An Efficient RFID Authentication Protocol for Lowcost Tags










- Slides: 20

多媒體網路安全實驗室 An Efficient RFID Authentication Protocol for Low-cost Tags Date: 2012. 08. 31 Reporter : Hong Ji Wei Authors : Yanfei Liu From : 2008 IEEE/IFIP International Conference on Embedded and Ubiquitous Computing

多媒體網路安全實驗室 OUTLINE 1 INTRODUCTION 2 RELATED WORKS 3 PROPOSED PROTOCOL 4 SECURITY AND PRIVACY ANALYSIS 35 EFFICIENCY ANALYSIS 64 CONCLUSION 1

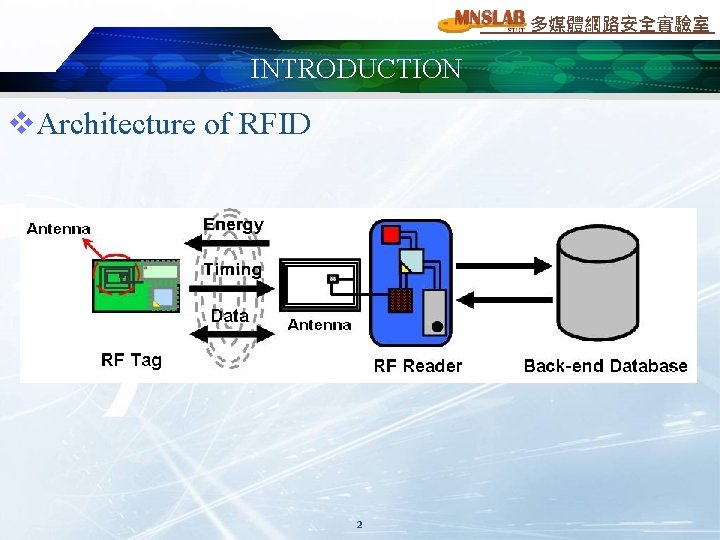
多媒體網路安全實驗室 INTRODUCTION v. Architecture of RFID 2

多媒體網路安全實驗室 INTRODUCTION v. RF Tag of RFID can be divided into two categories 1. Active RF Tag • Need to install the battery. • Sense distance is long than passive. 2. Passive RF Tag • Doesn’t need to install the battery. • Sense distance is short than active. 3

多媒體網路安全實驗室 RELATED WORKS v. RFID authentication protocols can be divided into four classes. 1. First - Weis et al. 2. Second – S. A. Weis 3. Third - Tree based protocol 4. Fourth - C. C. Tan

多媒體網路安全實驗室 PROPOSED PROTOCOL v. Notations S : The authentication server Ri : An RFID reader Tj : An RFID tag h(. ) : A one-way function fk(. ) : A one-way function with a secret key k ⊕ : Bitwise XOR operation 5

多媒體網路安全實驗室 PROPOSED PROTOCOL v. This proposed protocol can be divided into three phrases. 1. Assumptions 2. Initialization 3. Authentication 6

多媒體網路安全實驗室 PROPOSED PROTOCOL v. Assumptions 1. Each tag has enough memory to store a one-way hash function. 2. The hash functions are assumed to be known for the adversary, while the parameters used are secret. 3. Each tag has a rewriteable memory to store the security information. 4. Each tag can generate random numbers and perform hash function operations. 5. The channel between the reader and the authentication server is secure but another is not.

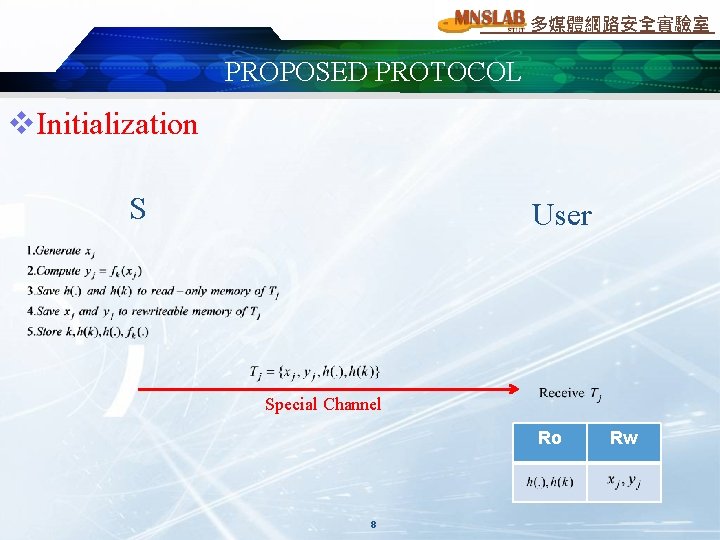
多媒體網路安全實驗室 PROPOSED PROTOCOL v. Initialization S User Special Channel Ro 8 Rw

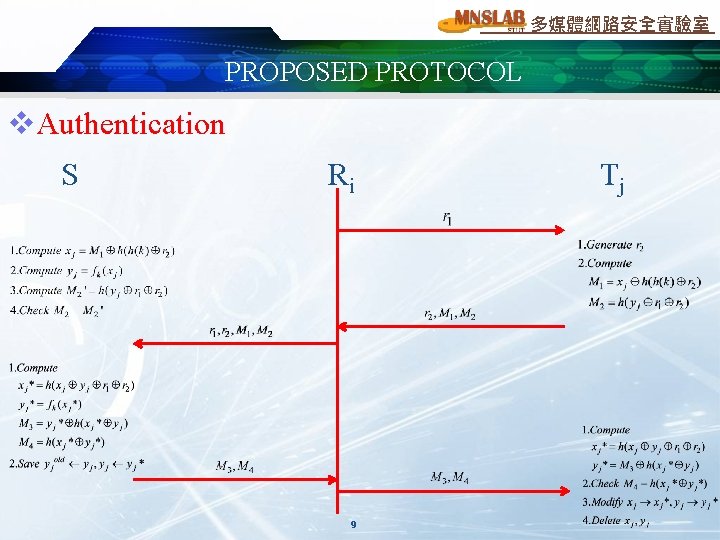
多媒體網路安全實驗室 PROPOSED PROTOCOL v. Authentication S Ri 9 Tj

多媒體網路安全實驗室 SECURITY AND PRIVACY ANALYSIS v. The analysis can be divided into sixth parts 1. Eavesdropping 2. Tag cloning 3. Tag tracking 4. Replay attack 5. Compromising attack 6. Denial of service attack 10

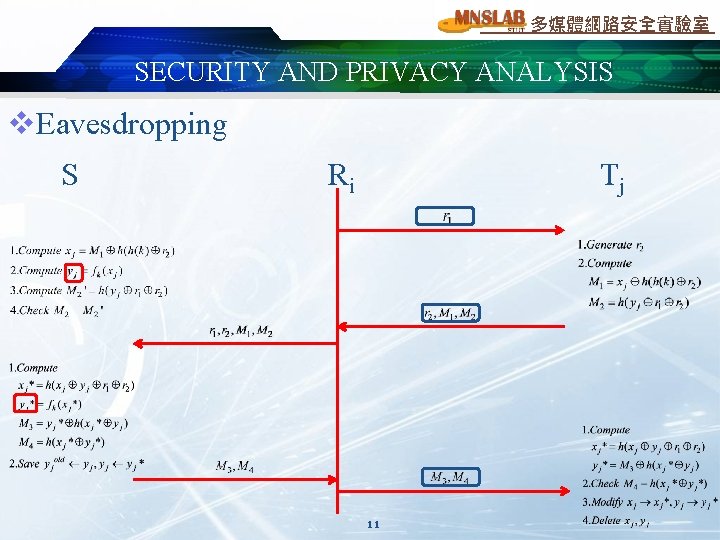
多媒體網路安全實驗室 SECURITY AND PRIVACY ANALYSIS v. Eavesdropping S Ri Tj 11

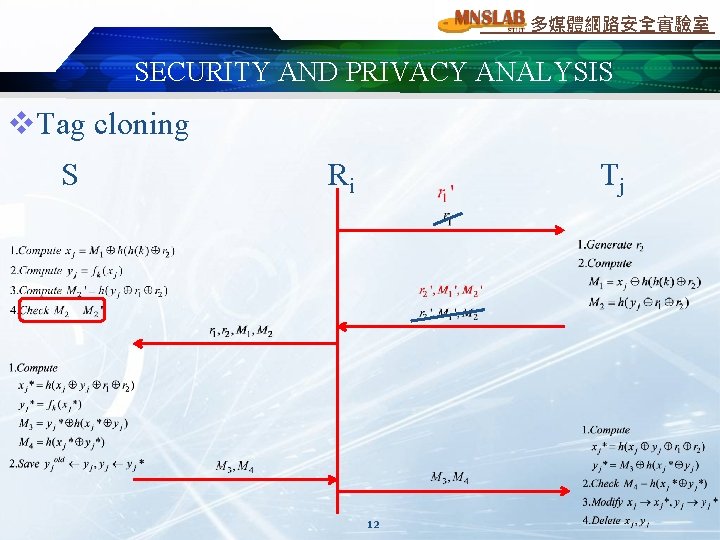
多媒體網路安全實驗室 SECURITY AND PRIVACY ANALYSIS v. Tag cloning S Ri Tj 12

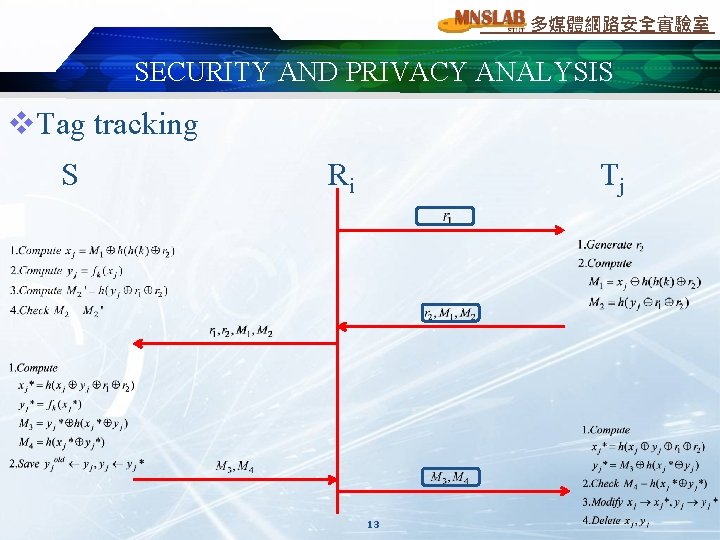
多媒體網路安全實驗室 SECURITY AND PRIVACY ANALYSIS v. Tag tracking S Ri Tj 13

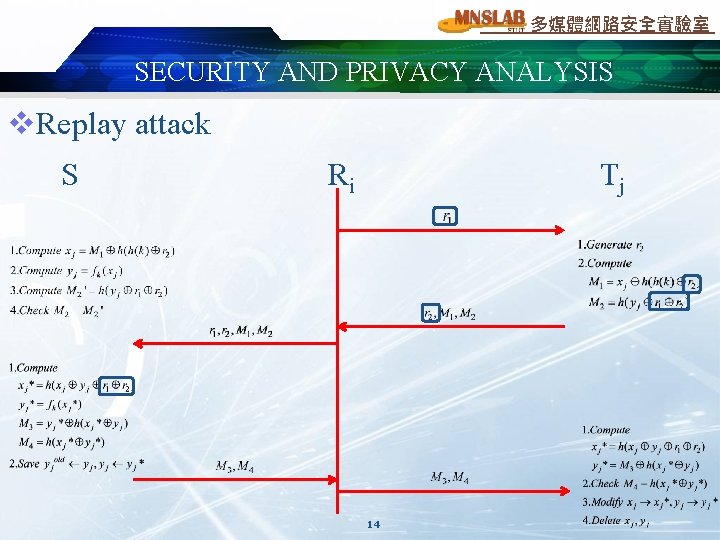
多媒體網路安全實驗室 SECURITY AND PRIVACY ANALYSIS v. Replay attack S Ri Tj 14

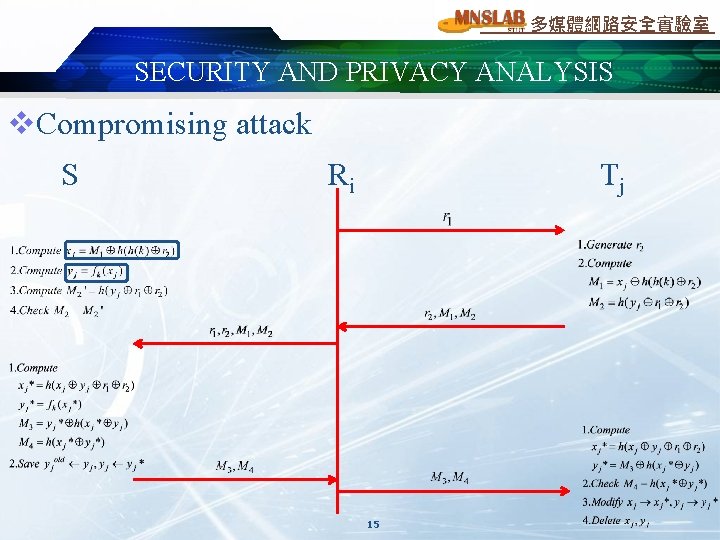
多媒體網路安全實驗室 SECURITY AND PRIVACY ANALYSIS v. Compromising attack S Ri Tj 15

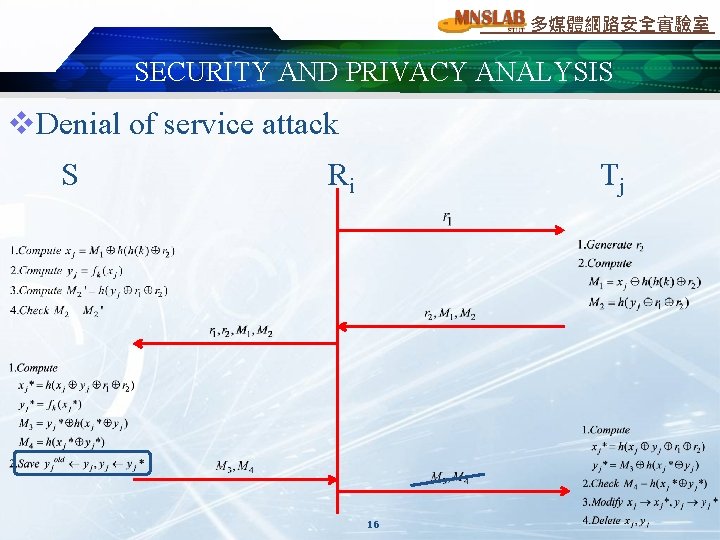
多媒體網路安全實驗室 SECURITY AND PRIVACY ANALYSIS v. Denial of service attack S Ri Tj 16

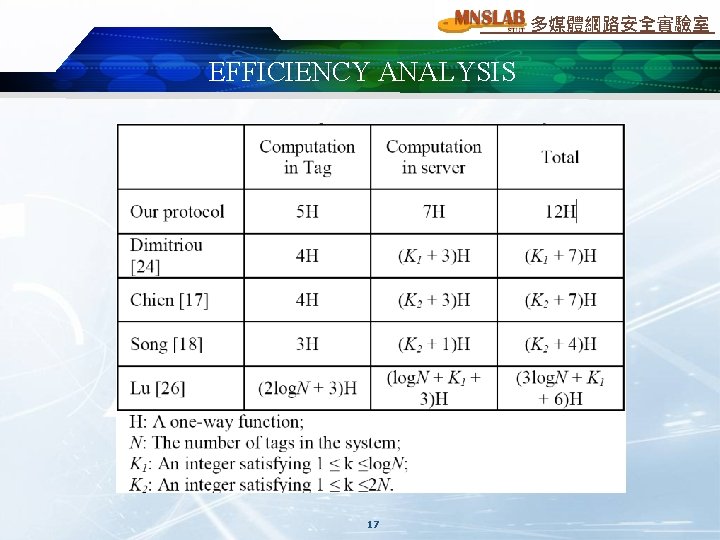
多媒體網路安全實驗室 EFFICIENCY ANALYSIS 17

多媒體網路安全實驗室 CONCLUSION v. In this paper, we proposed a much more efficient authentication protocol utilizing one-way functions only than most of recent protocols. v. The server just compute one-way function three times to check the identifier of the tag and its response without any other searching operation. v. Our protocol provides a mutual authentication between the reader and the tag. 18
