AGENDA Data Compliance Archive and Retention EDiscovery Data

















- Slides: 47



AGENDA Data Compliance • • Archive and Retention EDiscovery Data Flow and Data Access Compliance • • Data Loss Prevention Encryption Mobile Device Management Auditing and Reporting

AGENDA Data Compliance • • Archive and Retention EDiscovery Data Flow and Data Access Compliance • • Data Loss Prevention Encryption Mobile Device Management Auditing and Reporting

Risk: Got anything to worry about? You probably don’t need to be here if

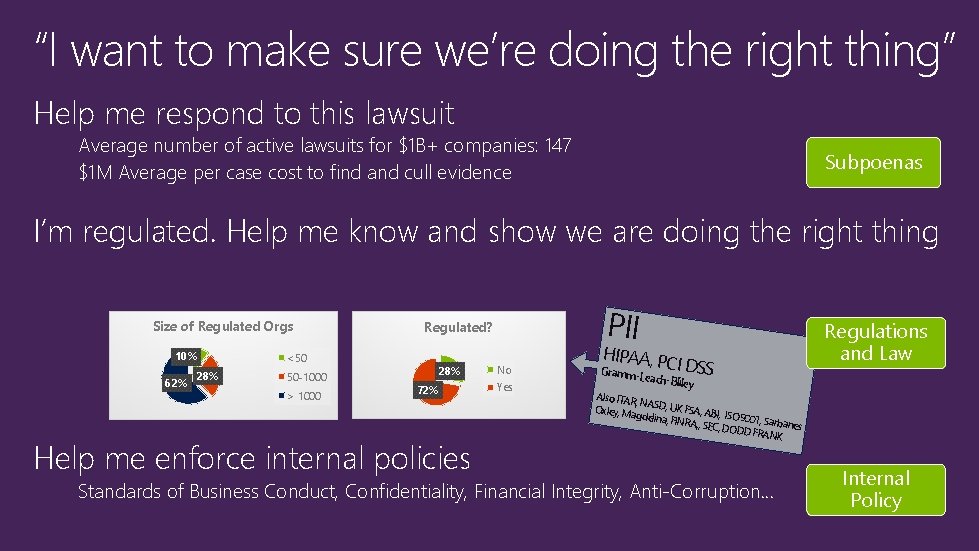
“I want to make sure we’re doing the right thing” Help me respond to this lawsuit Average number of active lawsuits for $1 B+ companies: 147 $1 M Average per case cost to find and cull evidence Subpoenas I’m regulated. Help me know and show we are doing the right thing Size of Regulated Orgs 10% 62% 28% <50 50 -1000 > 1000 PII Regulated? 28% 72% Help me enforce internal policies No Yes HIPAA, P CI DSS G ramm-Le ach-Bliley Regulations and Law Also ITAR , NASD, U KF Oxley, Ma gdelina, F SA, ABI, ISO 9001, Sarbanes INRA, , SE C, DODD FRANK Standards of Business Conduct, Confidentiality, Financial Integrity, Anti-Corruption… Internal Policy

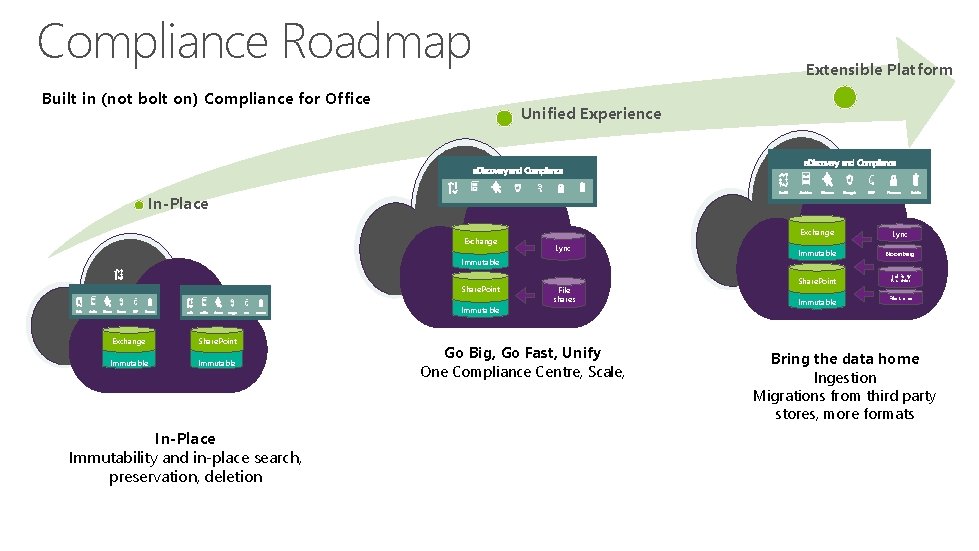
Compliance Roadmap Built in (not bolt on) Compliance for Office Extensible Platform Unified Experience In-Place Archiving Exchange Lync Immutable Share. Point Immutable Exchange Share. Point Immutable In-Place Immutability and in-place search, preservation, deletion File shares Go Big, Go Fast, Unify One Compliance Centre, Scale, Exchange Lync Immutable Bloomberg Share. Point 3 rd Party Archives Immutable File Shares Bring the data home Ingestion Migrations from third party stores, more formats

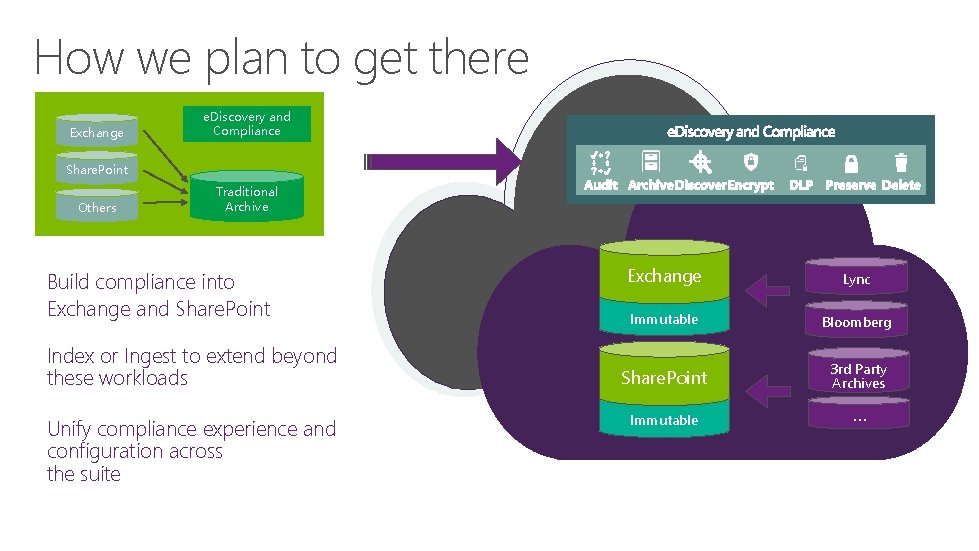
How we plan to get there Exchange e. Discovery and Compliance Share. Point Others Traditional Archive Build compliance into Exchange and Share. Point Index or Ingest to extend beyond these workloads Unify compliance experience and configuration across the suite Exchange Lync Immutable Bloomberg Share. Point 3 rd Party Archives Immutable …

AGENDA Risk, and how we can help Data Compliance • • Archive and Retention EDiscovery Data Flow and Data Access Compliance • • Data Loss Prevention Encryption Mobile Device Management Auditing and Reporting

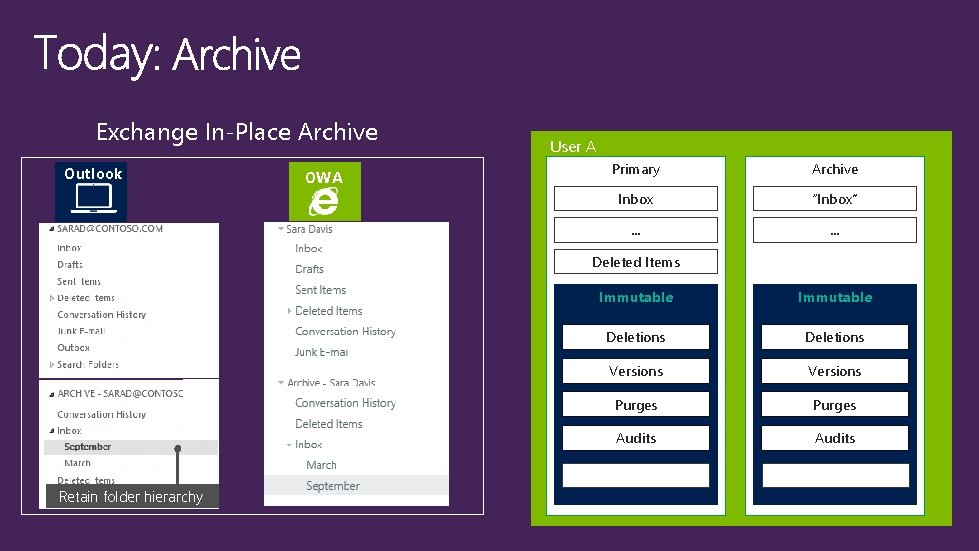
Exchange In-Place Archive Outlook OWA User A Primary Archive Inbox “Inbox” … … Deleted Items Retain folder hierarchy Immutable Deletions Versions Purges Audits … …

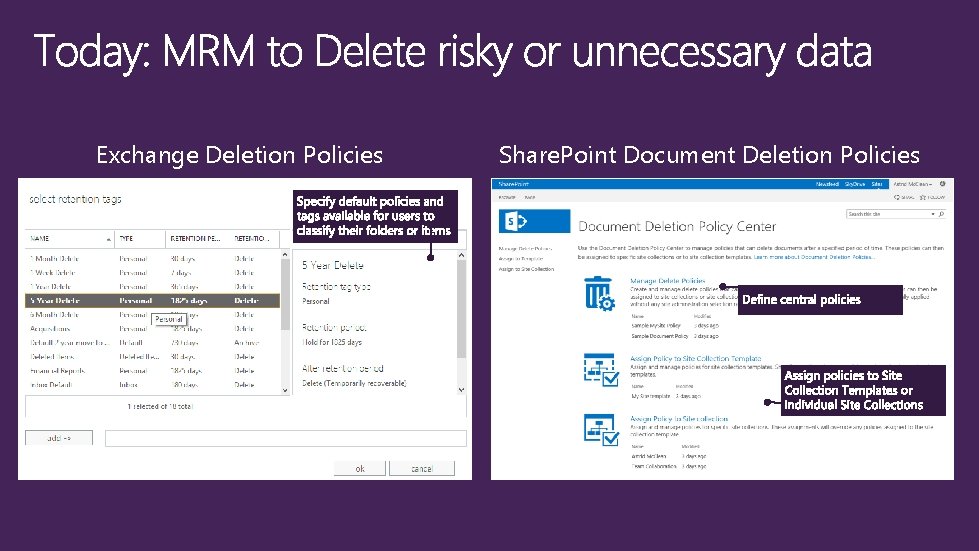
Exchange Deletion Policies Share. Point Document Deletion Policies

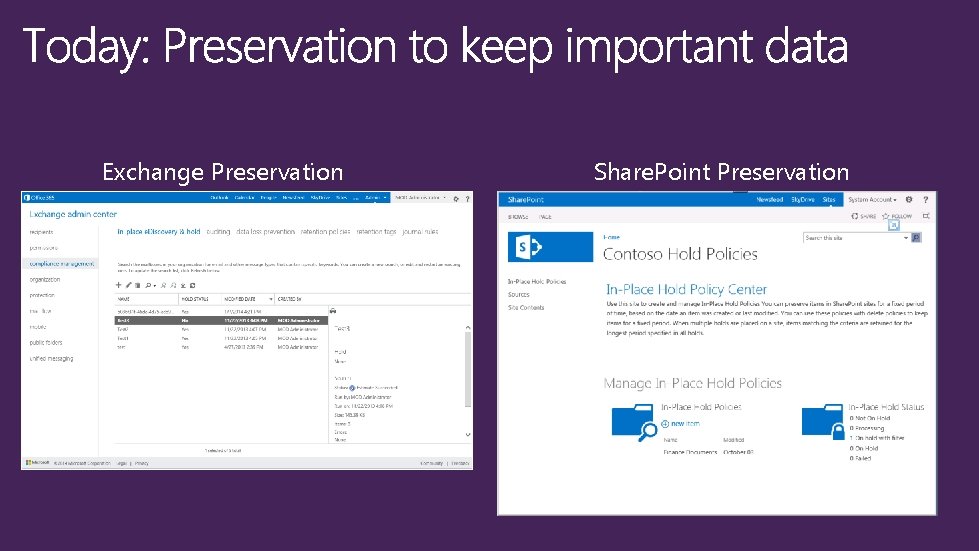
Exchange Preservation Share. Point Preservation

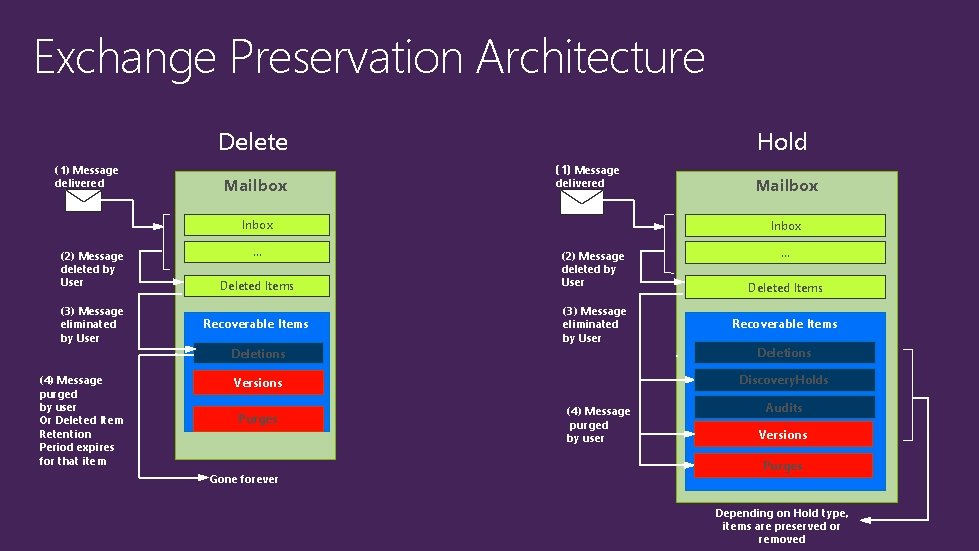
Exchange Preservation Architecture Hold Delete (1) Message delivered Mailbox (1) Message delivered Inbox (2) Message deleted by User (3) Message eliminated by User (4) Message purged by user Or Deleted Item Retention Period expires for that item … Deleted Items Recoverable Items Mailbox Inbox (2) Message deleted by User (3) Message eliminated by User … Deleted Items Recoverable Items Deletions Versions Discovery. Holds Purges Gone forever (4) Message purged by user Audits Versions Purges Depending on Hold type, items are preserved or removed

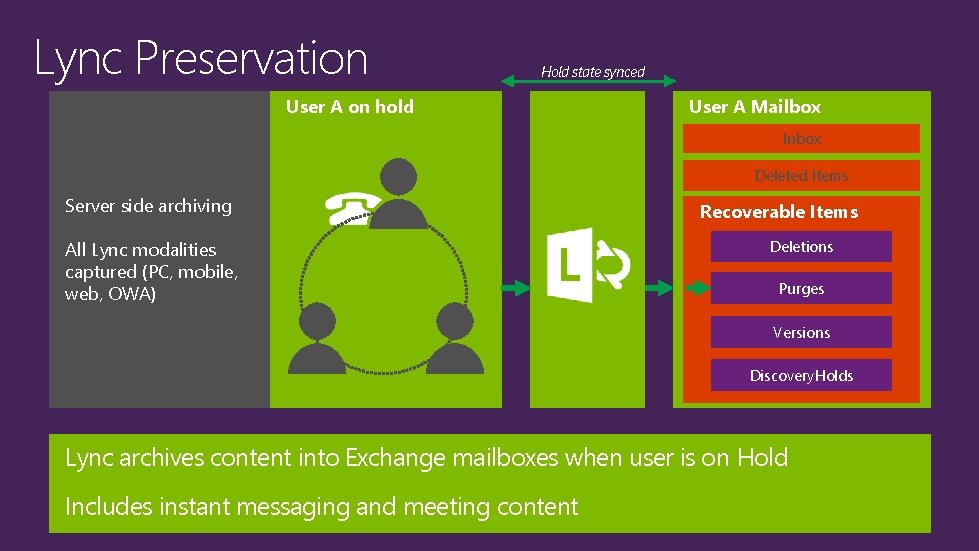
Lync Preservation Hold state synced User A on hold User A Mailbox Inbox Deleted Items Server side archiving All Lync modalities captured (PC, mobile, web, OWA) Recoverable Items Deletions Purges Versions Discovery. Holds Lync archives content into Exchange mailboxes when user is on Hold Includes instant messaging and meeting content

1. 2. • http: //aka. ms/inactivembx

http: //technet. microsoft. com/enus/library/dn 770225(v=exchg. 150). aspx

Future: Archiving • Ingestion • Public Folder Hold • Unified Preserve/Delete experiences • And more…

AGENDA Risk, and how we can help Data Compliance • • Archive and Retention EDiscovery Data Flow and Data Access Compliance • • Data Loss Prevention Encryption Mobile Device Management Auditing and Reporting

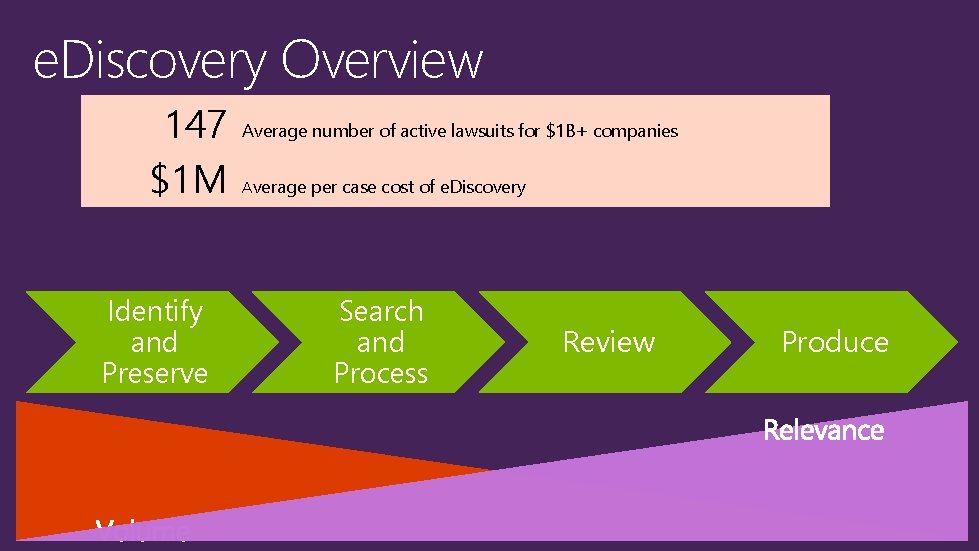
e. Discovery Overview 147 $1 M Identify and Preserve Average number of active lawsuits for $1 B+ companies Average per case cost of e. Discovery Search and Process Review Produce

Today: Multi-Mailbox Search in EAC


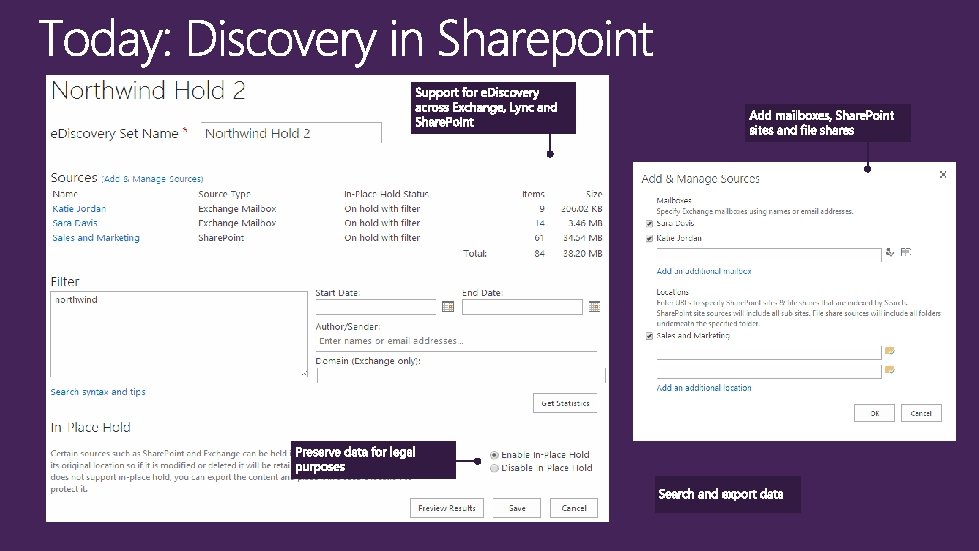
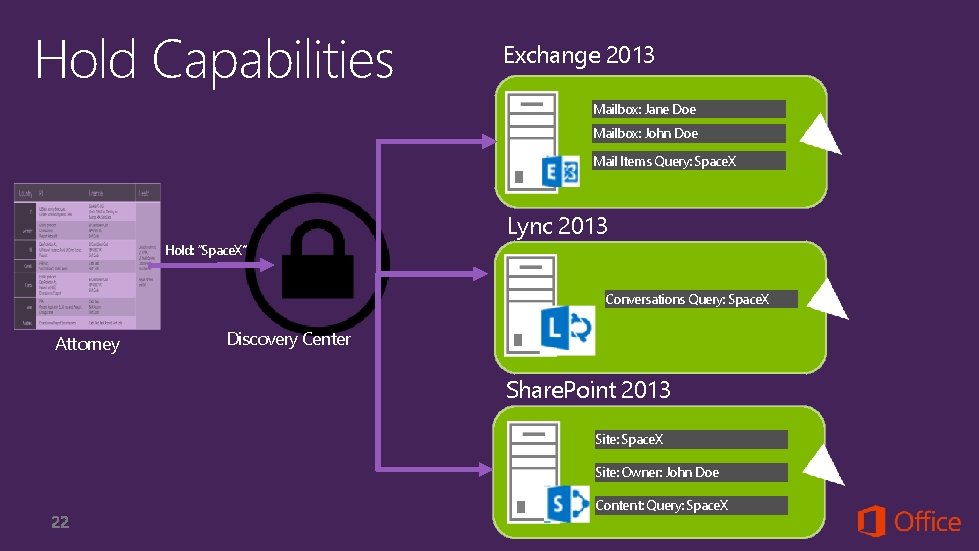
Hold Capabilities Exchange 2013 Mailbox: Jane Doe Mailbox: John Doe Mail Items Query: Space. X Lync 2013 Hold: “Space. X” Conversations Query: Space. X Attorney Discovery Center Share. Point 2013 Site: Space. X Site: Owner: John Doe Content: Query: Space. X

Export Capabilities Easy: download from Share. Point, Exchange, and file shares whether on premises or in Office 365 all at once EDRM XML Support: growing industry standard for data interchange, import into popular review tools Take it offline: Native files, PSTs, pages as. MHT, lists and feeds as. CSV


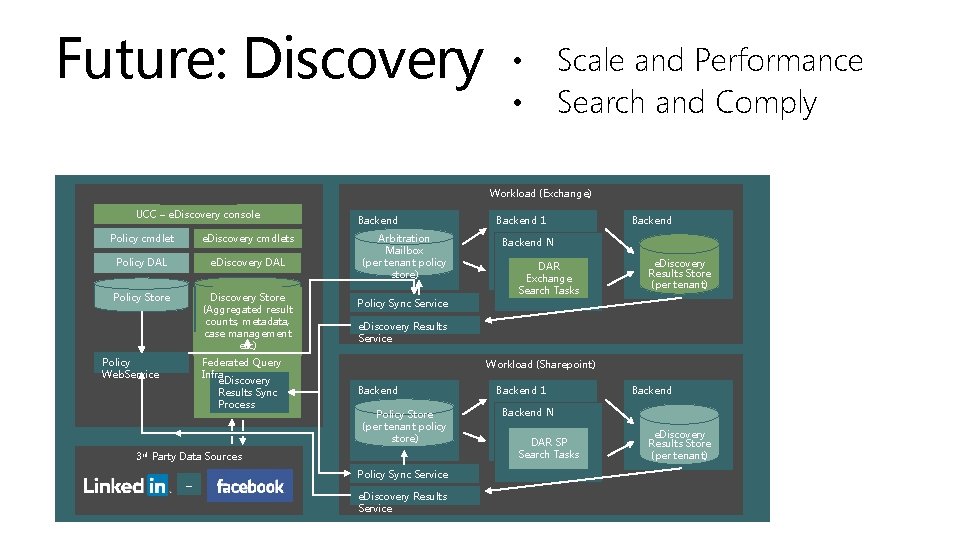
Future: Discovery Policy cmdlet e. Discovery cmdlets Policy DAL e. Discovery DAL Policy Store Discovery Store (Aggregated result counts, metadata, case management etc) Federated Query Infra e. Discovery Results Sync Process Policy Web. Service Backend Arbitration Mailbox (per tenant policy store) Backend 1 Backend N DAR Exchange Search Tasks e. Discovery Results Store (per tenant) Policy Sync Service e. Discovery Results Service Workload (Sharepoint) Backend Policy Store (per tenant policy store) 3 rd Party Data Sources … Scale and Performance Search and Comply Workload (Exchange) FFO/EOP UCC – e. Discovery console • • Policy Sync Service e. Discovery Results Service Backend 1 Backend N DAR SP Search Tasks e. Discovery Results Store (per tenant)

AGENDA Risk, and how we can help Data Compliance • • Archive and Retention Ediscovery Data Flow and Data Access Compliance • • Data Loss Prevention Encryption Mobile Device Management Auditing and Reporting

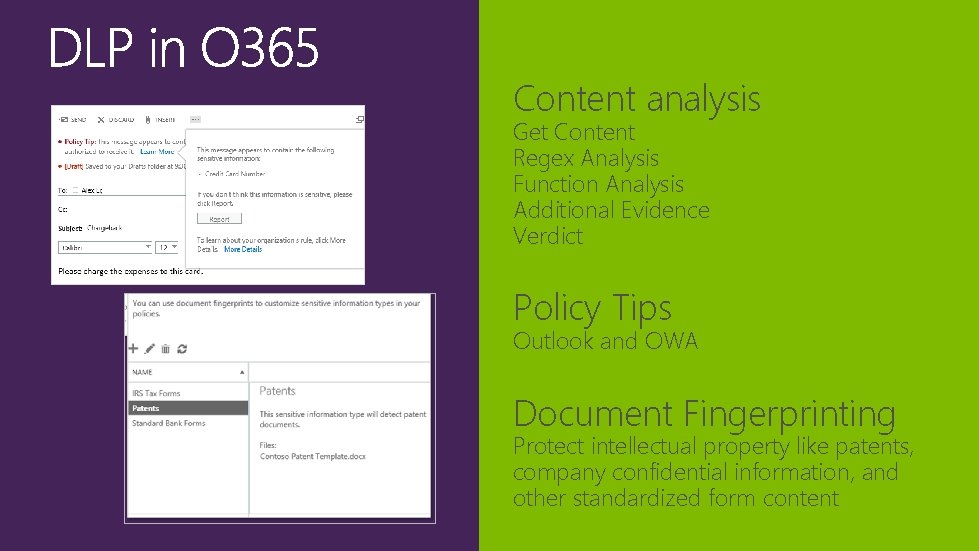
Content analysis Get Content Regex Analysis Function Analysis Additional Evidence Verdict Policy Tips Outlook and OWA Document Fingerprinting Protect intellectual property like patents, company confidential information, and other standardized form content

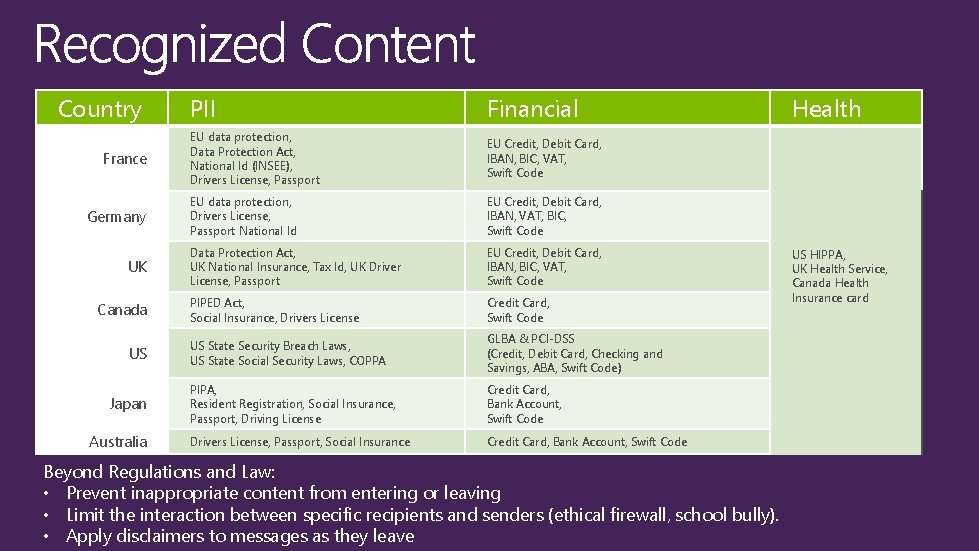
Country France Germany UK Canada US Japan Australia PII Financial EU data protection, Data Protection Act, National Id (INSEE), Drivers License, Passport EU Credit, Debit Card, IBAN, BIC, VAT, Swift Code EU data protection, Drivers License, Passport National Id EU Credit, Debit Card, IBAN, VAT, BIC, Swift Code Data Protection Act, UK National Insurance, Tax Id, UK Driver License, Passport EU Credit, Debit Card, IBAN, BIC, VAT, Swift Code PIPED Act, Social Insurance, Drivers License Credit Card, Swift Code US State Security Breach Laws, US State Social Security Laws, COPPA GLBA & PCI-DSS (Credit, Debit Card, Checking and Savings, ABA, Swift Code) PIPA, Resident Registration, Social Insurance, Passport, Driving License Credit Card, Bank Account, Swift Code Drivers License, Passport, Social Insurance Credit Card, Bank Account, Swift Code Beyond Regulations and Law: • Prevent inappropriate content from entering or leaving • Limit the interaction between specific recipients and senders (ethical firewall, school bully). • Apply disclaimers to messages as they leave Health US HIPPA, UK Health Service, Canada Health Insurance card

IRM (RMS) S/MIME OME Prevents sensitive information from being printed, forwarded, or copied by unauthorized people inside the organization Sign and encrypt messages to users using certificates Encrypt messages to any SMTP address

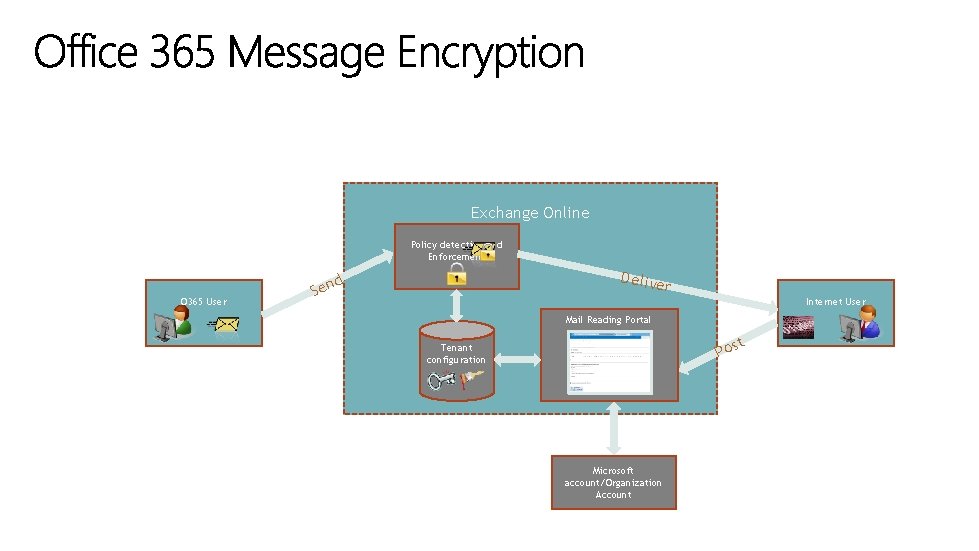
Exchange Online Policy detection and Enforcement O 365 User Delive d Sen r Internet User Mail Reading Portal t Pos Tenant configuration Microsoft account/Organization Account

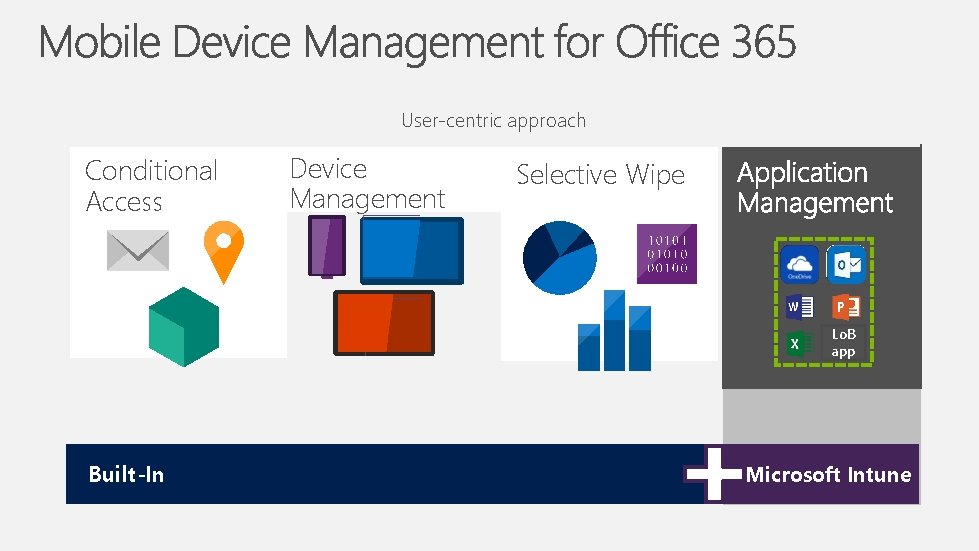
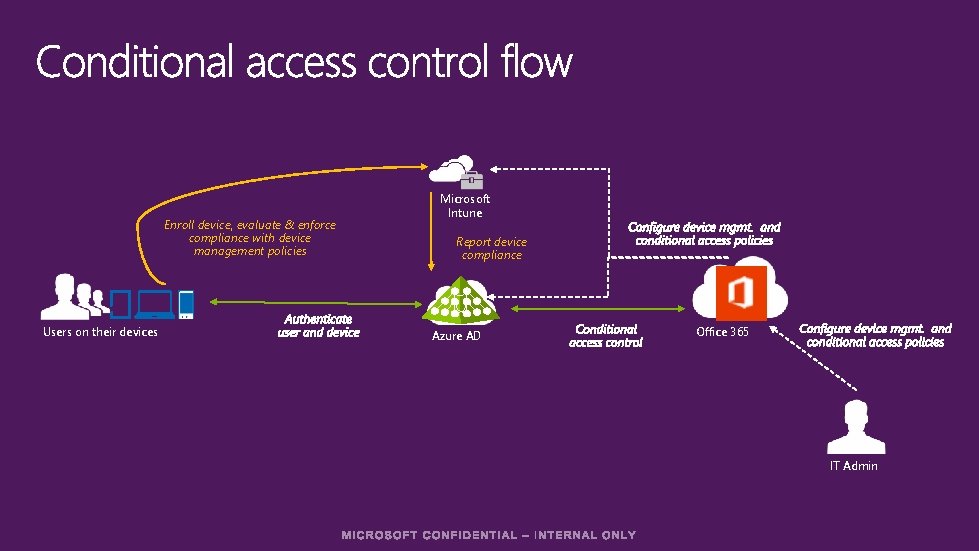
User-centric approach Conditional Access Device Management Selective Wipe Lo. B app Built-In Microsoft Intune

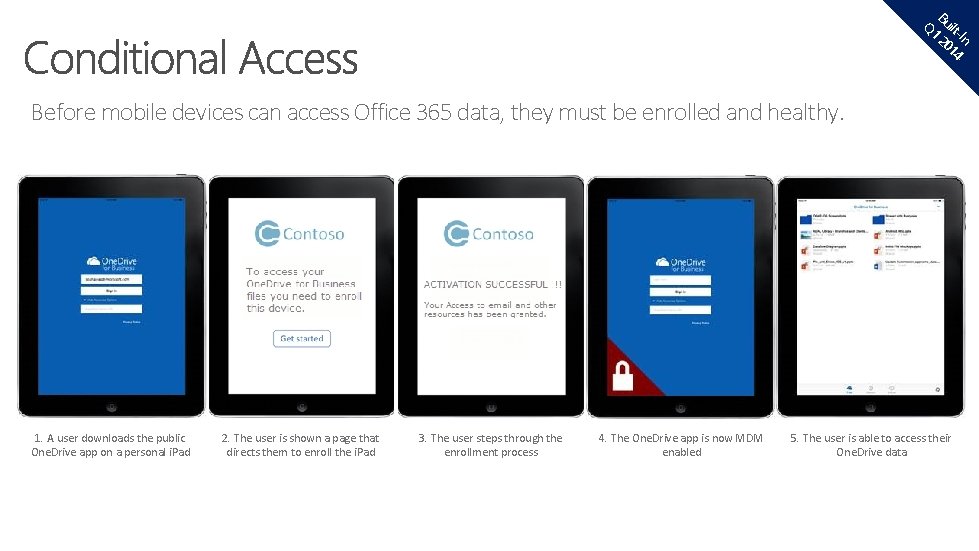
B Q 1 uilt 20 -In 14 Before mobile devices can access Office 365 data, they must be enrolled and healthy. 1. A user downloads the public One. Drive app on a personal i. Pad 2. The user is shown a page that directs them to enroll the i. Pad 3. The user steps through the enrollment process 4. The One. Drive app is now MDM enabled 5. The user is able to access their One. Drive data

Enroll device, evaluate & enforce compliance with device management policies Users on their devices Microsoft Intune Report device compliance Azure AD Office 365 IT Admin

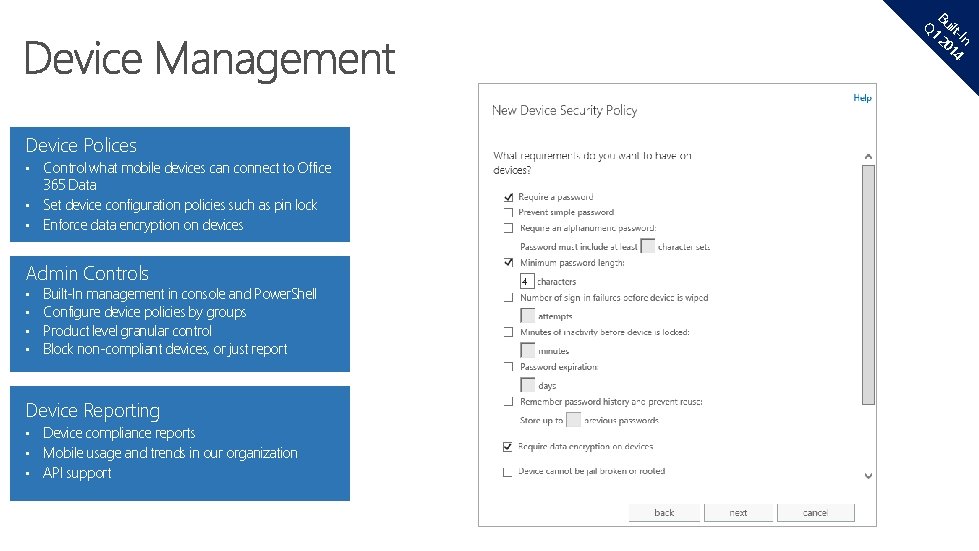
B Q 1 uilt 20 -In 14 Device Polices Control what mobile devices can connect to Office 365 Data • Set device configuration policies such as pin lock • Enforce data encryption on devices • Admin Controls • • Built-In management in console and Power. Shell Configure device policies by groups Product level granular control Block non-compliant devices, or just report Device Reporting Device compliance reports • Mobile usage and trends in our organization • API support •


Exchange Auditing Share. Point Auditing


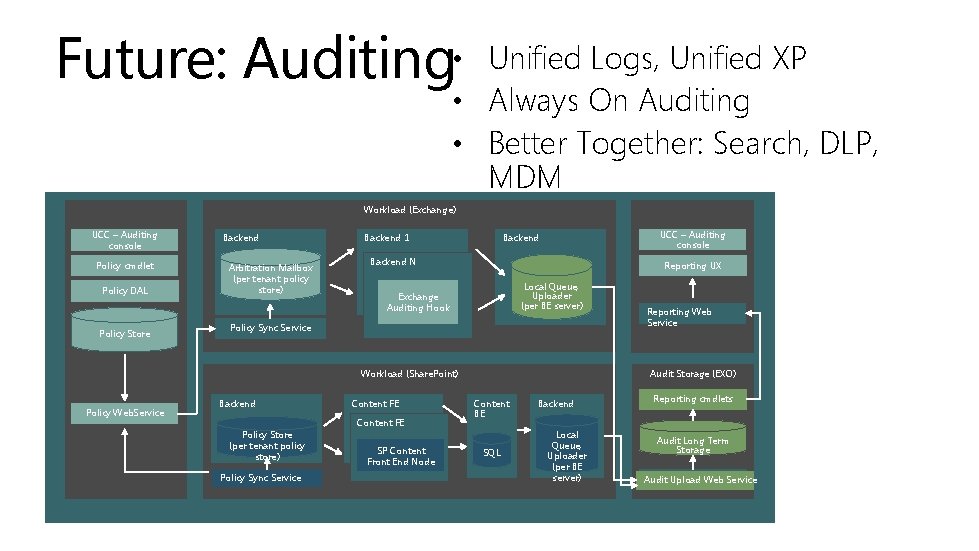
Future: Auditing • Unified Logs, Unified XP • Always On Auditing • Better Together: Search, DLP, MDM FFO/EOP UCC – Auditing console Policy cmdlet Policy DAL Policy Store FFO/EOP Workload (Exchange) Backend Arbitration Mailbox (per tenant policy store) Backend 1 UCC – Auditing console Backend N Reporting UX Local Queue, Uploader (per BE server) Exchange Auditing Hook Policy Sync Service Workload (Share. Point) Policy Web. Service Backend Content FE Policy Store (per tenant policy store) Policy Sync Service SP Content Front End Node Reporting Web Service Audit Storage (EXO) Content BE SQL Backend Local Queue, Uploader (per BE server) Reporting cmdlets Audit Long Term Storage Audit Upload Web Service

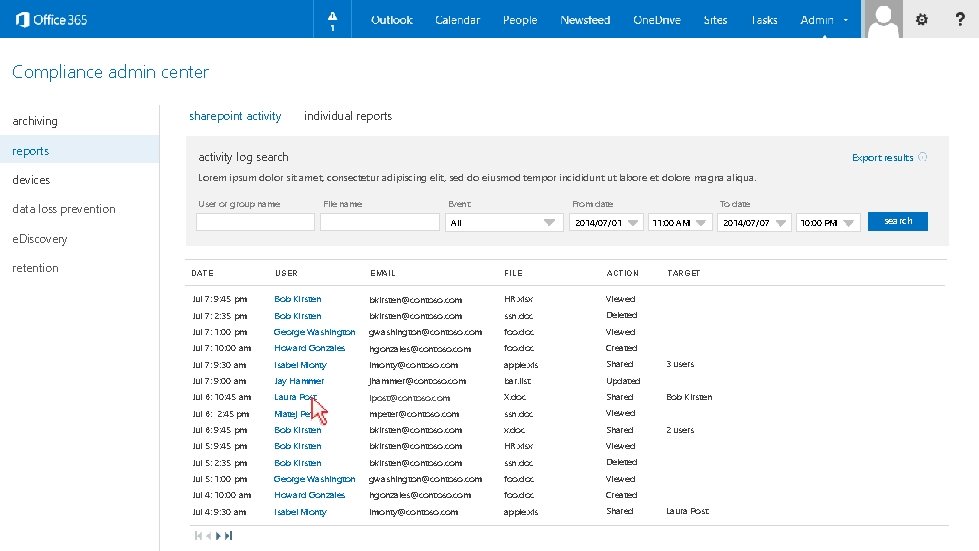
Compliance admin center archiving reports sharepoint activity individual reports activity log search Export results devices Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. data loss prevention User or group name File name From date Event All 2014/07/01 To date 11: 00 AM e. Discovery retention DATE USER EMAIL FILE ACTION Jul 7: 9: 45 pm Bob Kirsten bkirsten@contoso. com HR. xlsx Viewed Jul 7: 2: 35 pm Bob Kirsten bkirsten@contoso. com ssn. doc Deleted Jul 7: 1: 00 pm George Washington gwashington@contoso. com foo. doc Viewed Jul 7: 10: 00 am Howard Gonzales hgonzales@contoso. com foo. doc Created Jul 7: 9: 30 am Isabel Monty imonty@contoso. com apple. xls Shared Jul 7: 9: 00 am Jay Hammer jhammer@contoso. com bar. list Updated Jul 6: 10: 45 am Laura Post lpost@contoso. com X. doc Shared Jul 6: 2: 45 pm Matej Peter mpeter@contoso. com ssn. doc Viewed Jul 6: 9: 45 pm Bob Kirsten bkirsten@contoso. com x. doc Shared Jul 5: 9: 45 pm Bob Kirsten bkirsten@contoso. com HR. xlsx Viewed Jul 5: 2: 35 pm Bob Kirsten bkirsten@contoso. com ssn. doc Deleted Jul 5: 1: 00 pm George Washington gwashington@contoso. com foo. doc Viewed Jul 4: 10: 00 am Howard Gonzales hgonzales@contoso. com foo. doc Created Jul 4: 9: 30 am Isabel Monty imonty@contoso. com apple. xls Shared TARGET 3 users Bob Kirsten 2 users Laura Post 2014/07/07 10: 00 PM search

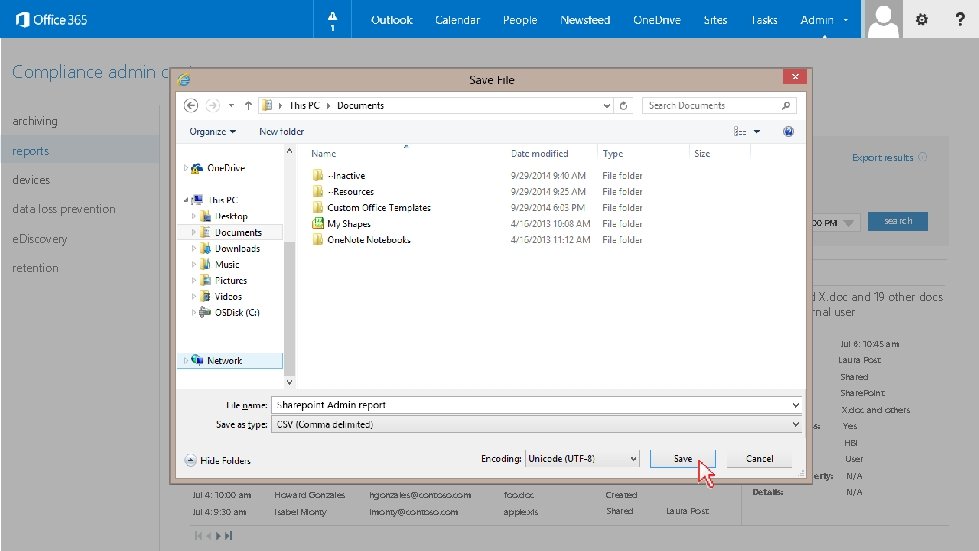
Compliance admin center archiving reports sharepoint activity individual reports activity log search Export results devices Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. data loss prevention User or group name File name From date Event All 2014/07/01 To date 11: 00 AM 2014/07/07 search 10: 00 PM e. Discovery retention DATE USER EMAIL FILE ACTION Jul 7: 9: 45 pm Bob Kirsten bkirsten@contoso. com HR. xlsx Viewed Jul 7: 2: 35 pm Bob Kirsten bkirsten@contoso. com ssn. doc Deleted Jul 7: 1: 00 pm George Washington gwashington@contoso. com foo. doc Viewed Jul 7: 10: 00 am Howard Gonzales hgonzales@contoso. com foo. doc Created Jul 7: 9: 30 am Isabel Monty imonty@contoso. com apple. xls Shared Jul 7: 9: 00 am Jay Hammer jhammer@contoso. com bar. list Updated Jul 6: 10: 45 am Laura Post lpost@contoso. com X. doc Shared Jul 6: 2: 45 pm Matej Peter mpeter@contoso. com ssn. doc Viewed Jul 6: 9: 45 pm Bob Kirsten bkirsten@contoso. com x. doc Shared Jul 5: 9: 45 pm Bob Kirsten bkirsten@contoso. com HR. xlsx Jul 5: 2: 35 pm Bob Kirsten bkirsten@contoso. com Jul 5: 1: 00 pm George Washington Jul 4: 10: 00 am Jul 4: 9: 30 am TARGET Laura shared X. doc and 19 other docs with an external user Date: Jul 6: 10: 45 am User: Laura Post Action: Shared Service: Share. Point Entity: X. doc and others External Access: Yes Viewed Classification: HBI ssn. doc Deleted User Type: User gwashington@contoso. com foo. doc Viewed Modified Property: N/A Howard Gonzales hgonzales@contoso. com foo. doc Created Details: N/A Isabel Monty imonty@contoso. com apple. xls Shared 3 users Bob Kirsten 2 users Laura Post

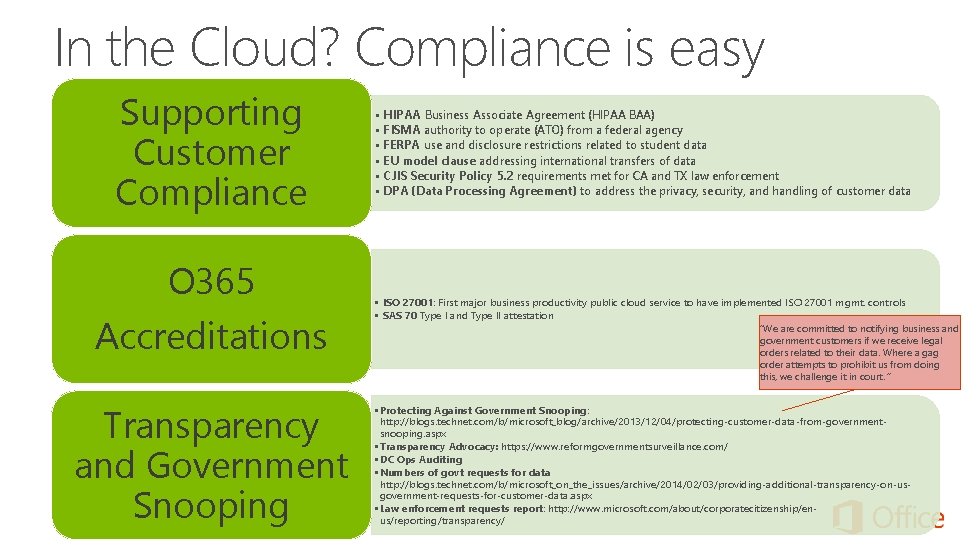
In the Cloud? Compliance is easy Supporting Customer Compliance O 365 Accreditations Transparency and Government Snooping • • • HIPAA Business Associate Agreement (HIPAA BAA) FISMA authority to operate (ATO) from a federal agency FERPA use and disclosure restrictions related to student data EU model clause addressing international transfers of data CJIS Security Policy 5. 2 requirements met for CA and TX law enforcement DPA (Data Processing Agreement) to address the privacy, security, and handling of customer data • ISO 27001: First major business productivity public cloud service to have implemented ISO 27001 mgmt. controls • SAS 70 Type I and Type II attestation “We are committed to notifying business and government customers if we receive legal orders related to their data. Where a gag order attempts to prohibit us from doing this, we challenge it in court. “ • Protecting Against Government Snooping: http: //blogs. technet. com/b/microsoft_blog/archive/2013/12/04/protecting-customer-data-from-governmentsnooping. aspx • Transparency Advocacy: https: //www. reformgovernmentsurveillance. com/ • DC Ops Auditing • Numbers of govt requests for data http: //blogs. technet. com/b/microsoft_on_the_issues/archive/2014/02/03/providing-additional-transparency-on-usgovernment-requests-for-customer-data. aspx • Law enforcement requests report: http: //www. microsoft. com/about/corporatecitizenship/enus/reporting/transparency/


http: //channel 9. msdn. com/Events/Tech. Ed www. microsoft. com/learning http: //microsoft. com/technet http: //developer. microsoft. com

M A S P E L

S M A E L P


\showsrusimagesCorporate_FontsPCSegoe UISegoe_UI_Font_family