An Introduction to CRYPTOCard Date Presented by A

An Introduction to CRYPTOCard Date Presented by: - A Sales person

At a glance • • • CRYPTOCard delivers Authentication to secure digital identities We deliver via traditional server & unique Saa. S models Broad industry use and dominant in key sectors – In the UK we have 24% share in Local Government • B 2 B focussed – Our biggest customers have 50, 000 – 150, 000 seats • Our points of difference are: – – Saa. S model Focus on automation of provisioning and integration Token quality and range Low TCO CRYPTOCard – The Authority in Securing Digital Identities
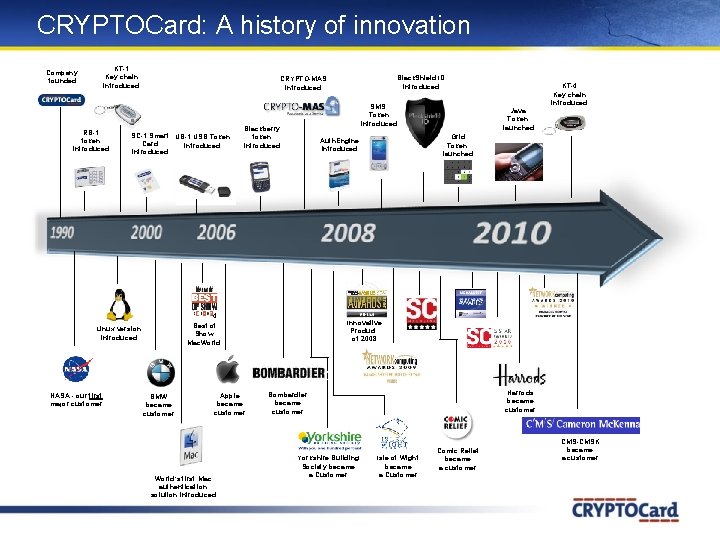
CRYPTOCard: A history of innovation KT-1 Key chain introduced Company founded RB-1 token introduced SC-1 Smart UB-1 USB Token Card introduced SMS Token introduced Blackberry token introduced BMW became customer Apple became customer World’s first Mac authentication solution introduced KT-4 Key chain introduced Java Token launched Grid Token launched Auth. Engine introduced 4 Best of Show Mac. World Linux version introduced NASA - our first major customer Black. Shield ID introduced CRYPTO-MAS introduced Innovative Product of 2008 Harrods became customer Bombardier became customer Yorkshire Building Society became a Customer Isle of Wight became a Customer Comic Relief became a customer CMS-CMSK became a customer
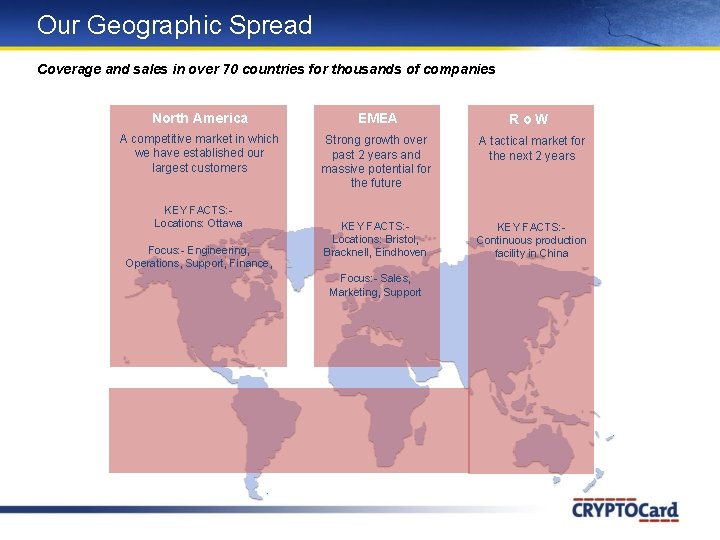
Our Geographic Spread Coverage and sales in over 70 countries for thousands of companies North America EMEA Ro. W A competitive market in which we have established our largest customers Strong growth over past 2 years and massive potential for the future A tactical market for the next 2 years KEY FACTS: Locations: Bristol, Bracknell, Eindhoven KEY FACTS: Continuous production facility in China KEY FACTS: Locations: Ottawa Focus: - Engineering, Operations, Support, Finance, Focus: - Sales, Marketing, Support
The problem with passwords Passwords are the weakest link in the security chain: Nearly every successful Hacking, Phishing or ID theft attempt involves obtaining a password Easy to guess Hard to remember Written down Easy to crack Difficult to audit Expensive to manage Easy to steal
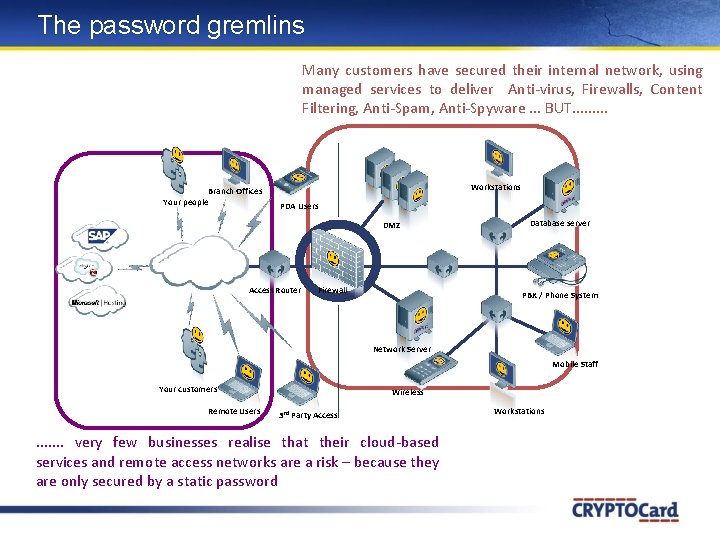
The password gremlins Many customers have secured their internal network, using managed services to deliver Anti-virus, Firewalls, Content Filtering, Anti-Spam, Anti-Spyware. . . BUT. . Branch Offices Your people Workstations PDA Users DMZ Access Router Firewall Database server PBX / Phone System Network Server Mobile Staff Your customers Remote Users Wireless 3 rd Party Access . . . . very few businesses realise that their cloud-based services and remote access networks are a risk – because they are only secured by a static password Workstations
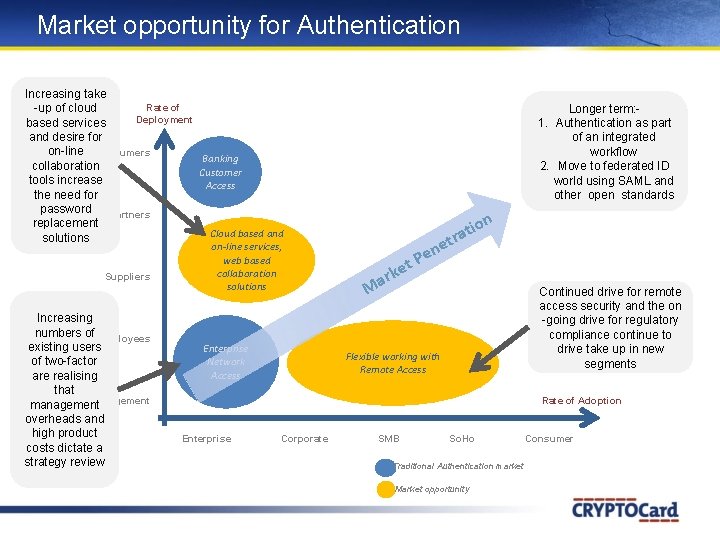
Market opportunity for Authentication Increasing take Rate of -up of cloud Deployment based services and desire for on-line Consumers Banking collaboration Customer tools increase Access the need for password Partners replacement Cloud based and solutions Suppliers Increasing numbers of Employees existing users of two-factor are realising that Management management overheads and high product costs dictate a strategy review on-line services, web based collaboration solutions Enterprise Network Access Longer term: 1. Authentication as part of an integrated workflow 2. Move to federated ID world using SAML and other open standards et k r a on i t tra e n Pe M Continued drive for remote access security and the on -going drive for regulatory compliance continue to drive take up in new segments Flexible working with Remote Access Rate of Adoption Enterprise Corporate SMB So. Ho Traditional Authentication market Market opportunity Consumer
Passwords are easy to hack "If your company suffered a malicious attack from a fraudster who stole important data or brought down critical business systems what would be the full cost to the business? “ Jason Hart Senior VP, CRYPTOCard
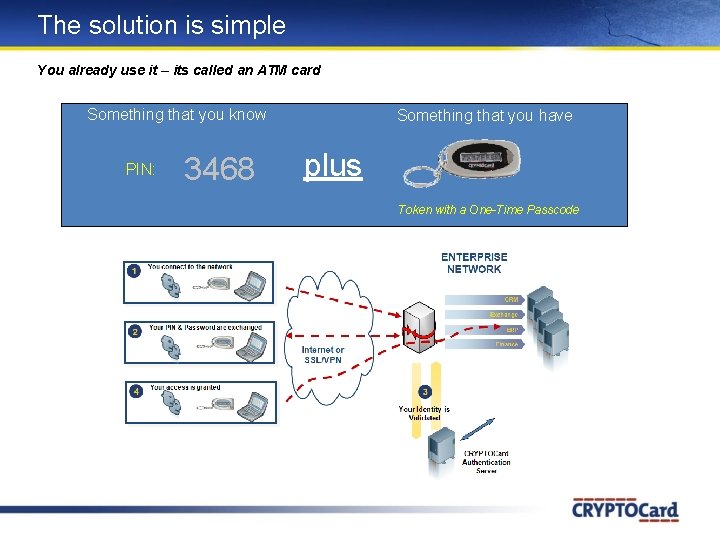
The solution is simple You already use it – its called an ATM card Something that you know PIN: 3468 Something that you have plus Token with a One-Time Passcode
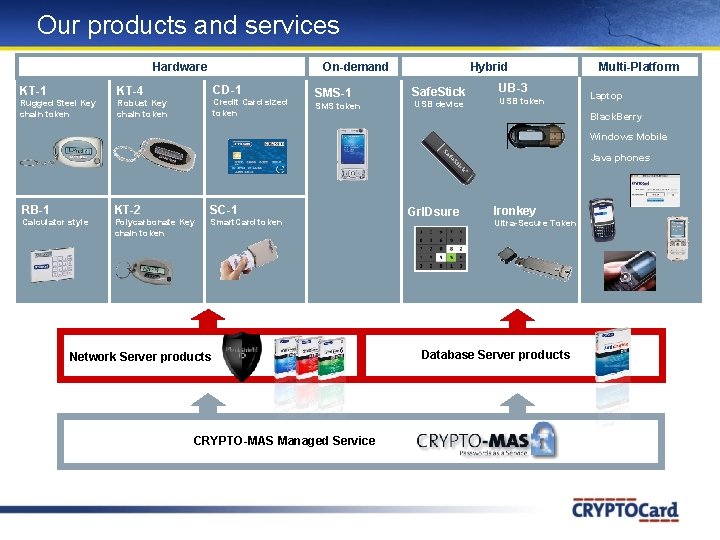
Our products and services Hardware KT-1 KT-4 Rugged Steel Key chain token Robust Key chain token On-demand CD-1 Credit Card sized token SMS-1 SMS token Hybrid Safe. Stick USB device UB-3 USB token Multi-Platform Laptop Black. Berry Windows Mobile Java phones RB-1 KT-2 SC-1 Calculator style Polycarbonate Key chain token Smart. Card token Network Server products CRYPTO-MAS Managed Service Gr. IDsure Ironkey Ultra-Secure Token Database Server products

CRYPTO-MAS: Simplementation tools VPN Firewall JAVA Tokens Black. Berry Tokens Outlook SSL SMS Tokens Citrix Remote Web Workplace VPN Terminal Services Citrix CAG, WI, AAC Web Apps IIS Key Chain Tokens Software Tokens Unix Logon NPS/IAS Active Directory Synchronization Apache Linux/Unix

Significant points of difference Six primary innovations of CRYPTO-MAS combine to deliver significant benefits Designed as a service Simple to use portal Cloud based architecture Wide token range Simple integration tools Migration Agent LDAP Agent Integration Agents Standard Reports included

CRYPTO-MAS: Simple to adopt and deploy Easily integrated and distributed within hours, not days –reducing overheads SUBSCRIBER COMPANY Applications Administrator 1 2 Set-up the customer administrator 3 Add the Access device to the network 2 MAS 4 Access device 5 3 Upload User information 4 5 Active Directory Set-up the customer company Add tokens Distribute tokens to users 6 TOKENS & USERS SERVICE PROVIDER 6 1 = Service Provider = Customer

Black. Shield ID Knowledge, Simplicity, Choice Total Authentication, Made Simple
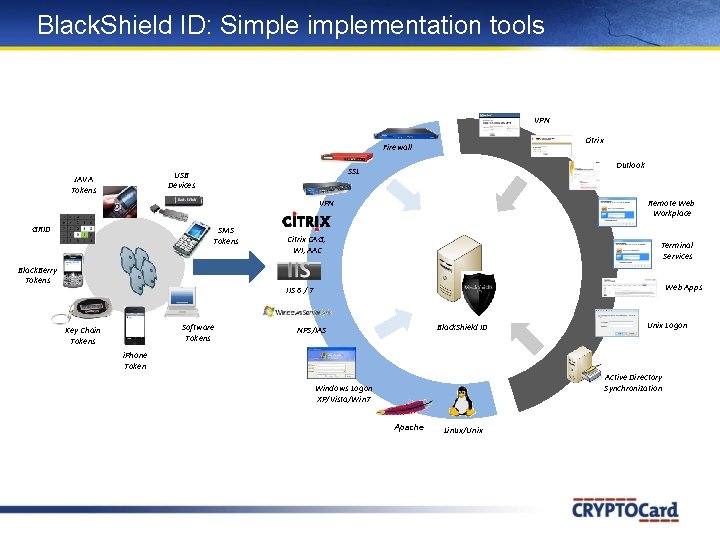
Black. Shield ID: Simplementation tools VPN Citrix Firewall Outlook SSL USB Devices JAVA Tokens Remote Web Workplace VPN GRID SMS Tokens Black. Berry Tokens Citrix CAG, WI, AAC Terminal Services Web Apps IIS 6 / 7 Software Tokens Key Chain Tokens Black. Shield ID NPS/IAS Unix Logon i. Phone Token Active Directory Synchronization Windows Logon XP/Vista/Win 7 Apache Linux/Unix
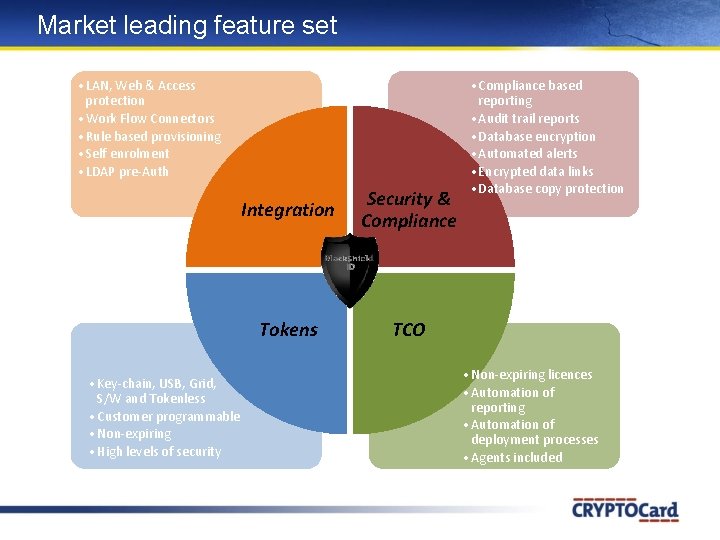
Market leading feature set • LAN, Web & Access protection • Work Flow Connectors • Rule based provisioning • Self enrolment • LDAP pre-Auth • Key-chain, USB, Grid, S/W and Tokenless • Customer programmable • Non-expiring • High levels of security Integration Security & Compliance Tokens TCO • Compliance based reporting • Audit trail reports • Database encryption • Automated alerts • Encrypted data links • Database copy protection • Non-expiring licences • Automation of reporting • Automation of deployment processes • Agents included
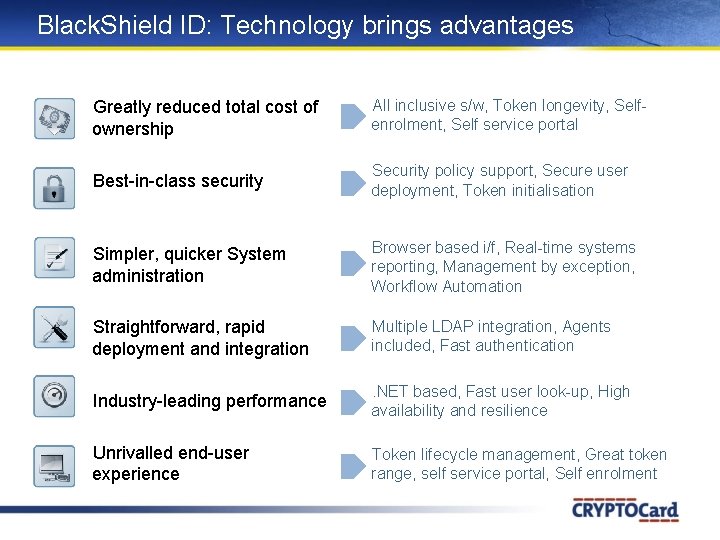
Black. Shield ID: Technology brings advantages Greatly reduced total cost of ownership All inclusive s/w, Token longevity, Selfenrolment, Self service portal Best-in-class security Security policy support, Secure user deployment, Token initialisation Simpler, quicker System administration Browser based i/f, Real-time systems reporting, Management by exception, Workflow Automation Straightforward, rapid deployment and integration Multiple LDAP integration, Agents included, Fast authentication Industry-leading performance . NET based, Fast user look-up, High availability and resilience Unrivalled end-user experience Token lifecycle management, Great token range, self service portal, Self enrolment
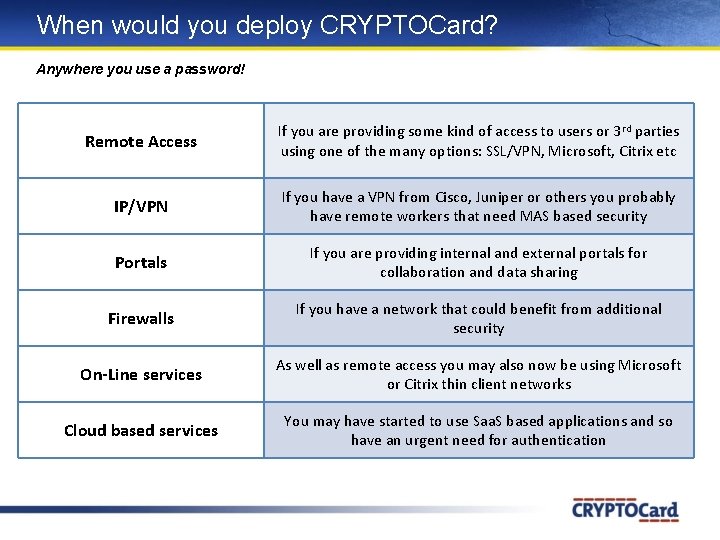
When would you deploy CRYPTOCard? Anywhere you use a password! Remote Access If you are providing some kind of access to users or 3 rd parties using one of the many options: SSL/VPN, Microsoft, Citrix etc IP/VPN If you have a VPN from Cisco, Juniper or others you probably have remote workers that need MAS based security Portals If you are providing internal and external portals for collaboration and data sharing Firewalls If you have a network that could benefit from additional security On-Line services As well as remote access you may also now be using Microsoft or Citrix thin client networks Cloud based services You may have started to use Saa. S based applications and so have an urgent need for authentication
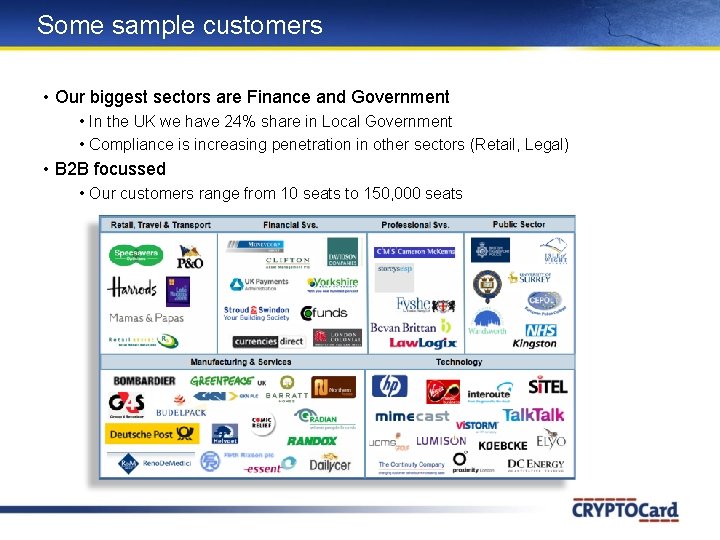
Some sample customers • Our biggest sectors are Finance and Government • In the UK we have 24% share in Local Government • Compliance is increasing penetration in other sectors (Retail, Legal) • B 2 B focussed • Our customers range from 10 seats to 150, 000 seats
Example: Stroud & Swindon Key benefits • • Who they are • Based in Swindon, UK • One of 50 UK building societies • Head office with 400 people plus 20 offices and 20 agencies in south-west England What they have • Over 60 remote workers – Financial consultants • SSL/VPN remote access network What problem they solved • Secure access for confidential client reviews Key features used • CRYPTO-MAS • Soft tokens • • • Compliance and audit support – FSA regulations Secure access from any broadband connection – Ad-hoc home working – Returning parents – Emergency working Lower cost than installing a server Outsourced IT headache Token portability “We tend to outsource those elements of infrastructure services that requires specialist knowledge. Authentication isn’t the kind of thing you’d have to do day-in-day -out, so any skills tend to be lost and the cost of employing key specialists in-house doesn’t make sense any more. ” Colin Campbell IT Services Manager, Stroud & Swindon
Example: TTT Moneycorp Key benefits • Who they are • Based in London, UK • Private and corporate money exchange • Over 600 employees around the world What they have • Secured web and telephone access by corporate customers • RB-1 tokens What problem they solved • Secure access for monetary transfers Key features used • CRYPTO-MAS • Security with AES 256 and Base 32 • Flexible payment options • • • Freedom of access – Phone or web Highest levels of security Speed and ease of install – Completed in minutes Low total cost of ownership – Outsourced overheads – No upfront investments “CRYPTO-MAS provided an instant, resilient authentication service. The development and installation took minutes as opposed to days, which is impressive given our stringent standards. ” Thomas Kadri Director of Support Services TTT Moneycorp
Points of difference Cloud Based The first/only major Authentication vendor to deliver a Saa. S model Affordable Total Cost of Ownership over 5 years CRYPTOCard will be over 50% less expensive than other platforms. Easy to Integrate CRYPTOCard prides itself on delivering authentication solutions that are easy to use and fast to integrate Simple to Manage CRYPTOCard boasts a high level of automation options for user and token management and administration Innovative CRYPTOCard has a broad and innovative token technology Focused CRYPTOCard is a pure-play authentication company, has been innovating for more than 20 years and will continue to lead the market.
- Slides: 22