Advanced Ajax Security Billy Hoffman billy hoffmanhp com

Advanced Ajax Security Billy Hoffman (billy. hoffman@hp. com) Manager, HP Security Labs © 2007 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice

Who am I? • Manager HP Security Labs • In security space for 6 years CS Degree from Georgia Tech • Areas of focus • − Crawling and sampling − Java. Script static analysis − XSS • Frequent presenter at hacker/security conferences 2

Presentation Overview • Manipulating Client-side logic • Defeating logic protection techniques Function Hijacking • JSON Hijacking • Hacking Google Gears • 3 9/25/2021
“Boring” Ajax Security • Increased attack surface • Direct API access Easier to reverse engineer • Amplifying web attacks • Offline attacks • • 4 “Surely no one actually does this right? ” 9/25/2021
Sexy Ajax Security Sample Ajax travel website • Built using “expert” advice • − Popular books − Articles/How-tos − Forums • 5 Riddled with security defects 9/25/2021
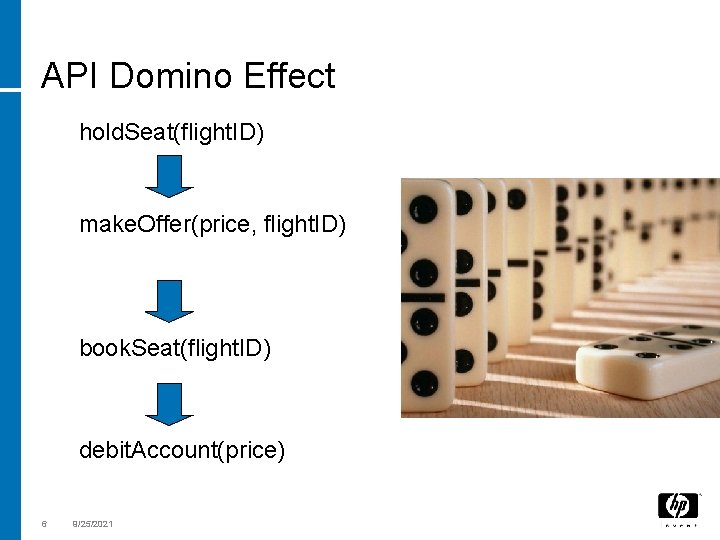
API Domino Effect hold. Seat(flight. ID) make. Offer(price, flight. ID) book. Seat(flight. ID) debit. Account(price) 6 9/25/2021
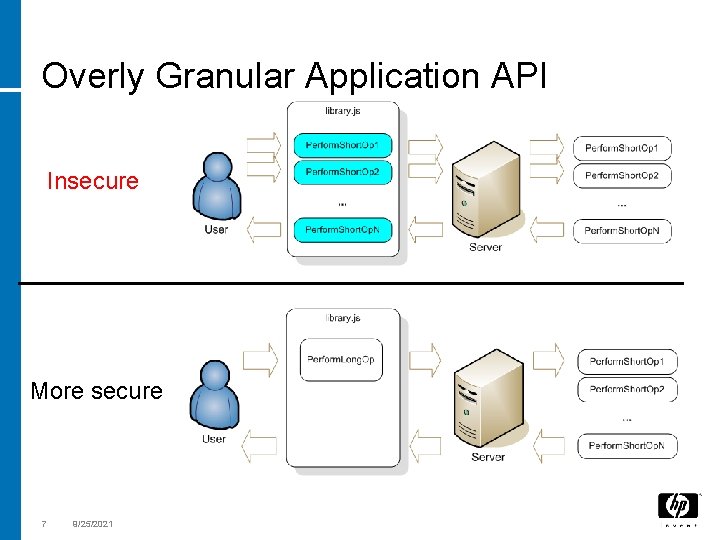
Overly Granular Application API Insecure More secure 7 9/25/2021
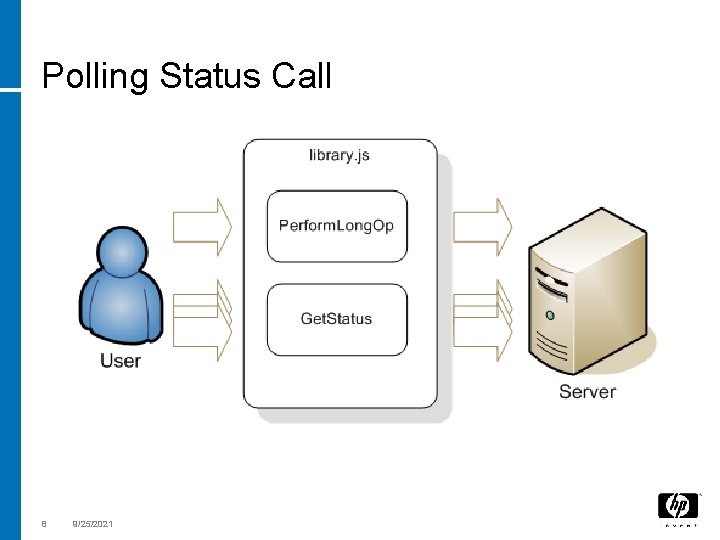
Polling Status Call 8 9/25/2021
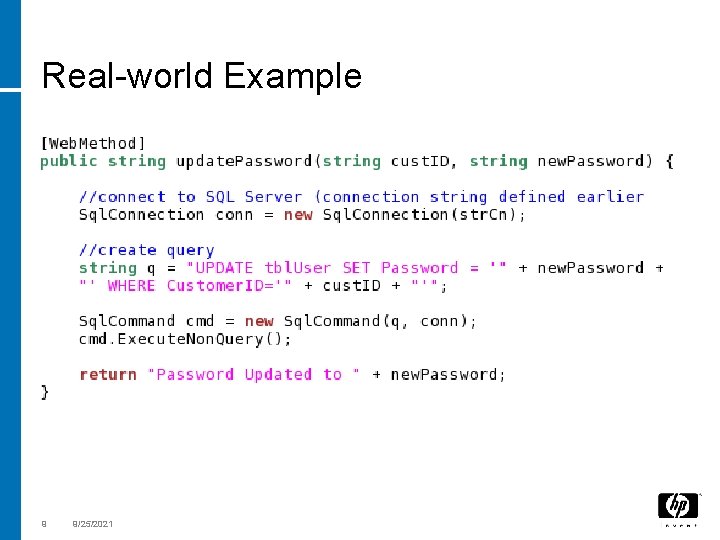
Real-world Example 9 9/25/2021
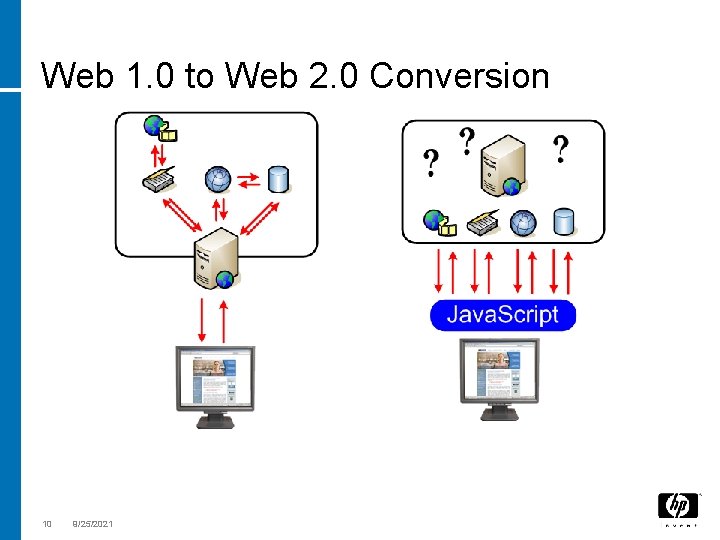
Web 1. 0 to Web 2. 0 Conversion 10 9/25/2021

Premature Ajax-ulation! 11 9/25/2021
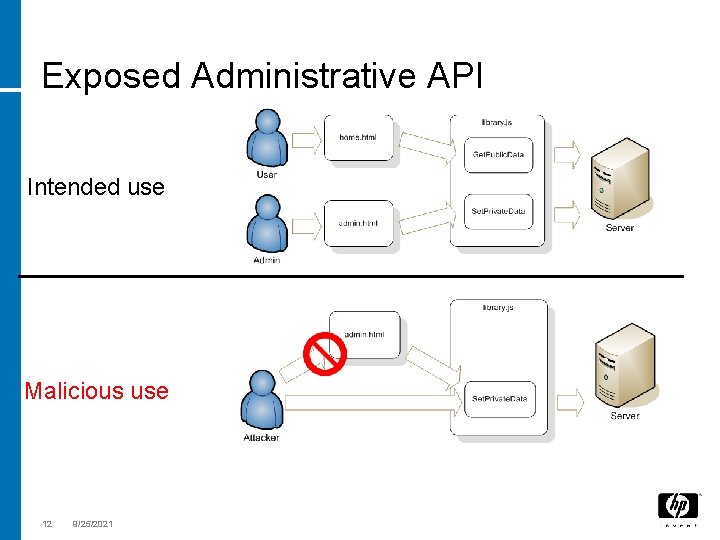
Exposed Administrative API Intended use Malicious use 12 9/25/2021

Defeating Logic Protection • Obfuscation • Lazy Loading 13 9/25/2021
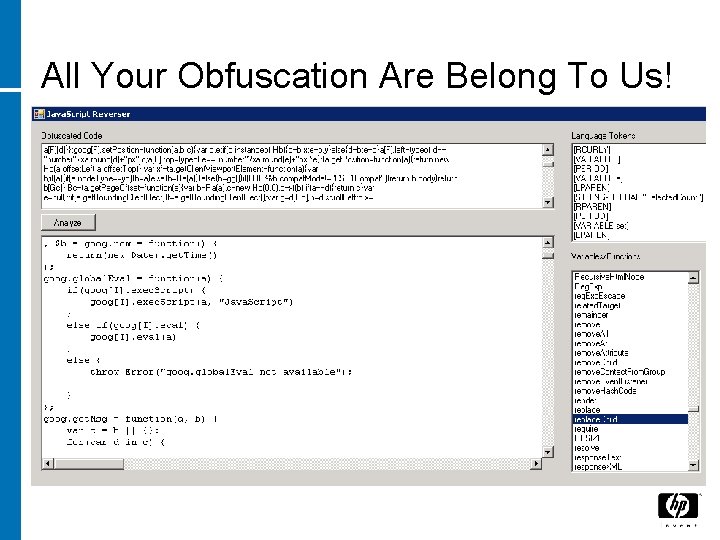
All Your Obfuscation Are Belong To Us!
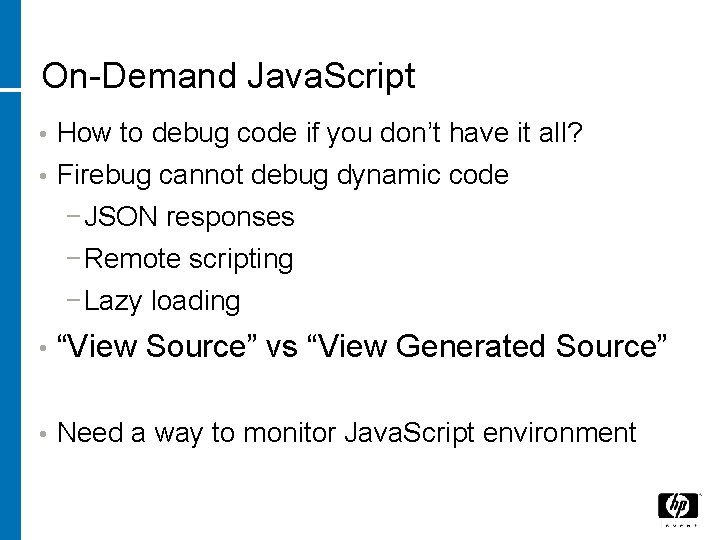
On-Demand Java. Script • How to debug code if you don’t have it all? • Firebug cannot debug dynamic code − JSON responses − Remote scripting − Lazy loading • “View Source” vs “View Generated Source” • Need a way to monitor Java. Script environment

Understanding Java. Script Variable Scope • Everything is a object − Primitives (Strings, numbers, regexp) − Functions • All global variables and functions are properties of global object • Provided by environment • Web browser = window • Can we enumerate?
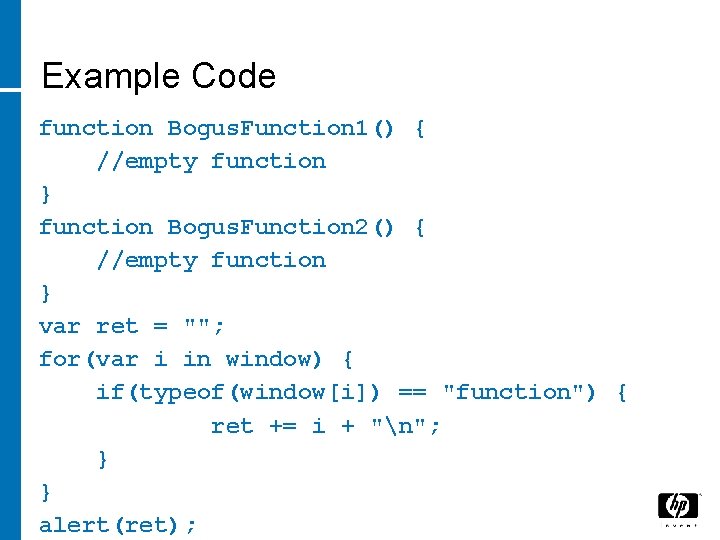
Example Code function Bogus. Function 1() { //empty function } function Bogus. Function 2() { //empty function } var ret = ""; for(var i in window) { if(typeof(window[i]) == "function") { ret += i + "n"; } } alert(ret);
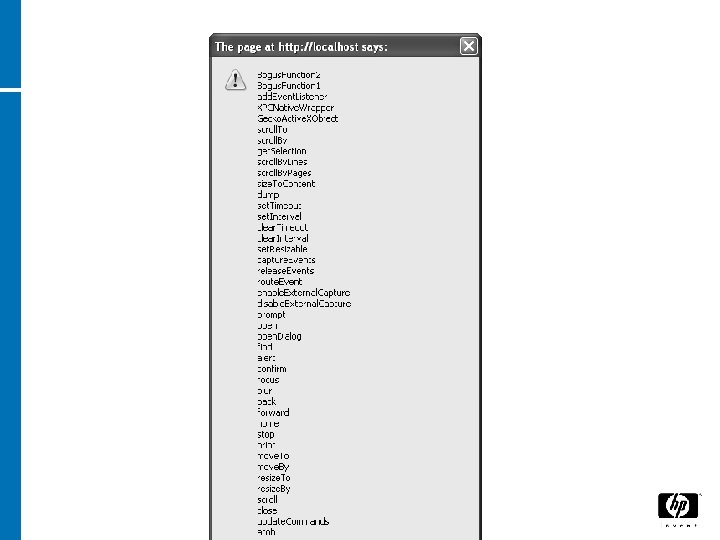
Enumerating All Functions

HOOK: Java. Script Monitoring Framework Enumerates the environment and traps ondemand code. • Side-steps obfuscation • Reads from the environment itself • • Demo

Take Aways: Client-side Code • Client-side code is just a suggestion! Client-side code cannot be protected, encrypted, or obfuscated • Store all secrets on the server • Enforce control flow on the server • Always match allocations with frees in the same method • • 20 Use Server-side locking to prevent race condition vulnerabilities 9/25/2021
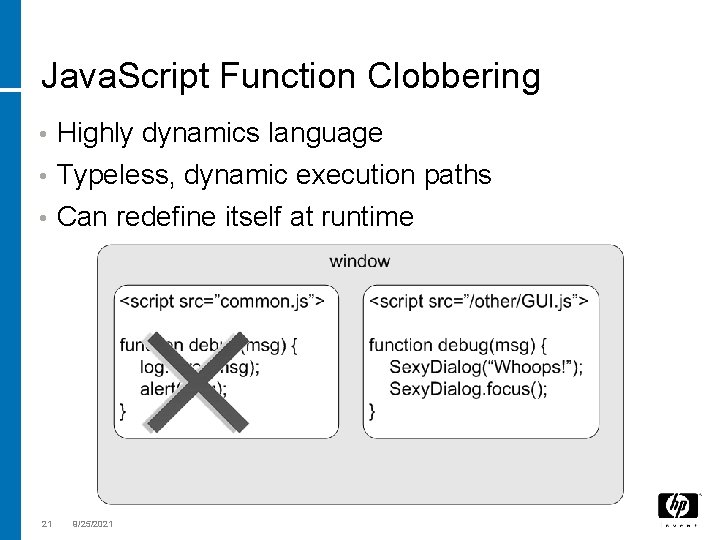
Java. Script Function Clobbering • Highly dynamics language • Typeless, dynamic execution paths • Can redefine itself at runtime 21 9/25/2021

Java. Script Namespaces • Namespaces prevent collisions • Solution: Make functions properties of objects var com. Some. Site. common = {}; com. Some. Site. common. debug = function () { … }; com. Some. Site. common. debug(); var com. Sexy. Widgets = {}; com. Sexy. Widgets. debug = function() {…}; com. Sexy. Widgets. debug();
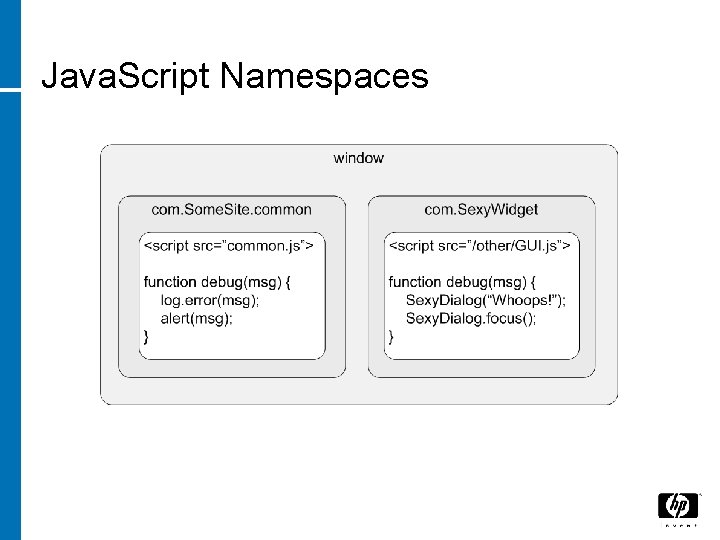
Java. Script Namespaces

Intentional Function Clobbering • Attacker deliberately clobbers functions • What kind of functions can you clobber? − User defined functions? − System functions? • Demo
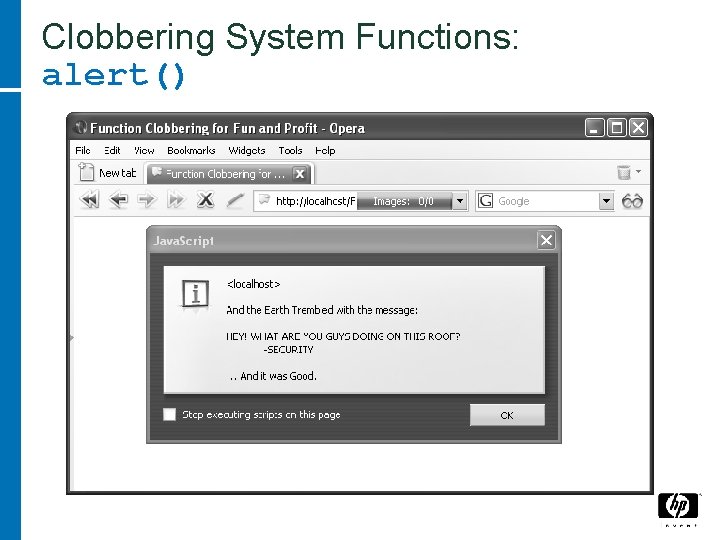
Clobbering System Functions: alert()
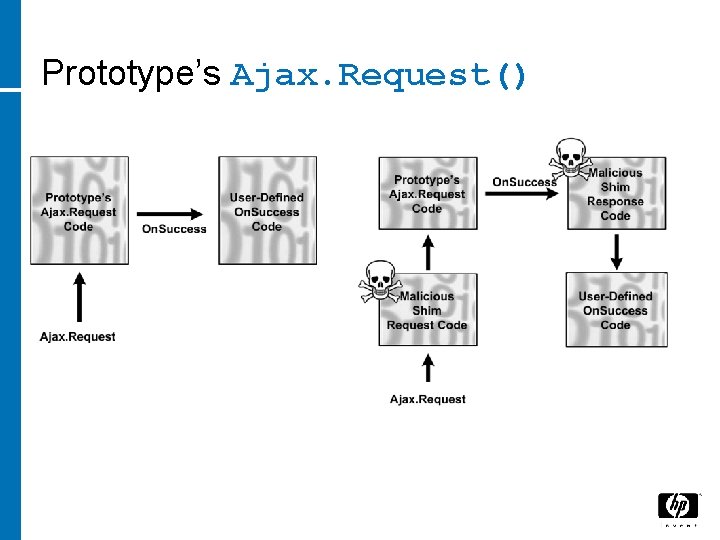
Prototype’s Ajax. Request()

Limitless Clobbering Possibilities • Can clobber anything • Automatic Man In The Middle • Other things − Dojo. Storage − Callback functions − Encryption functions?

The Myth of the Same Origin Policy Myth: Same Origin Restricts prevent Java. Script from seeing 3 rd party content • Fact: Kind of prevents • − Remote Scripting − Image and Iframe events (Java. Script port scanning) − 3 rd party plug-in communications

JSON Hijacking JSON is a valid subset of Java. Script • eval() can be used to “see” the response • • 29 Could use remoting scripting to read JSON web services? 9/25/2021
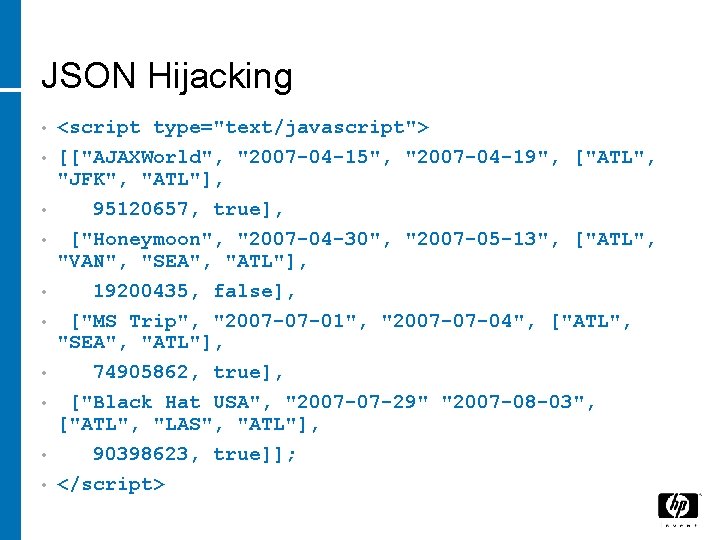
JSON Hijacking • • • <script type="text/javascript"> [["AJAXWorld", "2007 -04 -15", "2007 -04 -19", ["ATL", "JFK", "ATL"], 95120657, true], ["Honeymoon", "2007 -04 -30", "2007 -05 -13", ["ATL", "VAN", "SEA", "ATL"], 19200435, false], ["MS Trip", "2007 -07 -01", "2007 -07 -04", ["ATL", "SEA", "ATL"], 74905862, true], ["Black Hat USA", "2007 -07 -29" "2007 -08 -03", ["ATL", "LAS", "ATL"], 90398623, true]]; </script>

JSON Hijacking • How does JS interpreter handle literals? [9, 4, 3, 1, 33, 7, 2]. sort(); Creates temporary Array object • Executed sort() function • Never assigned to variable • Garbage collected away •

JSON Hijacking • How does JS interpreter handle literals? [9, 4, 3, 1, 33, 7, 2]. sort(); • Creates temporary Array object − Invokes Array() constructor function • Executed sort() function Never assigned to variable • Garbage collected away •
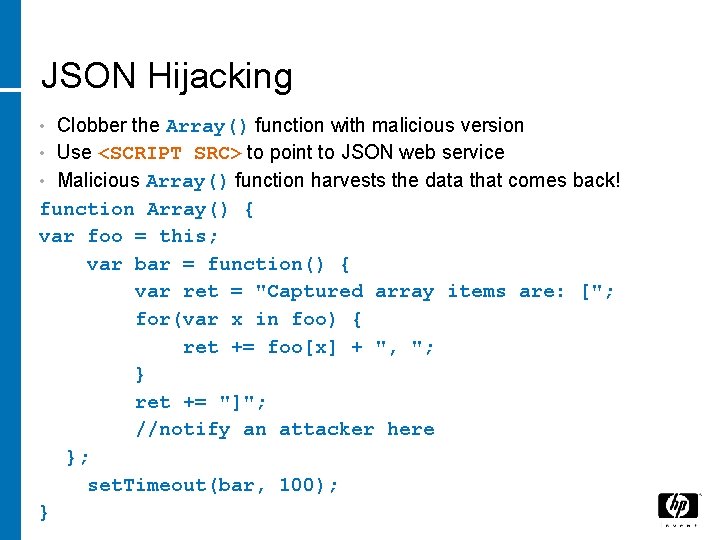
JSON Hijacking Clobber the Array() function with malicious version • Use <SCRIPT SRC> to point to JSON web service • Malicious Array() function harvests the data that comes back! function Array() { var foo = this; var bar = function() { var ret = "Captured array items are: ["; for(var x in foo) { ret += foo[x] + ", "; } ret += "]"; //notify an attacker here }; set. Timeout(bar, 100); } •
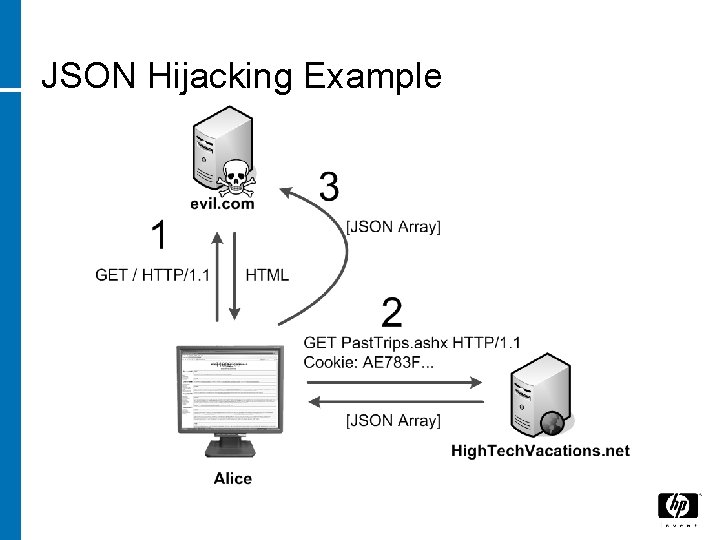
JSON Hijacking Example
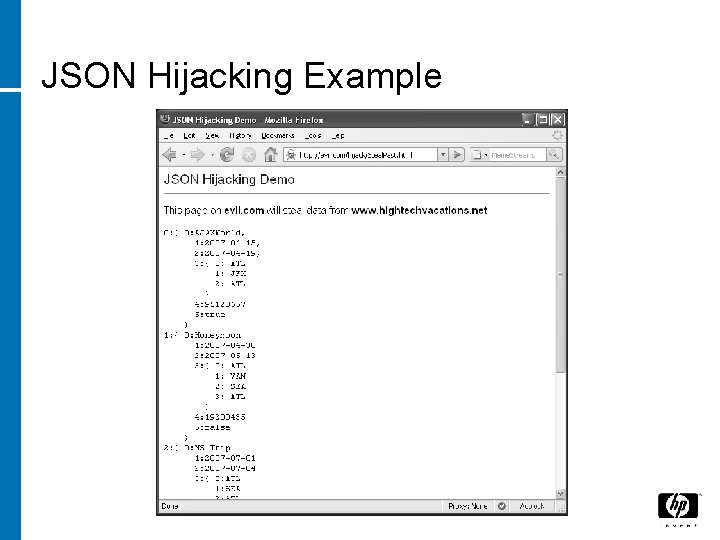
JSON Hijacking Example

JSON Hijacking Defense • XMLHttp. Request can see the response and perform operations on it before eval()ing <SCRIPT SRC> cannot! • Make the JSON response non-valid Java. Script • XHR removes it! • <SCRIPT SRC> fails! •
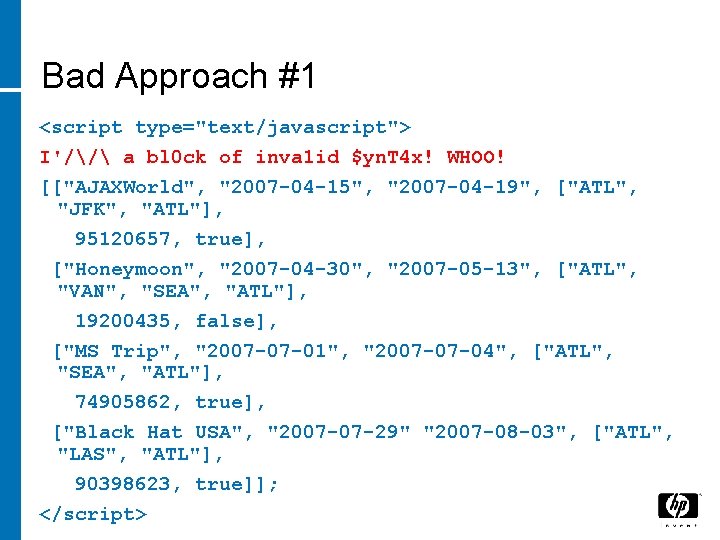
Bad Approach #1 <script type="text/javascript"> I'// a bl 0 ck of inva 1 id $yn. T 4 x! WHOO! [["AJAXWorld", "2007 -04 -15", "2007 -04 -19", ["ATL", "JFK", "ATL"], 95120657, true], ["Honeymoon", "2007 -04 -30", "2007 -05 -13", ["ATL", "VAN", "SEA", "ATL"], 19200435, false], ["MS Trip", "2007 -07 -01", "2007 -07 -04", ["ATL", "SEA", "ATL"], 74905862, true], ["Black Hat USA", "2007 -07 -29" "2007 -08 -03", ["ATL", "LAS", "ATL"], 90398623, true]]; </script>
![Bad Approch #2 <script type="text/javascript"> /* ["Eve", "Jill", "Mary", "Jen", "Ashley", "Nidhi"] */ </script> Bad Approch #2 <script type="text/javascript"> /* ["Eve", "Jill", "Mary", "Jen", "Ashley", "Nidhi"] */ </script>](http://slidetodoc.com/presentation_image_h2/c1bf144c4fe9ce37060609add6ceb12e/image-38.jpg)
Bad Approch #2 <script type="text/javascript"> /* ["Eve", "Jill", "Mary", "Jen", "Ashley", "Nidhi"] */ </script>
![Bad Approach #2 <script type="text/javascript"> /* ["Eve*/["bogus", "Jill", "Mary", "Jen", "Ashley", "bogus"]/*Nidhi"] */ </script> Bad Approach #2 <script type="text/javascript"> /* ["Eve*/["bogus", "Jill", "Mary", "Jen", "Ashley", "bogus"]/*Nidhi"] */ </script>](http://slidetodoc.com/presentation_image_h2/c1bf144c4fe9ce37060609add6ceb12e/image-39.jpg)
Bad Approach #2 <script type="text/javascript"> /* ["Eve*/["bogus", "Jill", "Mary", "Jen", "Ashley", "bogus"]/*Nidhi"] */ </script>
![Correct Approach <script type="text/javascript"> for(; ; ); ["Eve", "Jill", "Mary", "Jen", "Ashley", "Nidhi"] </script> Correct Approach <script type="text/javascript"> for(; ; ); ["Eve", "Jill", "Mary", "Jen", "Ashley", "Nidhi"] </script>](http://slidetodoc.com/presentation_image_h2/c1bf144c4fe9ce37060609add6ceb12e/image-40.jpg)
Correct Approach <script type="text/javascript"> for(; ; ); ["Eve", "Jill", "Mary", "Jen", "Ashley", "Nidhi"] </script>

Correct Approach function defang. JSON(json) { if(json. substring(0, 8) == "for(; ; ); ") { json = json. substring(8); } Return json; } var safe. JSONString = defang. JSON(xhr. response. Text); var json. Object = safe. JSONString. parse. JSON();

Securing Ajax Applications Perform authentication/authorization checks on both web pages and web services • Group code libraries by function • Validate all input for your application • − HTTP headers, cookies, query string, POST data • Verify data type, length and format Always use parameterized queries • Always encoded output appropriately • 42 9/25/2021

Salvation Is Here! • Ajax Security Addison-Wesley "Ajax Security is a remarkably rigorous and thorough examination of an underexplored subject. Every Ajax engineer needs to have the knowledge contained in this book or be able to explain why they don't. ” -Jesse James Garret • 43 In stores now! 9/25/2021

Advanced Ajax Security Billy Hoffman (billy. hoffman@hp. com) Manager, HP Security Labs © 2007 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice
- Slides: 44