An Impersonation Attack on OneTime Password Authentication Protocol








- Slides: 21

An Impersonation Attack on One-Time Password Authentication Protocol OSPA Source : IEICE Transactions on Communications, Vol. E 86 -B, No. 7, July 2003, pp. 21822185 Author : Takasuke TSUJI, Akihiro SHIMIZU Advisor : Dr. Chang, Chin-Chen Speaker : Chou Chien-Long

Outline l l Introduction The OSPA Protocol Impersonation Attack on The OSPA Conclusion 2

Introduction l Authentication methods have many security problems: l l l High hash overhead. Requirement of resetting the verifier. ‘Man in the Middle’ attack. 3

Introduction (cont. ) l l Optimal Strong-Password Authentication has solved the aforementioned security problems. In this letter, we devise an impersonation attack on the OSPA method without an active attack on the server. 4

The OSPA Protocol l Notations l l l A is the user’s identify. P is the user’s password. h is a one-way hash function. n is the number of authentication sessions. ⊕ represents bitwise XOR operation. 5

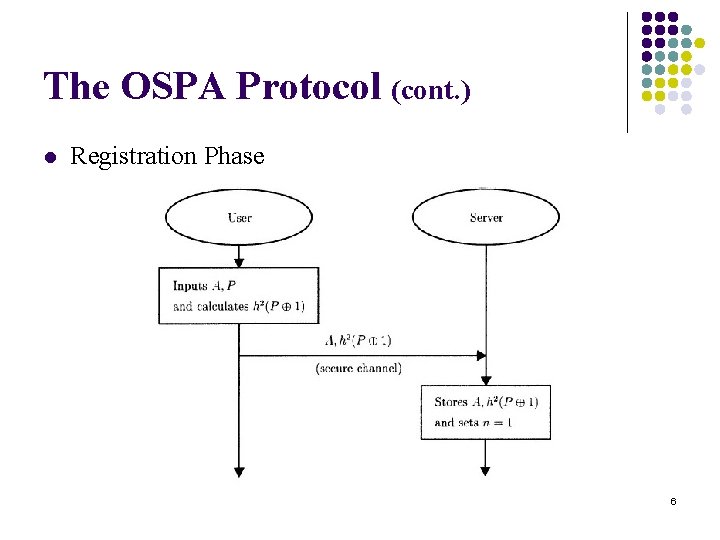
The OSPA Protocol (cont. ) l Registration Phase 6

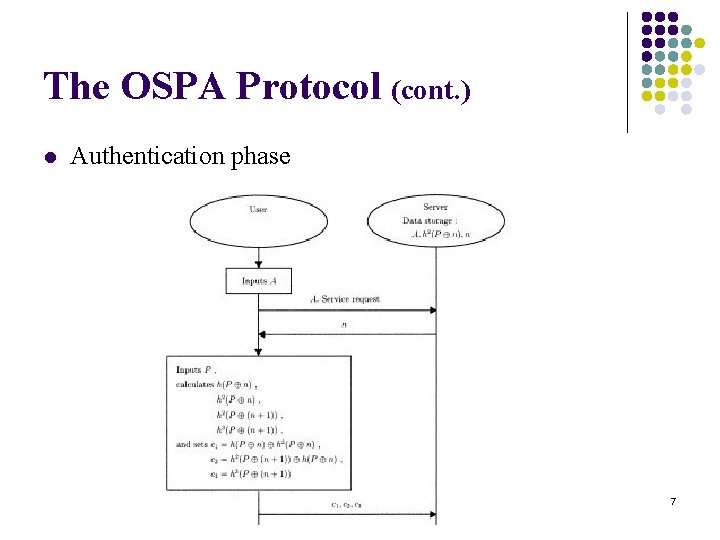
The OSPA Protocol (cont. ) l Authentication phase 7

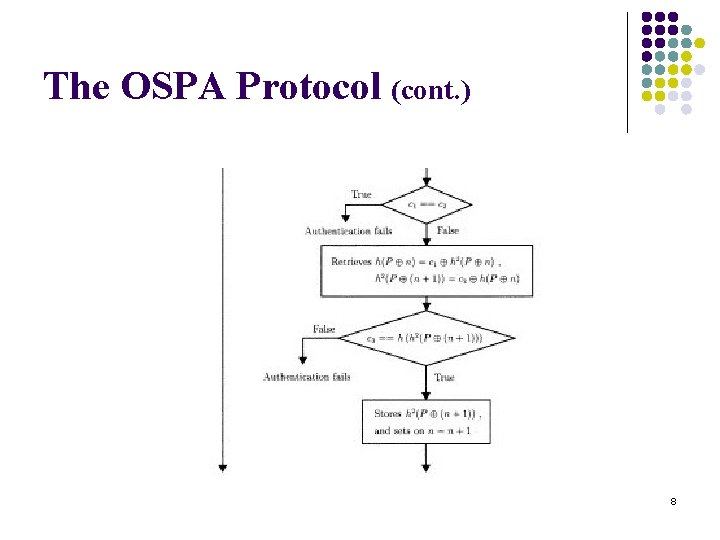
The OSPA Protocol (cont. ) 8

Impersonation Attack on The OSPA l l Impersonation Attack with Two Previous Verifiers Impersonation Attack Using Previous Verifiers Impersonation Attack with Various Verifiers Hybrid Impersonation Attack 9

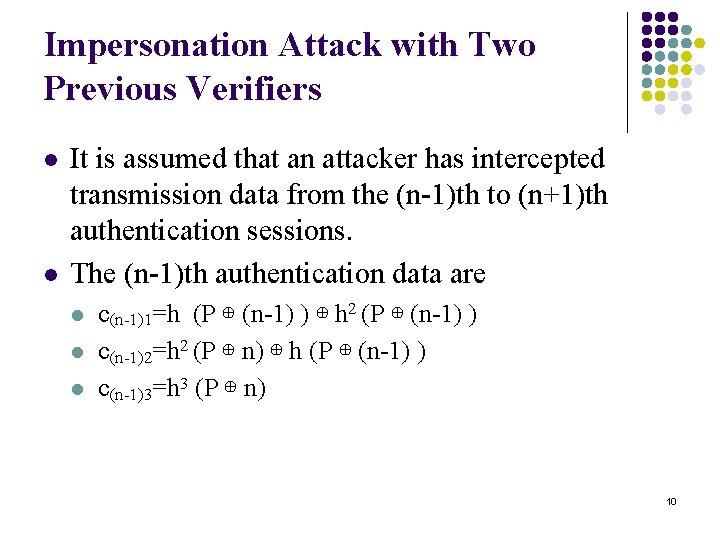
Impersonation Attack with Two Previous Verifiers l l It is assumed that an attacker has intercepted transmission data from the (n-1)th to (n+1)th authentication sessions. The (n-1)th authentication data are l l l c(n-1)1=h (P ⊕ (n-1) ) ⊕ h 2 (P ⊕ (n-1) ) c(n-1)2=h 2 (P ⊕ n) ⊕ h (P ⊕ (n-1) ) c(n-1)3=h 3 (P ⊕ n) 10

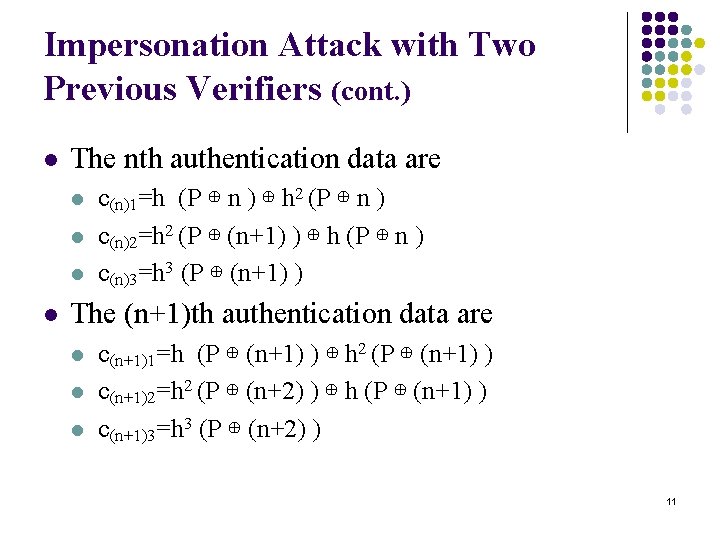
Impersonation Attack with Two Previous Verifiers (cont. ) l The nth authentication data are l l c(n)1=h (P ⊕ n ) ⊕ h 2 (P ⊕ n ) c(n)2=h 2 (P ⊕ (n+1) ) ⊕ h (P ⊕ n ) c(n)3=h 3 (P ⊕ (n+1) ) The (n+1)th authentication data are l l l c(n+1)1=h (P ⊕ (n+1) ) ⊕ h 2 (P ⊕ (n+1) ) c(n+1)2=h 2 (P ⊕ (n+2) ) ⊕ h (P ⊕ (n+1) ) c(n+1)3=h 3 (P ⊕ (n+2) ) 11

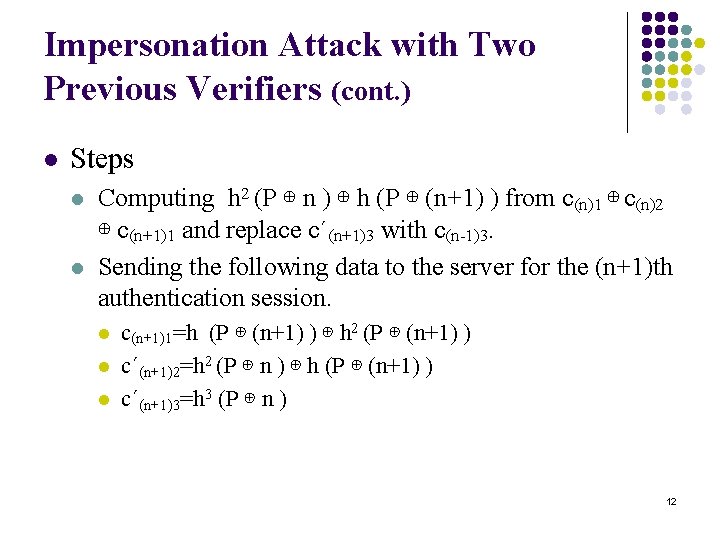
Impersonation Attack with Two Previous Verifiers (cont. ) l Steps l l Computing h 2 (P ⊕ n ) ⊕ h (P ⊕ (n+1) ) from c(n)1 ⊕ c(n)2 ⊕ c(n+1)1 and replace c´(n+1)3 with c(n-1)3. Sending the following data to the server for the (n+1)th authentication session. l l l c(n+1)1=h (P ⊕ (n+1) ) ⊕ h 2 (P ⊕ (n+1) ) c´(n+1)2=h 2 (P ⊕ n ) ⊕ h (P ⊕ (n+1) ) c´(n+1)3=h 3 (P ⊕ n ) 12

Impersonation Attack with Two Previous Verifiers (cont. ) l l Server checks c(n+1)1 ≠ c´(n+1)2. Retrieves h (P ⊕ (n+1) ) from c(n+1)1, and get h 2 (P ⊕ n ) from c´(n+1)2 ⊕ h (P ⊕ (n+1) ). Compares h ( h 2 (P ⊕ n )) with the received c´(n+1)3. These are the same so the user is authenticated. 13

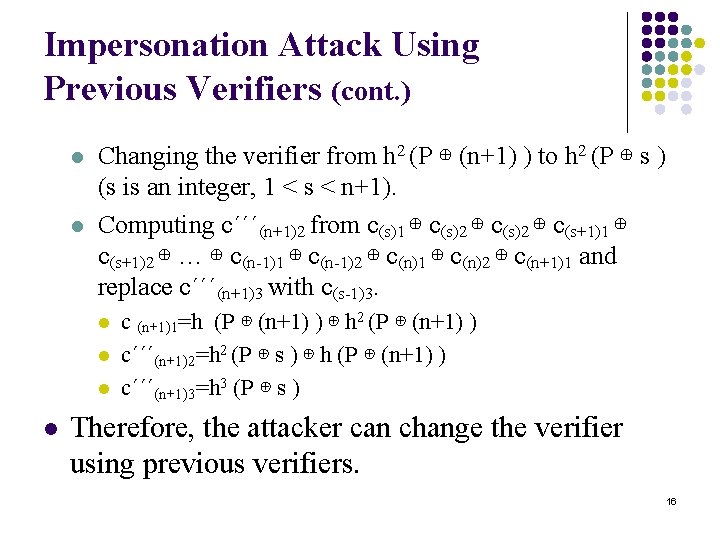
Impersonation Attack Using Previous Verifiers l l In an impersonation attack with two pervious verifiers, the invasion can be detected if the server has stored two verifiers. As a result, the attack has to change the next verifier intentionally. 14

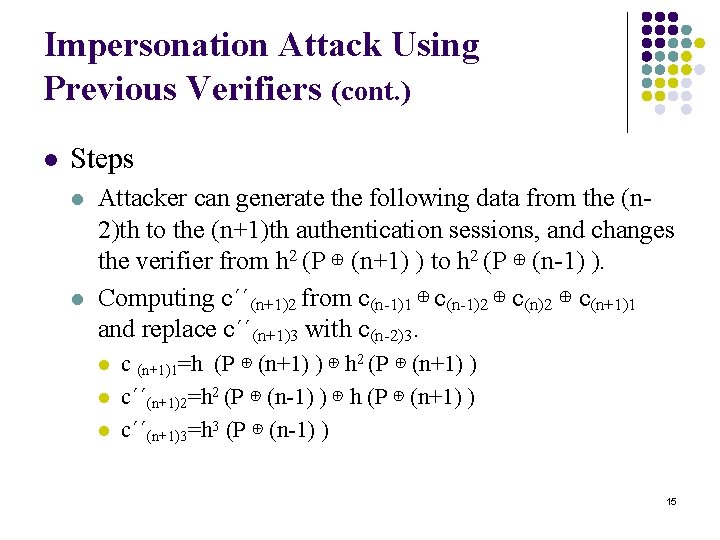
Impersonation Attack Using Previous Verifiers (cont. ) l Steps l l Attacker can generate the following data from the (n 2)th to the (n+1)th authentication sessions, and changes the verifier from h 2 (P ⊕ (n+1) ) to h 2 (P ⊕ (n-1) ). Computing c´´(n+1)2 from c(n-1)1 ⊕ c(n-1)2 ⊕ c(n+1)1 and replace c´´(n+1)3 with c(n-2)3. l l l c (n+1)1=h (P ⊕ (n+1) ) ⊕ h 2 (P ⊕ (n+1) ) c´´(n+1)2=h 2 (P ⊕ (n-1) ) ⊕ h (P ⊕ (n+1) ) c´´(n+1)3=h 3 (P ⊕ (n-1) ) 15

Impersonation Attack Using Previous Verifiers (cont. ) l l Changing the verifier from h 2 (P ⊕ (n+1) ) to h 2 (P ⊕ s ) (s is an integer, 1 < s < n+1). Computing c´´´(n+1)2 from c(s)1 ⊕ c(s)2 ⊕ c(s+1)1 ⊕ c(s+1)2 ⊕ … ⊕ c(n-1)1 ⊕ c(n-1)2 ⊕ c(n)1 ⊕ c(n)2 ⊕ c(n+1)1 and replace c´´´(n+1)3 with c(s-1)3. l l c (n+1)1=h (P ⊕ (n+1) ) ⊕ h 2 (P ⊕ (n+1) ) c´´´(n+1)2=h 2 (P ⊕ s ) ⊕ h (P ⊕ (n+1) ) c´´´(n+1)3=h 3 (P ⊕ s ) Therefore, the attacker can change the verifier using previous verifiers. 16

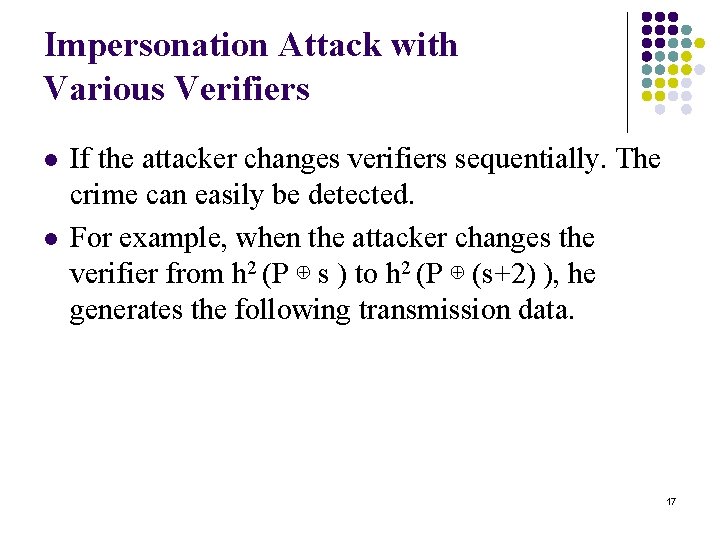
Impersonation Attack with Various Verifiers l l If the attacker changes verifiers sequentially. The crime can easily be detected. For example, when the attacker changes the verifier from h 2 (P ⊕ s ) to h 2 (P ⊕ (s+2) ), he generates the following transmission data. 17

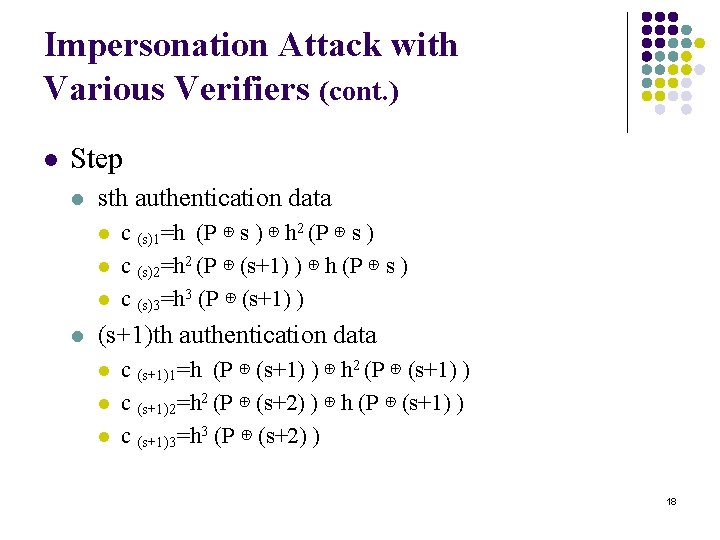
Impersonation Attack with Various Verifiers (cont. ) l Step l sth authentication data l l c (s)1=h (P ⊕ s ) ⊕ h 2 (P ⊕ s ) c (s)2=h 2 (P ⊕ (s+1) ) ⊕ h (P ⊕ s ) c (s)3=h 3 (P ⊕ (s+1) ) (s+1)th authentication data l l l c (s+1)1=h (P ⊕ (s+1) ) ⊕ h 2 (P ⊕ (s+1) ) c (s+1)2=h 2 (P ⊕ (s+2) ) ⊕ h (P ⊕ (s+1) ) c (s+1)3=h 3 (P ⊕ (s+2) ) 18

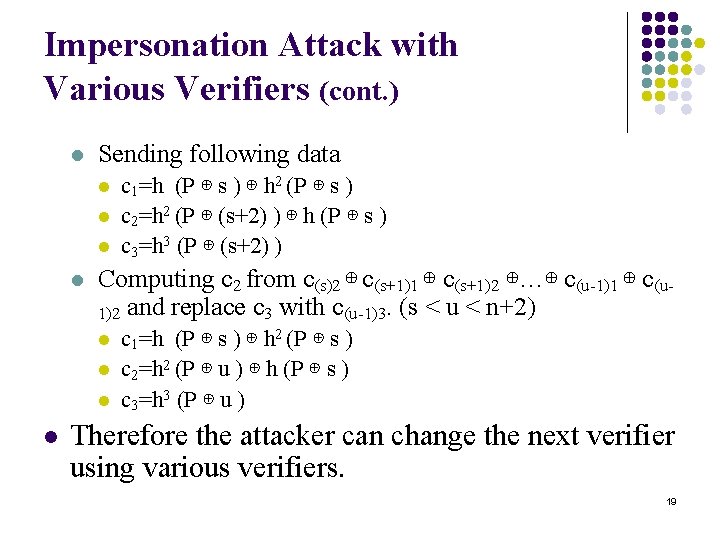
Impersonation Attack with Various Verifiers (cont. ) l Sending following data l l Computing c 2 from c(s)2 ⊕ c(s+1)1 ⊕ c(s+1)2 ⊕…⊕ c(u-1)1 ⊕ c(u 1)2 and replace c 3 with c(u-1)3. (s < u < n+2) l l c 1=h (P ⊕ s ) ⊕ h 2 (P ⊕ s ) c 2=h 2 (P ⊕ (s+2) ) ⊕ h (P ⊕ s ) c 3=h 3 (P ⊕ (s+2) ) c 1=h (P ⊕ s ) ⊕ h 2 (P ⊕ s ) c 2=h 2 (P ⊕ u ) ⊕ h (P ⊕ s ) c 3=h 3 (P ⊕ u ) Therefore the attacker can change the next verifier using various verifiers. 19

Hybrid Impersonation Attack l l l The crime can be detected if the server has stored all verifiers. Further, the user can’t use the same verifier if the server stores and checks all verifiers. Such a mechanism can’t ensure security if the user used the system for a long time. 20

Conclusion l l We have discussed an impersonation attack on the OSPA using communication data. Possibility of such impersonation attacks shows the OSPA method to be impractical. 21