An Introduction to Cybercrime Presented By Brian Nienhaus

An Introduction to Cybercrime Presented By: Brian Nienhaus

Introduction �What is cybercrime? �Running a cybercrime syndicate �Cybercrime attacks �Countermeasures �Organization profiles

Cybercrime at a Glace Who, Where, When, Why
![Food for Thought �“The degree of overlap between [organized crime and cybercrime] is likely Food for Thought �“The degree of overlap between [organized crime and cybercrime] is likely](http://slidetodoc.com/presentation_image_h/84b219fa1b2af726331099855fb4c567/image-4.jpg)
Food for Thought �“The degree of overlap between [organized crime and cybercrime] is likely to increase considerably in the next few years. This is something that needs to be recognized by business and government as an emerging and very serious threat to cyber-security. ”

Cybercrime at a Glance § Cybercrime is…? § “offenses ranging from criminal activity against data to content and copyright infringement” (Council of Europe’s CC Treaty) § United Nations refers to acts of fraud, forgery and unauthorized access § “…unlawful acts wherein the computer is either a tool or a target or both. ”.

Appeal § § The Internet encourages anonymity and is distributed in nature Many countries have very few laws addressing cybercrime § Love Bug Virus § VB script that spread via email and corrupted many different file types § FBI traced the virus to the Philippines § The increasing growth of e-commerce
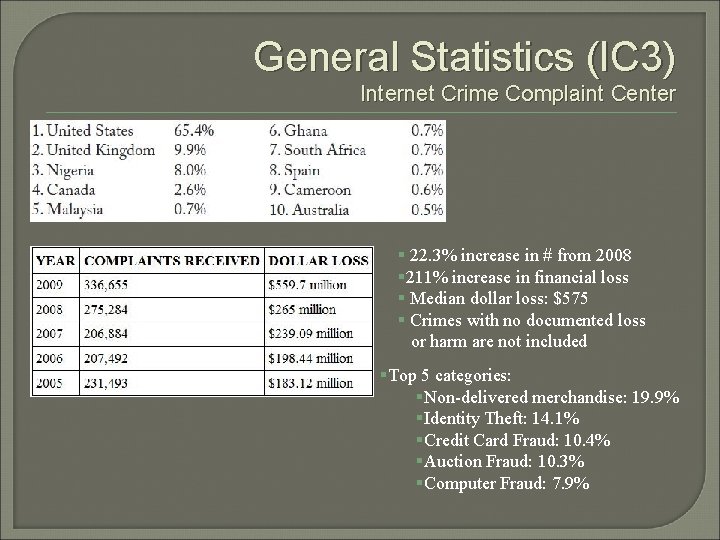
General Statistics (IC 3) Internet Crime Complaint Center § 22. 3% increase in # from 2008 § 211% increase in financial loss § Median dollar loss: $575 § Crimes with no documented loss or harm are not included §Top 5 categories: §Non-delivered merchandise: 19. 9% §Identity Theft: 14. 1% §Credit Card Fraud: 10. 4% §Auction Fraud: 10. 3% §Computer Fraud: 7. 9%
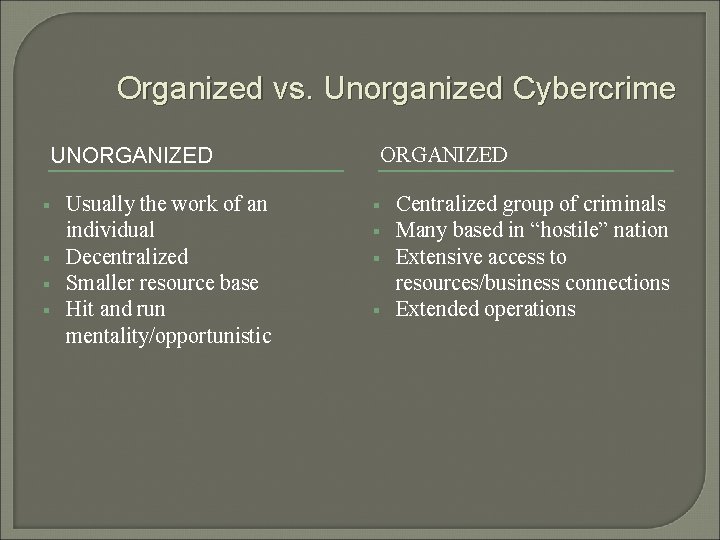
Organized vs. Unorganized Cybercrime UNORGANIZED § § Usually the work of an individual Decentralized Smaller resource base Hit and run mentality/opportunistic ORGANIZED § § Centralized group of criminals Many based in “hostile” nation Extensive access to resources/business connections Extended operations

Organized Cybercrime

Script Kiddies Crime Bosses The Paradigm Shift from “Hack for Fame” to “Cybercrime for Profit” § § § Hackers discover vulnerabilities and sell to the highest bidder Crimeware suites created and sold to less technically inclined users Crimeware-as-a-service mentality Data supplier model Pricing profiles introduced § Credits cards = cheap § Healthcare info/single logins for organizations = expensive § Cybercrime economy mirrors actual economy
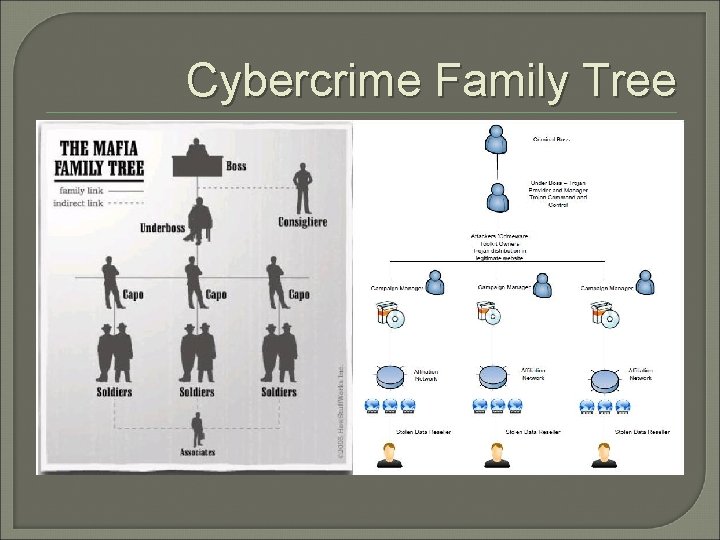
Cybercrime Family Tree

Criminal Economics 101 § Organized crime closely mimics the actual economy § Regionally-specific & enterprise-specific campaign § Each attack campaign gathered centrally to sell § Campaigns managed remotely from these central servers § Data and asset management is just as essential as in traditional business
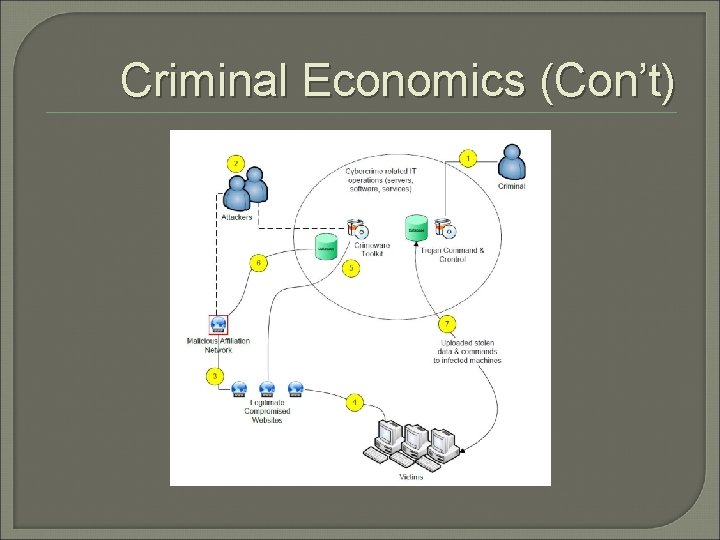
Criminal Economics (Con’t)

Criminal Economics (Con’t) § § § § (1) Boss deploys malicious code package (2) Campaign managers retrieve package and customized as needed (3) Malicious network used to inject package into legitimate sites. Commission-based (4) Injected code served to users (5) Toolkit affects individual users (6) Infection data sent back to central location (7) PII flows back to boss

Cybercrime Profile: Zeu. S

The Zeu. S Botnet § § Example of crimeware toolkit that originates from Eastern Europe, primarily Russia and the Ukraine Utilizes three major components and powerful encryption: § Zue. S trojan § Zue. S config file § Specifcation of dropsite

Zeu. S(con’t) § § Config file defines subset of targets Zue. S collects session variables during sessions § Bypasses auth. Mechanisms and piggybacks session § Criminals are able to move money to third parties in real-time § Zue. S Builder provides binary files for constructing a botnet
Zeu. S (con’t) § How simple is it? § Number of new Zeu. S binaries in the past month: 18, 985 § Number of new Zeu. S binaries seen in the past week: 4, 582 § Number of new Zeu. S binaries seen in one day: 977
Actual Examples § § Trend Report Zeu. S Video

Cybercrrime Countermeasures

Scared Yet? § Consider: § Hardware and software keeps getting cheaper § Combine the Internet and a global scope, the potential for attacks is limitless § Security will always be breached § Even when laws are passed to increase technological safeguards, new technology will always outstrip legislation

The Good Guys § I 3 C § Accepts complaints, investigates, and/or redirects to appropriate law enforcement § Joint operations with other agencies § Publishes cyber-security information § IT Act(2000) § Attempt to define various electronic specifications: § Digital Signatures § Use/Retention of electronic records § Security § Certification Authorities § Offenses
References § § § § http: //www. ic 3. gov/media/annualreport/2009_IC 3 Report. pdf http: //us. trendmicro. com/imperia/md/content/us/trendwatch/res earchandanalysis/zeusapersistentcriminalenterprise. pdf http: //www. legalserviceindia. com/cyber/itact. html http: //www. symantec. com/norton/cybercrime/definition. jsp http: //www. securityworld. com/ia-420 -love-bug-virus. aspx http: //www. finjan. com/Content. aspx? id=827
- Slides: 23