An enhanced fragile watermarking scheme to digital image


![Experimental results [10] S. Saeed, A. A. Mohammad, A source-channel coding approach to digital Experimental results [10] S. Saeed, A. A. Mohammad, A source-channel coding approach to digital](https://slidetodoc.com/presentation_image_h/33a3b5bdacafc4ca9dc23822fd850389/image-9.jpg)

- Slides: 10

An enhanced fragile watermarking scheme to digital image protection and self-recovery u Source : Signal Processing Image Communication Vol. 66, pp. 19 -29, Aug 2018 u Authors : Ming. Quan Fan, Hong. Xia Wang u Speaker : Si-Liang He u Date : 2018/8/3 1

Outline Introduction Related work Proposed scheme Experimental results Conclusions 2

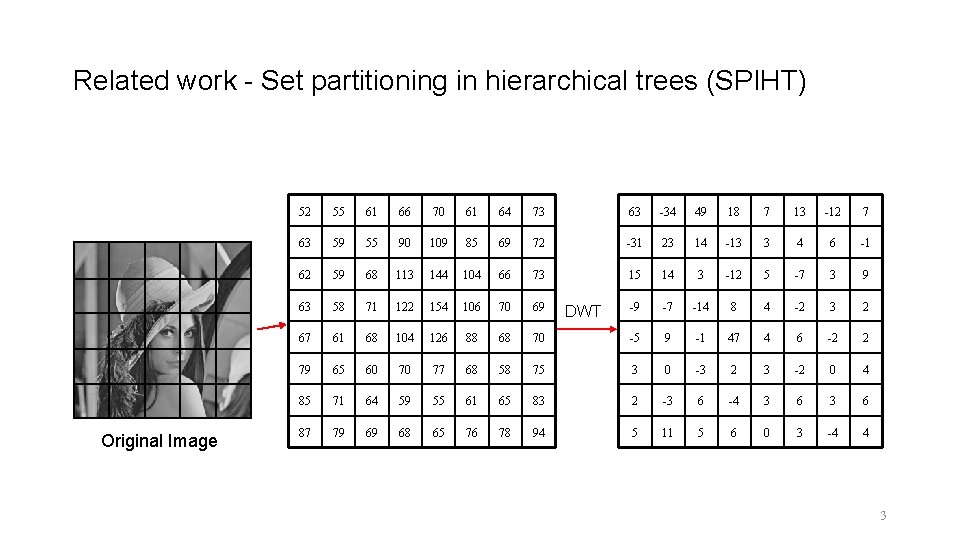
Related work - Set partitioning in hierarchical trees (SPIHT) Original Image 52 55 61 66 70 61 64 73 63 -34 49 18 7 13 -12 7 63 59 55 90 109 85 69 72 -31 23 14 -13 3 4 6 -1 62 59 68 113 144 104 66 73 15 14 3 -12 5 -7 3 9 63 58 71 122 154 106 70 69 -9 -7 -14 8 4 -2 3 2 67 61 68 104 126 88 68 70 -5 9 -1 47 4 6 -2 2 79 65 60 70 77 68 58 75 3 0 -3 2 3 -2 0 4 85 71 64 59 55 61 65 83 2 -3 6 -4 3 6 87 79 69 68 65 76 78 94 5 11 5 6 0 3 -4 4 DWT 3

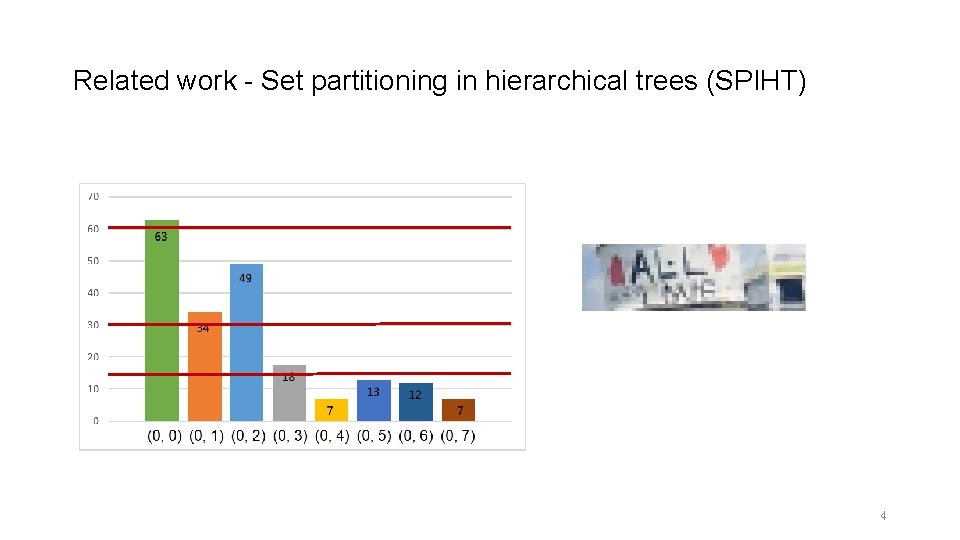
Related work - Set partitioning in hierarchical trees (SPIHT) 4

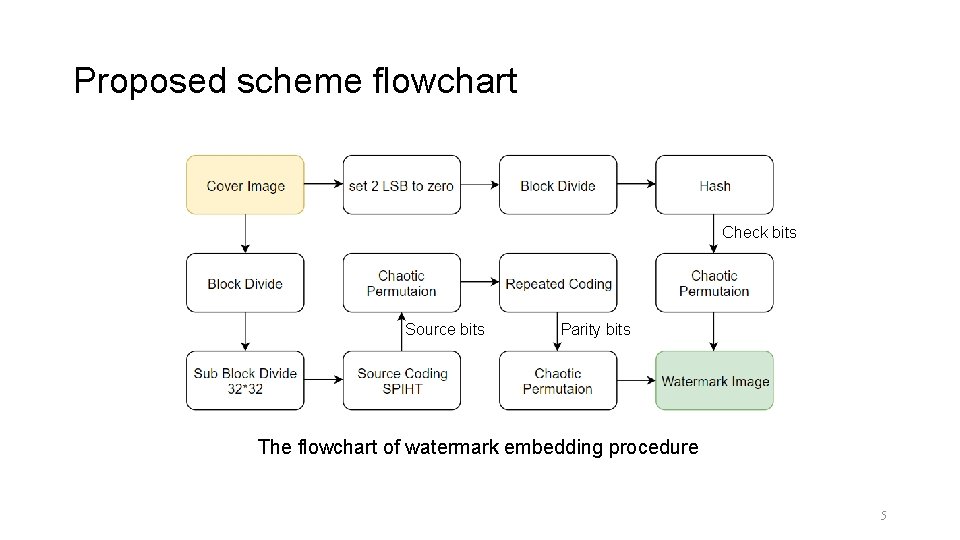
Proposed scheme flowchart Check bits Source bits Parity bits The flowchart of watermark embedding procedure 5

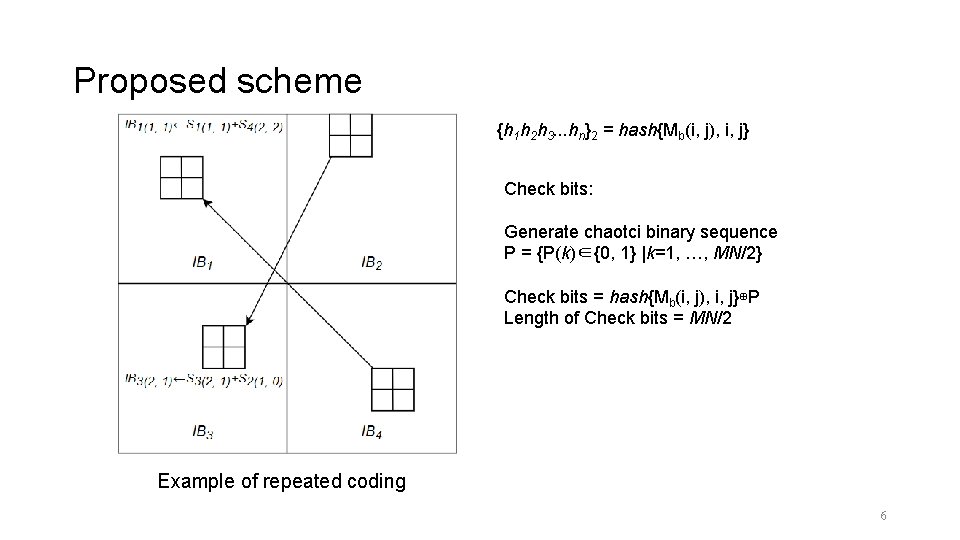
Proposed scheme {h 1 h 2 h 3. . . hn}2 = hash{Mb(i, j), i, j} Check bits: Generate chaotci binary sequence P = {P(k)∈{0, 1} |k=1, …, MN/2} Check bits = hash{Mb(i, j), i, j}⊕P Length of Check bits = MN/2 Example of repeated coding 6

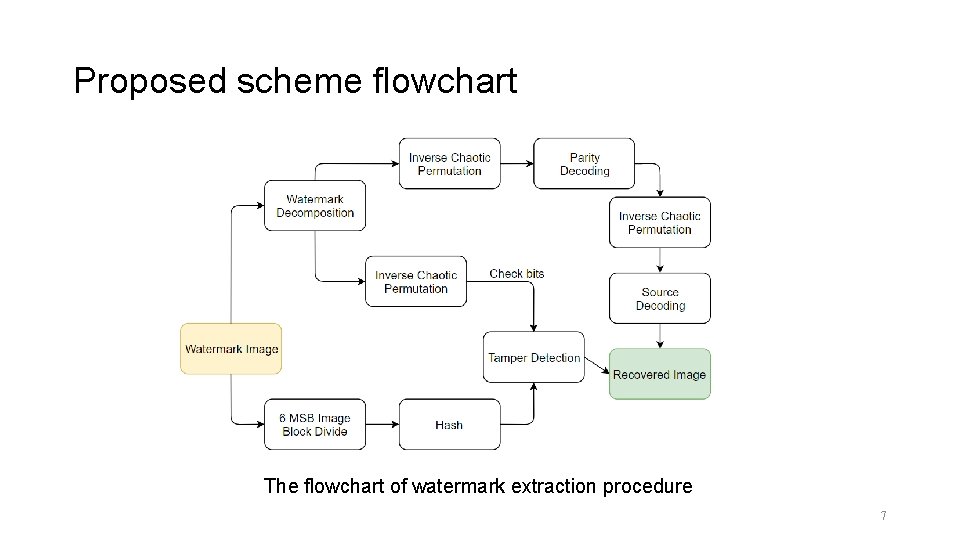
Proposed scheme flowchart The flowchart of watermark extraction procedure 7

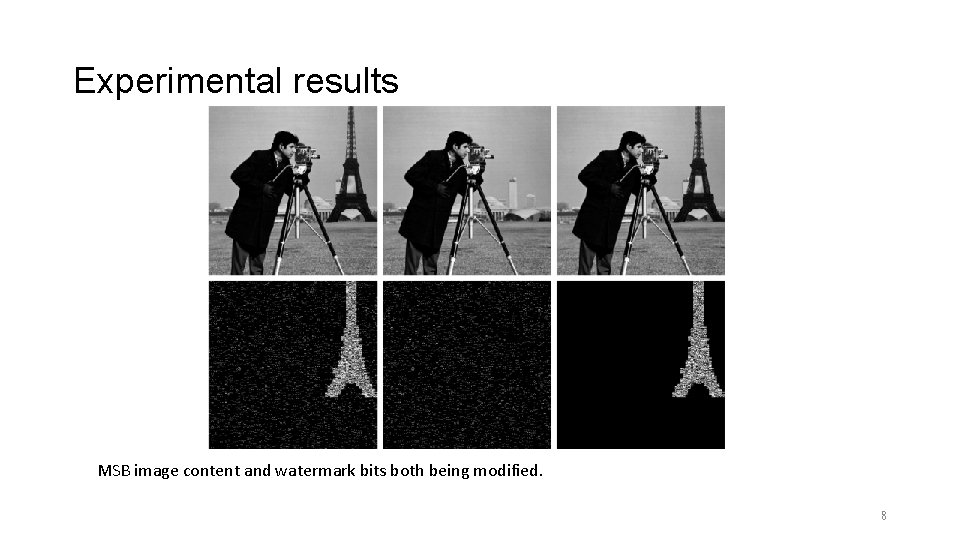
Experimental results MSB image content and watermark bits both being modified. 8
![Experimental results 10 S Saeed A A Mohammad A sourcechannel coding approach to digital Experimental results [10] S. Saeed, A. A. Mohammad, A source-channel coding approach to digital](https://slidetodoc.com/presentation_image_h/33a3b5bdacafc4ca9dc23822fd850389/image-9.jpg)
Experimental results [10] S. Saeed, A. A. Mohammad, A source-channel coding approach to digital image protection and self-recovery, IEEE Trans. Image Process, 24(7) (2015), pp. 2266 -2277 [12] Sreeja M. S. , Ann N. N. Enhancing the protection of digital images against tampering using joint source channel coding, Int. J. Sci. Res. , 5 (6) (2016), pp. 1419 -1421 9

Conclusions The proposed scheme has a higher chance to recover images The proposed scheme can distinguish whether MSB image content or watermark bits has been tampered with. 10