An example using the SUN provider The provider


![rgb = messagedigest(); outputstream. Message. Digest. write(rgb); } public static void main(String [] rgb = messagedigest(); outputstream. Message. Digest. write(rgb); } public static void main(String []](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-6.jpg)
![Input. Stream class: read method detailed § int read (byte[] b) v. Reads some Input. Stream class: read method detailed § int read (byte[] b) v. Reads some](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-8.jpg)
![Output. Stream class: write method detailed § void write (byte[] b) v. Writes b. Output. Stream class: write method detailed § void write (byte[] b) v. Writes b.](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-9.jpg)








![int n = 0; byte [] rgb = new byte [1000]; while ((n int n = 0; byte [] rgb = new byte [1000]; while ((n](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-29.jpg)


![public static void main(String [] rgstring) { try { File file. Private = new public static void main(String [] rgstring) { try { File file. Private = new](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-32.jpg)

![public static void main(String [] rgstring) { try { File file. Public = public static void main(String [] rgstring) { try { File file. Public =](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-35.jpg)


![for (Enumeration e = p[i]. keys(); e. has. More. Elements(); ) { String key for (Enumeration e = p[i]. keys(); e. has. More. Elements(); ) { String key](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-43.jpg)

![get. Providers method § public static Provider[ ] get. Providers() v. Returns an array get. Providers method § public static Provider[ ] get. Providers() v. Returns an array](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-46.jpg)
![get Providers method § public static Provider [] get. Providers (Map filter) v Returns get Providers method § public static Provider [] get. Providers (Map filter) v Returns](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-48.jpg)

- Slides: 49

An example using the SUN provider §The provider SUN is supplied in Java 2 SDK. § SUN provides both van implementation of the NIST Digital Signature Algorithm (DSA), and v an implementation of the MD 5 and NIST SHA-1 message digest algorithms. §Class Message. Digest : vlooking at code that generates a message digest from a message. Message. Digest messagedigest = Message. Digest. get. Instance("SHA"); Message. Digest messagedigest = Message. Digest. get. Instance("SHA", "SUN"); vget. Instance() method can be used in two different way. ü The first requires only the algorithm to be specified. üThe second requires both the algorithm and the provider to be specified. üBoth return an instance of a class that implements the SHA algorithm.

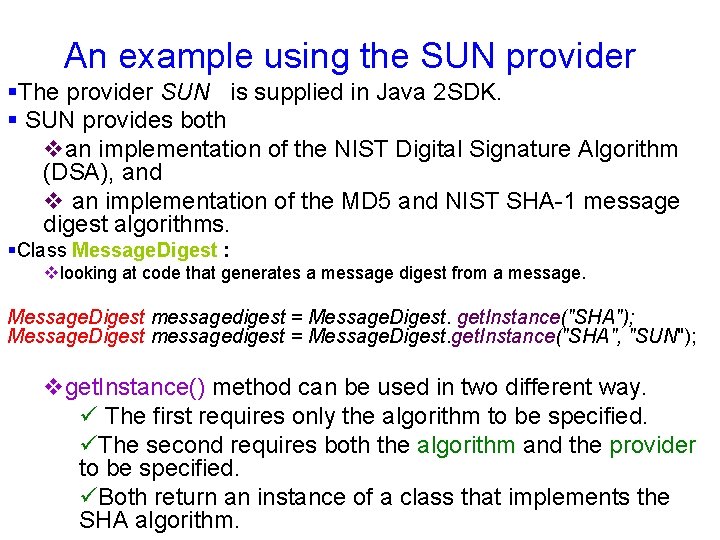
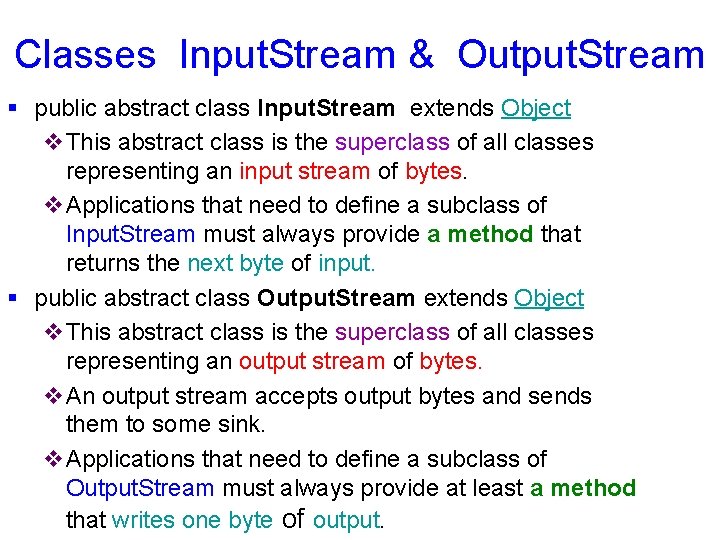
§ Next, we pass the message through the message-digest generator. int n = 0; byte [ ] rgb = new byte [1000]; while ((n = inputstream. Message. read(rgb)) > -1) { messagedigest. update(rgb, 0, n); } v This code works well for large messages of unknown length. v The update() method also accepts a single byte as an argument for messages of a few bytes in length, and ü a byte array for messages of a fixed or predictable size. § The final step involves generating the message digest itself. rgb = messagedigest(); The resulting digest is encoded in an array of bytes.

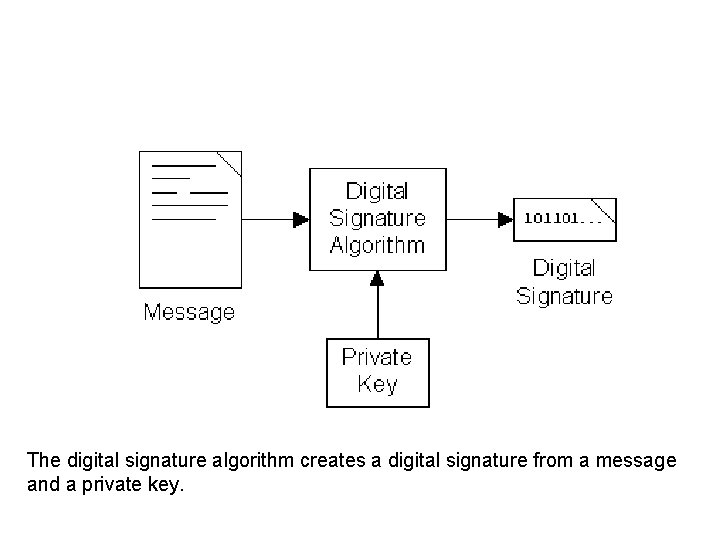
Message Digest Algorithm § A message digest algorithm computes a (typically shorter) fixed-size string from a message called the message digest (also known as a digital fingerprint). § Any change to the original message will result in a different message digest, providing a way to verify the integrity (that is, check the fingerprint) of the original message. The message digest algorithm creates a message digest from a message.

The Complete Source Code for a program that Generates a Message

import java. security. Message. Digest; import java. security. No. Such. Algorithm. Exception; import java. io. Input. Stream; import java. io. Output. Stream; import java. io. File. Input. Stream; import java. io. File. Output. Stream; import java. io. IOException; Public class Message. Digest. Generator { public void generate. Message. Digest( Input. Stream inputstream. Message, Output. Stream outputstream. Message. Digest) throws No. Such. Algorithm. Exception, IOException { Message. Digest messagedigest = Message. Digest. get. Instance("SHA"); int n = 0; byte [ ] rgb = new byte [1000]; while ((n = inputstream. Message. read(rgb)) > -1) { messagedigest. update(rgb, 0, n); }
![rgb messagedigest outputstream Message Digest writergb public static void mainString rgb = messagedigest(); outputstream. Message. Digest. write(rgb); } public static void main(String []](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-6.jpg)
rgb = messagedigest(); outputstream. Message. Digest. write(rgb); } public static void main(String [] rgstring) { try { File. Input. Stream fileinputstream = new File. Input. Stream(rgstring[0]); File. Output. Stream fileoutputstream = new File. Output. Stream(rgstring[1]); new Message. Digest. Generator(). generate. Message. Digest (fileinputstream, fileoutputstream); fileinputstream. close(); fileoutputstream. close(); } catch (Exception ex) { ex. print. Stack. Trace(); } } }

Classes Input. Stream & Output. Stream § public abstract class Input. Stream extends Object v. This abstract class is the superclass of all classes representing an input stream of bytes. v. Applications that need to define a subclass of Input. Stream must always provide a method that returns the next byte of input. § public abstract class Output. Stream extends Object v. This abstract class is the superclass of all classes representing an output stream of bytes. v. An output stream accepts output bytes and sends them to some sink. v. Applications that need to define a subclass of Output. Stream must always provide at least a method that writes one byte of output.
![Input Stream class read method detailed int read byte b v Reads some Input. Stream class: read method detailed § int read (byte[] b) v. Reads some](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-8.jpg)
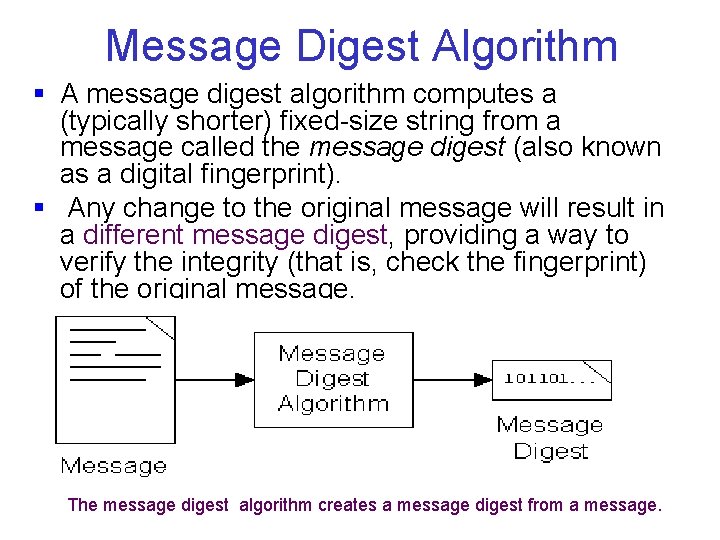
Input. Stream class: read method detailed § int read (byte[] b) v. Reads some number of bytes from the input stream and stores them into the buffer array b. v. The number of bytes actually read is returned as an integer. v. This method blocks until input data is available, end of file is detected, or an exception is thrown. v If b is null, a Null. Pointer. Exception is thrown v. If the length of b is zero, then no bytes are read and 0 is returned; votherwise, there is an attempt to read at least one byte. v If no byte is available because the stream is at end of file, the value 1 is returned; votherwise, at least one byte is read and stored into b. § Parameter: b - the buffer into which the data is read. § Returns: the total number of bytes read into the buffer, or -1 is there is no more data because the end of the stream has been reached. § Throws: IOException - if an I/O error occurs. Null. Pointer. Exception- if b is null.
![Output Stream class write method detailed void write byte b v Writes b Output. Stream class: write method detailed § void write (byte[] b) v. Writes b.](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-9.jpg)
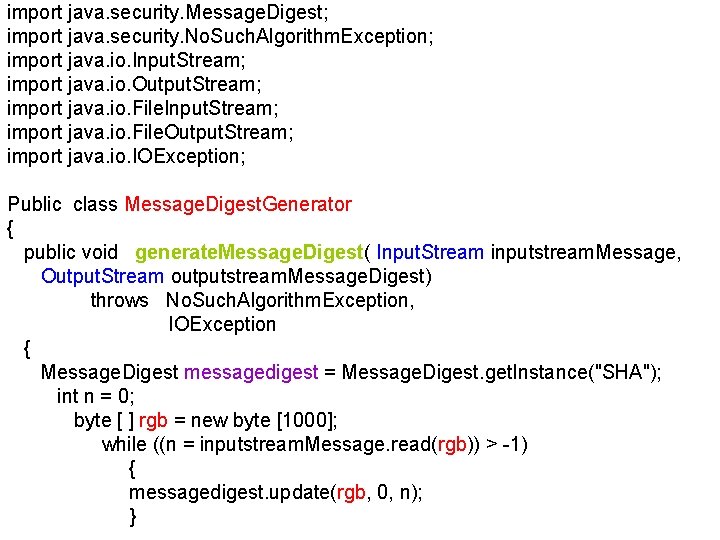
Output. Stream class: write method detailed § void write (byte[] b) v. Writes b. length bytes from the specified byte array to this output stream. v. The general contract for write(b) is that it should have exactly the same effect as the call vwrite(b, 0, b. length). ü Parameters: b - the data. ü Throws: IOException if an I/O error occurs. o Class IOException o java. lang. Object o java. lang. Throwable o java. lang. Exception java. io. IOException

Class File. Input. Stream § public class File. Input. Stream extends Input. Stream v. A File. Input. Stream obtains input bytes from a file in a file system. v What files are available depends on the host environment. v. File. Input. Stream is meant for reading streams of raw bytes such as image data. v. For reading streams of characters, consider using File. Reader.

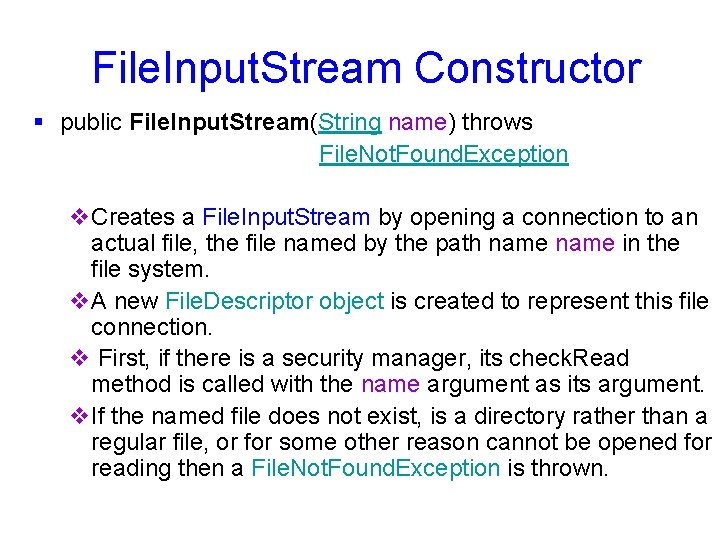
File. Input. Stream Constructor § public File. Input. Stream(String name) throws File. Not. Found. Exception v. Creates a File. Input. Stream by opening a connection to an actual file, the file named by the path name in the file system. v. A new File. Descriptor object is created to represent this file connection. v First, if there is a security manager, its check. Read method is called with the name argument as its argument. v. If the named file does not exist, is a directory rather than a regular file, or for some other reason cannot be opened for reading then a File. Not. Found. Exception is thrown.

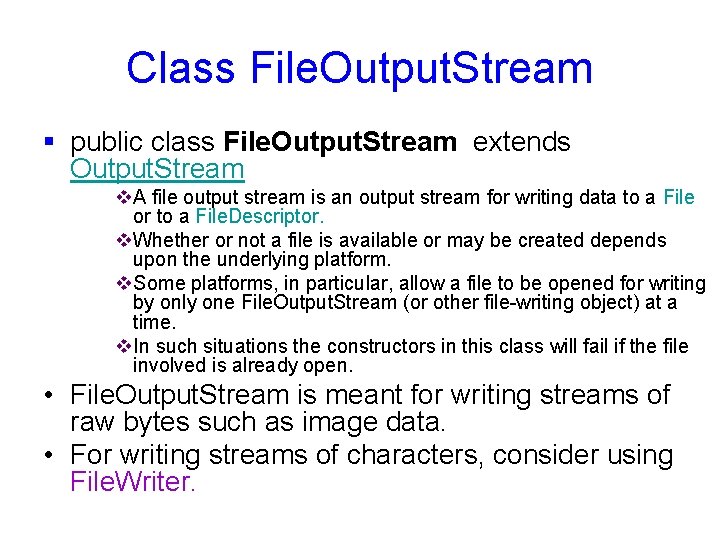
Class File. Output. Stream § public class File. Output. Stream extends Output. Stream v. A file output stream is an output stream for writing data to a File or to a File. Descriptor. v. Whether or not a file is available or may be created depends upon the underlying platform. v. Some platforms, in particular, allow a file to be opened for writing by only one File. Output. Stream (or other file-writing object) at a time. v. In such situations the constructors in this class will fail if the file involved is already open. • File. Output. Stream is meant for writing streams of raw bytes such as image data. • For writing streams of characters, consider using File. Writer.

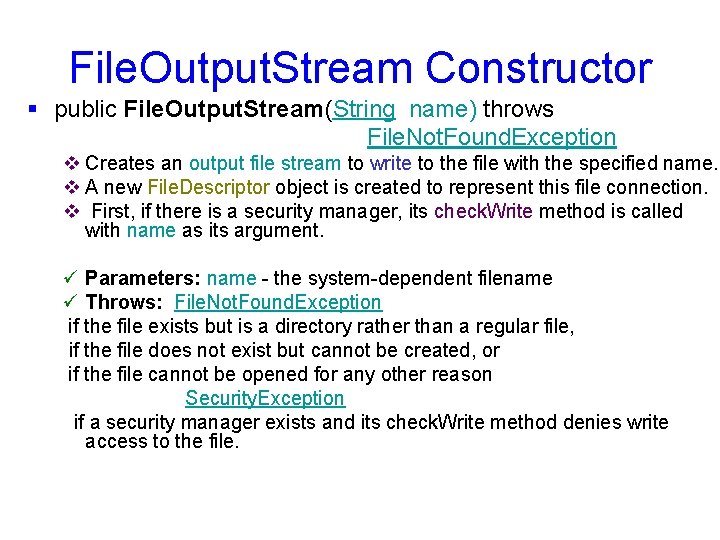
File. Output. Stream Constructor § public File. Output. Stream(String name) throws File. Not. Found. Exception v Creates an output file stream to write to the file with the specified name. v A new File. Descriptor object is created to represent this file connection. v First, if there is a security manager, its check. Write method is called with name as its argument. ü Parameters: name - the system-dependent filename ü Throws: File. Not. Found. Exception if the file exists but is a directory rather than a regular file, if the file does not exist but cannot be created, or if the file cannot be opened for any other reason Security. Exception if a security manager exists and its check. Write method denies write access to the file.

Key in Cryptographic Circles § A key is a piece of information used to encrypt and/or decrypt information § There are two types of key-based cryptography: secret-key and public-key. v. Secret-key cryptography uses a single key that both encrypts and decrypts the information to be protected. v. Both the sender and the receiver must share the secretkey. v. Secret-key cryptography is also known as symmetric cryptography. ü Public-key cryptography uses two keys: a public key and a private key. ü One key decrypts information encrypted with the other. ü Only the private key must be protected. ü Public key cryptography is used for authentication.

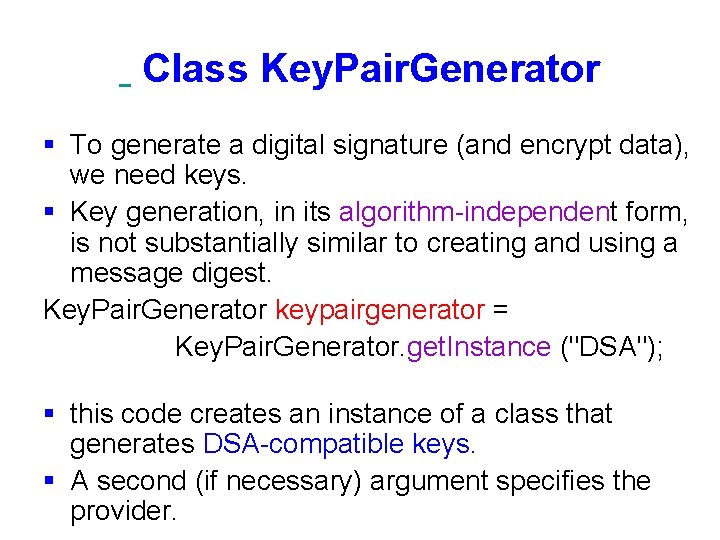
Class Key. Pair. Generator § To generate a digital signature (and encrypt data), we need keys. § Key generation, in its algorithm-independent form, is not substantially similar to creating and using a message digest. Key. Pair. Generator keypairgenerator = Key. Pair. Generator. get. Instance ("DSA"); § this code creates an instance of a class that generates DSA-compatible keys. § A second (if necessary) argument specifies the provider.

§ After a key-pair generator instance is created, it must be initialized. § We can initialize key-pair generators in one of two ways: algorithm-independent or algorithm-dependent. v. Which method we use depends on the amount of control we want over the final result. keypairgenerator. initialize(1024, new Secure. Random()); § Keys based on different algorithms differ in how they're generated, but they have one parameter in common -- the key's strength. § Strength is a relative term that corresponds roughly to how hard the key will be to "break. " § If we use the algorithm-independent initializer, we can specify only the strength -- any algorithm-dependent values assume reasonable defaults.

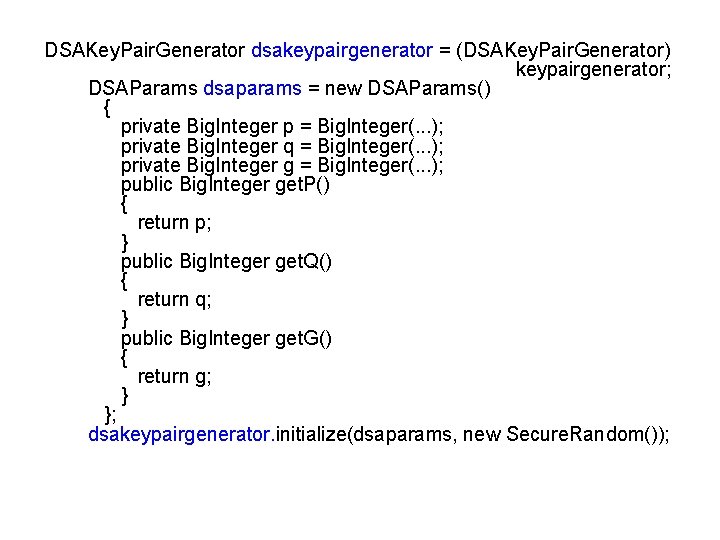
DSAKey. Pair. Generator dsakeypairgenerator = (DSAKey. Pair. Generator) keypairgenerator; DSAParams dsaparams = new DSAParams() { private Big. Integer p = Big. Integer(. . . ); private Big. Integer q = Big. Integer(. . . ); private Big. Integer g = Big. Integer(. . . ); public Big. Integer get. P() { return p; } public Big. Integer get. Q() { return q; } public Big. Integer get. G() { return g; } }; dsakeypairgenerator. initialize(dsaparams, new Secure. Random());

§ While the defaults are usually good enough, if we need more control, it is available. § Let's assume we used the engine to create a generator of DSA-compatible keys, as in the code above. § The engine loaded and instantiated an instance of a class that implements the DSAKey. Pair. Generator interface. § If we cast the generic key-pair generator we received to DSAKey. Pair. Generator, we then gain access to the algorithmdependent method of initialization. § To initialize a DSA key-pair generator, we need three values: the prime P, the subprime Q, and the base G. § These values are captured in an inner class instance that is passed to the initialize() method. • The Secure. Random class provides a secure source of random numbers used in the key-pair generation. return keypairgenerator. generate. Key. Pair(); § The final step involves generating the key pair itself.

The Complete Source Code for a program that Generates a Key Pair.

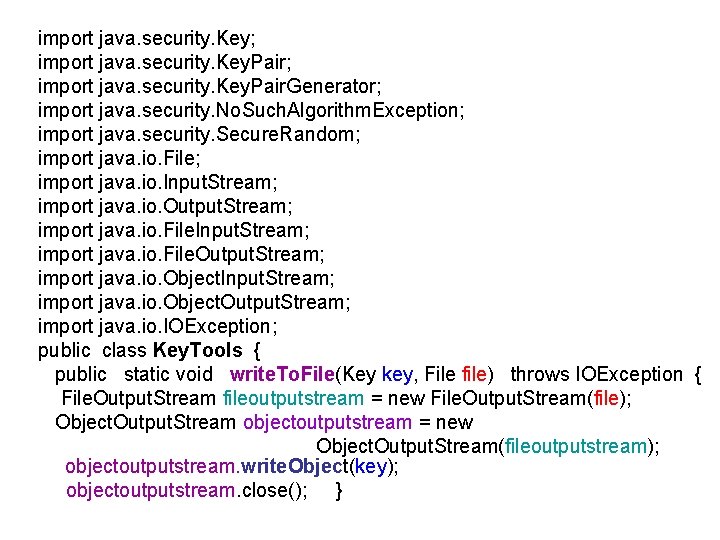
import java. security. Key; import java. security. Key. Pair. Generator; import java. security. No. Such. Algorithm. Exception; import java. security. Secure. Random; import java. io. File; import java. io. Input. Stream; import java. io. Output. Stream; import java. io. File. Input. Stream; import java. io. File. Output. Stream; import java. io. Object. Input. Stream; import java. io. Object. Output. Stream; import java. io. IOException; public class Key. Tools { public static void write. To. File(Key key, File file) throws IOException { File. Output. Stream fileoutputstream = new File. Output. Stream(file); Object. Output. Stream objectoutputstream = new Object. Output. Stream(fileoutputstream); objectoutputstream. write. Object(key); objectoutputstream. close(); }

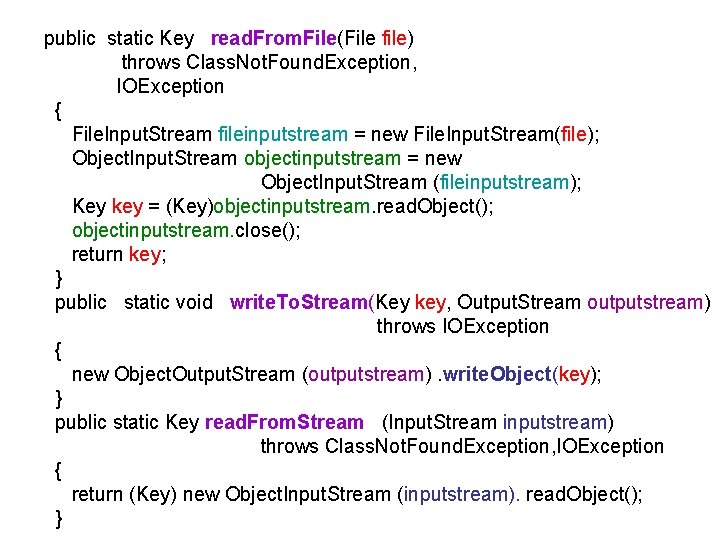
public static Key read. From. File(File file) throws Class. Not. Found. Exception, IOException { File. Input. Stream fileinputstream = new File. Input. Stream(file); Object. Input. Stream objectinputstream = new Object. Input. Stream (fileinputstream); Key key = (Key)objectinputstream. read. Object(); objectinputstream. close(); return key; } public static void write. To. Stream(Key key, Output. Stream outputstream) throws IOException { new Object. Output. Stream (outputstream). write. Object(key); } public static Key read. From. Stream (Input. Stream inputstream) throws Class. Not. Found. Exception, IOException { return (Key) new Object. Input. Stream (inputstream). read. Object(); }

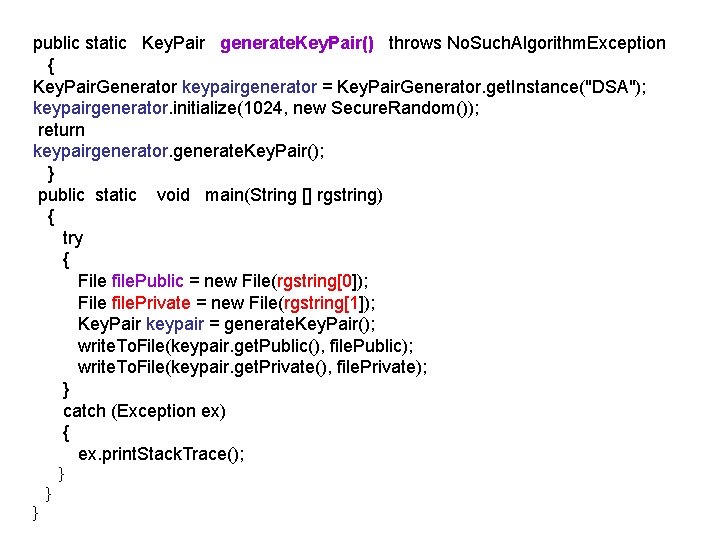
public static Key. Pair generate. Key. Pair() throws No. Such. Algorithm. Exception { Key. Pair. Generator keypairgenerator = Key. Pair. Generator. get. Instance("DSA"); keypairgenerator. initialize(1024, new Secure. Random()); return keypairgenerator. generate. Key. Pair(); } public static void main(String [] rgstring) { try { File file. Public = new File(rgstring[0]); File file. Private = new File(rgstring[1]); Key. Pair keypair = generate. Key. Pair(); write. To. File(keypair. get. Public(), file. Public); write. To. File(keypair. get. Private(), file. Private); } catch (Exception ex) { ex. print. Stack. Trace(); } } }

Class Object. Output. Stream § An Object. Output. Stream writes primitive data types and graphs of Java objects to an Output. Stream. public class Object. Output. Stream extends Output. Stream § For example to write an object that can be read by the example in Object. Input. Stream: File. Output. Stream fos = new File. Output. Stream("t. tmp"); Object. Output. Stream oos = new Object. Output. Stream(fos); oos. write. Int(12345); oos. write. Object ("Today"); oos. write. Object(new Date()); oos. close();

§ Only objects that support the java. io. Serializable interface can be written to streams. § The class of each serializable object is encoded including the class name and signature of the class, the values of the object's fields and arrays, and the closure of any other objects referenced from the initial objects. § The method write. Object is used to write an object to the stream. § Any object, including Strings and arrays, is written with write. Object. § Multiple objects or primitives can be written to the stream. § The objects must be read back from the corresponding Object. Inputstream with the same types and in the same order as they were written

Digital Signature

§ A digital signature is also generated from a message. § It differs from a message digest because the private key of the message generator is incorporated into the computation. § The result is a message that has been "signed" by the one who holds the private key. § The computation is carried out in such a way that anyone can use the message generator's public key to verify that the entity signed it. § A good digital signature algorithm guarantees that the digital signature can't be forged (assuming the private key is secret), vthat the signature is good for only the message from which it was generated, v that the message cannot be changed without invalidating the signature vthat the message's authenticity can be verified.

The digital signature algorithm creates a digital signature from a message and a private key.

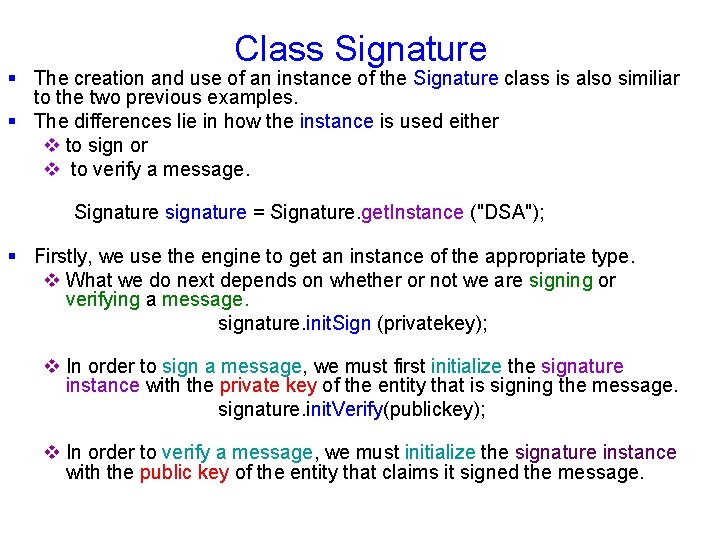
Class Signature § The creation and use of an instance of the Signature class is also similiar to the two previous examples. § The differences lie in how the instance is used either v to sign or v to verify a message. Signature signature = Signature. get. Instance ("DSA"); § Firstly, we use the engine to get an instance of the appropriate type. v What we do next depends on whether or not we are signing or verifying a message. signature. init. Sign (privatekey); v In order to sign a message, we must first initialize the signature instance with the private key of the entity that is signing the message. signature. init. Verify(publickey); v In order to verify a message, we must initialize the signature instance with the public key of the entity that claims it signed the message.
![int n 0 byte rgb new byte 1000 while n int n = 0; byte [] rgb = new byte [1000]; while ((n](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-29.jpg)
int n = 0; byte [] rgb = new byte [1000]; while ((n = inputstream. Message. read(rgb)) > -1) { signature. update(rgb, 0, n); } v Next, regardless of whether or not we are signing or verifying, we must pass the message through the signature generator. ü This process is similiar to the earlier example of generating a message digest. § The final step consists of generating the signature or verifying a signature. rgb = signature. sign(); v If we are signing a message, the sign() method returns the signature. signature. verify (rgb. Signature); v If we are verifying the signature previously generated from a message, v we must use the verify() method. v It takes as a parameter the previously generated signature and determines whether or not it is still valid.

The Complete Source Code for a program that Signs a Message

import java. security. Signature; import java. security. Private. Key; import java. security. No. Such. Algorithm. Exception; import java. security. Invalid. Key. Exception; import java. security. Signature. Exception; import java. io. File; import java. io. Input. Stream; import java. io. File. Input. Stream; import java. io. IOException; public class Sign { public static byte [ ] generate. Signature (Private. Key privatekey, Input. Stream inputstream. Message) throws No. Such. Algorithm. Exception, nvalid. Key. Exception, Signature. Exception, IOException { Signature signature = Signature. get. Instance("DSA"); signature. init. Sign (privatekey); int n = 0; byte [ ] rgb = new byte [1000]; while ((n = inputstream. Message. read(rgb)) > -1) { signature. update (rgb, 0, n); } rgb = signature. sign(); return rgb; }
![public static void mainString rgstring try File file Private new public static void main(String [] rgstring) { try { File file. Private = new](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-32.jpg)
public static void main(String [] rgstring) { try { File file. Private = new File(rgstring[0]); File file. Message = new File(rgstring[1]); File file. Signature = new File(rgstring[2]); Private. Key privatekey = (Private. Key)Key. Tools. read. From. File(file. Private); File. Input. Stream fileinputstream = new File. Input. Stream(file. Message); byte [] rgb = generate. Signature(privatekey, fileinputstream); fileinputstream. close(); Signature. Tools. write. To. File(rgb, file. Signature); } catch (Exception ex) { ex. print. Stack. Trace(); } } }

The Complete Source Code for a program that Verifies a Message.

import java. security. Signature; import java. security. Public. Key; import java. security. No. Such. Algorithm. Exception; import java. security. Invalid. Key. Exception; import java. security. Signature. Exception; import java. io. File; import java. io. Input. Stream; import java. io. IOException; import java. io. Output. Stream; import java. io. File. Input. Stream; import java. io. File. Output. Stream; public class Verify{ public static boolean verify. Signature (Public. Key publickey, Input Stream inputstream. Message, byte [] rgb. Signature) throws No. Such. Algorithm. Exception, Invalid. Key. Exception, Signature. Exception, IOException { Signature signature = Signature. get. Instance("DSA"); signature. init. Verify(publickey); int n = 0; byte [] rgb = new byte [1000]; while ((n = inputstream. Message. read(rgb)) > -1) { signature. update(rgb, 0, n); } return signature. verify(rgb. Signature); }
![public static void mainString rgstring try File file Public public static void main(String [] rgstring) { try { File file. Public =](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-35.jpg)
public static void main(String [] rgstring) { try { File file. Public = new File(rgstring[0]); File file. Message = new File(rgstring[1]); File file. Signature = new File(rgstring[2]); Public. Key publickey = (Public. Key)Key. Tools. read. From. File(file. Public); File. Input. Stream fileinputstream = new File. Input. Stream(file. Message); byte [] rgb = Signature. Tools. read. From. File(file. Signature); if (verify. Signature (publickey, fileinputstream, rgb)) { System. out. println ("true"); } else { System. out. println ("false"); } fileinputstream. close(); } catch (Exception ex) { ex. print. Stack. Trace(); } } }

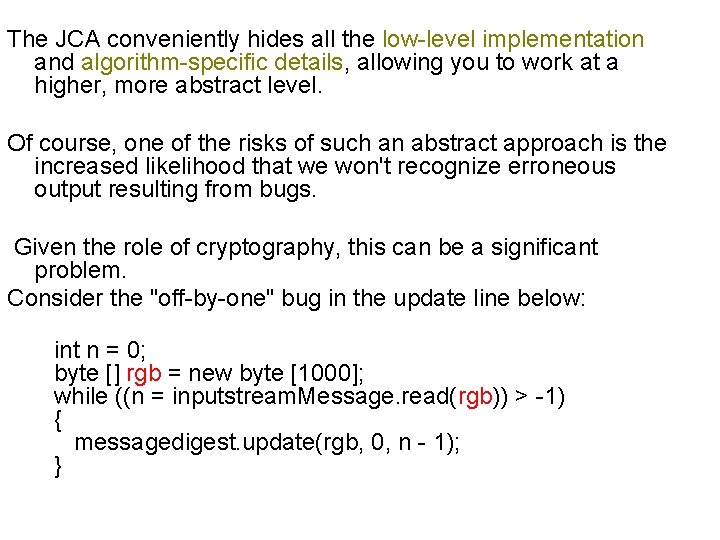
The JCA conveniently hides all the low-level implementation and algorithm-specific details, allowing you to work at a higher, more abstract level. Of course, one of the risks of such an abstract approach is the increased likelihood that we won't recognize erroneous output resulting from bugs. Given the role of cryptography, this can be a significant problem. Consider the "off-by-one" bug in the update line below: int n = 0; byte [] rgb = new byte [1000]; while ((n = inputstream. Message. read(rgb)) > -1) { messagedigest. update(rgb, 0, n - 1); }

§ SUN version 1. 5 sun. security. provider. Sun § Sun. Rsa. Sign version 1. 5 sun. security. rsa. Sun. Rsa. Sign § Sun. JSSE version 1. 5 com. sun. net. ssl. internal. ssl. Provider § Sun. JCE version 1. 5 com. sun. crypto. provider. Sun. JCE § Sun. JGSS version 1. 0 sun. security. jgss. Sun. Provider § Sun. SASL version 1. 5 com. sun. security. sasl. Provider § Sun. Deploy-MSCrypto 1. 5 version com. sun. deploy. security. MSCrypto. Provider

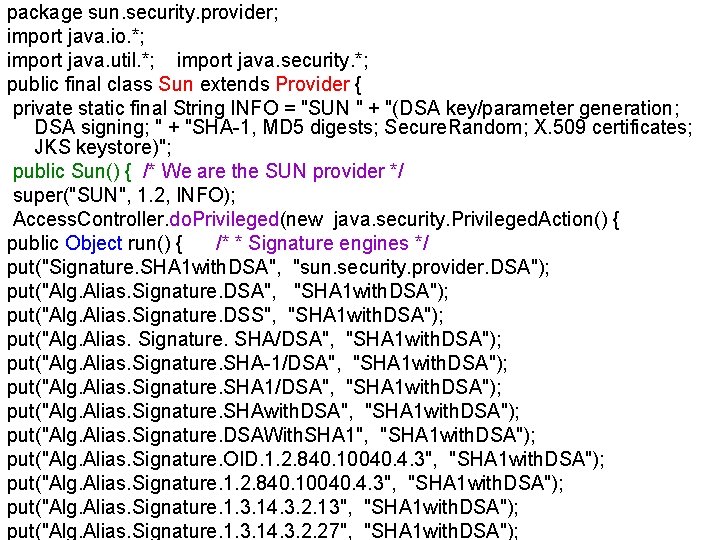
package sun. security. provider; import java. io. *; import java. util. *; import java. security. *; public final class Sun extends Provider { private static final String INFO = "SUN " + "(DSA key/parameter generation; DSA signing; " + "SHA-1, MD 5 digests; Secure. Random; X. 509 certificates; JKS keystore)"; public Sun() { /* We are the SUN provider */ super("SUN", 1. 2, INFO); Access. Controller. do. Privileged(new java. security. Privileged. Action() { public Object run() { /* * Signature engines */ put("Signature. SHA 1 with. DSA", "sun. security. provider. DSA"); put("Alg. Alias. Signature. DSA", "SHA 1 with. DSA"); put("Alg. Alias. Signature. DSS", "SHA 1 with. DSA"); put("Alg. Alias. Signature. SHA/DSA", "SHA 1 with. DSA"); put("Alg. Alias. Signature. SHA-1/DSA", "SHA 1 with. DSA"); put("Alg. Alias. Signature. SHAwith. DSA", "SHA 1 with. DSA"); put("Alg. Alias. Signature. DSAWith. SHA 1", "SHA 1 with. DSA"); put("Alg. Alias. Signature. OID. 1. 2. 840. 10040. 4. 3", "SHA 1 with. DSA"); put("Alg. Alias. Signature. 1. 3. 14. 3. 2. 13", "SHA 1 with. DSA"); put("Alg. Alias. Signature. 1. 3. 14. 3. 2. 27", "SHA 1 with. DSA");

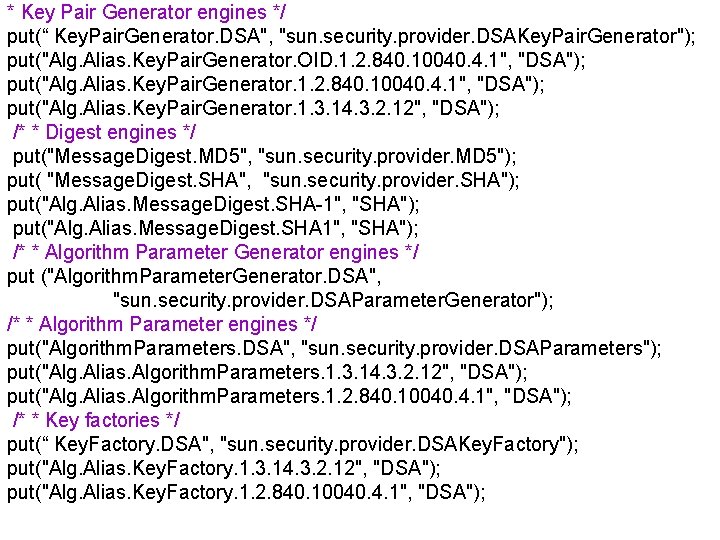
* Key Pair Generator engines */ put(“ Key. Pair. Generator. DSA", "sun. security. provider. DSAKey. Pair. Generator"); put("Alg. Alias. Key. Pair. Generator. OID. 1. 2. 840. 10040. 4. 1", "DSA"); put("Alg. Alias. Key. Pair. Generator. 1. 3. 14. 3. 2. 12", "DSA"); /* * Digest engines */ put("Message. Digest. MD 5", "sun. security. provider. MD 5"); put( "Message. Digest. SHA", "sun. security. provider. SHA"); put("Alg. Alias. Message. Digest. SHA-1", "SHA"); put("Alg. Alias. Message. Digest. SHA 1", "SHA"); /* * Algorithm Parameter Generator engines */ put ("Algorithm. Parameter. Generator. DSA", "sun. security. provider. DSAParameter. Generator"); /* * Algorithm Parameter engines */ put("Algorithm. Parameters. DSA", "sun. security. provider. DSAParameters"); put("Alg. Alias. Algorithm. Parameters. 1. 3. 14. 3. 2. 12", "DSA"); put("Alg. Alias. Algorithm. Parameters. 1. 2. 840. 10040. 4. 1", "DSA"); /* * Key factories */ put(“ Key. Factory. DSA", "sun. security. provider. DSAKey. Factory"); put("Alg. Alias. Key. Factory. 1. 3. 14. 3. 2. 12", "DSA"); put("Alg. Alias. Key. Factory. 1. 2. 840. 10040. 4. 1", "DSA");

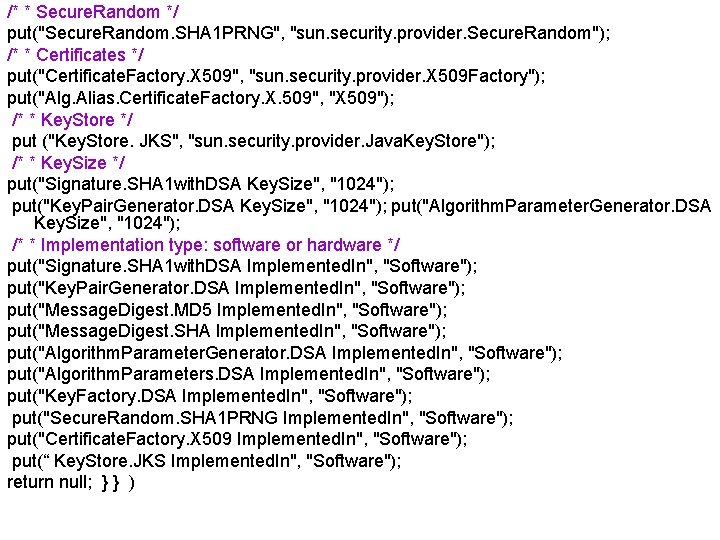
/* * Secure. Random */ put("Secure. Random. SHA 1 PRNG", "sun. security. provider. Secure. Random"); /* * Certificates */ put("Certificate. Factory. X 509", "sun. security. provider. X 509 Factory"); put("Alg. Alias. Certificate. Factory. X. 509", "X 509"); /* * Key. Store */ put ("Key. Store. JKS", "sun. security. provider. Java. Key. Store"); /* * Key. Size */ put("Signature. SHA 1 with. DSA Key. Size", "1024"); put("Key. Pair. Generator. DSA Key. Size", "1024"); put("Algorithm. Parameter. Generator. DSA Key. Size", "1024"); /* * Implementation type: software or hardware */ put("Signature. SHA 1 with. DSA Implemented. In", "Software"); put("Key. Pair. Generator. DSA Implemented. In", "Software"); put("Message. Digest. MD 5 Implemented. In", "Software"); put("Message. Digest. SHA Implemented. In", "Software"); put("Algorithm. Parameter. Generator. DSA Implemented. In", "Software"); put("Algorithm. Parameters. DSA Implemented. In", "Software"); put("Key. Factory. DSA Implemented. In", "Software"); put("Secure. Random. SHA 1 PRNG Implemented. In", "Software"); put("Certificate. Factory. X 509 Implemented. In", "Software"); put(“ Key. Store. JKS Implemented. In", "Software"); return null; } } )

Example: Java Security Providers § The following Java 2 applet enumerates all the Java Security Providers available to the j 2 re and their associated properties and values. § These property values specify the engine. algorithms and the classes that implement them, as well as other properties. § The public method of the applet is accessed by a scripted call to the method from Java. Script. § The method returns the data in a formatted table string. § A Java. Script function embeds the table of results into a simple html page in another scripted window.

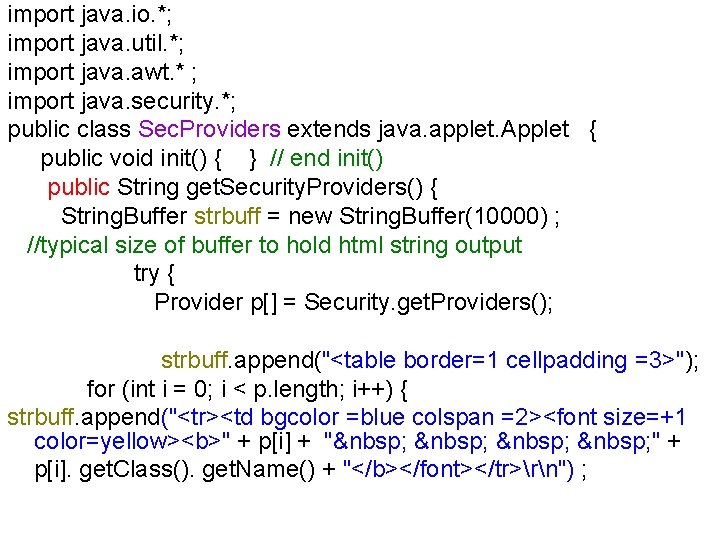
import java. io. *; import java. util. *; import java. awt. * ; import java. security. *; public class Sec. Providers extends java. applet. Applet { public void init() { } // end init() public String get. Security. Providers() { String. Buffer strbuff = new String. Buffer(10000) ; //typical size of buffer to hold html string output try { Provider p[] = Security. get. Providers(); strbuff. append("<table border=1 cellpadding =3>"); for (int i = 0; i < p. length; i++) { strbuff. append("<tr><td bgcolor =blue colspan =2><font size=+1 color=yellow><b>" + p[i] + " " + p[i]. get. Class(). get. Name() + "</b></font></tr>rn") ;
![for Enumeration e pi keys e has More Elements String key for (Enumeration e = p[i]. keys(); e. has. More. Elements(); ) { String key](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-43.jpg)
for (Enumeration e = p[i]. keys(); e. has. More. Elements(); ) { String key = (String) e. next. Element() ; strbuff. append("<tr><td>" + key + "</td><td>" + p[i]. get. Property(key) + "</td></tr>rn") ; } strbuff. append("</table>rn") ; return strbuff. to. String(); } catch (Exception e) { return e. to. String(); } } }

The subclasses of the Provider class For each service implemented by the provider, there must be a property whose name is the type of service: v Signature. alg. Name [one or more spaces] attr. Name v Message. Digest. alg. Name [one or more spaces] attr. Name v Key. Pair. Generator. alg. Name [one/more spaces] attr. Name v Secure. Random. alg. Name [one /spaces] attr. Name v Key. Factory. alg. Name [one / spaces] attr. Name v Certificate. Factory. cert. Type [one or more spaces] attr. Name v Key. Store. store. Type [one or more spaces] attr. Name v Algorithm. Parameter. Generator. alg. Name [one / spaces] attr. Name v Algorithm. Parameters. alg. Name [one / more spaces] attr. Name

Java Security Provider Examples § The default provider "SUN" implements the SHA 1 with. DSA Digital Signature Algorithm in software. § In the master class for the provider "SUN", it sets the "Signature. SHA 1 with. DSA Implemented. In" to have the value "Software" via the following: put ("Signature. SHA 1 with. DSA Implemented. In", "Software") § The default provider "SUN" implements the Digital Signature Algorithm (whose standard name is "SHA 1 with. DSA") in a class named DSA in the sun. security. provider package. • Its subclass of Provider sets the Signature. SHA 1 with. DSA property to have the value "sun. security. provider. DSA" via the following: put("Signature. SHA 1 with. DSA", "sun. security. provider. DSA")
![get Providers method public static Provider get Providers v Returns an array get. Providers method § public static Provider[ ] get. Providers() v. Returns an array](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-46.jpg)
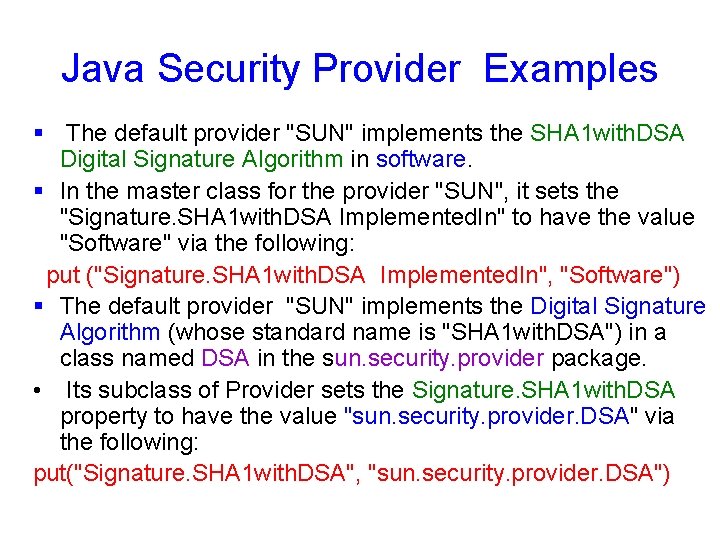
get. Providers method § public static Provider[ ] get. Providers() v. Returns an array containing all the installed providers. The order of the providers in the array is their preference order. üReturns an array of all the installed providers.

get. Provider method § public static Provider get. Provider(String name) v. Returns the provider installed with the specified name, if any. v. Returns null if no provider with the specified name is installed. ü Parameters: name - the name of the provider to get. ü Returns: he provider of the specified name.
![get Providers method public static Provider get Providers Map filter v Returns get Providers method § public static Provider [] get. Providers (Map filter) v Returns](https://slidetodoc.com/presentation_image_h/330a55b40a4821a06798d3142bfdb01b/image-48.jpg)
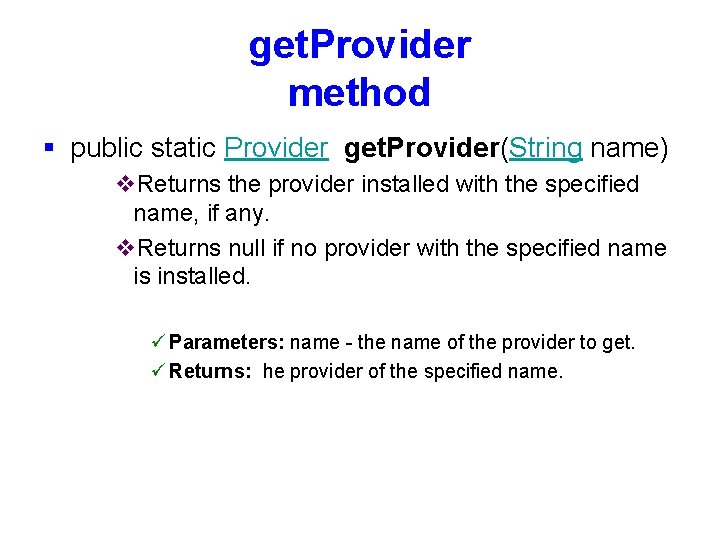
get Providers method § public static Provider [] get. Providers (Map filter) v Returns an array containing all installed providers that satisfy the specified selection criteria, or v Returns null if no such providers have been installed. v. The returned providers are ordered according to their preference order ü Parameters: filter - the criteria for selecting providers. The filter is caseinsensitive. ü Returns: all the installed providers that satisfy the selection criteria, or null if no such providers have been installed. ü Throws: Invalid. Parameter. Exception - if the filter is not in the required format § The selection criteria are represented by a map. § Each map entry represents a selection criterion. § A provider is selected iff it satisfies all selection criteria.

The key entry § The key for any entry in such a map must be in one of the following two formats: <crypto_service>. <algorithm_or_type> Message. Digest. SHA-384 , Message. Digest. MD 5 , v The cryptographic service name must not contain any dots. v The value associated with the key must be an empty string. v A provider satisfies this selection criterion iff the provider implements the specified algorithm or type for the specified cryptographic service. <crypto_service>. <algorithm_or_type> <attribute_name> Provider. id class. Name , Provider. id version , Key. Store. JKS Implemented. In , Message. Digest. SHA Implemented. In , Key. Factory. DSA Implemented. In v The cryptographic service name must not contain any dots. v The value associated with the key must be a non-empty string. v A provider satisfies this selection criterion iff the provider implements the specified algorithm or type for the specified cryptographic service and its implementation meets the constraint expressed by the specified attribute name/value pair.