An Introduction to Network Security Chapter 1 Introduction
































- Slides: 33

An Introduction to Network Security Chapter 1 Introduction 中国科学技术大学网络学院 李艺 E-Mail: LEEYI@USTC. EDU. CN Telephone: 0551 - 3606755


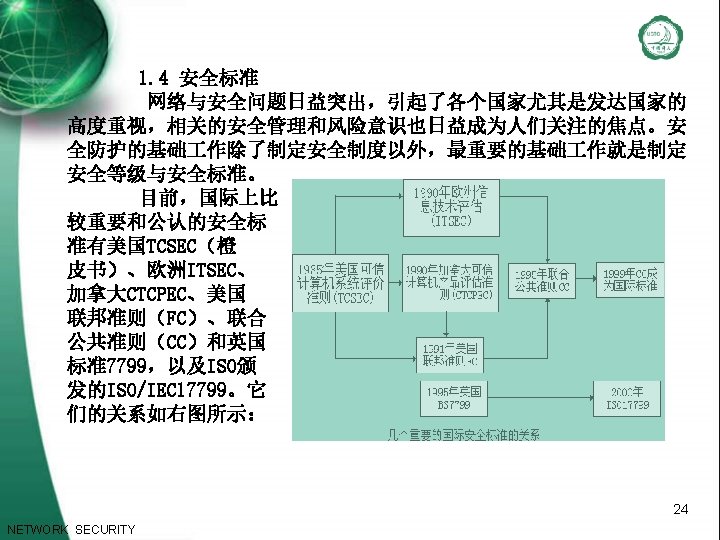
u 教材及参考文献: l 《信息安全概论》(ISBN 7 -5635 -0646 -2) 牛少鹏主编,北 京邮电大学出版社,2004年 l 《网络安全原理与应用》(ISBN: 7 -03 -011450 -7) 张世永 主编,科学出版社,2003年 l Making, Breaking Codes: An Introduction to Cryptology (ISBN 0 -13 -030369 -0) , le, by Paul Garrett l Cryptography and Network Security: principles and practice 2 nd ed. By William Stallings l 《初等数论》(第二版)闵嗣鹤,严士建编,高等教育出 版社,1982年 3 NETWORK SECURITY




Security Mechanisms安全机制 l Security Mechanisms 安全机制 n 用于检测和防止攻击、并在受到攻击后尽快恢 复的方法。 u a mechanism that is designed to detect, prevent, or recover from a security attack u no single mechanism that will support all functions required u however one particular element underlies(成为…的基础) many of the security mechanisms in use: cryptographic techniques u hence our focus on this area 7 NETWORK SECURITY

1. 1. 2 信息系统面临的威胁及分类 l 信息传输过程中的威胁: u 中断,interruption u 截获,interception u 篡改,modification u 伪造,fabrication 中断(干扰) Interruption 篡改 Modification data Source data Destination 正常流 Normal flow 截获(侦听) Interception 伪造 Fabrication 8 NETWORK SECURITY

Security Attacks l Security Attacks 安全攻击 u 使信息系统遭受破坏的任何行为 any action that compromises(危及) the security of information owned by an organization u information security is about how to prevent attacks, or failing that(受攻击而崩溃), to detect attacks on information-based systems u have a wide range of attacks u can focus of generic types of attacks u note: often threat & attack mean same 9 NETWORK SECURITY

l u u 主动攻击与被动攻击 Active Threads n Masquerade伪造 n Replay 重放 n Modification of Message n Denial of Service n Interrupt 被动攻击 Passive Threats 截取(保密性) Passive Threads n Release (泄露) of Message n Traffic Analysis 消息内容泄密 流量分析 主动攻击 Active Threats 中断 修改 伪造 (可用性) (完整性) (认证) 10 NETWORK SECURITY


1. 1. 3 威胁的表现形式 l 伪装(pseudonym) l 非法连接(illegal association) l 非授权访问(no-authorized access) l 拒绝服务(denial of service) l 抵赖(repudiation) l 信息泄露(leakage of information) l 通信流量分析(traffic analysis) l 改变信息流(invalid message sequencing) l 篡改或破坏数据(data modification or destruction) l 推断或演绎信息(deduction of information) l 非法篡改程序(illegal modification programs) 12 NETWORK SECURITY



1. 2. 1 网络安全模型 l 网络安全 Trusted third party e. g. , arbiter(仲裁人), distributor of secret information Principal 委托人 Principal Message Information Channel Message Secret information Security-related transformation Opponent 攻击者 Model for Network Security 15 NETWORK SECURITY

Model for Network Security l using this model requires us to: u design a suitable algorithm for the security transformation u generate the secret information (keys) used by the algorithm u develop methods to distribute and share the secret information u specify a protocol enabling the principals to use the transformation and secret information for a security service 16 NETWORK SECURITY

l 网络访问安全模型 Information System Computing Resources Opponent • human (e. g. , attacker) • software, (e. g. , virus, worm) (processor, memory, I/O) Access Channel Data Gatekeeper Function 门禁函数 Processes Software Internal security controls Network Access Security Model 17 NETWORK SECURITY

Model for Network Access(访问) Security l l using this model requires us to: u select appropriate gatekeeper functions to identify users u implement (执行) security controls to ensure only authorised users access designated information or resources trusted computer systems can be used to implement(执行 ) this model 18 NETWORK SECURITY

网络安全防范措施 l Encryption l Software Controls (access limitations in a data base, in operating system protect each user from other users) l Hardware Controls (smartcard) l Policies (frequent changes of passwords) 安全策略 l Physical Controls 19 NETWORK SECURITY













