An Energy Balanced Flooding Algorithm for a BLE
An Energy Balanced Flooding Algorithm for a BLE Mesh Network SPEAKER : Chung-Yuan Cheng ADVISOR: DR. HO-TING WU Date: 2020/10/7

Outline • Introduction • BLE & BLE mesh • BLE mesh challenges • Fruitymesh • Trickle protocol & Drypp algorithm • Experimentation • Results • Conclusion • References 2
Introduction • Nowadays, there are many wireless communication technologies that can be used for the deployment of Io. T applications in domestic, urban, and industrial scenarios. Prominent examples are Zig. Bee, ZWave, Wi-Fi, Bluetooth Low Energy (BLE) , Thread, 6 Lo. WPAN. • BLE is a widely used short-range technology, which has gained a dominant position thanks to its simplicity, low-power consumption, low-cost and robustness. BLE is currently present in almost all smartphones, tablets, computers and consumer electronics in general. 3

Introduction(cont’d) • Unlike other technologies such as Wi. Fi or Zig. Bee, until 2017, BLE lacked the capability of mesh networking. Mesh networks allow data transmission between pairs of nodes in a dynamic and nonhierarchical way. • The BLE SIG has only considered a flooding protocol in its first version. Indeed, a managed flooding, halfway between the basic flooding and routing. 4
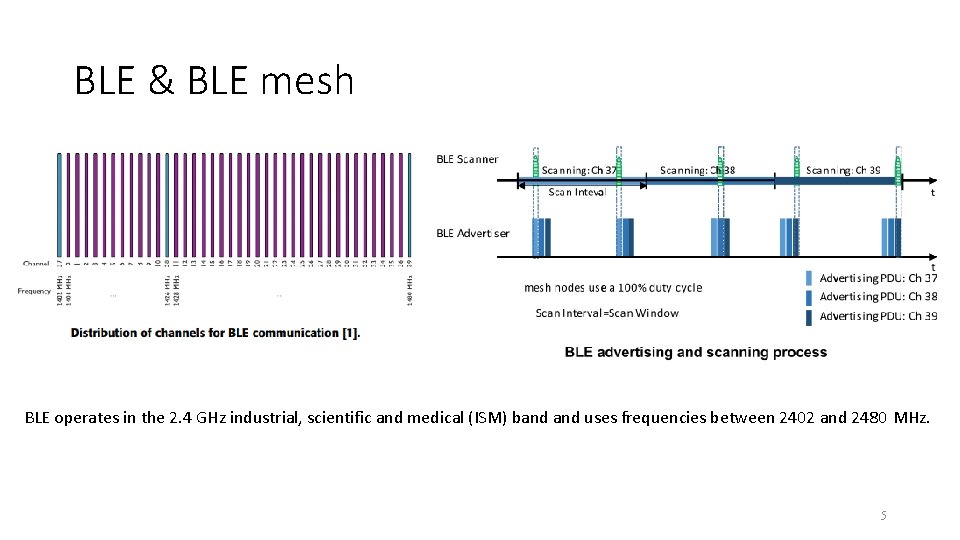
BLE & BLE mesh BLE operates in the 2. 4 GHz industrial, scientific and medical (ISM) band uses frequencies between 2402 and 2480 MHz. 5
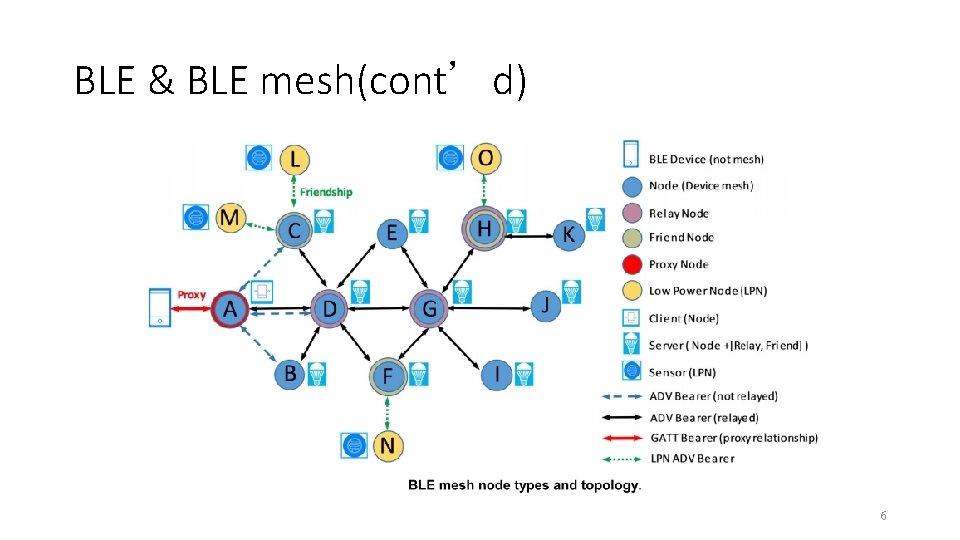
BLE & BLE mesh(cont’d) 6
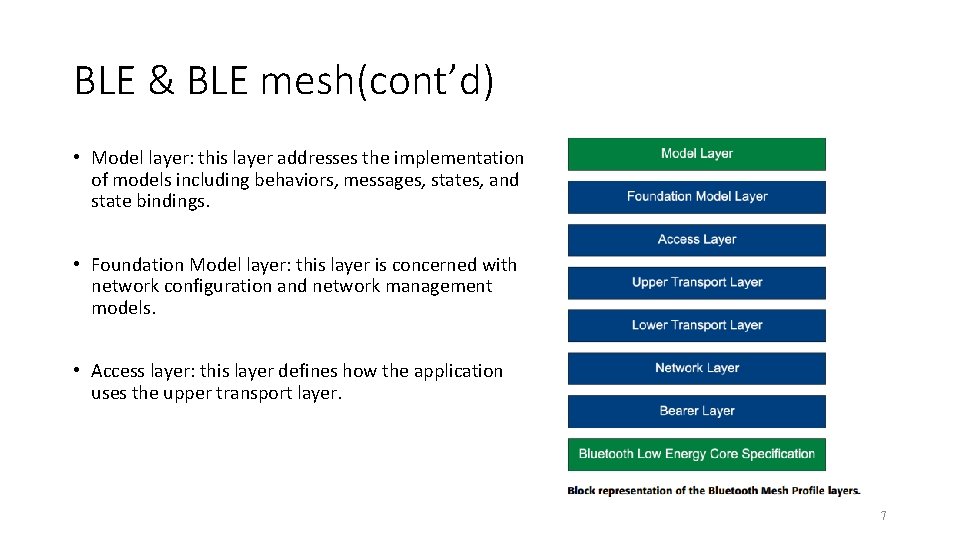
BLE & BLE mesh(cont’d) • Model layer: this layer addresses the implementation of models including behaviors, messages, states, and state bindings. • Foundation Model layer: this layer is concerned with network configuration and network management models. • Access layer: this layer defines how the application uses the upper transport layer. 7
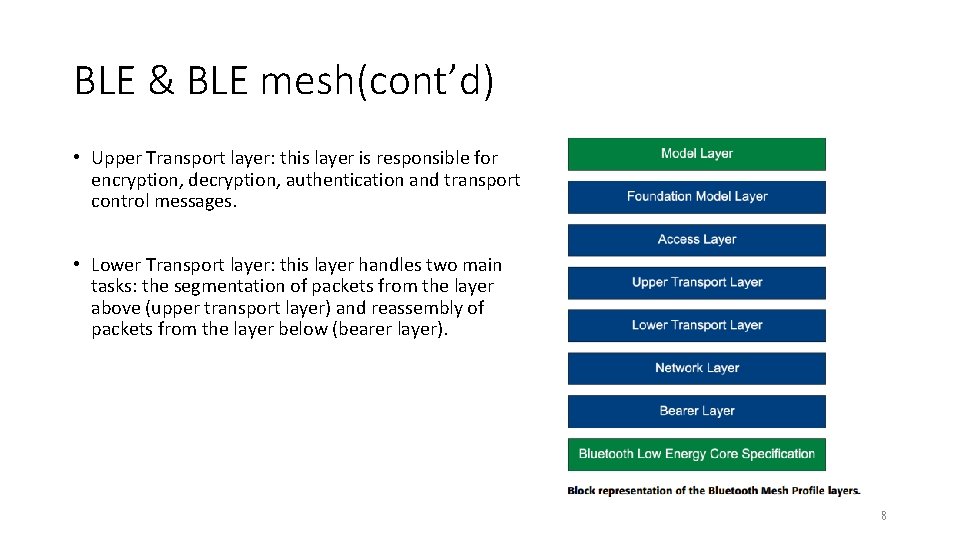
BLE & BLE mesh(cont’d) • Upper Transport layer: this layer is responsible for encryption, decryption, authentication and transport control messages. • Lower Transport layer: this layer handles two main tasks: the segmentation of packets from the layer above (upper transport layer) and reassembly of packets from the layer below (bearer layer). 8
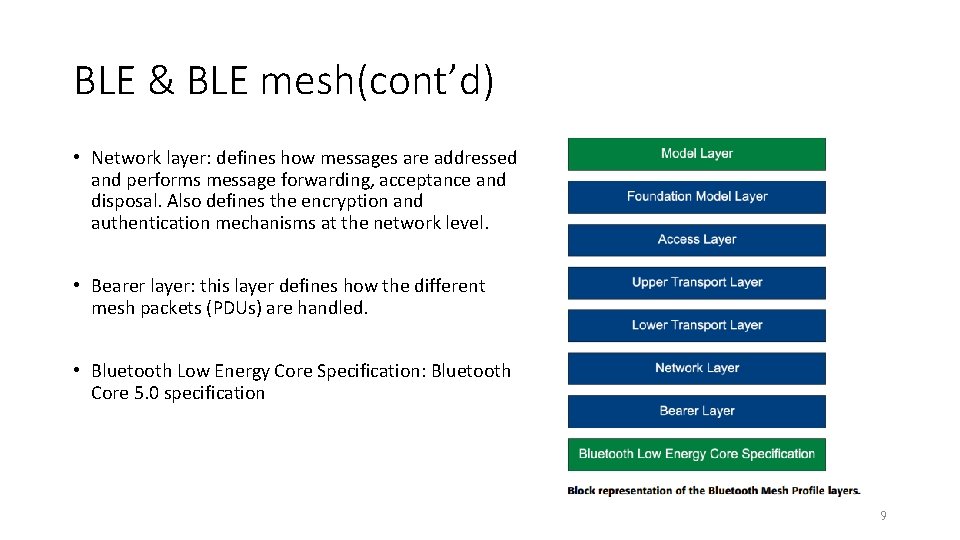
BLE & BLE mesh(cont’d) • Network layer: defines how messages are addressed and performs message forwarding, acceptance and disposal. Also defines the encryption and authentication mechanisms at the network level. • Bearer layer: this layer defines how the different mesh packets (PDUs) are handled. • Bluetooth Low Energy Core Specification: Bluetooth Core 5. 0 specification 9

BLE mesh challenges • Self optimized meshed network (son) • Parameters such as network transmit, publish and relay retransmit counts, interval steps and time-to-life need to be correctly tuned • The optimal values of these parameters will depend on the network layout, propagation conditions, interferences, Qo. S required for each service, etc • Dynamic and self-organized Bluetooth mesh networks constitute an interesting research topic 10

BLE mesh challenges(cont’d) • Soft combining • The managed flooding protocol allows the nodes to receive multiple copies of the original packet • The transmitter can generate different sets of coded bits, different incremental redundancy versions • The frame structure would allow a simplementation that may be of particular interest in scenarios where it is necessary to increase the range or overcome difficult attenuation situations. 11

BLE mesh challenges(cont’d) • Bluetooth 5 and newbearers • Bluetooth 5 is the first version of Bluetooth mesh uses non-connectable (broadcast only) and non-scannable advertising packets as a bearer • This type of packet entails a limitation in the amount of information that can be sent, the latency, immunity against interferences, the implementation of ACK protocols and eventually, in the communication throughput 12

BLE mesh challenges(cont’d) • Angle of arrival and departure • Bluetooth 5. 1 specifications have incorporated procedures to estimate Angle of Arrival (Ao. A) and Angle of Departure (Ao. D) of the received and transmitted signal • This information is aimed for location services but could also be exploited by mesh deployments. • Ao. A and Ao. D require that receiver and transmitter respectively have an array of antennas, which opens the door to introduce beamforming Such features could be used to increase the efficiency, performance and network range. 13

BLE mesh challenges(cont’d) • Energy consumption consideration • The mesh Bluetooth standard contemplates the use of low power consumption nodes. This functionality is reserved for applications which emit information periodically and that are delay tolerant • Relay nodes would require an external power supply, either from the power grid or through energy harvesting techniques • Bluetooth periodic advertising could be rethought for mesh networking to allow the relay (acting as a scanner) to sync with the transmitter 14

Fruitymesh • Fruitymesh is an algorithm for the creation and maintenance of a mesh BLE network topology. • Fruitymesh is based on neighbour-only routing, where no routing tables are stored but a connection is established between two nodes and kept open until the packets reach their final destination. 15
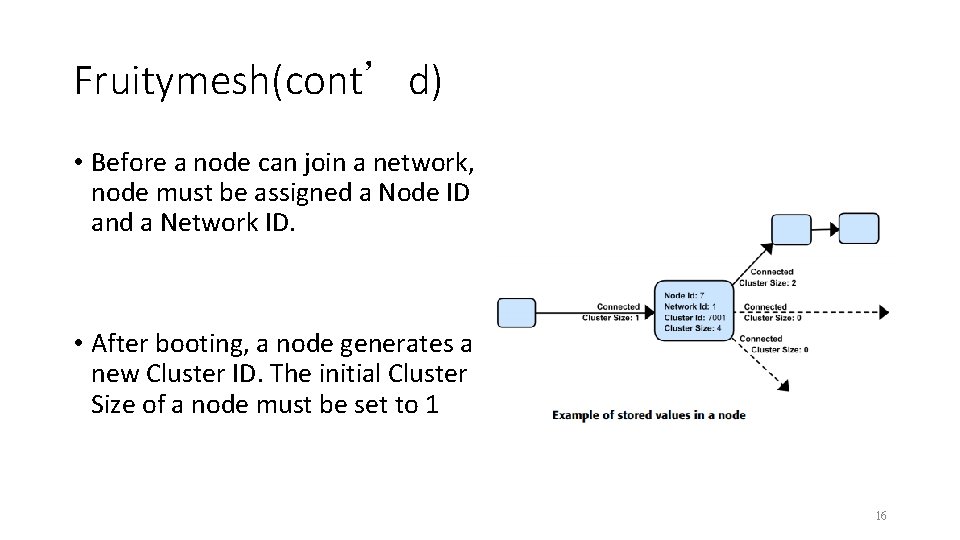
Fruitymesh(cont’d) • Before a node can join a network, node must be assigned a Node ID and a Network ID. • After booting, a node generates a new Cluster ID. The initial Cluster Size of a node must be set to 1 16
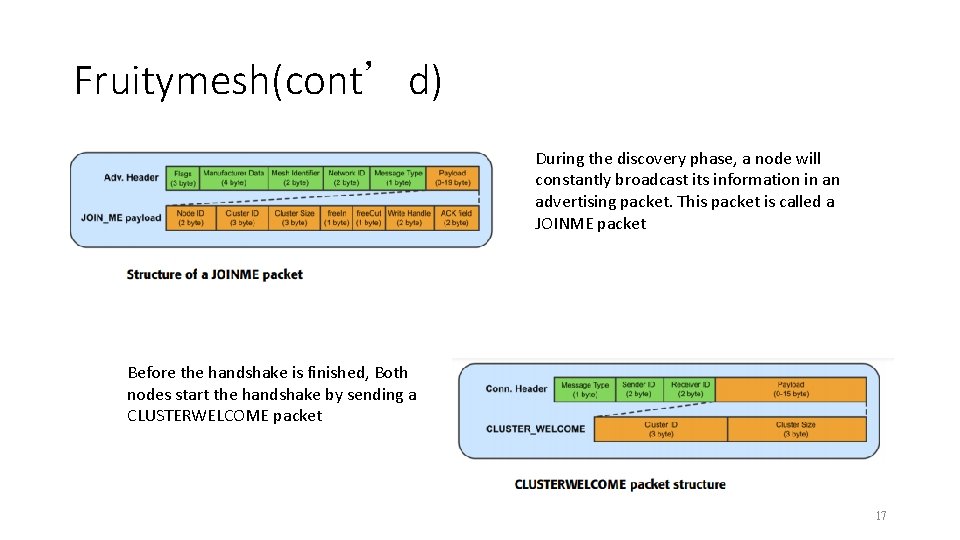
Fruitymesh(cont’d) During the discovery phase, a node will constantly broadcast its information in an advertising packet. This packet is called a JOINME packet Before the handshake is finished, Both nodes start the handshake by sending a CLUSTERWELCOME packet 17
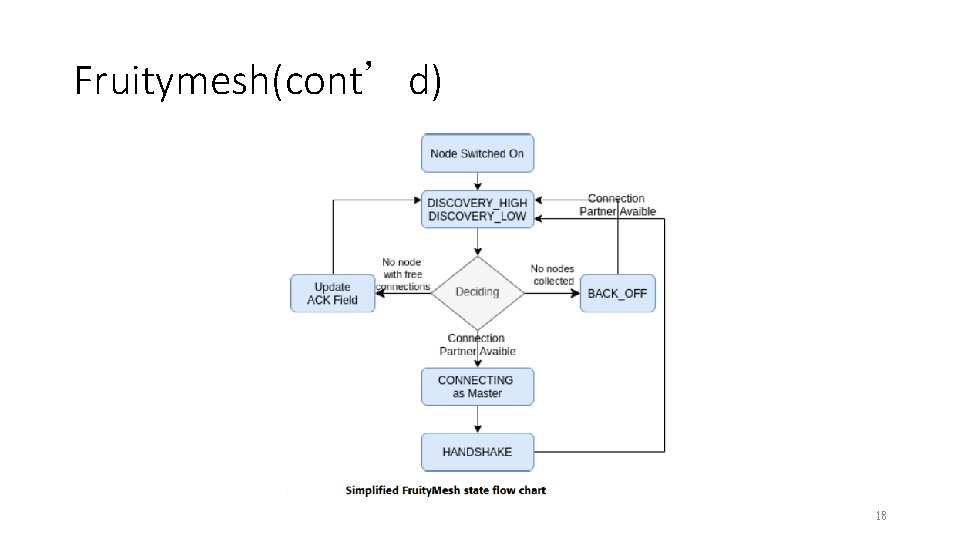
Fruitymesh(cont’d) 18

Trickle protocol • Trickle algorithm is a flooding control algorithm for wireless networks. It helps reduce the amount of redundant network traffic by adapting transmission rates to network density. 19

Trickle protocol (cont’d) • design-time parameters: • the minimum interval size ‘‘Imin’’ • the maximum interval size ‘‘Imax’’ • redundancy constant ‘‘k’’ • run-time parameters: • the current interval size ‘‘I’’ • time within the current interval ‘‘t’’ • counter ‘‘c’’ 20

Trickle protocol (cont’d) • 1. When the algorithm starts execution, it sets I to a value in the range of [Imin, Imax] , then begins the first interval • 2. When an interval begins, Trickle resets c to 0 and sets t to a random point in the interval, taken from the range [I/2, I) • 3. Whenever Trickle hears a transmission that is ‘‘consistent’’, it increments the counter c 21

Trickle protocol (cont’d) • 4. At time t, Trickle transmits if and only if the counter c is less than the redundancy constant k • 5. When the interval I expires, I*2. If I > Imax, Trickle sets the interval length I to be the time specified by Imax • 6. If Trickle hears a transmission that is ‘‘inconsistent’’ and I is greater than Imin, it resets I to Imin and starts a new interval as in step 2. If I is equal to Imin when Trickle hears an ‘‘inconsistent’’ transmission, Trickle does nothing or reset its timer in response to external ‘‘events’’ 22
Drypp algorithm • Based on the Trickle algorithm, the Drypp algorithm was proposed • The addition of two interval change constants, α and β, changes the value of the current Trickle interval I and the maximum interval Imax • The other constant is Imp with value 3. 23

Drypp algorithm(cont’d) • 24
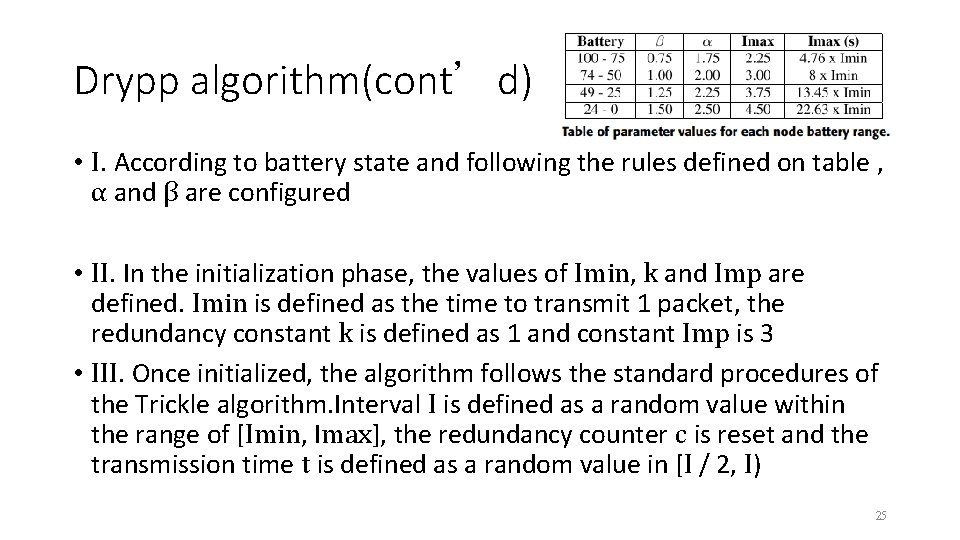
Drypp algorithm(cont’d) • I. According to battery state and following the rules defined on table , α and β are configured • II. In the initialization phase, the values of Imin, k and Imp are defined. Imin is defined as the time to transmit 1 packet, the redundancy constant k is defined as 1 and constant Imp is 3 • III. Once initialized, the algorithm follows the standard procedures of the Trickle algorithm. Interval I is defined as a random value within the range of [Imin, Imax], the redundancy counter c is reset and the transmission time t is defined as a random value in [I / 2, I) 25
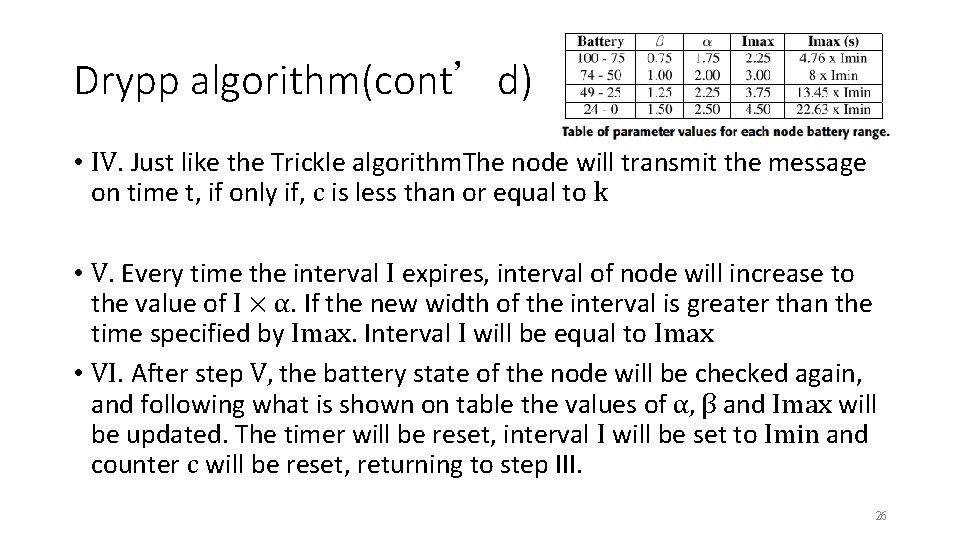
Drypp algorithm(cont’d) • IV. Just like the Trickle algorithm. The node will transmit the message on time t, if only if, c is less than or equal to k • V. Every time the interval I expires, interval of node will increase to the value of I × α. If the new width of the interval is greater than the time specified by Imax. Interval I will be equal to Imax • VI. After step V, the battery state of the node will be checked again, and following what is shown on table the values of α, β and Imax will be updated. The timer will be reset, interval I will be set to Imin and counter c will be reset, returning to step III. 26
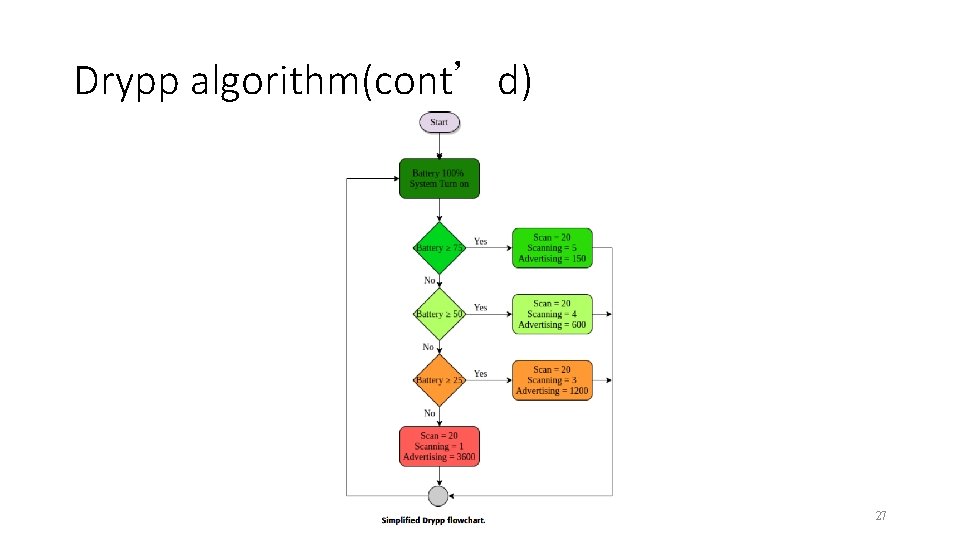
Drypp algorithm(cont’d) 27
Experimentation • The Nordic Semiconductors Software Development Kit (SDK) version 14 for the n. RF 52 family utilized did not allow access Trickle code. Due to this, the proposed protocol was not fully implemented as Fruity. Mesh only supports the SDK version 14. Today the SDK is in its version 16 28
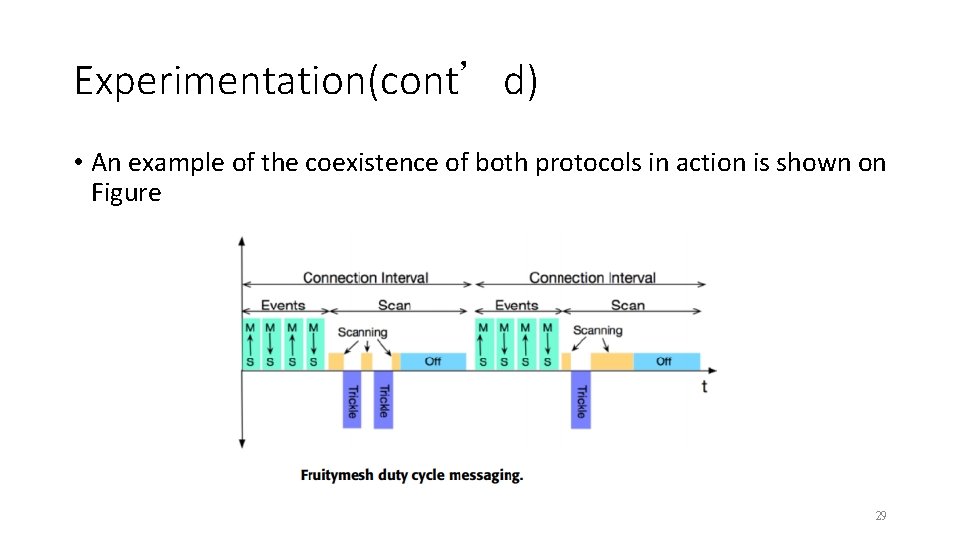
Experimentation(cont’d) • An example of the coexistence of both protocols in action is shown on Figure 29
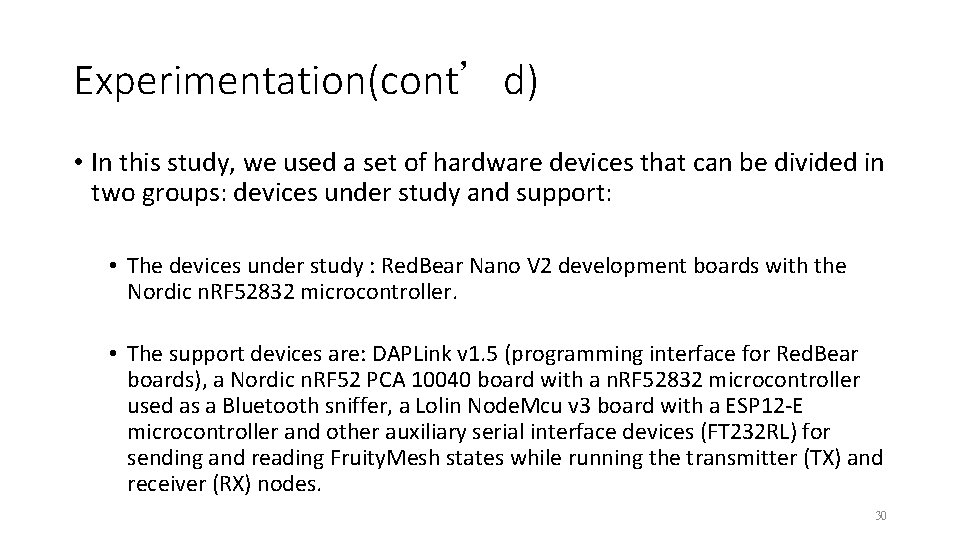
Experimentation(cont’d) • In this study, we used a set of hardware devices that can be divided in two groups: devices under study and support: • The devices under study : Red. Bear Nano V 2 development boards with the Nordic n. RF 52832 microcontroller. • The support devices are: DAPLink v 1. 5 (programming interface for Red. Bear boards), a Nordic n. RF 52 PCA 10040 board with a n. RF 52832 microcontroller used as a Bluetooth sniffer, a Lolin Node. Mcu v 3 board with a ESP 12 -E microcontroller and other auxiliary serial interface devices (FT 232 RL) for sending and reading Fruity. Mesh states while running the transmitter (TX) and receiver (RX) nodes. 30
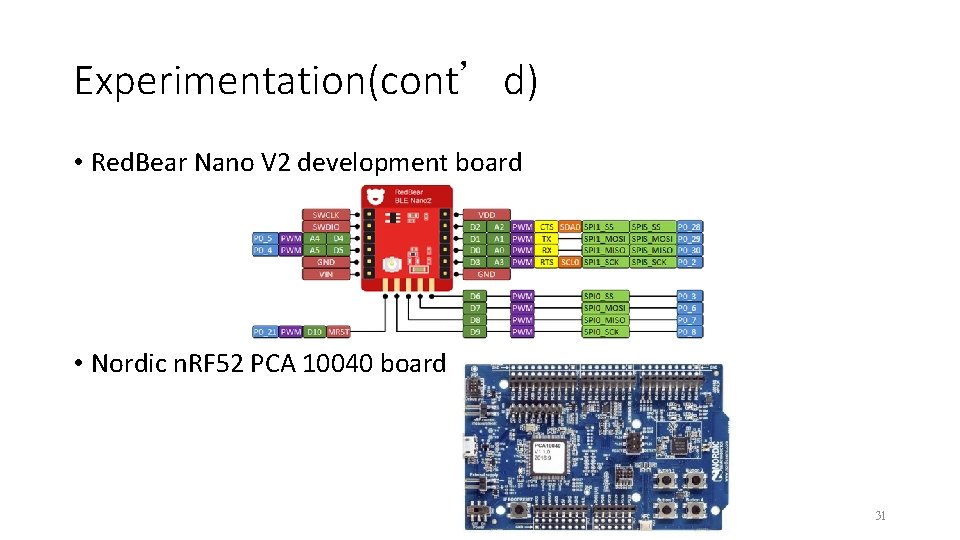
Experimentation(cont’d) • Red. Bear Nano V 2 development board • Nordic n. RF 52 PCA 10040 board 31
Experimentation(cont’d) • The tests were performed in the following order and topologies: • Tandem Trickle • Tandem Drypp • Parallel Trickle • Parallel Drypp 32
Experimentation(cont’d) • Compilation of the Fruitymesh code and its merger with a compatible softdevice • Insertion of the program to be tested in the central devices through DAPLink • Assembly of battery monitoring systems • Positioning of network nodes according to the proposed topology • Charging the capacitors to start the network 33
Experimentation(cont’d) • Initiating the capture of battery data and monitoring of serial interfaces • Starting the capture of BLE packages through Sniffer • Recharging of batteries from central nodes up to 3 V • Waiting for the network to lose connectivity • Finalizing the collection programs and analyzing the data 34
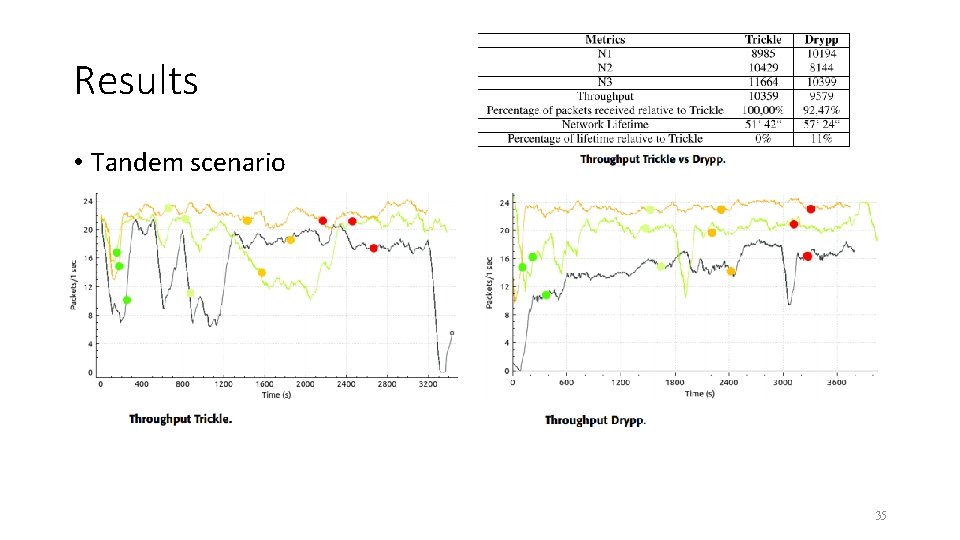
Results • Tandem scenario 35
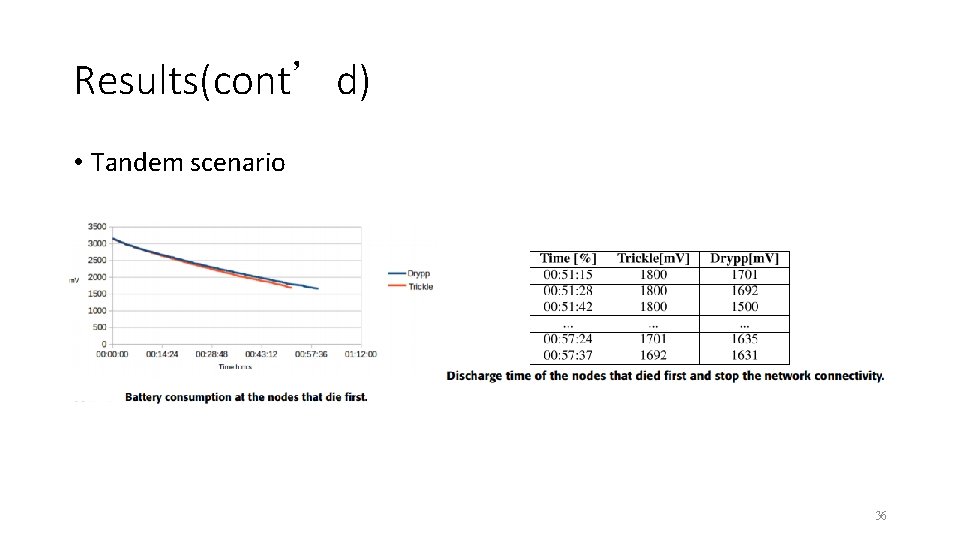
Results(cont’d) • Tandem scenario 36
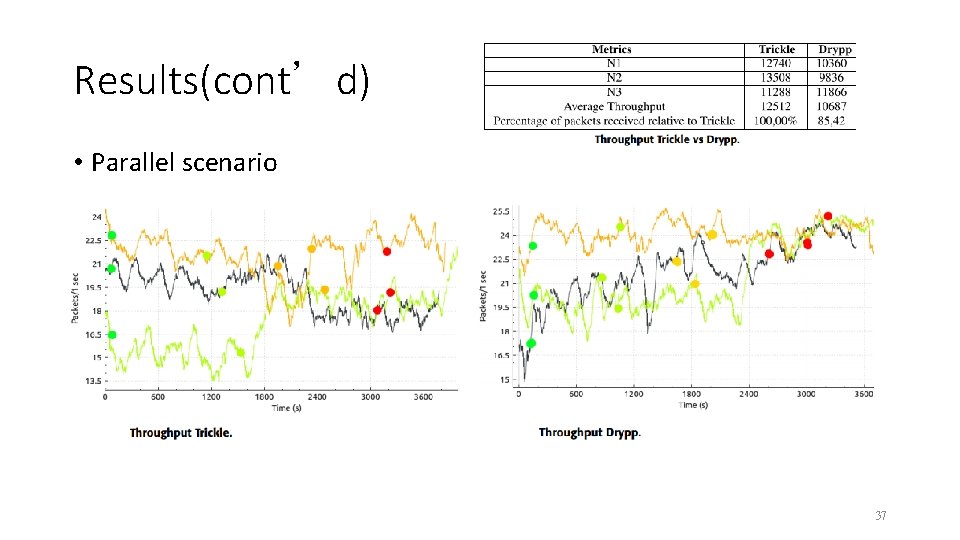
Results(cont’d) • Parallel scenario 37
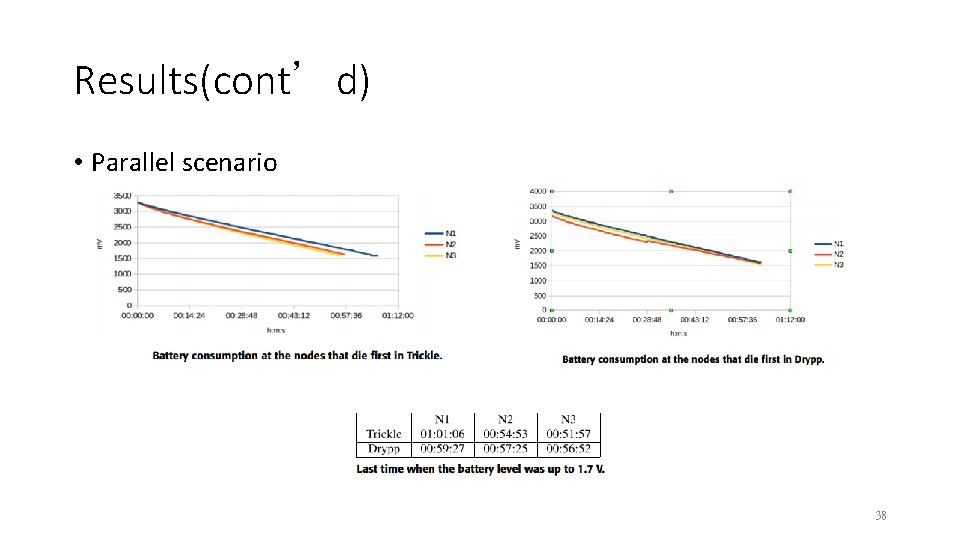
Results(cont’d) • Parallel scenario 38
Conclusion • With Drypp a BLE mesh network protocol solution was proposed. This protocol would saves the battery of the nodes present in the network, balancing their loads of flooding changing messages and forming an intelligent topology using Fruity. Mesh. • It can be seen that in the tandem topology scenario there was an increase in network lifetime. Resulting in an 11% increase in network lifetime, but the average throughput of the network decreased by only 7. 5%. 39

Conclusion(cont’d) • It was observed that the lifetime of the network had very similar values when comparing the two protocols in parallel topology. When the node load balancing occurred in the Drypp scenario, the battery was balanced and the node deaths were very close to each other, differently from the case of the Trickle protocol. • One of the biggest challenges was the lack of available information and documentation in relation to Fruity. Mesh but as it is an open source project there is still a vast path that can be covered regarding its functionality. 40

References • á. Hernández-Solana, D. Pérez-Díaz-De-Cerio, M. García-Lozano, A. V. Bardají and J. Valenzuela, "Bluetooth Mesh Analysis, Issues, and Challenges, " in. IEEE Access, vol. 8, pp. 53784 -53800, 2020, doi: 10. 1109/ACCESS. 2020. 2980795. • A. S. Brandão, M. C. Lima, C. J. B. Abbas and L. J. G. Villalba, "An Energy Balanced Flooding Algorithm for a BLE Mesh Network, " in IEEE Access, vol. 8, pp. 97946 -97958, 2020, doi: 10. 1109/ACCESS. 2020. 2993819. 41

Thanks for listening 42
- Slides: 42