An Extension to Packet Filtering of Programmable Networks
An Extension to Packet Filtering of Programmable Networks Marcus Schöller, Thomas Gamer, Roland Bless, and Martina Zitterbart Institut für Telematik Universität Karlsruhe (TH) Germany IWAN 2005 – November 23 th
Motivation q Building an attack detection system Ø DDo. S and worm propagation are major threats Ø Victim can not take any countermeasures Ø Support from network operator needed Ø Detection as early as possible q Objectives Ø Be extensible to adept to new attacks Ø Be resource saving to fit in high-speed environments Application level view Build an anomaly based attack detection system based on packet selection An Extension to Packet Filtering of Programmable Networks Marcus Schöller, Universität Karlsruhe (TH), Germany 2
Motivation q Building an attack detection system Ø DDo. S and worm propagation are major threats Ø Victim can not take any countermeasures Ø Support from network operator needed Ø Detection as early as possible Ø Attack are constantly changing q Objectives Ø Be extensible to adept to new attacks Ø Be resource saving to fit in high-speed environments Network level view Build an anomaly based attack detection system based on packet selection An Extension to Packet Filtering of Programmable Networks Marcus Schöller, Universität Karlsruhe (TH), Germany 3
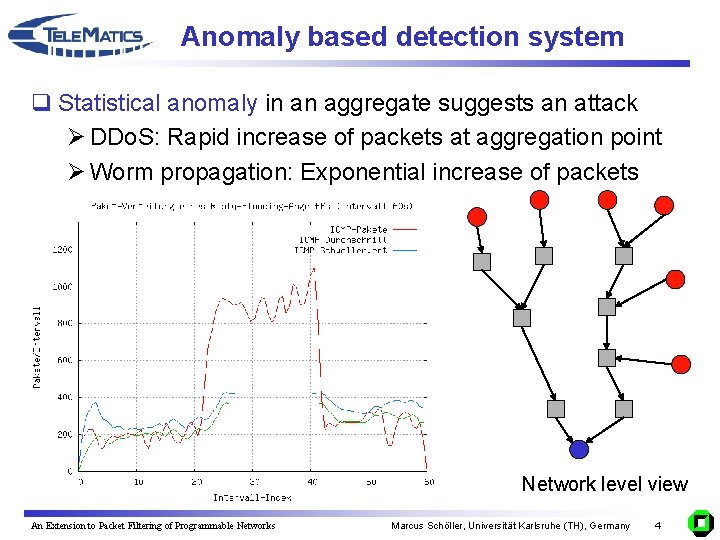
Anomaly based detection system q Statistical anomaly in an aggregate suggests an attack Ø DDo. S: Rapid increase of packets at aggregation point Ø Worm propagation: Exponential increase of packets Network level view An Extension to Packet Filtering of Programmable Networks Marcus Schöller, Universität Karlsruhe (TH), Germany 4
Anomaly based detection system q Statistical anomaly in an aggregate suggests an attack Ø Rapid increase of packets Ø Exponential increase of packets q Protocol anomalies within such an aggregate Ø Verify the suggestion Ø TCP connection establishment • # TCP-SYN approx. # TCP-SYN-ACK Ø TCP-SYN-Flooding • (# TCP-SYN > # TCP-SYN-ACK) & TCP-RST q Packet selection to find statistical anomalies Ø Attack hints can be detected with less resources An Extension to Packet Filtering of Programmable Networks Marcus Schöller, Universität Karlsruhe (TH), Germany 5
Packet Selection – PSAMP WG q Packet filtering Ø Field match filtering Ø Hash based selection Ø Router state filtering Node. OS is currently limited to this class q Packet sampling Ø Non-uniform probabilistic sampling Ø Systematic time based sampling Ø n-out-of-N sampling Ø Uniform probabilistic sampling Ø Systematic count based sampling An Extension to Packet Filtering of Programmable Networks Marcus Schöller, Universität Karlsruhe (TH), Germany 6
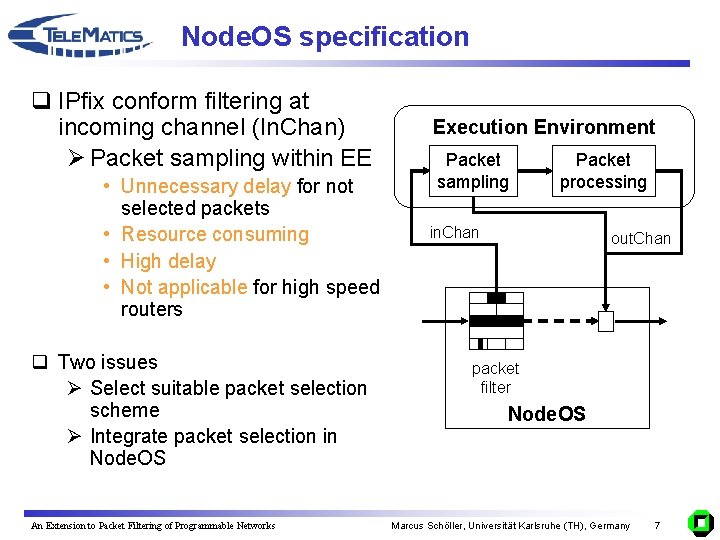
Node. OS specification q IPfix conform filtering at incoming channel (In. Chan) Ø Packet sampling within EE • Unnecessary delay for not selected packets • Resource consuming • High delay • Not applicable for high speed routers q Two issues Ø Select suitable packet selection scheme Ø Integrate packet selection in Node. OS An Extension to Packet Filtering of Programmable Networks Execution Environment Packet sampling Packet processing in. Chan out. Chan packet filter Node. OS Marcus Schöller, Universität Karlsruhe (TH), Germany 7
Selecting a suitable packet selector q Building an attack detection system Ø Packet filtering is unsuitable • Attacker can circumvent detection by packet crafting Ø Non-uniform probabilistic sampling is unsuitable • Deep packet inspection necessary Ø Systematic time-based sampling is unsuitable • Bad estimation during low bandwidth utilization Ø n-out-of-N sampling is suitable to only a limited extend • Generation of unique random numbers necessary Ø Uniform probabilistic sampling is well suitable • Only random number generator required Ø Systematic count based sampling is very well suited • Least resource demanding An Extension to Packet Filtering of Programmable Networks Marcus Schöller, Universität Karlsruhe (TH), Germany 8

Packet sampling experiment q Uniform probabilistic sampling Ø Sampling interval: 0, 5 s and 5 s Ø Accuracy depends on number of packets per interval q Same results for systematic count based sampling Estimation failure of uniform probabilistic sampling Packet average per sampling interval 20% 30% 40% ICMP 87, 9 21, 81% 16, 47% 13, 5% ICMP 890, 82 6, 84% 5, 04% 4, 39% UDP 1041, 95 6, 15% 4, 77% 3, 8% UDP 10451, 29 2, 15% 1, 52% 1, 27% TCP 9343, 11 2, 11% 1, 54% 1, 27% TCP 93423, 88 0, 69% 0, 42% An Extension to Packet Filtering of Programmable Networks Selection probability Marcus Schöller, Universität Karlsruhe (TH), Germany 9
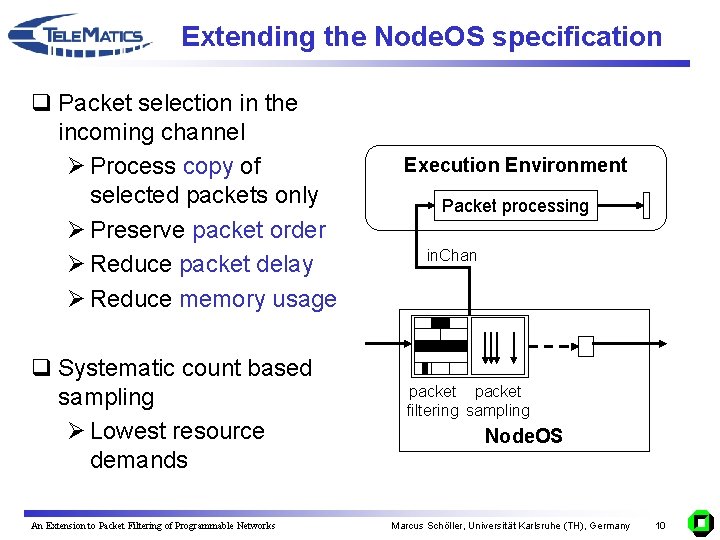
Extending the Node. OS specification q Packet selection in the incoming channel Ø Process copy of selected packets only Ø Preserve packet order Ø Reduce packet delay Ø Reduce memory usage q Systematic count based sampling Ø Lowest resource demands An Extension to Packet Filtering of Programmable Networks Execution Environment Packet processing in. Chan packet filtering sampling Node. OS Marcus Schöller, Universität Karlsruhe (TH), Germany 10
![Processing time [in 1000 processor tics] Evaluation results Average of overall processing time Selected Processing time [in 1000 processor tics] Evaluation results Average of overall processing time Selected](http://slidetodoc.com/presentation_image_h2/988c2b710159e8a4a0c60920c58e9816/image-11.jpg)
Processing time [in 1000 processor tics] Evaluation results Average of overall processing time Selected packet 245 858 Tics 205 617 Tics 3000 2500 61 795 Tics 2000 Not-selected packet 1 076 Tics 1500 1000 500 0 0 500 An Extension to Packet Filtering of Programmable Networks 1000 1500 Packet Index 2000 Marcus Schöller, Universität Karlsruhe (TH), Germany 11
Conclusion q Programmable networks well suited Ø Analysis modules are instantiated on-demand Ø Resource saving q Packet selection Ø Reduce resource demands Ø Extend Node. OS specification q Other applications based on packet selection Ø Traffic measurement Ø Traffic accounting Ø Trajectory sampling An Extension to Packet Filtering of Programmable Networks Marcus Schöller, Universität Karlsruhe (TH), Germany 12
Outlook q Eliminate simplification of our model Ø Internet routes are asymmetric • Cooperation of detection instances Ø Simultaneous attacks • Feedback between detection modules Ø Adaptive packet selection q Countermeasures Ø DDo. S vs. flash crowds An Extension to Packet Filtering of Programmable Networks Marcus Schöller, Universität Karlsruhe (TH), Germany 13

Thank you! Questions? Please visit www. tm. uka. de/projects/flexinet for further information and downloads! An Extension to Packet Filtering of Programmable Networks Marcus Schöller, Universität Karlsruhe (TH), Germany 14
- Slides: 14