confidential -

Standard User Interface Additional Functions and Capabilities Ø Dynamic Emulation Ø To. S & Diff Serv Emulation Ø Packet Tap Statistics Ø Packet Generator Ø Packet Analyzer Ø Data Replay Ø Modifiers - Packet. Storm Confidential -

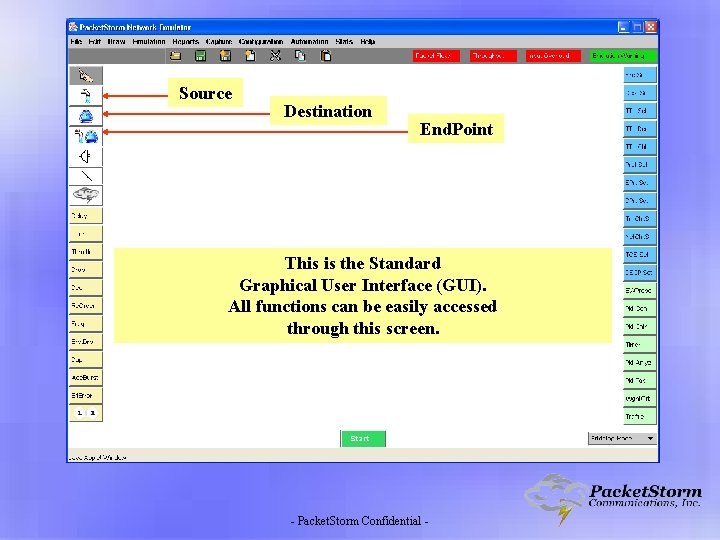
Source Destination End. Point This is the Standard Graphical User Interface (GUI). All functions can be easily accessed through this screen. - Packet. Storm Confidential -

The Source, Destination and Endpoint Icons Define Which Packets Are To Be Selected For Impairment and/or Modification Source: Defines the characteristics of a packet’s origination. Example: Source Address, Port Number, Bit Pattern, Protocol. Destination: Defines the characteristics of a packet’s destination. Example: Destination Address, Port Number, Bit Pattern. Endpoint: Unlike Source and Destination, Endpoint is Bi-Directional and can define a packet’s source or destination characteristics. Example: Source or Destination Address, Port Number, Bit Pattern, Protocol. - Packet. Storm Confidential -

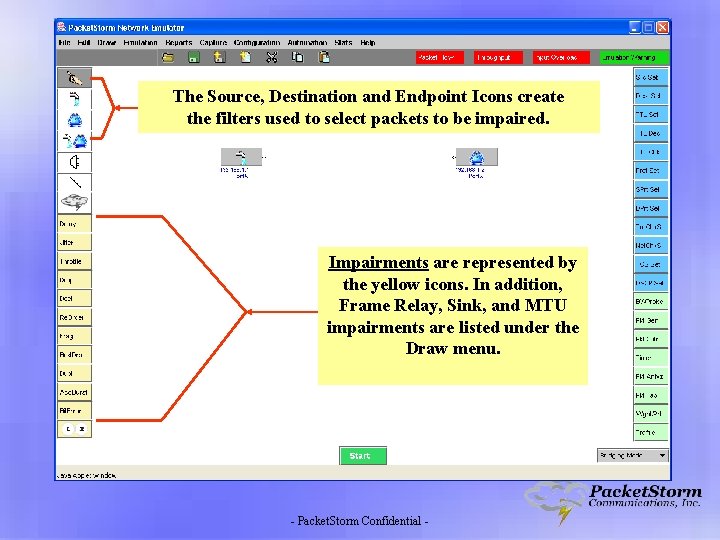
The Source, Destination and Endpoint Icons create the filters used to select packets to be impaired. Impairments are represented by the yellow icons. In addition, Frame Relay, Sink, and MTU impairments are listed under the Draw menu. - Packet. Storm Confidential -

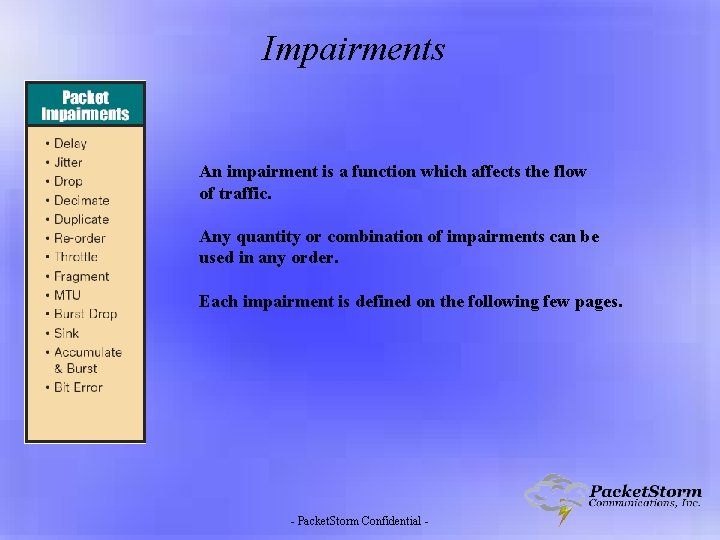
Impairments An impairment is a function which affects the flow of traffic. Any quantity or combination of impairments can be used in any order. Each impairment is defined on the following few pages. - Packet. Storm Confidential -

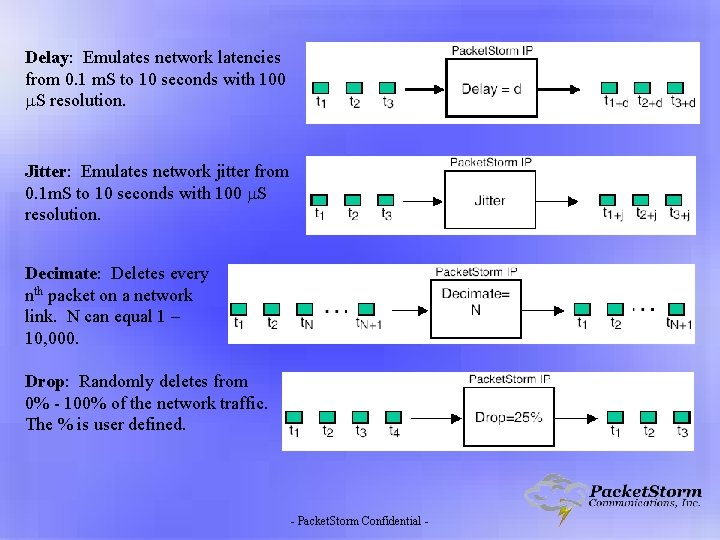
Delay: Emulates network latencies from 0. 1 m. S to 10 seconds with 100 S resolution. Jitter: Emulates network jitter from 0. 1 m. S to 10 seconds with 100 S resolution. Decimate: Deletes every nth packet on a network link. N can equal 1 – 10, 000. Drop: Randomly deletes from 0% - 100% of the network traffic. The % is user defined. - Packet. Storm Confidential -

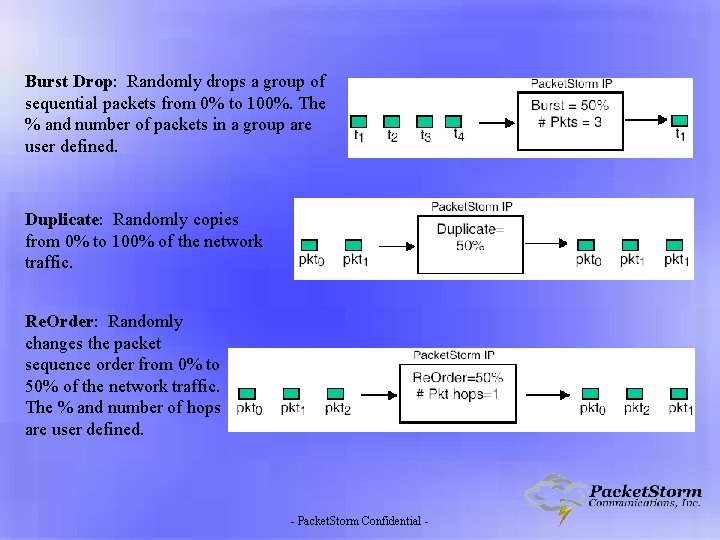
Burst Drop: Randomly drops a group of sequential packets from 0% to 100%. The % and number of packets in a group are user defined. Duplicate: Randomly copies from 0% to 100% of the network traffic. Re. Order: Randomly changes the packet sequence order from 0% to 50% of the network traffic. The % and number of hops are user defined. - Packet. Storm Confidential -

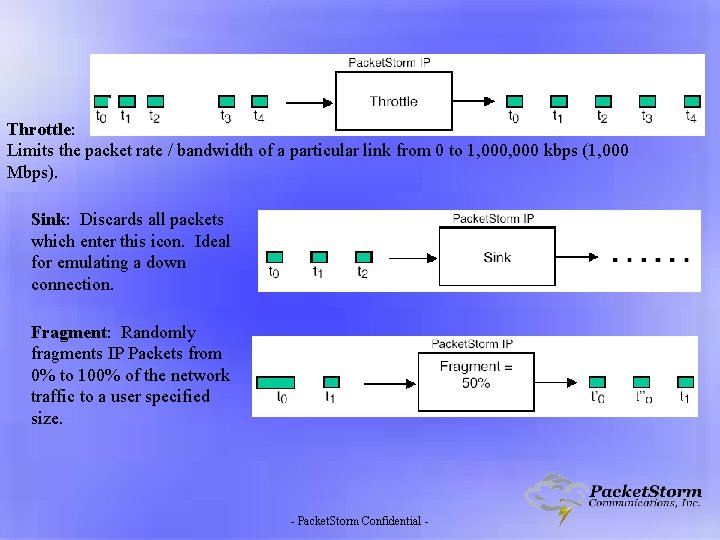
Throttle: Limits the packet rate / bandwidth of a particular link from 0 to 1, 000 kbps (1, 000 Mbps). Sink: Discards all packets which enter this icon. Ideal for emulating a down connection. Fragment: Randomly fragments IP Packets from 0% to 100% of the network traffic to a user specified size. - Packet. Storm Confidential -

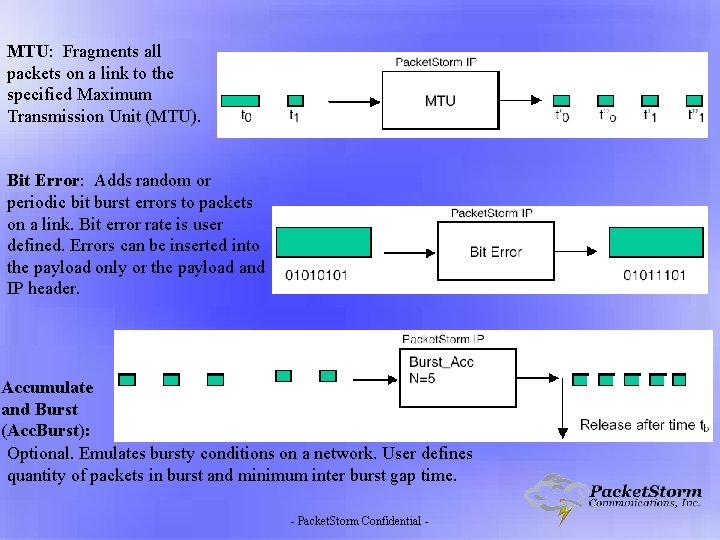
MTU: Fragments all packets on a link to the specified Maximum Transmission Unit (MTU). Bit Error: Adds random or periodic bit burst errors to packets on a link. Bit error rate is user defined. Errors can be inserted into the payload only or the payload and IP header. Accumulate and Burst (Acc. Burst): Optional. Emulates bursty conditions on a network. User defines quantity of packets in burst and minimum inter burst gap time. - Packet. Storm Confidential -

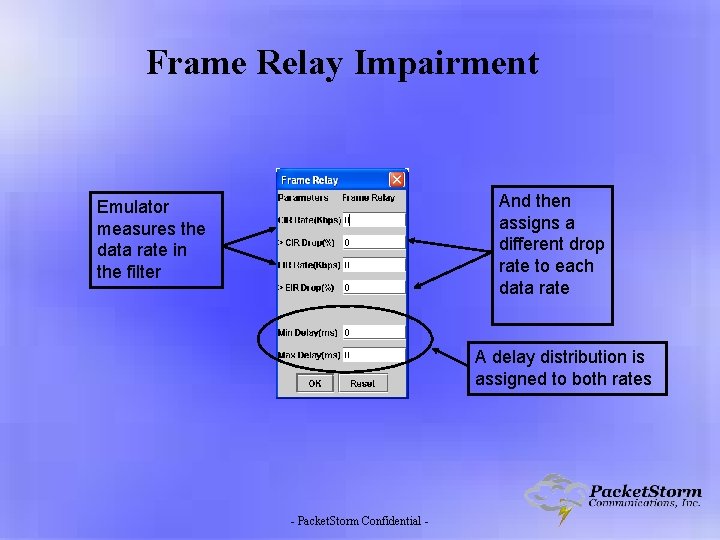
Frame Relay Impairment And then assigns a different drop rate to each data rate Emulator measures the data rate in the filter A delay distribution is assigned to both rates - Packet. Storm Confidential -

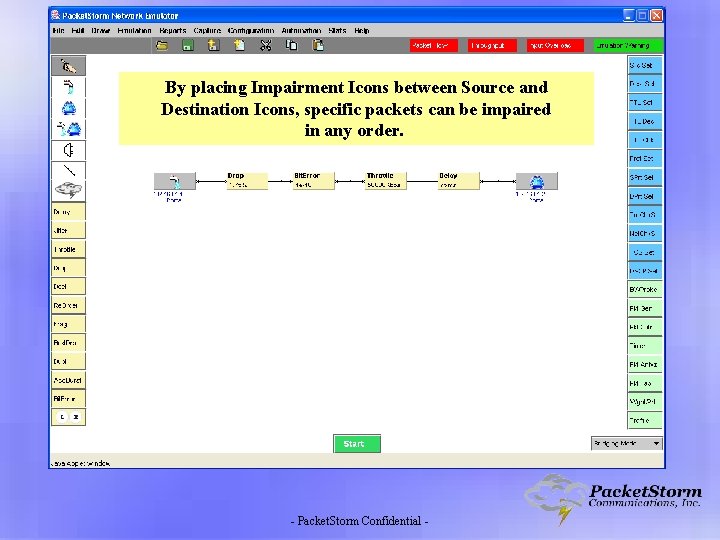
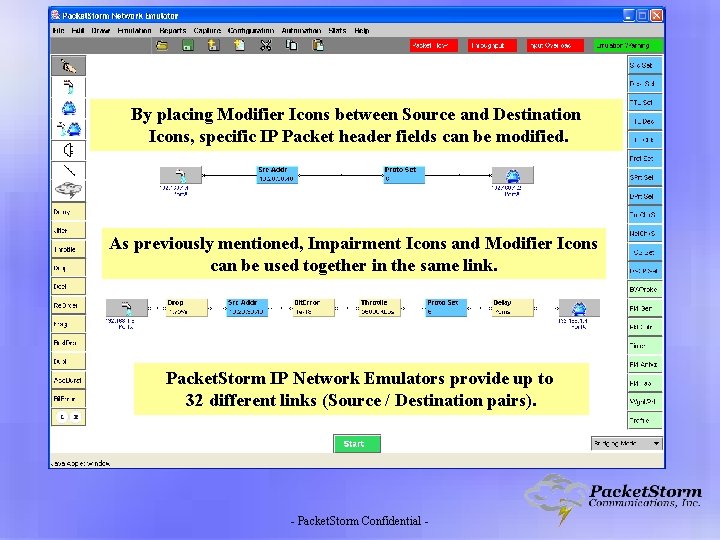
By placing Impairment Icons between Source and Destination Icons, specific packets can be impaired in any order. - Packet. Storm Confidential -

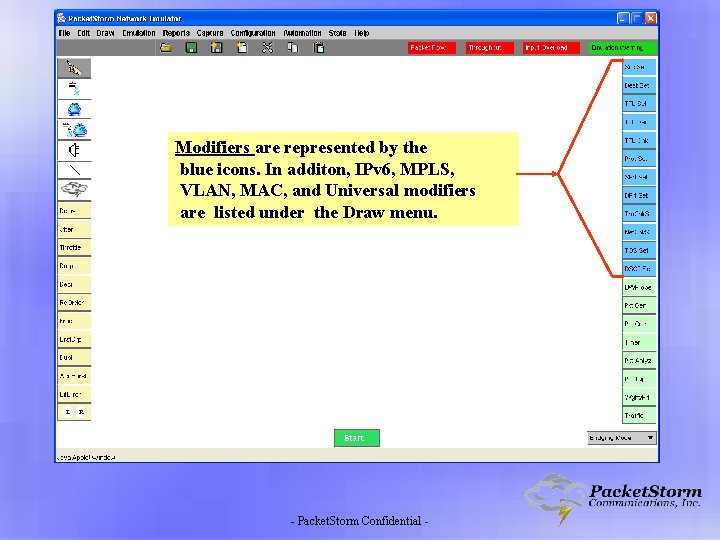
Modifiers are represented by the blue icons. In additon, IPv 6, MPLS, VLAN, MAC, and Universal modifiers are listed under the Draw menu. - Packet. Storm Confidential -

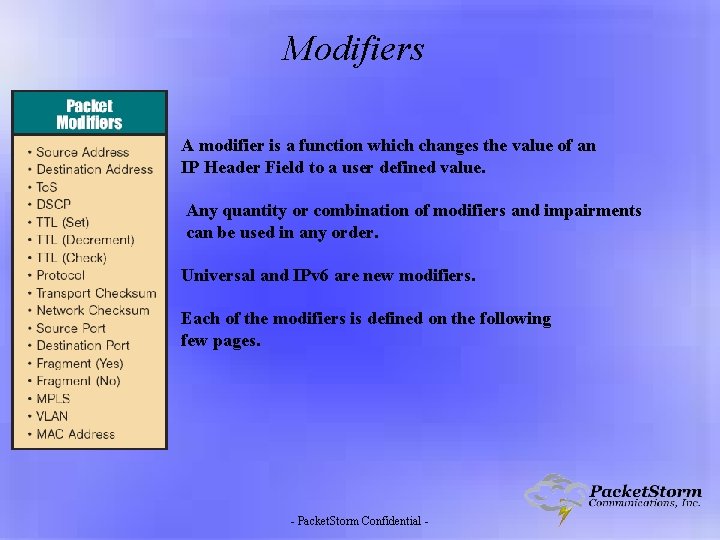
Modifiers A modifier is a function which changes the value of an IP Header Field to a user defined value. Any quantity or combination of modifiers and impairments can be used in any order. Universal and IPv 6 are new modifiers. Each of the modifiers is defined on the following few pages. - Packet. Storm Confidential -

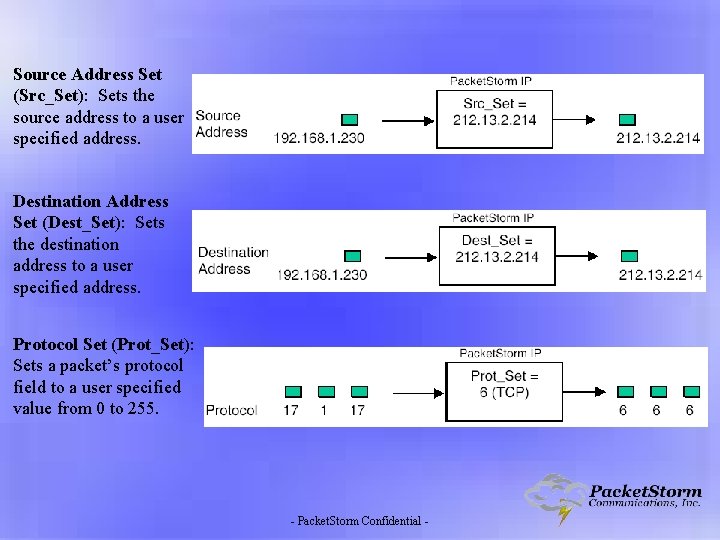
Source Address Set (Src_Set): Sets the source address to a user specified address. Destination Address Set (Dest_Set): Sets the destination address to a user specified address. Protocol Set (Prot_Set): Sets a packet’s protocol field to a user specified value from 0 to 255. - Packet. Storm Confidential -

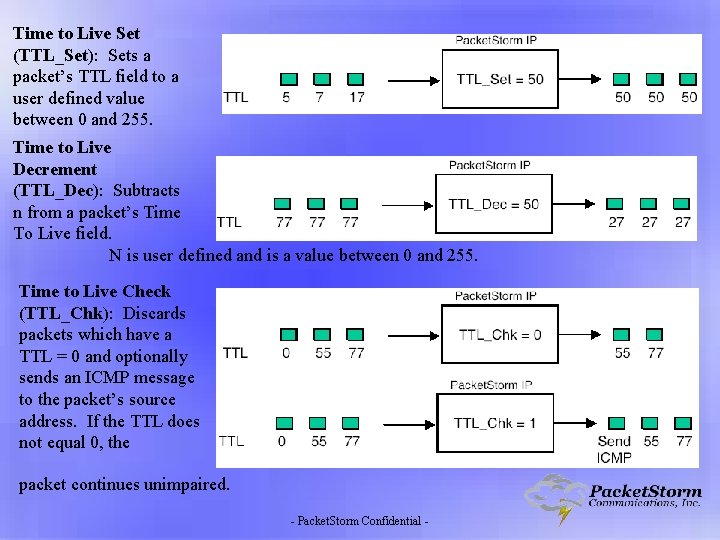
Time to Live Set (TTL_Set): Sets a packet’s TTL field to a user defined value between 0 and 255. Time to Live Decrement (TTL_Dec): Subtracts n from a packet’s Time To Live field. N is user defined and is a value between 0 and 255. Time to Live Check (TTL_Chk): Discards packets which have a TTL = 0 and optionally sends an ICMP message to the packet’s source address. If the TTL does not equal 0, the packet continues unimpaired. - Packet. Storm Confidential -

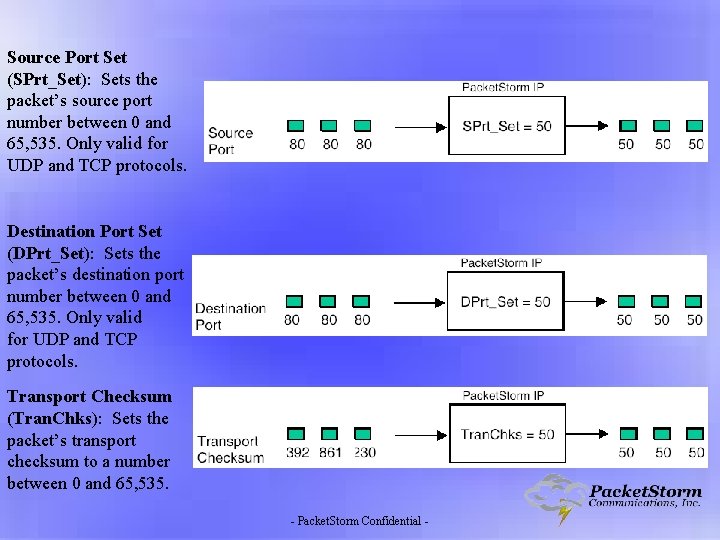
Source Port Set (SPrt_Set): Sets the packet’s source port number between 0 and 65, 535. Only valid for UDP and TCP protocols. Destination Port Set (DPrt_Set): Sets the packet’s destination port number between 0 and 65, 535. Only valid for UDP and TCP protocols. Transport Checksum (Tran. Chks): Sets the packet’s transport checksum to a number between 0 and 65, 535. - Packet. Storm Confidential -

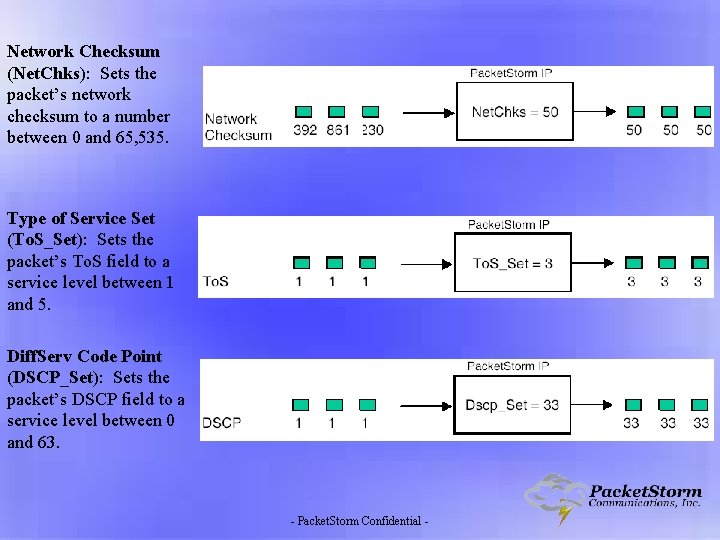
Network Checksum (Net. Chks): Sets the packet’s network checksum to a number between 0 and 65, 535. Type of Service Set (To. S_Set): Sets the packet’s To. S field to a service level between 1 and 5. Diff. Serv Code Point (DSCP_Set): Sets the packet’s DSCP field to a service level between 0 and 63. - Packet. Storm Confidential -

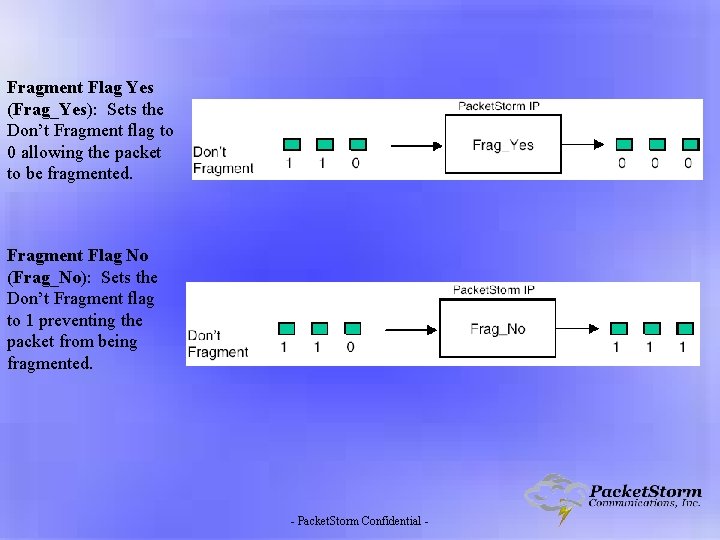
Fragment Flag Yes (Frag_Yes): Sets the Don’t Fragment flag to 0 allowing the packet to be fragmented. Fragment Flag No (Frag_No): Sets the Don’t Fragment flag to 1 preventing the packet from being fragmented. - Packet. Storm Confidential -

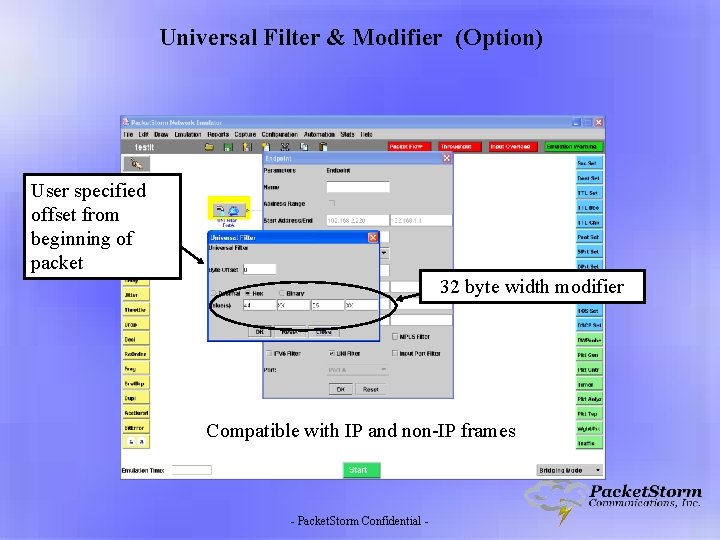
Universal Filter & Modifier (Option) User specified offset from beginning of packet 32 byte width modifier Compatible with IP and non-IP frames - Packet. Storm Confidential -

By placing Modifier Icons between Source and Destination Icons, specific IP Packet header fields can be modified. As previously mentioned, Impairment Icons and Modifier Icons can be used together in the same link. Packet. Storm IP Network Emulators provide up to 32 different links (Source / Destination pairs). - Packet. Storm Confidential -

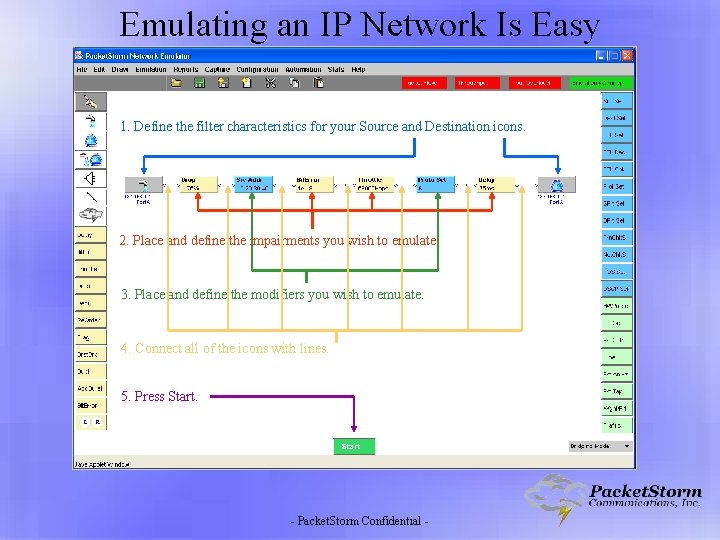
Emulating an IP Network Is Easy 1. Define the filter characteristics for your Source and Destination icons. 2. Place and define the impairments you wish to emulate. 3. Place and define the modifiers you wish to emulate. 4. Connect all of the icons with lines. 5. Press Start. - Packet. Storm Confidential -

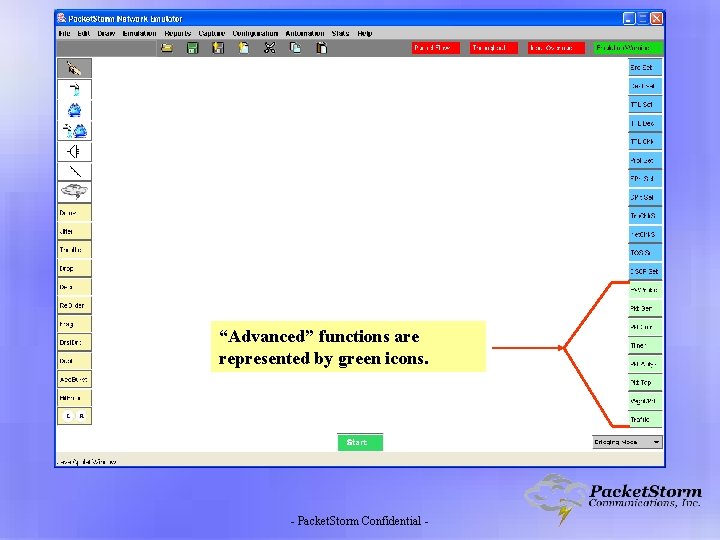
“Advanced” functions are represented by green icons. - Packet. Storm Confidential -

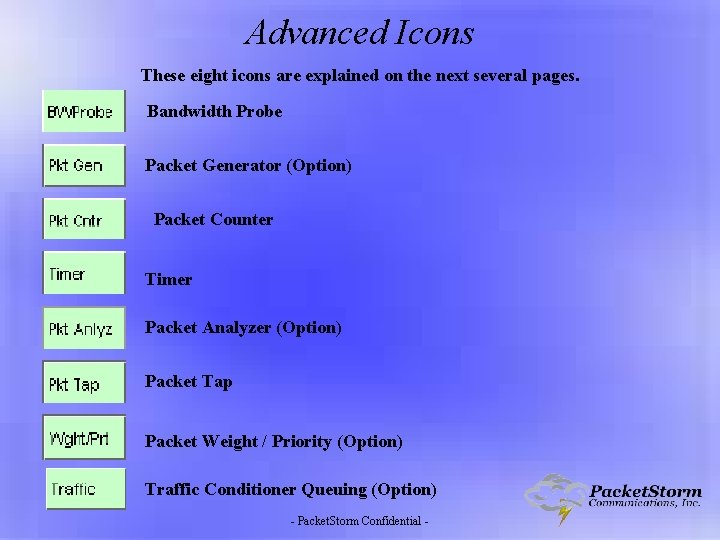
Advanced Icons These eight icons are explained on the next several pages. Bandwidth Probe Packet Generator (Option) Packet Counter Timer Packet Analyzer (Option) Packet Tap Packet Weight / Priority (Option) Traffic Conditioner Queuing (Option) - Packet. Storm Confidential -

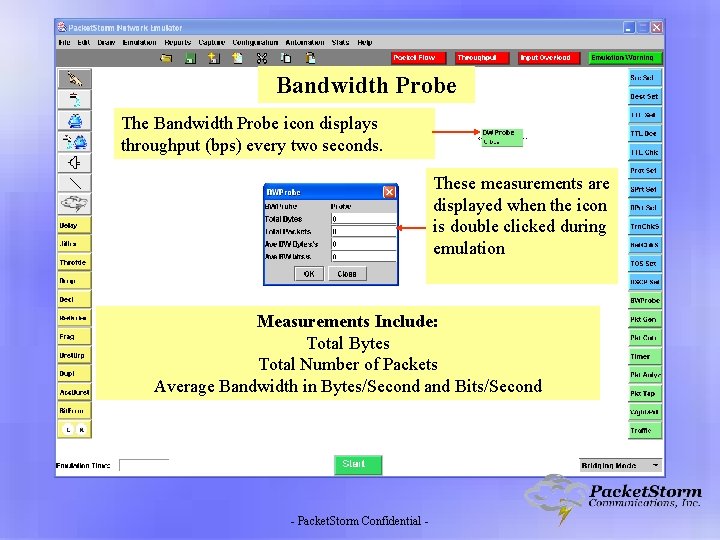
Bandwidth Probe The Bandwidth Probe icon displays throughput (bps) every two seconds. These measurements are displayed when the icon is double clicked during emulation Measurements Include: Total Bytes Total Number of Packets Average Bandwidth in Bytes/Second and Bits/Second - Packet. Storm Confidential -

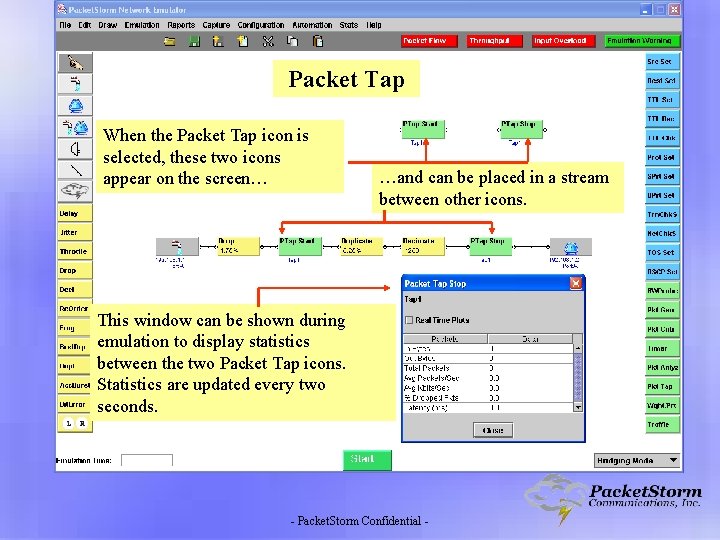
Packet Tap When the Packet Tap icon is selected, these two icons appear on the screen… …and can be placed in a stream between other icons. This window can be shown during emulation to display statistics between the two Packet Tap icons. Statistics are updated every two seconds. - Packet. Storm Confidential -

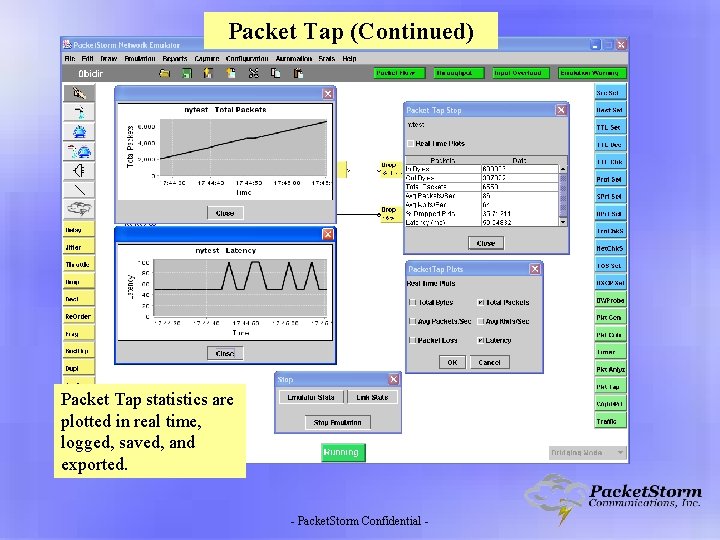
Packet Tap (Continued) Packet Tap statistics are plotted in real time, logged, saved, and exported. - Packet. Storm Confidential -

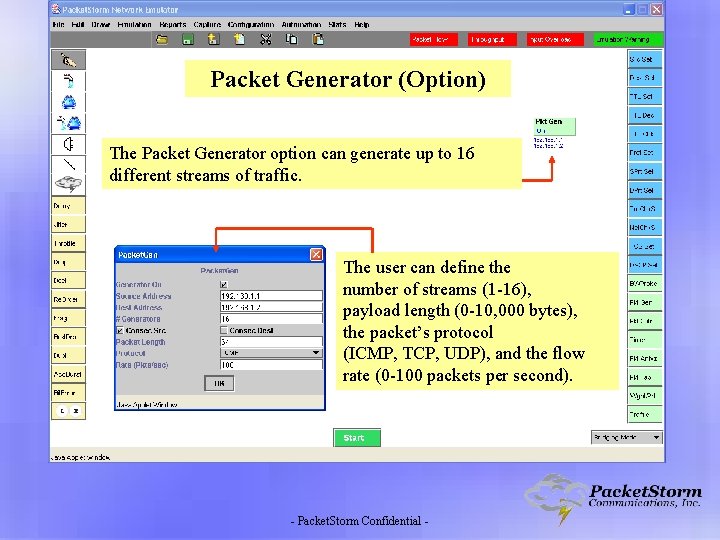
Packet Generator (Option) The Packet Generator option can generate up to 16 different streams of traffic. The user can define the number of streams (1 -16), payload length (0 -10, 000 bytes), the packet’s protocol (ICMP, TCP, UDP), and the flow rate (0 -100 packets per second). - Packet. Storm Confidential -

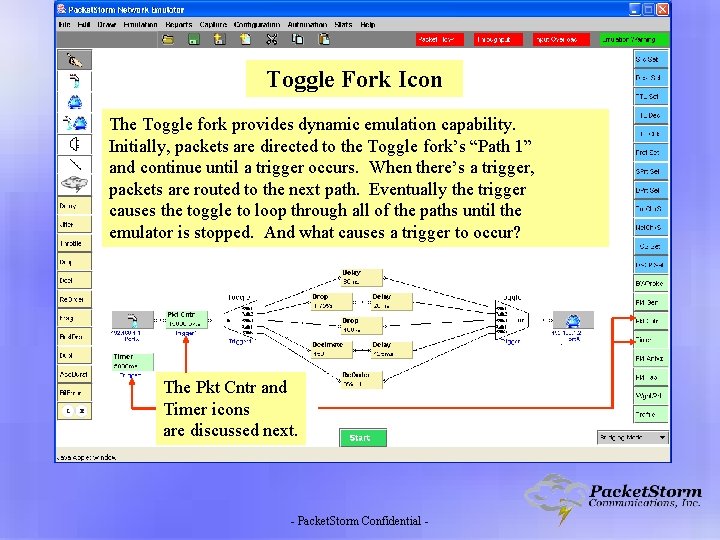
Toggle Fork Icon The Toggle fork provides dynamic emulation capability. Initially, packets are directed to the Toggle fork’s “Path 1” and continue until a trigger occurs. When there’s a trigger, packets are routed to the next path. Eventually the trigger causes the toggle to loop through all of the paths until the emulator is stopped. And what causes a trigger to occur? The Pkt Cntr and Timer icons are discussed next. - Packet. Storm Confidential -

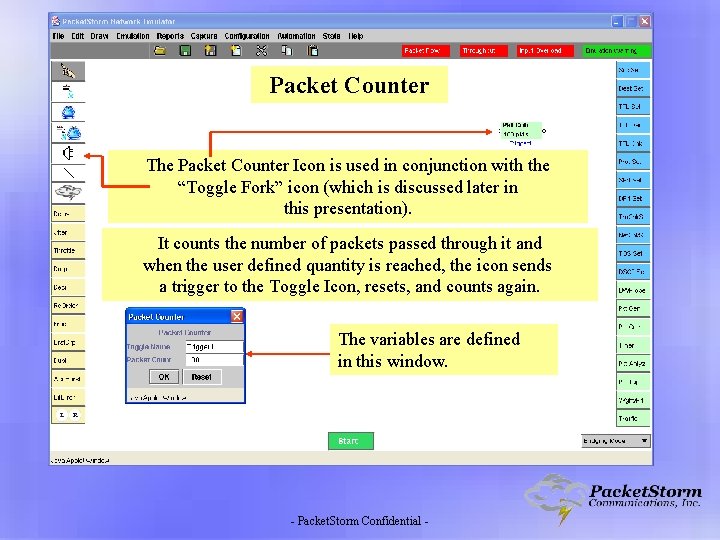
Packet Counter The Packet Counter Icon is used in conjunction with the “Toggle Fork” icon (which is discussed later in this presentation). It counts the number of packets passed through it and when the user defined quantity is reached, the icon sends a trigger to the Toggle Icon, resets, and counts again. The variables are defined in this window. - Packet. Storm Confidential -

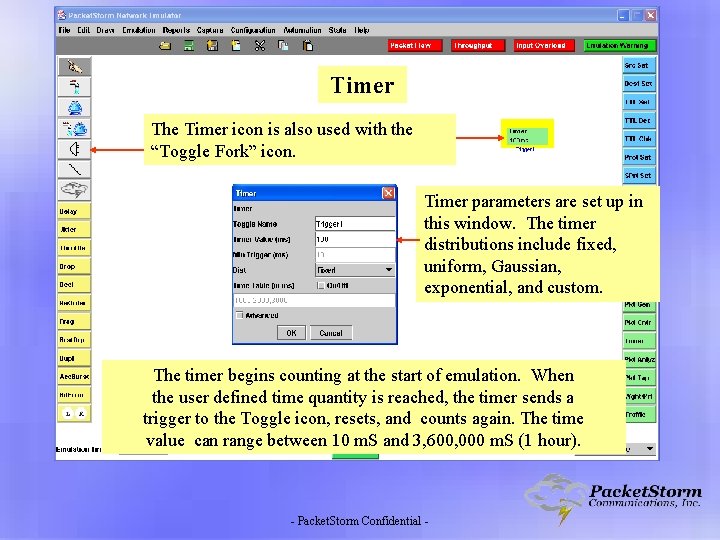
Timer The Timer icon is also used with the “Toggle Fork” icon. Timer parameters are set up in this window. The timer distributions include fixed, uniform, Gaussian, exponential, and custom. The timer begins counting at the start of emulation. When the user defined time quantity is reached, the timer sends a trigger to the Toggle icon, resets, and counts again. The time value can range between 10 m. S and 3, 600, 000 m. S (1 hour). - Packet. Storm Confidential -

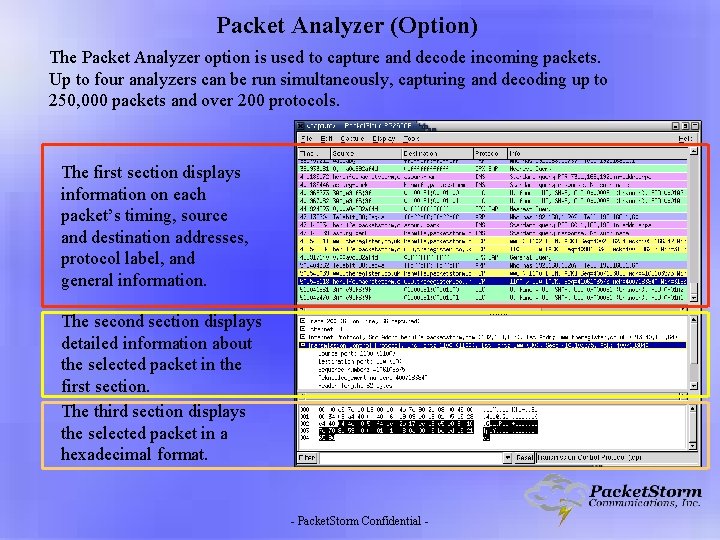
Packet Analyzer (Option) The Packet Analyzer option is used to capture and decode incoming packets. Up to four analyzers can be run simultaneously, capturing and decoding up to 250, 000 packets and over 200 protocols. The first section displays information on each packet’s timing, source and destination addresses, protocol label, and general information. The second section displays detailed information about the selected packet in the first section. The third section displays the selected packet in a hexadecimal format. - Packet. Storm Confidential -

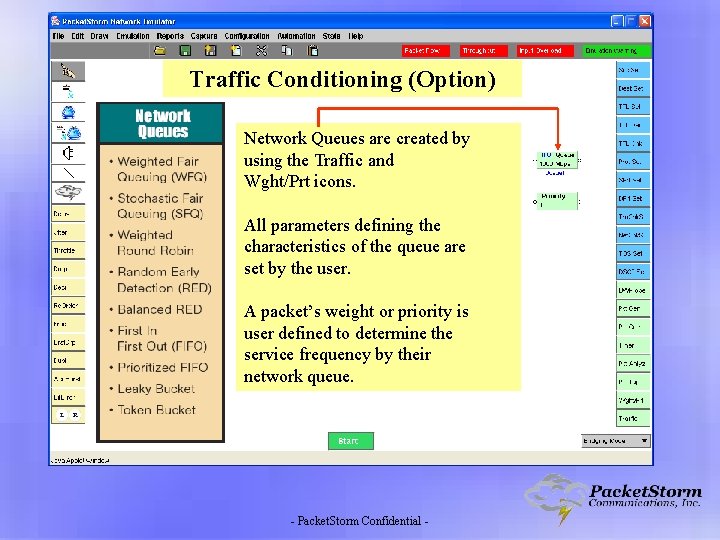
Traffic Conditioning (Option) Network Queues are created by using the Traffic and Wght/Prt icons. All parameters defining the characteristics of the queue are set by the user. A packet’s weight or priority is user defined to determine the service frequency by their network queue. - Packet. Storm Confidential -

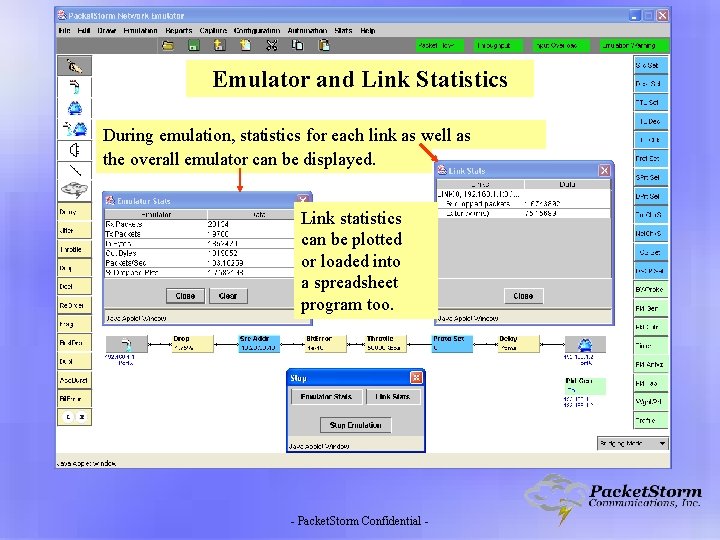
Emulator and Link Statistics During emulation, statistics for each link as well as the overall emulator can be displayed. Link statistics can be plotted or loaded into a spreadsheet program too. - Packet. Storm Confidential -

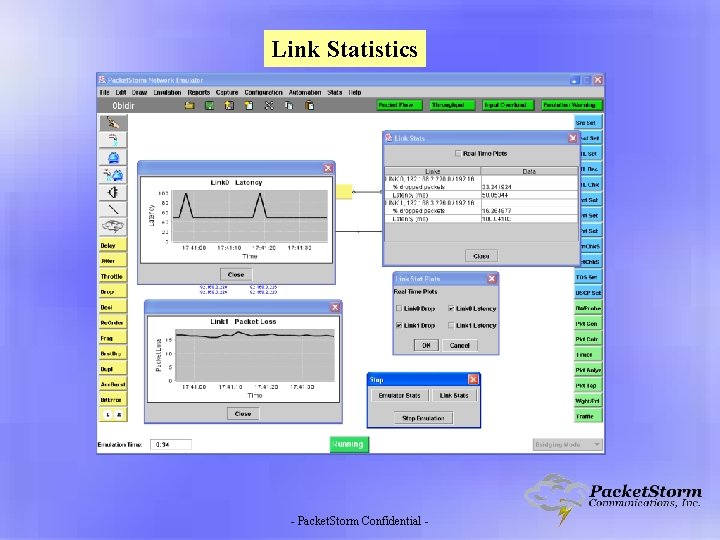
Link Statistics - Packet. Storm Confidential -

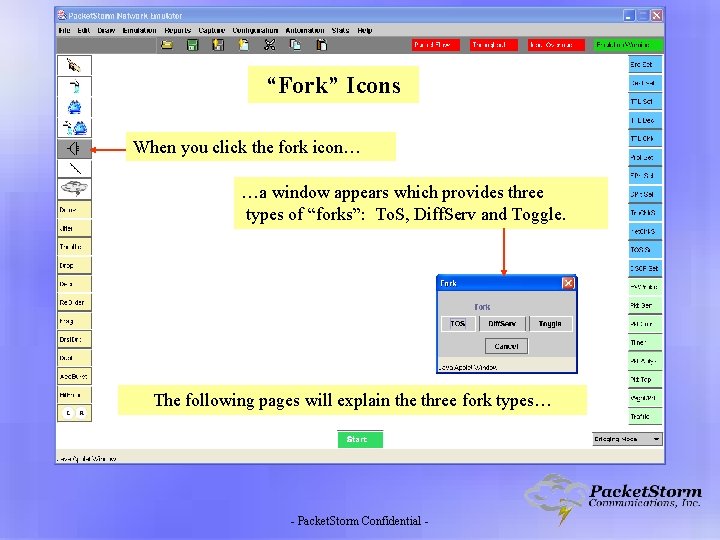
“Fork” Icons When you click the fork icon… …a window appears which provides three types of “forks”: To. S, Diff. Serv and Toggle. The following pages will explain the three fork types… - Packet. Storm Confidential -

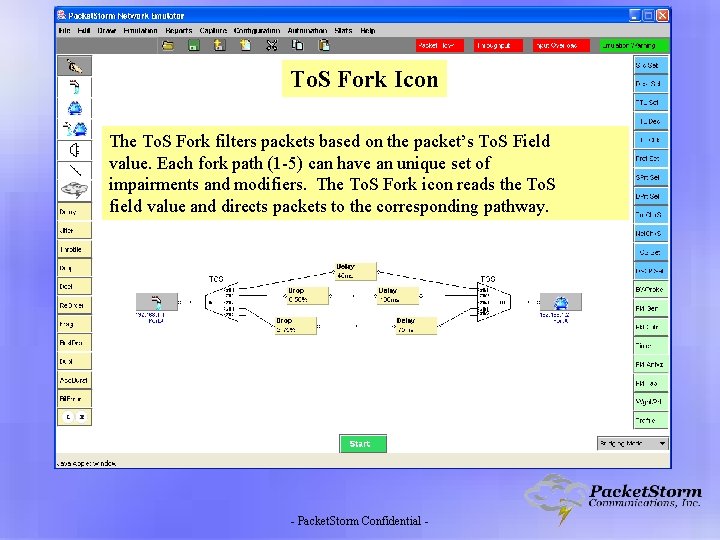
To. S Fork Icon The To. S Fork filters packets based on the packet’s To. S Field value. Each fork path (1 -5) can have an unique set of impairments and modifiers. The To. S Fork icon reads the To. S field value and directs packets to the corresponding pathway. - Packet. Storm Confidential -

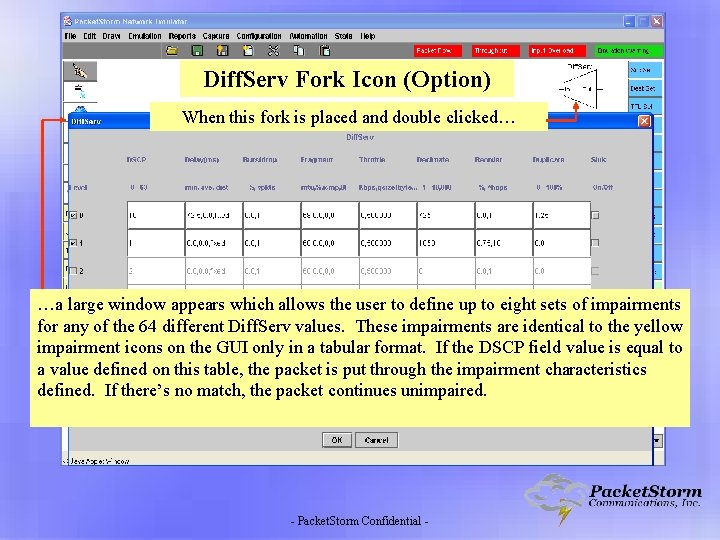
Diff. Serv Fork Icon (Option) When this fork is placed and double clicked… …a large window appears which allows the user to define up to eight sets of impairments for any of the 64 different Diff. Serv values. These impairments are identical to the yellow impairment icons on the GUI only in a tabular format. If the DSCP field value is equal to a value defined on this table, the packet is put through the impairment characteristics defined. If there’s no match, the packet continues unimpaired. - Packet. Storm Confidential -

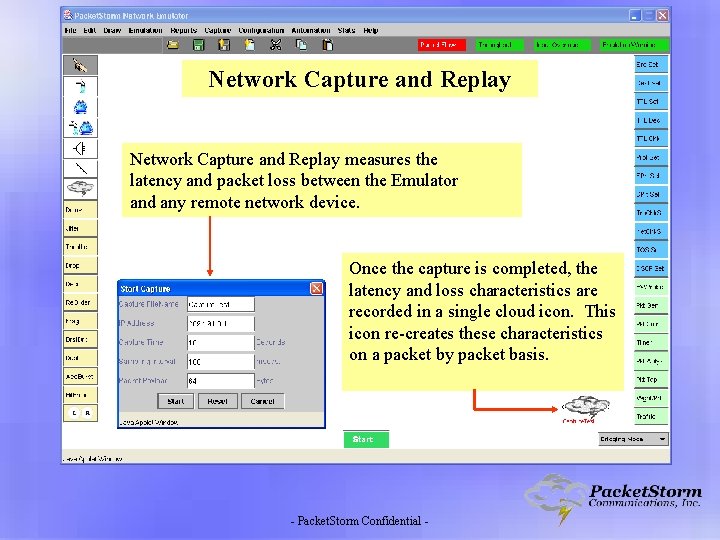
Network Capture and Replay measures the latency and packet loss between the Emulator and any remote network device. Once the capture is completed, the latency and loss characteristics are recorded in a single cloud icon. This icon re-creates these characteristics on a packet by packet basis. - Packet. Storm Confidential -

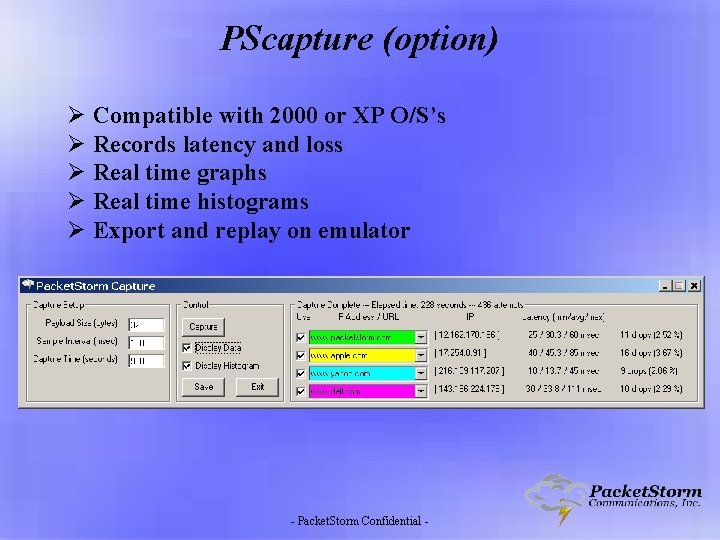
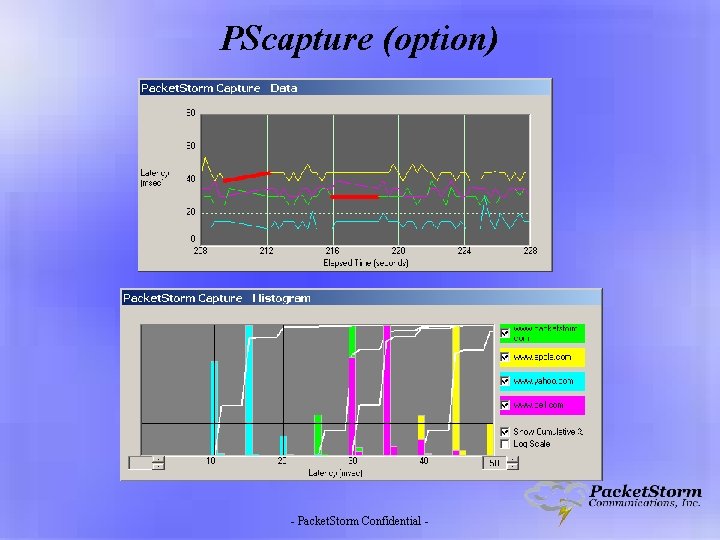
PScapture (option) Ø Compatible with 2000 or XP O/S’s Ø Records latency and loss Ø Real time graphs Ø Real time histograms Ø Export and replay on emulator - Packet. Storm Confidential -

PScapture (option) - Packet. Storm Confidential -

Other Features Data Capture & Replay (option) – regenerate packets from stored packet analyzer files Off-Line Configurator – Windows O/S software that allows user to create, save, and share configuration files without the emulator. Impair IP and non-IP – user selectable to impair ARP’s, propriety protocols, and other non-IP packets. GUI to tcl converter – converts GUI configuration file into tcl script for automation Multiple Interface Steering (option) – overrides routing mode for specific packets and allows broadcast capability to multiple ports - Packet. Storm Confidential -

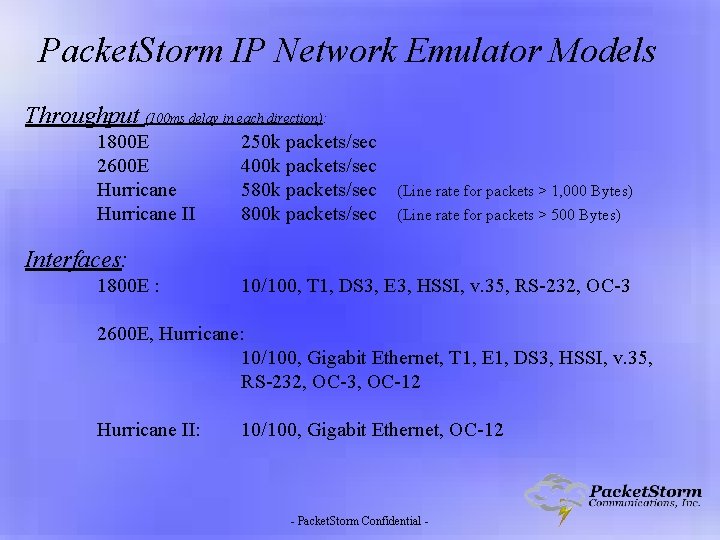
Packet. Storm IP Network Emulator Models Throughput (100 ms delay in each direction): 1800 E 2600 E Hurricane II 250 k packets/sec 400 k packets/sec 580 k packets/sec 800 k packets/sec (Line rate for packets > 1, 000 Bytes) (Line rate for packets > 500 Bytes) Interfaces: 1800 E : 10/100, T 1, DS 3, E 3, HSSI, v. 35, RS-232, OC-3 2600 E, Hurricane: 10/100, Gigabit Ethernet, T 1, E 1, DS 3, HSSI, v. 35, RS-232, OC-3, OC-12 Hurricane II: 10/100, Gigabit Ethernet, OC-12 - Packet. Storm Confidential -

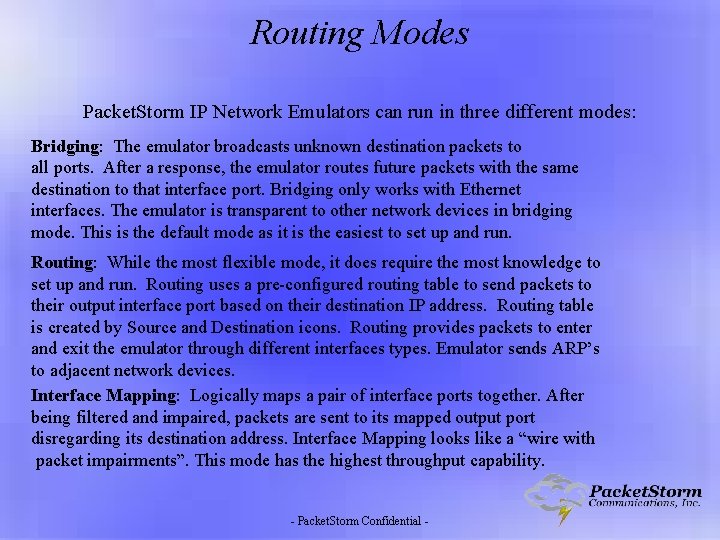
Routing Modes Packet. Storm IP Network Emulators can run in three different modes: Bridging: The emulator broadcasts unknown destination packets to all ports. After a response, the emulator routes future packets with the same destination to that interface port. Bridging only works with Ethernet interfaces. The emulator is transparent to other network devices in bridging mode. This is the default mode as it is the easiest to set up and run. Routing: While the most flexible mode, it does require the most knowledge to set up and run. Routing uses a pre-configured routing table to send packets to their output interface port based on their destination IP address. Routing table is created by Source and Destination icons. Routing provides packets to enter and exit the emulator through different interfaces types. Emulator sends ARP’s to adjacent network devices. Interface Mapping: Logically maps a pair of interface ports together. After being filtered and impaired, packets are sent to its mapped output port disregarding its destination address. Interface Mapping looks like a “wire with packet impairments”. This mode has the highest throughput capability. - Packet. Storm Confidential -

Operational Modes 1. Stand Alone: Allows the unit to be operated from a keyboard, mouse and video monitor connected directly to the connectors on the back of the chassis. 2. Browser Access: Using Microsoft Internet Explorer® or another browser, the emulator can be controlled by a remote computer via the network interface. This mode uses the same GUI. The Packet Analyzer isn’t supported remotely and is the only difference. 3. Tcl Access: Most functions of the Packet. Storm can be accessed via the Tcl Scripting language. A full Tcl Script library is included with every unit. (Note: Tcl Scripting does not support the Packet Analyzer option. ) - Packet. Storm Confidential -

Customer Oriented Policies §Great Customer Support Tier I and II Tcl Support Specialist § Trade-In Credit (75% in 1 st 12 months) § Free Upgrades with Warranty § Standard One Year Warranty - Packet. Storm Confidential -

Packet. Storm Communications History Packet. Storm was founded in 1998 by a team of Senior Engineers and Managers from the prestigious Bell Laboratories. The company shipped their first emulator in August, 2000 and continues to develop products that exceed the expectations of IP Developers and Network Managers around the world. Their world headquarters, located in Eatontown, New Jersey, handles product engineering, marketing and customer support. - Packet. Storm Confidential -

Some Of Packet. Storm’s Customers - Packet. Storm Confidential -

For More Information On the Complete Line of Packet. Storm IP Network Emulators Please Contact Your Packet. Storm Representative Packet. Storm Communications, Inc. 20 Meridian Drive Eatontown, New Jersey 07724 (732) 544 -2434 www. Packet. Storm. com - Packet. Storm Confidential -