Advanced Encryption Standard Origins NIST issued a new







![• Each added word w[i] depends on the immediately preceding word, w[i- 1], • Each added word w[i] depends on the immediately preceding word, w[i- 1],](https://slidetodoc.com/presentation_image_h2/4da9e9efc052144569669ed6a0f4371b/image-32.jpg)


- Slides: 36

Advanced Encryption Standard

Origins • NIST issued a new version of DES in 1999 (FIPS PUB 46 -3) • DES should only be used in legacy systems • 3 DES will be used • 3 DES has 2 attractions o 168 -bit key length § Removes vulnerability to brute force attack o The underlying algorithm in 3 DES is same as in DES § Easy to understand § Nothing new-it does not need to further evaluate § Resistant to cryptanalytic attack now • Therefore 3 DES was considered an appropriate choice for standardized algorithm for decades to come • But DES suffers some drawbacks o DES was not efficient algorithm in software and 3 DES involves three DES rounds, hence 3 times slower o Both DES and 3 DES use a 64 -bit block size • Because of these drawbacks, 3 DES is not a reasonable candidate for long term-NIST issued therefore a new call for the selection of new standard-called as Advanced Encryption Standard

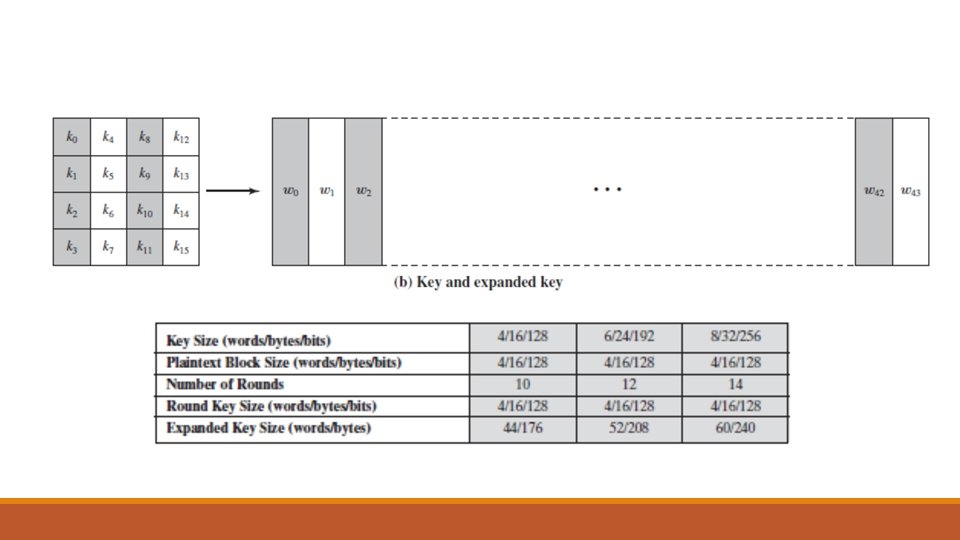
Origins • NIST issued a call for new Advanced Encryption Standard in 1997, for an algorithm: o Security strength equal or better than 3 DES o Improved efficiency as compared to 3 DES • In addition to this general criteria, NIST specified that o AES must be a symmetric cipher o Block length of 128 -bits o Support for key length of 128, 192 and 256 bits • Finally on 2 October 2000, NIST officially announced Rijndael as new AES

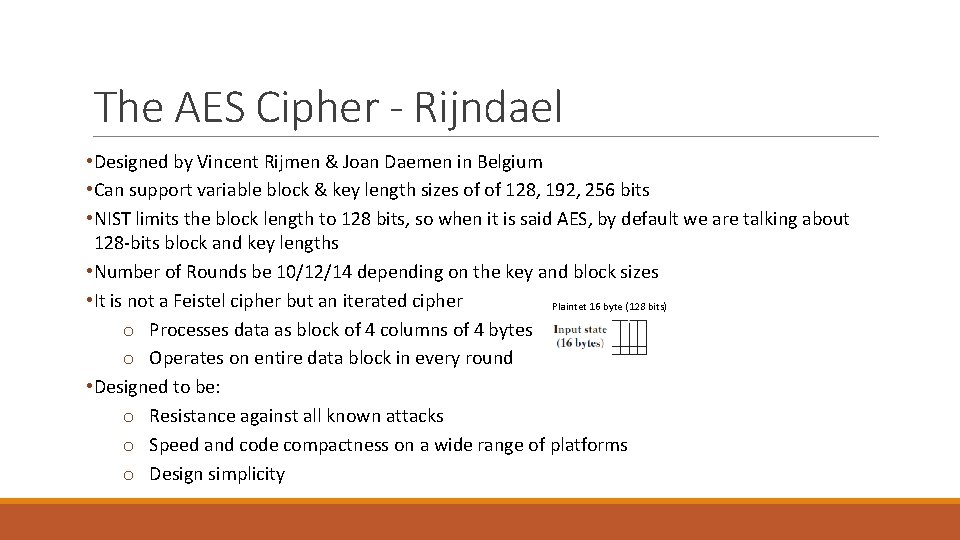
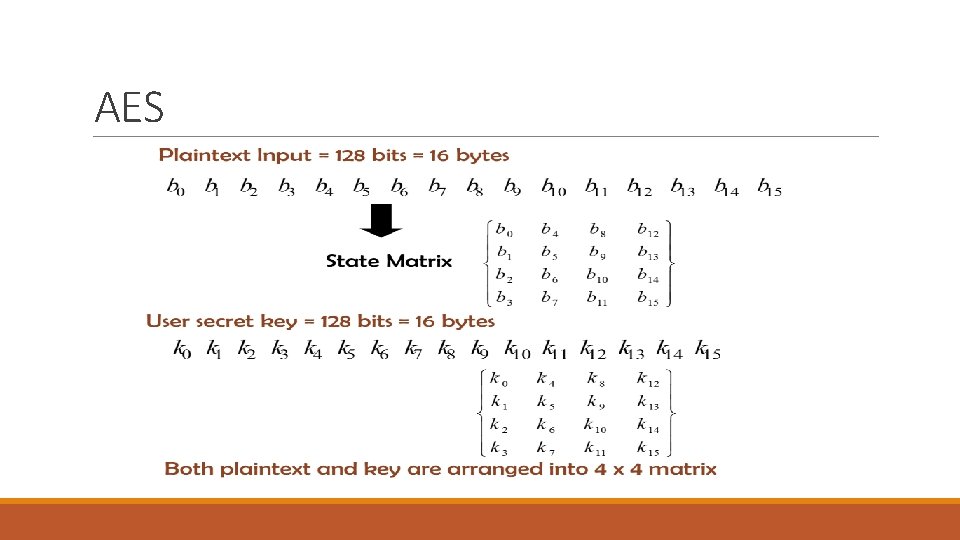
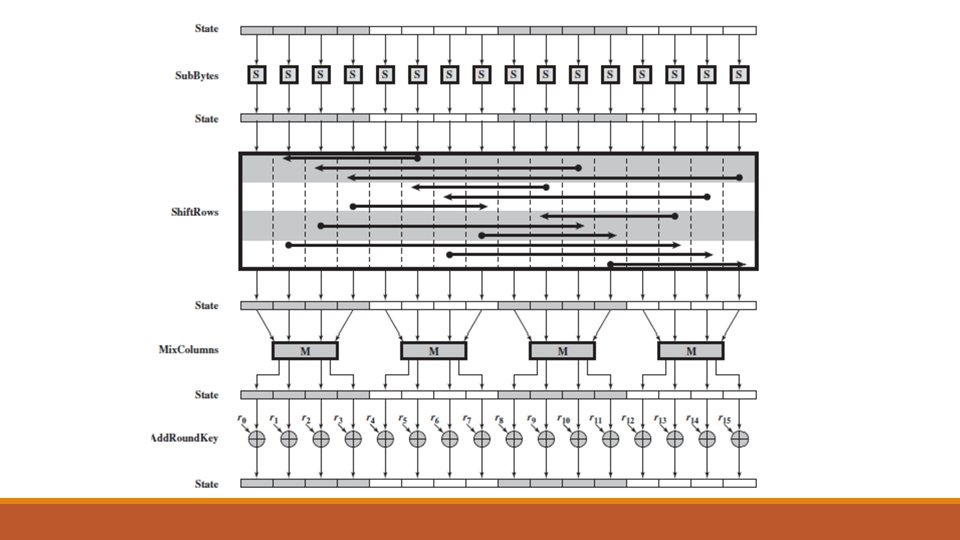
The AES Cipher - Rijndael • Designed by Vincent Rijmen & Joan Daemen in Belgium • Can support variable block & key length sizes of of 128, 192, 256 bits • NIST limits the block length to 128 bits, so when it is said AES, by default we are talking about 128 -bits block and key lengths • Number of Rounds be 10/12/14 depending on the key and block sizes • It is not a Feistel cipher but an iterated cipher Plaintet 16 byte (128 bits) o Processes data as block of 4 columns of 4 bytes o Operates on entire data block in every round • Designed to be: o Resistance against all known attacks o Speed and code compactness on a wide range of platforms o Design simplicity

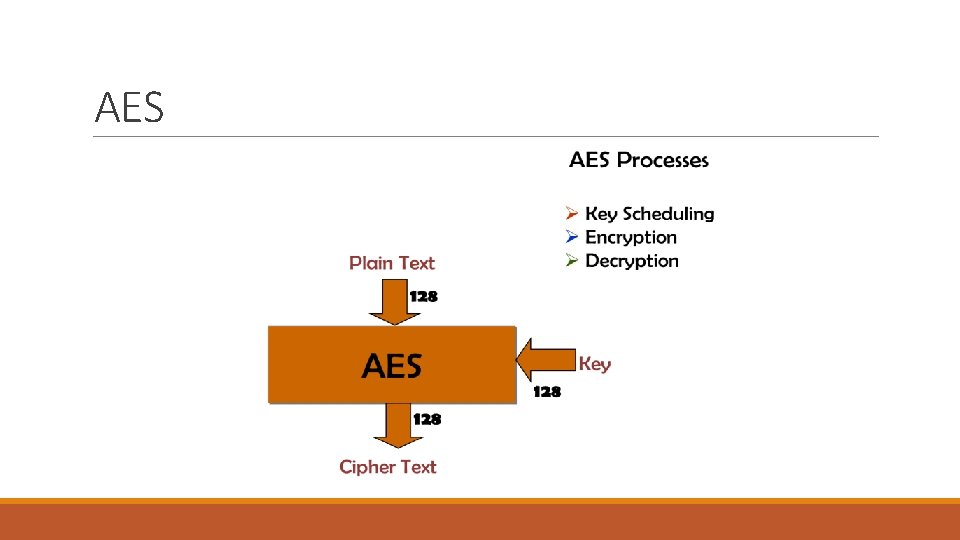
AES

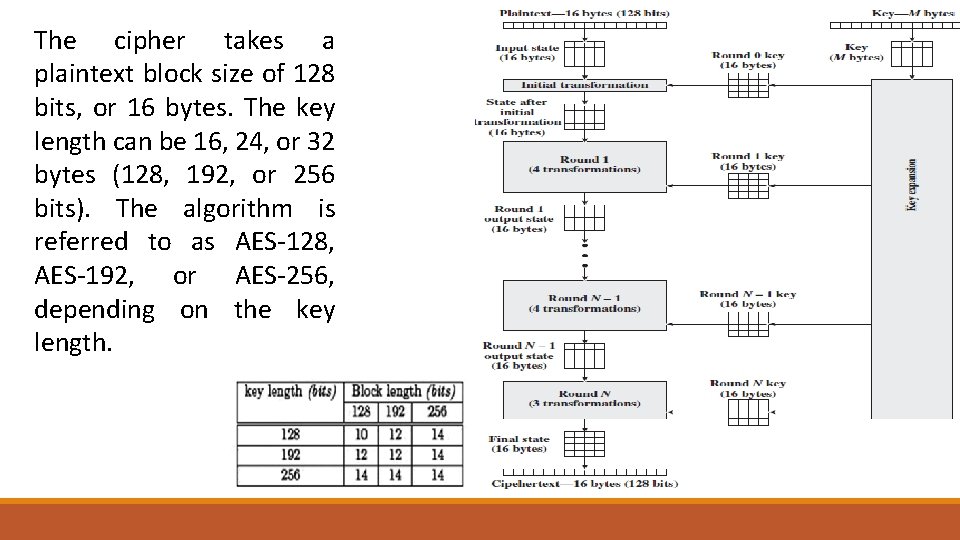
The cipher takes a plaintext block size of 128 bits, or 16 bytes. The key length can be 16, 24, or 32 bytes (128, 192, or 256 bits). The algorithm is referred to as AES-128, AES-192, or AES-256, depending on the key length.


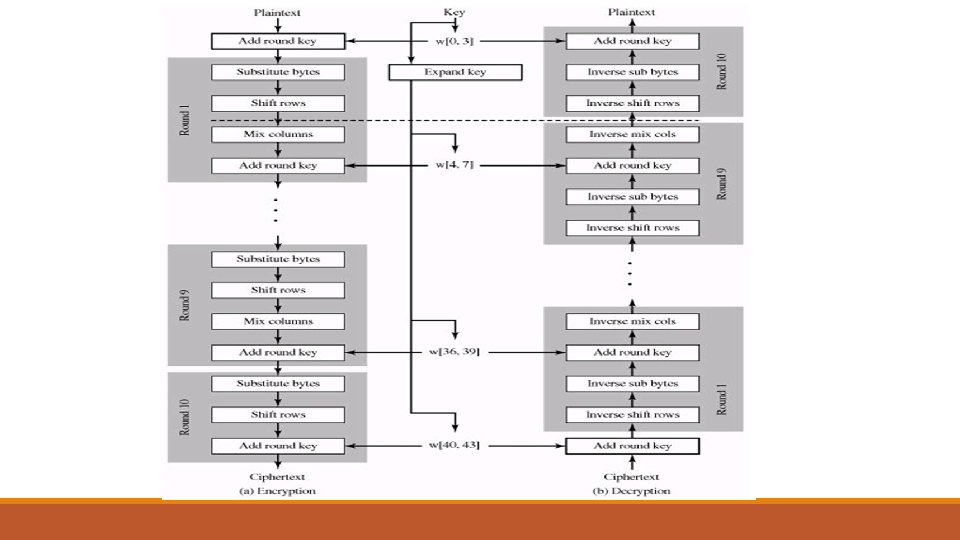
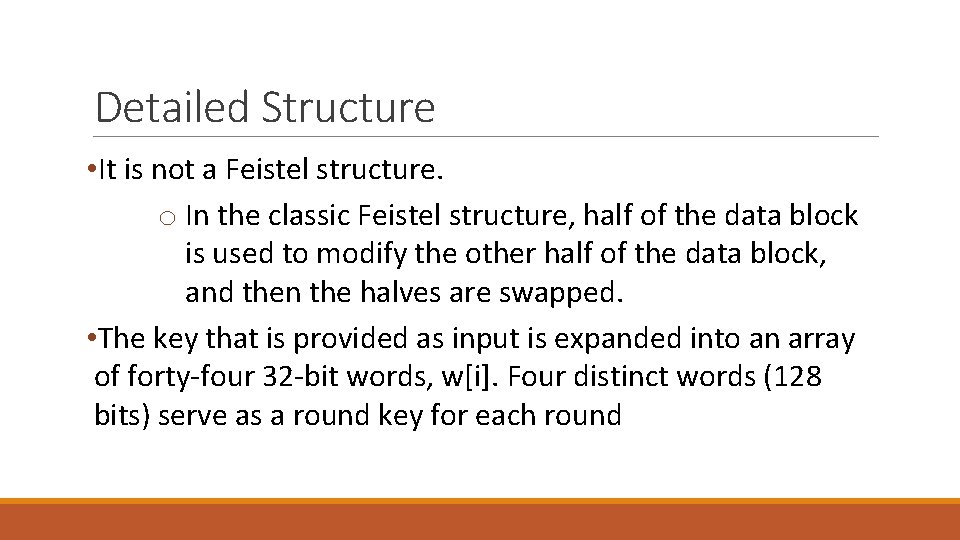
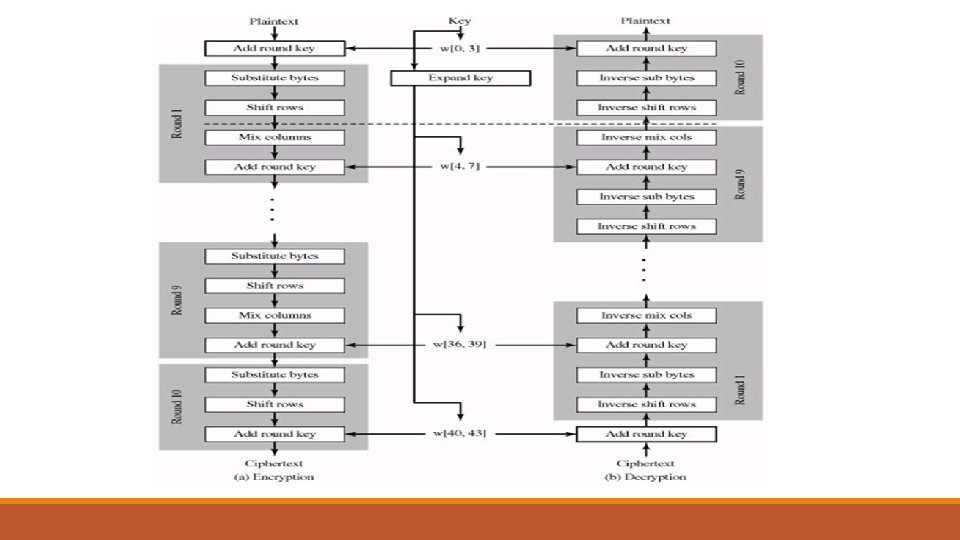
Detailed Structure • It is not a Feistel structure. o In the classic Feistel structure, half of the data block is used to modify the other half of the data block, and then the halves are swapped. • The key that is provided as input is expanded into an array of forty-four 32 -bit words, w[i]. Four distinct words (128 bits) serve as a round key for each round


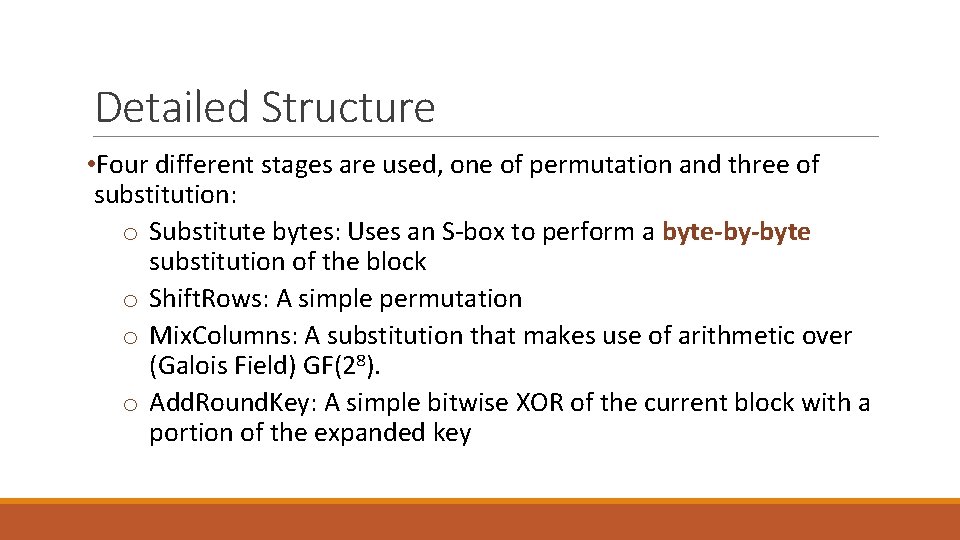
Detailed Structure • Four different stages are used, one of permutation and three of substitution: o Substitute bytes: Uses an S-box to perform a byte-by-byte substitution of the block o Shift. Rows: A simple permutation o Mix. Columns: A substitution that makes use of arithmetic over (Galois Field) GF(28). o Add. Round. Key: A simple bitwise XOR of the current block with a portion of the expanded key

AES

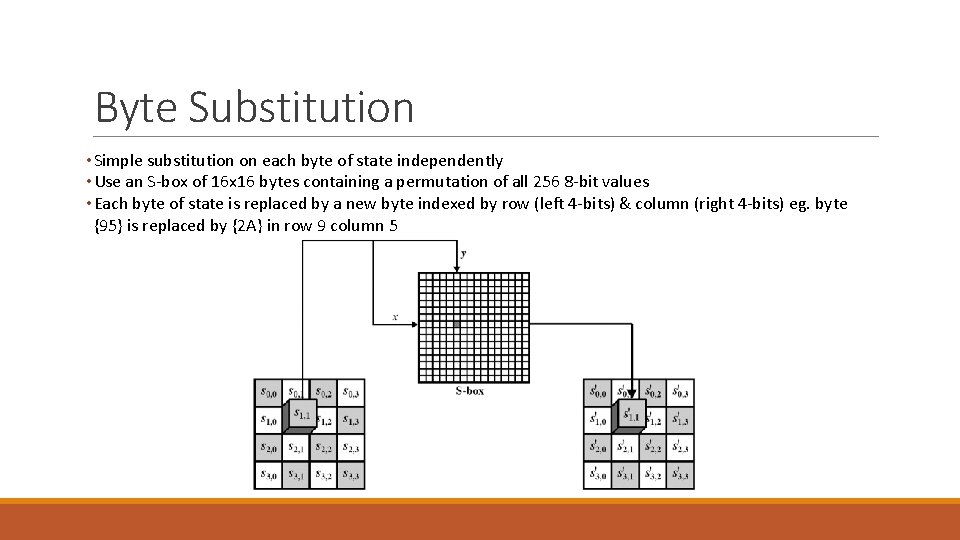
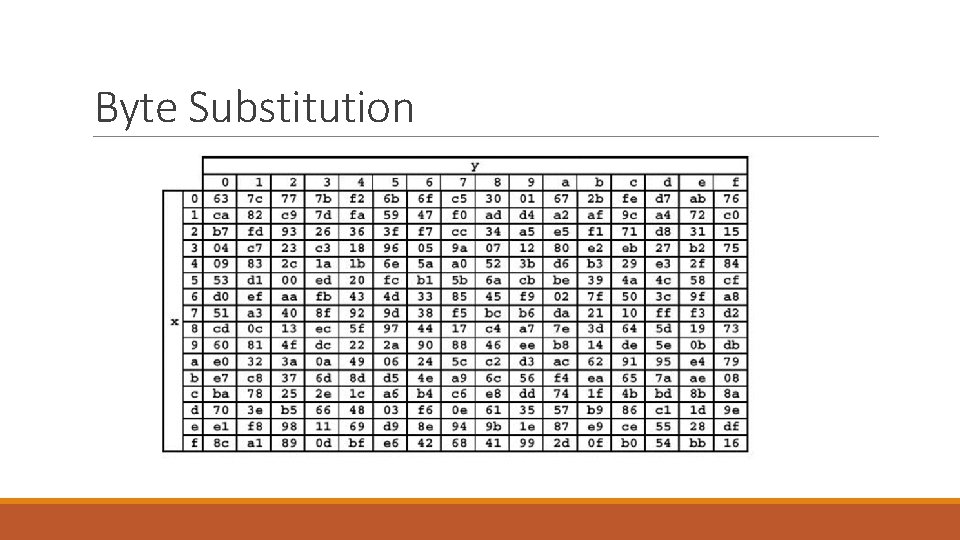
Byte Substitution • Simple substitution on each byte of state independently • Use an S-box of 16 x 16 bytes containing a permutation of all 256 8 -bit values • Each byte of state is replaced by a new byte indexed by row (left 4 -bits) & column (right 4 -bits) eg. byte {95} is replaced by {2 A} in row 9 column 5

Byte Substitution

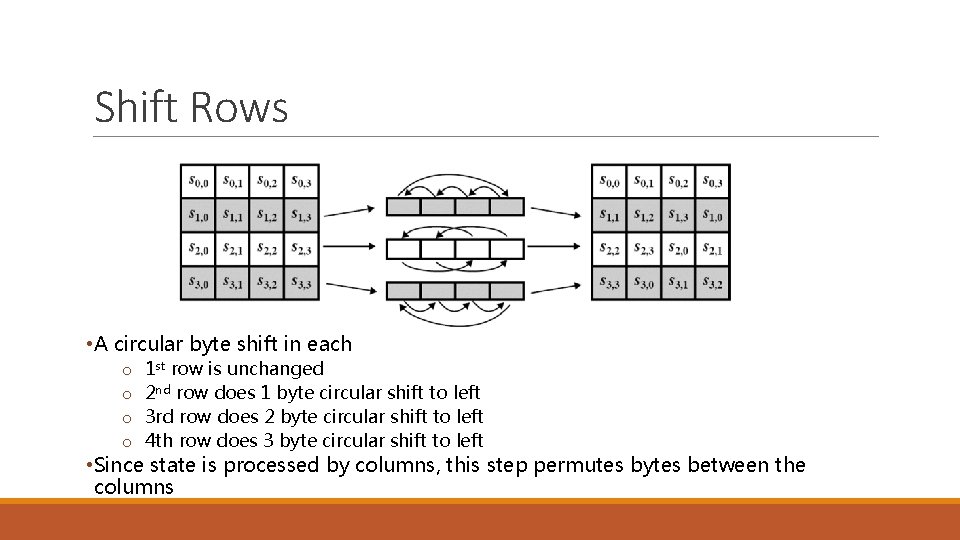
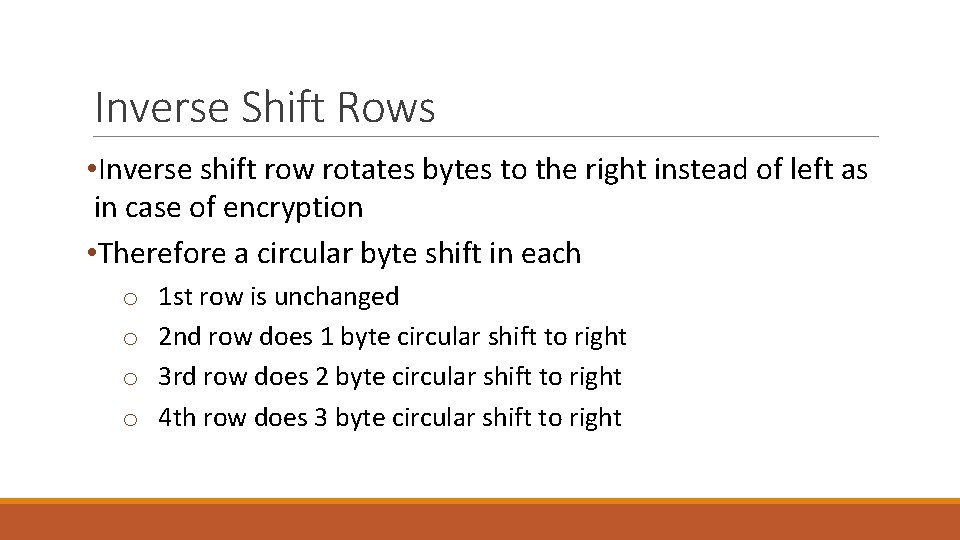
Shift Rows • A circular byte shift in each o o 1 st row is unchanged 2 nd row does 1 byte circular shift to left 3 rd row does 2 byte circular shift to left 4 th row does 3 byte circular shift to left • Since state is processed by columns, this step permutes bytes between the columns

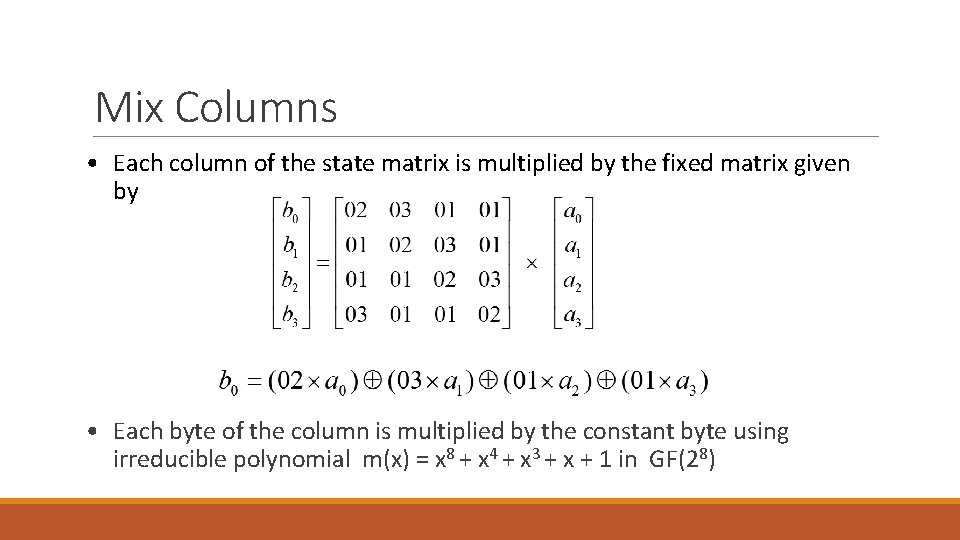
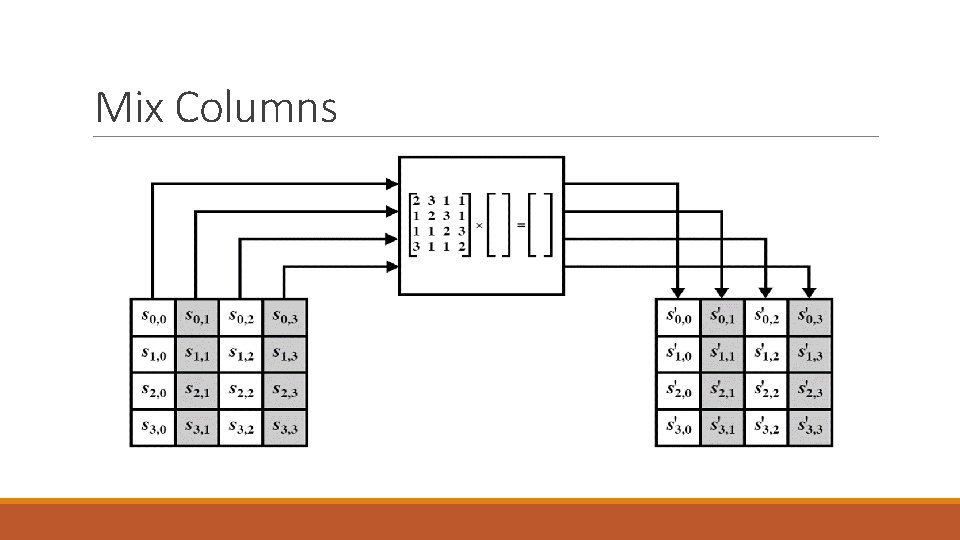
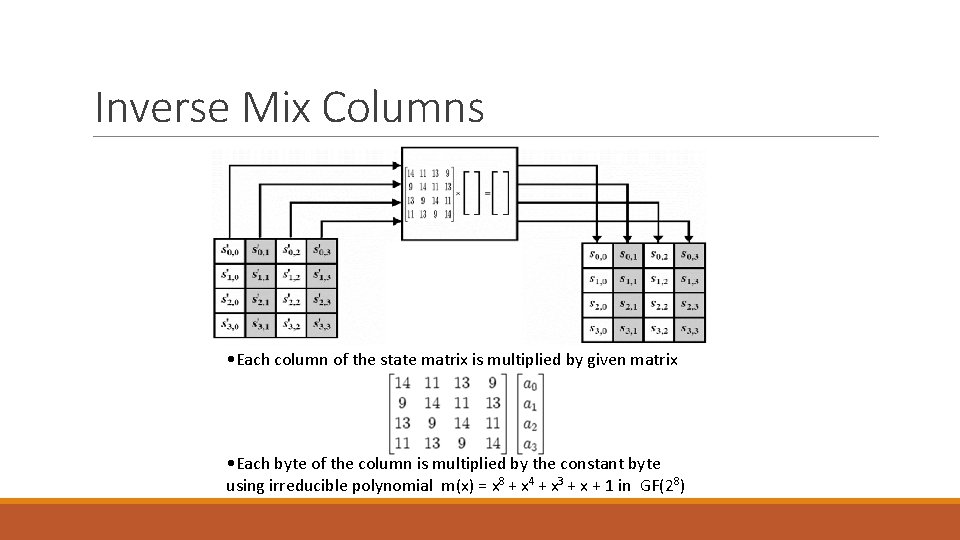
Mix Columns • Each column of the state matrix is multiplied by the fixed matrix given by • Each byte of the column is multiplied by the constant byte using irreducible polynomial m(x) = x 8 + x 4 + x 3 + x + 1 in GF(28)

Mix Columns

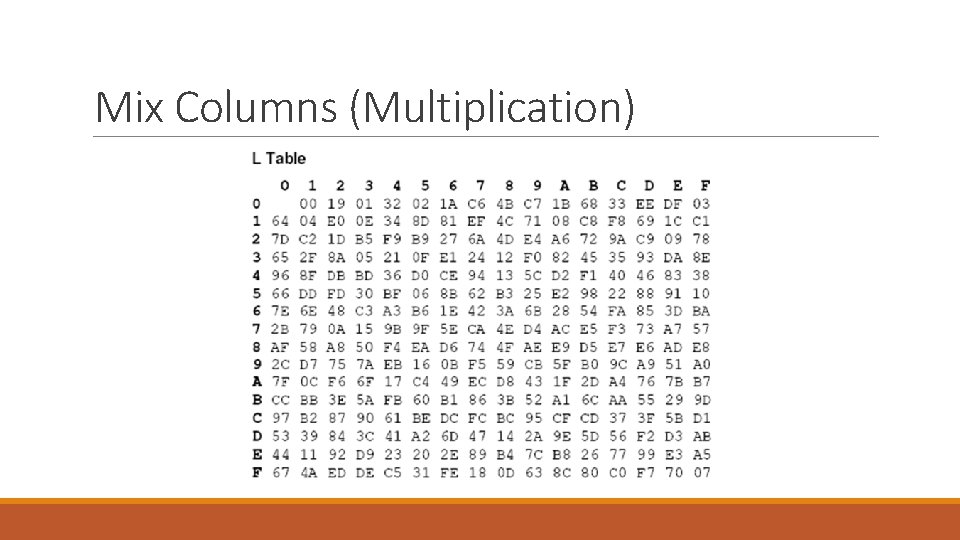
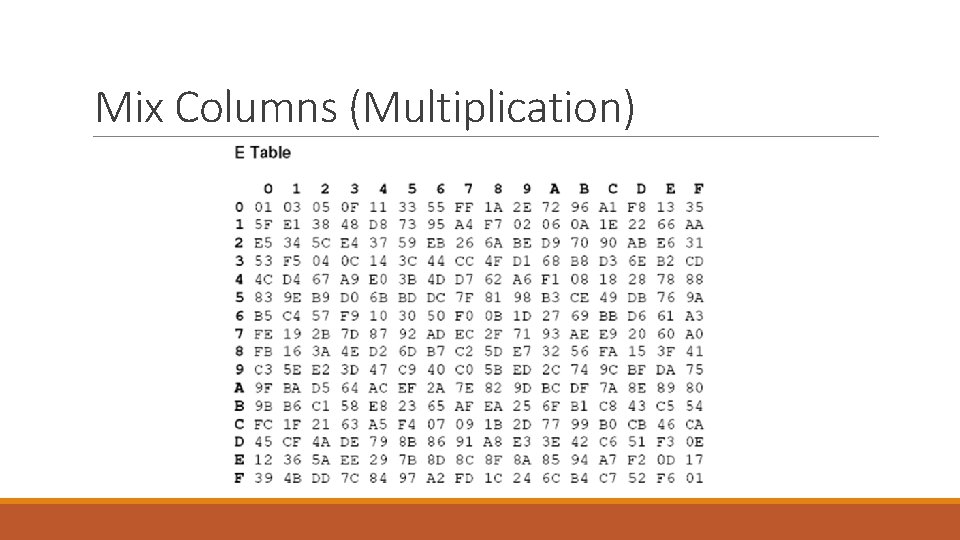
Mix Columns (Multiplication) • Following are the steps to follow in order to use L and E lookup table for GF multiplication – The result of the multiplication is simply the result of a lookup of the L table, followed by the addition of the results in base 16, followed by a lookup to the E table. – If the result of addition is greater then FF then simply subtract FF from result. – use the first digit in the number on the vertical index and the second number on the horizontal index. – If the value being multiplied is composed of only one digit then use 0 on the vertical index. • Two exceptions are that: – Any number multiplied by one is equal to its self and does not need to go through the above procedure. For example: FF * 1 = FF – Any number multiplied by zero equals zero

Mix Columns (Multiplication)

Mix Columns (Multiplication)

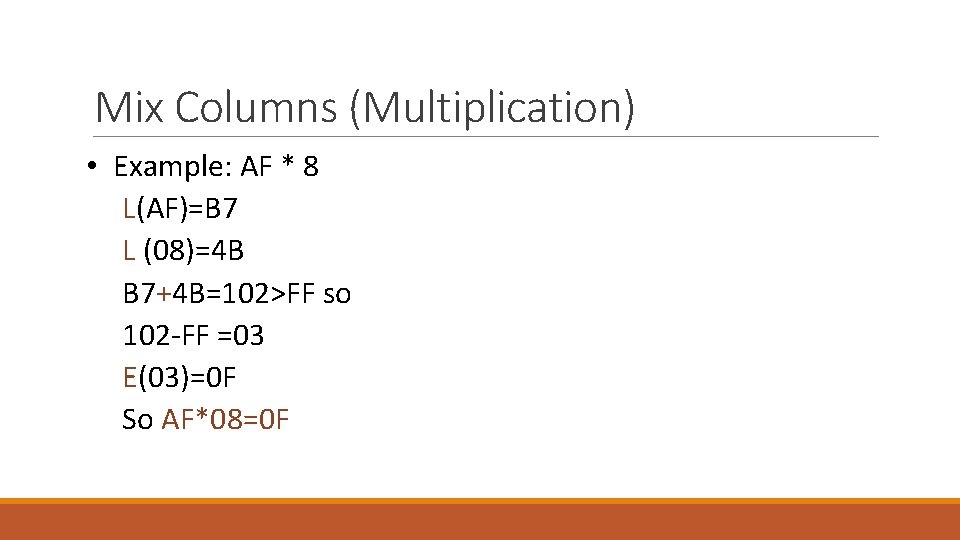
Mix Columns (Multiplication) • Example: AF * 8 L(AF)=B 7 L (08)=4 B B 7+4 B=102>FF so 102 -FF =03 E(03)=0 F So AF*08=0 F

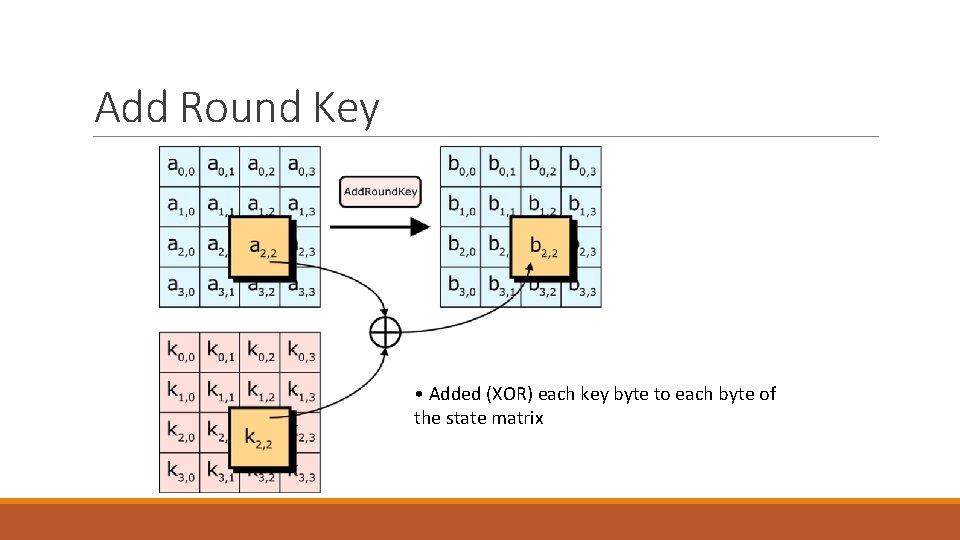
Add Round Key • Added (XOR) each key byte to each byte of the state matrix


AES Decryption

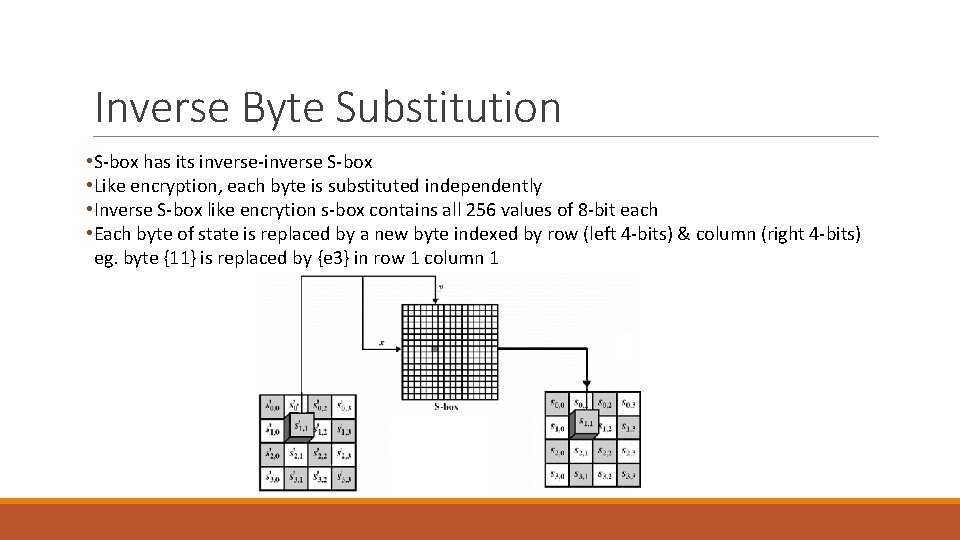
Inverse Byte Substitution • S-box has its inverse-inverse S-box • Like encryption, each byte is substituted independently • Inverse S-box like encrytion s-box contains all 256 values of 8 -bit each • Each byte of state is replaced by a new byte indexed by row (left 4 -bits) & column (right 4 -bits) eg. byte {11} is replaced by {e 3} in row 1 column 1

Inverse S-Box

Inverse Shift Rows • Inverse shift row rotates bytes to the right instead of left as in case of encryption • Therefore a circular byte shift in each o o 1 st row is unchanged 2 nd row does 1 byte circular shift to right 3 rd row does 2 byte circular shift to right 4 th row does 3 byte circular shift to right

Inverse Mix Columns • Each column of the state matrix is multiplied by given matrix • Each byte of the column is multiplied by the constant byte using irreducible polynomial m(x) = x 8 + x 4 + x 3 + x + 1 in GF(28)

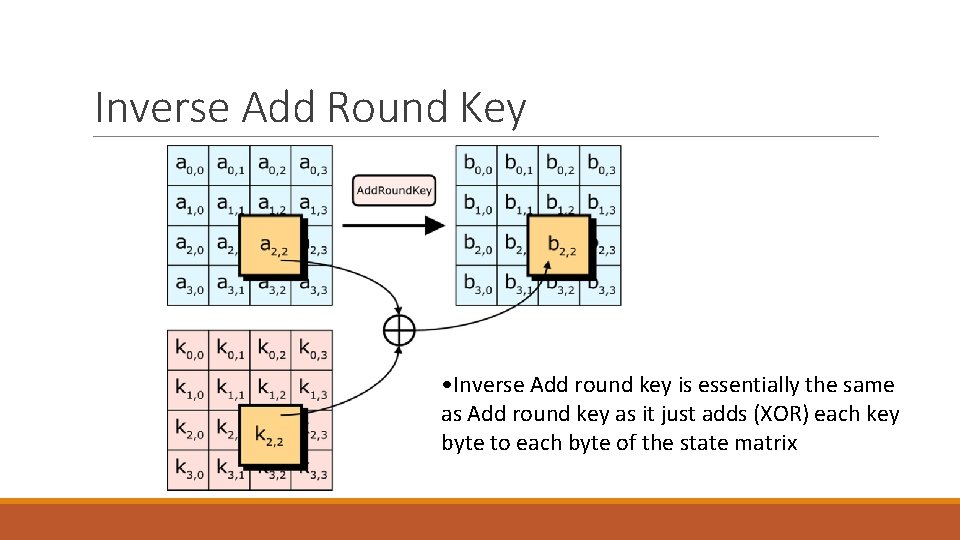
Inverse Add Round Key • Inverse Add round key is essentially the same as Add round key as it just adds (XOR) each key byte to each byte of the state matrix


AES: Key Expansion

AES Key Expansion • Takes 128 -bit (16 -byte; 4 -word) key and expands into array of 44 , 32 -bit words. • Start by copying key into first 4 words • Then loop creating words that depend on values in previous & 4 places back o In 3 of 4 cases just XOR these together o 1 st word in 4 has rotate + S-box + XOR round constant on previous, before XOR 4 th back
![Each added word wi depends on the immediately preceding word wi 1 • Each added word w[i] depends on the immediately preceding word, w[i- 1],](https://slidetodoc.com/presentation_image_h2/4da9e9efc052144569669ed6a0f4371b/image-32.jpg)
• Each added word w[i] depends on the immediately preceding word, w[i- 1], and the word four positions back, w[i-4]. • In three out of four cases, a simple XOR is used. • For a word whose position in the w array is a multiple of 4, a more complex function g is used

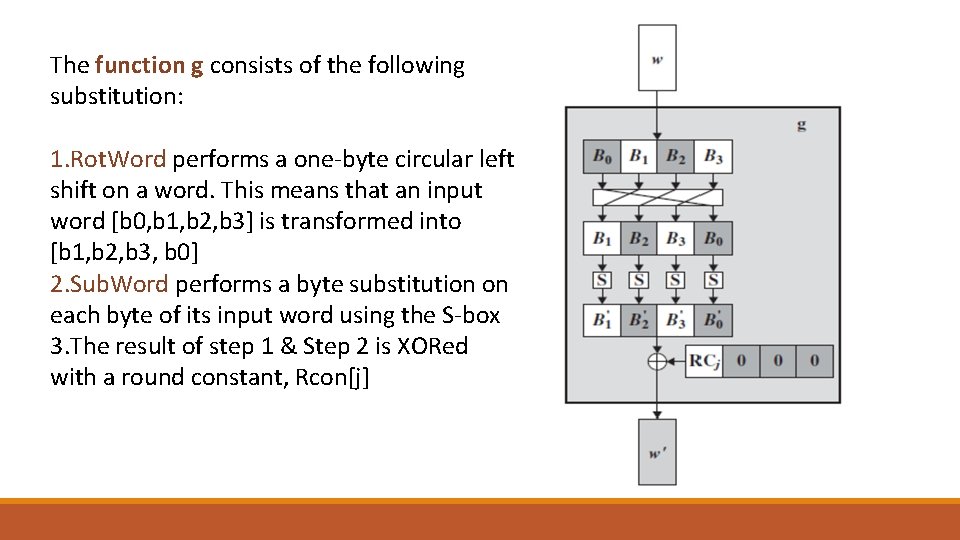
The function g consists of the following substitution: 1. Rot. Word performs a one-byte circular left shift on a word. This means that an input word [b 0, b 1, b 2, b 3] is transformed into [b 1, b 2, b 3, b 0] 2. Sub. Word performs a byte substitution on each byte of its input word using the S-box 3. The result of step 1 & Step 2 is XORed with a round constant, Rcon[j]

Round Constant • The round constant is a word in which the three rightmost bytes are always 0. • Thus, the effect of an XOR of a word with Rcon is to only perform an XOR on the leftmost byte of the word. • The round constant is different for each round, the values of RC[j] in hexadecimal are:

Key Expansion Rationale • The Rijndael developers designed the expansion key algorithm to be resistant to known cryptanalytic attacks. • Design criteria included: o. The inclusion of round constant eliminates the symmetry, or similarity, between the ways in which round keys are generated in different rounds. o. Knowledge of a part of the cipher key or round key does not enable calculation of many other round-key bits. o. Fast on wide range of CPU’s o. Simplicity of description

Reading “Cryptography and Network Security Principles and Practices”, Fourth Edition by William Stallings Chapter 5