An Introduction to Legal Issues Surrounding Social Media
















































- Slides: 57

An Introduction to Legal Issues Surrounding Social Media By Daliah Saper Law Offices, LLC 500 N Dearborn, Suite #1200 Chicago, IL 60610 http: //www. saperlaw. com

What is “Social Media”? Also referred to as “Web 2. 0” A category of sites that is based on user participation and user-generated content

Examples of Social Media n n n Linked. In: commonly used for business networking, job searches, and recruiting Facebook and My. Space: commonly used for friends to keep in touch with each other, users can post what is on their minds for friends to read Twitter: Users post “tweets” up to 140 characters that answer “what are you doing right now? ”

New legal issues as a result: n n n n Employees freely copying what they see on the internet; Posting of inappropriate or offensive content on company bulletin boards or blogs; Discrimination in hiring employees through internet job postings; Badmouthing a company on personal blogs; Using facebook, myspace, etc. to discriminate against or to harass fellow employees; Employees’ expectations of privacy on their office computers or in their e-mail, social media profiles; Requirements for backing up electronic communications in the event of litigation; and Electronic communications policies.

Today’s Seminar will broadly cover: n n n n Liability of Employers Privacy of Employee v Rights of Employer Utilizing & Protecting Intellectual Property: ¨ Buying a personal brand ¨ Copyrights (DMCA, DPRA), ¨ Trademarks, ¨ Trade Secrets Liability of ISPs (CDA) Social Media and Rules of Evidence SPAM act FTC advertising Rules Counseling Employers

What can your clients sue or be sued for? 1. Defamation: and false light family of claims 2. Privacy: publication of private facts, HIPPA violations 3. Interference with Business Relations 4. Negligence: assuming a duty, not following through. 5. Contract: ending up in an enforceable agreement. 6. Trademark: confusing consumers about a brand. 7. Copyright: using/sharing something that’s not yours. 8. Sexual Harassment: unwanted postings 9. Discrimination: especially as to hiring practices

Take away In most cases, traditional laws will apply to the online context…BUT n Finding the defamer or infringer requires extra steps. n Also, explaining context (ie what is a blog, a tweet, etc) may impact legal arguments and rules of evidence n

Daliah’s Case Examples n n n Rate my Professor. Com (finding name of poster, petition) Don’t Date Him Girl. Com (jurisdiction issues) Jaeger v. Okon (what is a blog? ) Paula Bonhomme v JSJ (IIED, Fraud, Defamation) Personal Trainer’s Website (copyright infringement, rights of publicity)

Privacy n Are postings on social media sites private? n A public posting on a public site is generally not private n A posting may be private if it is on a password protected site, or the poster has high security settings that prevent outside users from viewing the site ( Secured Communications Act)

Privacy n Can an employer check up on employees through social media? n Yes, with some limitations n Employers can check Linked. In to verify information supplied by an applicant or employee on previous work history. n Employers can check Twitter, Facebook, My. Space, etc. for postings that may be viewed as harassment of other employees or if an employee who called in sick is really out partying n Employers cannot use information found on social medial to discriminate against employees or candidates due to race, religion, sexual orientation or other protected class. (Better have screening policy in place)

Privacy n Whether an individual’s constitutional right to privacy has been violated depends first on a determination whether that individual had a personal and objectively reasonable expectation of privacy which was infringed. n There remains no established method for determining when an expectation of privacy is reasonable.

Privacy: public sites Moreno v. Hanford Sentinel, Inc. (2009) , Cal. App. 4 th n n n Moreno posts a poem about how much she hates her home town. Principal of her hometown high school sees it and submits it to the local paper. Her family is ruined. The court found no reasonable expectation of privacy because the essay was published on her public My. Space profile. BUT—they did allow a count for IIED to survive.

Konop v. Hawaiian Airlines, Inc. , 302 F. 3 d 868, 890 (9 th Cir. 2002), n Plaintiff Konop created a list of Hawaiian Airlines employees who were eligible to access his website, which contained critical comments about the airline’s management. “To gain access, one had to enter an eligible employee’s name, create a password, and click ‘SUBMIT’ indicating acceptance of the terms and conditions, which prohibited users from disclosing the website’s contents and prohibited viewing by Hawaiian Airlines management. ” n The Court of Appeals held that the employer's secret monitoring of a password-protected website could be a violation of the federal Stored Communications Act. Because the employee's passwordprotected website concerned union activity, the court ruled that the employer also may have violated the Railway Labor Act by retaliating or spying.

Pietrylo v. Hillstone Restaurant Group n In New Jersey, terminated employees are alleging that their employee unlawfully accessed their private My. Space group, used to rant about their restaurant workplace beyond the prying eyes of a supervisor. The employer gained access by demanding one employee's username and password, which she turned over for fear of being fired. n Is there a reasonable expectation of privacy in a group that requires an invitation and password access? Konop seems to say so. This case will likely turn on the issue of coercion. A "user" of a private website has a right to grant access to a third party, but what if that access is granted under duress or coercion?

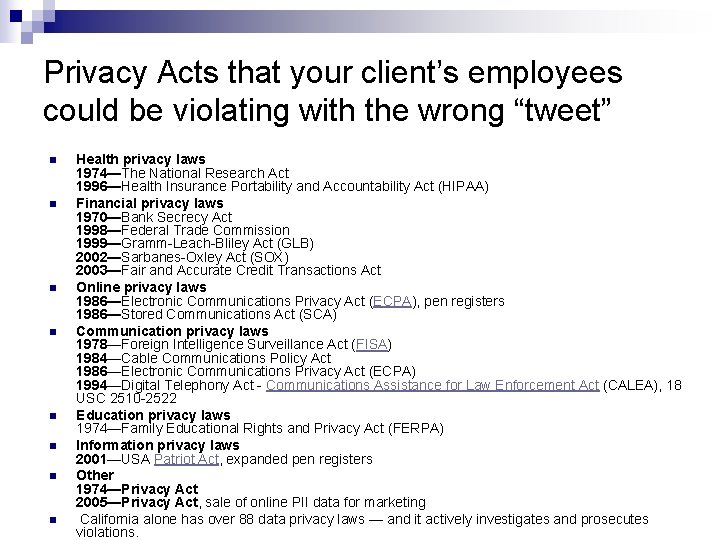
Privacy Acts that your client’s employees could be violating with the wrong “tweet” n n n n Health privacy laws 1974—The National Research Act 1996—Health Insurance Portability and Accountability Act (HIPAA) Financial privacy laws 1970—Bank Secrecy Act 1998—Federal Trade Commission 1999—Gramm-Leach-Bliley Act (GLB) 2002—Sarbanes-Oxley Act (SOX) 2003—Fair and Accurate Credit Transactions Act Online privacy laws 1986—Electronic Communications Privacy Act (ECPA), pen registers 1986—Stored Communications Act (SCA) Communication privacy laws 1978—Foreign Intelligence Surveillance Act (FISA) 1984—Cable Communications Policy Act 1986—Electronic Communications Privacy Act (ECPA) 1994—Digital Telephony Act - Communications Assistance for Law Enforcement Act (CALEA), 18 USC 2510 -2522 Education privacy laws 1974—Family Educational Rights and Privacy Act (FERPA) Information privacy laws 2001—USA Patriot Act, expanded pen registers Other 1974—Privacy Act 2005—Privacy Act, sale of online PII data for marketing California alone has over 88 data privacy laws — and it actively investigates and prosecutes violations.

Privacy n What employers need to think about ¨ Who owns the computer/blackberry/social media account being used? ¨ Where are the messages stored? ¨ What network are the messages traveling through? ¨ Are the messages being sent on employer time? ¨ Does the employee affiliate with Employer in his messages or use a pseudonym?

Intellectual Property- © n Who owns the Copyright to material posted on Social Media? n n The original author owns the copyright to their posts on Social Media. If someone is hired to promote a product to friends or other users on Social Media, the Work For Hire doctrine will apply, and it is best to clarify ownership in the contract. However, it should be considered that many postings may not meet the minimally creative threshold and therefore may not have Copyright protection. (Facebook Status updates? Twitter updates? ) There may be Copyright protection for a compilation of postings on a social media site.

Digital Millennium Copyright Act (DMCA) n The DMCA established that certain Web casts are exempt from securing performance rights, or really any rights, so long as they meet certain criteria. n DMCA Title II, the Online Copyright Infringement Liability Act ("OCILLA"), creates a safe harbor for online service providers against copyright liability.

What is a service provider? n What defines a service provider under the DMCA? An entity offering transmission, routing, or providing connections for digital online communications, between or among points specified by a user, of material of the user's choosing, without modification to the content of the material as sent or received. OR ¨ A provider of online services or network access, or the operator of facilities thereof. ¨ n Includes network services companies such as Internet service providers (ISPs), search engines, bulletin board system operators, and even auction web sites.

Service Provider Protection n How does a service provider qualify for protection? ¨ In addition to informing its customers of its policies, a service provider must follow the proper notice and takedown procedures and also meet several other requirements in order to qualify for exemption under the safe harbor provisions. ¨ Make sure your clients sign up with copyright office indicating the “registered agent”

Takedown Example n Here's an example of how the takedown procedures work: ¨ ¨ ¨ Alice puts a copy of Bob's song on her My. Space page. Bob, searching the Internet, finds Alice's copy. Charlie, Bob's lawyer, sends a letter to My. Space's designated agent including: n n n ¨ ¨ Contact information. The name of the song that was copied. The address of the copied song. A statement that he has a good faith belief that the material is not legal. A statement that, under penalty of perjury, Charlie is authorized to act for the copyright holder. His signature. My. Space takes the song down. My. Space tells Alice that they have taken the song down.

Takedown Example continued ¨ Alice now has the option of sending a counter-notice to My. Space, if she feels the song was taken down unfairly. The notice includes: n n n Contact information. Identification of the removed song. A statement under penalty of perjury that Alice has a good faith belief the material was mistakenly taken down. A statement consenting to the jurisdiction of Alice's local US Federal District Court, or, if outside the US, to a US Federal District Court in any jurisdiction in which My. Space is found. Her signature. My. Space then waits 10 -14 business days for a lawsuit to be filed by Bob. ¨ If Bob does not file a lawsuit, then My. Space may put the material back up. ¨

Intellectual Property- TM, ® n Trademarks ¨ There may be liability for creating a user name that confuses other users about your relationship to a Trademark owner, or dilutes a trademark owners brand ¨ There may also be liability for use of another’s mark in Google Adwords, Keywords, Metatag usage. ¨ Domain Name Disputes, Icann Proceedings, etc.

Twitter Parody or TM Infringement/Identify Theft? Trademark Infringement on Twitter ¨ ¨ ¨ Danyelle Freeman is a restaurant critic for The New York Daily News using the name “Restaurant Girl. ” Adam Robb Rucinsky uses Freeman’s writing style and Freeman’s name “Restaurant Girl” for a writing exercise using Twitter and a blog. Freeman is claiming that Rucinsky’s Twitter account and blog impersonating Freeman is infringing on her trademark name. The question is whether readers would be able to tell whether they are reading Freeman’s or Rucinsky’s blog, despite his recent disclaimers on Rucinsky’s Twitter and blog accounts. Does Rucinsky have a valid parody defense?

Name Squatting n User name squatting is against the Twitter Rules Name squatting and "user name for sale" accounts will be permanently suspended. Attempts to sell or extort other forms of payment in exchange for user names will result in account suspension. Accounts that are inactive for more than 6 months may be removed without further notice. Twitter is not currently releasing inactive/squatter accounts unless in cases of infringement. (Hint: no updates/profile image on an account or no intent to mislead usually = no infringement. )

Intellectual Property- Trade Secrets n Trade Secrets ¨ Trade Secrets can easily be leaked on Social Media, often inadvertently ¨ An employee leaking Trade Secrets has breached the duty of loyalty, misappropriation of Trade Secrets, breach of contractual confidentiality, or non-disclosure agreements, which can be grounds for termination.

Intellectual Property- Trade Secrets n What happens if Trade Secret is leaked? ¨ Trade Secret protection is based on “reasonable efforts” to keep information secret ¨ Once a Trade Secret is leaked by an employee, it is fair game ¨ Exit Interviews! Remind leaving employees they cannot spill your secrets!

Communications Decency Act n Provides immunity from liability for providers and users of an "interactive computer service" who publish information provided by others n No provider or user of an interactive computer service shall be treated as the publisher or speaker of any information provided by another information content provider. n Protection for service providers against liability for users’ defamatory statements n Enhances free speech by making it unnecessary for ISPs and other service providers to unduly restrict customers' actions for fear of being found legally liable for customers' conduct.

Communications Decency Act n In analyzing the availability of the immunity offered by this provision, courts generally apply a three-prong test. A defendant must satisfy each of the three prongs to gain the benefit of the immunity: 1. The defendant must be a "provider or user" of an "interactive computer service. “ 2. The cause of action asserted by the plaintiff must "treat" the defendant "as the publisher or speaker" of the harmful information at issue. 3. The information must be "provided by another information content provider, " i. e. , the defendant must not be the "information content provider" of the harmful information at issue.

DMCA in the Real World n Ning. com ¨ Ning is a website that allows users to create their own social networking sites within the Ning network. ¨ Multimedia content was posted on a Ning page by a user that did not have the permission of the owner of the copyright in that content. ¨ Ning is immune from liability for copyright infringement. n You. Tube ¨ Hundreds of videos uploaded to You. Tube infringe copyrights ¨ You. Tube, due to the DMCA safe harbor provisions, is not liable for the infringing videos shared by its users. (FOR NOW…. )

CDA in the Real World n Wiki ¨ A wiki is a collection of web pages designed to enable anyone who accesses it to contribute or modify content. ¨ The provider of a Wiki page cannot be held accountable for defamatory statements posted to the page by a user n Facebook, Twitter, Ning, etc. ¨ Each of these social networking sites are entitled to immunity from liability brought about by users’ libel statements.

CDA in the Real World n Chicago Lawyers' Committee For Civil Rights Under Law, Inc. v. Craigslist, Inc. ¨ n Doe v. My. Space ¨ n CDA immunity applied to Craiglist on Fair Housing Act claims based on discrimination in postings Social networking site immune from negligence and gross negligence liability for failing to institute safety measures to prevent sexual assaults of minors and failure to institute policies relating to age verification Gentry v. e. Bay, Inc. ¨ CDA immunity applied to e. Bay for claims based on forged autograph sports items purchased

Twitter is not liable but your client or client’s company can be n Twitter’s Fist Libel Suite: Simorangkir v. Love • Courtney Love made angry tweets against her former fashion designer • Designer, Down Simorangkir, filed claim against Love in CA • tweets accused the designer of… • a history of dealing cocaine • losing custody of her child • being guilty of assault and burglary • A nasty, lying hosebag thief n Marc Cuban: • the NBA fined $25, 000 for his criticism of referees on Twitter • after a game Cuban questioned why a technical foul wasn’t called on a player for taunting

Evidence and Social Media Generally, any postings online should be considered the same as email or text messages. This information is discoverable and can lead to liability.

Case Examples: Facebook profiles admitted into evidence n n n Joshua Lipton, 21, posted a photo of himself on Facebook jokingly wearing an orange prison jumpsuit during a Halloween party. Rhode Island Assistant Attorney General Jay Sullivan displayed the photo in court as part of a Power. Point presentation with the title "Remorseful? " Superior Court Judge Daniel Procaccini focused in part on the photo when deciding to sentence Lipton to two years in state prison for his DUI. Andrea Panciera, "Facebook Photo Plays Role In DUI Accident Sentencing, " Providence J. , May 27, 2008. Lara Buys, 22, on trial in Santa Barbara County, Calif. , Superior Court, received two years in prison after posting pictures on the Internet of herself drinking and partying just months after causing the death of her best friend in a drunken driving accident. Melissa Evans, "Internet Plays Key Role in Vehicular Manslaughter Sentence, " Santa Barbara Newsroom, April 14, 2007. Jessica Binkerd, 22, was sentenced to five years by Santa Barbara Superior Court Judge Brian Hill for a fatal DUI accident. During the trial, Binkerd was advised by her defense attorney, Steve Balash, to remove incriminating photos of herself on her My. Space profile page. She neglected to do so. "Unrepentant on Facebook? Expect Jail Time, " July 20, 2008, CNN. com.

Horizon Blue Cross Blue Shield of New Jersey n BCBS was sued for not covering medical claims for anorexia and bulimia. The court is allowing Facebook posts to be entered into evidence showing plaintiff’s statements concerning their eating disorders. The judge weighed the fact that the Facebook page was only available to 6 people against the teenage girls not being deposed.

CAN-SPAM ACT of 2003 n Employer/Clients can be liable for anti-spam violations due to Tweets ¨ The CAN-SPAM Act of 2003 – regulates unsolicited e-mail otherwise known as ‘junk mail’ ¨ Enforced by the FTC

SPAM continued ¨ Under the act businesses of all sizes can be held liable for SPAM mail ¨ To Comply with the act… Keep your e-mail header honest n Don’t Mislead with Your Subject Lines n Provide an Unsubscribe or Opt-Out Method n

Spam Continued n Compliance continued: n Honor and Manage all Unsubscribe requests n List Privacy- it’s illegal to sell or distribute the email addresses of people who have chosen to unsubscribe from your emails to another entity seeking to send email to that party n Include a Physical Mailing Address– all commercial e-mail must contain your business’ full physical mailing address

Spam continued Non-compliance results in blacklisting of e-mail domain by ISPs at the request of your customers or recipients of SPAM mail ¨ Can chose to block sender or report SPAM at the click of a button n Blacklisting means e-mail won’t reach those who want to read the e-mail n

Spam Continued n n If a company hires an employee for their following on Twitter, and then the employee tweets ads for the company, these tweets maybe considered SPAM, and thus the company may endure liability under the CANSPAM Act Or, if the company uses Twitter for advertising and other business purposes and sends tweets to those who have not registered as a follower the company may incur liability for SPAM

Spam continued ¨ Twitter does have its own internal SPAM monitoring in place. Twitter looks for accounts that do not receive responses and will block accounts that are suspected of Spamming ¨ One way to Spam well is to personalize tweets so that the person advertising a product has a personal connection with the recipient.

Online Advertising n FTC Guidelines for online Advertising ¨ FTC Act’s prohibition on “unfair or deceptive acts or practices” broadly covers advertising claims, marketing and promotional activities, and sales practices in general. n The Act is not limited to any particular medium. Thus, applies to internet

FTC ¨ Rules prohibit specific acts or practices that the FTC has found to be unfair or deceptive ¨ Guidelines help businesses to comply with the law by providing examples or direction on how to avoid unfair or deceptive acts or practices n Find guidelines for ads at…http: //www. ftc. gov/bcp/edu/pubs/business/ecommer ce/bus 41. pdf

FTC ¨ When it comes to online ads, the basic principles of advertising law apply: n Advertising must be truthful and not misleading n Advertisers must have evidence to back up their claims n Advertisements cannot be unfair ¨ Must look at the ad as a whole

FTC n Tweets, Facebook and other social media can qualify as endorsements and testimonials in advertising and therefore can be subject to FTC rules and guidelines n Rules on: Consumer endorsements ¨ Expert endorsements ¨ Endorsements by organizations ¨ n FTC Guides Concerning Use of Endorsements and Testimonials in Advertisements: http: //www. ftc. gov/bcp/guides/endorse. htm

FTC n The FTC is proposing new Guidelines for Online marketing and will vote on policies this summer ¨ The FTC is suggesting that bloggers and social media marketers who use false statements about products they promote will be held liable. ¨ Stay tuned for more updates this summer

What Employers Need to Consider n What are employees doing now? n What policies should be adopted? n What is at risk?

What Employers Need to Consider Employers should examine the activity of employees online to assess if there is a problem with information being leaked, or inappropriate messages being posted. n You would be amazed at what employees post online n

What Employers Need to Consider n Examples of “famous” tweets: ¨ "Cisco just offered me a job! Now I have to weigh the utility of a fatty paycheck against the daily commute to San Jose and hating the work. " ¨ Ketchum public-relations exec who said of client Fed. Ex's hometown: "I would die if I had to live here!"

What Employers Need to Consider n Right now there are several different stances employers can take on Social Media: ¨ Tell employees they are not allowed to discuss anything work related online ¨ Counsel employees on what is appropriate, how to use better judgment, and if confused, talk to a manager ¨ Designating a gatekeeper to be responsible for posts online or on the employer’s website, instead of any employee posting anything, anytime

What Employers Need to Consider n How will employees react? ¨ Consultants are advising employers not to be oppressively strict ¨ Employees react negatively when told they cannot do something ever!

What Employers Need to Consider n n Have a company policy for e-mail, internet usage and other social media ¨ Internet usage policies should be updated to accommodate changes in technology Have filters/blockers on the company’s network Counsel employees on appropriate postings and the consequences of inappropriate postings Counsel employees on appropriate and inappropriate use of company equipment, i. e. computers, cell phones, and blackberries

What Employers Need to Consider n The Employee Handbook ¨ Many companies are updating the employee handbook to clearly address what is permissible in Social Media, and what is not. Companies are also addressing the ramifications if employees don’t comply, i. e. probation or termination

What Employers Need to Consider n Do you want to monitor employees closely? This can be a costly and a time consuming endeavor, but these costs could be minimal compared to the leak of Trade Secrets, or Confidential Customer Lists. ¨ This could be monitored through the IT department. ¨ n Another consideration: employees can post on Twitter through cell phones and blackberries, bypassing internal networks and internal safeguards.

What Employers Need to Consider n Employees can tweet a message in just seconds, without realizing the consequences of that tweet ¨ Counsel employees on using their best judgment and common sense ¨ Counsel employees on how bad it looks when they tweet about their hang over

Questions? n Saper Law Contact Info: Daliah Saper 500 N Dearborn, Suite 1200 Chicago, IL 60654 312. 527. 4100 www. saperlaw. com
 Social issues in information technology
Social issues in information technology What ethical issues surrounding executive compensation
What ethical issues surrounding executive compensation Legal, ethical and societal issues in media and information
Legal, ethical and societal issues in media and information State legal, ethical and professional aspects of security.
State legal, ethical and professional aspects of security. Legal implications of social media
Legal implications of social media Big data privacy issues in public social media
Big data privacy issues in public social media Legal and ethical issues in use of ict
Legal and ethical issues in use of ict What is ethical issues in e commerce
What is ethical issues in e commerce Legal and ethical issues in computer security
Legal and ethical issues in computer security Professional and ethical issues during internship
Professional and ethical issues during internship Chapter 2 ethical and legal issues
Chapter 2 ethical and legal issues Chapter 3 medical legal and ethical issues
Chapter 3 medical legal and ethical issues Legal and ethical issues chapter 3
Legal and ethical issues chapter 3 Legal issues in performance appraisal
Legal issues in performance appraisal Legal issues in hrm
Legal issues in hrm Attack sophistication vs intruder technical knowledge
Attack sophistication vs intruder technical knowledge Legal and ethical issues chapter 5
Legal and ethical issues chapter 5 Legal issues in sport/event marketing match-up
Legal issues in sport/event marketing match-up Chapter 3 legal and ethical issues
Chapter 3 legal and ethical issues Reward system and legal issues
Reward system and legal issues Legal issues in nursing practice
Legal issues in nursing practice Legal issues in computer science
Legal issues in computer science Legal issues in special education
Legal issues in special education Chapter 6 legal and ethical issues
Chapter 6 legal and ethical issues Chapter 5 legal and ethical responsibilities
Chapter 5 legal and ethical responsibilities Legal and ethical aspects in nursing
Legal and ethical aspects in nursing Ethical and legal issues chapter 2
Ethical and legal issues chapter 2 Ethical and legal issues chapter 2
Ethical and legal issues chapter 2 Ch 5 legal and ethical responsibilities
Ch 5 legal and ethical responsibilities Ethical and legal issues affecting the nursing assistant
Ethical and legal issues affecting the nursing assistant What is the difference between ethical and legal issues
What is the difference between ethical and legal issues Ethical and legal issues in community health nursing
Ethical and legal issues in community health nursing Legal issues in psychiatric nursing
Legal issues in psychiatric nursing Legal and ethical issues chapter 5
Legal and ethical issues chapter 5 Chapter 2 ethical and legal issues
Chapter 2 ethical and legal issues Legal regulatory and political issues
Legal regulatory and political issues Nursing legal terms
Nursing legal terms Legal and ethical issues in information security
Legal and ethical issues in information security Legal issues in international business
Legal issues in international business Based on a true story legal issues
Based on a true story legal issues Ict legal issues
Ict legal issues Chapter 6 legal and ethical issues
Chapter 6 legal and ethical issues Chapter 6 legal and ethical issues
Chapter 6 legal and ethical issues Medical legal and ethical issues chapter 3
Medical legal and ethical issues chapter 3 Characteristics of people media
Characteristics of people media Introduction about social media
Introduction about social media Introduction about social media
Introduction about social media Introduction to social media
Introduction to social media Landforms of ancient greece
Landforms of ancient greece Italy border countries
Italy border countries Countries surrounding brazil
Countries surrounding brazil Surrounding net
Surrounding net Surrounding
Surrounding Surrounding
Surrounding Chapter 5 the skeletal system axial skeleton skull
Chapter 5 the skeletal system axial skeleton skull Chapter 5 the skeletal system figure 5-10
Chapter 5 the skeletal system figure 5-10 A thin layer of gases surrounding earth
A thin layer of gases surrounding earth How geographers look at the world
How geographers look at the world













































































