An efficient threshold RSA digital signature scheme SourceApplied







- Slides: 18

An efficient threshold RSA digital signature scheme Source:Applied Mathematics and Computation, Volume 166, Issue 1, 6 July 2005, Pages 25 -34 Author:Qiu-Liang Xu, Tzer-Shyong Chen Speaker:李士勳 Date: 2005, 12, 14 1

Outline o o Introduction Descriptions of the scheme Analysis of security and efficiency Conclusions 2

Introduction o o Resisting conspiracy attack (t, n) threshold signature scheme 3

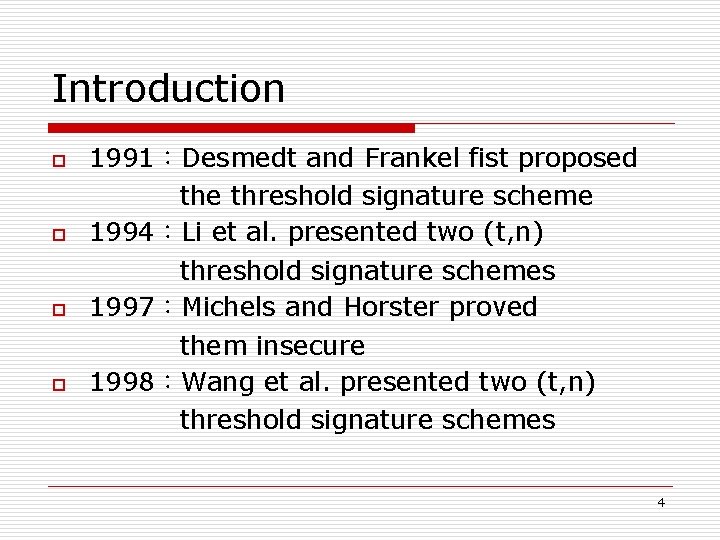
Introduction o o 1991:Desmedt and Frankel fist proposed the threshold signature scheme 1994:Li et al. presented two (t, n) threshold signature schemes 1997:Michels and Horster proved them insecure 1998:Wang et al. presented two (t, n) threshold signature schemes 4

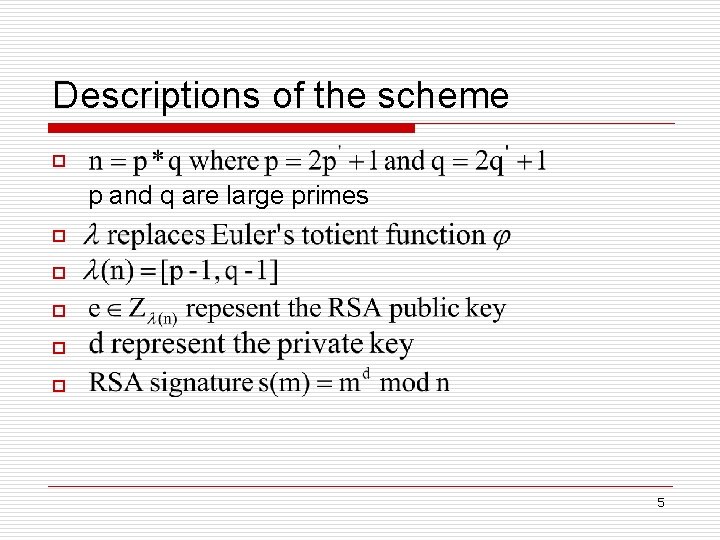
Descriptions of the scheme o p and q are large primes o o o 5

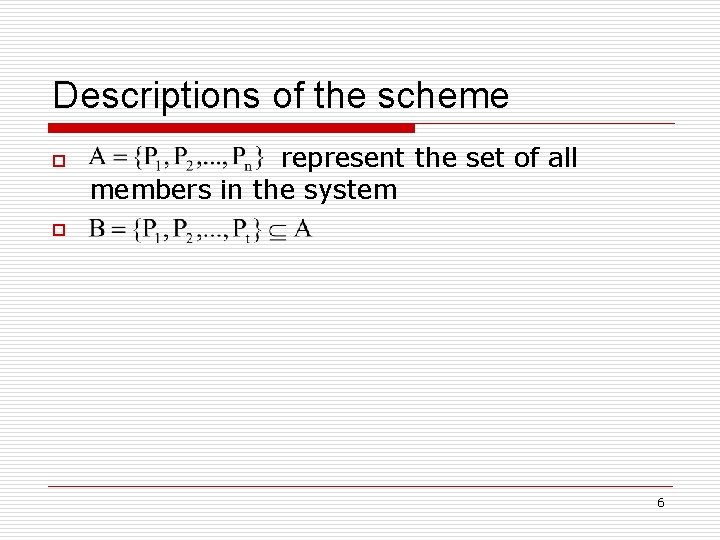
Descriptions of the scheme o represent the set of all members in the system o 6

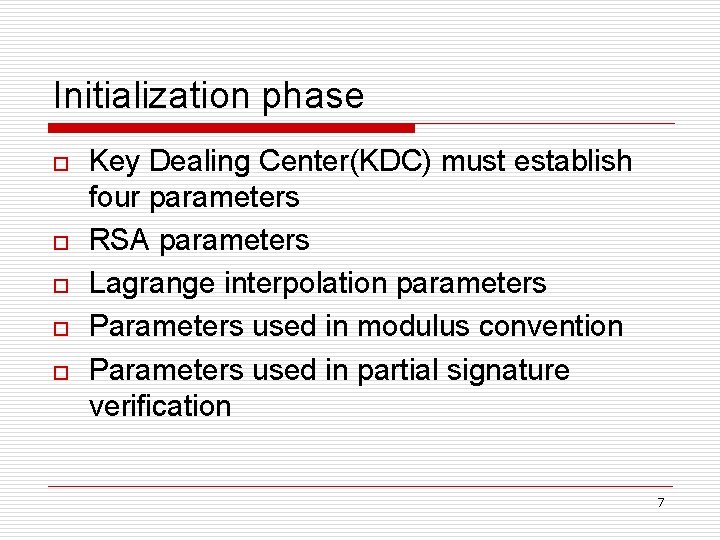
Initialization phase o o o Key Dealing Center(KDC) must establish four parameters RSA parameters Lagrange interpolation parameters Parameters used in modulus convention Parameters used in partial signature verification 7

RSA parameters o o p, q, n, e and d to generatethe group signature, where n=p*q, p and p are two safe primes, (n, e) is the public key, and d is the private key P, Q, N, E and D which is used by the signature generator(SG), where N=P*Q>n, P and Q are also two safe primes, (N, E) is the public key, and D is the private key 8

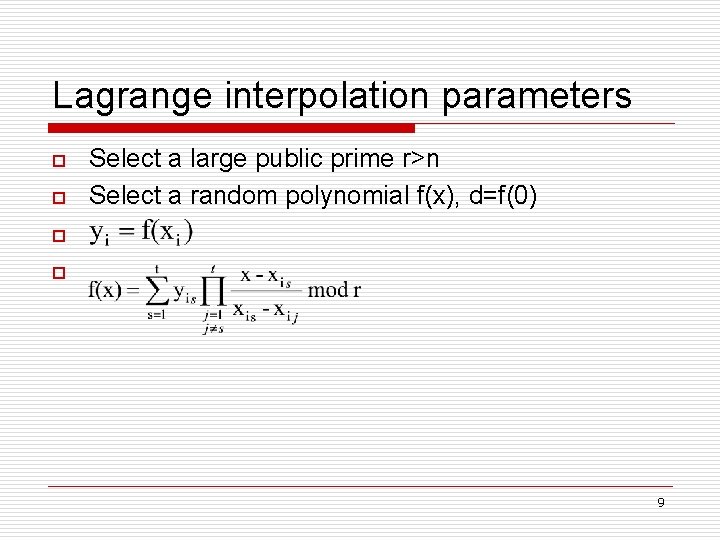
Lagrange interpolation parameters o o Select a large public prime r>n Select a random polynomial f(x), d=f(0) o o 9

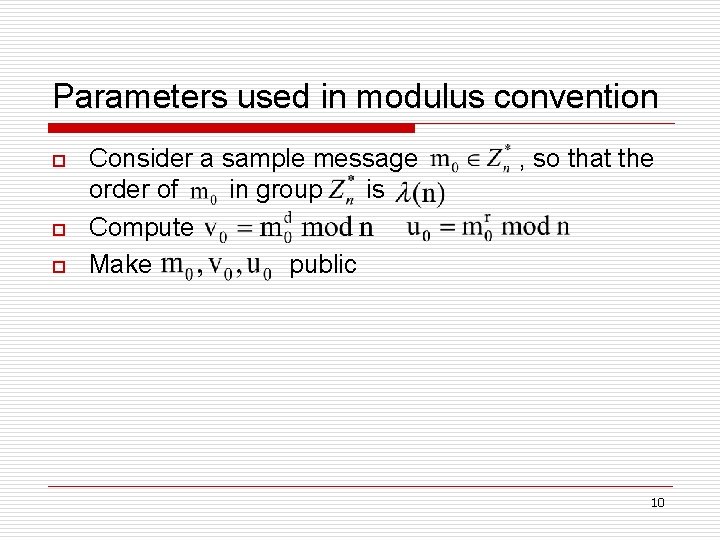
Parameters used in modulus convention o o o Consider a sample message order of in group is Compute Make public , so that the 10

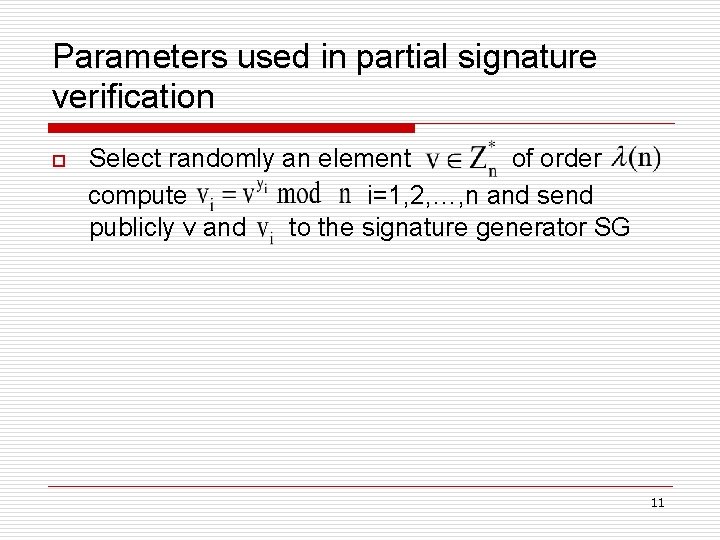
Parameters used in partial signature verification o Select randomly an element of order compute i=1, 2, …, n and send publicly v and to the signature generator SG 11

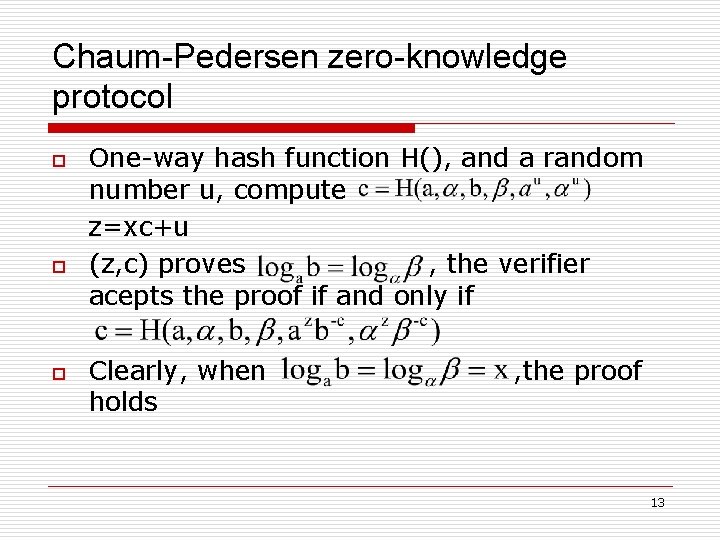
Signature phase o Chaum-Pedersen zero-knowledge protocol o 12

Chaum-Pedersen zero-knowledge protocol o o o One-way hash function H(), and a random number u, compute z=xc+u (z, c) proves , the verifier acepts the proof if and only if Clearly, when holds , the proof 13

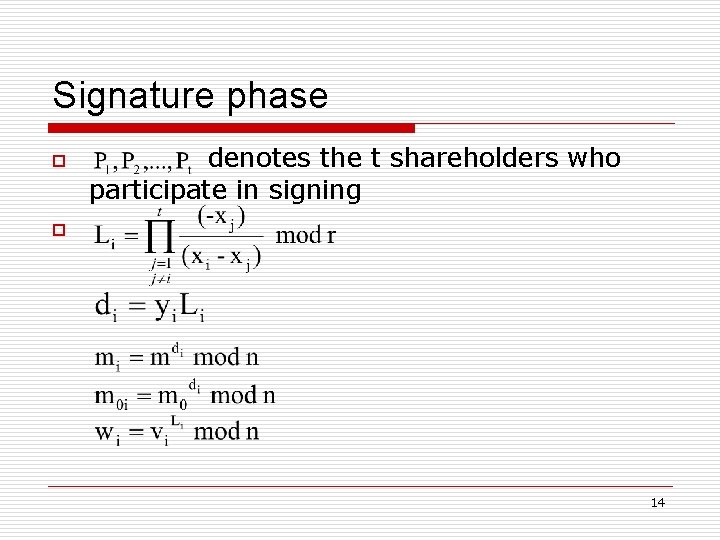
Signature phase o denotes the t shareholders who participate in signing o 14

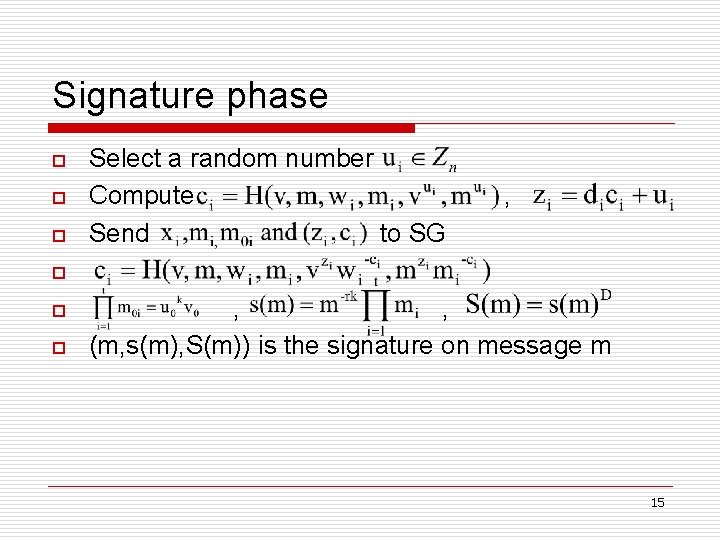
Signature phase o o o Select a random number Compute Send to SG , o o o , , (m, s(m), S(m)) is the signature on message m 15

Signature phase o If then (m, s(m), S(m)) is appetped as a valid signature 16

Analysis of security and efficiency o o o The fist step of the initialization phase builds only the RSA cryptosystem, without providing any extra information The second step is to establish a (t, n) threshold system based on Lagrange interpolation The third and forth step is hard to slove the discrete logarithm problem 17

Conclusions o Resisting conspiracy attack 18