Address Resolution Logic for NCTU TEL 03591 5708



















- Slides: 40

Address Resolution Logic (for NCTU) 呂國正 研院電通所高速網路部 TEL : (03)591 -5708 Email : lkc@n 300. ccl. itri. org. tw Confidential & Proprietary

Agenda • • • Position of ARL in L 3 S Chip Concept of IP Routing & Multi-Layer Switching Introduction to CIDR and Longest Prefix Matching ARL Architecture and I/O interface ARL Detailed Design Forwarding Table Management 2 Confidential & Proprietary

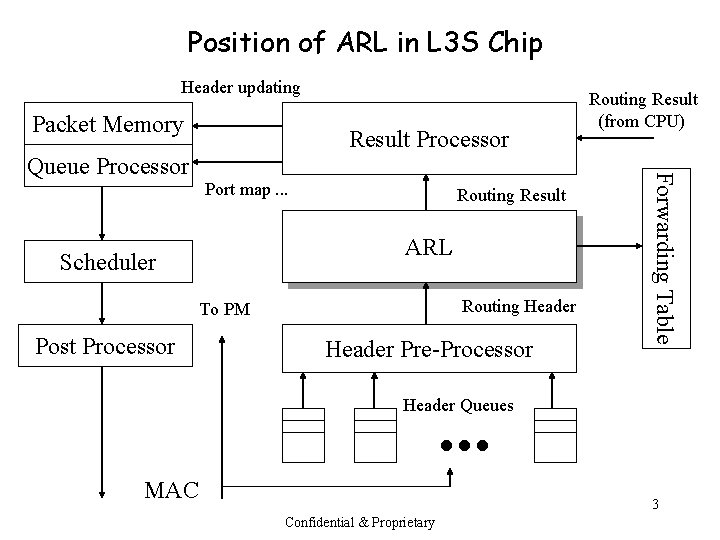
Position of ARL in L 3 S Chip Header updating Packet Memory Port map. . . Routing Result ARL Scheduler Routing Header To PM Post Processor Header Pre-Processor Forwarding Table Queue Processor Result Processor Routing Result (from CPU) . . . Header Queues MAC 3 Confidential & Proprietary

ARL Specification 4 Confidential & Proprietary

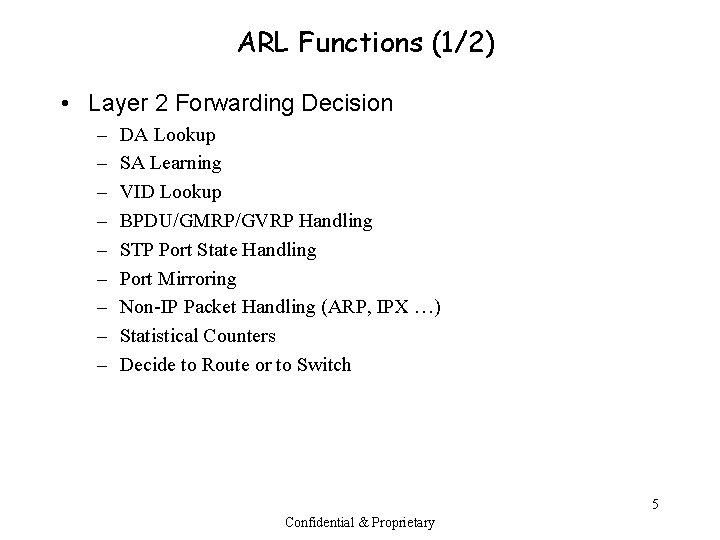
ARL Functions (1/2) • Layer 2 Forwarding Decision – – – – – DA Lookup SA Learning VID Lookup BPDU/GMRP/GVRP Handling STP Port State Handling Port Mirroring Non-IP Packet Handling (ARP, IPX …) Statistical Counters Decide to Route or to Switch 5 Confidential & Proprietary

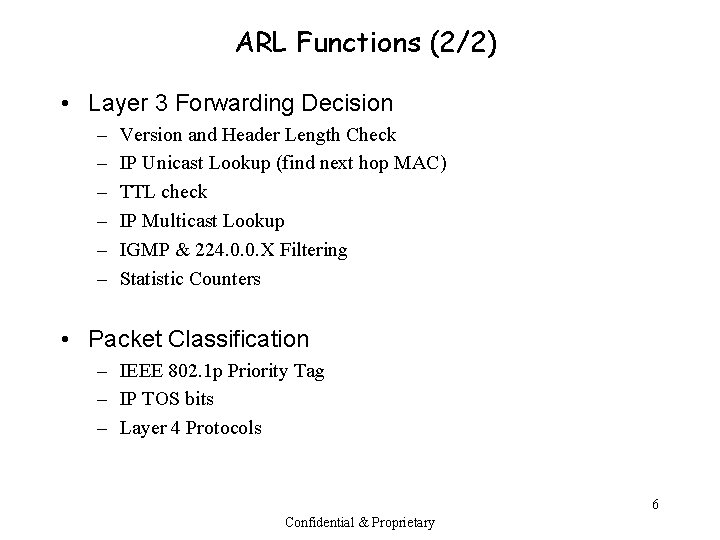
ARL Functions (2/2) • Layer 3 Forwarding Decision – – – Version and Header Length Check IP Unicast Lookup (find next hop MAC) TTL check IP Multicast Lookup IGMP & 224. 0. 0. X Filtering Statistic Counters • Packet Classification – IEEE 802. 1 p Priority Tag – IP TOS bits – Layer 4 Protocols 6 Confidential & Proprietary

Agenda • • • Position of ARL in L 3 S Chip Concept of IP Routing & Multi-Layer Switching Introduction to CIDR and Longest Prefix Matching ARL Architecture and I/O interface ARL Detailed Design Forwarding Table Management 7 Confidential & Proprietary

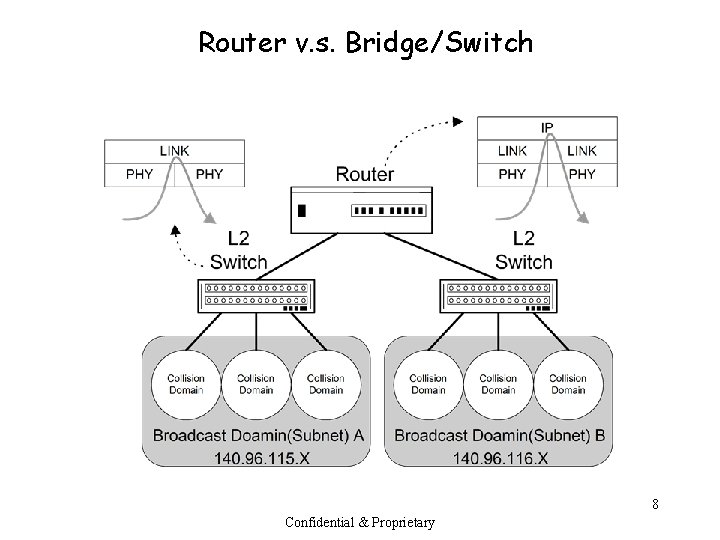
Router v. s. Bridge/Switch 8 Confidential & Proprietary

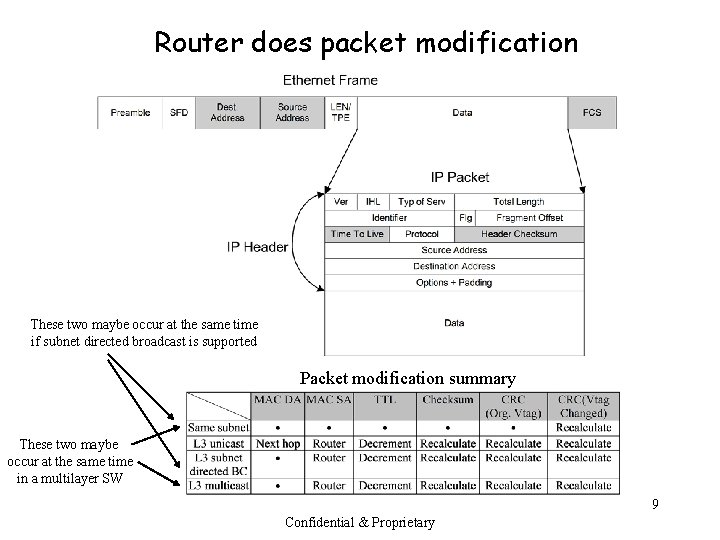
Router does packet modification These two maybe occur at the same time if subnet directed broadcast is supported Packet modification summary These two maybe occur at the same time in a multilayer SW 9 Confidential & Proprietary

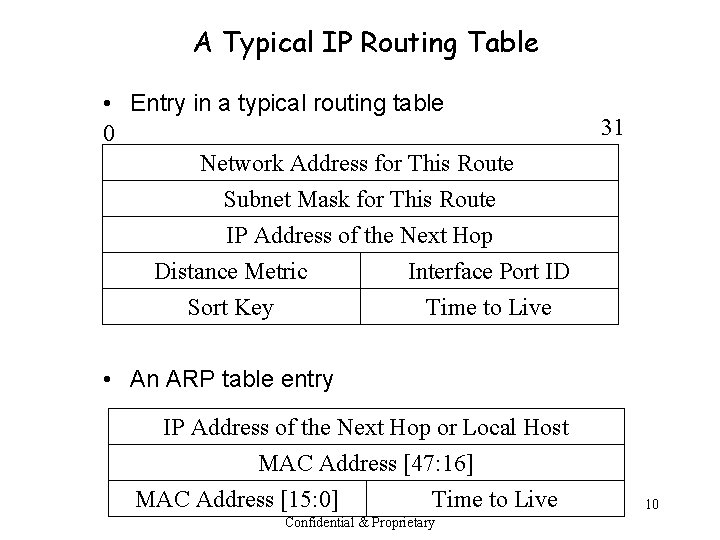
A Typical IP Routing Table • Entry in a typical routing table 0 Network Address for This Route Subnet Mask for This Route IP Address of the Next Hop Distance Metric Interface Port ID Sort Key Time to Live 31 • An ARP table entry IP Address of the Next Hop or Local Host MAC Address [47: 16] MAC Address [15: 0] Time to Live Confidential & Proprietary 10

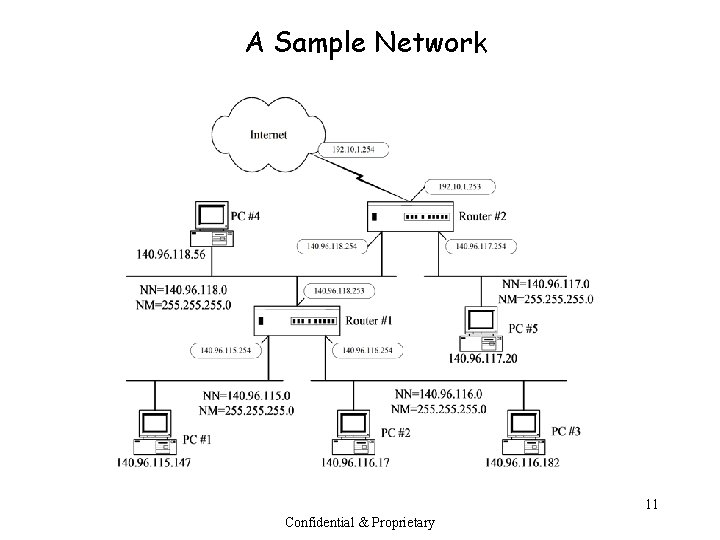
A Sample Network 11 Confidential & Proprietary

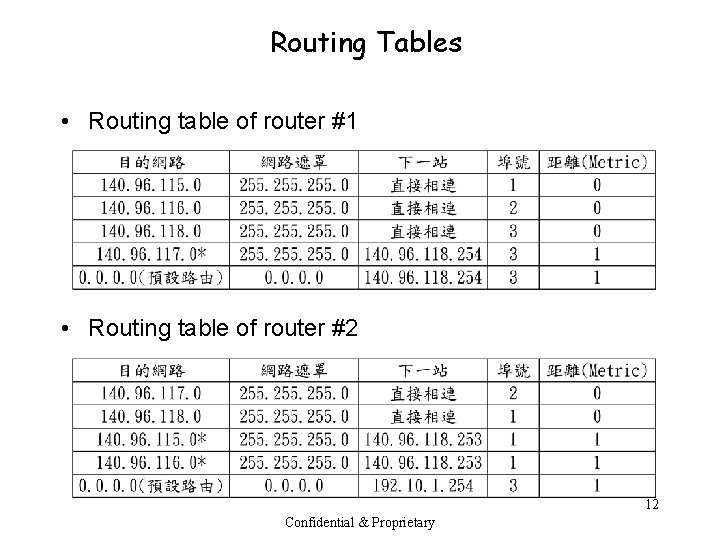
Routing Tables • Routing table of router #1 • Routing table of router #2 12 Confidential & Proprietary

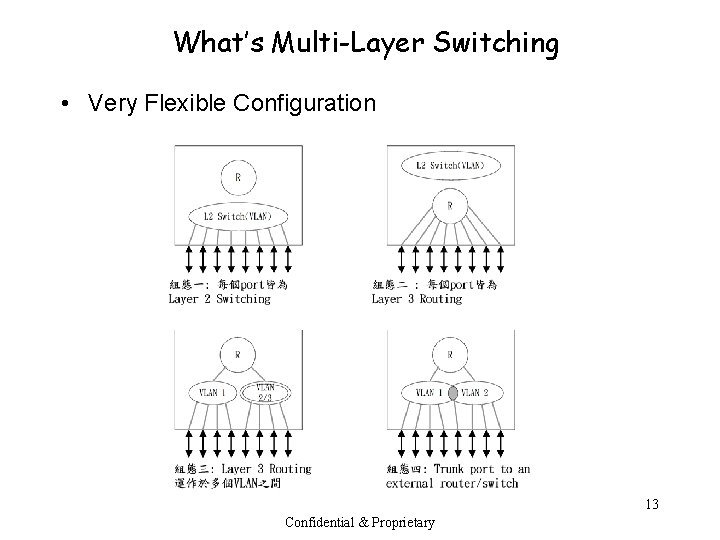
What’s Multi-Layer Switching • Very Flexible Configuration 13 Confidential & Proprietary

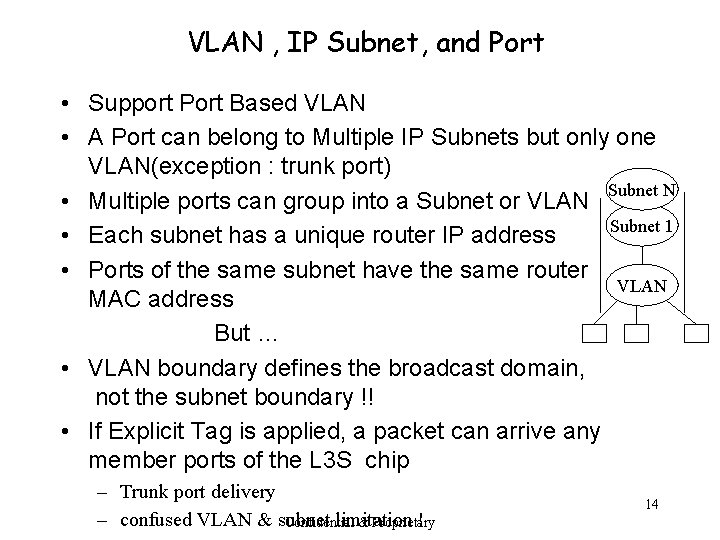
VLAN , IP Subnet, and Port • Support Port Based VLAN • A Port can belong to Multiple IP Subnets but only one VLAN(exception : trunk port) Subnet N • Multiple ports can group into a Subnet or VLAN Subnet 1 • Each subnet has a unique router IP address • Ports of the same subnet have the same router VLAN MAC address But … • VLAN boundary defines the broadcast domain, not the subnet boundary !! • If Explicit Tag is applied, a packet can arrive any member ports of the L 3 S chip – Trunk port delivery – confused VLAN & subnet limitation ! Confidential & Proprietary 14

VLAN , IP Subnet, and Port In Short, • VLAN (VID) is just a method to defines the broadcast domain of a IP subnet in our L 3 S design – Actually, there is only VLAN boundary but no subnet boundary !! – Or, Subnet boundary is virtually contained by the same router MAC address • Set VLAN Boundary = Subnet boundary you want to be -> normal operation 聽無 ? ! 15 Confidential & Proprietary

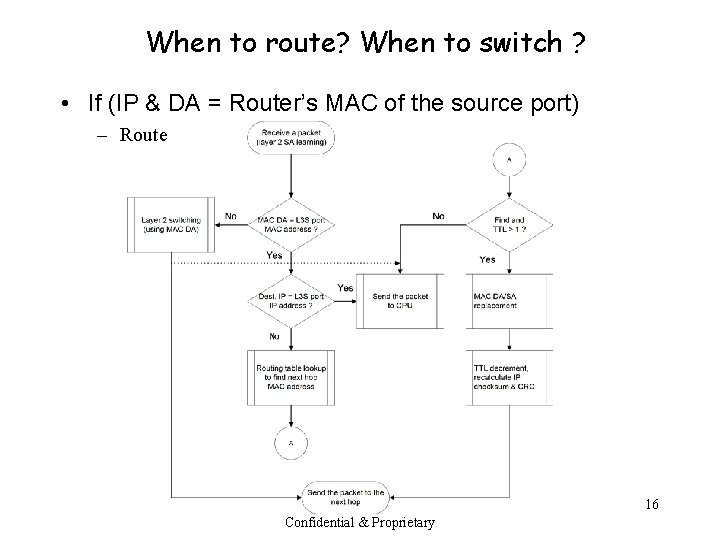
When to route? When to switch ? • If (IP & DA = Router’s MAC of the source port) – Route 16 Confidential & Proprietary

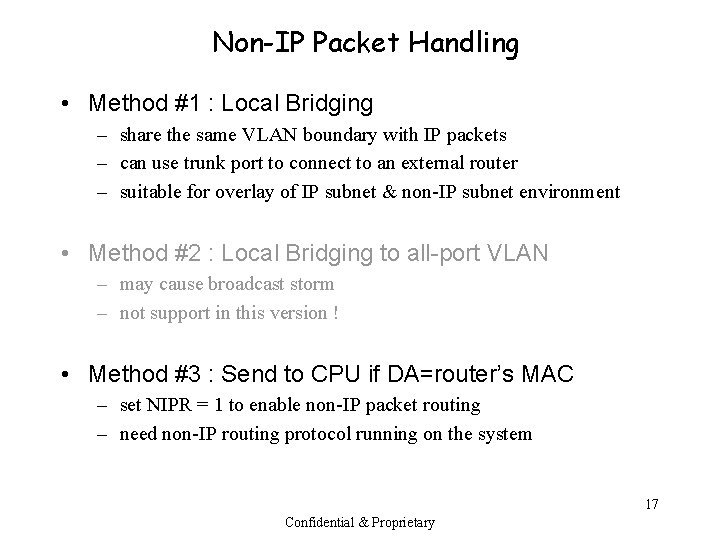
Non-IP Packet Handling • Method #1 : Local Bridging – share the same VLAN boundary with IP packets – can use trunk port to connect to an external router – suitable for overlay of IP subnet & non-IP subnet environment • Method #2 : Local Bridging to all-port VLAN – may cause broadcast storm – not support in this version ! • Method #3 : Send to CPU if DA=router’s MAC – set NIPR = 1 to enable non-IP packet routing – need non-IP routing protocol running on the system 17 Confidential & Proprietary

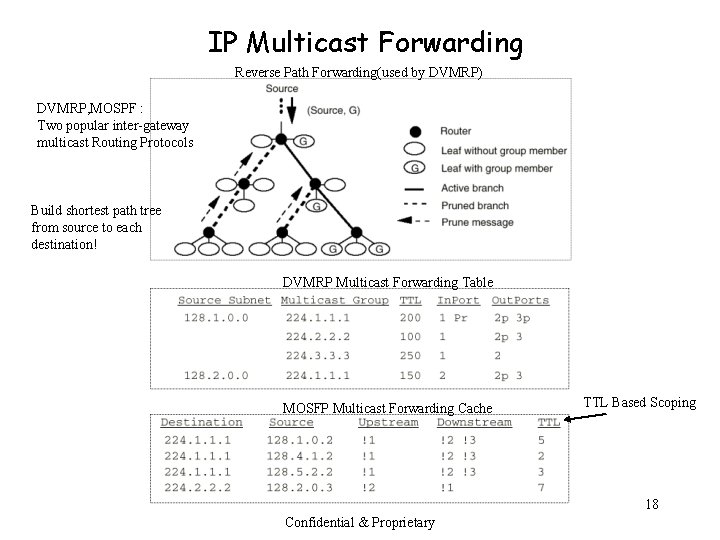
IP Multicast Forwarding Reverse Path Forwarding(used by DVMRP) DVMRP, MOSPF : Two popular inter-gateway multicast Routing Protocols Build shortest path tree from source to each destination! DVMRP Multicast Forwarding Table MOSFP Multicast Forwarding Cache TTL Based Scoping 18 Confidential & Proprietary

Agenda • • • Position of ARL in L 3 S Chip Concept of IP Routing & Multi-Layer Switching ARL Architecture and I/O interface Introduction to CIDR and Longest Prefix Matching ARL Detailed Design Forwarding Table Management ARL Performance Estimation Configuration Registers and Statistical Counters ARL Pin Assignment Q&A 19 Confidential & Proprietary

What’s CIDR • CIDR(Classless Inter-Domain Routing) is introduced to overcome the following problems – exhausting of class B network – explosion of internet routing table • CIDR allows any length of subnet mask – e. g. TWNIC can assign 2 class C networks(subnet mask length = 23) to a company if he has only 300 hosts=> efficient for IP address allocation – Router can aggregate several routes to a big route with less mask length=> reduce core router’s routing table size 20 Confidential & Proprietary

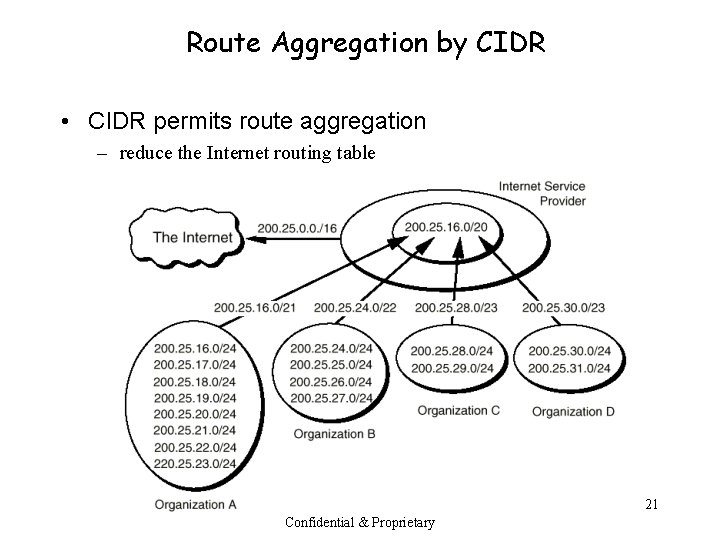
Route Aggregation by CIDR • CIDR permits route aggregation – reduce the Internet routing table 21 Confidential & Proprietary

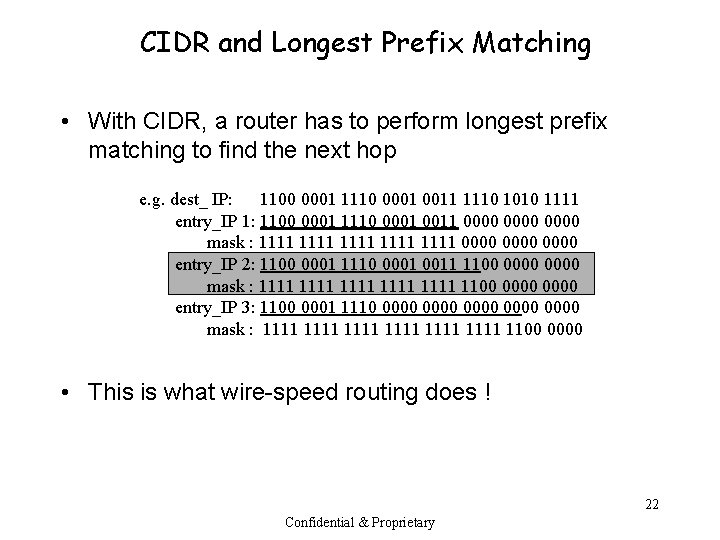
CIDR and Longest Prefix Matching • With CIDR, a router has to perform longest prefix matching to find the next hop e. g. dest_ IP: 1100 0001 1110 0001 0011 1110 1010 1111 entry_IP 1: 1100 0001 1110 0001 0011 0000 mask : 1111 1111 0000 entry_IP 2: 1100 0001 1110 0001 0011 1100 0000 mask : 1111 1111 1100 0000 entry_IP 3: 1100 0001 1110 0000 0000 mask : 1111 1111 1100 0000 • This is what wire-speed routing does ! 22 Confidential & Proprietary

Algorithm for Longest Prefix Matching 23 Confidential & Proprietary

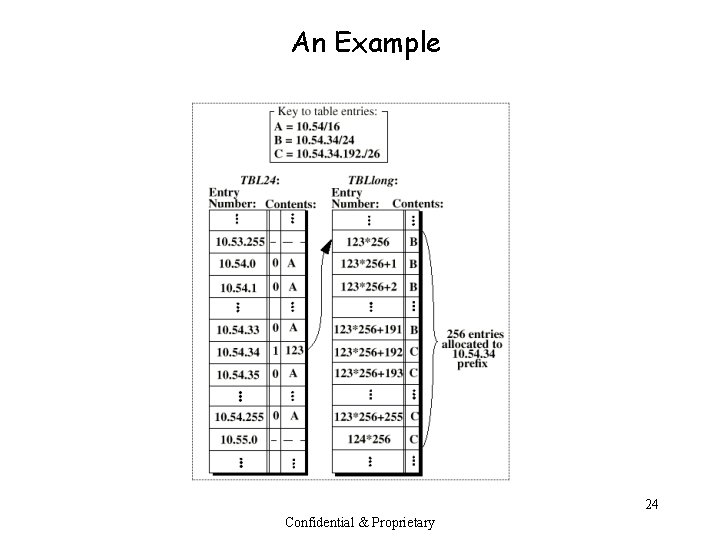
An Example 24 Confidential & Proprietary

Agenda • • • Position of ARL in L 3 S Chip Concept of IP Routing & Multi-Layer Switching Introduction to CIDR and Longest Prefix Matching ARL Architecture and I/O interface ARL Detailed Design Forwarding Table Management 25 Confidential & Proprietary

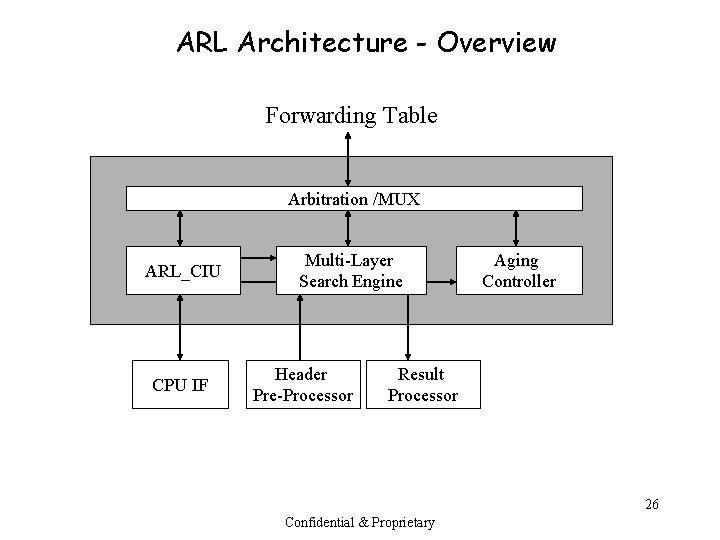
ARL Architecture - Overview Forwarding Table Arbitration /MUX ARL_CIU CPU IF Multi-Layer Search Engine Header Pre-Processor Aging Controller Result Processor 26 Confidential & Proprietary

ARL Architecture - Block Diagram 27 Confidential & Proprietary

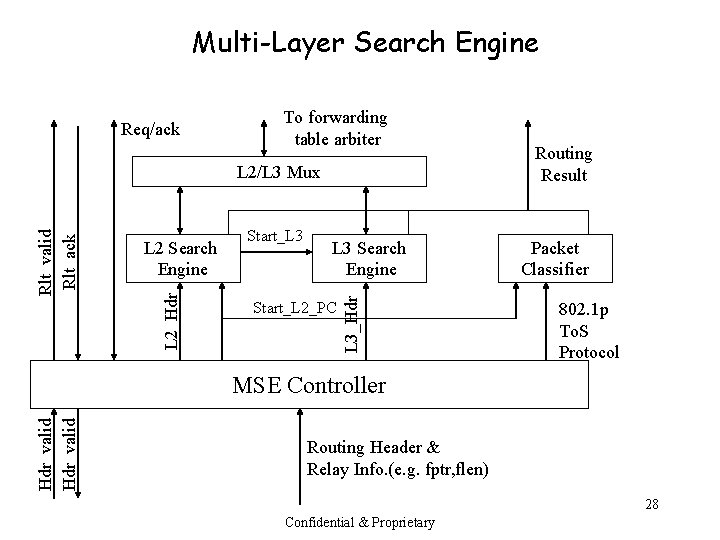
Multi-Layer Search Engine Req/ack To forwarding table arbiter Start_L 3 Search Engine Start_L 2_PC L 3_Hdr L 2 Search Engine L 2_Hdr Rlt_valid Rlt_ack L 2/L 3 Mux Routing Result Packet Classifier 802. 1 p To. S Protocol Hdr_valid MSE Controller Routing Header & Relay Info. (e. g. fptr, flen) 28 Confidential & Proprietary

Agenda • • • Position of ARL in L 3 S Chip Concept of IP Routing & Multi-Layer Switching Introduction to CIDR and Longest Prefix Matching ARL Architecture and I/O interface ARL Detailed Design Forwarding Table Management 29 Confidential & Proprietary

Overall Lookup Flow 30 Confidential & Proprietary

Forwarding Table Entry Format 31 Confidential & Proprietary

Layer 2 Search Engine- Flow Chart 32 Confidential & Proprietary

Layer 2 Search Engine- State Machine 33 Confidential & Proprietary

When to enter L 3 search engine • A Valid IP Packet – header checksum OK & length check OK…(by HPP) & • Routing Enable on this ort – configured by REM & • Destination MAC = Router port’s MAC or = Broadcast/Multicast MAC 34 Confidential & Proprietary

Layer 3 Search Engine- Flow Chart 35 Confidential & Proprietary

Layer 3 Search Engine- State Machine 36 Confidential & Proprietary

Packets to CPU • Layer 2 Control packets – BPDU, GMRP, GVRP • ARP packets • !IP & DA=Router’s MAC or Multicast MAC & RE & NIPR=1 – e. g. IPX packets • IP & DA=Router’s MAC or Multicast MAC & !RE – disable hardware routing but enable CPU routing for IPpackets • Layer 3 Lookup with AT=00, 01, 10 or an invalid ARP entry – black hole, ARP age out, router’s IP(s), broadcast IP(s) • • Layer 3 Lookup with TTL < 2 Layer 3 Lookup with a Miss in IP Multicast lookup Layer 3 Lookup with Ver != 4 or Hlen != 5 IGMP or IP=224. x. x. 0 37 Confidential & Proprietary

Packet Classifier - Circuit 38 Confidential & Proprietary

Agenda • • • Position of ARL in L 3 S Chip Concept of IP Routing & Multi-Layer Switching ARL Architecture and I/O interface Introduction to CIDR and Longest Prefix Matching ARL Detailed Design Forwarding Table Management 39 Confidential & Proprietary

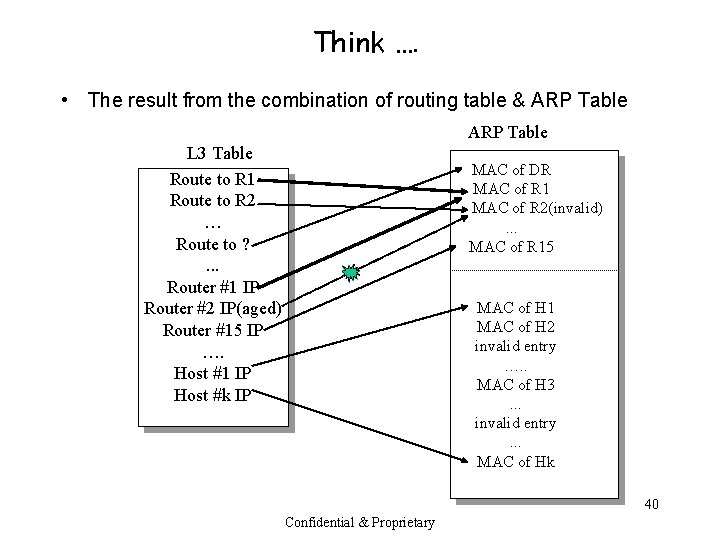
Think …. • The result from the combination of routing table & ARP Table L 3 Table Route to R 1 Route to R 2 … Route to ? . . . Router #1 IP Router #2 IP(aged) Router #15 IP …. Host #1 IP Host #k IP MAC of DR MAC of R 1 MAC of R 2(invalid). . . MAC of R 15 MAC of H 1 MAC of H 2 invalid entry …. . MAC of H 3. . . invalid entry. . . MAC of Hk 40 Confidential & Proprietary