Advanced Operating Systems Lecture notes Dr Clifford Neuman




























- Slides: 40

Advanced Operating Systems Lecture notes Dr. Clifford Neuman University of Southern California Information Sciences Institute Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

CSci 555: Advanced Operating Systems Lecture 4 – September 18 2009 Naming and Binding Dr. Clifford Neuman University of Southern California Information Sciences Institute Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Naming Concepts v. Name q What you call something v. Address q Where it is located v. Route q How one gets to it What is http: //www. isi. edu/~bcn ? v. But it is not that clear anymore, it depends on perspective. A name from one perspective may be an address from another. q Perspective means layer of abstraction Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

What are things we name v Users q To direct, and to identify v Hosts (computers) q High level and low level v Services q Service and instance v Files and other “objects” q Content and repository v Groups q Of any of the above Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

How we name things v Host-Based Naming q Host-name is required part of object name v Global Naming q Must look-up name in global database to find address q Name transparency v User/Object Centered Naming q Namespace is centered around user or object v Attribute-Based Naming q Object identified by unique characteristics q Related to resource discovery / search / indexes Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

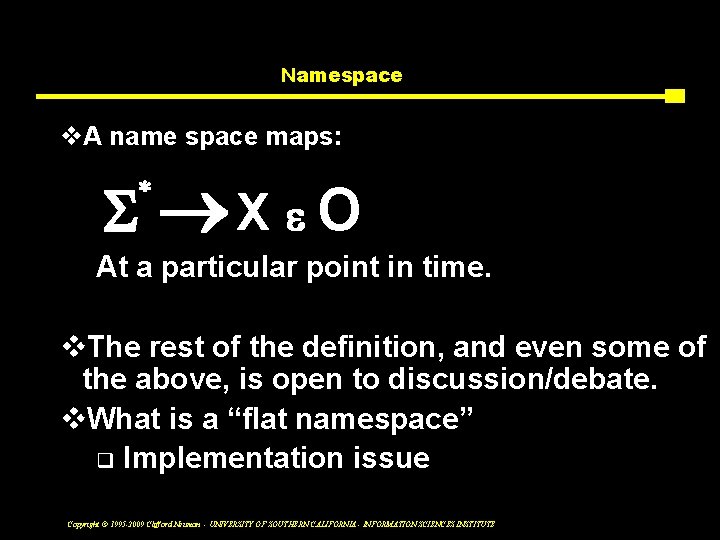
Namespace v. A name space maps: S * ®X e O At a particular point in time. v. The rest of the definition, and even some of the above, is open to discussion/debate. v. What is a “flat namespace” q Implementation issue Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

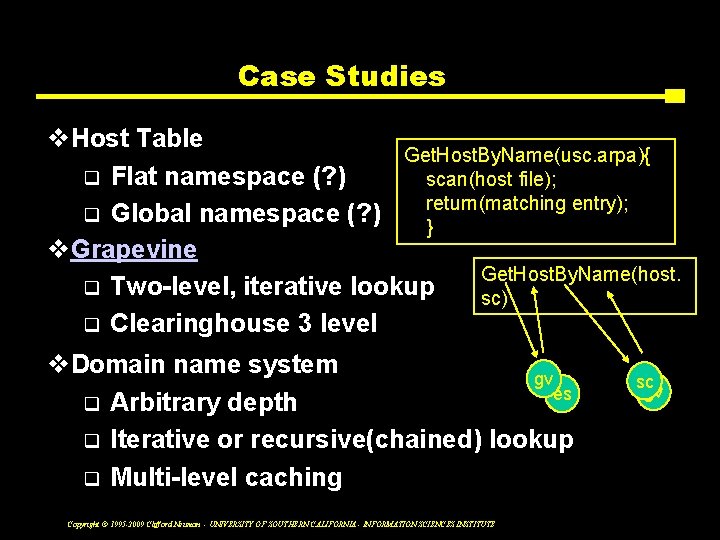
Case Studies v. Host Table Get. Host. By. Name(usc. arpa){ q Flat namespace (? ) scan(host file); return(matching entry); q Global namespace (? ) } v. Grapevine Get. Host. By. Name(host. q Two-level, iterative lookup sc) q Clearinghouse 3 level v. Domain name system gv es q Arbitrary depth q Iterative or recursive(chained) lookup q Multi-level caching Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE sc gv

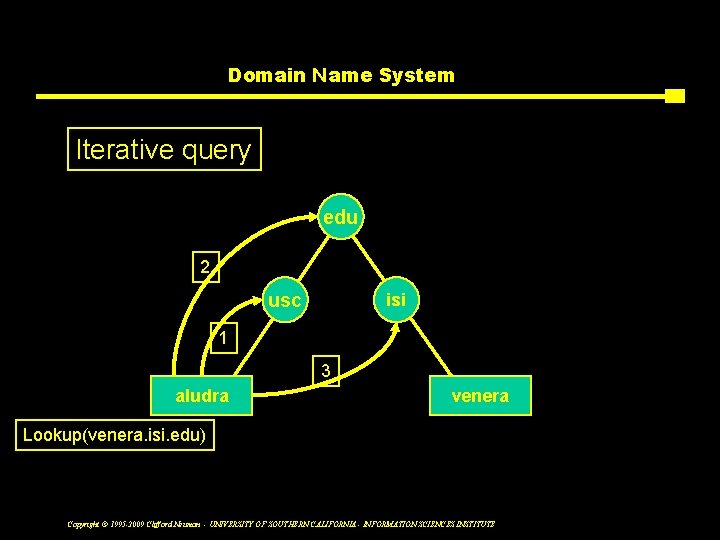
Domain Name System Iterative query edu 2 usc isi 1 3 aludra venera Lookup(venera. isi. edu) Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

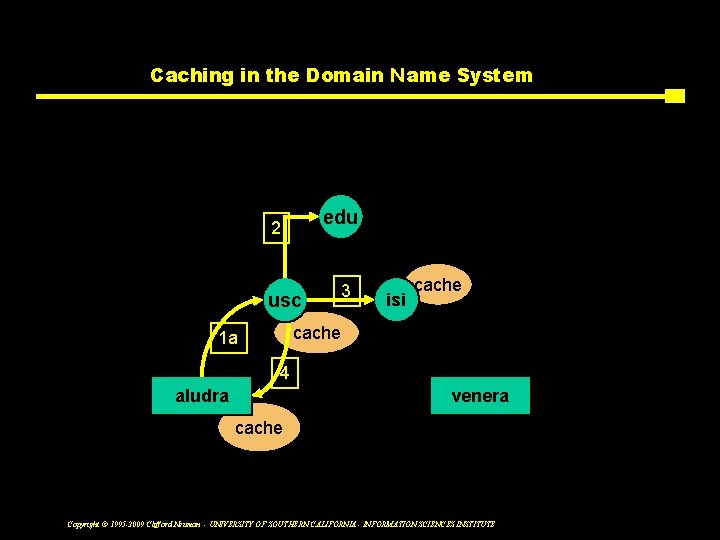
Caching in the Domain Name System Chained query edu 2 usc 3 isi cache 1 a 4 aludra Lookup(venera. isi. edu) venera cache Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Scalability of naming v Scalability q Ability to continue to operate efficiently as a system grows large, either numerically, geographically, or administratively. v Affected by q Frequency of update q Granularity q Evolution/reconfiguration v DNS characteristics q Multi-level implementation q Replication of root and other servers q Multi-level caching Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Closure v Closure binds an object to the namespace within which names embedded in the object are to be resolved. q “Object” may as small as the name itself § GNS binds the names to namespaces § Prospero binds enclosing object to multiple namespaces § Tilde and quicksilver bind users to namespaces § NFS mount table constructs system centered namespace q Movement of objects can cause problems § When closure is associated with wrong entity Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Other implementations of naming v. Broadcast q Limited scalability, but faster local response v. Prefix tables q Essentially a form of caching v. Capabilities q Combines security and naming q Traditional name service built over capability based addresses Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Advanced Name Systems v DEC’s Global Naming q Support for reorganization the key idea q Little coordination needed in advance v Half Closure q Names are all tagged with namespace identifiers § DID - Directory Identifier § Hidden part of name - makes it global § Upon reorganization, new DID assigned § Old names relative to old root q But the DID’s must be unique - how do we assign? Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Prospero Directory Service v Multiple namespace centered around a “root” node that is specific to each namespace. q Closure binds objects to this “root” node. v Layers of naming q User level names are “object” centered q Objects still have an address which is global q Namespaces also have global addresses v Customization in Prospero q Filters create user level derived namespaces on the fly q Union links support merging of views Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Resource Discovery v. Similar to naming q Browsing related to directory services q Indexing and search similar to attribute based naming v. Attribute based naming q Profile q Multi-structured naming v. Search engines v. Computing resource discovery Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

The Web v. Object handles q Uniform Resource Identifier (URI’s) q Uniform Resource Locators (URL’s) q Uniform Resource Names (URN’s) v. XML q Definitions provide a form of closure § Conceptual level rather than the “namespace” level. Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

LDAP v. Manage information about users, services q Lighter weight than X. 500 DAP § Heavier than DNS q Applications have conventions on where to look § Often data is duplicated because of multiple conventions q Performance enhancements not as well defined § Caching harder because of less constrained patterns of access Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

CSci 555: Advanced Operating Systems Lecture 5 – September 26 2008 ADVANCE SLIDES (These slides WILL change) Dr. Clifford Neuman University of Southern California Information Sciences Institute Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

New Computing Environments v. Ubiquitous and Pervasive Computing q Including Sensor Nodes q Managing Devices v. Mobile computing q Portable Devices Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Characteristics v. Low power availability v. Constrained resources v. Transient relationships v. Ad-hoc deployment v. Peer to Peer relationships v. Weakly managed Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Ubiquitous computing v. According to Mark Weiser at Xerox: q Transparent computing is the ultimate goal q Computers should disappear into the background q Computation becomes part of the environment Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Ubiquitous Computing v Computing everywhere q Desktop, Laptop, Palmtop q Cars, Cell phones q Shoes, Clothing, Walls (paper / paint) v Connectivity everywhere q Broadband q Wireless v Mobile everywhere q Users move around q Disposable devices Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Ubiquitous Computing v. Structure q q q Resource and service discovery critical User location an issue Interface discovery Disconnected operation Ad-hoc organization v. Security q q Small devices with limited power Intermittent connectivity v. Agents v. Sensor Networks Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Mobile Computing v. Often managed devices q Cell phones q PDA’s q Subscription Services Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Ad-hoc Networking v. Peer-to-peer of network routing v. Transient devices v. Issues: q Discovery q Security q Power v. Examples: q Many Sensor Networks Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

CSci 555: Advanced Operating Systems Lecture 5 – September 25 2009 Ubiquitous and Mobile Computing Dr. Clifford Neuman University of Southern California Information Sciences Institute Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

New Computing Environments v. Ubiquitous and Pervasive Computing q Including Sensor Nodes q Managing Devices v. Mobile computing q Portable Devices Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Characteristics v. Low power availability v. Constrained resources v. Transient relationships v. Ad-hoc deployment v. Peer to Peer relationships v. Weakly managed v. Context aware Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Ubiquitous computing v. According to Mark Weiser at Xerox: q Transparent computing is the ultimate goal q Computers should disappear into the background q Computation becomes part of the environment Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Ubiquitous Computing v Computing everywhere q Desktop, Laptop, Palmtop q Cars, Cell phones q Shoes, Clothing, Walls (paper / paint) v Connectivity everywhere q Broadband q Wireless v Mobile everywhere q Users move around q Disposable devices Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Ubiquitous Computing v. Structure q q q Resource and service discovery critical User location an issue Interface discovery Disconnected operation Ad-hoc organization v. Security q q Small devices with limited power Intermittent connectivity v. Agents v. Sensor Networks Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Mobile Computing v. Often managed devices q Cell phones q PDA’s q Subscription Services Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Ad-hoc Networking v. Peer-to-peer of network routing v. Transient devices v. Issues: q Discovery q Security q Power v. Examples: q Many Sensor Networks Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

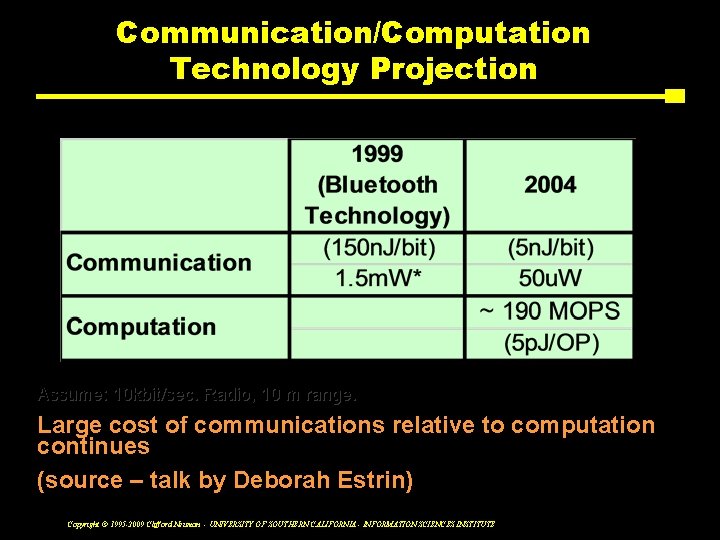
Source: ISI & DARPA PAC/C Program Communication/Computation Technology Projection Assume: 10 kbit/sec. Radio, 10 m range. Large cost of communications relative to computation continues (source – talk by Deborah Estrin) Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Active Badges v. Provides location information and one or more buttons v. Simple interface q Controlled access q Carries context § Two way, device knows where your are, and your location knows you are present § Moves your environment Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

In-Network Processing v. Communication is expensive, computing less-so, so pre-process to reduce data sent. v. Send information, not-data. v. Requires more knowledge at the edges so that query can be distributed. v. Intermediate nodes correlate and agregate results. Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Directed Diffusion v. Publish/Subscribe model v. Data named, not nodes v. But what are the implications q discussion Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

A Taxonomy v. Approaches/Products/Devices differ by placement/nature of: q Management q Storage q Computing q Communication q Context maintenance q Authority Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Classes v. Mobile Terminals v. Passive devices v. Personal Devices v. Remote Sensors/Actuators v. Communicating Devices v. Sensor Networks Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE

Examples v. Cell Phones vi-phone v. PDA v. Home automation v. Proximity cards v. Laptop computer v. In Vehicle networks v. Active Badges Copyright © 1995 -2009 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE