An Efficient Distributed Trust Model for Wireless Sensor

An Efficient Distributed Trust Model for Wireless Sensor Networks J. Jiang, G. Han, F. Weng, L. Shu, M. Guizani Presenter: Kshitij D. Karki

Topics q Related Works q Introduction q Issues in Existing Literatures on Trust Assessment q Assumptions and Network Model q Definitions q Architecture q Direct Trust q Recommendation Trust q Indirect Trust q Update of Trust Value q Simulation and Analysis q Summary q References

Related Works • Reputation Based Framework for Sensor Network (RFSN) • Consists of Watchdog and Reputation System to monitor neighbor nodes and maintain their reputation • Only uses direct trust but NOT recommendation trust • Parameterized and Localized tr. Ust management Scheme (PLUS) • Uses both direct and recommendation trust to calculate final trust • Has drawback of suspect node getting unfair penalty if data integrity fails • Node Behavioral strategies Banding belief theory of the Trust Evaluation algorithm (NBBTE) • Based on behavioral strategy banding D-S (Dempster – Shafer) belief theory • Allows combination of evidence from different sources and arrive at a degree of belief • Establishes various trust factors, calculates direct trust values, and incorporates neighbor recommendation to determine integrated trust value instead of weighted trust value

Introduction • Wireless Sensor Networks is a wireless network consisting of spatially distributed autonomous devices using sensors to monitor physical and environmental conditions [1] • Useful in emergency responses, healthcare monitoring, battlefield surveillance, habitat monitoring, traffic management, smart power • Critical vulnerabilities such as node capture and Do. S attacks • Security mechanism such as cryptography, authentication, confidentiality, and message integrity

Issues in Existing Literatures on Trust Assessment • Based on communication point of view • May not be entirely accurate • Does not consider other parameters such as energy level • Should deal with uncertainty by noisy communication and unstable nodes • 2 ways to establish trust in WSN • Direct trust and indirect trust • Discriminate analysis of other nodes and their recommendation is essential • Provide trust assessment of neighbor nodes only • Some algorithms require trust values of non-neighbor nodes • Do not solve the trust dynamic problem
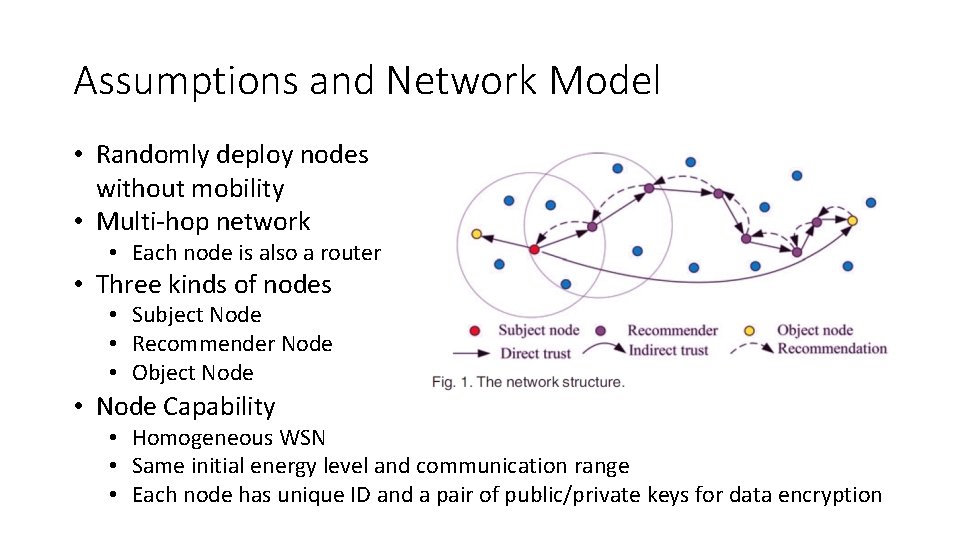
Assumptions and Network Model • Randomly deploy nodes without mobility • Multi-hop network • Each node is also a router • Three kinds of nodes • Subject Node • Recommender Node • Object Node • Node Capability • Homogeneous WSN • Same initial energy level and communication range • Each node has unique ID and a pair of public/private keys for data encryption

Attack Model • Some of the malicious attacks in WSNs • Do. S attack, node replication, Sybil attack, wormhole attack, attack on Info • Trust Model is vulnerable to malicious attacks • Bad/good-mouthing attack, on-off attack

Trust Definition and Types of Trust • Trust is defined as a belief level that one sensor node puts on another node for a specific action according to previous observation of behaviors • Reflects if a node is willing and able to act normally in WSN • Trust value ranges from 0 to 1 where 1 is completely trustworthy • Direct Trust: based on direct communication behaviors • Recommendation Trust: Filtered recommendations for 1 -hop nodes • Indirect Trust: trust for multi-hop nodes based on recommendations

Properties of Trust • Asymmetry • If node A trusts node B, it does not imply node B trusts node A • Transitivity • Trust value can be passed along a path of trusted nodes • If node A trust node B and node B trust node C, then A trusts C at certain level • Important in trust calculation between two non-neighbor nodes • Composability • Trust values received from multiple available paths can be composed to obtain an integrated value
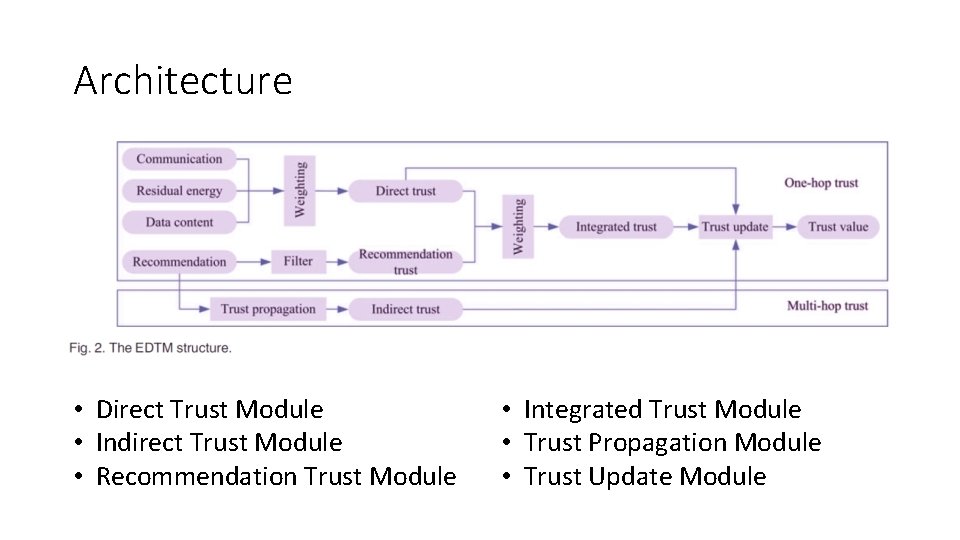
Architecture • Direct Trust Module • Indirect Trust Module • Recommendation Trust Module • Integrated Trust Module • Trust Propagation Module • Trust Update Module

Direct Trust • Composed of communication trust, energy trust, and data trust • Communication Trust: indicates if a node can cooperatively execute the intended protocol • Energy Trust: indicated if a node is competent in performing its intended function • Data Trust: assessment of fault tolerance and data integrity
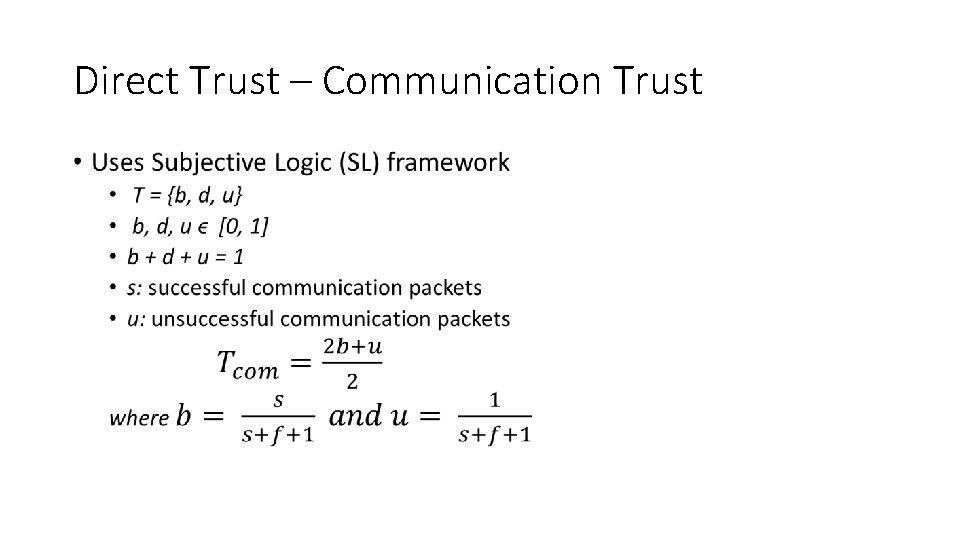
Direct Trust – Communication Trust •
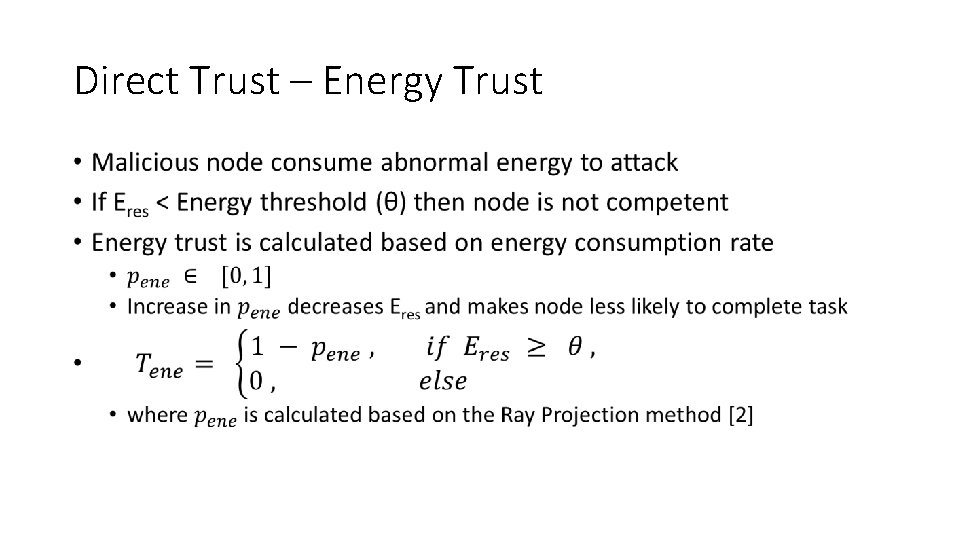
Direct Trust – Energy Trust •
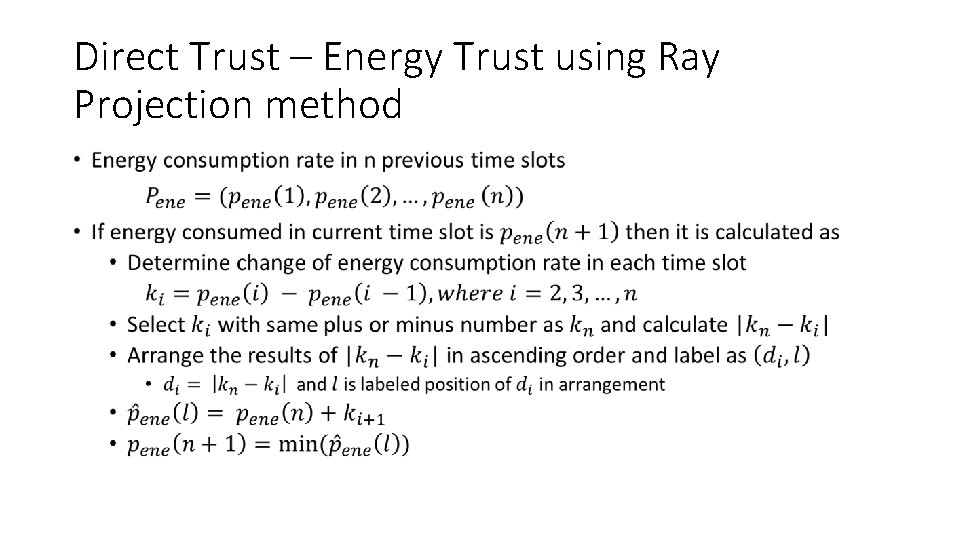
Direct Trust – Energy Trust using Ray Projection method •
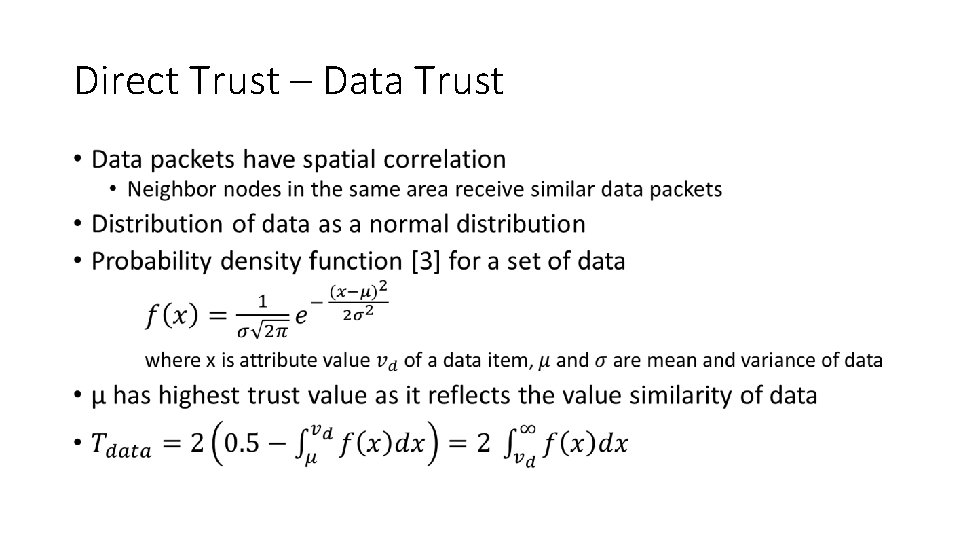
Direct Trust – Data Trust •
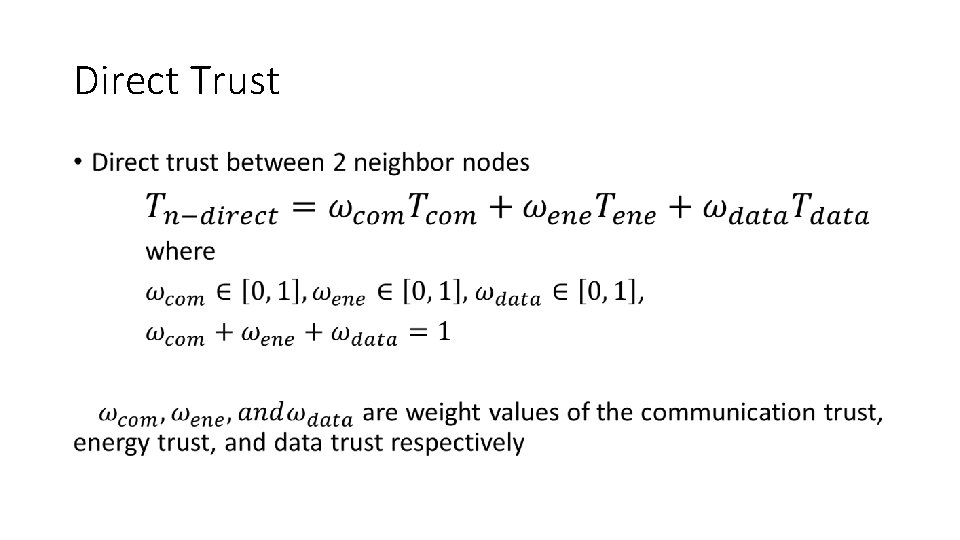
Direct Trust •
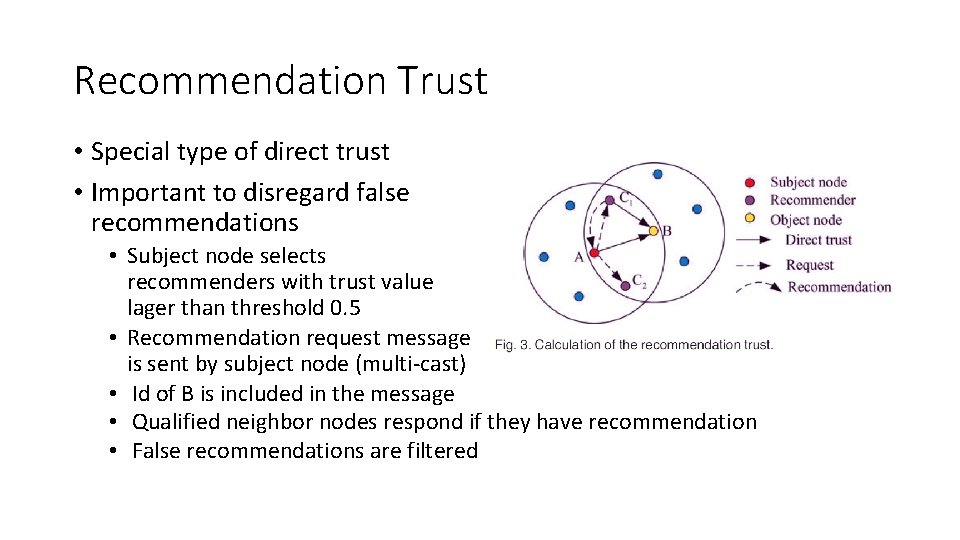
Recommendation Trust • Special type of direct trust • Important to disregard false recommendations • Subject node selects recommenders with trust value lager than threshold 0. 5 • Recommendation request message is sent by subject node (multi-cast) • Id of B is included in the message • Qualified neighbor nodes respond if they have recommendation • False recommendations are filtered
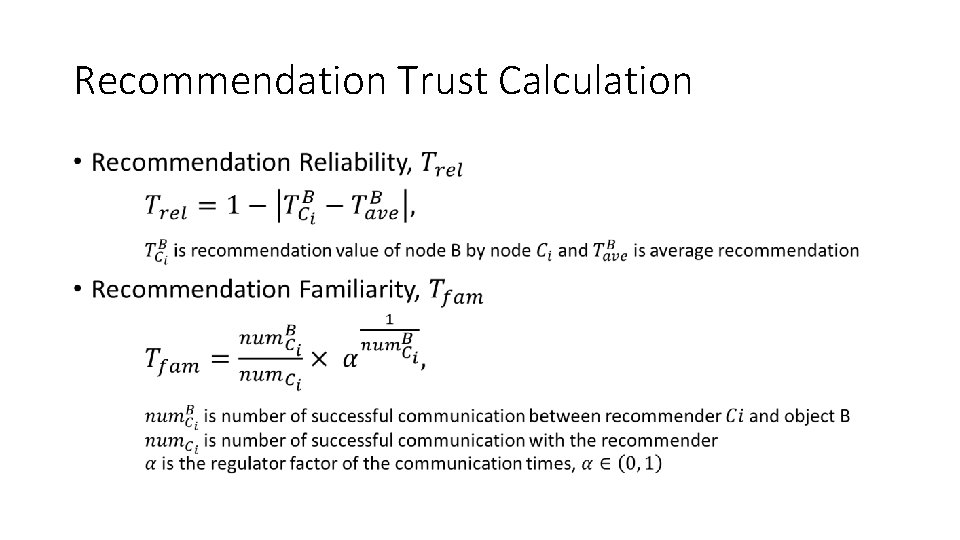
Recommendation Trust Calculation •
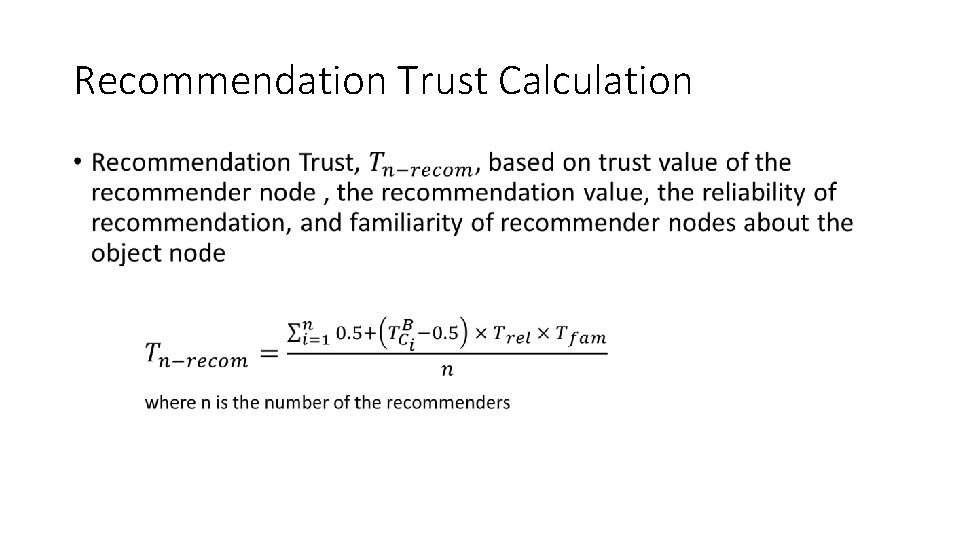
Recommendation Trust Calculation •
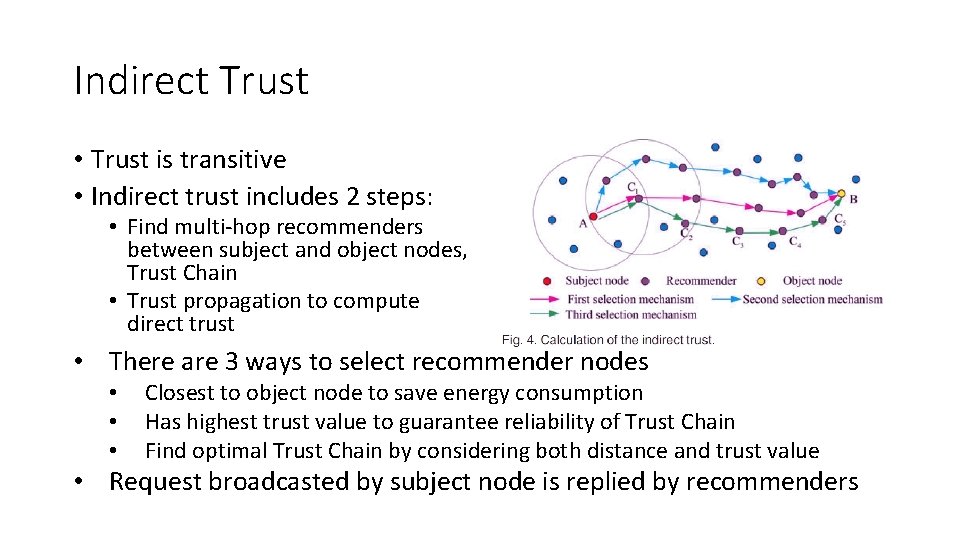
Indirect Trust • Trust is transitive • Indirect trust includes 2 steps: • Find multi-hop recommenders between subject and object nodes, Trust Chain • Trust propagation to compute direct trust • There are 3 ways to select recommender nodes • • • Closest to object node to save energy consumption Has highest trust value to guarantee reliability of Trust Chain Find optimal Trust Chain by considering both distance and trust value • Request broadcasted by subject node is replied by recommenders
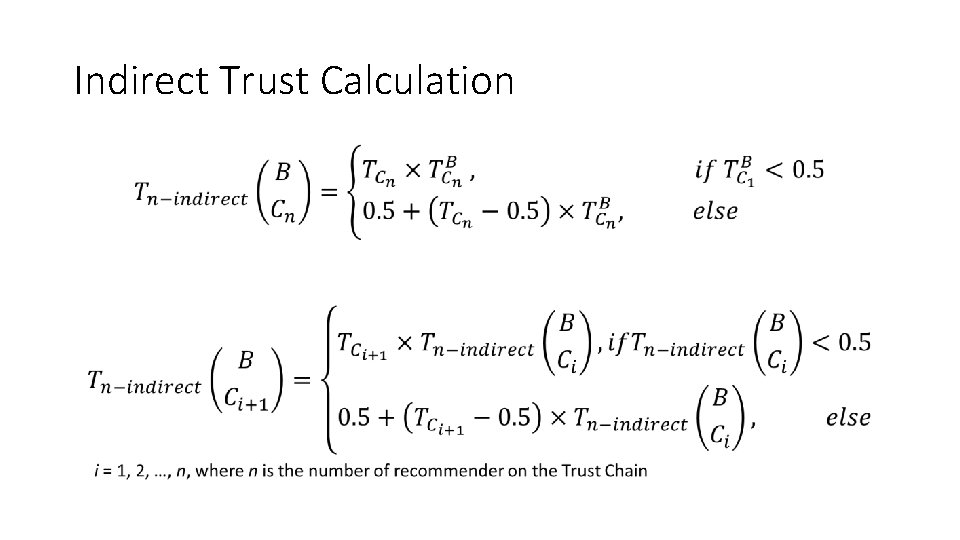
Indirect Trust Calculation •
Update of Trust Value •
Simulation and Analysis • Deployment area is set to 100 m x 100 m • 100 sensor nodes randomly deployed • Malicious nodes can perform selective forwarding attack, data forgery attack, Do. S attack, on/off attack, bad and good mouthing attack • For comparison purpose, object trust is derived • Based on actual information of each node without considering any network dynamics like mobility, trust decay, and malicious attacks • Rate of malicious node is set as 30%
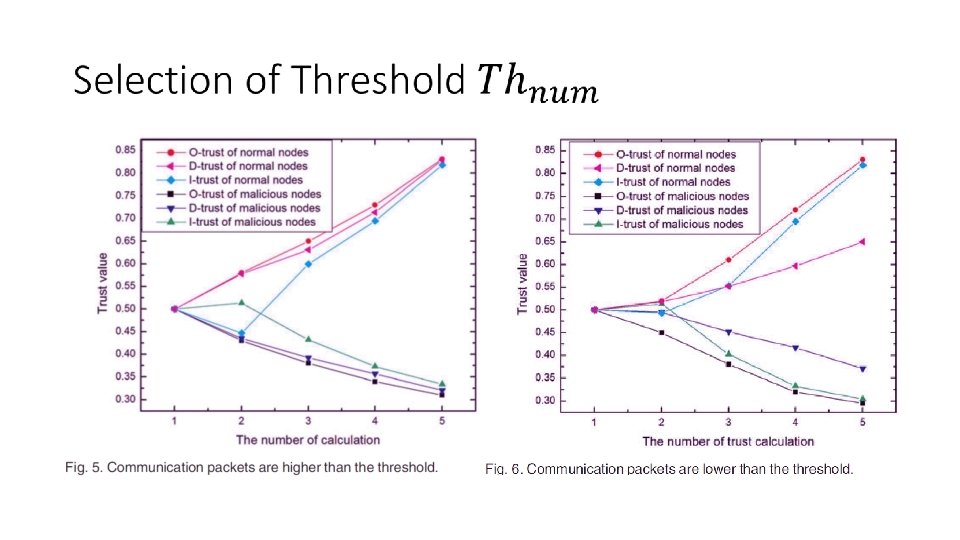
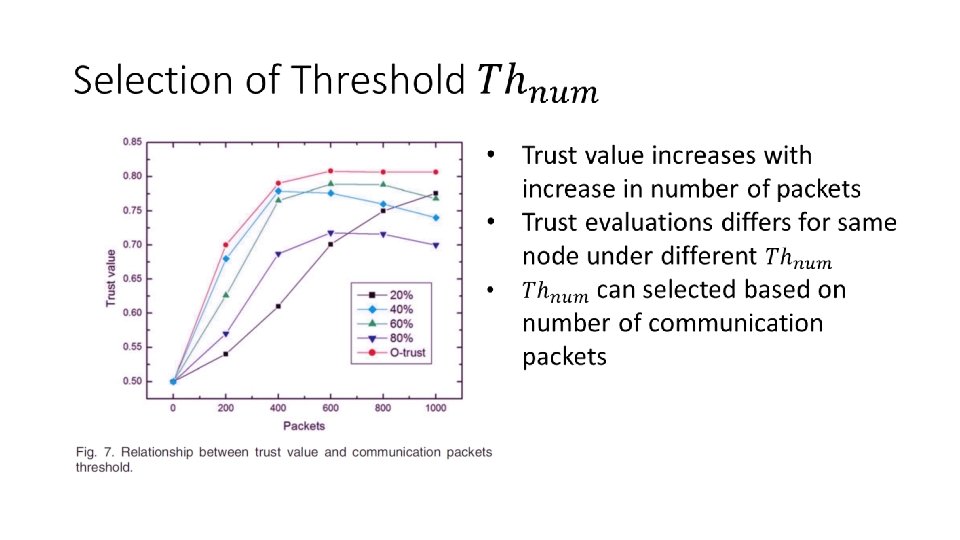
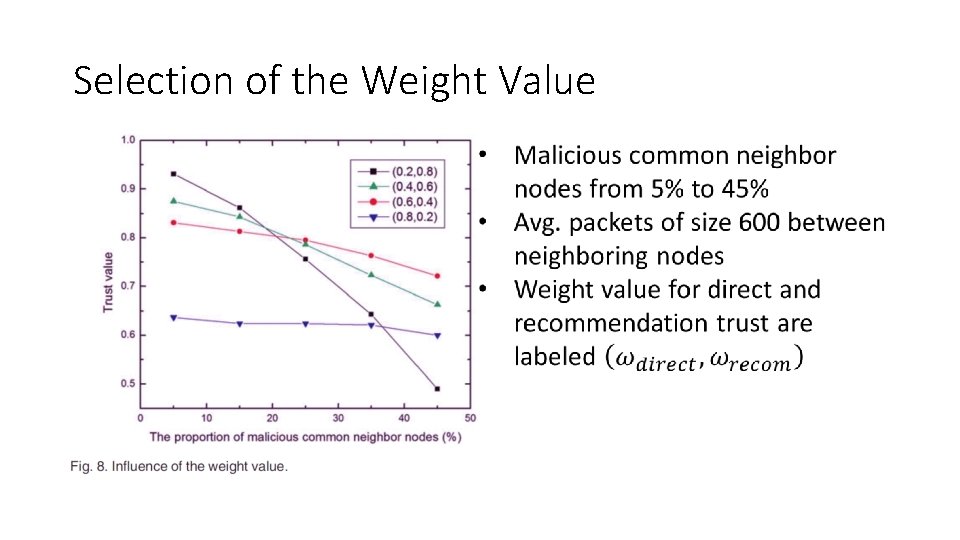
Selection of the Weight Value
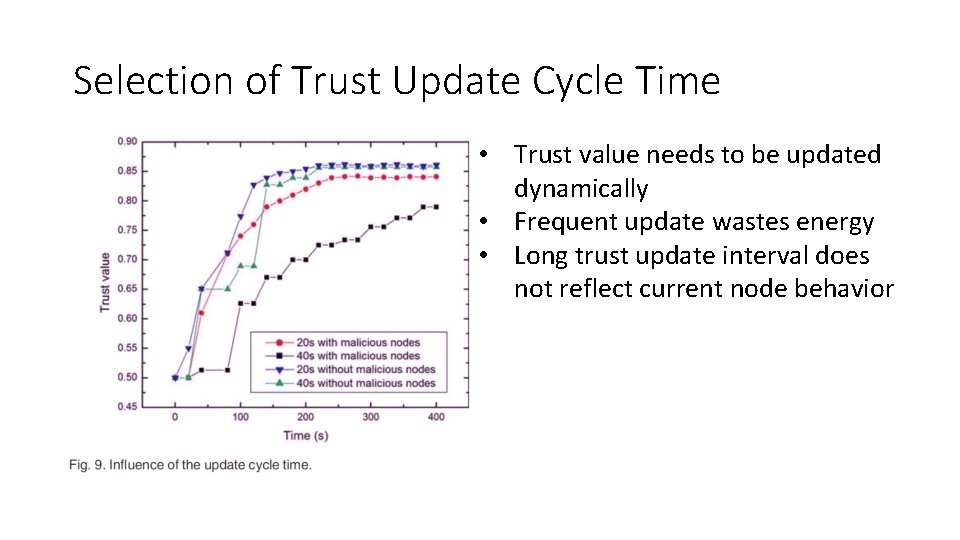
Selection of Trust Update Cycle Time • Trust value needs to be updated dynamically • Frequent update wastes energy • Long trust update interval does not reflect current node behavior
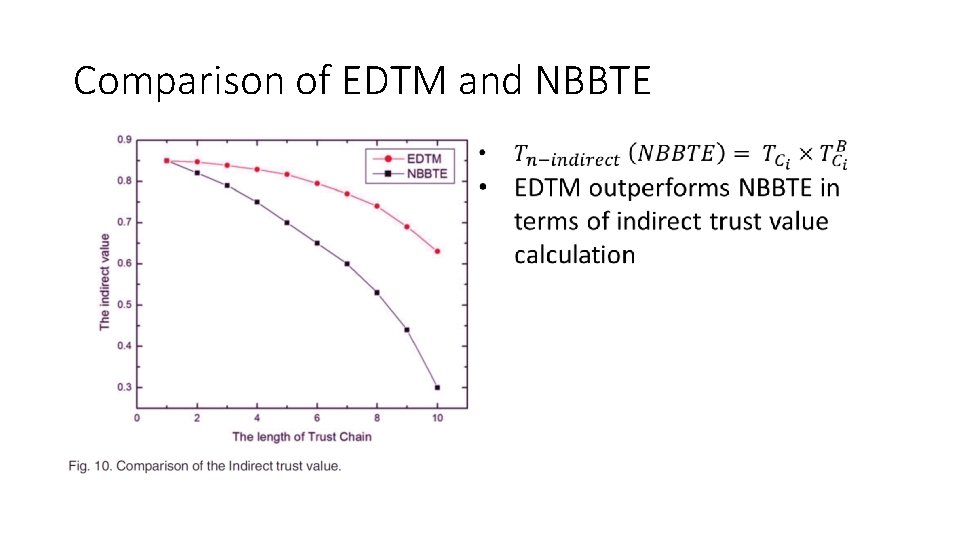
Comparison of EDTM and NBBTE
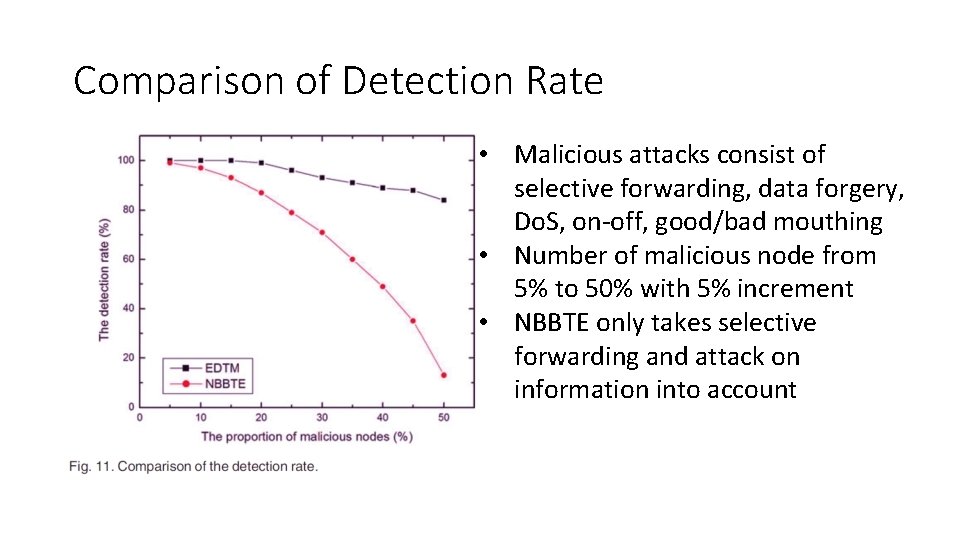
Comparison of Detection Rate • Malicious attacks consist of selective forwarding, data forgery, Do. S, on-off, good/bad mouthing • Number of malicious node from 5% to 50% with 5% increment • NBBTE only takes selective forwarding and attack on information into account
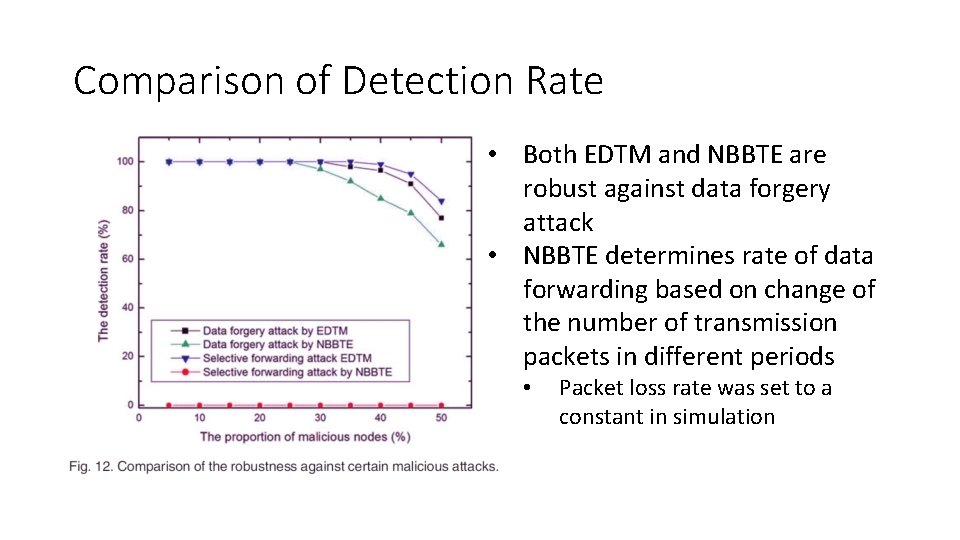
Comparison of Detection Rate • Both EDTM and NBBTE are robust against data forgery attack • NBBTE determines rate of data forwarding based on change of the number of transmission packets in different periods • Packet loss rate was set to a constant in simulation
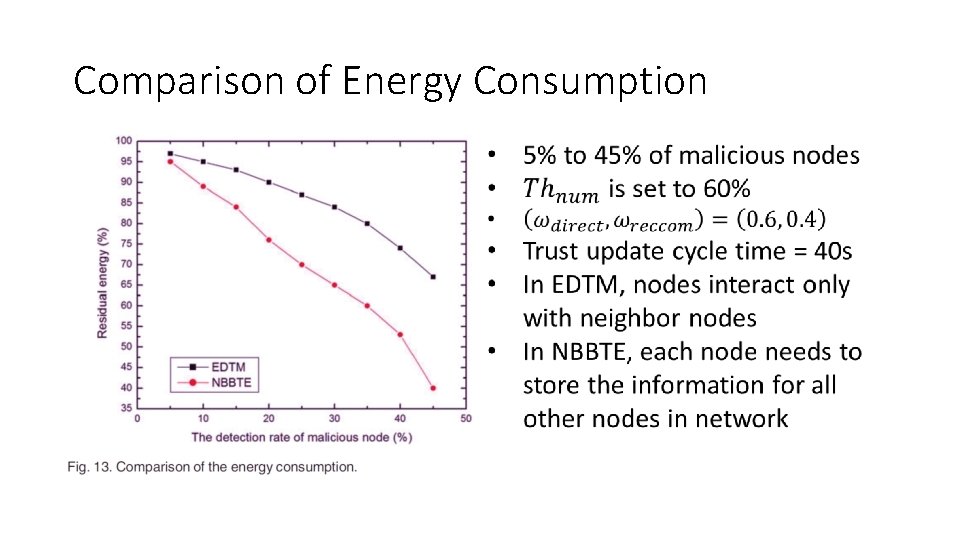
Comparison of Energy Consumption

Summary • Identify some of the issues in existing literatures • Differentiate direct, recommendation, and indirect trust • Defined trust properties: Asymmetry, Transitivity, Composability • Direct trust is composed of communication, energy, and data trust • Recommendation trust takes Recommendation Reliability and Recommendation Familiarity into account • Indirect trust depends on how Trust Chain is constructed • Trust Update has sliding window and aging factor • Outperformed NBBTE algorithm
![References • [1] http: //www. ni. com/white-paper/7142/en/ • [2] H. S. Lim, Y. S. References • [1] http: //www. ni. com/white-paper/7142/en/ • [2] H. S. Lim, Y. S.](http://slidetodoc.com/presentation_image_h2/11b8c0f4226b80f4c7b52b3c61fcda38/image-33.jpg)
References • [1] http: //www. ni. com/white-paper/7142/en/ • [2] H. S. Lim, Y. S. Moon, and E. Bertino, “Provenance based trustworthiness assessment in sensor networks, ” in Proc. 7 th Int. Workshop Data Manage. Sens. Netw. , 2010, pp. 2– 7. • [3] https: //en. wikipedia. org/wiki/Probability_density_function
- Slides: 33