An Analysis Framework for Security in Web Applications

An Analysis Framework for Security in Web Applications Gary Wassermann and Zhendong Su University of California, Davis
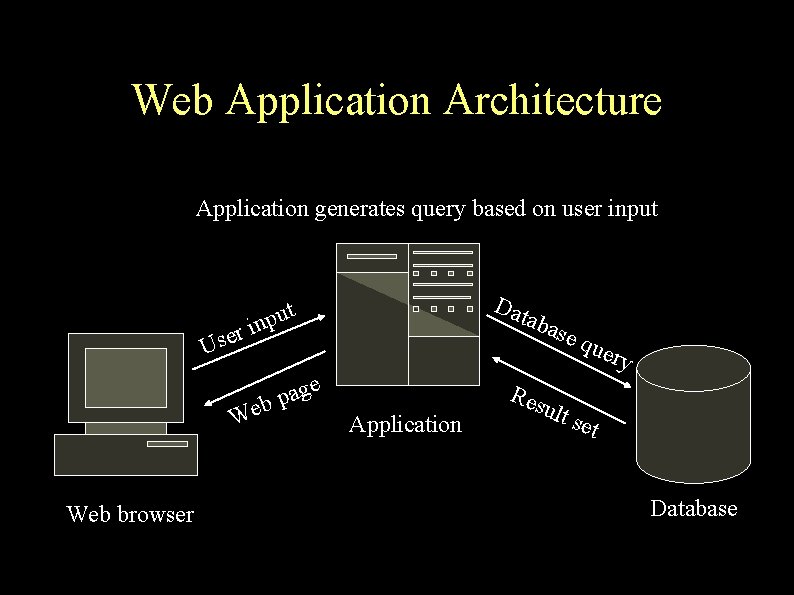
Web Application Architecture Application generates query based on user input r Use ge a p eb W Web browser Dat t u p in aba Application Res se q u ult ery set Database

Command Injection Attacks String query = “SELECT * FROM users WHERE username = ‘” + str. UName + “’ AND password = ‘” + str. Passwd + “’; ”; Expected input: SELECT * FROM users WHERE username = ‘John’ AND password = ‘Johns. Pass’; Result: John logs in
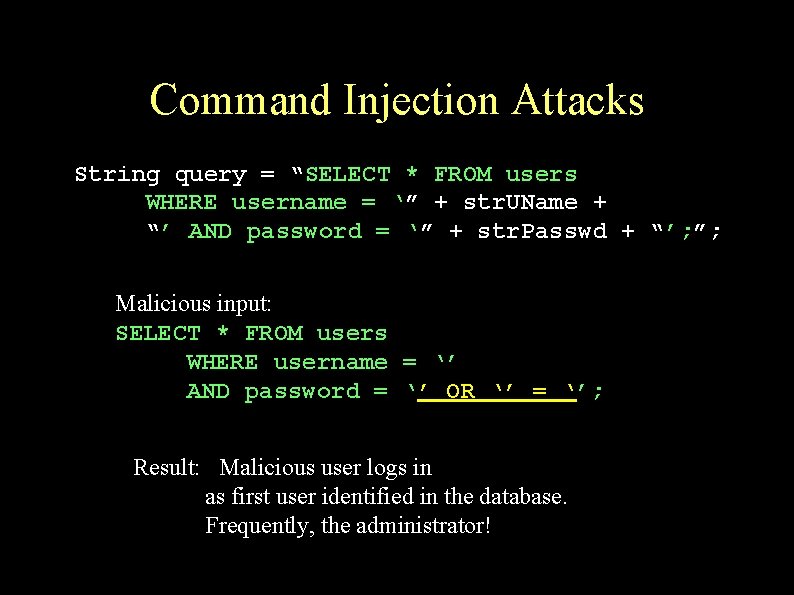
Command Injection Attacks String query = “SELECT * FROM users WHERE username = ‘” + str. UName + “’ AND password = ‘” + str. Passwd + “’; ”; Malicious input: SELECT * FROM users WHERE username = ‘’ AND password = ‘’ OR ‘’ = ‘’; Result: Malicious user logs in as first user identified in the database. Frequently, the administrator!

Motivation ~60% of web applications are vulnerable Found vulnerable sites easily in web search Many ways to regulate user inputs Limit length of input Filter out “bad” strings Escape quotes, etc. Are the regulations sufficient? Goal: Check whether any “dangerous” queries, not user inputs, exist
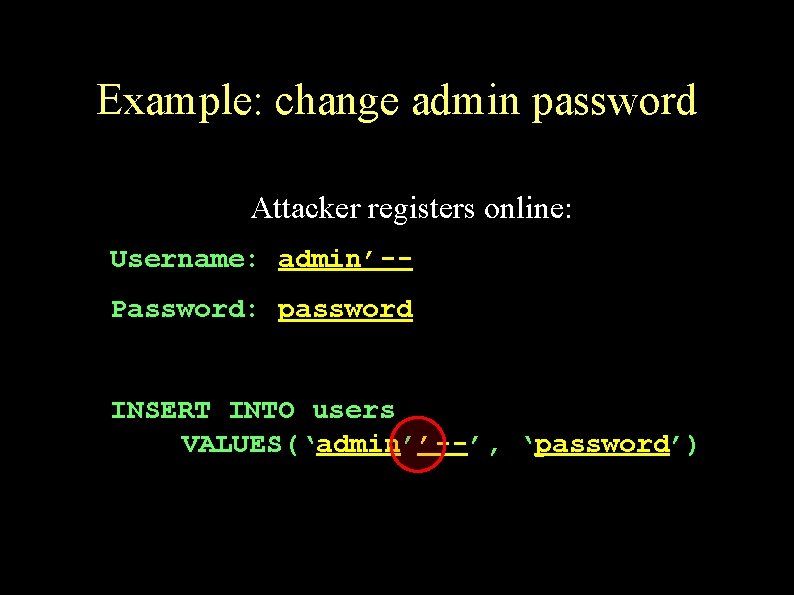
Example: change admin password Attacker registers online: Username: admin’-Password: password INSERT INTO users VALUES(‘admin’’--’, ‘password’)
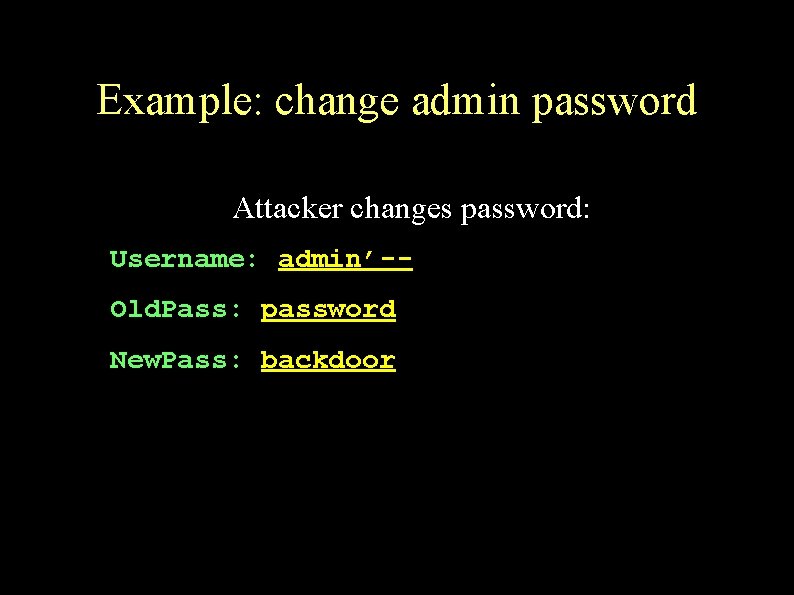
Example: change admin password Attacker changes password: Username: admin’-Old. Pass: password New. Pass: backdoor
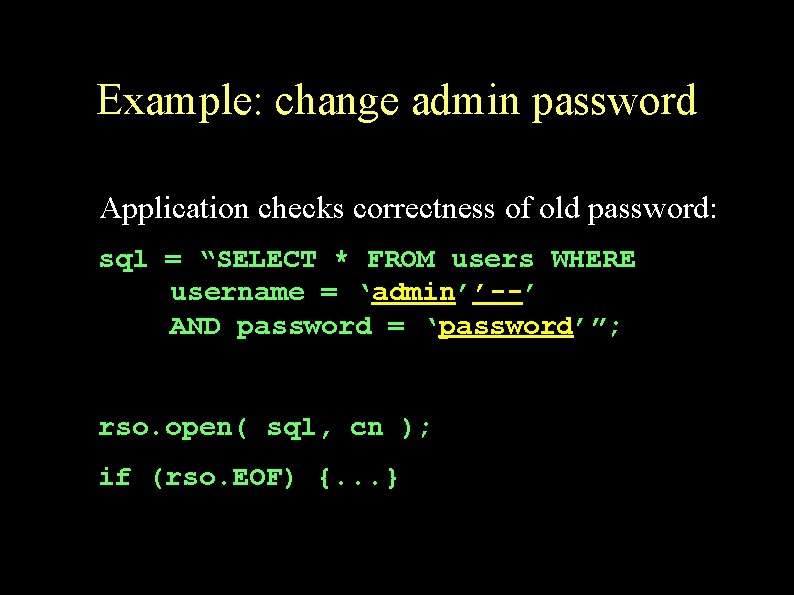
Example: change admin password Application checks correctness of old password: sql = “SELECT * FROM users WHERE username = ‘admin’’--’ AND password = ‘password’”; rso. open( sql, cn ); if (rso. EOF) {. . . }

Example: change admin password Admin’s password gets changed: sql = “UPDATE users SET password = ‘” + newpass + “’ WHERE username = ‘” + rso(“username”) + “’”; UPDATE users SET password = ‘backdoor’ WHERE username = ‘admin’--’
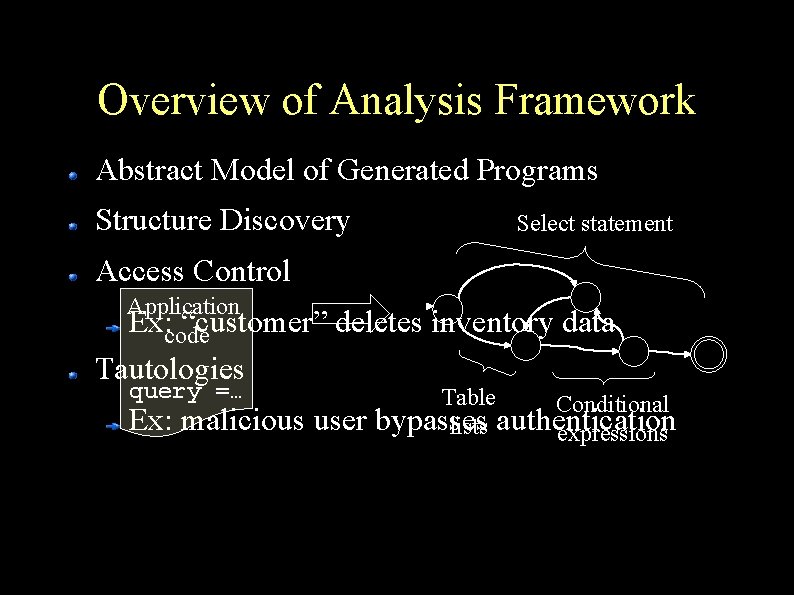
Overview of Analysis Framework Abstract Model of Generated Programs Structure Discovery Select statement Access Control Application Ex: code “customer” deletes inventory data Tautologies query =… Ex: malicious user Table Conditional bypasses lists authentication expressions

Example with cycles String query WHERE ” for( int i = query = = “SELECT * FROM stock + str. ID + “ = id”; 0; i < dat. length(); i++) query + “ AND ” + dat[i] + “ = “ + inp[i];
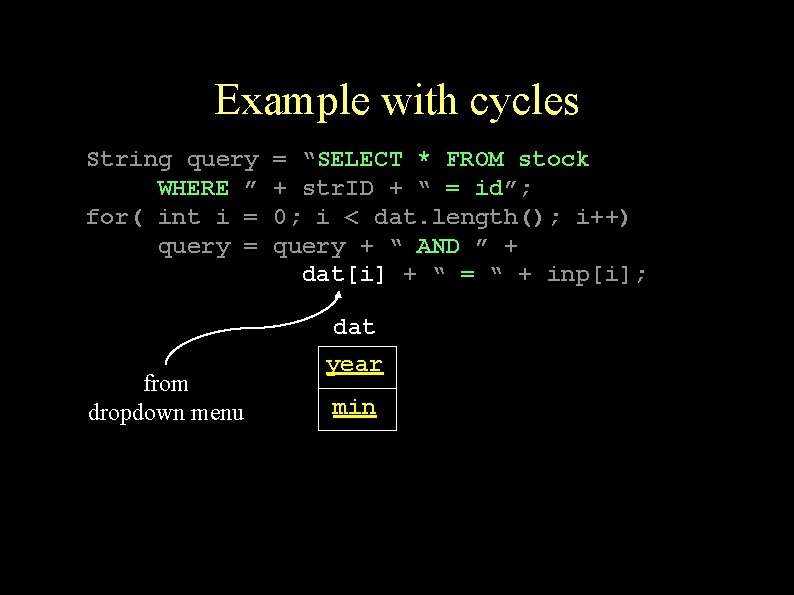
Example with cycles String query WHERE ” for( int i = query = = “SELECT * FROM stock + str. ID + “ = id”; 0; i < dat. length(); i++) query + “ AND ” + dat[i] + “ = “ + inp[i]; dat from dropdown menu year min
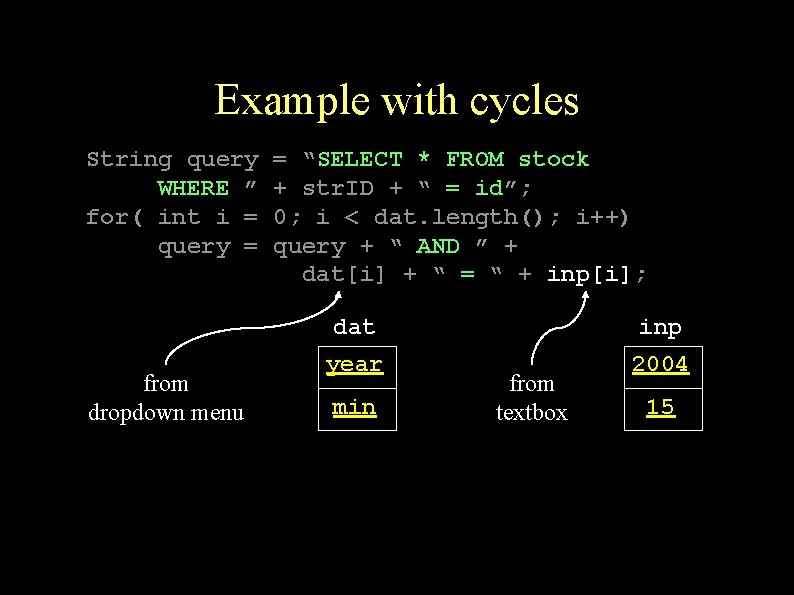
Example with cycles String query WHERE ” for( int i = query = from dropdown menu = “SELECT * FROM stock + str. ID + “ = id”; 0; i < dat. length(); i++) query + “ AND ” + dat[i] + “ = “ + inp[i]; dat inp year 2004 min from textbox 15
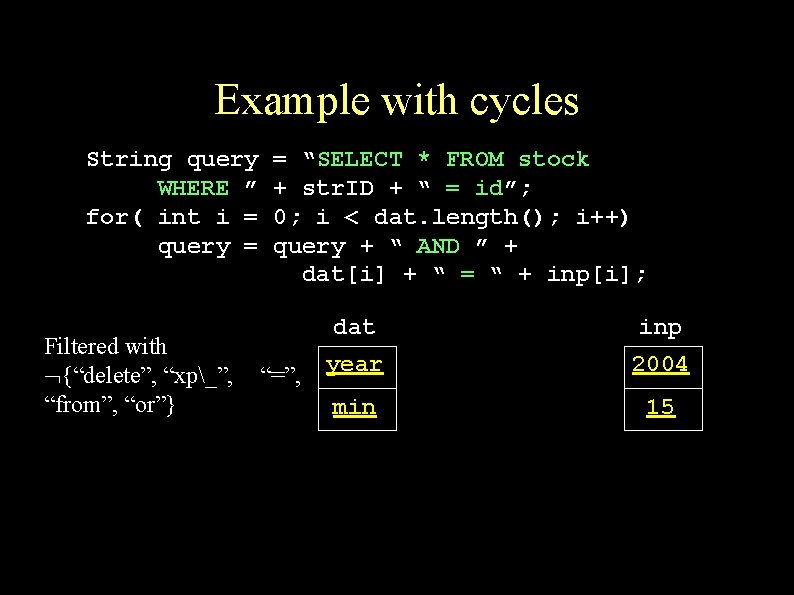
Example with cycles String query WHERE ” for( int i = query = Filtered with {“delete”, “xp_”, “from”, “or”} = “SELECT * FROM stock + str. ID + “ = id”; 0; i < dat. length(); i++) query + “ AND ” + dat[i] + “ = “ + inp[i]; “=”, dat inp year 2004 min 15
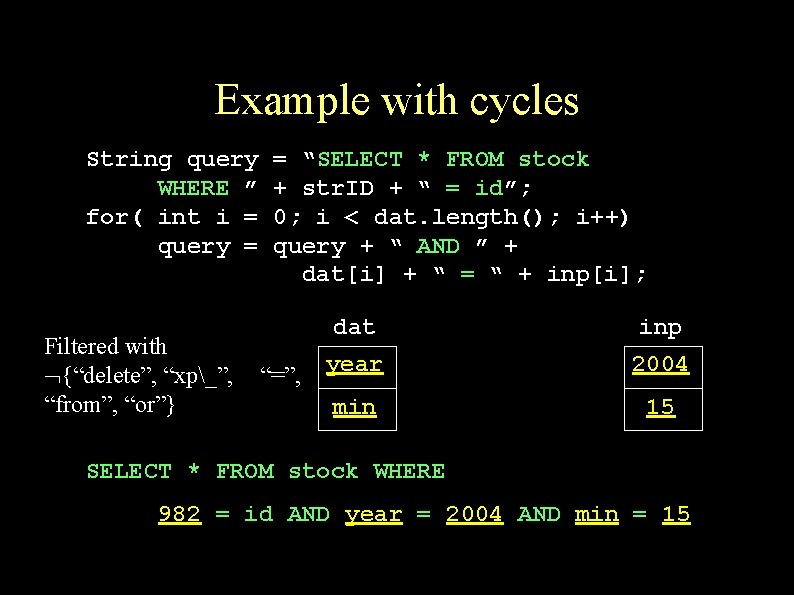
Example with cycles String query WHERE ” for( int i = query = Filtered with {“delete”, “xp_”, “from”, “or”} = “SELECT * FROM stock + str. ID + “ = id”; 0; i < dat. length(); i++) query + “ AND ” + dat[i] + “ = “ + inp[i]; “=”, dat inp year 2004 min 15 SELECT * FROM stock WHERE 982 = id AND year = 2004 AND min = 15
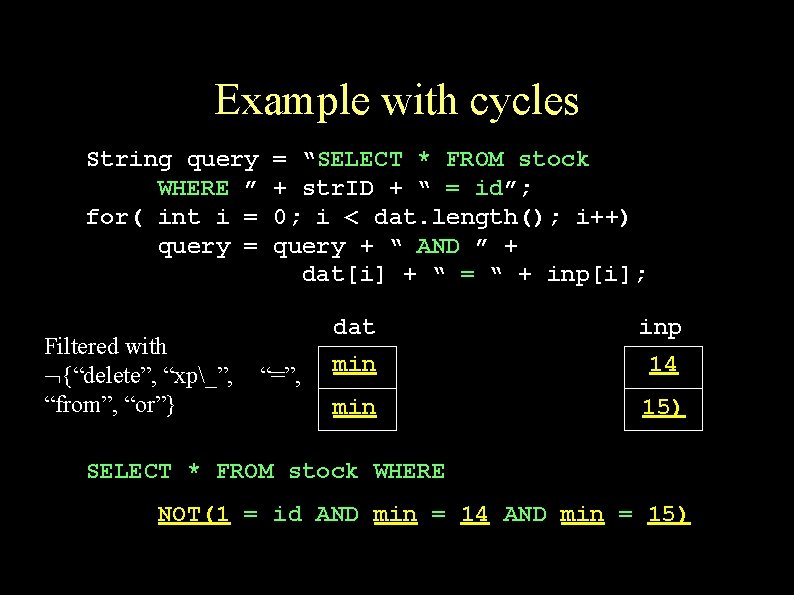
Example with cycles String query WHERE ” for( int i = query = Filtered with {“delete”, “xp_”, “from”, “or”} = “SELECT * FROM stock + str. ID + “ = id”; 0; i < dat. length(); i++) query + “ AND ” + dat[i] + “ = “ + inp[i]; “=”, dat inp min 14 min 15) SELECT * FROM stock WHERE NOT(1 = id AND min = 14 AND min = 15)
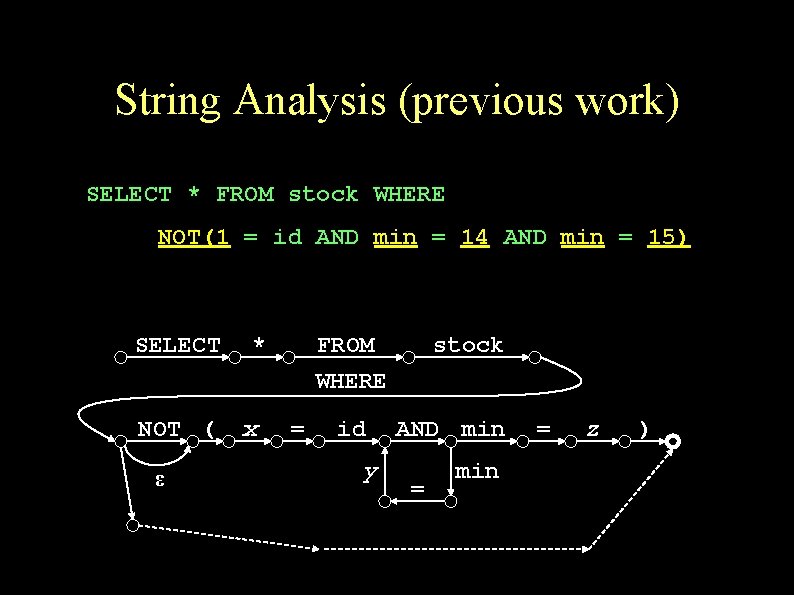
String Analysis (previous work) SELECT * FROM stock WHERE NOT(1 = id AND min = 14 AND min = 15) SELECT NOT ( ε * x FROM WHERE = id y stock AND min = z )
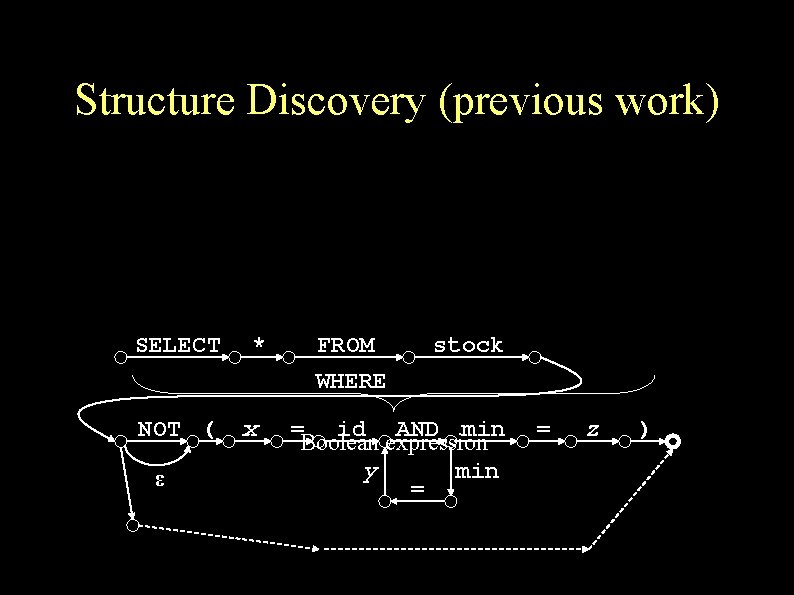
Structure Discovery (previous work) SELECT NOT ( ε * x FROM WHERE stock = id AND min Boolean expression y min = = z )
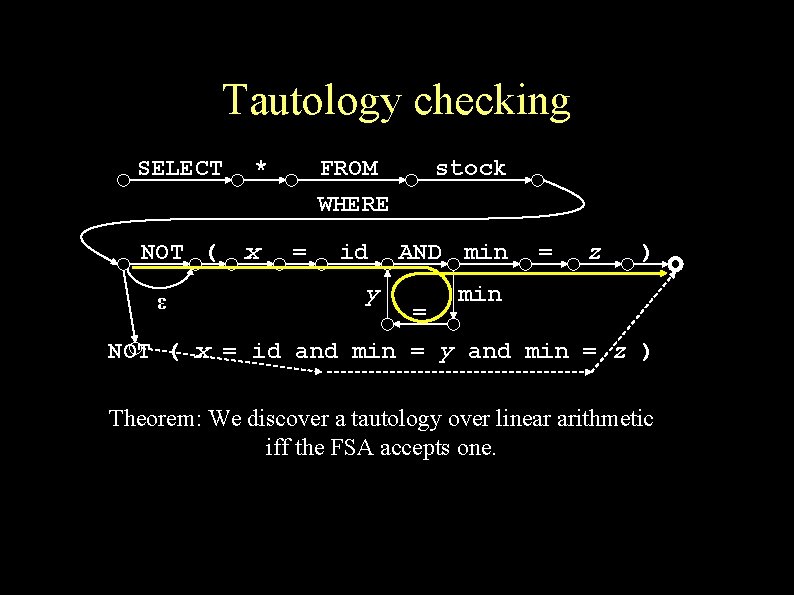
Tautology checking SELECT NOT ( ε * x FROM WHERE = id y stock AND min = = z ) min NOT ( x = id and min = y and min = z ) Theorem: We discover a tautology over linear arithmetic iff the FSA accepts one.

Overview of Tautology Checking Main idea: Generate finite number of validity queries from FSA Challenges: Loops/cycles Arithmetic Boolean
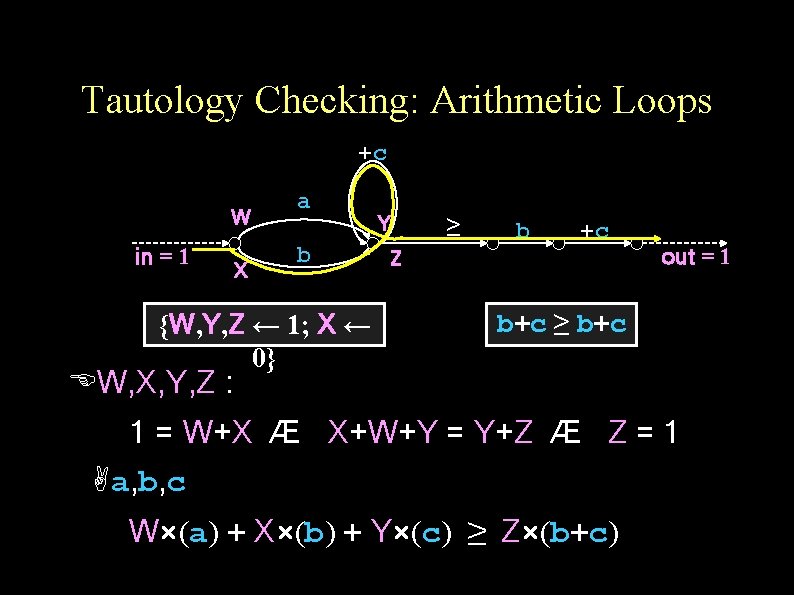
Tautology Checking: Arithmetic Loops +c W in = 1 X a b {W, Y, Z ← 1; X ← 0} Y ≥ b +c Z out = 1 b+c ≥ b+c W, X, Y, Z : 1 = W+X Æ X+W+Y = Y+Z Æ Z = 1 a, b, c W×(a) + X×(b) + Y×(c) ≥ Z×(b+c)
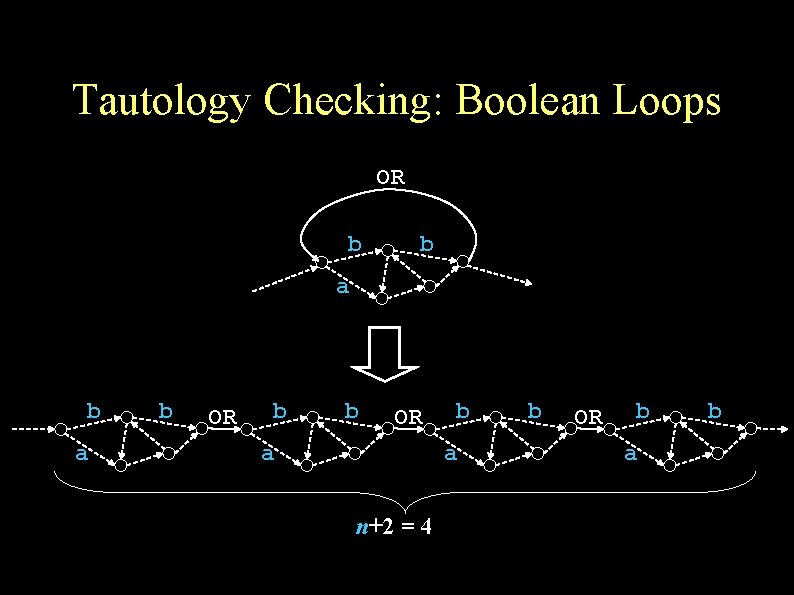
Tautology Checking: Boolean Loops OR b b a b OR b b OR a b a n+2 = 4 b OR b a b
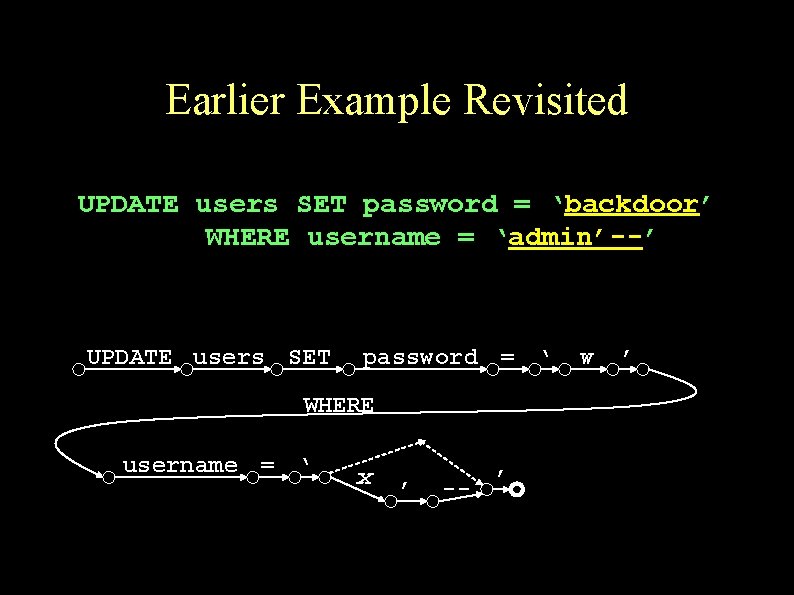
Earlier Example Revisited UPDATE users SET password = ‘backdoor’ WHERE username = ‘admin’--’ UPDATE users SET password = ‘ WHERE username = ‘ x ’ -- ’ w ’

Earlier Example Revisited sql = “UPDATE users SET password = ‘” + newpass + “’ WHERE username = ‘” + rso(“username”) + “’”; This code may also generate a query with a tautology UPDATE users SET password = ‘backdoor’ WHERE username = ‘’OR‘a’=‘a’;
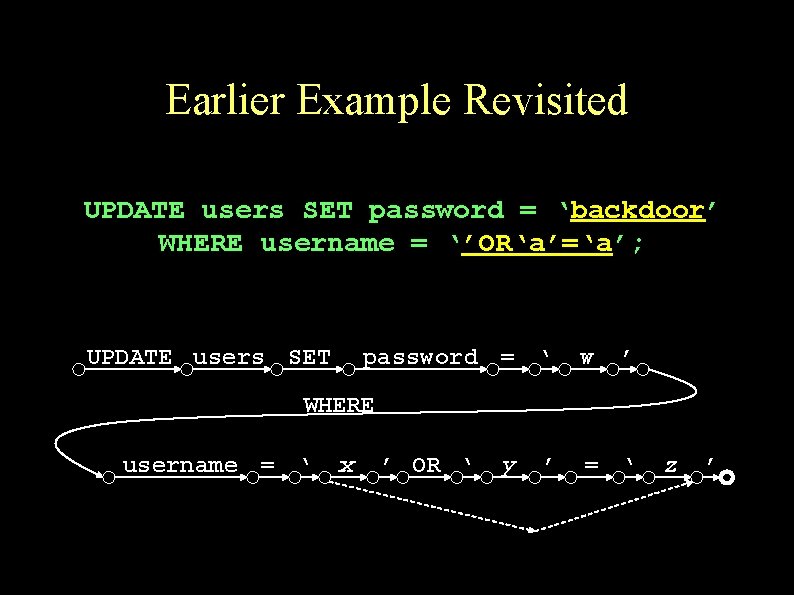
Earlier Example Revisited UPDATE users SET password = ‘backdoor’ WHERE username = ‘’OR‘a’=‘a’; UPDATE users SET password = ‘ w ’ WHERE username = ‘ x ’ OR ‘ y ’ = ‘ z ’

Conclusions Analysis Framework: Generate and analyze FSA model of all possible queries Semantic analysis of generated programs Not only types but values Implementation in progress Questions?

Why n+2?
- Slides: 28